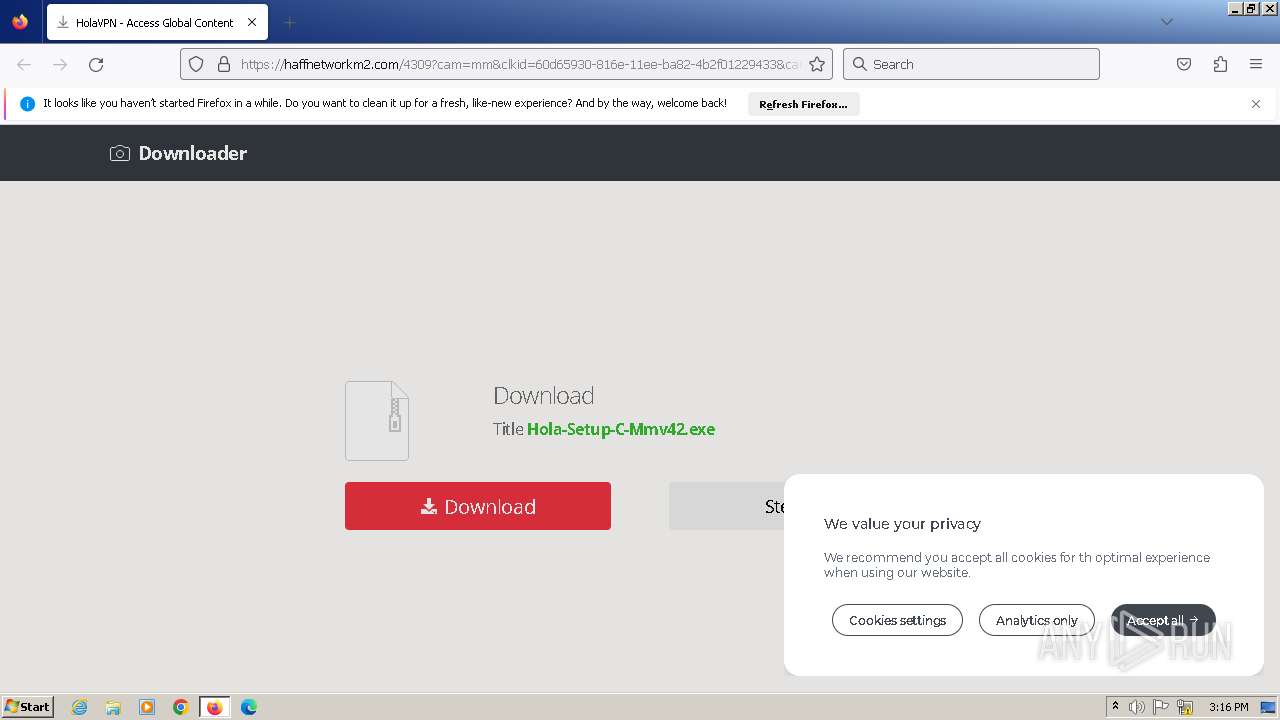
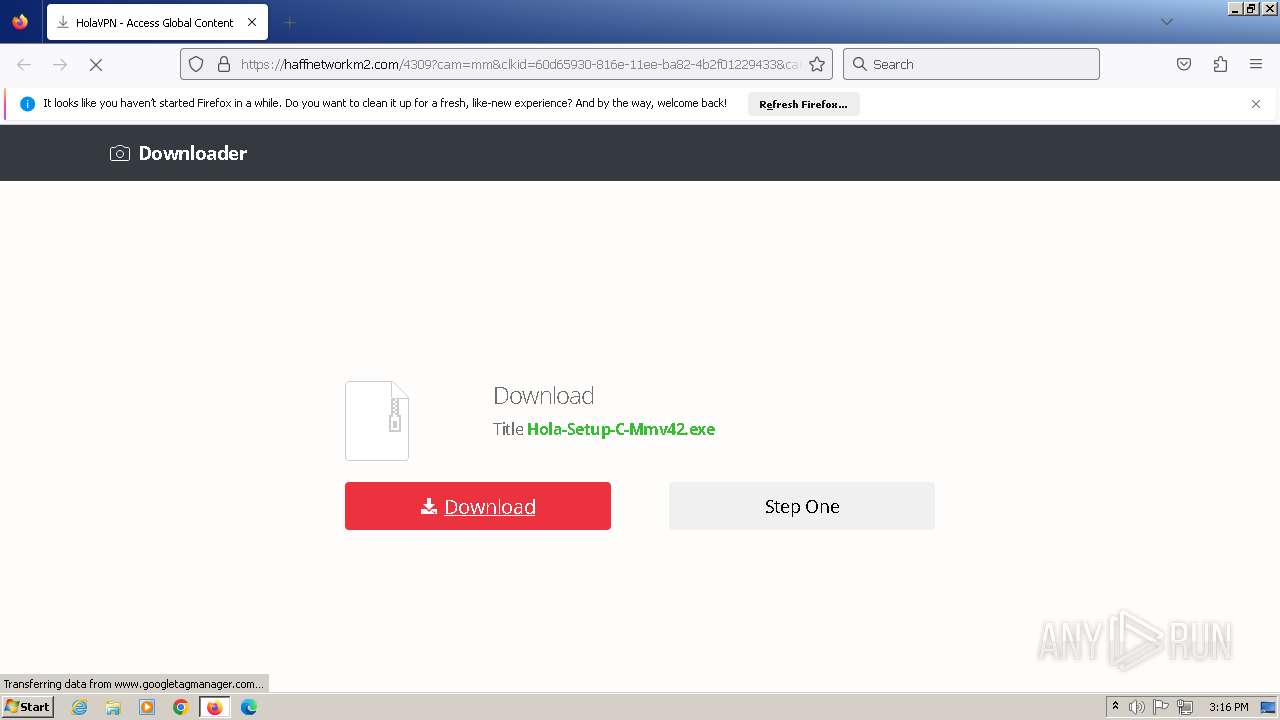
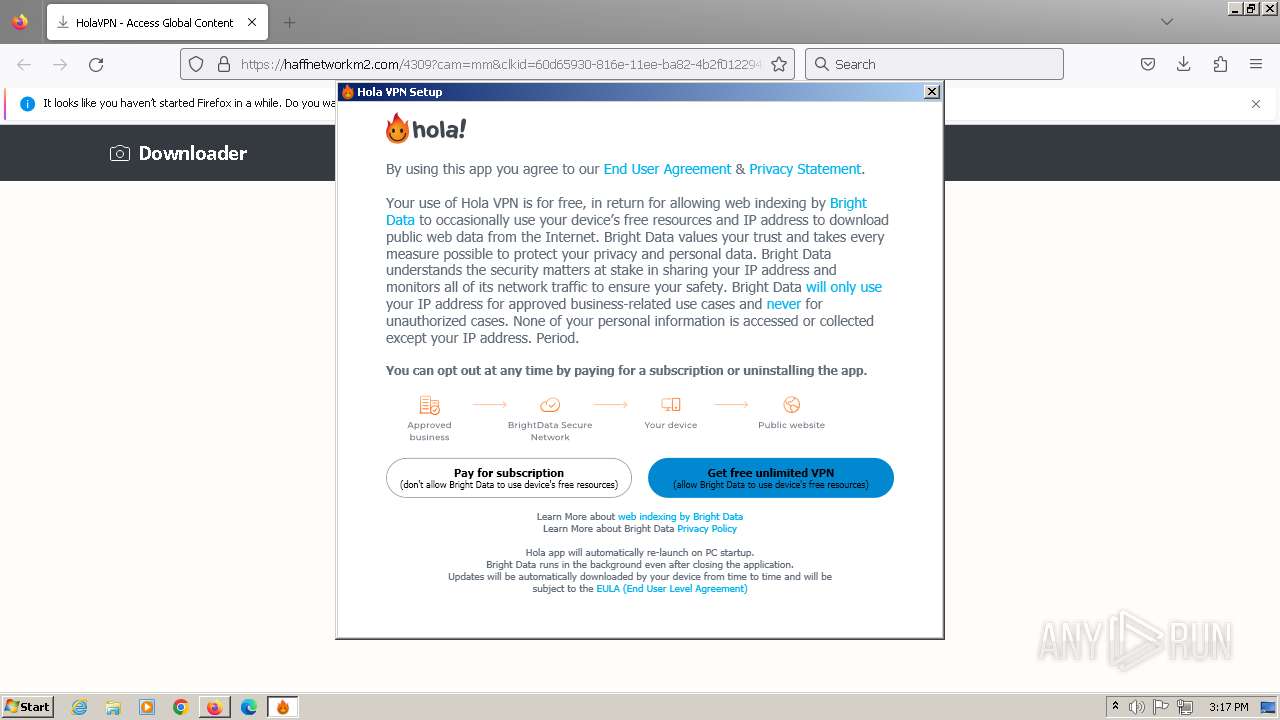
| URL: | https://haffnetworkm2.com/4309?cam=mm&clkid=60d65930-816e-11ee-ba82-4b2f01229433&cam_id=5398_6058394&site= |
| Full analysis: | https://app.any.run/tasks/409e99ea-d8e4-498a-b3d1-f953ac97e785 |
| Verdict: | Malicious activity |
| Analysis date: | November 12, 2023, 15:16:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| SHA1: | 14CC6AED34C1317B982A266534CCED6CD3992340 |
| SHA256: | BE2A3B5EFC67BB55F41A4C7AE9FA25655EE311BB6747D529F8B0A79DBD276902 |
| SSDEEP: | 3:N84A5STKZIGAMuZBC/nXQWWaEHq6TVQ19:246WKmGAZ8nXQRaEhTVQD |
MALICIOUS
Drops the executable file immediately after the start
- Hola-Setup-C-Mmv42.exe (PID: 3464)
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- net_updater64.exe (PID: 124)
- 7zr.exe (PID: 3376)
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
Creates a writable file the system directory
- net_updater64.exe (PID: 544)
Actions looks like stealing of personal data
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
- hola.exe (PID: 3784)
- hola_svc.exe (PID: 2436)
- hola_cr.exe (PID: 648)
- hola_cr.exe (PID: 124)
- hola_cr.exe (PID: 2648)
- hola_cr.exe (PID: 3368)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 1632)
- hola_cr.exe (PID: 3720)
- hola_cr.exe (PID: 1652)
- hola_cr.exe (PID: 2420)
- hola_cr.exe (PID: 2996)
- hola_cr.exe (PID: 4048)
- hola_cr.exe (PID: 3580)
- hola_cr.exe (PID: 944)
- 7zr.exe (PID: 3376)
- hola_cr.exe (PID: 3640)
SUSPICIOUS
Reads settings of System Certificates
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 3064)
- hola_cr.exe (PID: 3064)
Reads security settings of Internet Explorer
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 3064)
Reads the Internet Settings
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- hola_cr.exe (PID: 3064)
Application launched itself
- Hola-Setup-Core.exe (PID: 3496)
- hola_svc.exe (PID: 2436)
- hola_cr.exe (PID: 3064)
Adds/modifies Windows certificates
- Hola-Setup-C-Mmv42.exe (PID: 3464)
Checks Windows Trust Settings
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- net_updater64.exe (PID: 124)
Executes as Windows Service
- PresentationFontCache.exe (PID: 3660)
- net_updater64.exe (PID: 544)
- hola_svc.exe (PID: 2436)
Drops 7-zip archiver for unpacking
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
Drops a system driver (possible attempt to evade defenses)
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
Process drops legitimate windows executable
- net_updater64.exe (PID: 3964)
- 7zr.exe (PID: 3376)
The process drops C-runtime libraries
- net_updater64.exe (PID: 3964)
Detected use of alternative data streams (AltDS)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- net_updater64.exe (PID: 124)
Connects to unusual port
- hola_svc.exe (PID: 2436)
Process requests binary or script from the Internet
- hola.exe (PID: 3784)
INFO
Checks supported languages
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-C-Mmv42.exe (PID: 3464)
- Hola-Setup-Core.exe (PID: 3576)
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
- PresentationFontCache.exe (PID: 3660)
- net_updater64.exe (PID: 3964)
- test_wpf.exe (PID: 4004)
- net_updater64.exe (PID: 544)
- test_wpf.exe (PID: 3420)
- test_wpf.exe (PID: 3440)
- net_updater64.exe (PID: 3064)
- hola_svc.exe (PID: 2436)
- idle_report.exe (PID: 3856)
- net_updater64.exe (PID: 124)
- test_wpf.exe (PID: 2200)
- hola_svc.exe (PID: 1984)
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
- 7zr.exe (PID: 3376)
- Hola-Setup-x64-1.217.339.exe (PID: 4076)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 648)
- hola.exe (PID: 3784)
- hola_cr.exe (PID: 2996)
- hola_cr.exe (PID: 124)
- hola_cr.exe (PID: 3368)
- hola_cr.exe (PID: 4048)
- hola_cr.exe (PID: 3720)
- hola_cr.exe (PID: 3580)
- hola_cr.exe (PID: 1652)
- hola_cr.exe (PID: 944)
- hola_cr.exe (PID: 2420)
- hola_cr.exe (PID: 1632)
- hola_cr.exe (PID: 2648)
- hola_cr.exe (PID: 3640)
The process uses the downloaded file
- firefox.exe (PID: 2700)
Application launched itself
- firefox.exe (PID: 2700)
Reads the computer name
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- PresentationFontCache.exe (PID: 3660)
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
- net_updater64.exe (PID: 3964)
- test_wpf.exe (PID: 4004)
- net_updater64.exe (PID: 544)
- test_wpf.exe (PID: 3420)
- net_updater64.exe (PID: 3064)
- test_wpf.exe (PID: 3440)
- hola_svc.exe (PID: 2436)
- net_updater64.exe (PID: 124)
- idle_report.exe (PID: 3856)
- test_wpf.exe (PID: 2200)
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
- 7zr.exe (PID: 3376)
- Hola-Setup-x64-1.217.339.exe (PID: 4076)
- hola.exe (PID: 3784)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 2996)
- hola_cr.exe (PID: 4048)
- hola_cr.exe (PID: 3640)
Reads the machine GUID from the registry
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- PresentationFontCache.exe (PID: 3660)
- net_updater64.exe (PID: 3964)
- test_wpf.exe (PID: 4004)
- net_updater64.exe (PID: 544)
- test_wpf.exe (PID: 3420)
- net_updater64.exe (PID: 3064)
- test_wpf.exe (PID: 3440)
- net_updater64.exe (PID: 124)
- idle_report.exe (PID: 3856)
- hola_svc.exe (PID: 2436)
- test_wpf.exe (PID: 2200)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 3640)
Create files in a temporary directory
- Hola-Setup-C-Mmv42.exe (PID: 3464)
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
- Hola-Setup-x64-1.217.339.exe (PID: 4076)
- hola_cr.exe (PID: 3064)
Reads Environment values
- Hola-Setup-Core.exe (PID: 3496)
- Hola-Setup-Core.exe (PID: 3576)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- net_updater64.exe (PID: 124)
Creates files or folders in the user directory
- Hola-Setup-Core.exe (PID: 3496)
- net_updater64.exe (PID: 3964)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 2996)
Drops the executable file immediately after the start
- firefox.exe (PID: 2700)
Creates files in the program directory
- Hola-Setup-x64-1.217.339.exe (PID: 3920)
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- hola_svc.exe (PID: 2436)
- net_updater64.exe (PID: 124)
- 7zr.exe (PID: 3376)
- Hola-Setup-x64-1.217.339.exe (PID: 4004)
- Hola-Setup-x64-1.217.339.exe (PID: 4076)
- hola.exe (PID: 3784)
Process checks computer location settings
- net_updater64.exe (PID: 3964)
- net_updater64.exe (PID: 544)
- net_updater64.exe (PID: 3064)
- net_updater64.exe (PID: 124)
- hola_cr.exe (PID: 3064)
- hola_cr.exe (PID: 3720)
- hola_cr.exe (PID: 944)
- hola_cr.exe (PID: 2420)
- hola_cr.exe (PID: 1652)
Reads the Internet Settings
- explorer.exe (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
108
Monitored processes
58
Malicious processes
29
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Hola\app\net_updater64.exe" --uuid | C:\Program Files\Hola\app\net_updater64.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: BrightData Ltd. (certified) Integrity Level: SYSTEM Description: BrightData service allows free use of certain features in an app you installed Exit code: 0 Version: 1.418.267 Modules
| |||||||||||||||
| 124 | "C:\Program Files\Hola\app\chromium\hola_cr.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-GB --service-sandbox-type=service --user-data-dir="C:\\Users\\admin\\AppData\\Roaming\\Hola\\chromium_profile" --mojo-platform-channel-handle=1564 --field-trial-handle=1228,i,8783256162927311156,13509082375797555229,131072 /prefetch:8 | C:\Program Files\Hola\app\chromium\hola_cr.exe | hola_cr.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: LOW Description: Hola Browser Exit code: 0 Version: 109.0.5414.74 Modules
| |||||||||||||||
| 544 | "C:/Program Files/Hola/app/net_updater64.exe" --updater win_hola.org | C:\Program Files\Hola\app\net_updater64.exe | services.exe | ||||||||||||
User: SYSTEM Company: BrightData Ltd. (certified) Integrity Level: SYSTEM Description: BrightData service allows free use of certain features in an app you installed Exit code: 0 Version: 1.418.267 Modules
| |||||||||||||||
| 648 | "C:\Program Files\Hola\app\chromium\hola_cr.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Roaming\Hola\chromium_profile /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Roaming\Hola\chromium_profile\Crashpad --annotation=plat=Win32 "--annotation=prod=Hola Browser" --annotation=ver=109.0.5414.74 --initial-client-data=0xec,0xf0,0xf4,0xc0,0xf8,0x745bd9f0,0x745bda00,0x745bda0c | C:\Program Files\Hola\app\chromium\hola_cr.exe | hola_cr.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: MEDIUM Description: Hola Browser Exit code: 0 Version: 109.0.5414.74 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Hola\app\chromium\hola_cr.exe" --type=renderer --user-data-dir="C:\\Users\\admin\\AppData\\Roaming\\Hola\\chromium_profile" --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-GB --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=3180 --field-trial-handle=1228,i,8783256162927311156,13509082375797555229,131072 /prefetch:1 | C:\Program Files\Hola\app\chromium\hola_cr.exe | hola_cr.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: LOW Description: Hola Browser Exit code: 0 Version: 109.0.5414.74 Modules
| |||||||||||||||
| 1220 | rasdial | C:\Windows\System32\rasdial.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2700.1.1054295105\12232237" -parentBuildID 20230710165010 -prefsHandle 1408 -prefMapHandle 1404 -prefsLen 29857 -prefMapSize 244187 -appDir "C:\Program Files\Mozilla Firefox\browser" - {fad5e577-7212-4de1-a941-da67fce30ed0} 2700 "\\.