| File name: | GandCrab 5.0.3 downloader.js |
| Full analysis: | https://app.any.run/tasks/e39a3493-8474-4540-ad51-7ce71a933caa |
| Verdict: | Malicious activity |
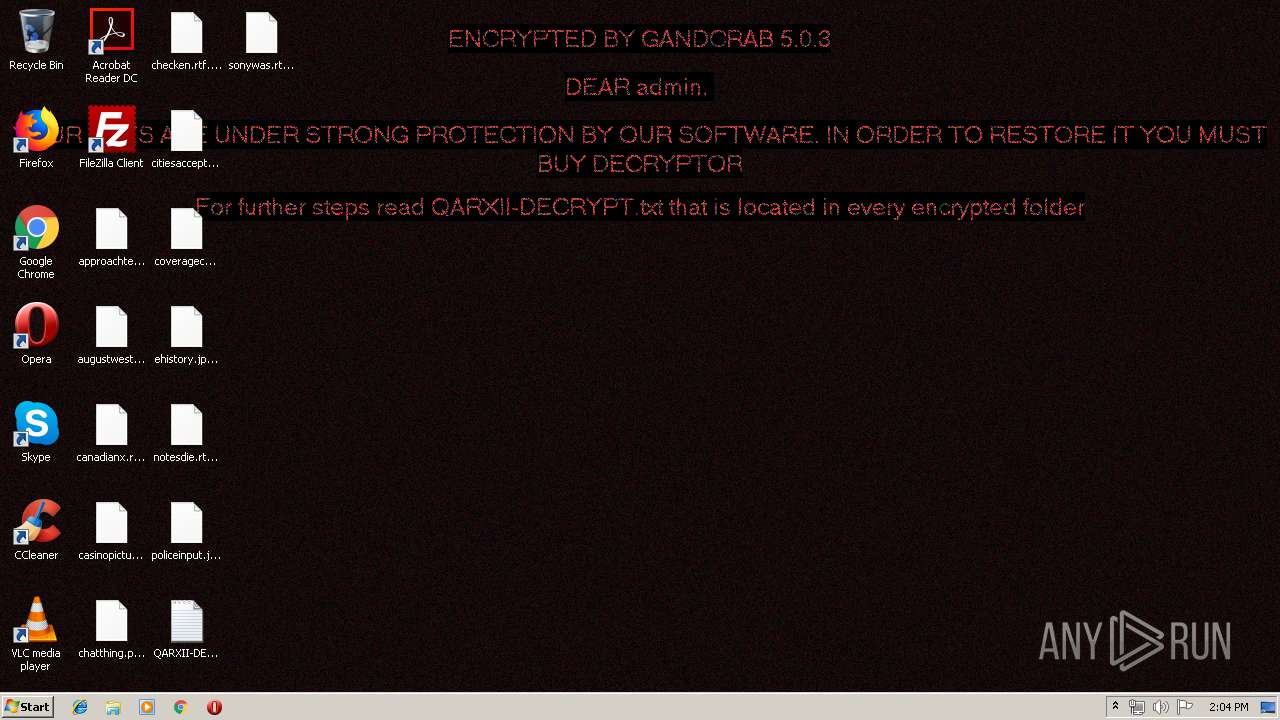
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | May 24, 2019, 13:03:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 595A31A4913951D3EB7211618AE75DEA |
| SHA1: | 16DBFE657AC36A8D84AF411F13EBFF1CCC5E56AD |
| SHA256: | BE6A4997FDF6EA0D74A973AE0A361EBCC4CBBC74A5801E75A76BB52A2B424E34 |
| SSDEEP: | 12288:lNelh1RLsMUu8HRCTEr45VYYtkG8eAVIsNOd:lNelh1RLsMUu8HRCR3UeAVIsNs |
MALICIOUS
Application was dropped or rewritten from another process
- dsoyaltj.exe (PID: 2844)
GandCrab keys found
- wermgr.exe (PID: 3612)
Writes file to Word startup folder
- wermgr.exe (PID: 3612)
Actions looks like stealing of personal data
- wermgr.exe (PID: 3612)
Renames files like Ransomware
- wermgr.exe (PID: 3612)
Dropped file may contain instructions of ransomware
- wermgr.exe (PID: 3612)
Deletes shadow copies
- wermgr.exe (PID: 3612)
GANDCRAB detected
- wermgr.exe (PID: 3612)
SUSPICIOUS
Executable content was dropped or overwritten
- WScript.exe (PID: 2716)
Reads the cookies of Mozilla Firefox
- wermgr.exe (PID: 3612)
Creates files like Ransomware instruction
- wermgr.exe (PID: 3612)
Creates files in the user directory
- wermgr.exe (PID: 3612)
INFO
Dropped object may contain Bitcoin addresses
- wermgr.exe (PID: 3612)
Dropped object may contain TOR URL's
- wermgr.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | wermgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2716 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\GandCrab 5.0.3 downloader.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\dsoyaltj.exe" | C:\Users\admin\dsoyaltj.exe | — | WScript.exe | |||||||||||
User: admin Company: www.sopcast.com Integrity Level: MEDIUM Description: SopCast Main Application Exit code: 0 Version: 4.2.0.800 Modules
| |||||||||||||||
| 3612 | "C:\Windows\System32\wermgr.exe" | C:\Windows\System32\wermgr.exe | dsoyaltj.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
508
Read events
473
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2716) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2716) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E007100610072007800690069000000 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001009DC51F0C8849C58233C00D697DDF5F170B9BE0B9A5D027225D9AEA3ADF3E255A4EB980B2D4BBBCFDDBFA61078D3F16733BC3B44F1ECA5713D1A6141F7EE57CE0A512AB91702F31DF83697AD78B7EFECF10CFFC7C376F2FD4522AF5D801326ADB5BBE546D7009554FE04404718E7C60FA718FFB348E654BDCE11724E4DCADBC39D049B7B7EA2B440E8F1F16857E1D319634A968B57DEE6C843B97C9D2368A720A3E9A7222F77B4DA70151819C8EAEB3BECA1FFEB1985CA79CECD4BA878168ACF78622DF30B9A09FA027063A22C351AC8EE32D906782D282226839CAC2A53CE4B42BF23EC7B1943281A4A23700CEF7F27331F1C21C1AA4A4729D613ADAD50AA8E5 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 940400004D621AA4B3C06DA8A0CE6CF0F83D2D340AA5FAAF5719E998C9405E03D09324E67B7D6BCF4E2A5872EFA9E456DCB2420B2B68F601426C1773C07868B18E74956AC5946FAD32FD19239BB5F6F0FC97945B85CA040CAE9800F70AC61CD658D727825BB2D6909C3FB502288642EFCA42096A87AEF1C3019DE22AD9240634A87B5C91BBEBEA989FFDFA0C5D661AF2D033DD3A9FA1ABBAF48D871222D52234C0DC49549A2178768A7E52368BA2200B94ABA1EC10A309002EEFFD7A23855022399CCAC7F6F2C3DE67CEA1A8D3A95B1D1E0F07F9C25A0E6FD24DD09E67E1AC41D6FDC37C8181E065370964759F4B52302D3531AB17FFAE7FD0CF0CA9FD163B16D77C3D98ADF127E0B2474C15E4971875D45409188072FCF3B9EFF3EAE20ECD774E9AEA3A54C9BC290A59FB7A08EAB06F47C0FD2A5D985D8255651FA1AA2D932CA8AF3447C8641E149D6ACBF900A06BE6403F1FFCAC300596BA843D4F3253EB04D224AF2DA1E4C7771262FEE1A18DF3F71667D0725B49769037A9B37E62A8C5123D2CD60D93928833109EB3BD3A7476859F3B6CC65F14D532E296CCF31137950C08B0695770F8ED82B2D488F524431A539438FF5B681B885D7F4AA5222845C63BCF3C089B9BEAA9774E13A406C1D28F15193D7C5F21C5E2F1ECD3DC3BCC043D9B2D2EE8D525AC2DF4E55F6A05B3B30945B4A4FAFB7E64B0D153662A5237B6C0C62AF35E10A130EA0BE9CF5CE12863745225DD4A126BB1DAB9F5B1763CCA9369EDECE871D55341E7B1FD5996A6627AA3596FF26D8C727717F0BED61EDA51B8C926D92734AF046321D384A6DADA6CF4DE9403B4822816110813750763D606BC3930852ABEC9898108E6730C486B024FB1F56C42876A943344DC89BA6CCA342F3789BEB57F7092621FF2D464BCF624FB948B73B47F3C6FF5F92EC31F5DB82B5C26E1DDCA6D4C26F91C005AB1479571237BA300987790FB40437761FFE7C9A91262E3CCD8D30096A9F77D4D8185C4B38AE71BBD327C6AA52CC4A68421269B807906E0F618CC1F092F30F7F1102D7E2C0204A6FD76BD601FCA4C2B0764EB40A0539E7FFD6F2FA05B411F7D79B6309D9D4AAA86C62B72650DB0B913EF0A12604DA901AAEB7F9973D8DC566A7191522D96577AB3EBA670FBB45663A00AE6821D7271C5C92D4305E4576059826DDE87AF28A297B910F171C78D919327C6C9933CD28975E3D362C099B4FBFE71726AB35B301CDB4F68022C97A61754CDF088FE21E410AC575BFA852F14D94581F4B9746B761F0BFE3EA85FF076E2A542548E100ADE16168F1D59CB1A82901A53EB07F02B5D18D3402180007299F0E2F1BD778EB7582AB8A1474FF8DF8135BF24BE2B2C478D2EDEA61D9655CC2A239EAA6ECEC3D85276B09C17F7656B09D773392CF8076E15B3BDC1A60FB664E1E23F30BA7D6367705222AE96067289DCD8AF91B6983F6C637F5ACB33E3CD51CD282BD6F7EDE16D2F0C81E17EE229867C822E06D9A8766F003BC3DFE6335D11DBD9F48BF682AE9BA5B7103B8305B8AFF81098519CAEE025C6400DBAACED89A07198DDB36CC8CF587051BA24780089C0250A70A07409C95507580B59456C8EE72AA49C92573EE92B331BFC241753A14FE0CD9F6C069E3649691A48A4684F681A43C83E9C5E5B00627C58AFB82538C6506802EF7215C2AC3A046F18506D378FA677EB9C07C39665462EBB766E7DAF11F1473B0BB9BFD1D70DED388A23B944DDAB8A753665CDE36535362349C5E0B0F0A80C6DF5143DF94333E3B3FFEE2553CE073A4C8DBF8211E78BB2830721FA63B147EC86A1B39A396565194352A9E2A3E53FFE6AE610B19FEE54A867D94E15FF908625A04430092BD02BED7F7C502D1B5C3BC238986A0B8A38E1B7FEDB6E01C35223726CD3C0CDD6F8414C055623D7E666BEFA3180A7D64189EAD2ECEA7613864F67C6ECA1E56E9DF2FA9867D1D53303AC943BC388C643002F4B88439552C9930A3F6F59D942AFCD33FE0450684078AB7D5D69F4B6B72900BB6E00AF7F7C19A8935A378C60173106660310873D5AF66C1F7151352008AD5CA3E49CC5A035923F6C6499A5ABE4AF714B35E369F1DFB8AA3AEF69E0AA63BEC75098F3F0A34408DD362633B405749AB91AA366D6D2C9B97DB9E7122BBFF9424BED51FB01FE24EA148CB153B0E517F64038B11111433D34A17580F5E07CD5D93220BD1B4583A0B075BB396FC9219C2FA6574B9C86C657747527F6E340084455B459F7C2449C3F4EB2A219A54970A66D7E0CF329718F7508926352A5E36D270796E26E33B77F081427045F3554C9B2BB0E26D5303D4DC0531D5544D1A5865E49019CDDCFD2EADDF6105E47A20760F87B045937B6F3E3866E2D231F576B1EC4 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3612) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
1
Suspicious files
278
Text files
203
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | dsoyaltj.exe | C:\Users\admin\AppData\Local\Temp\Liebert.bmp | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\QARXII-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\QARXII-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3612 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\QARXII-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
8
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3612 | wermgr.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3612 | wermgr.exe | 78.46.77.98:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3612 | wermgr.exe | 217.26.53.161:443 | www.haargenau.biz | Hostpoint AG | CH | malicious |
3612 | wermgr.exe | 74.220.199.8:443 | www.bizziniinfissi.com | Unified Layer | US | malicious |
3612 | wermgr.exe | 136.243.13.215:443 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
3612 | wermgr.exe | 185.52.2.154:443 | www.fliptray.biz | RouteLabel V.O.F. | NL | suspicious |
3612 | wermgr.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3612 | wermgr.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.download.windowsupdate.com |
| whitelisted |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3612 | wermgr.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |