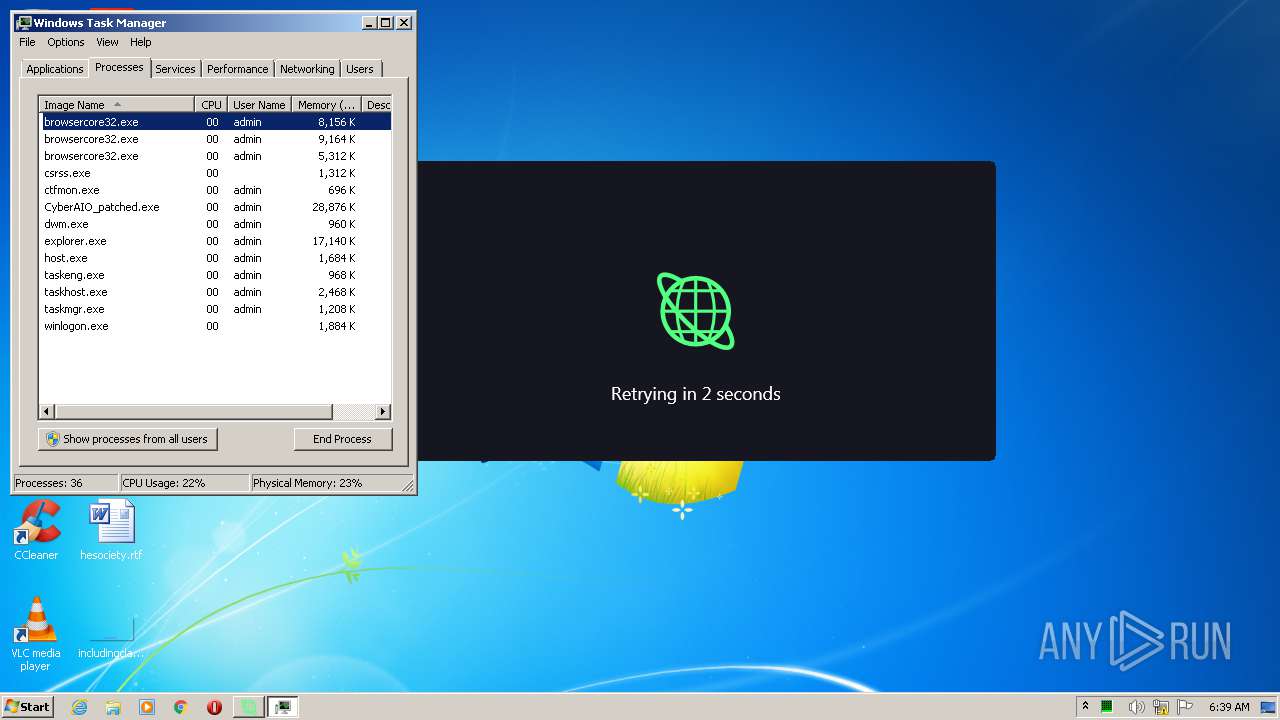
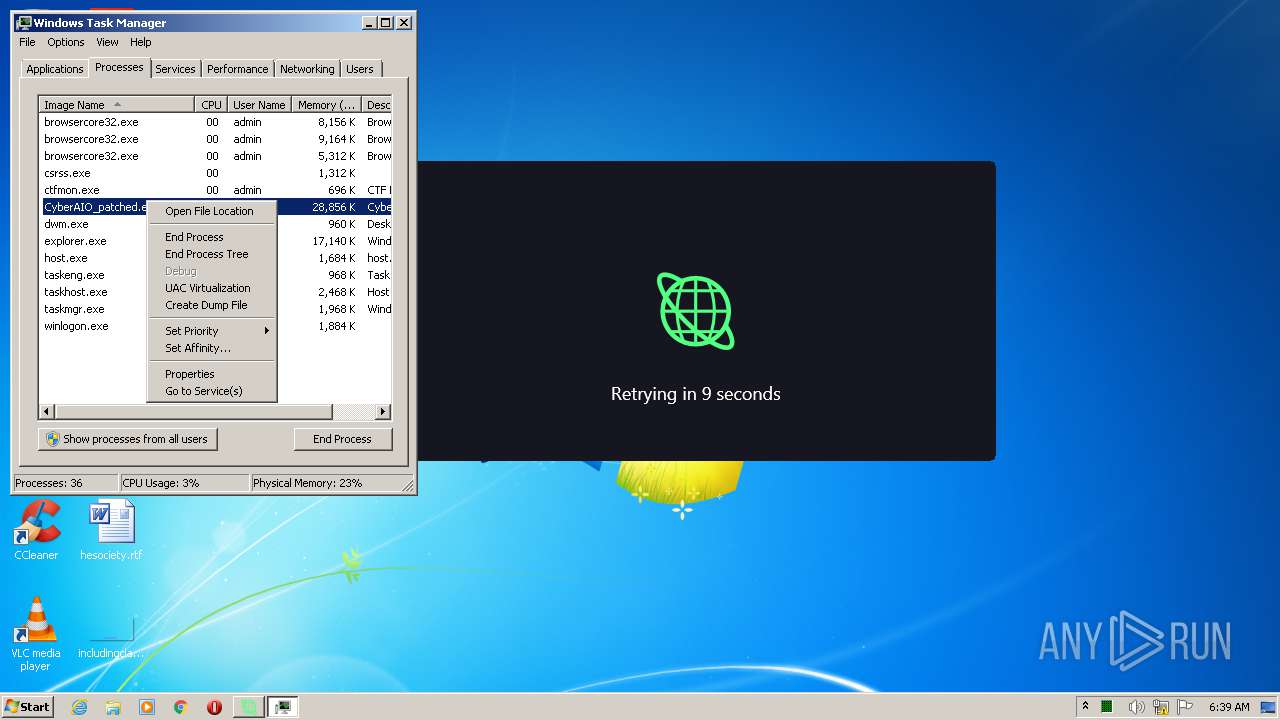
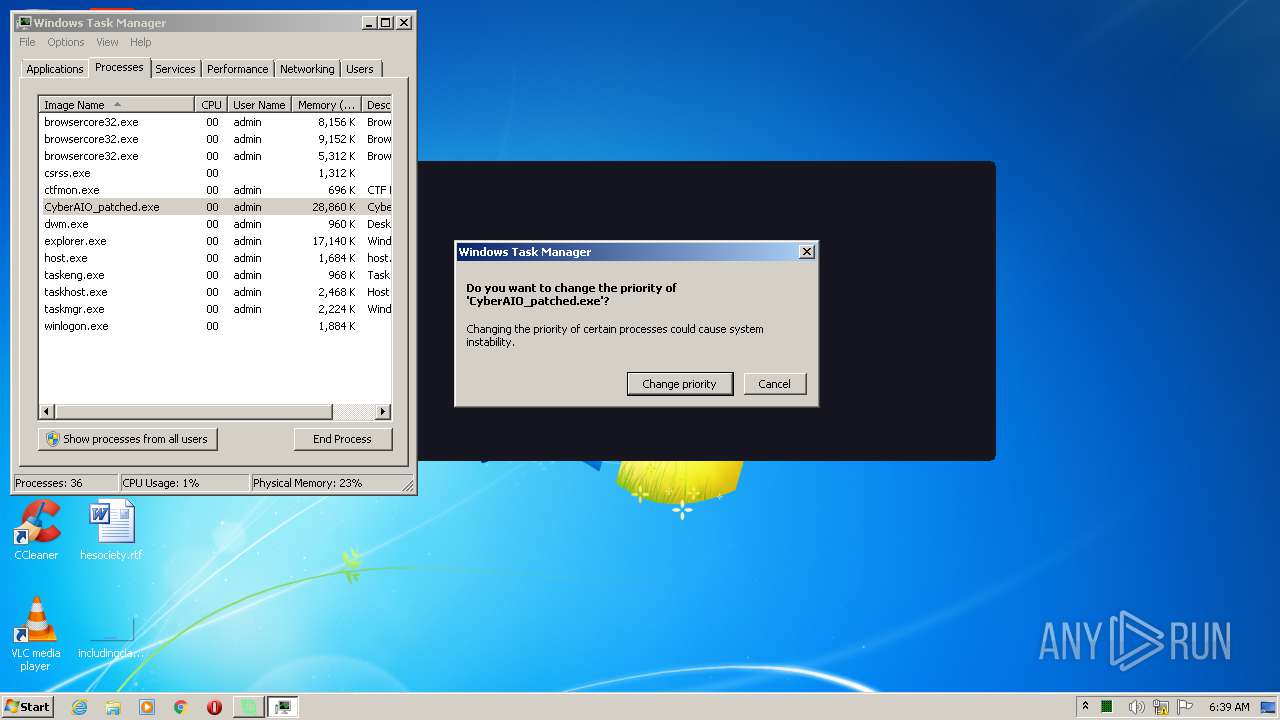
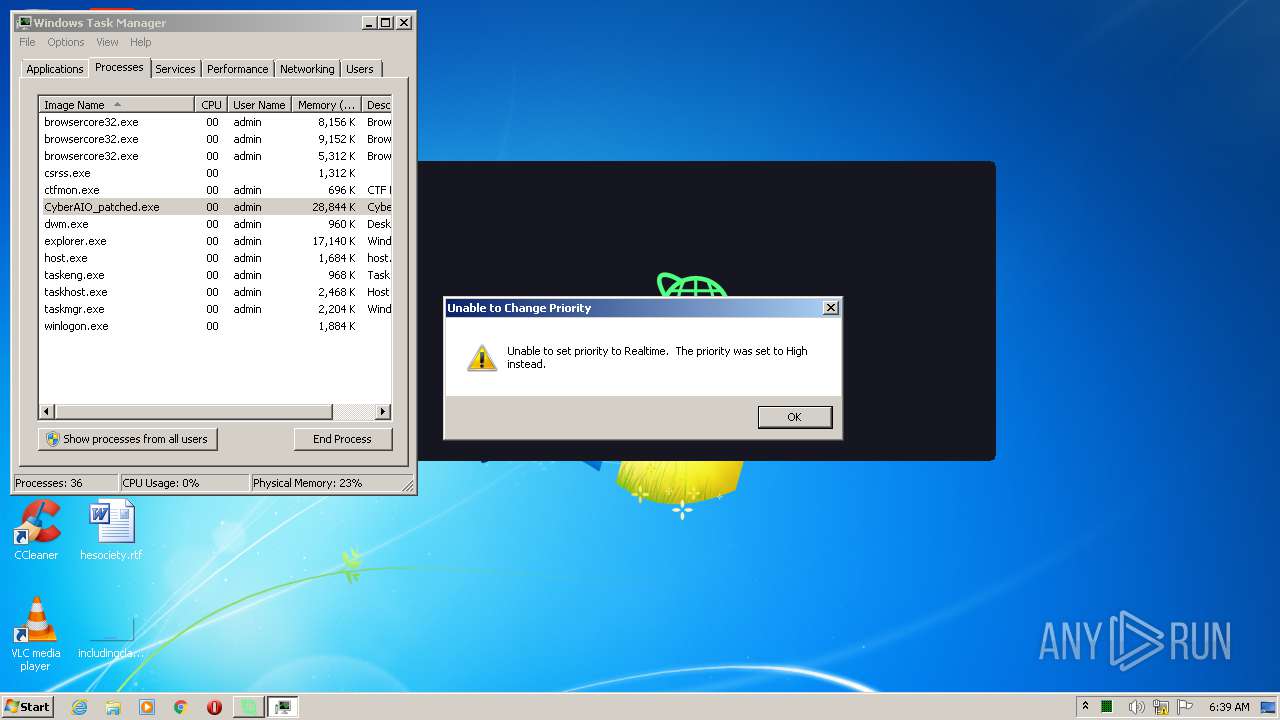
| URL: | https://anonfiles.com/B19eYcEao3/CyberAIO_patched_exe |
| Full analysis: | https://app.any.run/tasks/0cc1320a-130c-492f-88ba-797e8b8468e5 |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2021, 05:34:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4E027513010459BB48FE0360A6DDFAF1 |
| SHA1: | C4C8914C8347C5A276AF219E6892103AF0B6E0E6 |
| SHA256: | BEBF637E1FF4AAF3DD718F483A3DE7EDEE3F5DD6806C05046A5C21138C3165B7 |
| SSDEEP: | 3:N8M2mAamXw6u9BJAn:2M23129BJAn |
MALICIOUS
Application was dropped or rewritten from another process
- CyberAIO_patched.exe (PID: 1004)
- GZipCompress.exe (PID: 2284)
- browsercore32.exe (PID: 3136)
- browsercore32.exe (PID: 4088)
- browsercore32.exe (PID: 2244)
- browsercore32.exe (PID: 2644)
- browsercore32.exe (PID: 3616)
Loads dropped or rewritten executable
- CyberAIO_patched.exe (PID: 1004)
- browsercore32.exe (PID: 3616)
- browsercore32.exe (PID: 2644)
Drops executable file immediately after starts
- GZipCompress.exe (PID: 2284)
Actions looks like stealing of personal data
- browsercore32.exe (PID: 3136)
- browsercore32.exe (PID: 4088)
- browsercore32.exe (PID: 2244)
- browsercore32.exe (PID: 3616)
- browsercore32.exe (PID: 2644)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3004)
- GZipCompress.exe (PID: 2284)
- CyberAIO_patched.exe (PID: 1004)
Creates files in the program directory
- CyberAIO_patched.exe (PID: 1004)
Reads Environment values
- CyberAIO_patched.exe (PID: 1004)
Creates files in the user directory
- CyberAIO_patched.exe (PID: 1004)
Drops a file that was compiled in debug mode
- CyberAIO_patched.exe (PID: 1004)
- GZipCompress.exe (PID: 2284)
Application launched itself
- browsercore32.exe (PID: 3136)
Drops a file with too old compile date
- GZipCompress.exe (PID: 2284)
INFO
Reads settings of System Certificates
- iexplore.exe (PID: 3004)
- iexplore.exe (PID: 2760)
Changes settings of System certificates
- iexplore.exe (PID: 3004)
Creates files in the user directory
- iexplore.exe (PID: 3004)
- iexplore.exe (PID: 2760)
Reads internet explorer settings
- iexplore.exe (PID: 2760)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3004)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3004)
Changes internet zones settings
- iexplore.exe (PID: 3004)
Application launched itself
- iexplore.exe (PID: 3004)
Dropped object may contain Bitcoin addresses
- GZipCompress.exe (PID: 2284)
Reads the hosts file
- browsercore32.exe (PID: 3136)
Manual execution by user
- taskmgr.exe (PID: 612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
10
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CyberAIO_patched.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CyberAIO_patched.exe | iexplore.exe | ||||||||||||
User: admin Company: Cybersole Ltd Integrity Level: MEDIUM Description: CyberAIO Exit code: 0 Version: 4.3.2.2 Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe" --type=renderer --no-sandbox --file-url-path-alias="/gen=C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\gen" --disable-features=UseSurfaceLayerForVideo --disable-databases --disable-gpu-compositing --service-pipe-token=588532594043697268 --lang=en-US --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=588532594043697268 --renderer-client-id=2 --mojo-platform-channel-handle=1668 /prefetch:1 | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe | browsercore32.exe | ||||||||||||
User: admin Company: TeamDev Integrity Level: MEDIUM Description: BrowserCore Chromium Native Process Exit code: 0 Version: 69.0.3497.12 Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\GZipCompress.exe" "C:\Users\admin\AppData\Roaming\CyberAIO 4.0\packages\DotNetBrowser.Chromium32.dll" "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit" | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\GZipCompress.exe | CyberAIO_patched.exe | ||||||||||||
User: admin Company: TeamDev Ltd. Integrity Level: MEDIUM Description: GZipCompress Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2644 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe" --type=gpu-process --disable-features=UseSurfaceLayerForVideo --disable-gpu-sandbox --no-sandbox --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --dpi-awareness=system-aware --gpu-preferences=KAAAAAAAAACAAwBgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --use-gl=swiftshader-webgl --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --dpi-awareness=system-aware --service-request-channel-token=9404601568273698670 --mojo-platform-channel-handle=1724 /prefetch:2 | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe | browsercore32.exe | ||||||||||||
User: admin Company: TeamDev Integrity Level: MEDIUM Description: BrowserCore Chromium Native Process Exit code: 0 Version: 69.0.3497.12 Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3004 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Internet Explorer\iexplore.exe" https://anonfiles.com/B19eYcEao3/CyberAIO_patched_exe | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3136 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe" "--port=51213" "--no-sandbox" "--pid=1004" "--dpi-awareness=system-aware" "--crash-dump-dir=C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" "--lang=en-US" "--disable-surfaces" "--noerrdialogs" "--disable-web-security" "--disable-gpu" "--disable-gpu-compositing" | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe | CyberAIO_patched.exe | ||||||||||||
User: admin Company: TeamDev Integrity Level: MEDIUM Description: BrowserCore Chromium Native Process Exit code: 0 Version: 69.0.3497.12 Modules
| |||||||||||||||
| 3616 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe" --type=gpu-process --disable-features=UseSurfaceLayerForVideo --no-sandbox --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --dpi-awareness=system-aware --gpu-preferences=KAAAAAAAAACAAwBgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --use-gl=swiftshader-webgl --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --dpi-awareness=system-aware --service-request-channel-token=17505274569815845898 --mojo-platform-channel-handle=1712 /prefetch:2 | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe | browsercore32.exe | ||||||||||||
User: admin Company: TeamDev Integrity Level: MEDIUM Description: BrowserCore Chromium Native Process Exit code: 0 Version: 69.0.3497.12 Modules
| |||||||||||||||
| 4088 | "C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe" --type=utility --disable-features=UseSurfaceLayerForVideo --lang=en-US --no-sandbox --no-sandbox --crash-dump-dir="C:\Users\admin\AppData\Roaming\DotNetBrowser\dotnetbrowser.dmp.dir" --dpi-awareness=system-aware --service-request-channel-token=12415228350373821896 --mojo-platform-channel-handle=1600 /prefetch:8 | C:\Users\admin\AppData\Local\Temp\dotnetbrowser-chromium\69.0.3497.12.1.21.5.0.685\32bit\browsercore32.exe | browsercore32.exe | ||||||||||||
User: admin Company: TeamDev Integrity Level: MEDIUM Description: BrowserCore Chromium Native Process Exit code: 0 Version: 69.0.3497.12 Modules
| |||||||||||||||
Total events
1 213
Read events
1 066
Write events
143
Delete events
4
Modification events
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1442713810 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30876765 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
11
Suspicious files
29
Text files
109
Unknown types
67
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8E56.tmp | — | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8E57.tmp | — | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\CyberAIO_patched_exe[1].htm | html | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\anonfiles[1].css | text | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\KP42JS6M.txt | text | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\app[1].js | text | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\exe[1].png | image | |
MD5:6BF5E4AB859FD40841D4B6E3F73672D7 | SHA256:F7501F1E544E84CC5FA5A6D98DD4064B8DB0AE2AEC7F8FBC24A5C78FC7F2B2D9 | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\api[1].js | text | |
MD5:6C6281C15CBC981BC05942BAC40BCD7E | SHA256:0D3118E306C6A26F1D2EFCB698984E6922C5E7E155C94A84760E36E5592A3C11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
46
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3004 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2760 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.48 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
2760 | iexplore.exe | GET | 200 | 23.55.163.73:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 23.55.163.73:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3004 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3004 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 4.19 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3004 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2760 | iexplore.exe | 151.101.66.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
3004 | iexplore.exe | 172.67.144.254:443 | anonfiles.com | — | US | suspicious |
2760 | iexplore.exe | 13.224.194.221:443 | djv99sxoqpv11.cloudfront.net | — | US | unknown |
2760 | iexplore.exe | 23.55.163.73:80 | crl.identrust.com | Akamai International B.V. | US | unknown |
2760 | iexplore.exe | 217.64.149.22:443 | cdn-105.anonfiles.com | — | IR | unknown |
2760 | iexplore.exe | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
2760 | iexplore.exe | 13.224.194.38:443 | djv99sxoqpv11.cloudfront.net | — | US | suspicious |
2760 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
1004 | CyberAIO_patched.exe | 104.22.36.247:443 | cdn.cybersole.io | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
anonfiles.com |
| shared |
ocsp.digicert.com |
| whitelisted |
vjs.zencdn.net |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
ocsp2.globalsign.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
s.symcd.com |
| shared |
cdn-105.anonfiles.com |
| suspicious |
crl.identrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
browsercore32.exe | [0329/063725.762:ERROR:gpu_process_transport_factory.cc(1018)] Lost UI shared context.
|
browsercore32.exe | [0329/063725.887:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|
browsercore32.exe | [0329/063725.887:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|
browsercore32.exe | [0329/063725.903:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|
browsercore32.exe | [0329/063725.903:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|
browsercore32.exe | [0329/063725.903:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|
browsercore32.exe | [0329/063725.903:WARNING:account_consistency_mode_manager.cc(290)] Desktop Identity Consistency cannot be enabled as no OAuth client ID and client secret have been configured.
|