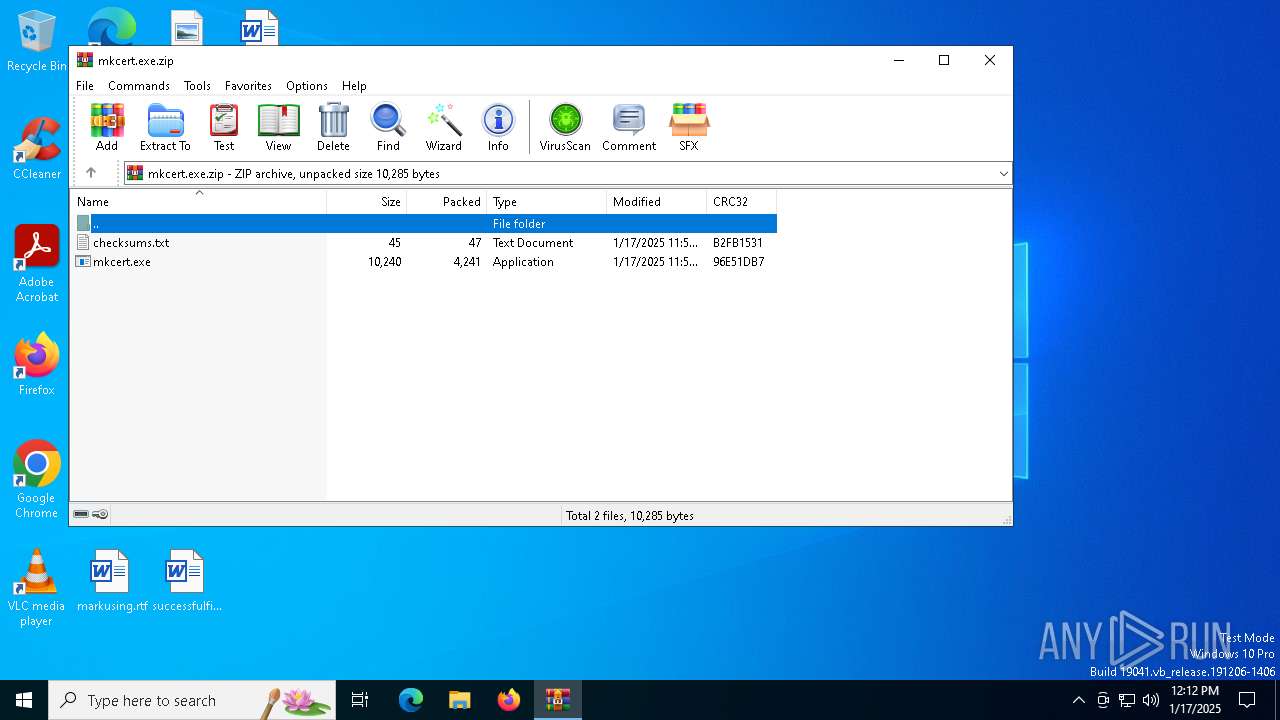
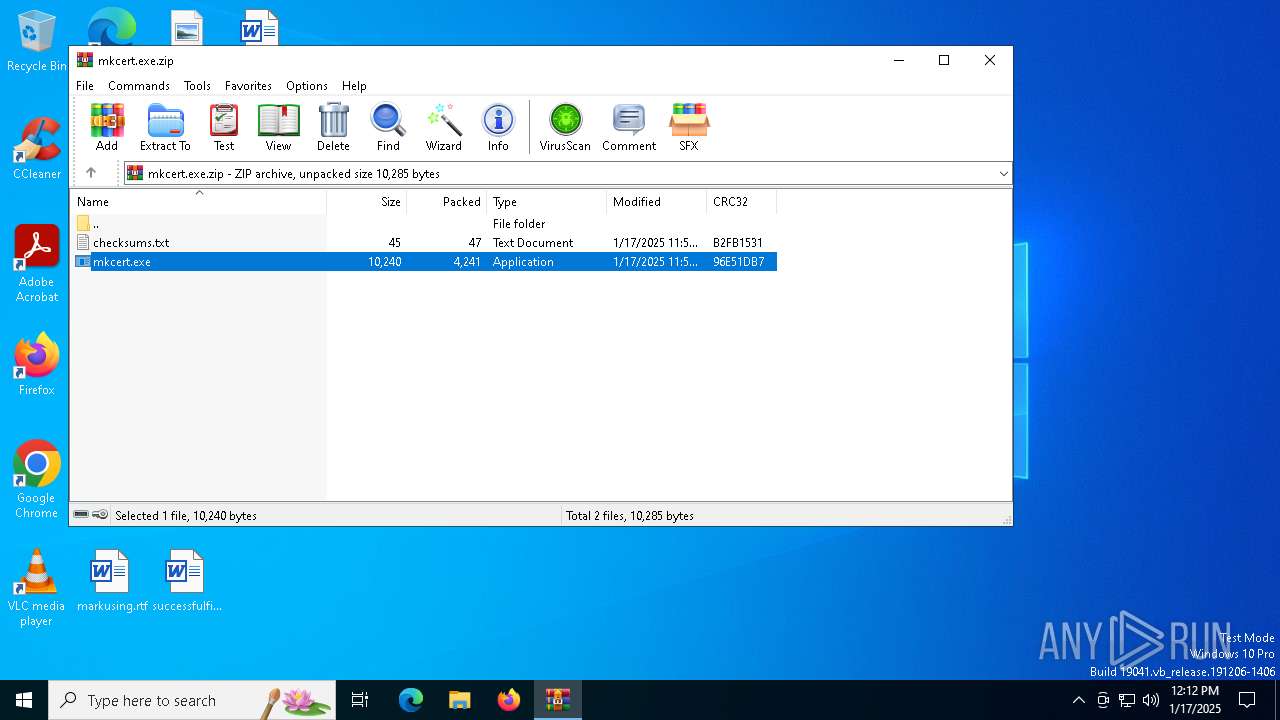
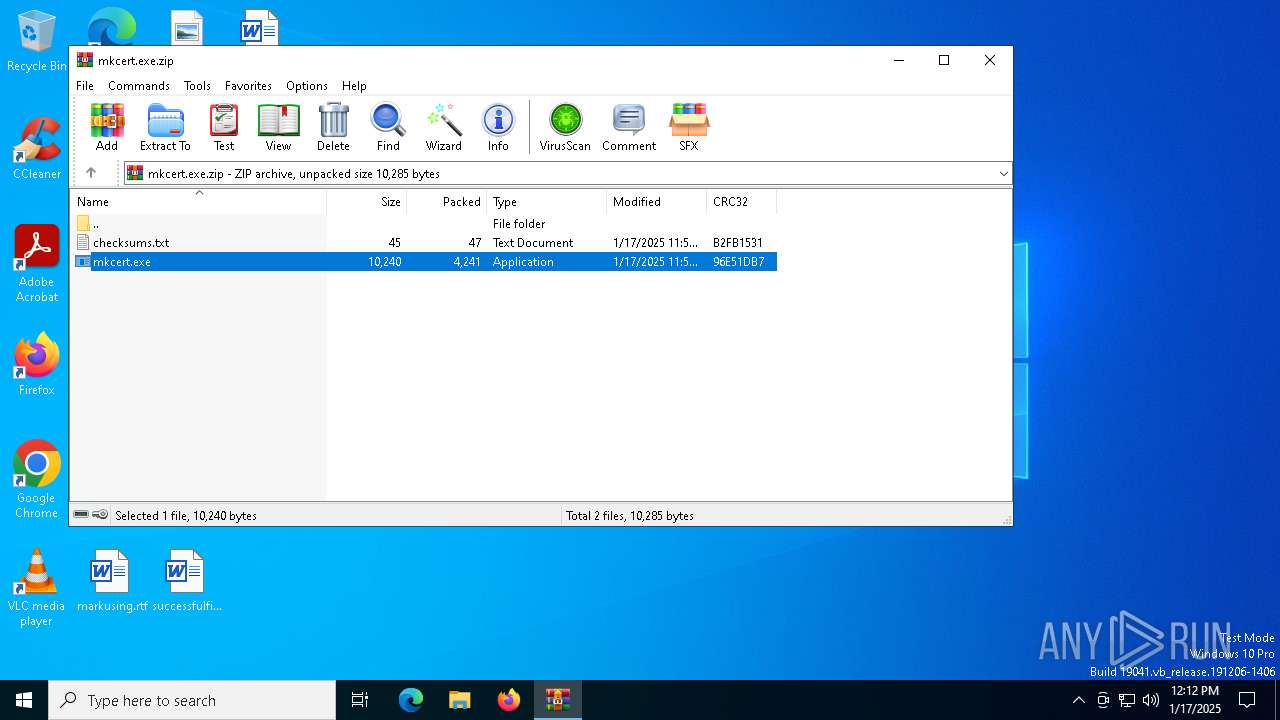
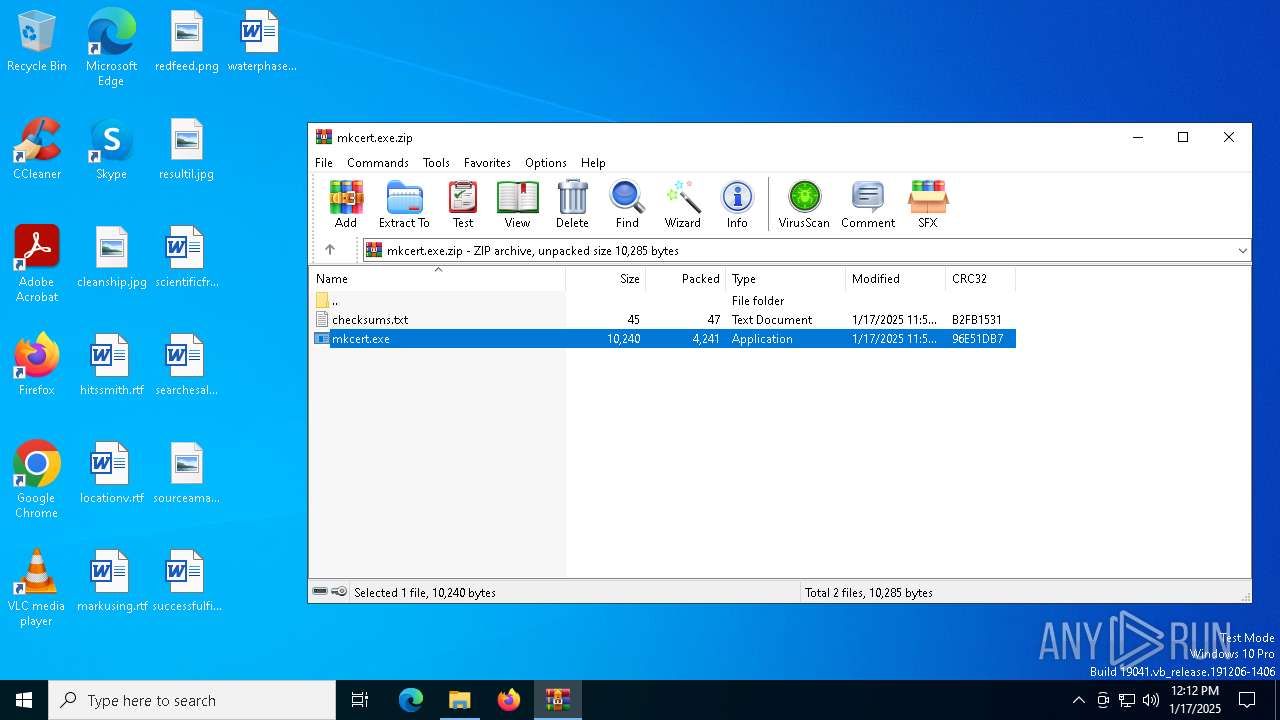
| File name: | mkcert.exe.zip |
| Full analysis: | https://app.any.run/tasks/e4e61c23-c041-4375-a5d5-85dd8c1eb8bf |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 12:12:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
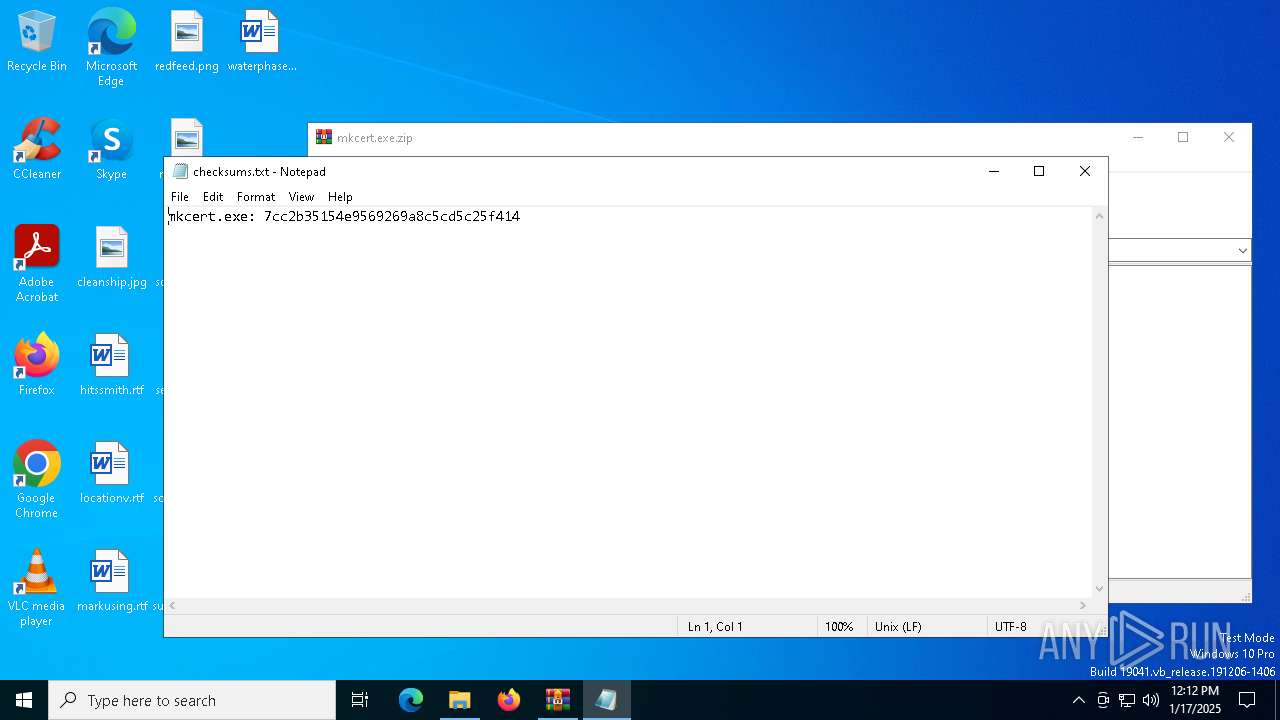
| MD5: | D52FCCC127AA3F5EC91E89E871BBC584 |
| SHA1: | D6A252049CBCB88377D105C673A35A7FB5C6E4C1 |
| SHA256: | BED99A4D9DD4F0E1858E0B2394990020D09FDBCD4DC5AD3A6A2A1F5AD85D9AA4 |
| SSDEEP: | 96:b79PcsHwUkN7Fo2BqHv/8tPbEX+5uPb8HnrcFyBSgWHHhil:H5PwhFo/2TXmNFyBSHBg |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6396)
SUSPICIOUS
Reads security settings of Internet Explorer
- mkcert.exe (PID: 6572)
- mkcert.exe (PID: 5964)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6396)
Checks Windows Trust Settings
- mkcert.exe (PID: 6572)
- mkcert.exe (PID: 5964)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6396)
Reads the machine GUID from the registry
- mkcert.exe (PID: 6572)
- mkcert.exe (PID: 5964)
Reads the computer name
- mkcert.exe (PID: 6572)
Checks supported languages
- mkcert.exe (PID: 6572)
- mkcert.exe (PID: 5964)
Reads the software policy settings
- mkcert.exe (PID: 6572)
- mkcert.exe (PID: 5964)
Create files in a temporary directory
- mkcert.exe (PID: 6572)
The process uses the downloaded file
- WinRAR.exe (PID: 6396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
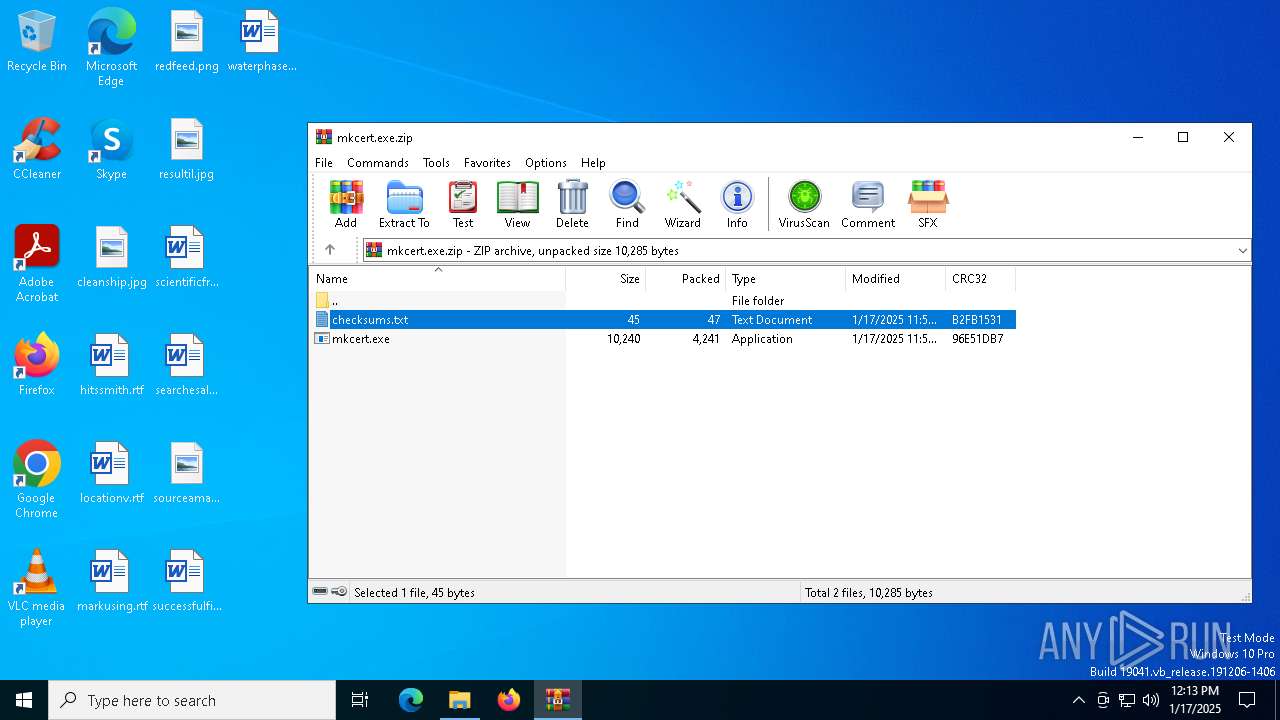
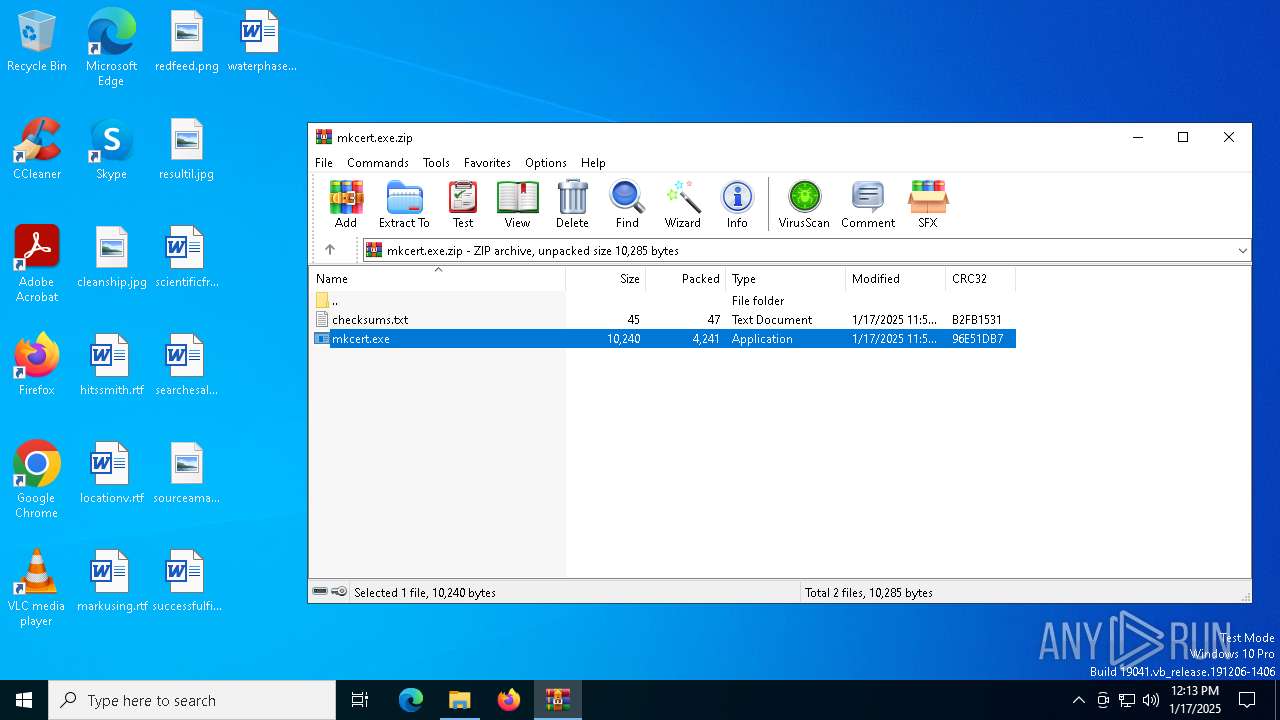
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:17 11:56:34 |
| ZipCRC: | 0x96e51db7 |
| ZipCompressedSize: | 4241 |
| ZipUncompressedSize: | 10240 |
| ZipFileName: | mkcert.exe |
Total processes
133
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mkcert.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3260 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa6396.28266\checksums.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
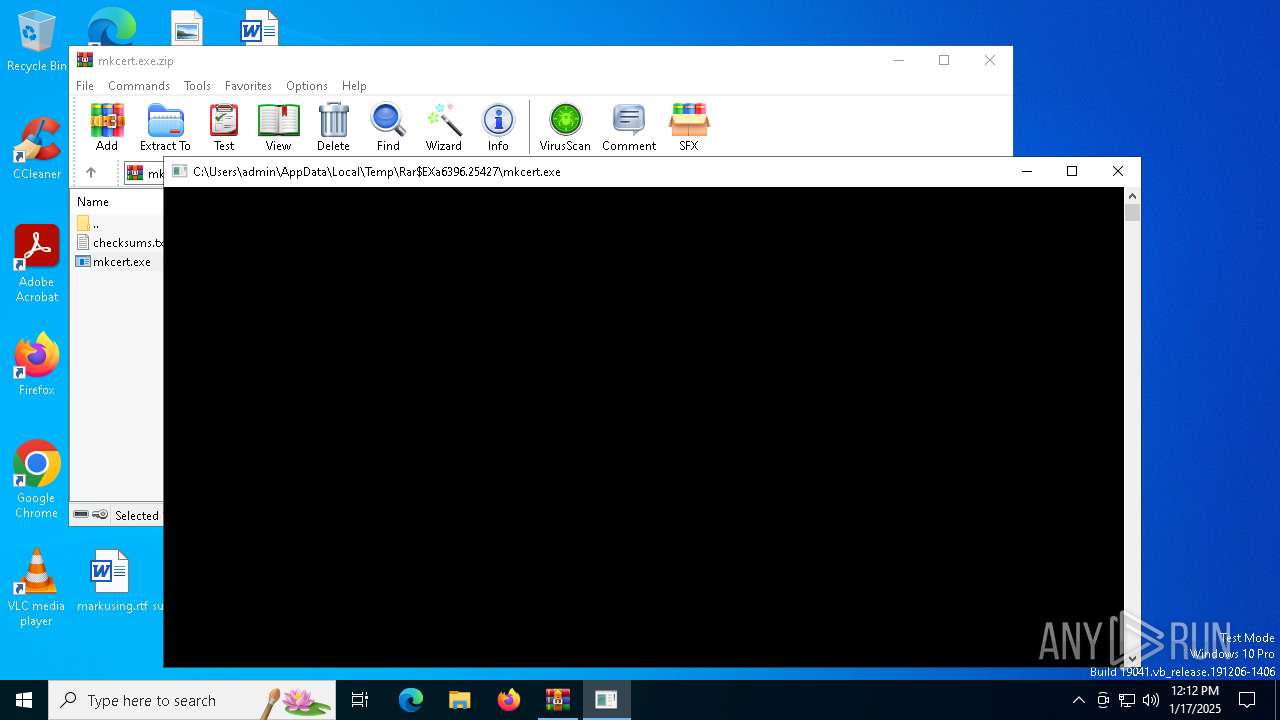
| 5964 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.32609\mkcert.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.32609\mkcert.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: mkcert Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6396 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\mkcert.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6572 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.25427\mkcert.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.25427\mkcert.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: mkcert Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mkcert.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 924
Read events
14 915
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\mkcert.exe.zip | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
Executable files
2
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.25427\checksums.txt | text | |
MD5:66D9F2A24AD6C480671FB83CAA703ED7 | SHA256:AB745DFCB817984791BE1732A5BE8B5C5CA187C45C30293AE4319D9DF18E67B4 | |||
| 6572 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jcupanna.12a.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6396.28266\checksums.txt | text | |
MD5:66D9F2A24AD6C480671FB83CAA703ED7 | SHA256:AB745DFCB817984791BE1732A5BE8B5C5CA187C45C30293AE4319D9DF18E67B4 | |||
| 6572 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3ubsuhbb.vsj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.32609\checksums.txt | text | |
MD5:66D9F2A24AD6C480671FB83CAA703ED7 | SHA256:AB745DFCB817984791BE1732A5BE8B5C5CA187C45C30293AE4319D9DF18E67B4 | |||
| 6572 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ultt345u.ehx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6572 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kwrrbzln.wd4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6396.25427\mkcert.exe | executable | |
MD5:7CC2B35154E9569269A8C5CD5C25F414 | SHA256:3ED7944368BB86402333FC360415C763B7924179601DB092CCA8009B45CFE0B7 | |||
| 5964 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ikbj1ccf.cqu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5964 | mkcert.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t24sxjwu.l1f.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7096 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | unknown |
372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
crl.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
ocsp.digicert.com |
| unknown |
login.live.com |
| unknown |
go.microsoft.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| unknown |