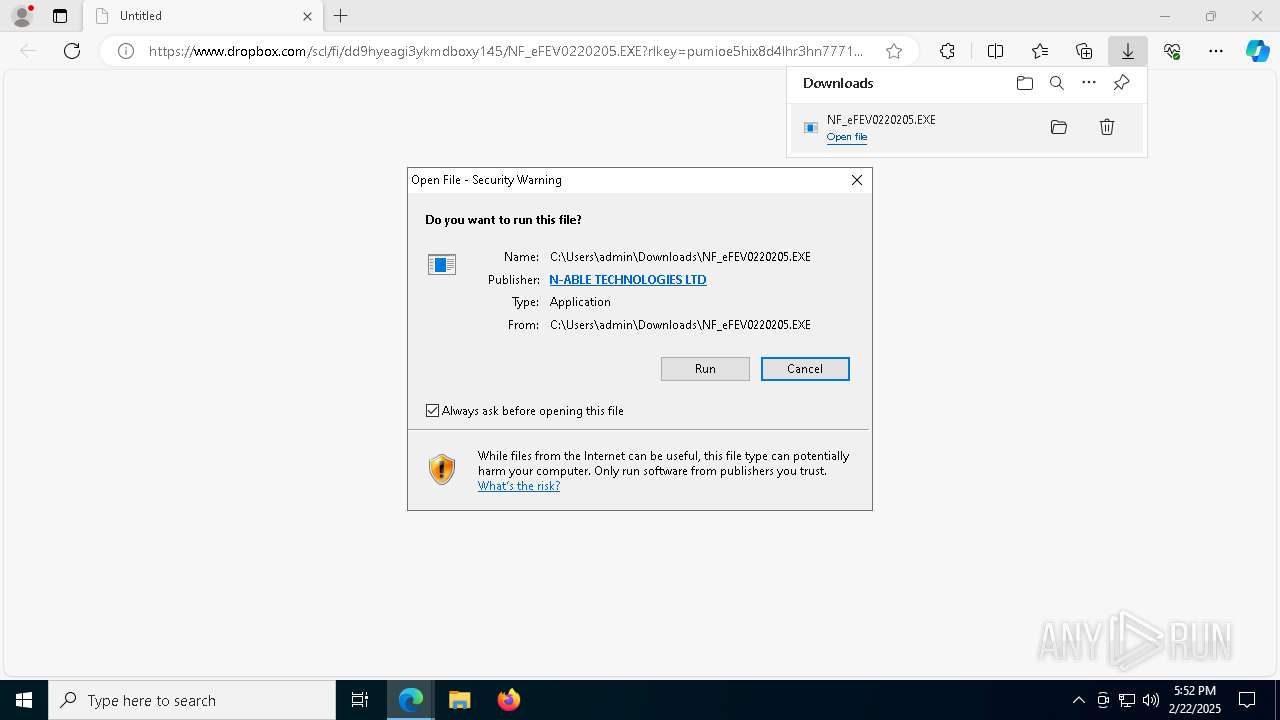
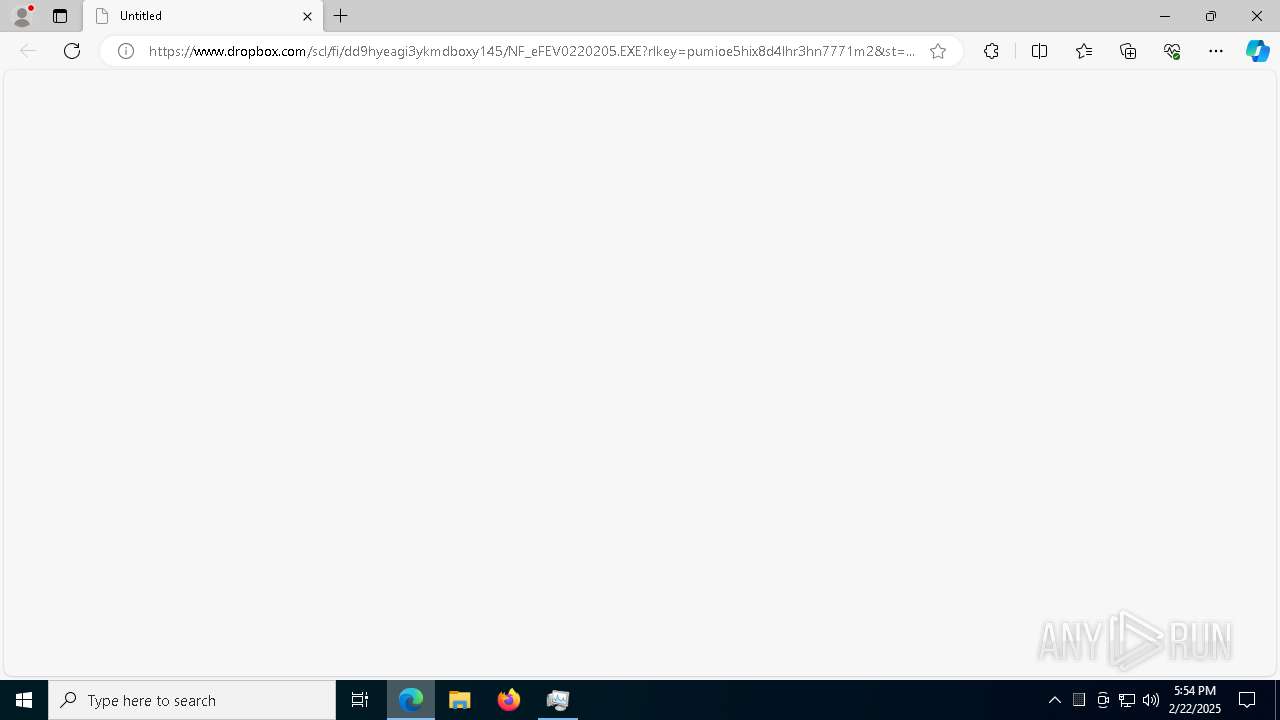
| URL: | https://www.dropbox.com/scl/fi/dd9hyeagi3ykmdboxy145/NF_eFEV0220205.EXE?rlkey=pumioe5hix8d4lhr3hn7771m2&st=m1tk3s4z&dl=1 |
| Full analysis: | https://app.any.run/tasks/bceade64-8e51-4c75-85a1-e8d47f2473e2 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2025, 17:51:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C0DDD80348BB932957C2F1503FD7A91A |
| SHA1: | 5F89FE61B937FE0B8D41871CA41BE6C0325203BF |
| SHA256: | BEE10B2444F8458C5B223D6B49AC6E8053096E63968FC7D06EA6BE66F33A0012 |
| SSDEEP: | 3:N8DSLcVHGkG6sxE1ARyGEeg9/JvcY6xbQeDTSbB:2OLHkM4AR9gplcY6xbpnu |
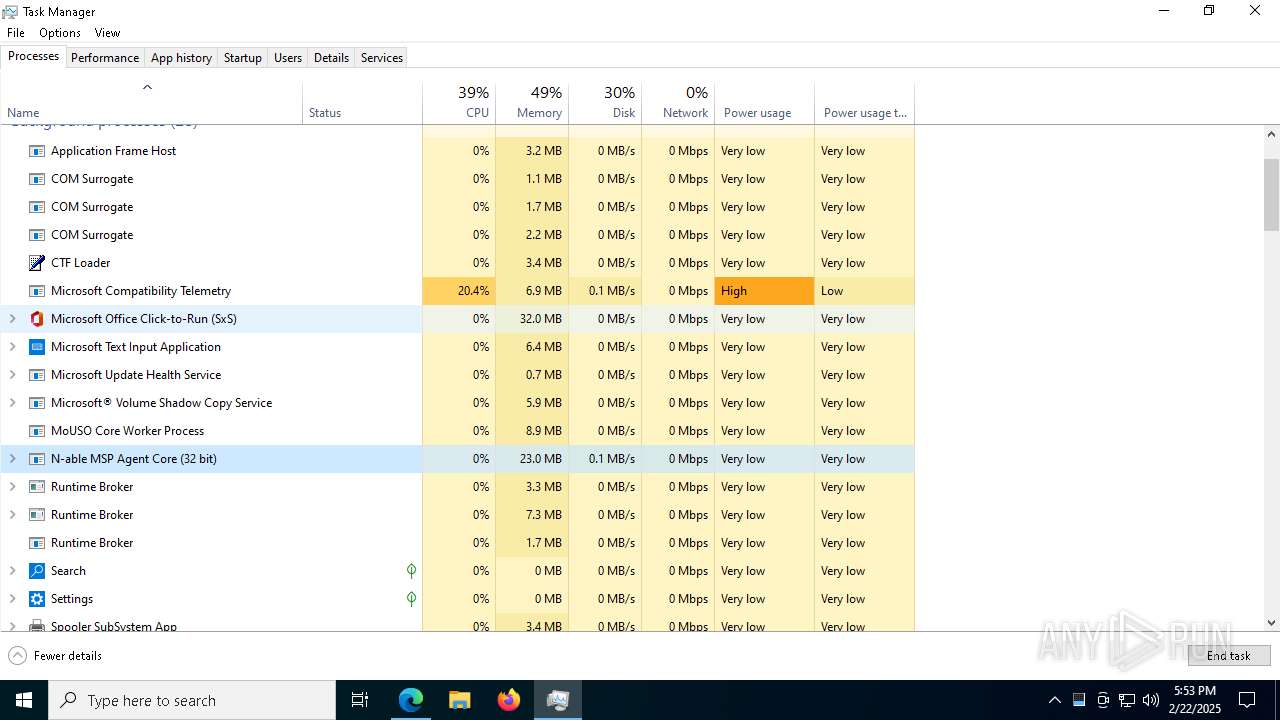
MALICIOUS
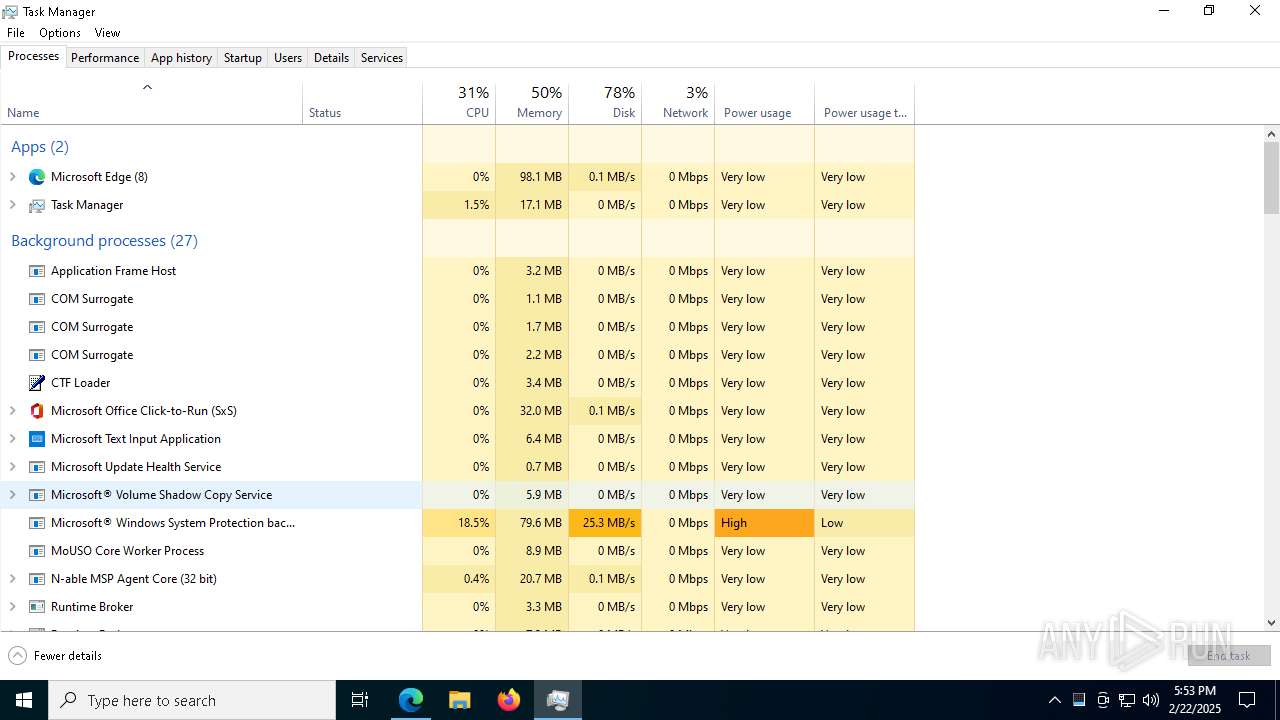
Changes the autorun value in the registry
- vcredist_x86.exe (PID: 7516)
- ScriptRunner.Installer.exe (PID: 6016)
- MSP_Connect.exe (PID: 4576)
Starts NET.EXE for service management
- agent.tmp (PID: 7224)
- net.exe (PID: 7076)
Changes the Windows auto-update feature
- PME.Agent.exe (PID: 5556)
SUSPICIOUS
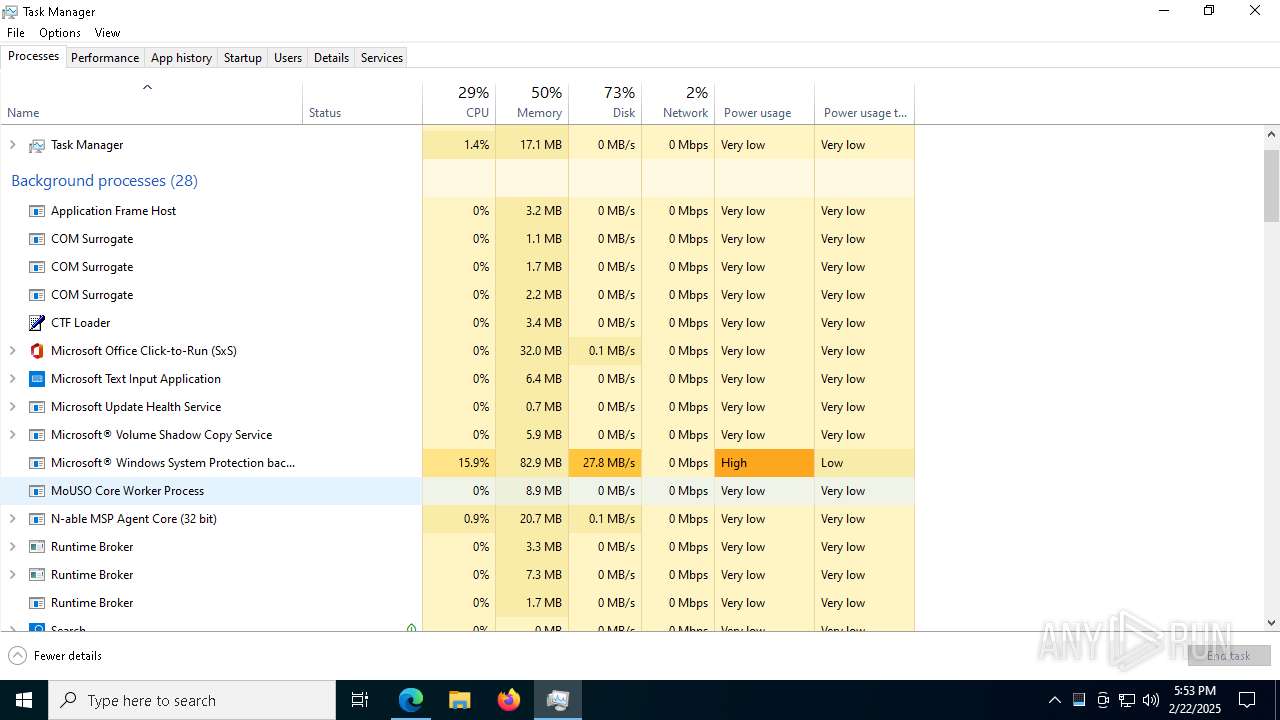
Executable content was dropped or overwritten
- agent.exe (PID: 5320)
- agent.exe (PID: 5028)
- NF_eFEV0220205.EXE (PID: 1616)
- agent.tmp (PID: 5548)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 8024)
- ScriptRunner.Installer.exe (PID: 6016)
- msp-agent-core.exe (PID: 7356)
- MSP_Connect.exe (PID: 4576)
- msp-agent-core-upgrade.exe (PID: 6624)
- winagent.exe (PID: 3812)
- NF_eFEV0220205.EXE (PID: 3544)
- agent.exe (PID: 880)
- agent.tmp (PID: 7224)
- BASupSrvc.exe (PID: 7004)
- PMESetup.exe (PID: 828)
- PMESetup.tmp (PID: 6824)
- RequestHandlerAgentSetup.exe (PID: 6664)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- FileCacheServiceAgentSetup.exe (PID: 6900)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- NetworkManagementInstall.exe (PID: 2012)
- NetworkManagementInstall.tmp (PID: 3912)
Reads security settings of Internet Explorer
- agent.tmp (PID: 4640)
- NF_eFEV0220205.EXE (PID: 1616)
- vcredist_x86.exe (PID: 7516)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- NF_eFEV0220205.EXE (PID: 3544)
- TCLauncherHelper.exe (PID: 6516)
- RequestHandlerAgent.exe (PID: 6644)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- NetworkManagement.exe (PID: 6672)
Reads the Windows owner or organization settings
- agent.tmp (PID: 5548)
- msiexec.exe (PID: 4328)
- agent.tmp (PID: 7224)
- PMESetup.tmp (PID: 6824)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- NetworkManagementInstall.tmp (PID: 3912)
Process drops legitimate windows executable
- agent.tmp (PID: 5548)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- MSP_Connect.exe (PID: 4576)
- agent.tmp (PID: 7224)
- PMESetup.tmp (PID: 6824)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- NetworkManagementInstall.tmp (PID: 3912)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
Creates/Modifies COM task schedule object
- winagent.exe (PID: 7688)
- MSP_Connect.exe (PID: 4576)
Searches for installed software
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- dllhost.exe (PID: 4592)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
- msp-agent-core.exe (PID: 3488)
- NetworkManagementInstall.tmp (PID: 3912)
The process checks if it is being run in the virtual environment
- winagent.exe (PID: 7688)
- winagent.exe (PID: 3812)
Application launched itself
- vcredist_x86.exe (PID: 7516)
- BASupSrvcCnfg.exe (PID: 6424)
- TCLauncherHelper.exe (PID: 6516)
Executes as Windows Service
- VSSVC.exe (PID: 4668)
- winagent.exe (PID: 3812)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 3488)
- BASupSrvc.exe (PID: 7004)
- BASupSrvcUpdater.exe (PID: 3664)
- RequestHandlerAgent.exe (PID: 6404)
- FileCacheServiceAgent.exe (PID: 1864)
- PME.Agent.exe (PID: 5556)
- NetworkManagement.exe (PID: 6968)
Creates a software uninstall entry
- vcredist_x86.exe (PID: 7516)
- ScriptRunner.Installer.exe (PID: 6016)
- msp-agent-core.exe (PID: 3488)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- PMESetup.tmp (PID: 6824)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- NetworkManagementInstall.tmp (PID: 3912)
Checks Windows Trust Settings
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- BASupSrvc.exe (PID: 7004)
- BASupSrvcUpdater.exe (PID: 3664)
- RequestHandlerAgent.exe (PID: 6644)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- winagent.exe (PID: 3812)
- NetworkManagement.exe (PID: 6672)
The process drops C-runtime libraries
- msiexec.exe (PID: 4328)
- MSP_Connect.exe (PID: 4576)
The process creates files with name similar to system file names
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- MSP_Connect.exe (PID: 4576)
Starts itself from another location
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7276)
Executes application which crashes
- winagent.exe (PID: 7688)
Starts CMD.EXE for commands execution
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 6812)
- msp-agent-core.exe (PID: 7328)
- msp-agent-core.exe (PID: 3488)
Creates or modifies Windows services
- BASupSrvc.exe (PID: 7788)
- RequestHandlerAgent.exe (PID: 6644)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- NetworkManagement.exe (PID: 6672)
The process executes via Task Scheduler
- TCLauncherHelper.exe (PID: 6516)
Windows service management via SC.EXE
- sc.exe (PID: 7776)
- sc.exe (PID: 5252)
- sc.exe (PID: 7468)
- sc.exe (PID: 4580)
- sc.exe (PID: 7436)
- sc.exe (PID: 4160)
- sc.exe (PID: 8068)
- sc.exe (PID: 2844)
- sc.exe (PID: 7276)
- sc.exe (PID: 7040)
- sc.exe (PID: 1348)
- sc.exe (PID: 1328)
Uses ICACLS.EXE to modify access control lists
- RequestHandlerAgentSetup.tmp (PID: 7408)
- PMESetup.tmp (PID: 6824)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
Restarts service on failure
- sc.exe (PID: 7280)
- sc.exe (PID: 7600)
- sc.exe (PID: 5448)
- sc.exe (PID: 6452)
Starts SC.EXE for service management
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- NetworkManagement.exe (PID: 6672)
Adds/modifies Windows certificates
- winagent.exe (PID: 3812)
INFO
Application launched itself
- msedge.exe (PID: 6412)
- msedge.exe (PID: 7272)
Reads the computer name
- identity_helper.exe (PID: 7468)
- agent.tmp (PID: 4640)
- agent.tmp (PID: 5548)
- NF_eFEV0220205.EXE (PID: 1616)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- msiexec.exe (PID: 7276)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 6812)
- msp-agent-core-upgrade.exe (PID: 6624)
- MSP_Connect.exe (PID: 4576)
- msp-agent-core.exe (PID: 3488)
- identity_helper.exe (PID: 7936)
- BASupSrvc.exe (PID: 7788)
- TCLauncherHelper.exe (PID: 7972)
- BASupSrvcCnfg.exe (PID: 6424)
- agent.tmp (PID: 7224)
- NF_eFEV0220205.EXE (PID: 3544)
- BASupSrvc.exe (PID: 7004)
- TCLauncherHelper.exe (PID: 6544)
- TCLauncherHelper.exe (PID: 6516)
- msp-agent-core.exe (PID: 6724)
- BASupSysInf.exe (PID: 7684)
- BASupSrvcUpdater.exe (PID: 3664)
- BASupSrvcCnfg.exe (PID: 6396)
- TCLauncherHelper.exe (PID: 1856)
- PMESetup.exe (PID: 828)
- PMESetup.tmp (PID: 6824)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- RequestHandlerAgent.exe (PID: 6644)
- RequestHandlerAgentSetup.exe (PID: 6664)
- FileCacheServiceAgentSetup.exe (PID: 6900)
- RequestHandlerAgent.exe (PID: 6404)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- FileCacheServiceAgent.exe (PID: 1864)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 5556)
