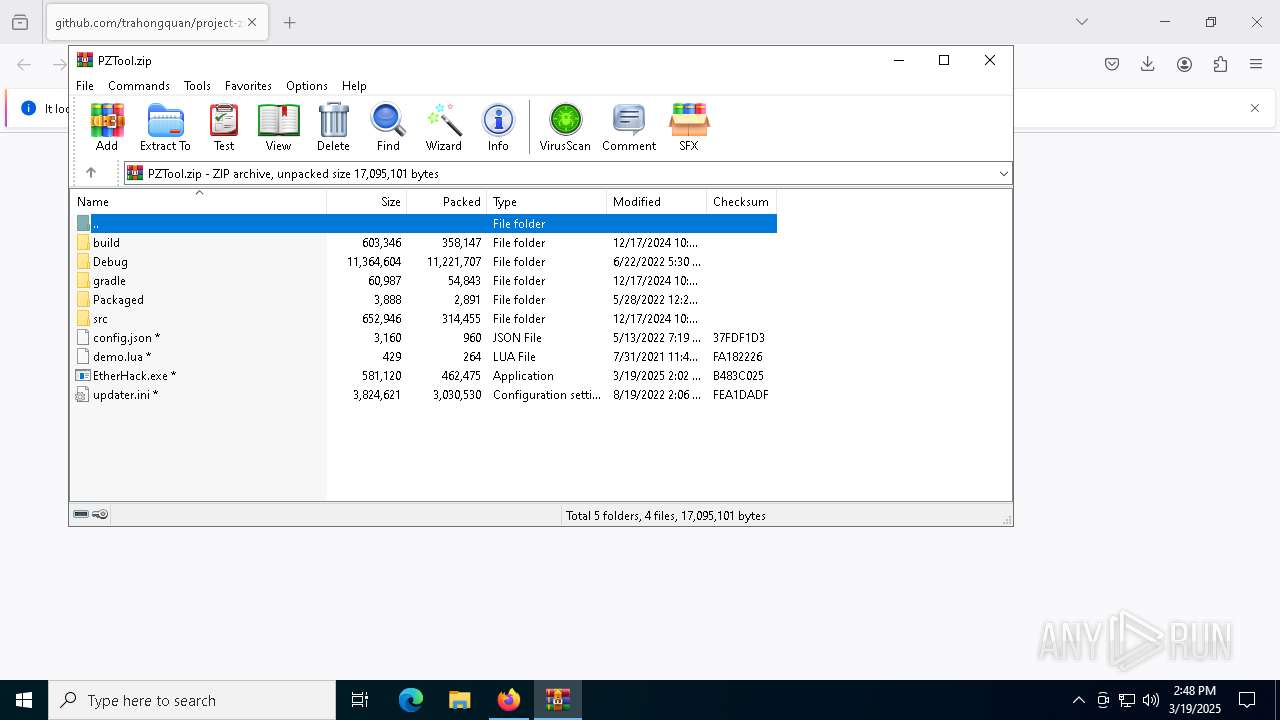
| URL: | https://github.com/trahongquan/project-zomboid-cheat-menu/releases/download/Project-Zomboid-Cheat-menu/PZTool.zip |
| Full analysis: | https://app.any.run/tasks/3076361e-891d-423d-b7b8-7cfabfe2b4ad |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | March 19, 2025, 14:48:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0E4EC64323AD937B9EAF400BAE04C0BE |
| SHA1: | 70C38C5A19BCAEC0C7CF0F94C7195388BC3326AA |
| SHA256: | BEE8F1C1F9AF2414CA0E6061732B73DA491FEFBC191E2258559E716651BF97F3 |
| SSDEEP: | 3:N8tEdhXENXJiOa4GE+GNHQa2kCd4rr4QG4fUn:2uE19alE+GeVz4rrH/fU |
MALICIOUS
LUMMA mutex has been found
- MSBuild.exe (PID: 904)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 904)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 904)
SUSPICIOUS
Reads security settings of Internet Explorer
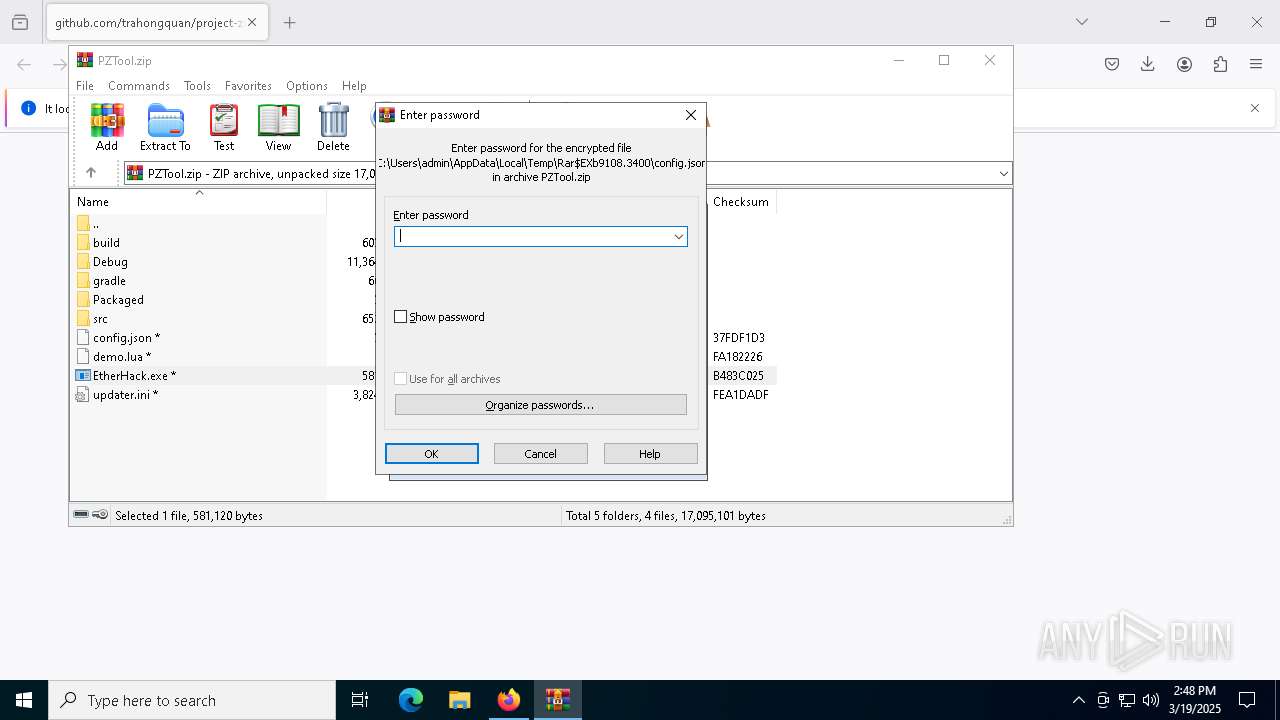
- WinRAR.exe (PID: 9108)
Process requests binary or script from the Internet
- MSBuild.exe (PID: 904)
Connects to the server without a host name
- MSBuild.exe (PID: 904)
Executable content was dropped or overwritten
- MSBuild.exe (PID: 904)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 904)
Searches for installed software
- MSBuild.exe (PID: 904)
Potential Corporate Privacy Violation
- MSBuild.exe (PID: 904)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 9108)
Application launched itself
- firefox.exe (PID: 2384)
- firefox.exe (PID: 2320)
Manual execution by a user
- WinRAR.exe (PID: 9108)
Checks supported languages
- MSBuild.exe (PID: 904)
- EtherHack.exe (PID: 5392)
Reads the software policy settings
- MSBuild.exe (PID: 904)
- slui.exe (PID: 8752)
Create files in a temporary directory
- MSBuild.exe (PID: 904)
Checks proxy server information
- slui.exe (PID: 8752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
171
Monitored processes
23
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 904 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | EtherHack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Local\Temp\9KMPMWFBGY56L2YXYH2J4ZL57ZF5VO.exe" | C:\Users\admin\AppData\Local\Temp\9KMPMWFBGY56L2YXYH2J4ZL57ZF5VO.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft® Windows® Integrity Level: MEDIUM Description: Programs Engine Exit code: 3221226540 Version: 10.0.19041.746 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://github.com/trahongquan/project-zomboid-cheat-menu/releases/download/Project-Zomboid-Cheat-menu/PZTool.zip | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://github.com/trahongquan/project-zomboid-cheat-menu/releases/download/Project-Zomboid-Cheat-menu/PZTool.zip" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
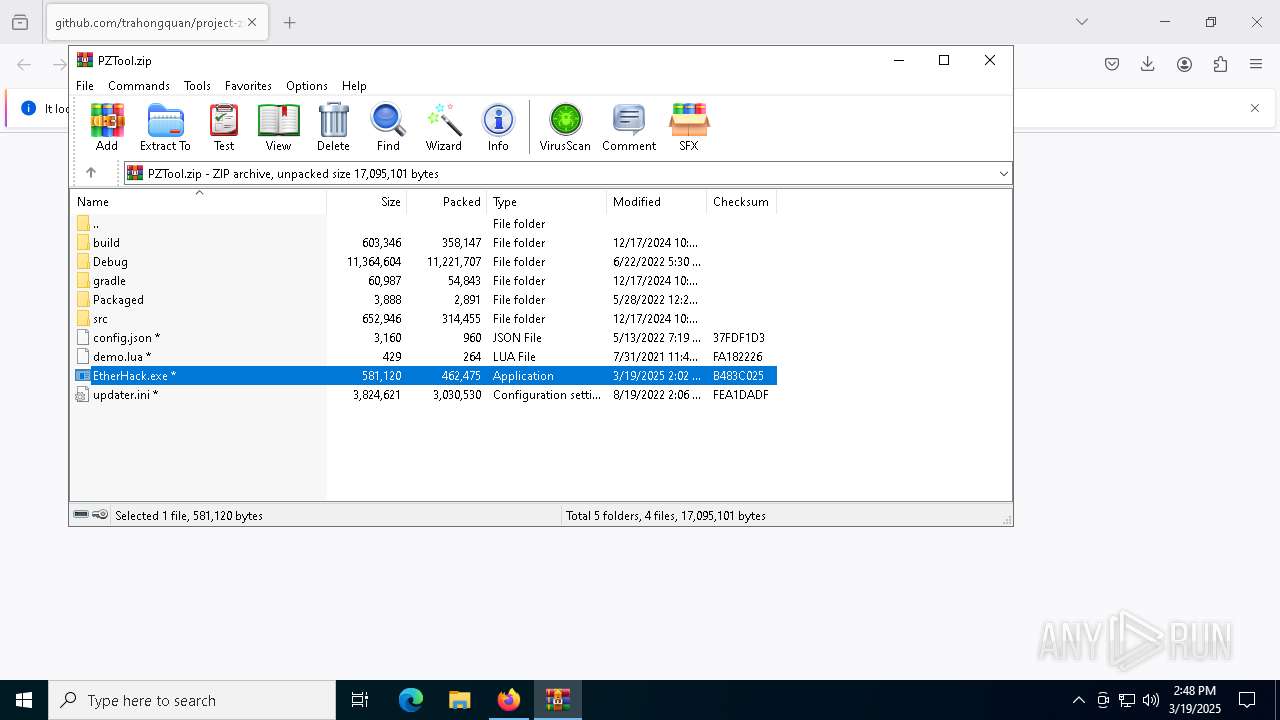
| 5392 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb9108.3400\EtherHack.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb9108.3400\EtherHack.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | EtherHack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7188 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5184 -childID 6 -isForBrowser -prefsHandle 5096 -prefMapHandle 5100 -prefsLen 38188 -prefMapSize 244583 -jsInitHandle 1316 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {48527869-1e75-480c-8e29-aa2c16eab6ef} 2320 "\\.\pipe\gecko-crash-server-pipe.2320" 1a2beb41850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 7196 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5108 -childID 5 -isForBrowser -prefsHandle 5116 -prefMapHandle 5028 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1316 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {13f8b424-d6e3-4b40-90d7-36b1d3079c01} 2320 "\\.\pipe\gecko-crash-server-pipe.2320" 1a2beb41690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
16 282
Read events
16 271
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2320) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\PZTool.zip | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (9108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
209
Text files
124
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:1B7DA940DB7CE55D8A97003792488186 | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 2320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2320 | firefox.exe | C:\Users\admin\Downloads\PZTool.NSDHxNPM.zip.part | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
95
DNS requests
120
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2320 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2320 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | — | 142.250.185.195:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | — | 142.250.185.195:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2320 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2320 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
2320 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
2320 | firefox.exe | 142.250.185.202:443 | safebrowsing.googleapis.com | — | — | whitelisted |
2320 | firefox.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2320 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2320 | firefox.exe | 185.199.110.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
904 | MSBuild.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
904 | MSBuild.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
904 | MSBuild.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
904 | MSBuild.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
904 | MSBuild.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |