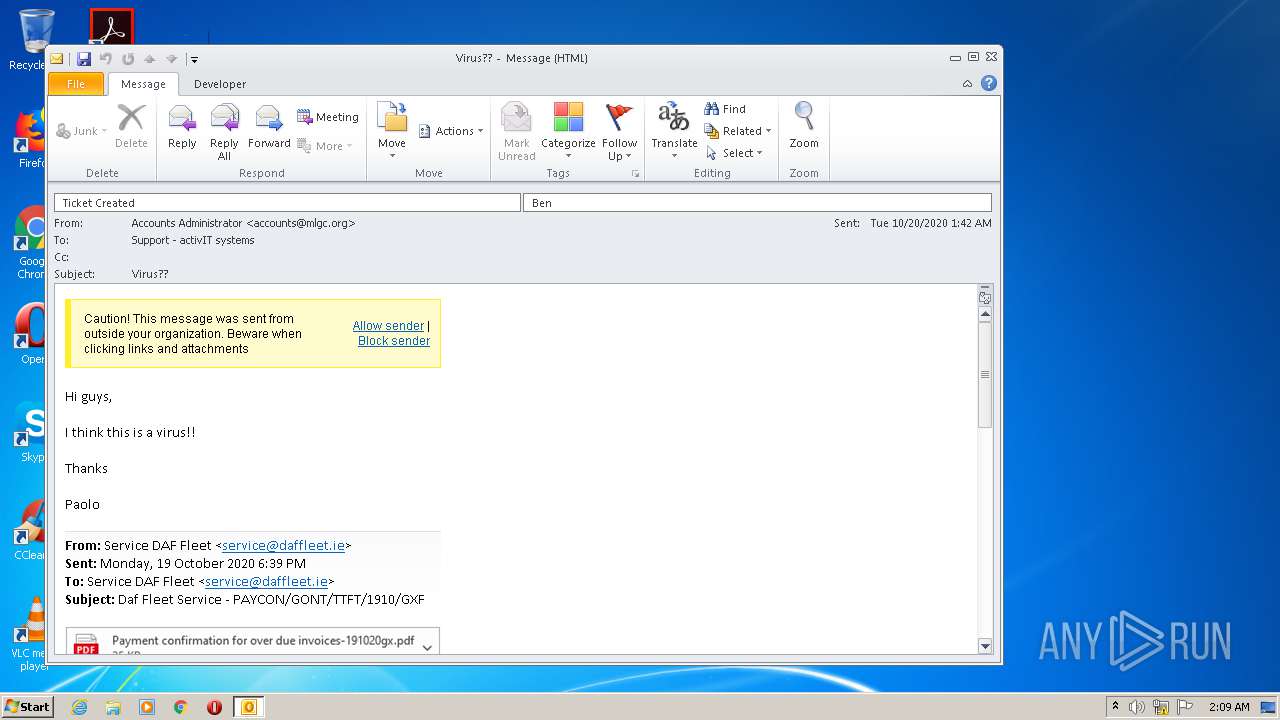
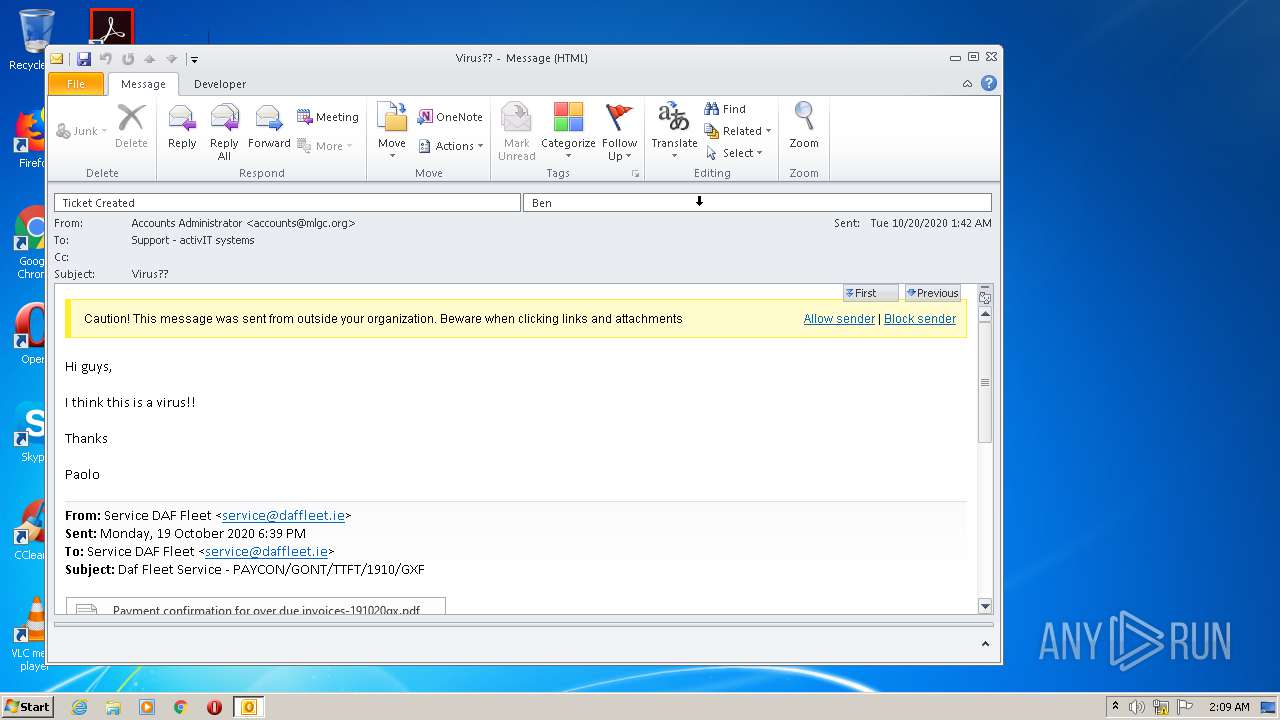
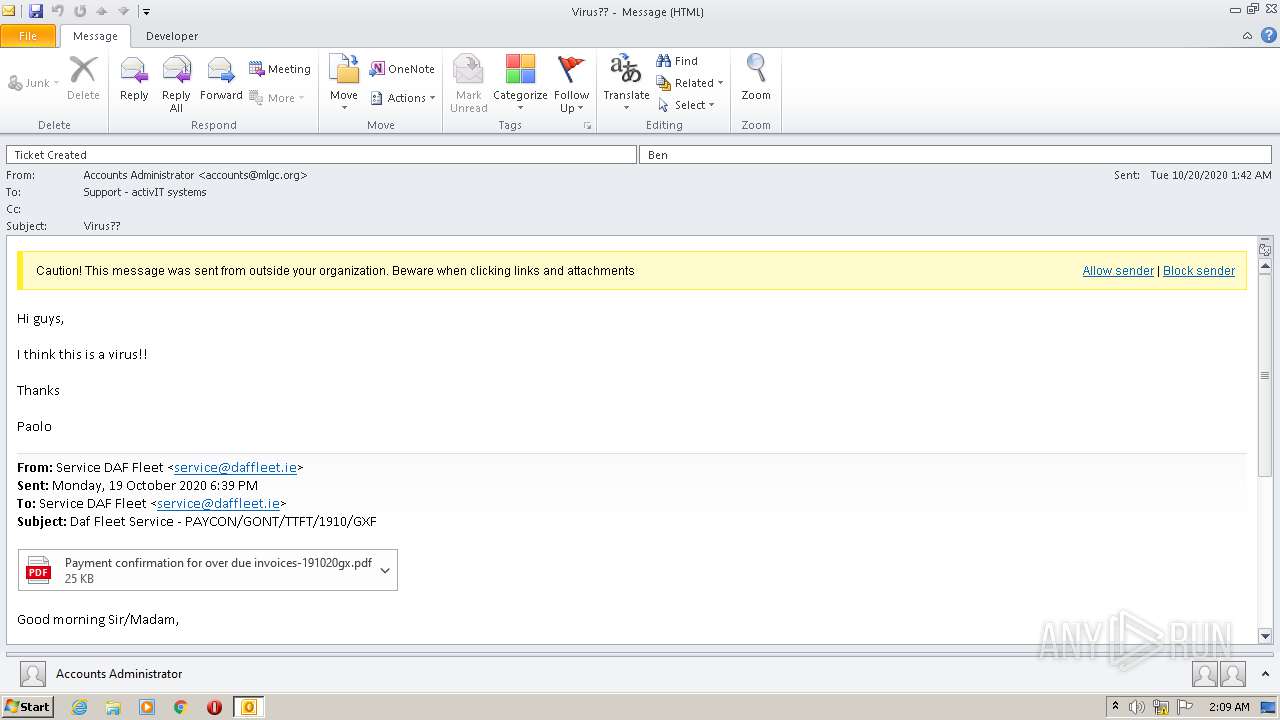
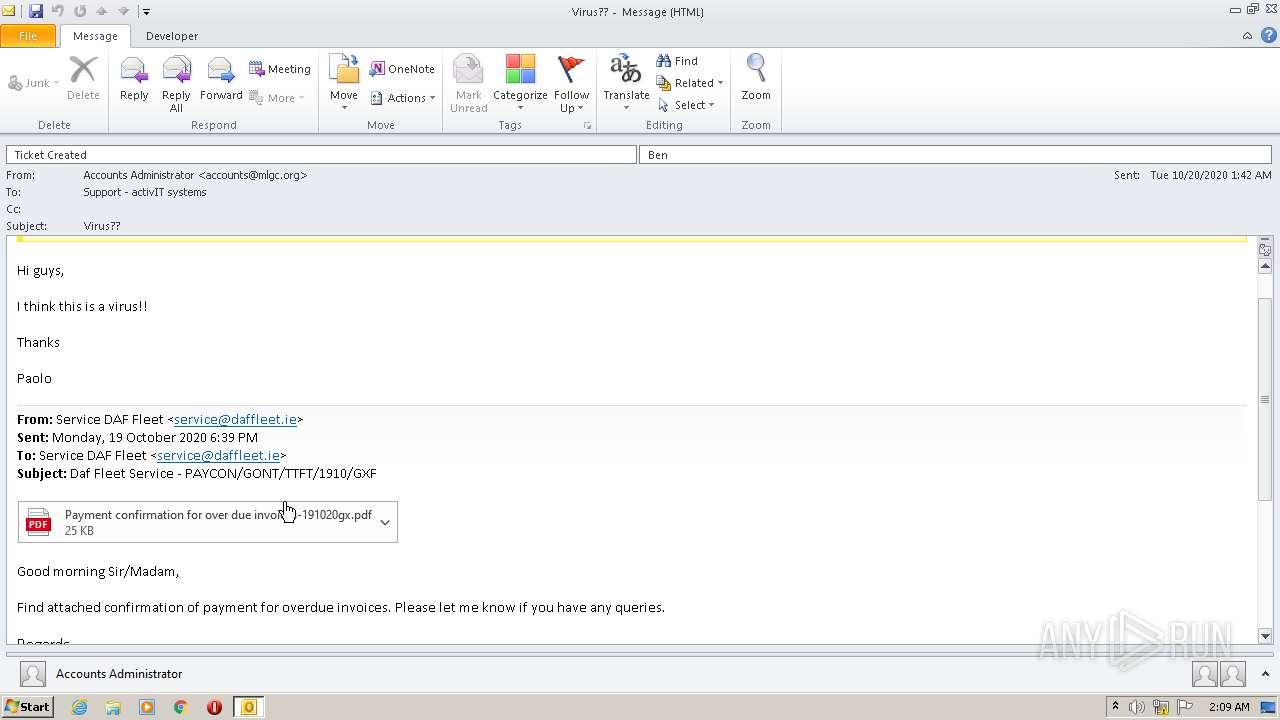
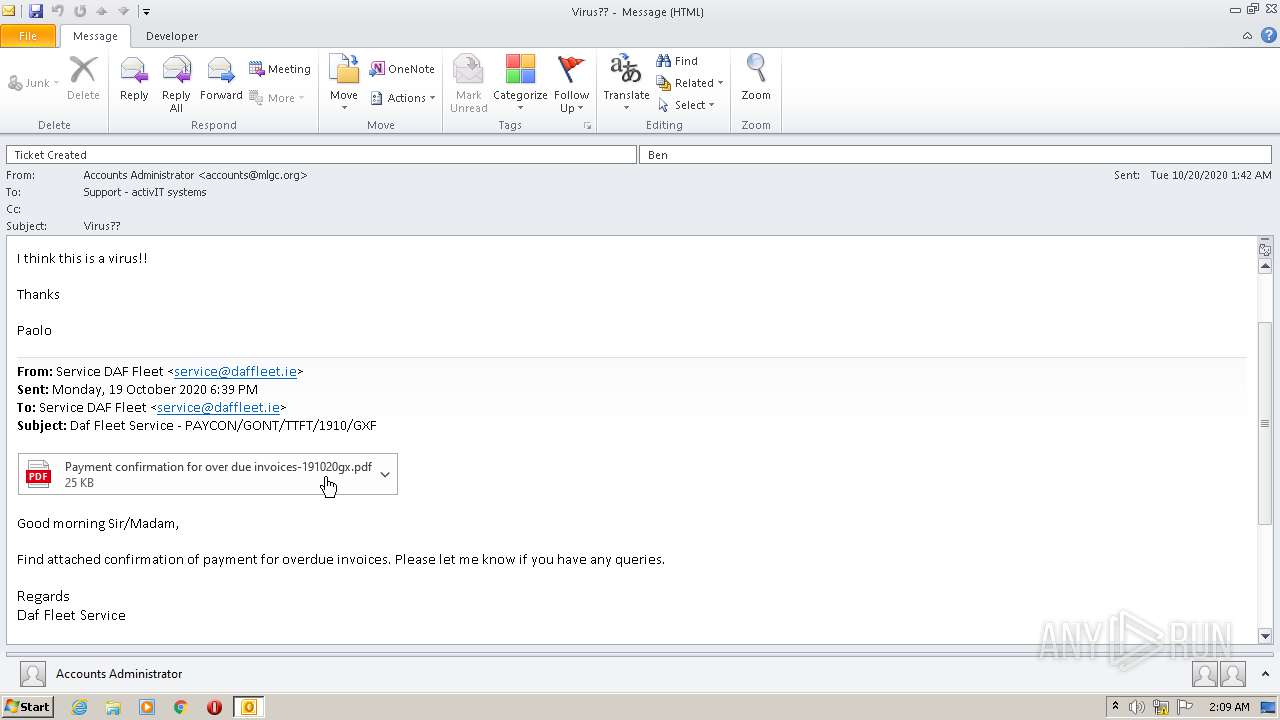
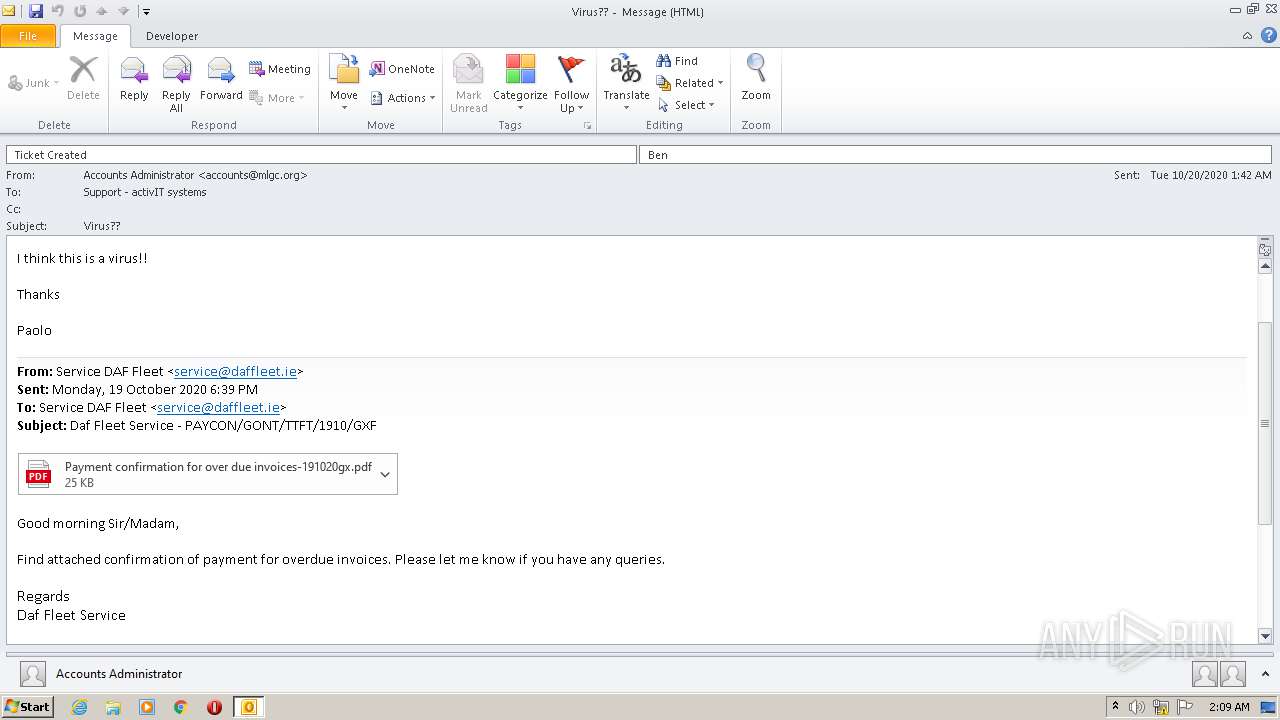
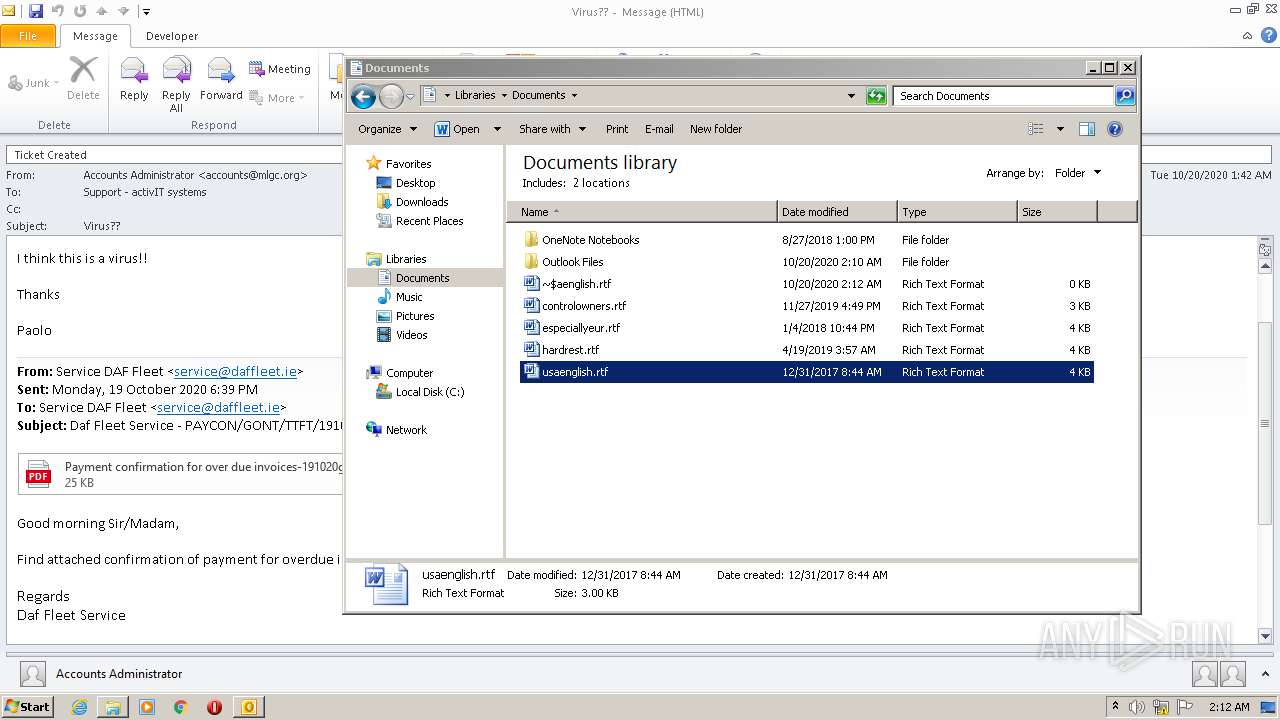
| File name: | Virus__.msg |
| Full analysis: | https://app.any.run/tasks/01dd79ca-280e-4bbd-85c8-d04a43225c8c |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | October 20, 2020, 01:08:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 6FD4E26FDCC3C9AAB981835F59427DD4 |
| SHA1: | 5E521AF536F4CC9AE81CFDB0AB7174AF1C8079E5 |
| SHA256: | BE6DE4B6321C84F2A044D7F676BECBE1E8AC28C1BC817E71279E75ECCA02876E |
| SSDEEP: | 3072:a1wWIeryy137FO0qZyB9qEIm1iqgfsTjibOLgWCD+aggpkrDypq:GTp3Z8Y9J13Kb9WCyaggpfp |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2556)
Executes PowerShell scripts
- cmd.exe (PID: 1748)
QEALLER was detected
- javaw.exe (PID: 3532)
Actions looks like stealing of personal data
- javaw.exe (PID: 3532)
Loads dropped or rewritten executable
- javaw.exe (PID: 3532)
Loads the Task Scheduler COM API
- mmc.exe (PID: 3940)
SUSPICIOUS
Creates files in the user directory
- javaw.exe (PID: 3532)
- powershell.exe (PID: 3432)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2556)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3532)
Executable content was dropped or overwritten
- javaw.exe (PID: 3532)
Starts application with an unusual extension
- cmd.exe (PID: 1748)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1652)
- OUTLOOK.EXE (PID: 2556)
- iexplore.exe (PID: 2380)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2380)
Manual execution by user
- javaw.exe (PID: 3532)
- explorer.exe (PID: 3840)
- WINWORD.EXE (PID: 1856)
- mmc.exe (PID: 916)
- mmc.exe (PID: 3940)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2556)
- WINWORD.EXE (PID: 1856)
Application launched itself
- iexplore.exe (PID: 2380)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2556)
- WINWORD.EXE (PID: 1856)
Changes internet zones settings
- iexplore.exe (PID: 2380)
Reads settings of System Certificates
- iexplore.exe (PID: 1652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
58
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2380 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1748 | cmd.exe /c chcp 1252 > NUL & powershell.exe -ExecutionPolicy Bypass -NoExit -NoProfile -Command - | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
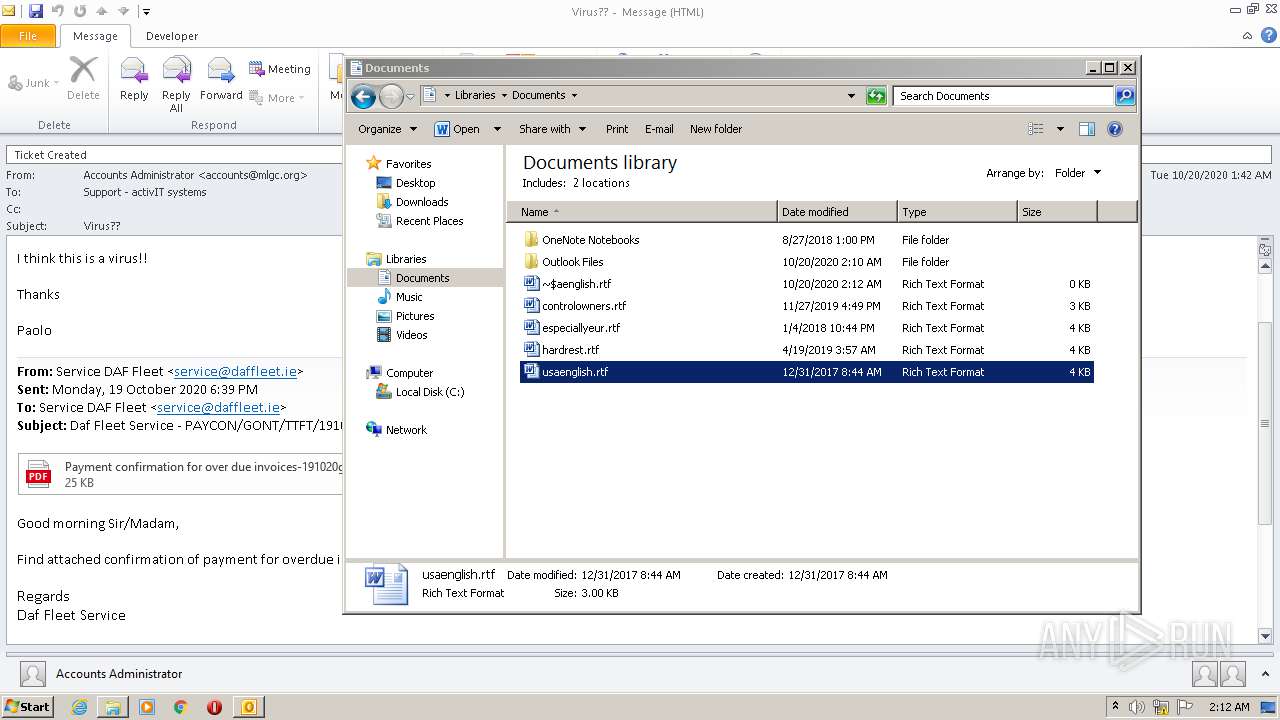
| 1856 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\usaenglish.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2104 | chcp 1252 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
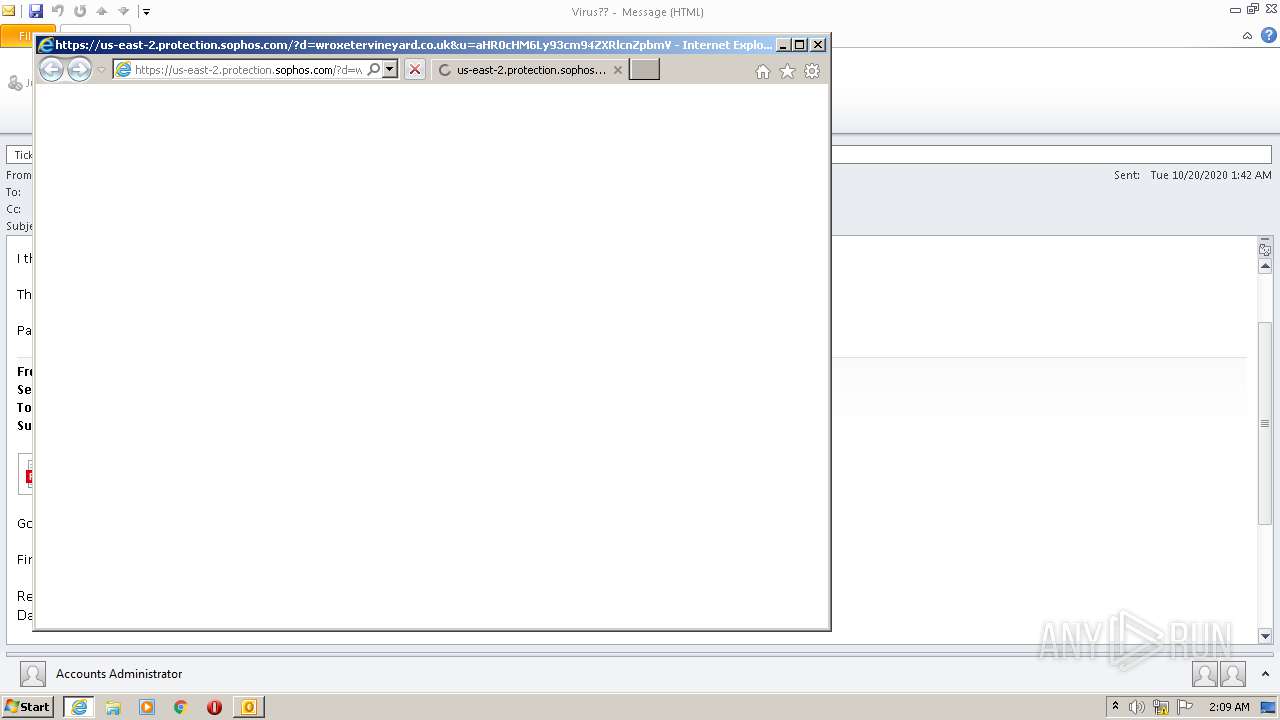
| 2380 | "C:\Program Files\Internet Explorer\iexplore.exe" https://us-east-2.protection.sophos.com/?d=wroxetervineyard.co.uk&u=aHR0cHM6Ly93cm94ZXRlcnZpbmV5YXJkLmNvLnVrLw==&e=c3VwcG9ydEBhaXRzeXMuY29tLmF1&t=Wi9zNHptSURkemIvY2FNT3Z2dzBac0lYOUVQaGhLRFNYQUx3SEtsWHh3RT0=&h=c9ef06e1c6f043e2b540d5d154980b1c | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2556 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Virus__.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3432 | powershell.exe -ExecutionPolicy Bypass -NoExit -NoProfile -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
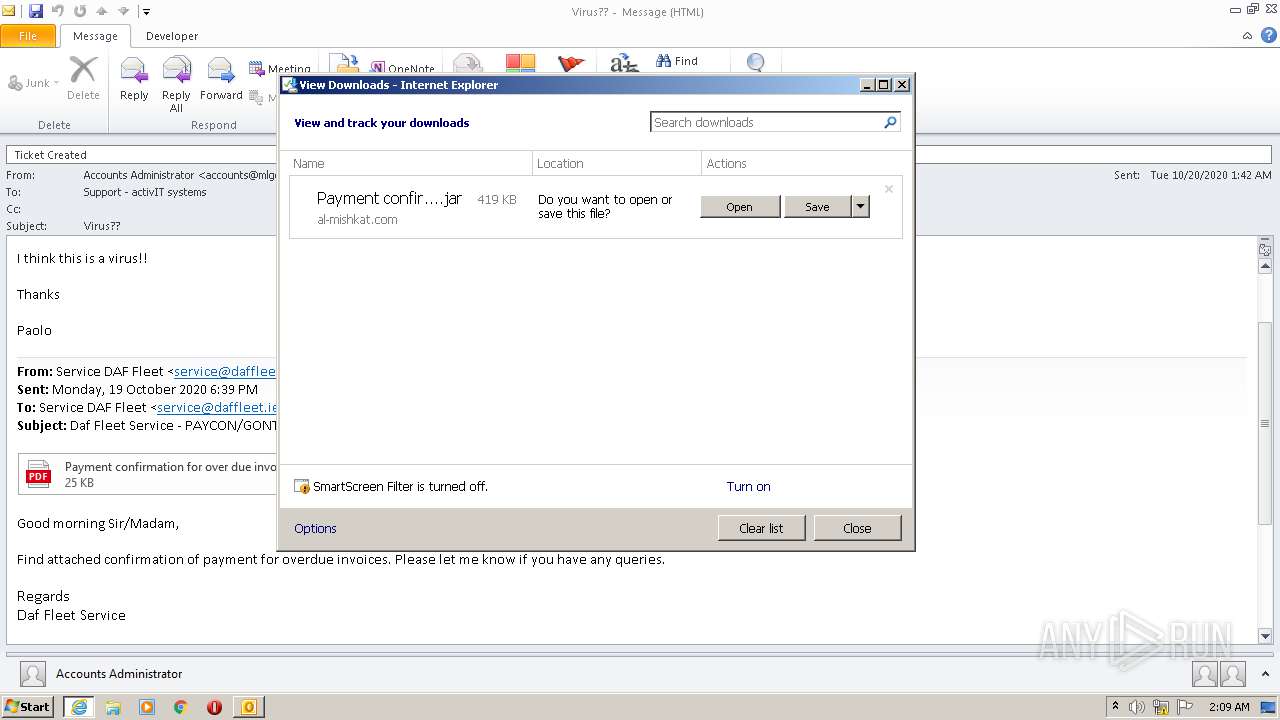
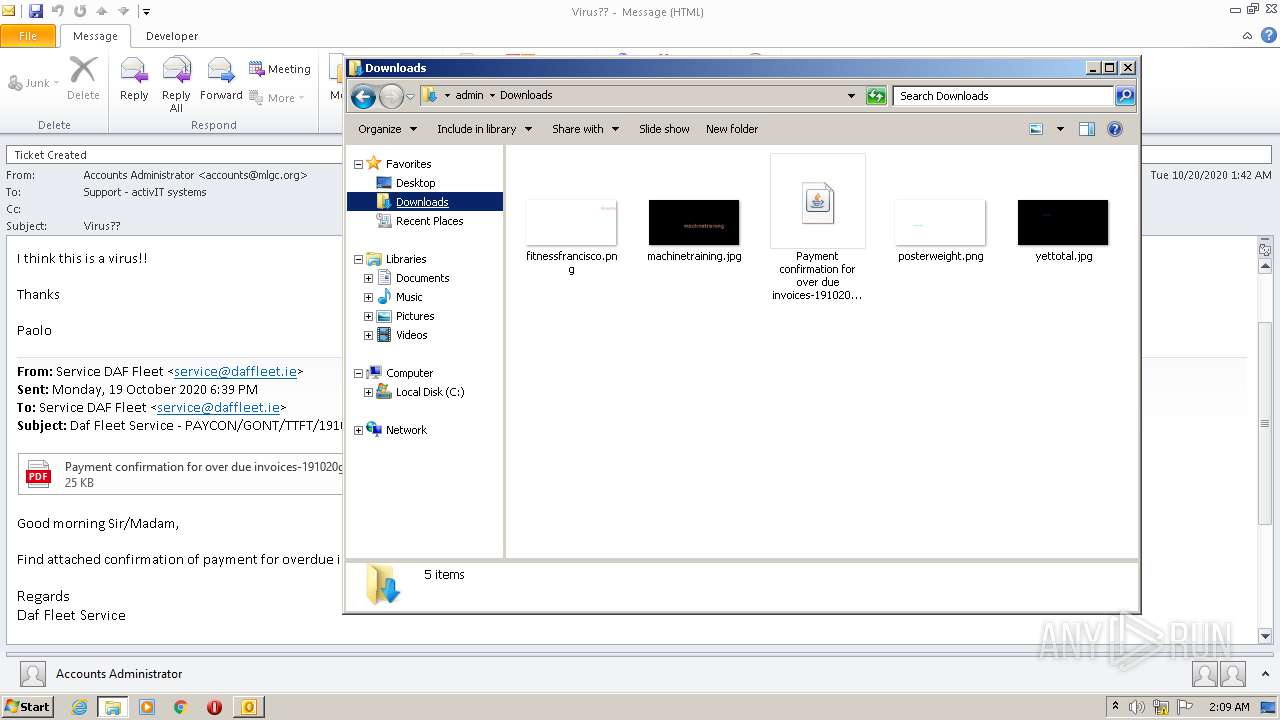
| 3532 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Downloads\Payment confirmation for over due invoices-191020gx.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3840 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 817
Read events
2 846
Write events
811
Delete events
160
Modification events
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2556) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
4
Suspicious files
21
Text files
38
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4098.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4D496867.dat | image | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7E9C560D.dat | image | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\42A0667E.dat | image | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\C212E0A3.dat | image | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1652 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab691F.tmp | — | |
MD5:— | SHA256:— | |||
| 1652 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6920.tmp | — | |
MD5:— | SHA256:— | |||
| 2556 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1F7E8CAA.dat | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
27
DNS requests
14
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2556 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1652 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEC8w4tAgdEt1RiKXlOpl6%2FU%3D | US | der | 471 b | whitelisted |
1652 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
1652 | iexplore.exe | GET | 200 | 54.230.182.118:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEALiUkureckjj7MJj36f730%3D | US | der | 471 b | whitelisted |
1652 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 728 b | whitelisted |
1652 | iexplore.exe | GET | 200 | 54.230.182.13:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
1652 | iexplore.exe | GET | 200 | 52.222.177.172:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
1652 | iexplore.exe | GET | 200 | 54.230.182.13:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
1652 | iexplore.exe | GET | 200 | 52.222.177.67:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2380 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1652 | iexplore.exe | 54.230.182.13:80 | o.ss2.us | Amazon.com, Inc. | US | unknown |
1652 | iexplore.exe | 54.230.182.118:80 | ocsp.sca1b.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
1652 | iexplore.exe | 52.222.177.67:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
1652 | iexplore.exe | 209.182.213.43:443 | wroxetervineyard.co.uk | InMotion Hosting, Inc. | US | unknown |
1652 | iexplore.exe | 103.8.25.8:443 | al-mishkat.com | SKSA TECHNOLOGY SDN BHD | MY | unknown |
1652 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
3532 | javaw.exe | 179.43.141.91:80 | — | Private Layer INC | CH | malicious |
2380 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1652 | iexplore.exe | 52.222.177.214:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
1652 | iexplore.exe | 54.230.183.38:443 | us-east-2.protection.sophos.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
us-east-2.protection.sophos.com |
| shared |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
wroxetervineyard.co.uk |
| unknown |
ocsp.comodoca.com |
| whitelisted |
al-mishkat.com |
| unknown |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
3532 | javaw.exe | A Network Trojan was detected | STEALER [PTsecurity] Pyrogenic.Qealler |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|