| File name: | WhatsApp-Key-DB-Extractor-master.zip |
| Full analysis: | https://app.any.run/tasks/4d6cbc79-c02f-4d02-b96d-5d001e3c9f87 |
| Verdict: | Malicious activity |
| Analysis date: | January 20, 2021, 16:22:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 0769154334E022047C0A23D93E3CEF8A |
| SHA1: | 551761662BFE233D1109C810BFCC6F640F10C76C |
| SHA256: | BEB32B7494D9BE95AF90219E1CA73209808C55AD4FA6AAEFF539B8FB1C4F4FE2 |
| SSDEEP: | 196608:WsKmk9D8czVbuBtuKL58BzP6gbCzK9xgaqRtfUXLY:p7kTsbugVgecY |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3352)
- adb.exe (PID: 2196)
- adb.exe (PID: 3472)
- adb.exe (PID: 184)
- adb.exe (PID: 3152)
Application was dropped or rewritten from another process
- adb.exe (PID: 3472)
- adb.exe (PID: 2196)
- adb.exe (PID: 184)
- adb.exe (PID: 3152)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2800)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2800)
Drops a file with too old compile date
- WinRAR.exe (PID: 2800)
Application launched itself
- adb.exe (PID: 3472)
INFO
Manual execution by user
- cmd.exe (PID: 528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2016:10:20 19:26:21 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | WhatsApp-Key-DB-Extractor-master/ |
Total processes
42
Monitored processes
7
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | adb fork-server server | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\adb.exe | adb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
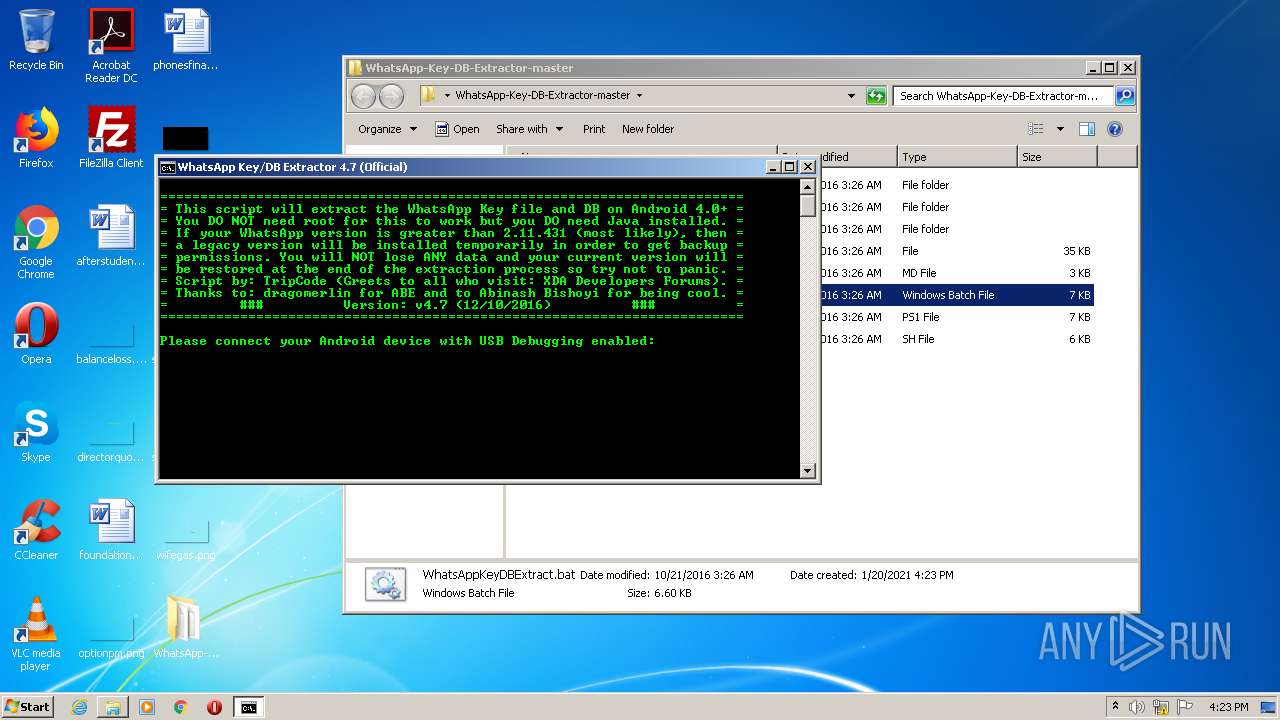
| 528 | cmd /c ""C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\WhatsAppKeyDBExtract.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2196 | bin\adb.exe kill-server | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\adb.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WhatsApp-Key-DB-Extractor-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3152 | bin\adb.exe wait-for-device | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\adb.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3352 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3472 | bin\adb.exe start-server | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\adb.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
809
Read events
783
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WhatsApp-Key-DB-Extractor-master.zip | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2800) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
11
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\LICENSE | text | |
MD5:84DCC94DA3ADB52B53AE4FA38FE49E5D | SHA256:589ED823E9A84C56FEB95AC58E7CF384626B9CBF4FDA2A907BC36E103DE1BAD2 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\grep.exe | executable | |
MD5:83A3D89F40A05038760110B1E6E54762 | SHA256:E8030DB6E3438355D098533B3CCDCBDE1801AB67FA8917506FE50489C11A5751 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\curl.exe | executable | |
MD5:E87C7A33BB6802C39D1905622BBDC80C | SHA256:632CC16CE51CF77F342BA60035749B496A80738334ADD769253474A506910960 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\AdbWinUsbApi.dll | executable | |
MD5:5F23F2F936BDFAC90BB0A4970AD365CF | SHA256:041C6859BB4FC78D3A903DD901298CD1ECFB75B6BE0646B74954CD722280A407 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\AdbWinApi.dll | executable | |
MD5:47A6EE3F186B2C2F5057028906BAC0C6 | SHA256:14A51482AA003DB79A400F4B15C158397FE6D57EE6606B3D633FA431A7BFDF4B | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\libiconv2.dll | executable | |
MD5:E0DC8C6BBC787B972A9A468648DBFD85 | SHA256:6DEEDAD652BFAB7B09EBD0E06045810390B6AC6CB5AA9EF41C9DAA5616181F22 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\regex2.dll | executable | |
MD5:547C43567AB8C08EB30F6C6BACB479A3 | SHA256:3A71BF90E8BDDFB813B44F9CBCECF431311A7979C1DEBC976767B3E5E59031AF | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\bin\adb.exe | executable | |
MD5:C4BE24DF324EE7892EFA1FA1871B9BC0 | SHA256:AD5D27384D1B5BCEB6342BB3204FEE977217422BCAFD252AB18F763A3DE43931 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\README.md | text | |
MD5:515EDD3D594543F2FDB8E0756CD8506F | SHA256:9766FFC6464ED3096E3448BE1E9F8949D9A7F6FB522C644709DA4EDF6CE33108 | |||
| 2800 | WinRAR.exe | C:\Users\admin\Desktop\WhatsApp-Key-DB-Extractor-master\extracted\.placeholder | binary | |
MD5:68B329DA9893E34099C7D8AD5CB9C940 | SHA256:01BA4719C80B6FE911B091A7C05124B64EEECE964E09C058EF8F9805DACA546B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report