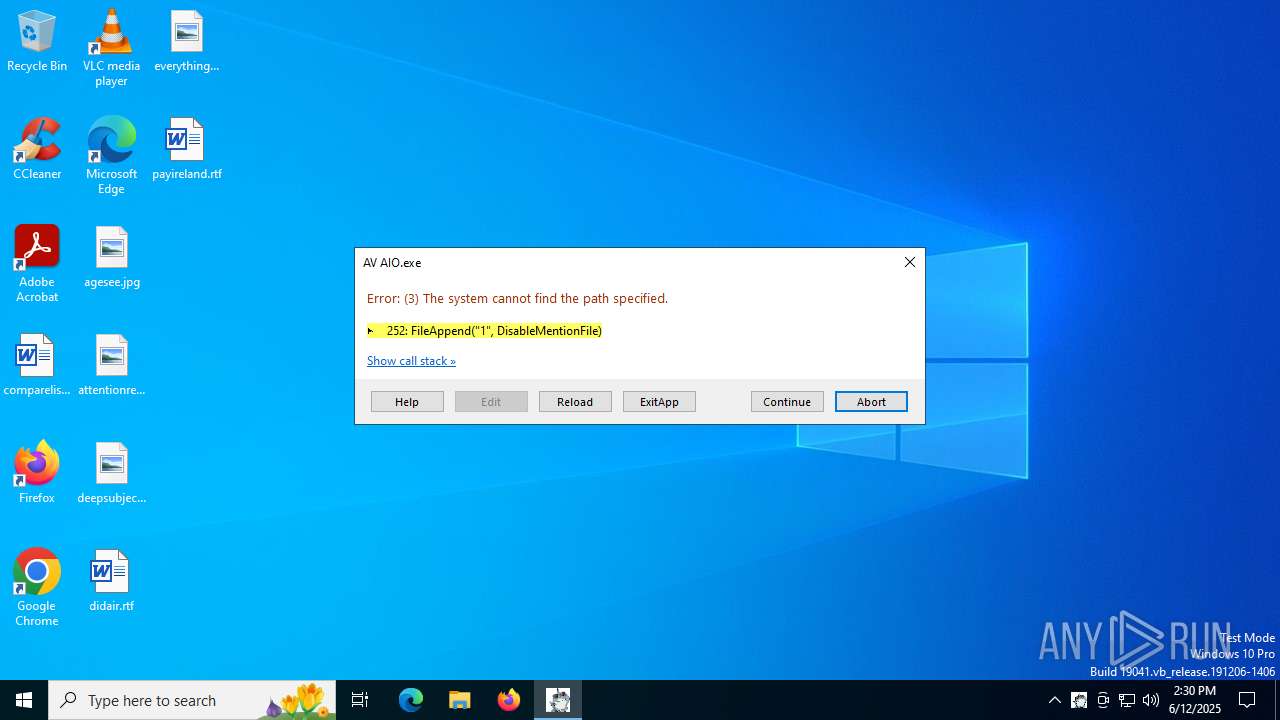
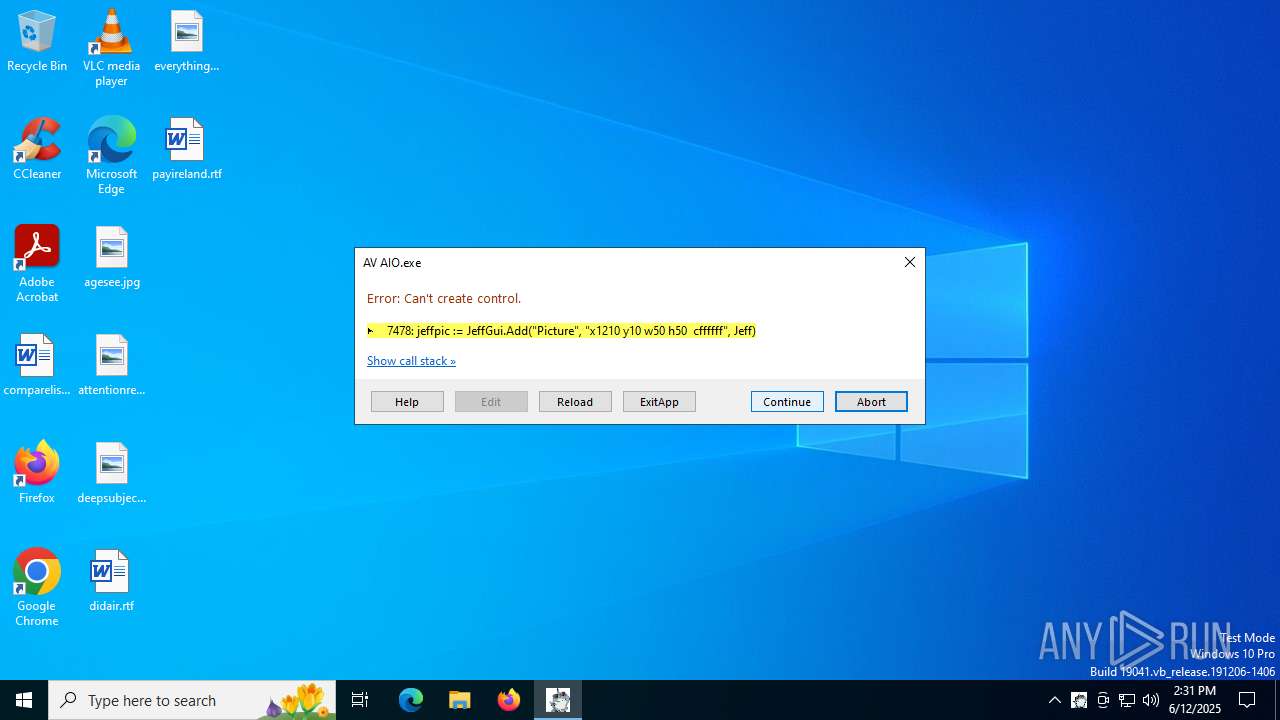
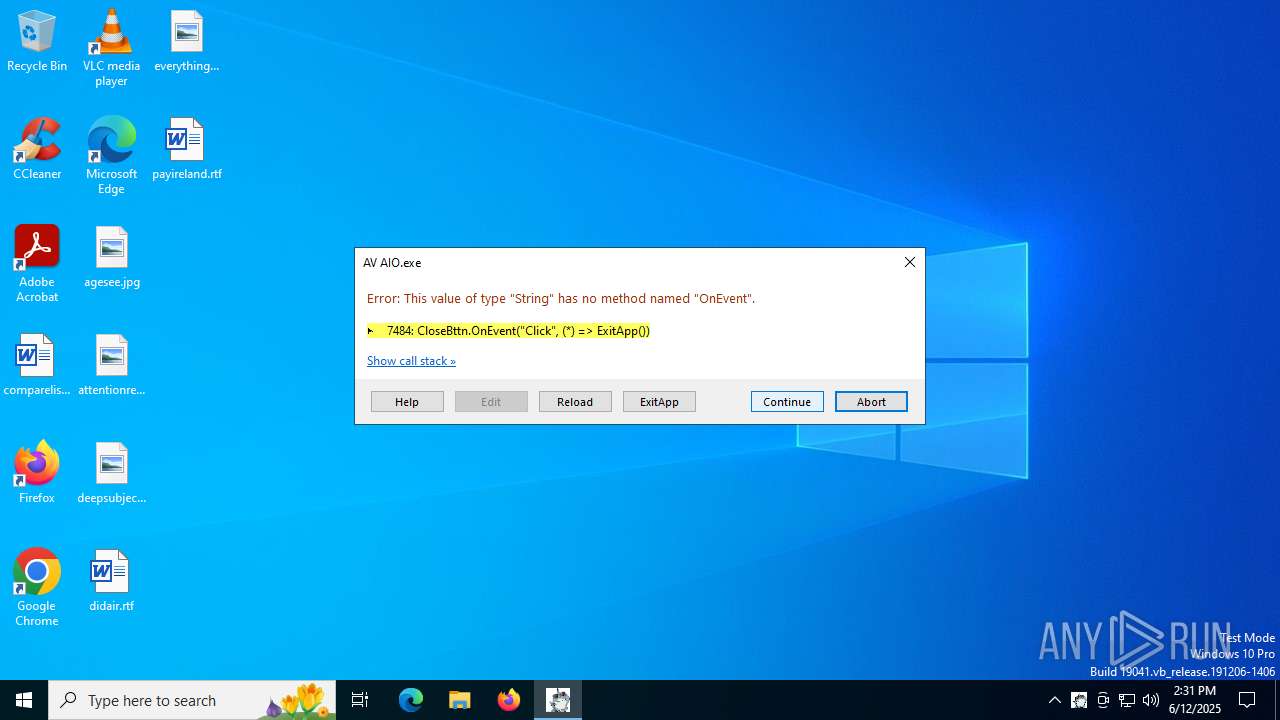
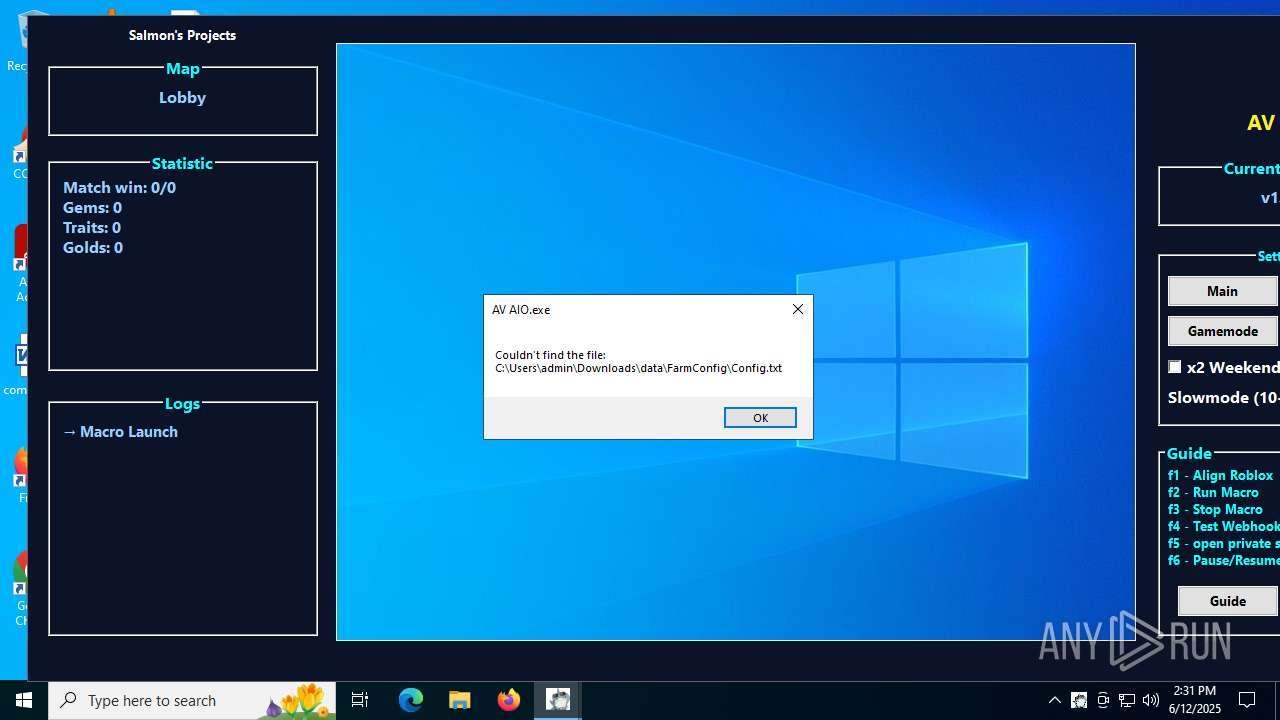
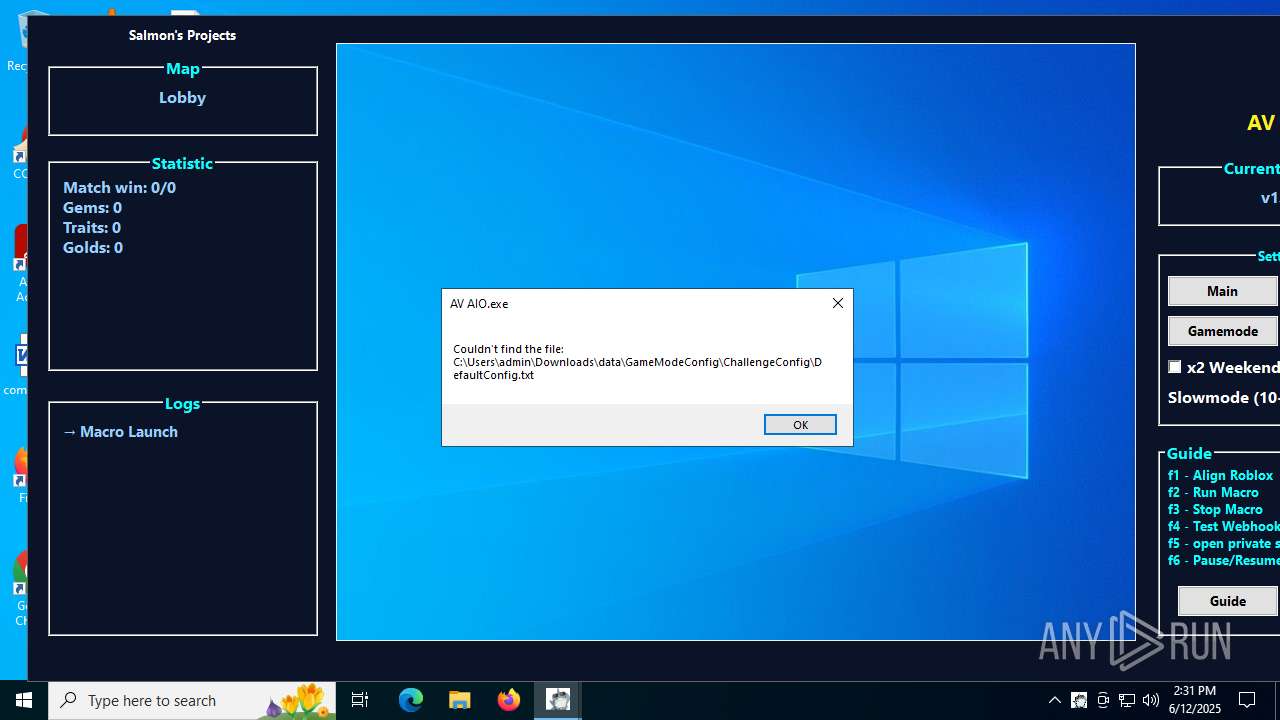
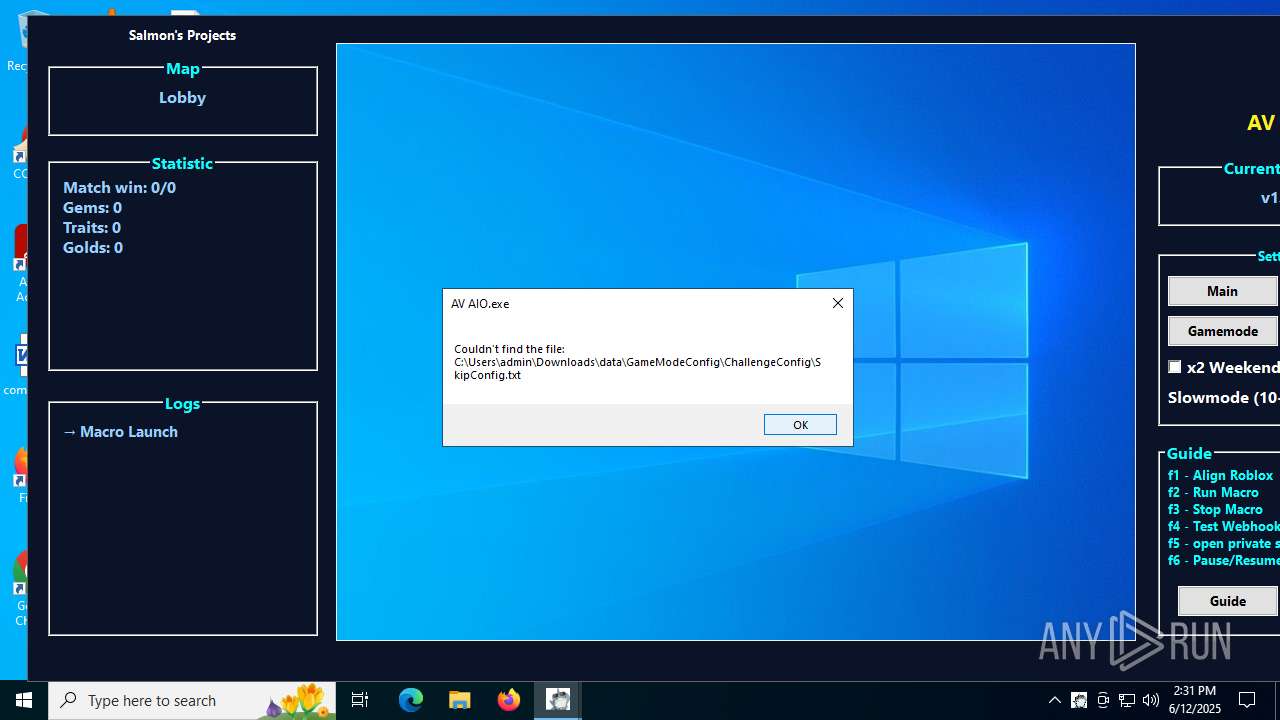
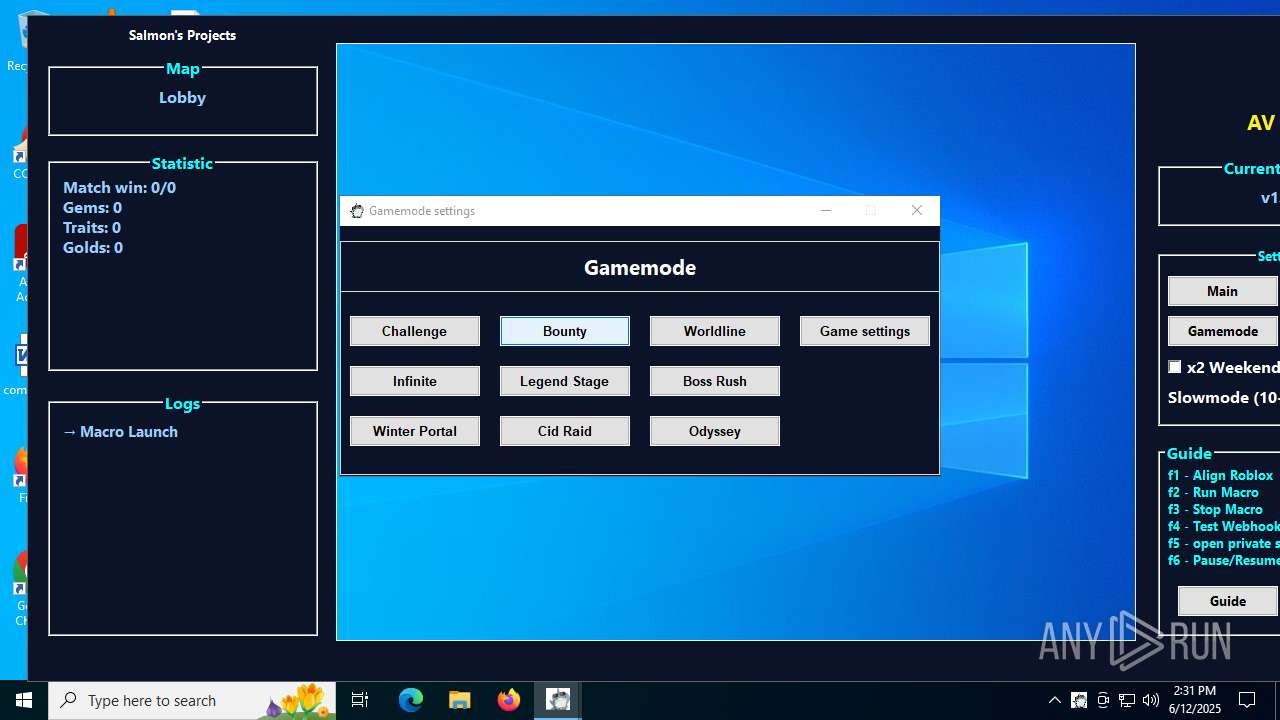
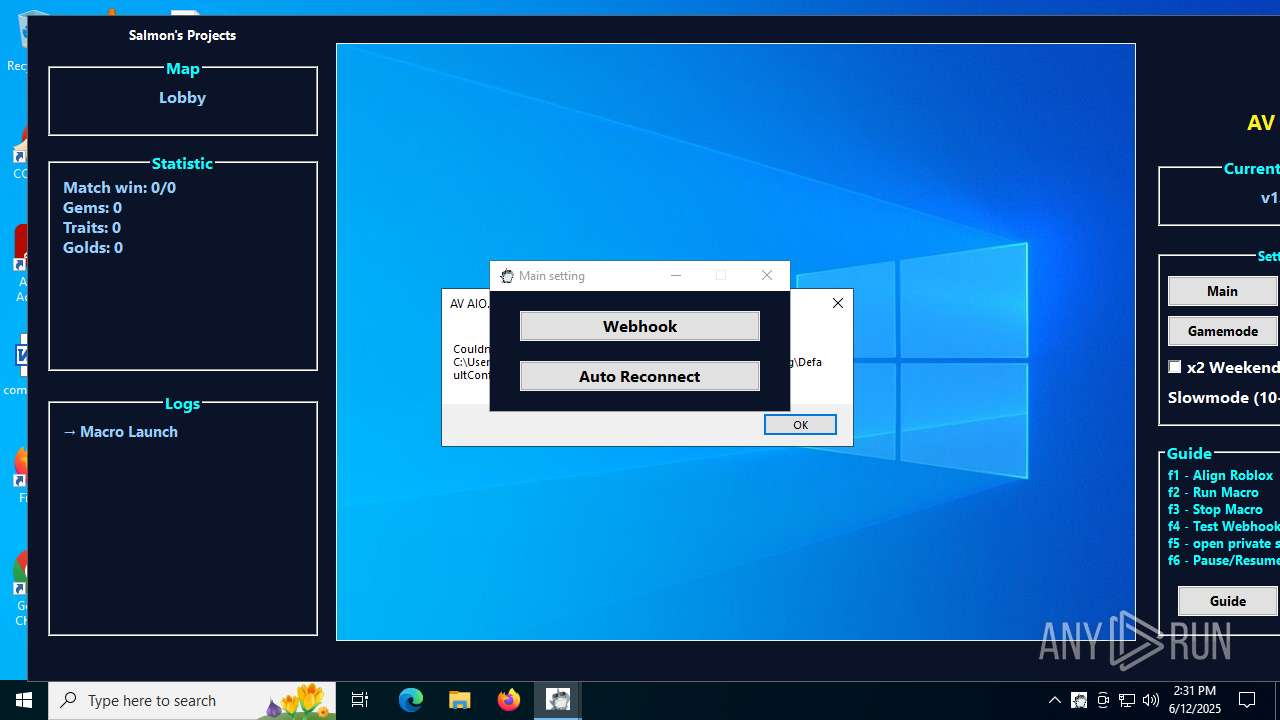
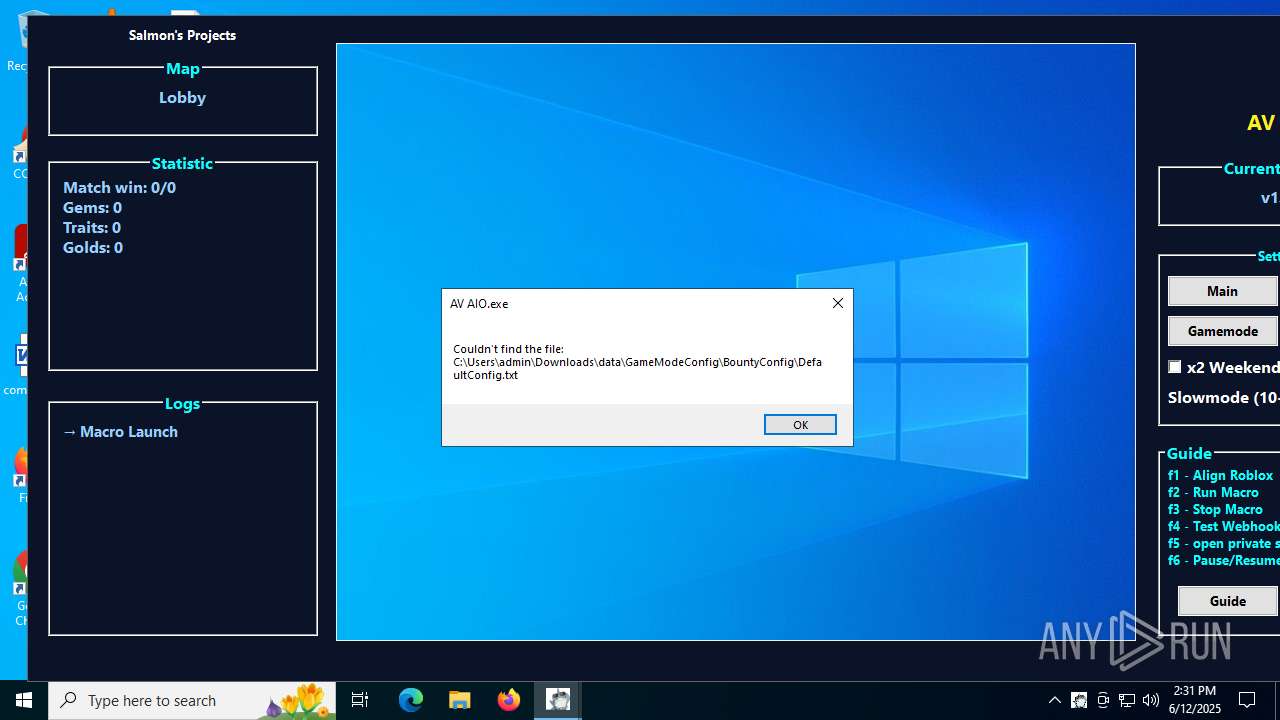
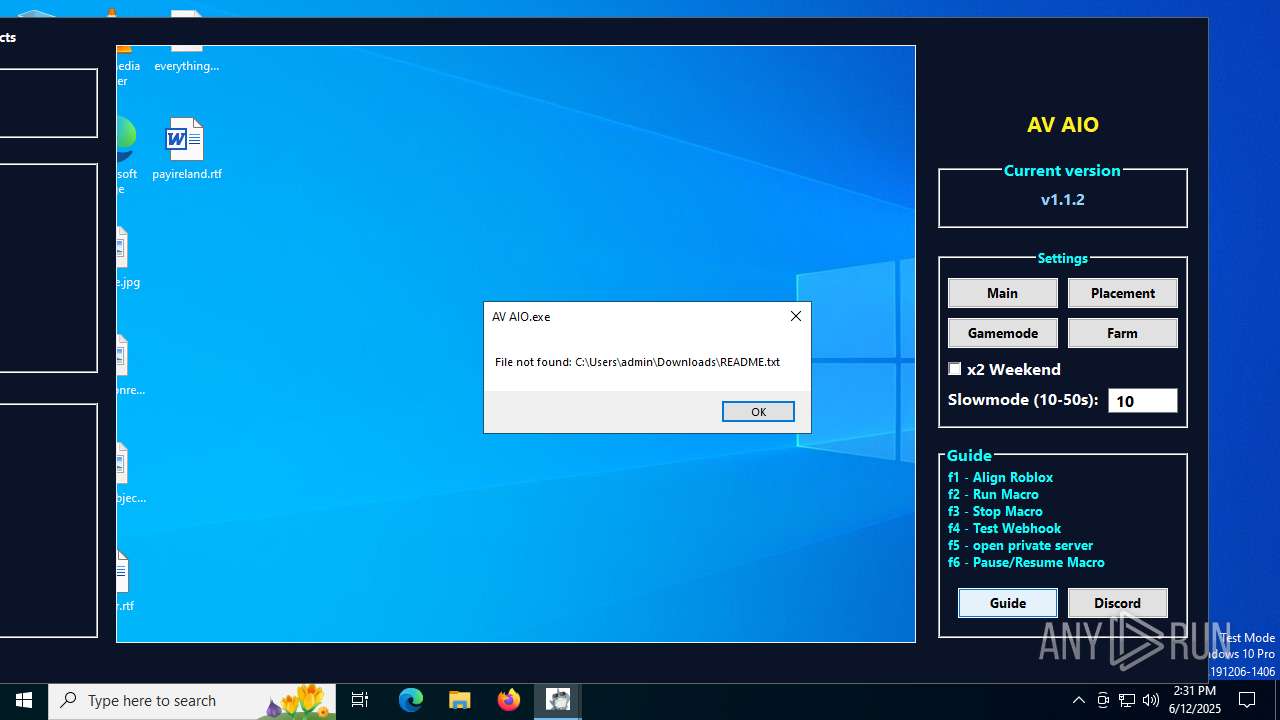
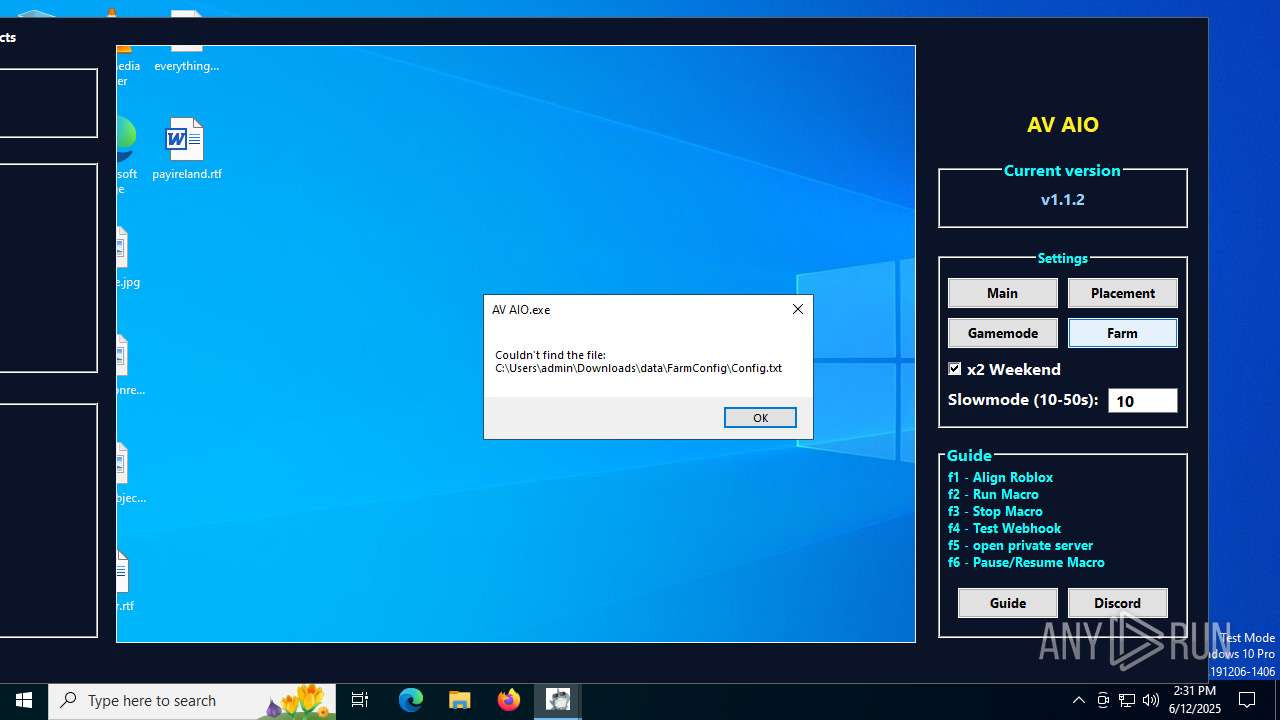
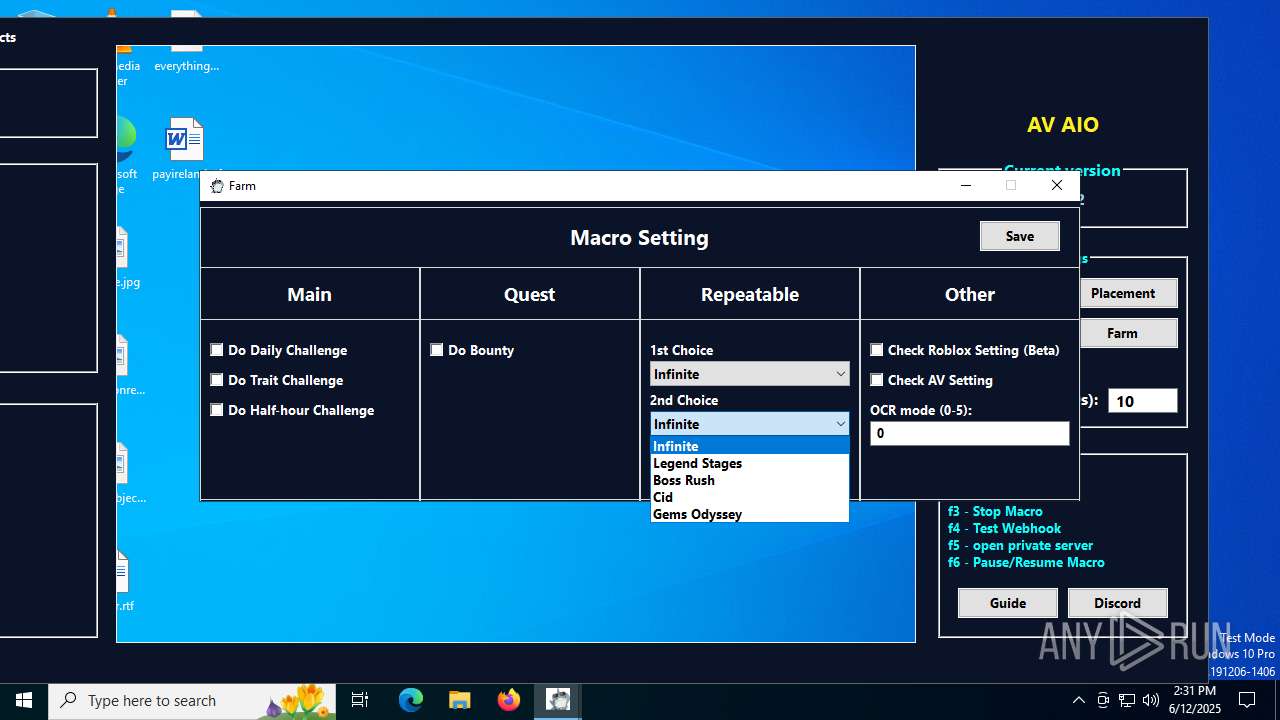
| File name: | AV AIO.exe |
| Full analysis: | https://app.any.run/tasks/7734b188-58c2-4326-bec9-8c8bbc1e7ddc |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2025, 14:30:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 8278B02ECC74DEF56C75932752FC67FB |
| SHA1: | 6062AFD4063B90C5624FD26BA18F63569FC50569 |
| SHA256: | BE4DE8F0A206B36712511A776C89EB75D511658EC10148D1DF8AC0B0BF7F6167 |
| SSDEEP: | 98304:Z+j5/m8J1F0CJ4zW8xjtXUifzOKOMJ7J5q9kb4X2JEnyxNbgAw/:Uh |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- AV AIO.exe (PID: 1208)
Possible usage of Discord/Telegram API has been detected (YARA)
- AV AIO.exe (PID: 1208)
INFO
Detects AutoHotkey samples (YARA)
- AV AIO.exe (PID: 1208)
Checks supported languages
- AV AIO.exe (PID: 1208)
The sample compiled with english language support
- AV AIO.exe (PID: 1208)
Reads the software policy settings
- AV AIO.exe (PID: 1208)
Found Base64 encoded reference to WMI classes (YARA)
- AV AIO.exe (PID: 1208)
Reads the computer name
- AV AIO.exe (PID: 1208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:06 08:24:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.39 |
| CodeSize: | 929280 |
| InitializedDataSize: | 1055232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x17a9a0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.18.0 |
| ProductVersionNumber: | 2.0.18.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 2.0.18 |
| ProductVersion: | 2.0.18 |
Total processes
137
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1208 | "C:\Users\admin\Downloads\AV AIO.exe" | C:\Users\admin\Downloads\AV AIO.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 2.0.18 Modules
| |||||||||||||||
| 2952 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
736
Read events
736
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
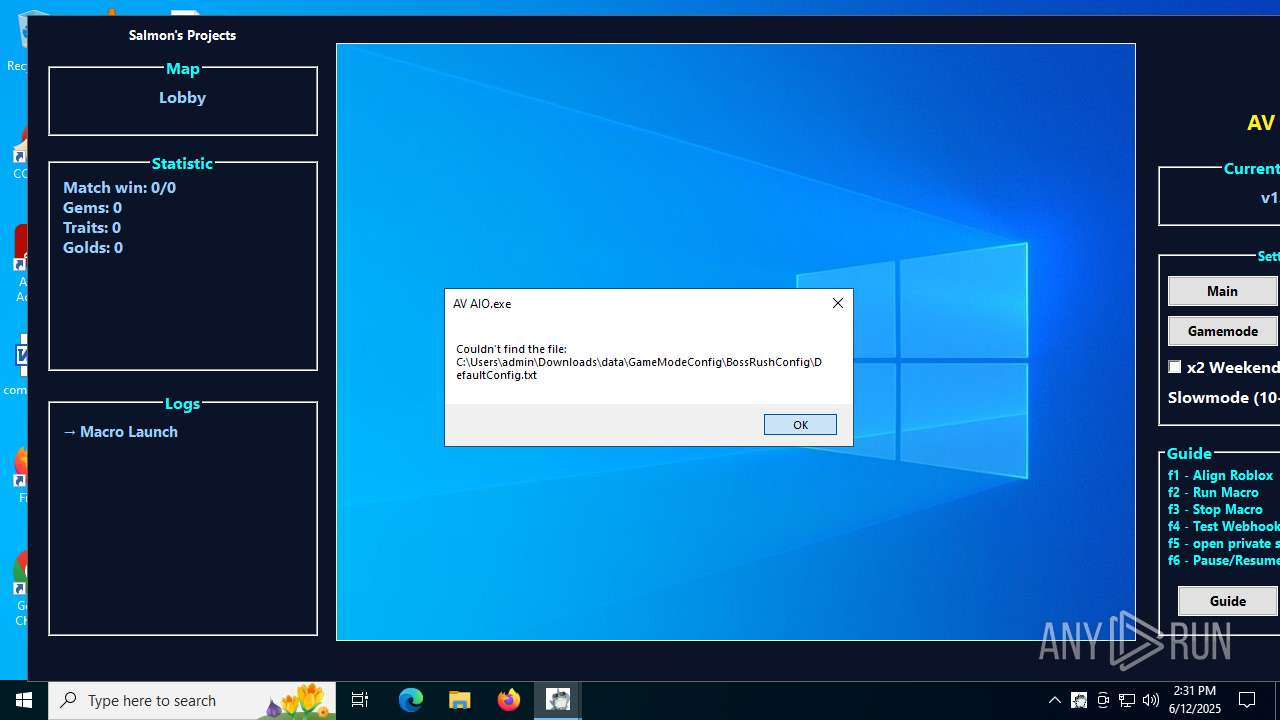
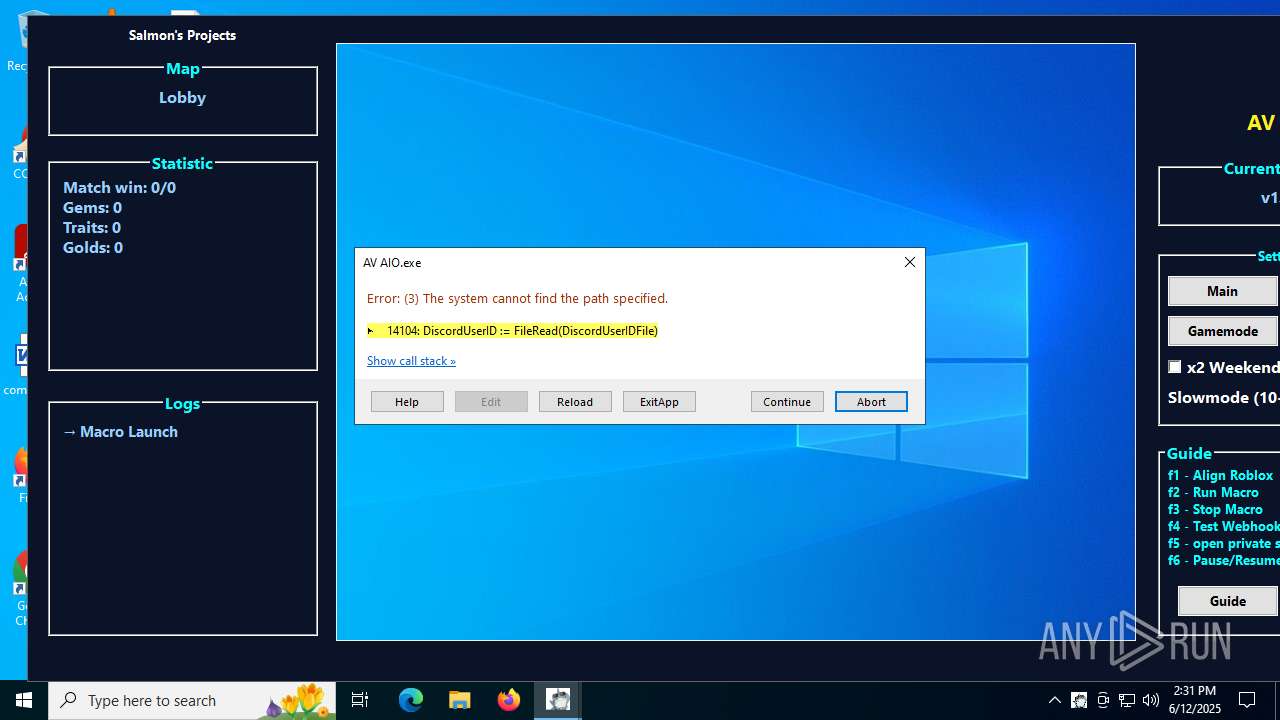
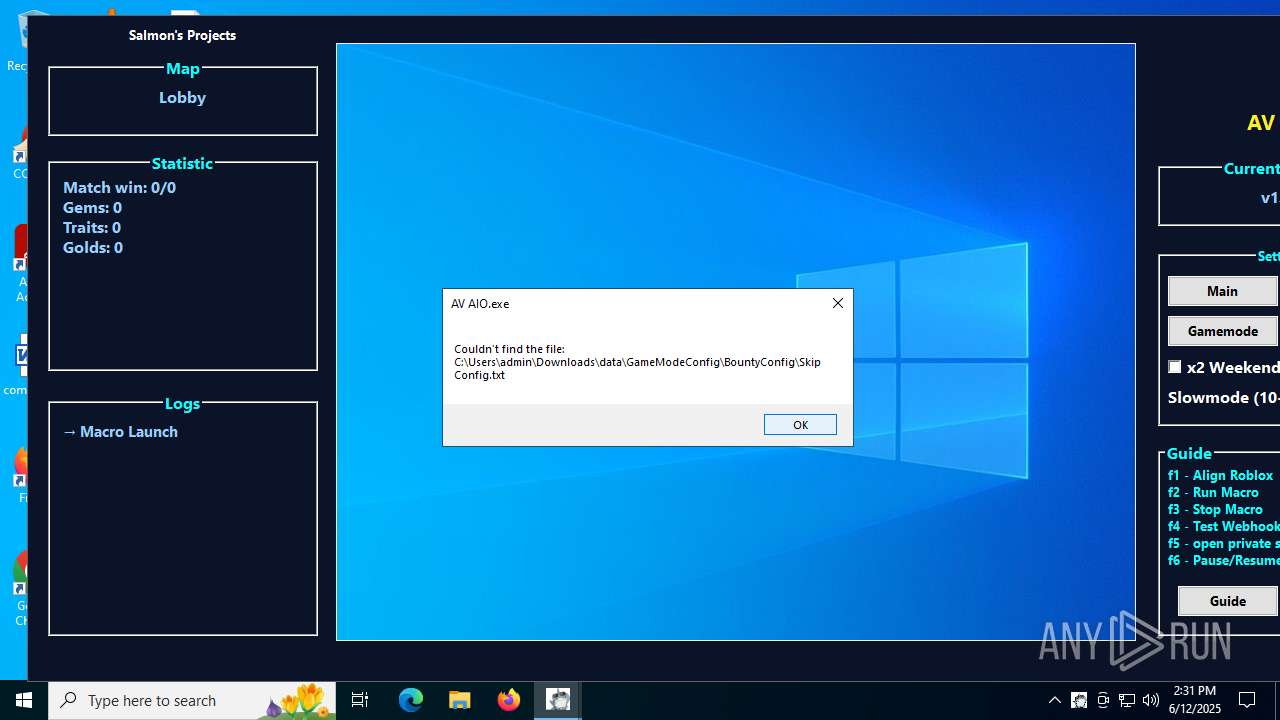
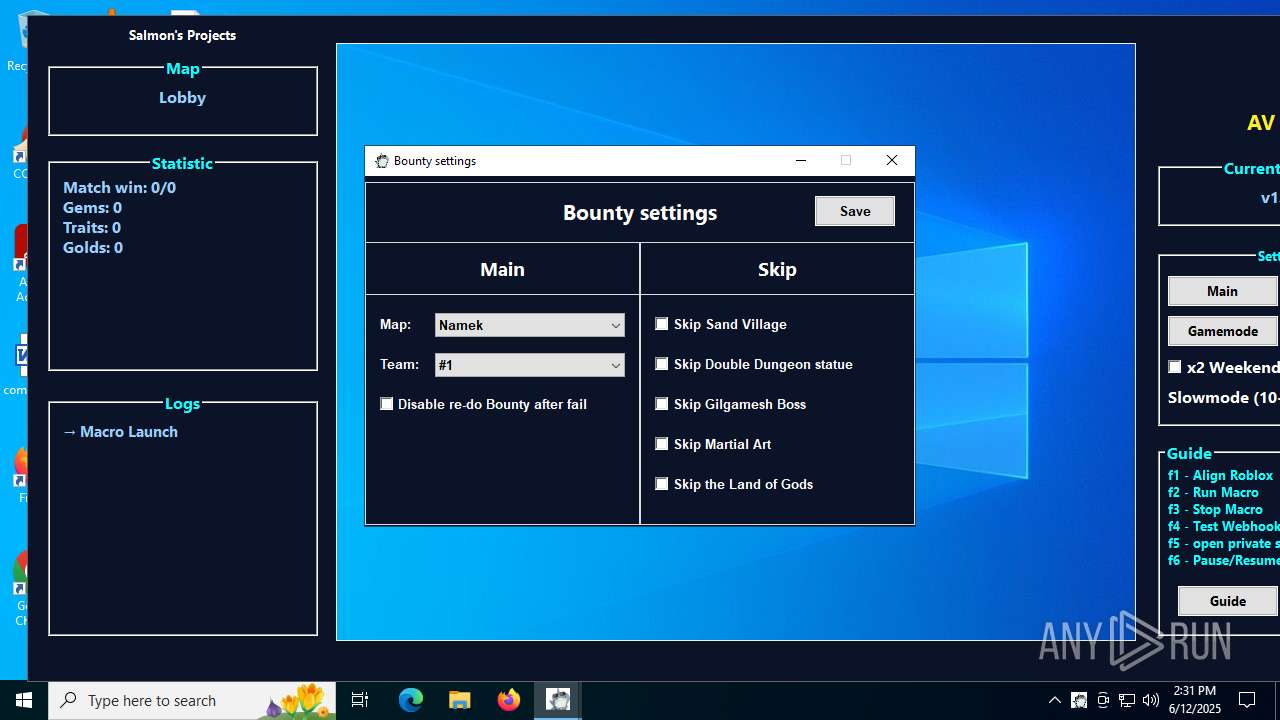
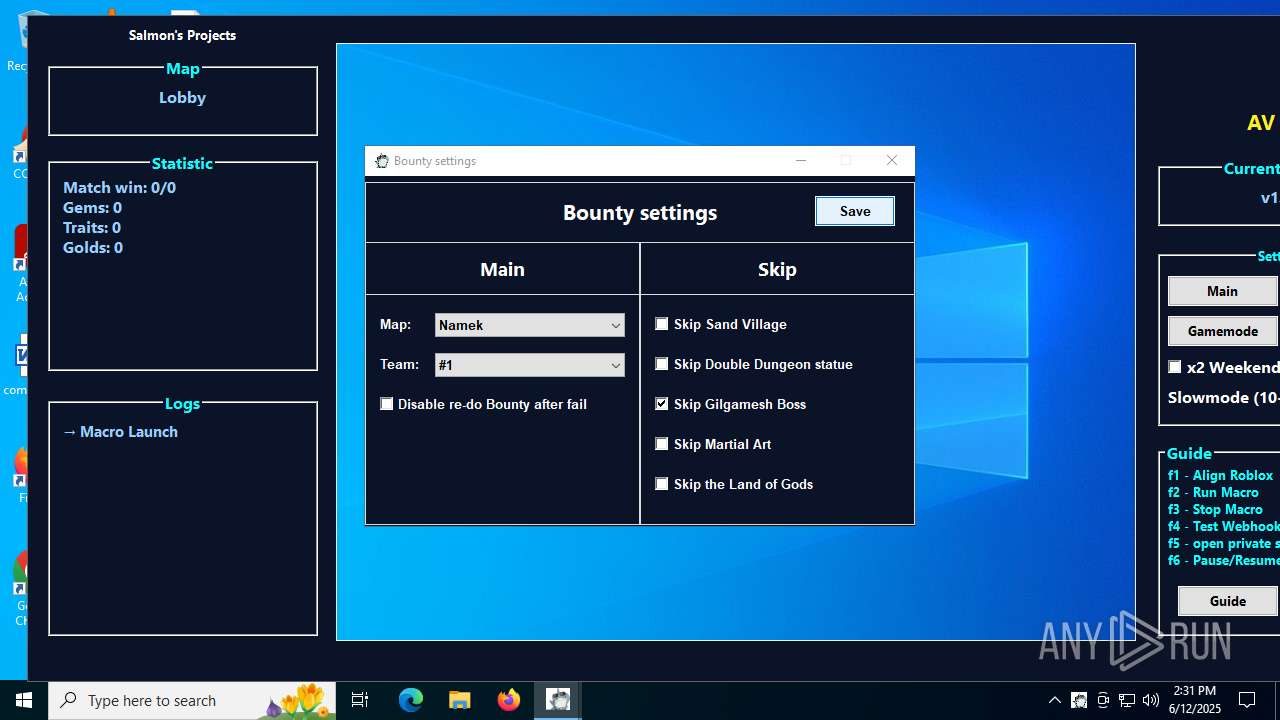
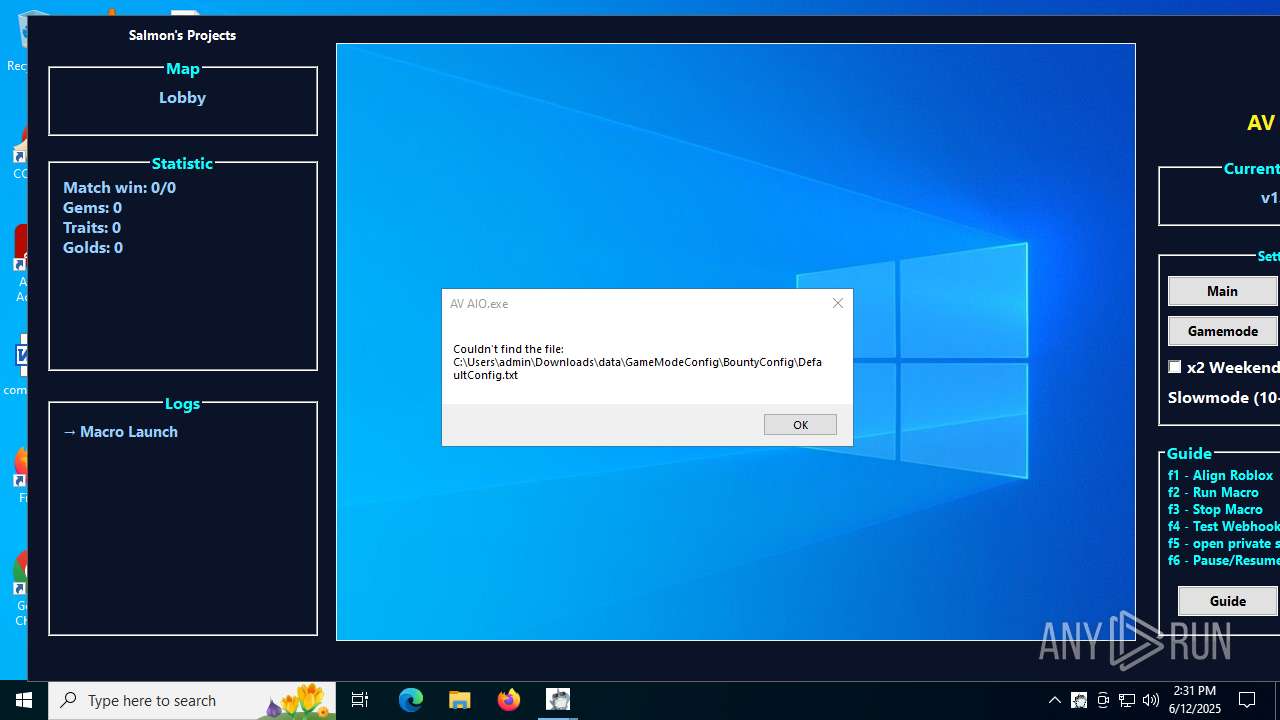
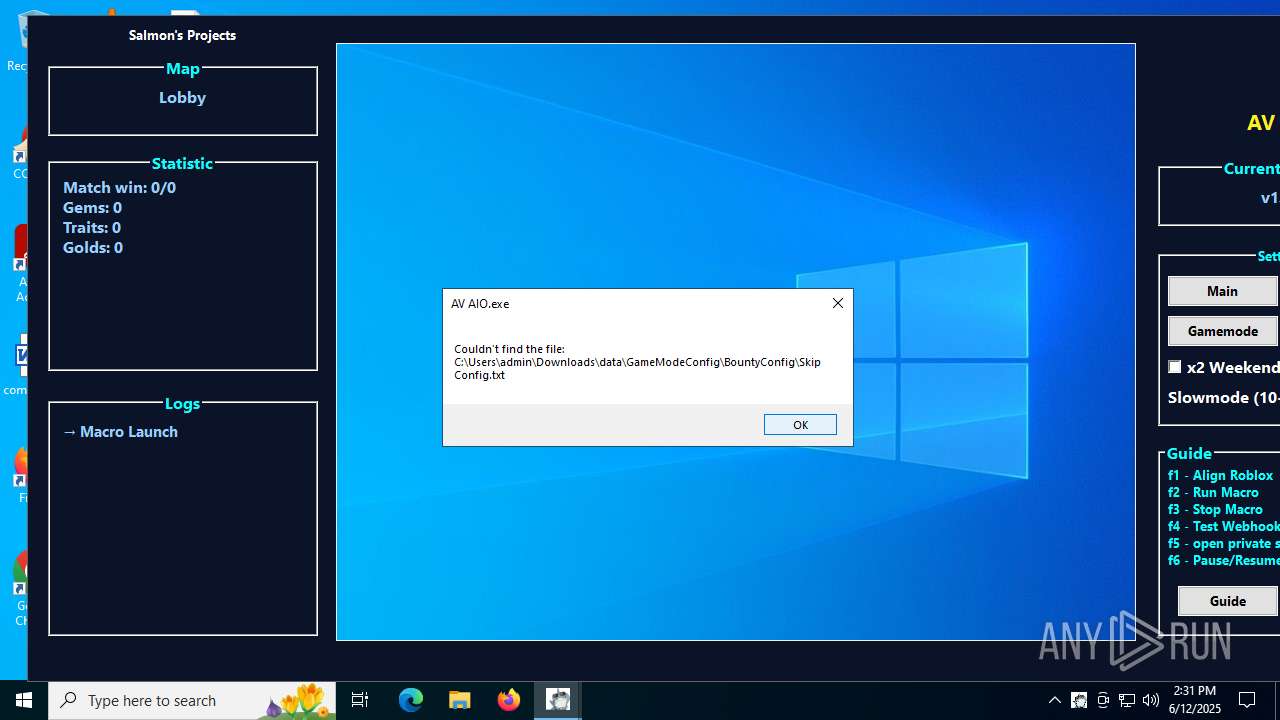
| 1208 | AV AIO.exe | C:\Users\admin\Downloads\data\GameModeConfig\GameConfig\DefaultConfig.txt | text | |
MD5:7651BB5183D11A5E7247BD8FAF5FB021 | SHA256:210D051FE04CDE3B30CCDF158727B46E28AF08B2D6F1377688CA96E55EFA61DC | |||
| 1208 | AV AIO.exe | C:\Users\admin\Downloads\data\GameModeConfig\WorldlineConfig\DefaultConfig.txt | text | |
MD5:3F2AE71F1F9E4705F82FC41D9A9DC03B | SHA256:90AD1E651F562198BA33089FE619A31F87B5F096A98FE9E10345F5E2D973C257 | |||
| 1208 | AV AIO.exe | C:\Users\admin\Downloads\data\GameModeConfig\GameConfig\time.txt | text | |
MD5:85241D52D2758C30CAB7FF6B84E995DE | SHA256:DA3173B4C02C24B4C3B37A2A15570E006DCFEA26F8E190AC76E9663BD7575A98 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5528 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5468 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5468 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1564 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1208 | AV AIO.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5528 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5528 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.github.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |