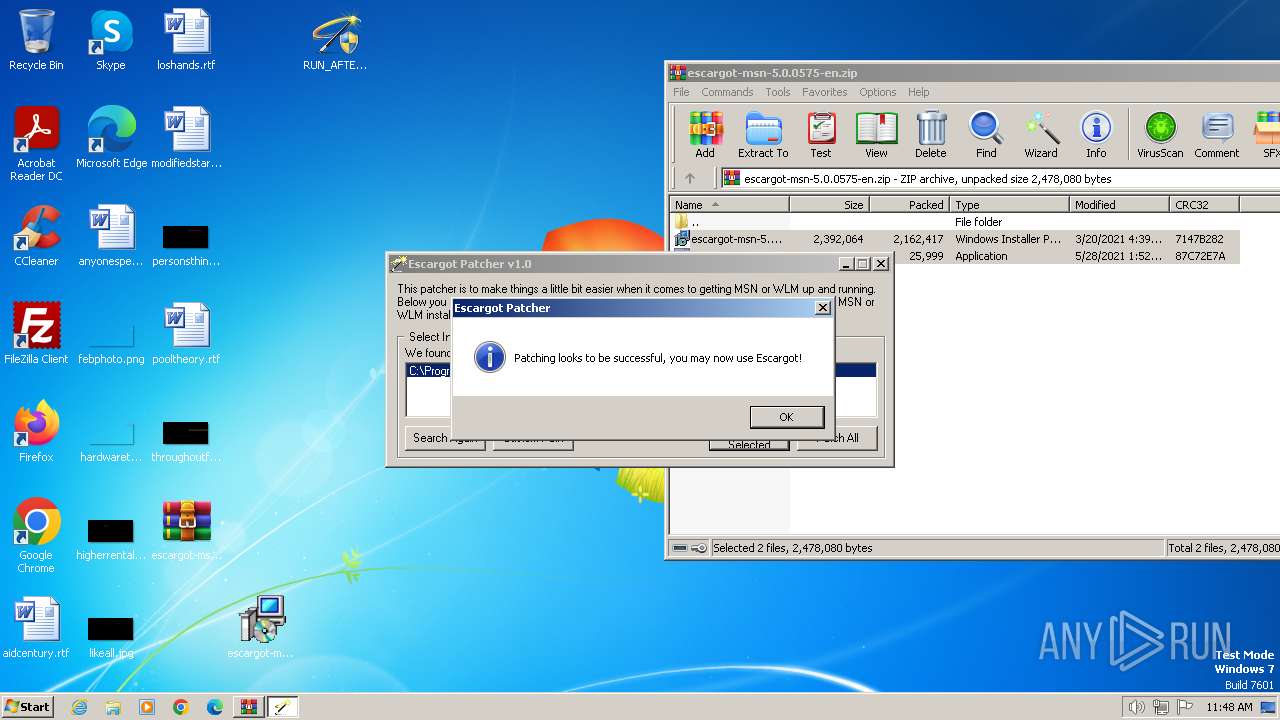
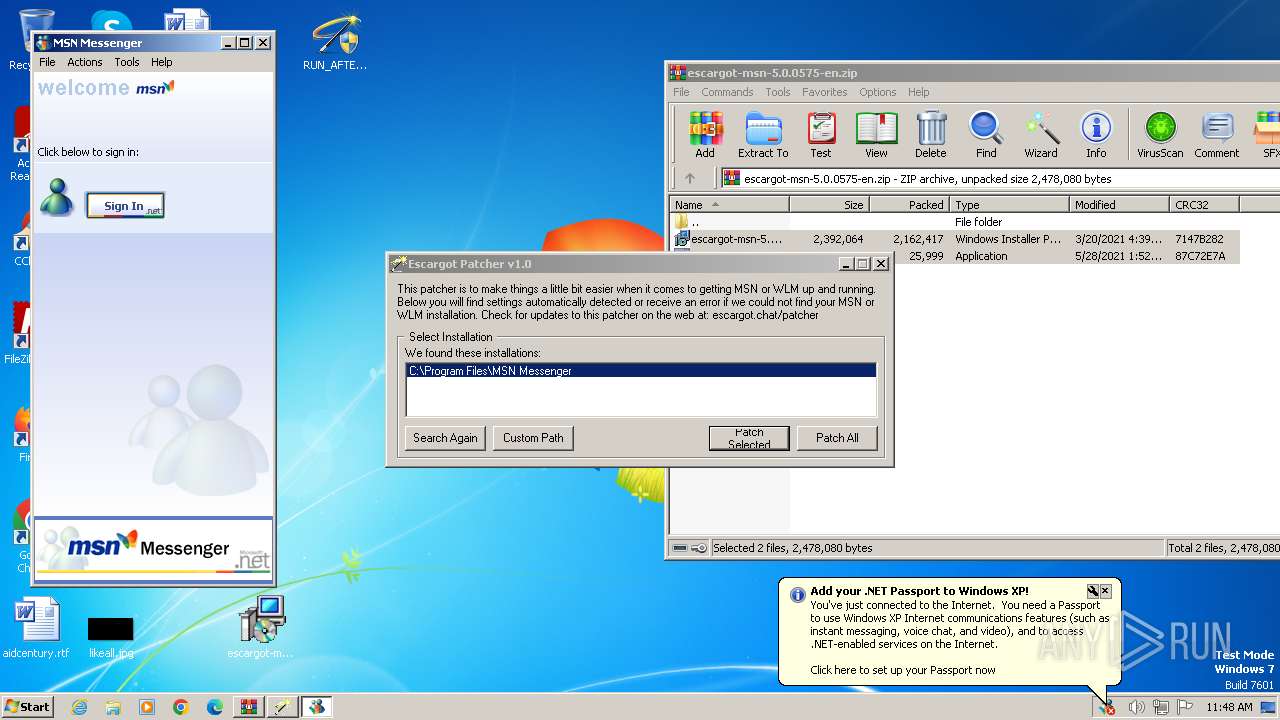
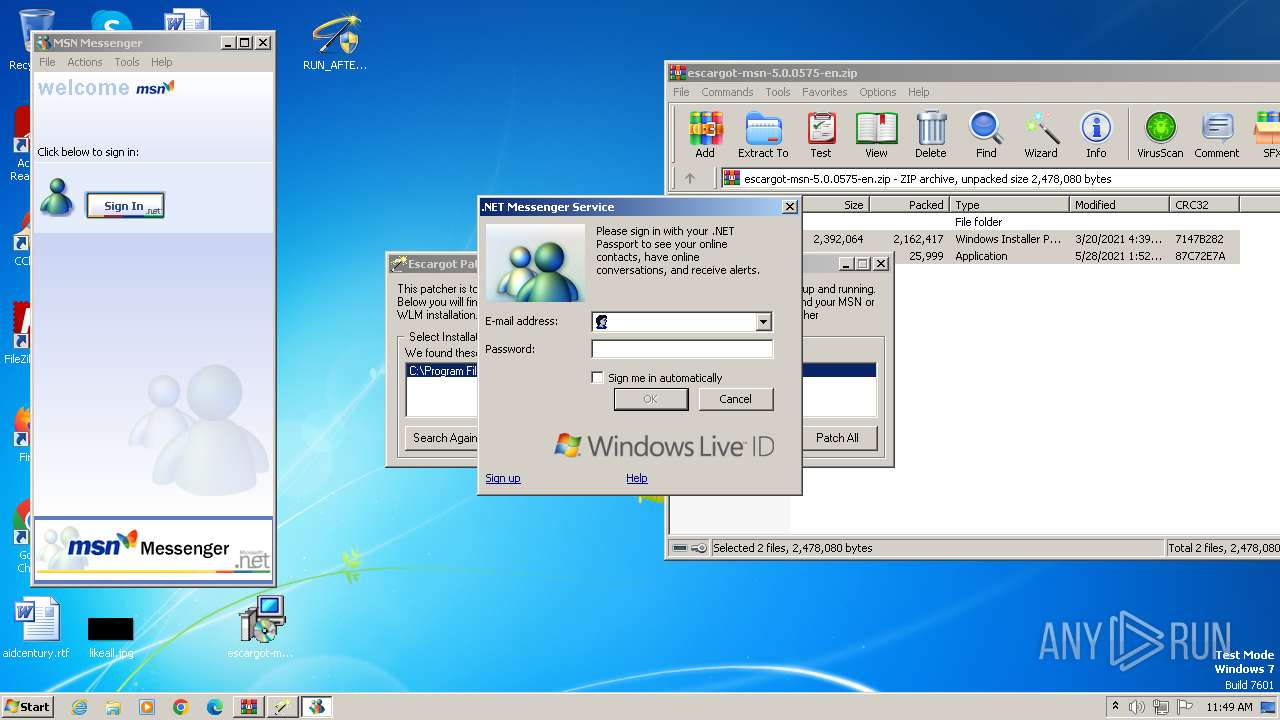
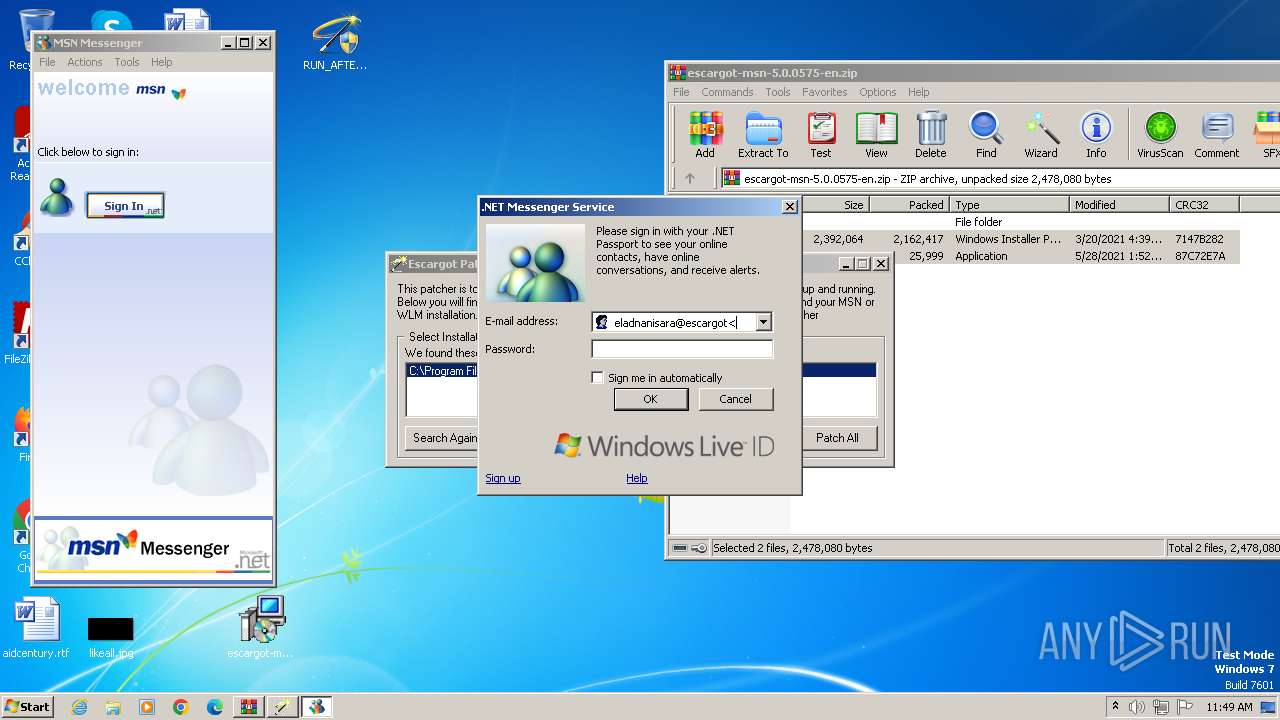
| File name: | escargot-msn-5.0.0575-en.zip |
| Full analysis: | https://app.any.run/tasks/49f8c9f6-d833-4b11-be18-7aed719a5372 |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2024, 11:47:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BB21E4D5862F2AA373F90D19BAF44B9E |
| SHA1: | 75C5648969706ED06D8A542CED632C1D3FB5E3E0 |
| SHA256: | BEEC09CC772EF29D86E77F2AA691814E7BA0419C15E81BE4F4A38F3AFAF516A9 |
| SSDEEP: | 98304:p9csrnZKWjXaFFkxKdsLd5K5rILiubSafqmwVV/UpCM5Z8tdJZ2XDPqmTLKtZAt4:HvX2Yhhluu0 |
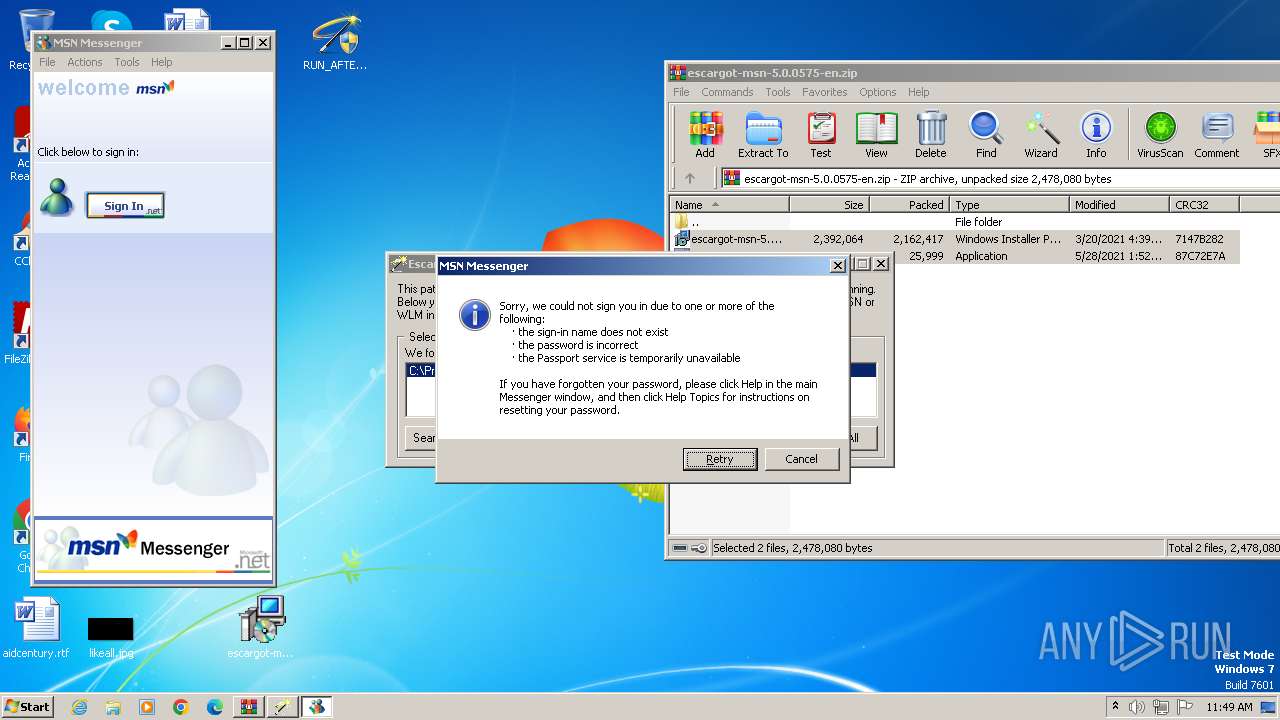
MALICIOUS
Drops the executable file immediately after the start
- rundll32.exe (PID: 2472)
Changes the autorun value in the registry
- msnmsgr.exe (PID: 2244)
Scans artifacts that could help determine the target
- msnmsgr.exe (PID: 2244)
- msnmsgr.exe (PID: 3556)
SUSPICIOUS
Process drops legitimate windows executable
- rundll32.exe (PID: 2472)
- msiexec.exe (PID: 3500)
Executes as Windows Service
- VSSVC.exe (PID: 3392)
Reads the Internet Settings
- msnmsgr.exe (PID: 2244)
- msnmsgr.exe (PID: 3556)
Checks Windows Trust Settings
- msnmsgr.exe (PID: 3556)
Reads security settings of Internet Explorer
- msnmsgr.exe (PID: 3556)
Reads settings of System Certificates
- msnmsgr.exe (PID: 3556)
Reads Microsoft Outlook installation path
- msnmsgr.exe (PID: 3556)
Connects to unusual port
- msnmsgr.exe (PID: 3556)
Reads Internet Explorer settings
- msnmsgr.exe (PID: 3556)
Adds/modifies Windows certificates
- msnmsgr.exe (PID: 3556)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3944)
- rundll32.exe (PID: 3720)
- msiexec.exe (PID: 3500)
- RUN_AFTER_INSTALL.exe (PID: 2972)
- RUN_AFTER_INSTALL.exe (PID: 1544)
- msnmsgr.exe (PID: 3556)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3500)
- WinRAR.exe (PID: 3944)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3500)
- WinRAR.exe (PID: 3944)
Checks supported languages
- msnmsgr.exe (PID: 2244)
- RUN_AFTER_INSTALL.exe (PID: 1544)
- msnmsgr.exe (PID: 3556)
Reads the computer name
- msnmsgr.exe (PID: 2244)
- msnmsgr.exe (PID: 3556)
Reads the machine GUID from the registry
- msnmsgr.exe (PID: 2244)
- RUN_AFTER_INSTALL.exe (PID: 1544)
- msnmsgr.exe (PID: 3556)
Checks proxy server information
- msnmsgr.exe (PID: 2244)
- msnmsgr.exe (PID: 3556)
Create files in a temporary directory
- RUN_AFTER_INSTALL.exe (PID: 1544)
- msnmsgr.exe (PID: 3556)
Reads the software policy settings
- msnmsgr.exe (PID: 3556)
Creates files or folders in the user directory
- msnmsgr.exe (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:03:20 11:39:54 |
| ZipCRC: | 0x7147b282 |
| ZipCompressedSize: | 2162417 |
| ZipUncompressedSize: | 2392064 |
| ZipFileName: | escargot-msn-5.0.0575-en.msi |
Total processes
54
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Users\admin\Desktop\RUN_AFTER_INSTALL.exe" | C:\Users\admin\Desktop\RUN_AFTER_INSTALL.exe | explorer.exe | ||||||||||||
User: admin Company: Level Leap, Inc (levelleap.com) Integrity Level: HIGH Description: Patcher for Escargot Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\MSN Messenger\msnmsgr.exe" | C:\Program Files\MSN Messenger\msnmsgr.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Messenger Exit code: 1 Version: 5.0.0575 Modules
| |||||||||||||||
| 2472 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\Desktop\escargot-msn-5.0.0575-en.zip.xpi" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | "C:\Users\admin\Desktop\RUN_AFTER_INSTALL.exe" | C:\Users\admin\Desktop\RUN_AFTER_INSTALL.exe | — | explorer.exe | |||||||||||
User: admin Company: Level Leap, Inc (levelleap.com) Integrity Level: MEDIUM Description: Patcher for Escargot Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 3392 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3500 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\escargot-msn-5.0.0575-en.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3556 | "C:\Program Files\MSN Messenger\msnmsgr.exe" | C:\Program Files\MSN Messenger\msnmsgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Messenger Exit code: 0 Version: 5.0.0575 Modules
| |||||||||||||||
| 3720 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\escargot-msn-5.0.0575-en.zip.xpi | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3944 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\escargot-msn-5.0.0575-en.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 088
Read events
11 858
Write events
203
Delete events
27
Modification events
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\escargot-msn-5.0.0575-en.zip | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3944) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
6
Text files
18
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA042.tmp | executable | |
MD5:F89D26235C1C595031E66F1535393751 | SHA256:921A5FC7E0E6E14E5B4AB7E6AA4795E26EF268FE21945BCA1060029B4772F8E1 | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:3AA9A4C77380967F9DCCBF42D2C1D289 | SHA256:66237F71069966635C418E0E98B04AC7EF8BB0BCEF5AACDD1C2353A8E4AA5233 | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 3944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3944.26174\escargot-msn-5.0.0575-en.msi | executable | |
MD5:FDA36DB9CF47698D0E19A3AB74392D8B | SHA256:D429B485B05B85187A07F2C7FF285D6B99AB82B30F0DA2459636CA460165B981 | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\wlm[1].htm | html | |
MD5:BD2695F4B079C71DBDDDE3436286FB9C | SHA256:2E04A18FF185BA5B16F762A0538339BC4049ACEAEF9738EDD43AF77D2CEB788B | |||
| 3500 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA796.tmp | executable | |
MD5:F89D26235C1C595031E66F1535393751 | SHA256:921A5FC7E0E6E14E5B4AB7E6AA4795E26EF268FE21945BCA1060029B4772F8E1 | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:6EC7E3A90A364EBB94FC1CC9E9158FC7 | SHA256:31B9B36EAB494D5019341A1EC731AB85CE45AC0CC5EBE0A701D655D0AF47A6ED | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\adxml_main[1].htm | html | |
MD5:CD2E0E43980A00FB6A2742D3AFD803B8 | SHA256:BD9DF047D51943ACC4BC6CF55D88EDB5B6785A53337EE2A0F74DD521AEDDE87D | |||
| 3556 | msnmsgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\tabs[1].xml | xml | |
MD5:215FF7D9909B0D22B46A1E22DBA2E58E | SHA256:3B2EE95EAD64178A670293078A647C5F16A626C4B7C6E50FC433D50AF7884FE7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
27
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3556 | msnmsgr.exe | GET | 304 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?87bd4a9a22bae384 | unknown | — | — | unknown |
3556 | msnmsgr.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3556 | msnmsgr.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
1080 | svchost.exe | GET | 200 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b8fee253118cbef | unknown | compressed | 67.5 Kb | unknown |
3556 | msnmsgr.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/s/gts1p5/gpmwVaPxyz8/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTsSieX%2BJFZNROWeLPoyKIdCXsxLgQU1fyeDd8eyt0Il5duK8VfxSv17LgCEA5zqYMOM7T%2FE7sziAKxSmU%3D | unknown | binary | 471 b | unknown |
3556 | msnmsgr.exe | GET | 301 | 143.198.4.104:80 | http://msnmsgr.escargot.chat/svcs/mms/adxml_main.asp?Version=5.0&Plcid=0409&CLCID=0409&BrandID=MSMSGS&country=00&PUID=e90310745484e9a3&random=1752421 | unknown | html | 178 b | unknown |
1080 | svchost.exe | GET | 304 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9e294a7a0d3799e6 | unknown | compressed | 67.5 Kb | unknown |
3556 | msnmsgr.exe | GET | 301 | 143.198.4.104:80 | http://msnmsgr.escargot.chat/svcs/mms/portal.asp?Plcid=0409&Version=5.0&CLCID=0409&BrandID=MSMSGS&Country=00&component=MSNExtra&autolaunch=1&random=1752421&pod=797 | unknown | html | 178 b | unknown |
3556 | msnmsgr.exe | GET | 302 | 143.198.4.104:80 | http://msnmsgr.escargot.chat/5meen_us/60?Plcid=0409&Version=5.0&CLCID=0409&BrandID=MSMSGS&Country=00 | unknown | text | 10 b | unknown |
3556 | msnmsgr.exe | GET | 302 | 143.198.4.104:80 | http://msnmsgr.escargot.chat/svcs/mms/tabs.asp | unknown | text | 10 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3556 | msnmsgr.exe | 143.198.4.104:443 | msnmsgr.escargot.chat | DIGITALOCEAN-ASN | US | unknown |
3556 | msnmsgr.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3556 | msnmsgr.exe | 142.250.184.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3556 | msnmsgr.exe | 143.198.4.104:1863 | msnmsgr.escargot.chat | DIGITALOCEAN-ASN | US | unknown |
3556 | msnmsgr.exe | 143.198.4.104:80 | msnmsgr.escargot.chat | DIGITALOCEAN-ASN | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
msnmsgr.escargot.chat |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
m1.escargot.chat |
| unknown |
e450.voice.microsoft.com |
| unknown |
conf.escargot.chat |
| unknown |
escargot.chat |
| unknown |
storage.levelleap.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3556 | msnmsgr.exe | Potential Corporate Privacy Violation | GPL CHAT MSN login attempt |