- PME.Agent.exe (PID: 6752)
- NetworkManagementInstall.tmp (PID: 3912)
- NetworkManagement.exe (PID: 6672)
- NetworkManagement.exe (PID: 6664)
- NetworkManagement.exe (PID: 6968)
Reads Environment values
- identity_helper.exe (PID: 7468)
- winagent.exe (PID: 7688)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
- identity_helper.exe (PID: 7936)
- FileCacheServiceAgent.exe (PID: 1864)
- FileCacheServiceAgent.exe (PID: 6572)
Checks supported languages
- NF_eFEV0220205.EXE (PID: 1616)
- identity_helper.exe (PID: 7468)
- agent.exe (PID: 5320)
- agent.tmp (PID: 4640)
- agent.tmp (PID: 5548)
- agent.exe (PID: 5028)
- unzip.exe (PID: 5488)
- unzip.exe (PID: 7428)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7516)
- vcredist_x86.exe (PID: 7512)
- msiexec.exe (PID: 4328)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 8024)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- msiexec.exe (PID: 7276)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 7328)
- msp-agent-core.exe (PID: 6812)
- msp-agent-core-upgrade.exe (PID: 6624)
- msp-agent-core-upgrade.exe (PID: 4384)
- MSP_Connect.exe (PID: 4576)
- msp-agent-core-upgrade.exe (PID: 3888)
- msp-agent-core.exe (PID: 3488)
- identity_helper.exe (PID: 7936)
- TCLauncherHelper.exe (PID: 7972)
- BASupSrvc.exe (PID: 7788)
- NF_eFEV0220205.EXE (PID: 3544)
- agent.exe (PID: 880)
- BASupSrvcCnfg.exe (PID: 6424)
- BASupSrvc.exe (PID: 7004)
- agent.tmp (PID: 7224)
- TCLauncherHelper.exe (PID: 6544)
- TCLauncherHelper.exe (PID: 6516)
- msp-agent-core.exe (PID: 3172)
- msp-agent-core.exe (PID: 7012)
- msp-agent-core.exe (PID: 6724)
- BASupSysInf.exe (PID: 7684)
- BASupSrvcUpdater.exe (PID: 3664)
- BASupSrvcCnfg.exe (PID: 6396)
- TCLauncherHelper.exe (PID: 1856)
- PMESetup.exe (PID: 828)
- PMESetup.tmp (PID: 6824)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- RequestHandlerAgent.exe (PID: 6644)
- RequestHandlerAgentSetup.exe (PID: 6664)
- RequestHandlerAgent.exe (PID: 6404)
- FileCacheServiceAgentSetup.exe (PID: 6900)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- FileCacheServiceAgent.exe (PID: 1864)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- PME.Agent.exe (PID: 5556)
- NetworkManagementInstall.exe (PID: 2012)
- NetworkManagement.exe (PID: 6672)
- NetworkManagementInstall.tmp (PID: 3912)
- NetworkManagement.exe (PID: 6664)
- NetworkManagement.exe (PID: 6968)
Executable content was dropped or overwritten
- msedge.exe (PID: 6412)
- msedge.exe (PID: 6708)
- msiexec.exe (PID: 4328)
Process checks computer location settings
- NF_eFEV0220205.EXE (PID: 1616)
- agent.tmp (PID: 4640)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- NF_eFEV0220205.EXE (PID: 3544)
- TCLauncherHelper.exe (PID: 6516)
Create files in a temporary directory
- agent.exe (PID: 5320)
- NF_eFEV0220205.EXE (PID: 1616)
- agent.exe (PID: 5028)
- agent.tmp (PID: 5548)
- vcredist_x86.exe (PID: 7512)
- NF_eFEV0220205.EXE (PID: 3544)
- agent.exe (PID: 880)
- agent.tmp (PID: 7224)
Creates files in the program directory
- unzip.exe (PID: 5488)
- agent.tmp (PID: 5548)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
- msp-agent-core.exe (PID: 7636)
- msiexec.exe (PID: 7832)
- msp-agent-core-upgrade.exe (PID: 6624)
- msp-agent-core.exe (PID: 7356)
- MSP_Connect.exe (PID: 4576)
- msp-agent-core.exe (PID: 3488)
- BASupSrvc.exe (PID: 7788)
- BASupSrvcCnfg.exe (PID: 6424)
- TCLauncherHelper.exe (PID: 7972)
- BASupSrvc.exe (PID: 7004)
- TCLauncherHelper.exe (PID: 6516)
- BASupSysInf.exe (PID: 7684)
- BASupSrvcUpdater.exe (PID: 3664)
- PMESetup.tmp (PID: 6824)
- BASupSrvcCnfg.exe (PID: 6396)
- RequestHandlerAgentSetup.tmp (PID: 7408)
- RequestHandlerAgent.exe (PID: 6644)
- FileCacheServiceAgentSetup.tmp (PID: 6536)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- NetworkManagementInstall.tmp (PID: 3912)
- FileCacheServiceAgent.exe (PID: 1864)
- NetworkManagement.exe (PID: 6672)
The sample compiled with english language support
- agent.tmp (PID: 5548)
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7512)
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 8024)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core-upgrade.exe (PID: 6624)
- MSP_Connect.exe (PID: 4576)
- agent.tmp (PID: 7224)
- winagent.exe (PID: 3812)
- PMESetup.tmp (PID: 6824)
- NetworkManagementInstall.tmp (PID: 3912)
Creates a software uninstall entry
- agent.tmp (PID: 5548)
- msiexec.exe (PID: 4328)
Reads the software policy settings
- winagent.exe (PID: 7688)
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- winagent.exe (PID: 3812)
- WerFault.exe (PID: 4908)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 3488)
- BASupSrvc.exe (PID: 7004)
- msp-agent-core.exe (PID: 6724)
- BASupSrvcUpdater.exe (PID: 3664)
- RequestHandlerAgent.exe (PID: 6644)
- FileCacheServiceAgent.exe (PID: 6572)
- PME.Agent.exe (PID: 6752)
- NetworkManagementInstall.tmp (PID: 3912)
- FileCacheServiceAgent.exe (PID: 1864)
- NetworkManagement.exe (PID: 6672)
Reads product name
- winagent.exe (PID: 7688)
- winagent.exe (PID: 3812)
- assetscan.exe (PID: 2124)
Manages system restore points
- SrTasks.exe (PID: 2136)
Checks proxy server information
- vcredist_x86.exe (PID: 7516)
- WerFault.exe (PID: 4908)
Creates files or folders in the user directory
- vcredist_x86.exe (PID: 7516)
- WerFault.exe (PID: 4908)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 7516)
- msiexec.exe (PID: 4328)
- ScriptRunnerInstaller-2.97.0.1.exe (PID: 7560)
- ScriptRunner.Installer.exe (PID: 6016)
- winagent.exe (PID: 3812)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 3488)
- BASupSrvc.exe (PID: 7788)
- TCLauncherHelper.exe (PID: 7972)
- BASupSrvcCnfg.exe (PID: 6424)
- BASupSrvc.exe (PID: 7004)
- TCLauncherHelper.exe (PID: 6516)
- msp-agent-core.exe (PID: 6724)
- TCLauncherHelper.exe (PID: 6544)
- TCLauncherHelper.exe (PID: 1856)
- BASupSrvcCnfg.exe (PID: 6396)
- BASupSrvcUpdater.exe (PID: 3664)
- RequestHandlerAgent.exe (PID: 6644)
- RequestHandlerAgent.exe (PID: 6404)
- FileCacheServiceAgent.exe (PID: 6572)
- FileCacheServiceAgent.exe (PID: 1864)
- PME.Agent.exe (PID: 6752)
- PME.Agent.exe (PID: 5556)
- NetworkManagement.exe (PID: 6664)
- NetworkManagement.exe (PID: 6672)
- NetworkManagement.exe (PID: 6968)
The sample compiled with russian language support
- msiexec.exe (PID: 4328)
The sample compiled with french language support
- msiexec.exe (PID: 4328)
The sample compiled with chinese language support
- msiexec.exe (PID: 4328)
The sample compiled with german language support
- msiexec.exe (PID: 4328)
The sample compiled with spanish language support
- msiexec.exe (PID: 4328)
The sample compiled with japanese language support
- msiexec.exe (PID: 4328)
The sample compiled with Italian language support
- msiexec.exe (PID: 4328)
The sample compiled with korean language support
- msiexec.exe (PID: 4328)
Manual execution by a user
- Taskmgr.exe (PID: 7816)
- Taskmgr.exe (PID: 4400)
- NF_eFEV0220205.EXE (PID: 3544)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 4400)
Drops encrypted JS script (Microsoft Script Encoder)
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 7328)
- msp-agent-core.exe (PID: 6812)
- msp-agent-core.exe (PID: 3488)
Checks operating system version
- msp-agent-core.exe (PID: 7636)
- msp-agent-core.exe (PID: 7356)
- msp-agent-core.exe (PID: 6812)
- msp-agent-core.exe (PID: 7328)
- msp-agent-core.exe (PID: 3488)
Reads Windows Product ID
- assetscan.exe (PID: 2124)
Process checks whether UAC notifications are on
- BASupSrvcCnfg.exe (PID: 6424)
- TCLauncherHelper.exe (PID: 7972)
- TCLauncherHelper.exe (PID: 6544)
- TCLauncherHelper.exe (PID: 6516)
- TCLauncherHelper.exe (PID: 1856)
- BASupSrvcCnfg.exe (PID: 6396)
Disables trace logs
- FileCacheServiceAgent.exe (PID: 1864)
SQLite executable
- NetworkManagementInstall.tmp (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
343
Monitored processes
199
Malicious processes
24
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=4996 --field-trial-handle=2160,i,15938716448177219535,1998806794404799446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2444 --field-trial-handle=2268,i,7764087211973101435,11913408524135847124,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 828 | "C:\PROGRA~2\ADVANC~1\featureres\PMESetup.exe" /SP- /VERYSILENT /SUPPRESSMSGBOXES /NORESTART /CLOSEAPPLICATIONS /DIR="C:\PROGRA~2\ADVANC~1\patchman" /LOG="C:\PROGRA~2\ADVANC~1\feature_2_install.log" | C:\Program Files (x86)\Advanced Monitoring Agent\featureres\PMESetup.exe | winagent.exe | ||||||||||||
User: SYSTEM Company: N-able Integrity Level: SYSTEM Description: Patch Management Service Controller Setup Exit code: 0 Version: 2.13.0.5511 Modules
| |||||||||||||||
| 880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | unzip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\agent.exe" /VERYSILENT /norestart | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\agent.exe | NF_eFEV0220205.EXE | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Advanced Monitoring Agent Setup Version: Modules
| |||||||||||||||
| 1192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BASupSysInf.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5444 --field-trial-handle=2268,i,7764087211973101435,11913408524135847124,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\WINDOWS\system32\sc.exe" qdescription SolarWinds.MSP.RpcServerService | C:\Windows\SysWOW64\sc.exe | — | PMESetup.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\WINDOWS\system32\sc.exe" start SolarWinds.MSP.RpcServerService | C:\Windows\SysWOW64\sc.exe | — | PMESetup.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | msp-agent-core-upgrade.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
132 271
Read events
130 114
Write events
1 965
Delete events
192
Modification events
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (6228) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: FC0C510C558D2F00 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328206 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {88208AB3-9711-4FBF-8B48-B963C18601F8} | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
Executable files
626
Suspicious files
626
Text files
300
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF134d68.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF134d87.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF134d68.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF134d58.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF13542e.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
143
DNS requests
88
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6832 | svchost.exe | GET | 206 | 2.22.242.146:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1740402690&P2=404&P3=2&P4=Br4VumX%2f1GuTR47OCZi5aJzKN38iGUDK3dJ0ksWfffEl9pjFgOh8TRL3pxL%2bziIU3HK9LMn24q6yzNPJt3aNAw%3d%3d | unknown | — | — | whitelisted |
6832 | svchost.exe | GET | 206 | 2.22.242.146:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1740402690&P2=404&P3=2&P4=Br4VumX%2f1GuTR47OCZi5aJzKN38iGUDK3dJ0ksWfffEl9pjFgOh8TRL3pxL%2bziIU3HK9LMn24q6yzNPJt3aNAw%3d%3d | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6412 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6412 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6412 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAa7Qj4Jnq0A09Vb8dNyx3M%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3508 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2736 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2736 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6708 | msedge.exe | 162.125.66.18:443 | www.dropbox.com | DROPBOX | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2192 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2192 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2192 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
Process | Message |
|---|---|
NetworkManagement.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Advanced Monitoring Agent Network Management\x64\SQLite.Interop.dll"...
|