| File name: | ValoSploit V3_71196246.exe |
| Full analysis: | https://app.any.run/tasks/6b8e313a-d6f5-4139-b116-6cacefd59f39 |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2023, 21:23:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 93D16508432C3FF3512EB9DE584F48E6 |
| SHA1: | 6ED9FD4D190AFC6C5154730D85CF883FD3AD4D2E |
| SHA256: | BE5357F63B036DA79D198978CBC5B652EA02B1CCFCB1538352442CDC7F4D5549 |
| SSDEEP: | 98304:F7GowcdPyJC8JRlobIlEQBYIXwUOZkj0o14vZGcwhnVx/mp9814L/fKBUe3VBOUu:R/JiB |
MALICIOUS
Actions looks like stealing of personal data
- setup71196246.exe (PID: 1596)
SUSPICIOUS
Checks Windows Trust Settings
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
Reads security settings of Internet Explorer
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
Reads the Internet Settings
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 2304)
- setup71196246.exe (PID: 1596)
The process creates files with name similar to system file names
- setup71196246.exe (PID: 1596)
Reads the Windows owner or organization settings
- setup71196246.exe (PID: 1596)
Reads settings of System Certificates
- setup71196246.exe (PID: 1596)
- ValoSploit V3_71196246.exe (PID: 2408)
Adds/modifies Windows certificates
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
Searches for installed software
- setup71196246.exe (PID: 1596)
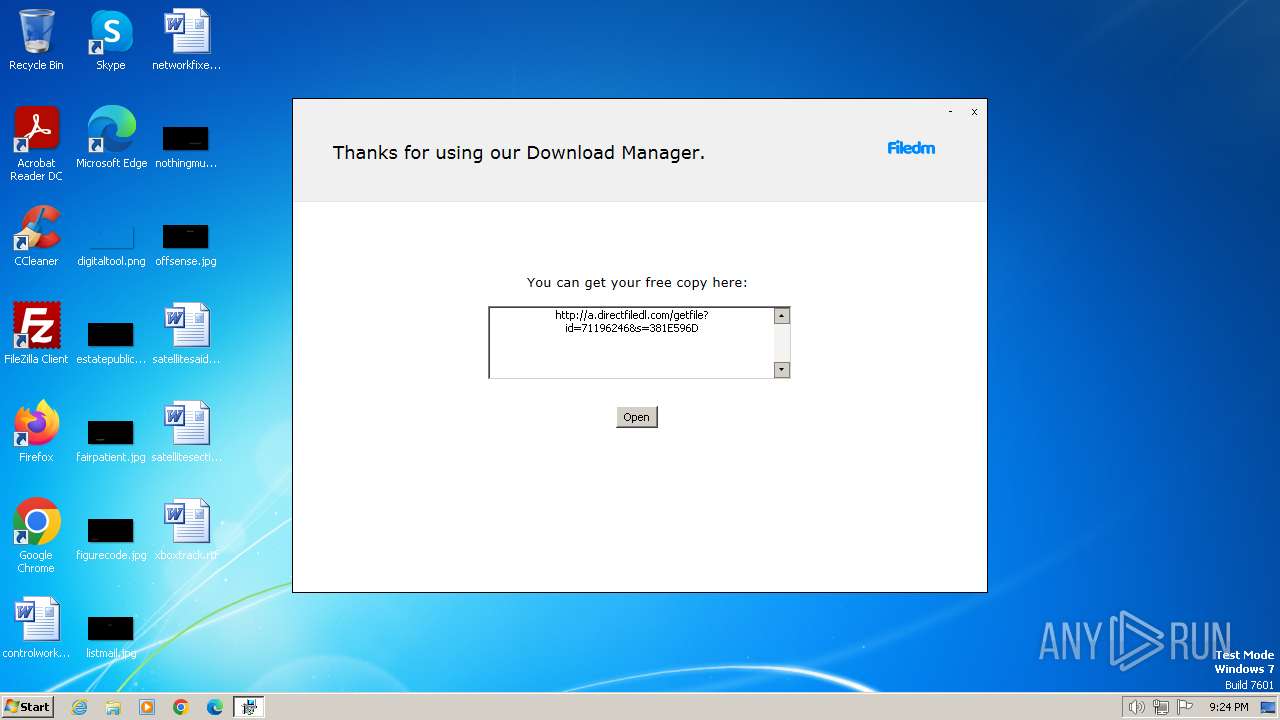
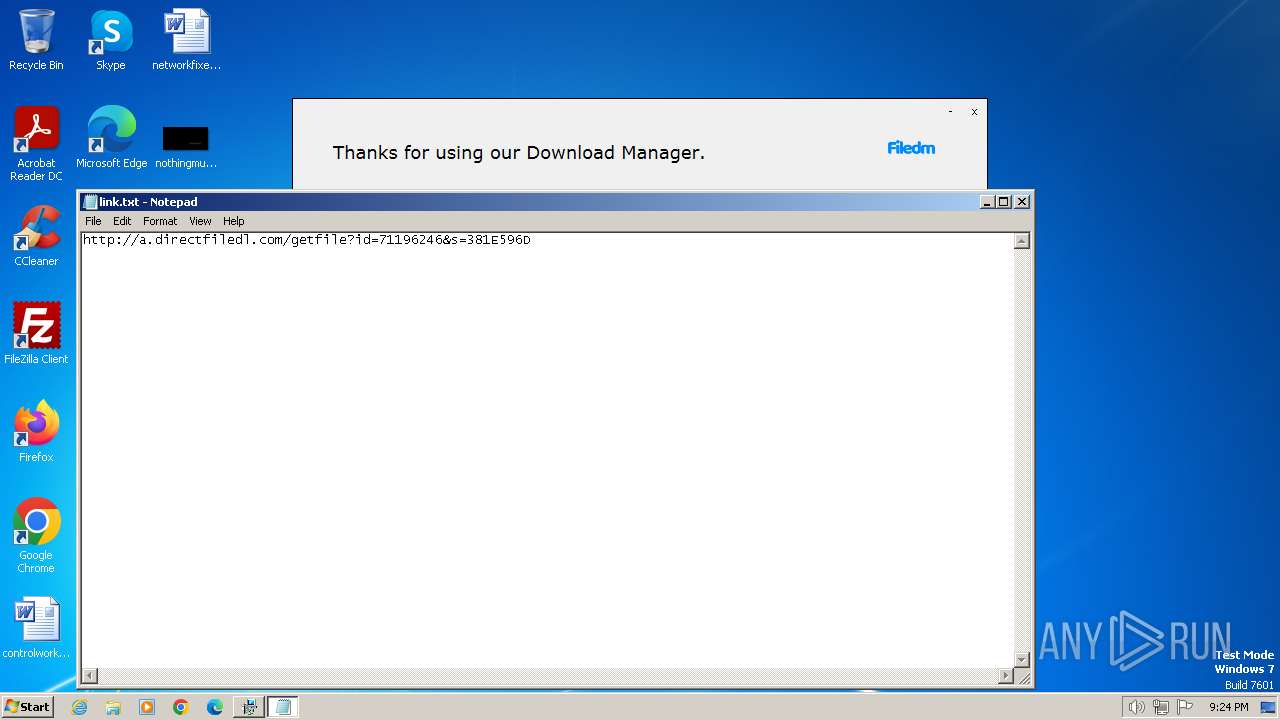
Start notepad (likely ransomware note)
- ValoSploit V3_71196246.exe (PID: 2408)
Get information on the list of running processes
- cmd.exe (PID: 2668)
Executing commands from a ".bat" file
- setup71196246.exe (PID: 1596)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2668)
Starts CMD.EXE for commands execution
- setup71196246.exe (PID: 1596)
INFO
Drops the executable file immediately after the start
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
Reads the computer name
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
- setup71196246.exe (PID: 2304)
Checks proxy server information
- ValoSploit V3_71196246.exe (PID: 2408)
Reads the machine GUID from the registry
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
- setup71196246.exe (PID: 2304)
Checks supported languages
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
- setup71196246.exe (PID: 2304)
Reads Environment values
- setup71196246.exe (PID: 1596)
Create files in a temporary directory
- setup71196246.exe (PID: 1596)
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 2304)
Creates files or folders in the user directory
- ValoSploit V3_71196246.exe (PID: 2408)
- setup71196246.exe (PID: 1596)
The process drops C-runtime libraries
- setup71196246.exe (PID: 1596)
Reads product name
- setup71196246.exe (PID: 1596)
Process drops legitimate windows executable
- setup71196246.exe (PID: 1596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:21 20:16:16+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.22 |
| CodeSize: | 4345344 |
| InitializedDataSize: | 5646336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x39649e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Download Manager |
| FileVersion: | 1 |
| InternalName: | Download Manager |
| LegalCopyright: | Download Manager |
| OriginalFileName: | Download Manager |
| ProductName: | Download Manager |
| ProductVersion: | 1 |
Total processes
47
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\AppData\Local\Temp\ValoSploit V3_71196246.exe" | C:\Users\admin\AppData\Local\Temp\ValoSploit V3_71196246.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Download Manager Exit code: 3221226540 Version: 1 Modules
| |||||||||||||||
| 1596 | C:\Users\admin\AppData\Local\setup71196246.exe hhwnd=196904 hreturntoinstaller hextras=id:65d81099910a0e7-TW-pSqeX | C:\Users\admin\AppData\Local\setup71196246.exe | ValoSploit V3_71196246.exe | ||||||||||||
User: admin Company: DT001 Integrity Level: HIGH Description: Software Installation Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2304 | C:\Users\admin\AppData\Local\setup71196246.exe hready | C:\Users\admin\AppData\Local\setup71196246.exe | — | ValoSploit V3_71196246.exe | |||||||||||
User: admin Company: DT001 Integrity Level: HIGH Description: Software Installation Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\AppData\Local\Temp\ValoSploit V3_71196246.exe" | C:\Users\admin\AppData\Local\Temp\ValoSploit V3_71196246.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Download Manager Exit code: 0 Version: 1 Modules
| |||||||||||||||
| 2572 | tasklist /FI "PID eq 1596" /fo csv | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2584 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | find /I "1596" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\System32\notepad.exe | — | ValoSploit V3_71196246.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\H2OCleanup.bat"" | C:\Windows\System32\cmd.exe | — | setup71196246.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
17 550
Read events
17 447
Write events
103
Delete events
0
Modification events
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2408) ValoSploit V3_71196246.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1596) setup71196246.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | |||
Executable files
23
Suspicious files
18
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | ValoSploit V3_71196246.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D6B9B96066529CA4A2FCE19C18A34EBB | SHA256:90A528279A47408466EB4B8E287D1B762869EB3ED184D63E3C4DF098C6F9453C | |||
| 2408 | ValoSploit V3_71196246.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:037AE8164352CA91E80AD33054D1906D | SHA256:07C018EB07002663D5248DAA8A65EAF587955E3DB45735E7E3AC9CB13D7D664E | |||
| 2408 | ValoSploit V3_71196246.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2408 | ValoSploit V3_71196246.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:7FB8D915032BD30ADAB5F30E0F0B44D9 | SHA256:6DC8D24A83CCD5FB7250AC3D5B358706824EB17FCCB6E7751287D00C462B508B | |||
| 1596 | setup71196246.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\vcruntime140.dll | executable | |
MD5:1A84957B6E681FCA057160CD04E26B27 | SHA256:9FAEAA45E8CC986AF56F28350B38238B03C01C355E9564B849604B8D690919C5 | |||
| 2408 | ValoSploit V3_71196246.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\869CC3B84BEE922ABCE8CDCAA964F3D9_6F32A0985879EB33E63263938C358721 | der | |
MD5:E93E0A22E2DFD34BF4F2D2D7912BBA91 | SHA256:7600C7BEAE6444D8C6ED82D9227047F7D67C2B95995AA49847C18445F777997B | |||
| 1596 | setup71196246.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\ServiceHide.dll | executable | |
MD5:72990C7E32EE6C811EA3D2EA64523234 | SHA256:E77E0B4F2762F76A3EAAADF5A3138A35EC06ECE80EDC4B3396DE7A601F8DA1B3 | |||
| 1596 | setup71196246.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\H2OServices.dll | executable | |
MD5:6DF226BDA27D26CE4523B80DBF57A9EA | SHA256:17D737175D50EEE97AC1C77DB415FE25CC3C7A3871B65B93CC3FAD63808A9ABC | |||
| 1596 | setup71196246.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\Ninject.dll | executable | |
MD5:8DB691813A26E7D0F1DB5E2F4D0D05E3 | SHA256:3043A65F11AC204E65BCA142FF4166D85F1B22078B126B806F1FECB2A315C701 | |||
| 1596 | setup71196246.exe | C:\Users\admin\AppData\Local\Temp\ec05d89197b949eb6957b79472e8723d\SciterWrapper.dll | executable | |
MD5:105A9E404F7AC841C46380063CC27F50 | SHA256:69FE749457218EC9A765F9AAC74CAF6D4F73084CF5175D3FD1E4F345AF8B3B8B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
22
DNS requests
16
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2408 | ValoSploit V3_71196246.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4a53176c7d6f234f | unknown | compressed | 4.66 Kb | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?999758feac79a2da | unknown | compressed | 65.2 Kb | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ea9f9887970ec6ef | unknown | compressed | 65.2 Kb | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/s/gts1d4/BLyg_-h63RA/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEACRI2vGqzWlEof0zfA2Du0%3D | unknown | binary | 471 b | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/s/gts1d4/tPVfSrt3g1k/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQDASJ2qLaCI5xAFjJiGxx93 | unknown | binary | 472 b | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 184.24.77.205:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9ffb40419a294727 | unknown | compressed | 65.2 Kb | unknown |
2408 | ValoSploit V3_71196246.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2408 | ValoSploit V3_71196246.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
2408 | ValoSploit V3_71196246.exe | 184.24.77.205:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2408 | ValoSploit V3_71196246.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1596 | setup71196246.exe | 104.17.9.52:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
1596 | setup71196246.exe | 104.18.67.73:443 | sos.adaware.com | CLOUDFLARENET | — | unknown |
1596 | setup71196246.exe | 104.18.68.73:443 | sos.adaware.com | CLOUDFLARENET | — | unknown |
1596 | setup71196246.exe | 18.245.86.41:443 | anypdf.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dlsft.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| whitelisted |
flow.lavasoft.com |
| whitelisted |
sos.adaware.com |
| whitelisted |
dlsft.com |
| unknown |
sdl.adaware.com |
| whitelisted |
anypdf.com |
| unknown |
package.avira.com |
| unknown |
Threats
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
setup71196246.exe | at sciter:init-script.tis
|
setup71196246.exe | Error: File not found - sciterwrapper:console.tis
|
setup71196246.exe | |
setup71196246.exe | |
setup71196246.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
setup71196246.exe | at sciter:init-script.tis
|
setup71196246.exe | Error: File not found - sciterwrapper:console.tis
|
setup71196246.exe | |
setup71196246.exe | |
setup71196246.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|