\pipe\gecko-crash-server-pipe.2700" 1420 f8d4b58 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1632 | "C:\Program Files\Hola\app\chromium\hola_cr.exe" --type=gpu-process --user-data-dir="C:\\Users\\admin\\AppData\\Roaming\\Hola\\chromium_profile" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --mojo-platform-channel-handle=1180 --field-trial-handle=1228,i,8783256162927311156,13509082375797555229,131072 /prefetch:2 | C:\Program Files\Hola\app\chromium\hola_cr.exe | hola_cr.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: LOW Description: Hola Browser Exit code: 0 Version: 109.0.5414.74 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Hola\app\chromium\hola_cr.exe" --type=renderer --user-data-dir="C:\\Users\\admin\\AppData\\Roaming\\Hola\\chromium_profile" --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-GB --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=3160 --field-trial-handle=1228,i,8783256162927311156,13509082375797555229,131072 /prefetch:1 | C:\Program Files\Hola\app\chromium\hola_cr.exe | hola_cr.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: LOW Description: Hola Browser Exit code: 0 Version: 109.0.5414.74 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2700.0.1910655269\1732283839" -parentBuildID 20230710165010 -prefsHandle 1108 -prefMapHandle 1100 -prefsLen 29780 -prefMapSize 244187 -appDir "C:\Program Files\Mozilla Firefox\browser" - {8cd478aa-3ba7-4300-906e-e9e44f37af4f} 2700 "\\.\pipe\gecko-crash-server-pipe.2700" 1180 f8d3358 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
26 310
Read events
26 096
Write events
212
Delete events
2
Modification events
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 0 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: F8B731ACA1C5D901 | |||
| (PID) Process: | (2700) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
40
Suspicious files
787
Text files
87
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2700 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\urlCache-current.bin | binary | |
MD5:4DF9B77C7650AF87B264E535779AE2A4 | SHA256:C57071FCFEF26EE4F08A2029E547848EC015B10045ABAD705195A9F966FEAE58 | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs-1.js | text | |
MD5:142A266DC67A741D85023F01C355804F | SHA256:5A3840F7DB7DB387C632189A6D94A9C3A2B439BBB97AA7022C0E4A93E5644BEA | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs.js | text | |
MD5:142A266DC67A741D85023F01C355804F | SHA256:5A3840F7DB7DB387C632189A6D94A9C3A2B439BBB97AA7022C0E4A93E5644BEA | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2700 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\cache2\entries\6D89348819C8881868053197CA0754F36784BF5F | compressed | |
MD5:9ABA9185DBD7431022B8C234F9C8D72B | SHA256:5094AB566188EA79372E4B6C1FD4C04F501711188BE58E28BBBC708BFB56523D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
741
DNS requests
263
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2700 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
2700 | firefox.exe | POST | 200 | 23.53.40.154:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2700 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | binary | 472 b | unknown |
2700 | firefox.exe | POST | — | 23.53.40.154:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
2700 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | binary | 472 b | unknown |
2700 | firefox.exe | POST | 200 | 65.9.98.16:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | binary | 471 b | unknown |
2700 | firefox.exe | POST | 200 | 23.53.40.154:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2700 | firefox.exe | POST | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
2700 | firefox.exe | POST | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
2700 | firefox.exe | POST | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2700 | firefox.exe | 107.22.193.119:443 | haffnetworkm2.com | AMAZON-AES | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2700 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2700 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
2700 | firefox.exe | 35.168.31.31:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
2700 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | unknown |
2700 | firefox.exe | 23.53.40.154:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2700 | firefox.exe | 142.250.186.74:443 | safebrowsing.googleapis.com | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
haffnetworkm2.com |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
544 | net_updater64.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
544 | net_updater64.exe | Misc activity | ET INFO DropBox User Content Download Access over SSL M2 |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\amd64fre\base\isolation\com\enumidentityattribute.cpp, line 144
|