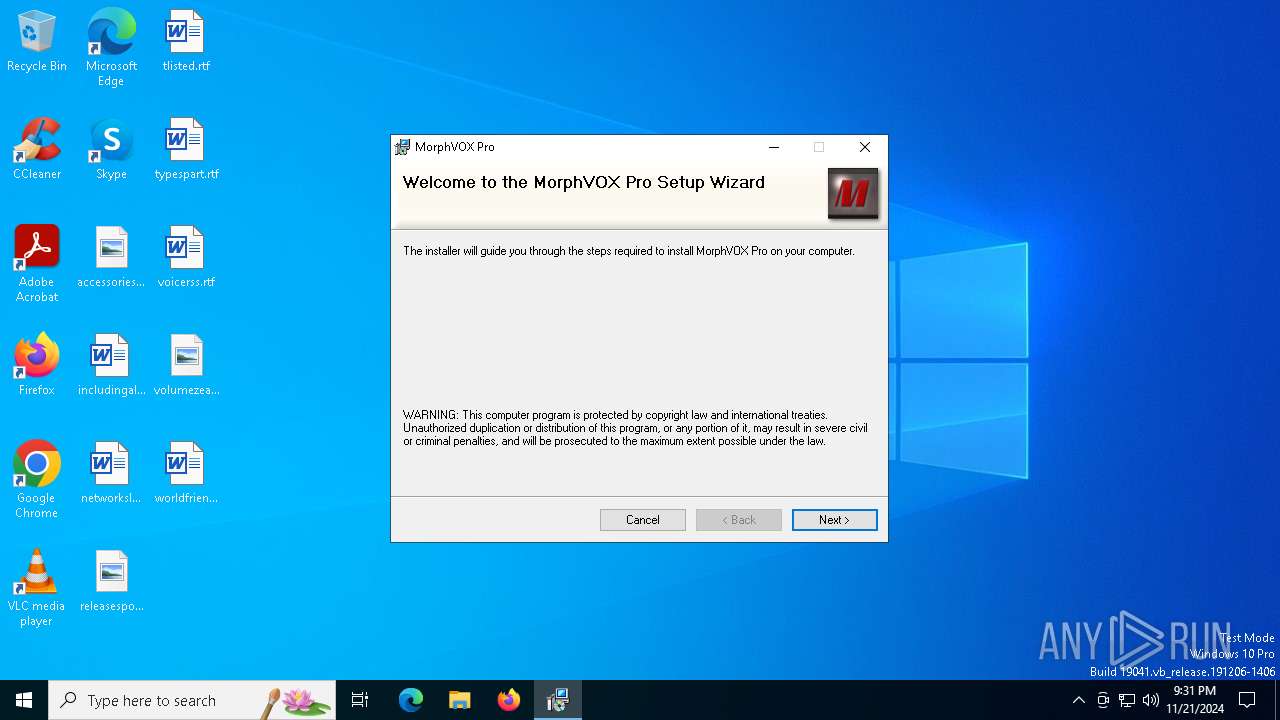
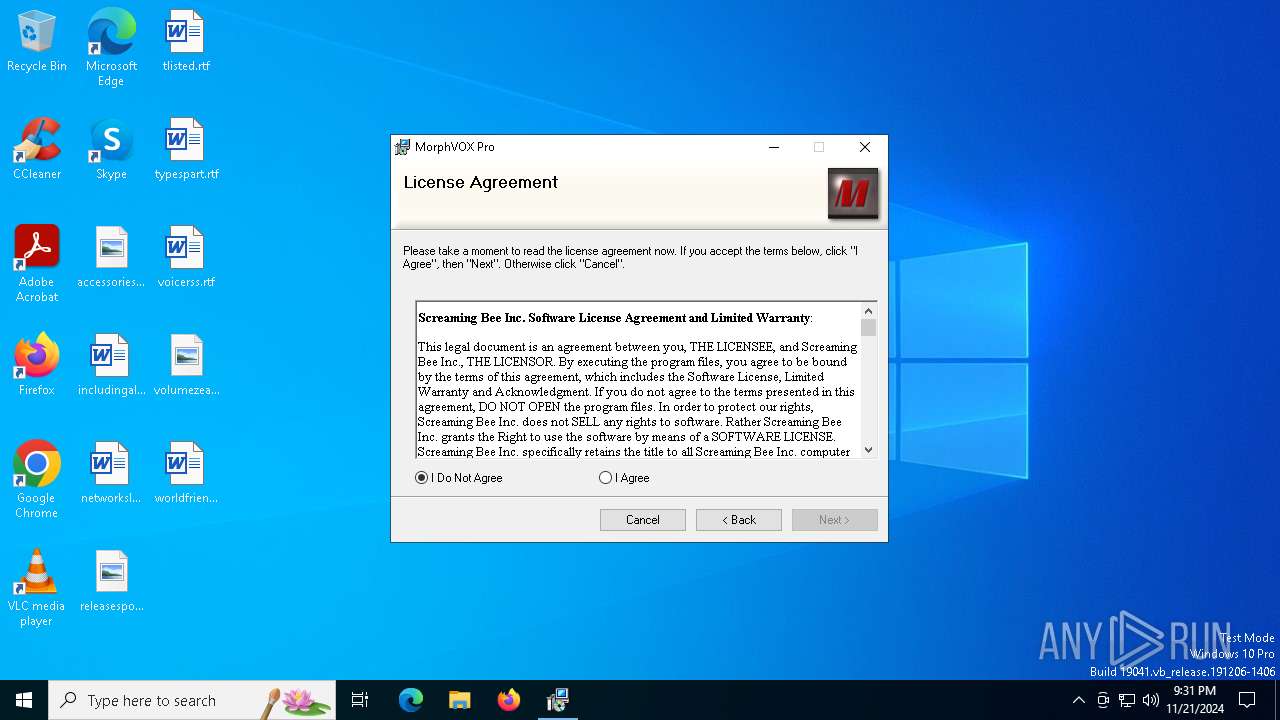
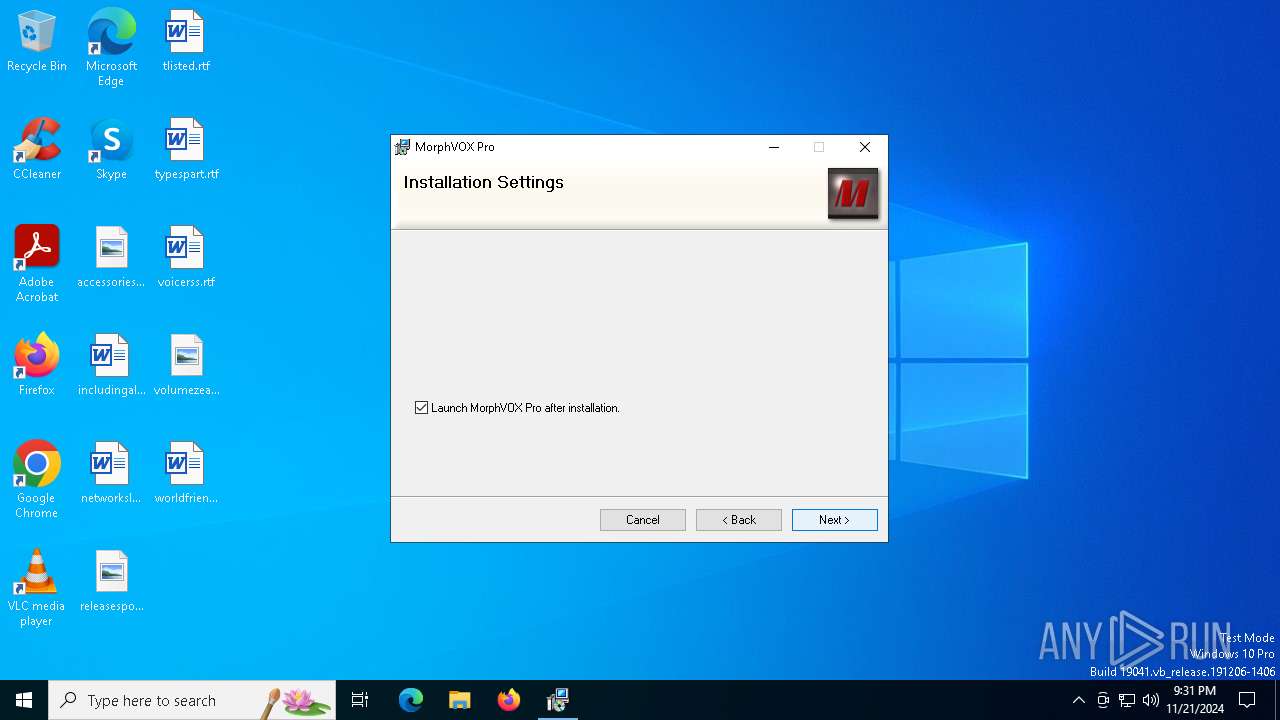
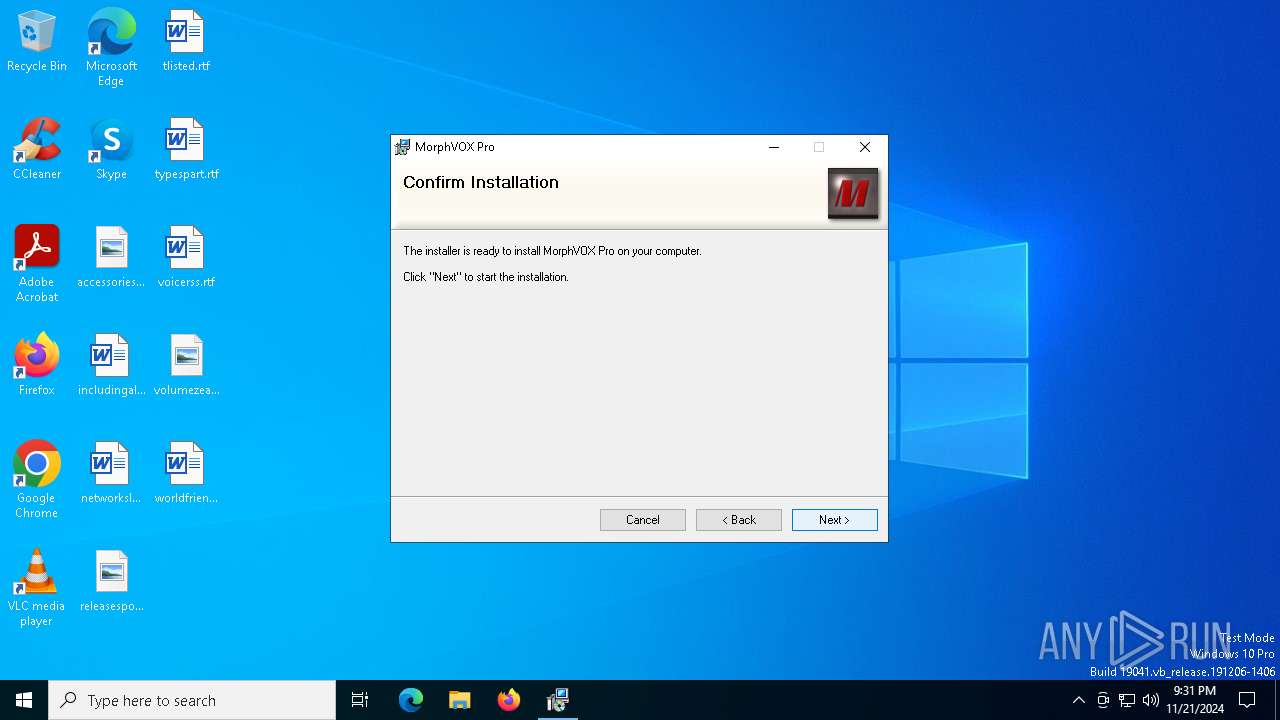
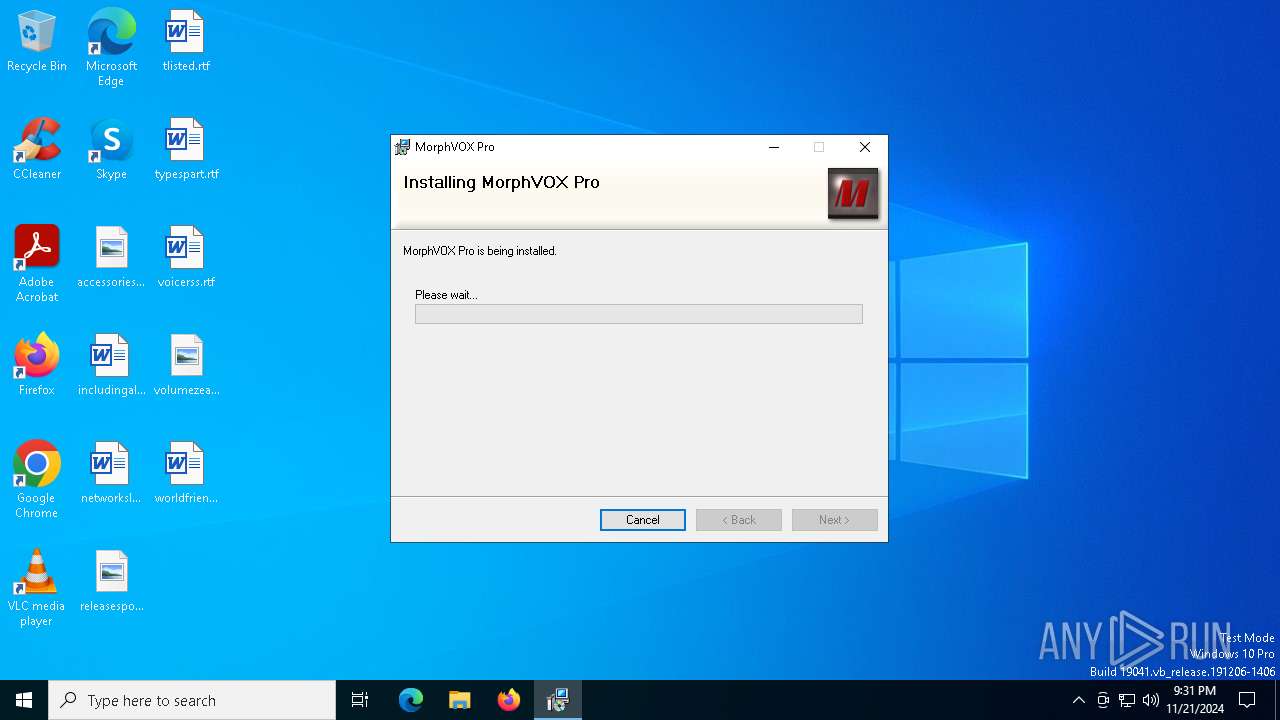
| File name: | MorphVOXPro.msi |
| Full analysis: | https://app.any.run/tasks/704d742c-8d5a-4306-9865-3cd4616bbc76 |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2024, 21:31:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: MorphVOX Pro, Author: Screaming Bee Inc., Keywords: MorphVOX Pro Voice Changer game tools, Comments: MorphVOX Pro Installer, Template: Intel;1033, Revision Number: {F0D3D450-99B2-491F-B35A-E59D60210323}, Create Time/Date: Wed Oct 23 19:42:18 2019, Last Saved Time/Date: Wed Oct 23 19:42:18 2019, Number of Pages: 301, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.0.1701), Security: 2 |
| MD5: | 1067B768CF4705D5FB4EFA1A0736F063 |
| SHA1: | 63131EC8CBAFB30BB6376F4F882D8859CA960F58 |
| SHA256: | BF01560D2510DF39C8697D2ACEC7F48F5C08588276959B6829F7888F504E9E9B |
| SSDEEP: | 98304:+03bbXZv7kc1r1l+wuM01aUS/GRkiixoCrpaUa4OHbtCnElCDi6erAA+VnaA990M:Yx7wVUJ5cN4wrR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 7004)
- drvinst.exe (PID: 7052)
- msiexec.exe (PID: 492)
Process drops legitimate windows executable
- msiexec.exe (PID: 492)
Executable content was dropped or overwritten
- drvinst.exe (PID: 7004)
- drvinst.exe (PID: 7052)
Executes as Windows Service
- VSSVC.exe (PID: 6192)
INFO
Reads the software policy settings
- msiexec.exe (PID: 1616)
An automatically generated document
- msiexec.exe (PID: 1616)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1616)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1616)
- msiexec.exe (PID: 492)
Manages system restore points
- SrTasks.exe (PID: 6580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | MorphVOX Pro |
| Author: | Screaming Bee Inc. |
| Keywords: | MorphVOX Pro Voice Changer game tools |
| Comments: | MorphVOX Pro Installer |
| Template: | Intel;1033 |
| RevisionNumber: | {F0D3D450-99B2-491F-B35A-E59D60210323} |
| CreateDate: | 2019:10:23 19:42:18 |
| ModifyDate: | 2019:10:23 19:42:18 |
| Pages: | 301 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.0.1701) |
| Security: | Read-only recommended |
Total processes
143
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\MorphVOXPro.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3428 | C:\Windows\syswow64\MsiExec.exe -Embedding AE9747A827BDC8DBB3A7FB5478D467C6 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 1 Version: 123.26505.0.0 | |||||||||||||||
| 6192 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6580 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6732 | C:\Windows\syswow64\MsiExec.exe -Embedding 81C03D743AA9B8E2CE7B0FCACA565835 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 6788 | C:\Windows\syswow64\MsiExec.exe -Embedding BCDBF12DAA60FD772CE0E0CC8B5B6340 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 6868 | "C:\Program Files (x86)\Screaming Bee\MorphVOX Pro\Drivers\SBDriverInstaller.exe" i | C:\Program Files (x86)\Screaming Bee\MorphVOX Pro\drivers\SBDriverInstaller.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Screaming Bee Inc Integrity Level: SYSTEM Description: Screaming Bee Driver Installer x86 Exit code: 0 Version: 3.0.3.0 | |||||||||||||||
Total events
6 724
Read events
6 585
Write events
130
Delete events
9
Modification events
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000000D33B3B95C3CDB01EC01000020180000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000D33B3B95C3CDB01EC01000020180000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000098D6EEB95C3CDB01EC01000020180000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000098D6EEB95C3CDB01EC01000020180000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000119FF3B95C3CDB01EC01000020180000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000E0EFF5B95C3CDB01EC01000020180000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000022F6DBA5C3CDB01EC01000020180000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000006D926FBA5C3CDB01EC01000088180000E8030000010000000000000000000000955A9326A8D4384AAE49393A7A89C4E100000000000000000000000000000000 | |||
| (PID) Process: | (6192) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000032847BBA5C3CDB0130180000A0180000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
21
Suspicious files
44
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 492 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 492 | msiexec.exe | C:\Windows\Installer\f070b.msi | — | |
MD5:— | SHA256:— | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_E6095CD2AECC9011BCD0D7B421356B17 | der | |
MD5:9006C7E4BE1D714E609B00DDE9218D79 | SHA256:A225F15F364303660E4569489FEB9D574E1A33DC8215A57409A40F1C84E55840 | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI9AA5.tmp | executable | |
MD5:911AA8D08B7CCAB654E897B0E4439354 | SHA256:BA56A2FA13E5DAE48B6D74A8FA40F2F44473B386E71BA1E7EC2DED90AD56BB8B | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_E6095CD2AECC9011BCD0D7B421356B17 | binary | |
MD5:15C5A45CC1F7ABC85C7EF6446523574F | SHA256:3D479338801EAB2B4BB460177037488197B62FC0F308FD8F011E902484BB7DF7 | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D7833C286363AD25C70511661A83D581_8BAE630DB3DD7F85102CAF57E0473945 | der | |
MD5:6EBA68AE11A2D50A45F2F6312BC48BAD | SHA256:D951416635E7540313193CE69896D6907D0C91FECDAB1D37B141DB3E6DC1701D | |||
| 492 | msiexec.exe | C:\Windows\Installer\MSI8F0.tmp | executable | |
MD5:911AA8D08B7CCAB654E897B0E4439354 | SHA256:BA56A2FA13E5DAE48B6D74A8FA40F2F44473B386E71BA1E7EC2DED90AD56BB8B | |||
| 492 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:BB0824BEBDAD1C0AFC02CC68BB5AB3DA | SHA256:D6D9B2FED9D7C61022D6C9F142338E6470F483DFB1432018204379E80A0FC85A | |||
| 492 | msiexec.exe | C:\Windows\Temp\~DF0EC98E6E775C112A.TMP | binary | |
MD5:BB0824BEBDAD1C0AFC02CC68BB5AB3DA | SHA256:D6D9B2FED9D7C61022D6C9F142338E6470F483DFB1432018204379E80A0FC85A | |||
| 492 | msiexec.exe | C:\Windows\Installer\MSIA78.tmp | binary | |
MD5:0E9587800D9504B50566C3FFB9A5AE8F | SHA256:DFB40A511DB38525E31ACF120455A25110352C6F625B161B18761288D7E36500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
39
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1616 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ5suEceKjAJbxseAmHFkQ9FrhTWQQUDuE6qFM6MdWKvsG7rWcaA4WtNA4CEBBfVLf%2FUI84r0eBQQQxRkk%3D | unknown | — | — | whitelisted |
1616 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB2iSDBvmyYY0ILgln0z02o%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1616 | msiexec.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | whitelisted |
4932 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |