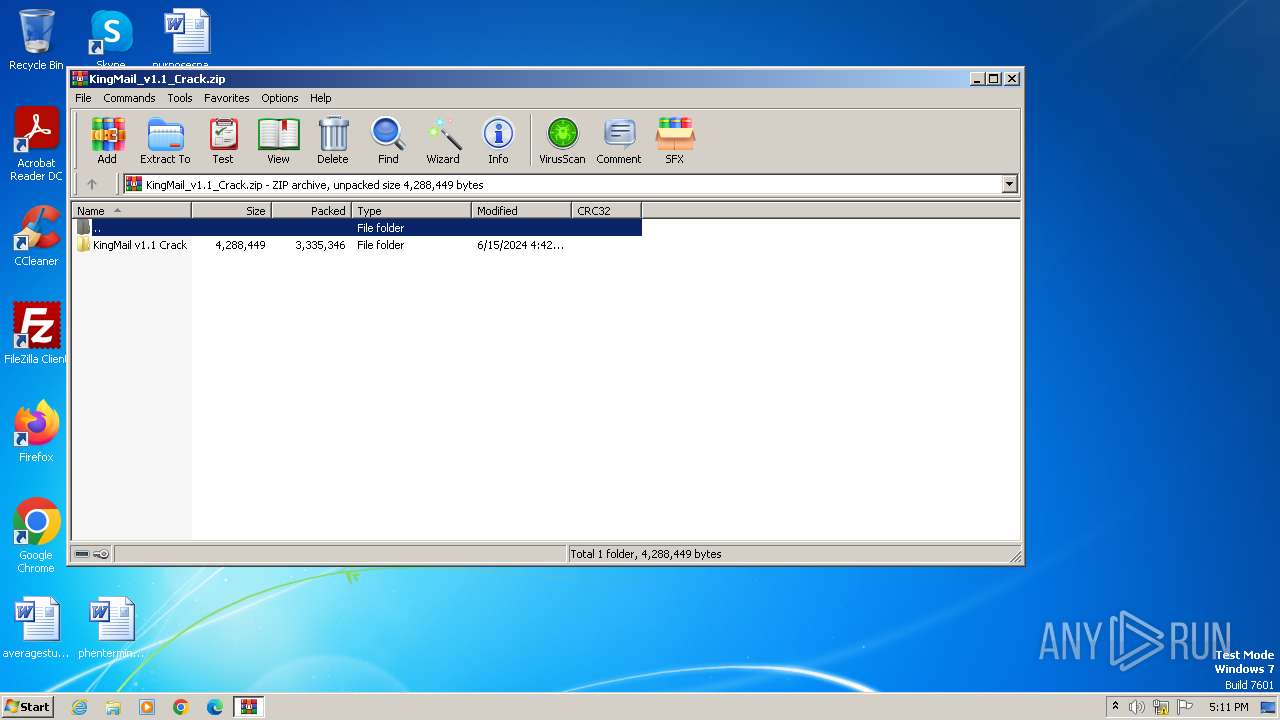
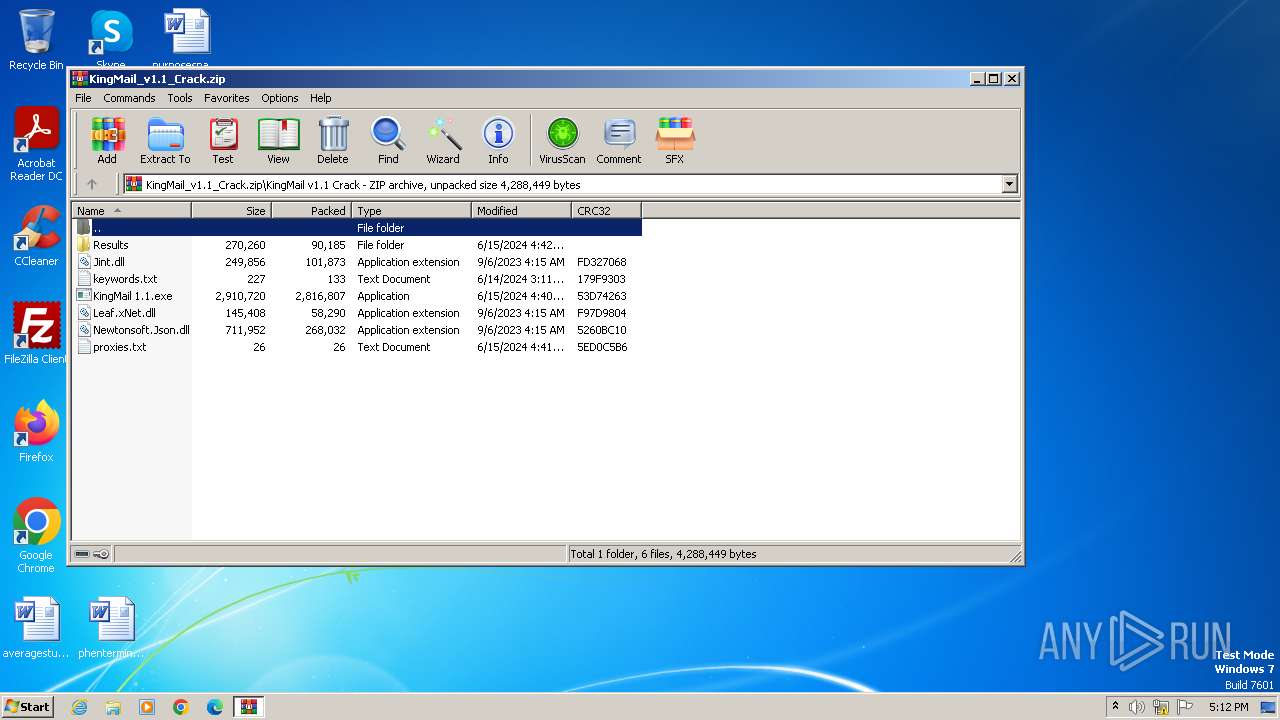
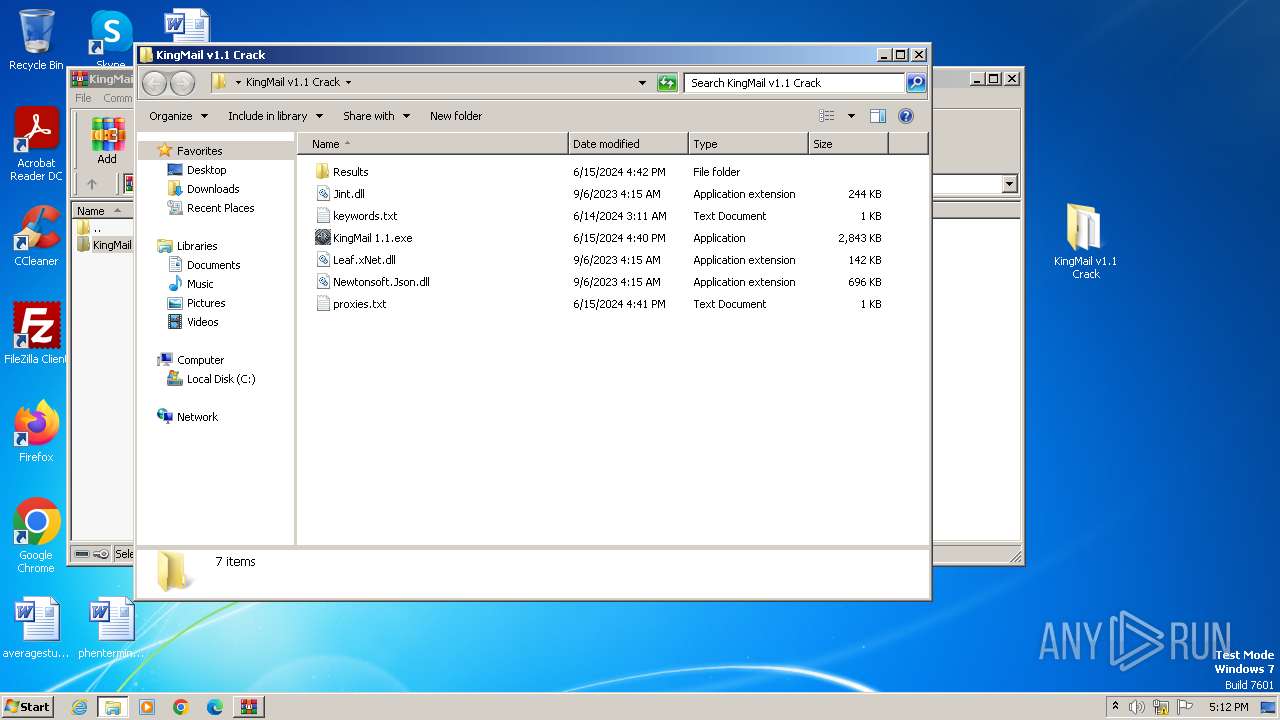
| File name: | KingMail_v1.1_Crack.zip |
| Full analysis: | https://app.any.run/tasks/8025f185-6865-401e-9252-dce6a0d4ef6e |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2024, 16:11:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | FD80BA58E946F39E59E3B1B0A6CB1FD7 |
| SHA1: | 2635602C21D834C7316E9A283B6E5318CCD67AF2 |
| SHA256: | BE1B793D6CEA78BDF91384963CDCB7B009FF61D87E1CCEC17239BE2EA5B85E0F |
| SSDEEP: | 98304:huc2ffTDx1/fQ9LgSQizOZs0FhD2wRouuUM57dWhOuL4mRIzUS9UHskAAWcjM3Qz:I7RF |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
- KingMail 1.1.exe (PID: 2072)
- sanctam.exe (PID: 1120)
- mscomponentBrowserFontwin.exe (PID: 1432)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 748)
SUSPICIOUS
Executable content was dropped or overwritten
- KingMail 1.1.exe (PID: 2072)
- sanctam.exe (PID: 1120)
- mscomponentBrowserFontwin.exe (PID: 1432)
Reads the Internet Settings
- KingMail 1.1.exe (PID: 2072)
- wscript.exe (PID: 748)
- sanctam.exe (PID: 1120)
Reads security settings of Internet Explorer
- KingMail 1.1.exe (PID: 2072)
- sanctam.exe (PID: 1120)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 748)
Runs shell command (SCRIPT)
- wscript.exe (PID: 748)
Executing commands from a ".bat" file
- wscript.exe (PID: 748)
INFO
Checks supported languages
- KingMail 1.1.exe (PID: 2072)
- sanctam.exe (PID: 1120)
- mscomponentBrowserFontwin.exe (PID: 1432)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Create files in a temporary directory
- KingMail 1.1.exe (PID: 2072)
Reads the computer name
- KingMail 1.1.exe (PID: 2072)
- sanctam.exe (PID: 1120)
- mscomponentBrowserFontwin.exe (PID: 1432)
Reads Environment values
- mscomponentBrowserFontwin.exe (PID: 1432)
Reads the machine GUID from the registry
- mscomponentBrowserFontwin.exe (PID: 1432)
Reads product name
- mscomponentBrowserFontwin.exe (PID: 1432)
Manual execution by a user
- KingMail 1.1.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:06:15 08:42:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | KingMail v1.1 Crack/ |
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Windows\System32\WScript.exe" "C:\fontsavesperf\IqDu.vbe" | C:\Windows\System32\wscript.exe | — | sanctam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1120 | "C:\Users\admin\AppData\Local\Temp\sanctam.exe" | C:\Users\admin\AppData\Local\Temp\sanctam.exe | KingMail 1.1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1432 | "C:\fontsavesperf/mscomponentBrowserFontwin.exe" | C:\fontsavesperf\mscomponentBrowserFontwin.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3762504530 Version: 16.10.31418.88 Modules
| |||||||||||||||
| 1872 | C:\Windows\system32\cmd.exe /c ""C:\fontsavesperf\HronhTxGy0bMjeIAkJVetpPpU3.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3762504530 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\Desktop\KingMail v1.1 Crack\KingMail 1.1.exe" | C:\Users\admin\Desktop\KingMail v1.1 Crack\KingMail 1.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\KingMail_v1.1_Crack.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 530
Read events
7 486
Write events
44
Delete events
0
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KingMail_v1.1_Crack.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
8
Suspicious files
2
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\keywords.txt | text | |
MD5:8C80A98C3AEAFEC0694A8469B6D25EB0 | SHA256:071698FA0CFD1E20759F7EC6F18BC6F21AE62B6332262C1EA6E9DEAA0BABEA59 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Leaf.xNet.dll | executable | |
MD5:2C607159E31C1E091697E74EFA5CFEBE | SHA256:056900C587B7E574CCD154A83FE299BADA653347C3862076B0EF6035039C0BEC | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Jint.dll | executable | |
MD5:734C5CE8F9B104D8AD3C7B494E96F9B9 | SHA256:ED618668AE9E7C02C7C2B7332DD09079168CCA96432A051044683C996337001C | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\proxies.txt | binary | |
MD5:8AF14DABEF638E7AF592C48FF7C43E98 | SHA256:45B3A8CA7BFC14DB0410E5A697F1BAB75424D65671BA43CEC66FD91A93F2100E | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Results\Hotmail__Hotmail_Valids_US\aq_Hotmail_Valids_US_All_Hotmail_Valids.txt | text | |
MD5:3AB23A433D78BE94C2B2BAE6DDE3E2A1 | SHA256:C6F9A05D02C8962D9F10E77191094BD28830492F97422138A02D7C6956DC01A4 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Results\Hotmail__Hotmail_Valids_US\aq_Hotmail_Valids_US_BuggedX1.txt | text | |
MD5:6F92C758EF1D5739B823A7204D081C93 | SHA256:D2918DC419F212B96DCA8EE1926321471B45F3C3320D0220BE94876CDB304EF4 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Results\Hotmail__Hotmail_Valids_US\aq_Hotmail_Valids_US_hits_@members.netflix.com.txt | text | |
MD5:2B60F15EAA386924D1E5F6E2CCA3D0EA | SHA256:CA91D0C2BCD61514207B952E8A04B6D95B6694D0DEAE6F922E8A182DBF41C803 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\Results\Hotmail__Hotmail_Valids_US\aq_Hotmail_Valids_US_hits_no-reply@coinbase.com.txt | text | |
MD5:E3FC61BAD09D34C0285CF42AFB2CF8BB | SHA256:9A2BB25264DBDEBA322BBF30FE0E89E909FE3351A56BFD4A4FE21151C7FE5F77 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3976.25141\KingMail v1.1 Crack\KingMail 1.1.exe | executable | |
MD5:A8F954748047B339C19DF2711E0DB074 | SHA256:0EEBDE0EAF8BDA36E4F80AC3987586555C60D309C4E3CBFED3C83B107DC6B264 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |