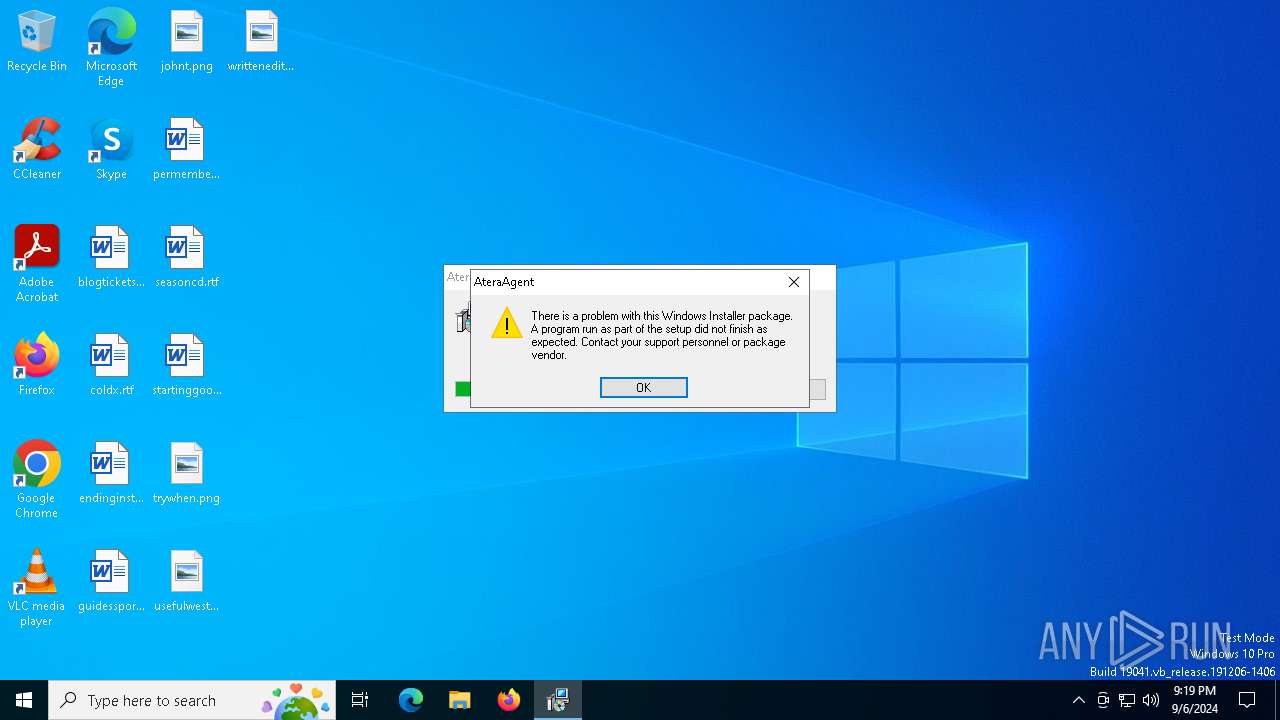
| File name: | ateraAgentSetup64_1_8_7_2.msi |
| Full analysis: | https://app.any.run/tasks/5b23db22-71e1-4e18-92f8-3d9d28914b0b |
| Verdict: | Malicious activity |
| Analysis date: | September 06, 2024, 21:19:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: AteraAgent, Author: Atera networks, Keywords: Installer, Comments: This installer database contains the logic and data required to install AteraAgent., Template: x64;1033, Revision Number: {911E9E2F-B38D-4D02-A148-5E49FC9D8943}, Create Time/Date: Wed Feb 28 10:52:04 2024, Last Saved Time/Date: Wed Feb 28 10:52:04 2024, Number of Pages: 200, Number of Words: 6, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 5E90226ABB5A004B0B9DB9A9E67BAC21 |
| SHA1: | 34EB703055BAFA469A714F18C7F00E5098B764AF |
| SHA256: | BE0C53481ED4CF3EC4D0AD16053CD18D6AAD8C349B8281F5F9B90B526420CEAE |
| SSDEEP: | 98304:5IZTffzvns6eLKLdpRwznfsJb+7J7ERXndiWaKzPtSjXmbABY/lT8vjkZBvrePV1:W3XP9ND |
MALICIOUS
ATERAAGENT has been detected (YARA)
- msiexec.exe (PID: 4100)
- msiexec.exe (PID: 4804)
Starts NET.EXE for service management
- msiexec.exe (PID: 6432)
- net.exe (PID: 2628)
SUSPICIOUS
Checks Windows Trust Settings
- msiexec.exe (PID: 4804)
- AteraAgent.exe (PID: 568)
Process drops legitimate windows executable
- rundll32.exe (PID: 4080)
- msiexec.exe (PID: 4804)
- rundll32.exe (PID: 4732)
- rundll32.exe (PID: 6188)
- msiexec.exe (PID: 4100)
Executable content was dropped or overwritten
- rundll32.exe (PID: 4080)
- rundll32.exe (PID: 4732)
- rundll32.exe (PID: 6188)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4804)
Executes as Windows Service
- VSSVC.exe (PID: 5708)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 6432)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 568)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 4732)
INFO
Creates files or folders in the user directory
- msiexec.exe (PID: 4100)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4100)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4804)
Reads the software policy settings
- msiexec.exe (PID: 4100)
- msiexec.exe (PID: 4804)
- rundll32.exe (PID: 4732)
- AteraAgent.exe (PID: 568)
Checks supported languages
- msiexec.exe (PID: 4804)
- msiexec.exe (PID: 4068)
- msiexec.exe (PID: 6432)
- AteraAgent.exe (PID: 568)
Reads the computer name
- msiexec.exe (PID: 4068)
- msiexec.exe (PID: 4804)
- msiexec.exe (PID: 6432)
- AteraAgent.exe (PID: 568)
Create files in a temporary directory
- rundll32.exe (PID: 4080)
- rundll32.exe (PID: 4732)
- rundll32.exe (PID: 6188)
- msiexec.exe (PID: 4100)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4804)
- AteraAgent.exe (PID: 568)
Checks proxy server information
- msiexec.exe (PID: 4100)
- rundll32.exe (PID: 4732)
Disables trace logs
- rundll32.exe (PID: 4732)
Creates files in the program directory
- AteraAgent.exe (PID: 568)
Creates a software uninstall entry
- msiexec.exe (PID: 4804)
The process uses the downloaded file
- AteraAgent.exe (PID: 568)
Reads Environment values
- AteraAgent.exe (PID: 568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | AteraAgent |
| Author: | Atera networks |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install AteraAgent. |
| Template: | x64;1033 |
| RevisionNumber: | {911E9E2F-B38D-4D02-A148-5E49FC9D8943} |
| CreateDate: | 2024:02:28 10:52:04 |
| ModifyDate: | 2024:02:28 10:52:04 |
| Pages: | 200 |
| Words: | 6 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
151
Monitored processes
18
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe" /i /IntegratorLogin="" /CompanyId="" /IntegratorLoginUI="" /CompanyIdUI="" /FolderId="" /AccountId="" /AgentId="c0bdf4c8-b290-4a29-9c06-ade76beb4e1e" | C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe | msiexec.exe | ||||||||||||
User: admin Company: ATERA Networks Ltd. Integrity Level: MEDIUM Description: AteraAgent Exit code: 3762504530 Version: 1.8.7.2 Modules
| |||||||||||||||
| 888 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | "NET" STOP AteraAgent | C:\Windows\SysWOW64\net.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | C:\Windows\syswow64\MsiExec.exe -Embedding 52B36B42B262D008DD172394FB9A1133 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | rundll32.exe "C:\WINDOWS\Installer\MSIE538.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1238500 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\ateraAgentSetup64_1_8_7_2.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4732 | rundll32.exe "C:\WINDOWS\Installer\MSIE8F2.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1239328 6 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ReportMsiStart | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 892
Read events
14 623
Write events
260
Delete events
9
Modification events
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000006A80AA71A200DB01C41200003C160000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000006A80AA71A200DB01C41200003C160000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000A00EF271A200DB01C41200003C160000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000A00EF271A200DB01C41200003C160000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000041D6F671A200DB01C41200003C160000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000FF39F971A200DB01C41200003C160000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000018B77E72A200DB01C41200003C160000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4804) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000991A8172A200DB01C412000048190000E8030000010000000000000000000000E8B691E8042C1944884D38B5346D9E5200000000000000000000000000000000 | |||
| (PID) Process: | (5708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000060AD8A72A200DB014C16000098050000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
26
Suspicious files
16
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4804 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4080 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIE538.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
| 4100 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_DEB07B5578A606ED6489DDA2E357A944 | binary | |
MD5:013E8CCE550C57E5C3BB83BB2965CB3E | SHA256:CB9EE62E1CBDE7C6866B45A7854D7B686BA9143A8BC88224BC231D4B9326AD52 | |||
| 4080 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIE538.tmp-\System.Management.dll | executable | |
MD5:878E361C41C05C0519BFC72C7D6E141C | SHA256:24DE61B5CAB2E3495FE8D817FB6E80094662846F976CF38997987270F8BBAE40 | |||
| 4804 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{e891b6e8-2c04-4419-884d-38b5346d9e52}_OnDiskSnapshotProp | binary | |
MD5:7793E8B27CE36A53160C58C1D50AF6B5 | SHA256:B581BBEB21DA58FB3511BB858D5D383452CAB7AA0B71C368214523D41894FFCD | |||
| 4080 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIE538.tmp-\AlphaControlAgentInstallation.dll | executable | |
MD5:AA1B9C5C685173FAD2DABEBEB3171F01 | SHA256:E44A6582CD3F84F4255D3C230E0A2C284E0CFFA0CA5E62E4D749E089555494C7 | |||
| 4804 | msiexec.exe | C:\Windows\Installer\12e1dc.msi | executable | |
MD5:5E90226ABB5A004B0B9DB9A9E67BAC21 | SHA256:BE0C53481ED4CF3EC4D0AD16053CD18D6AAD8C349B8281F5F9B90B526420CEAE | |||
| 4804 | msiexec.exe | C:\Windows\Installer\MSIE538.tmp | executable | |
MD5:88D29734F37BDCFFD202EAFCDD082F9D | SHA256:87C97269E2B68898BE87B884CD6A21880E6F15336B1194713E12A2DB45F1DCCF | |||
| 4100 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_DEB07B5578A606ED6489DDA2E357A944 | der | |
MD5:B92AA610F8C73CA117E1D577A237542A | SHA256:84ACB90A50B5E306D45DA36C0F242E0614B4A7B376253895B5AF76DA64DDB782 | |||
| 4732 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIE8F2.tmp-\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
43
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4100 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
4100 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1440 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4132 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4100 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
3328 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
568 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
568 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
3328 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
568 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6164 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4100 | msiexec.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1440 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1440 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
agent-api.atera.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report