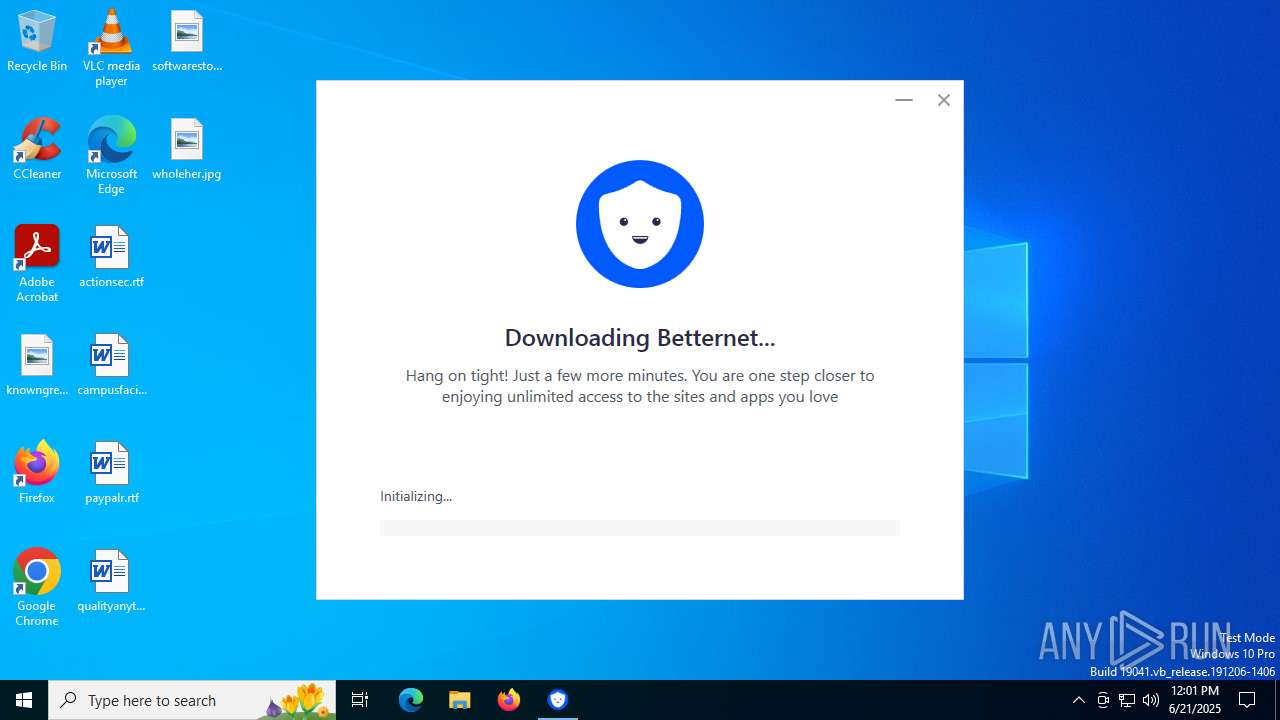
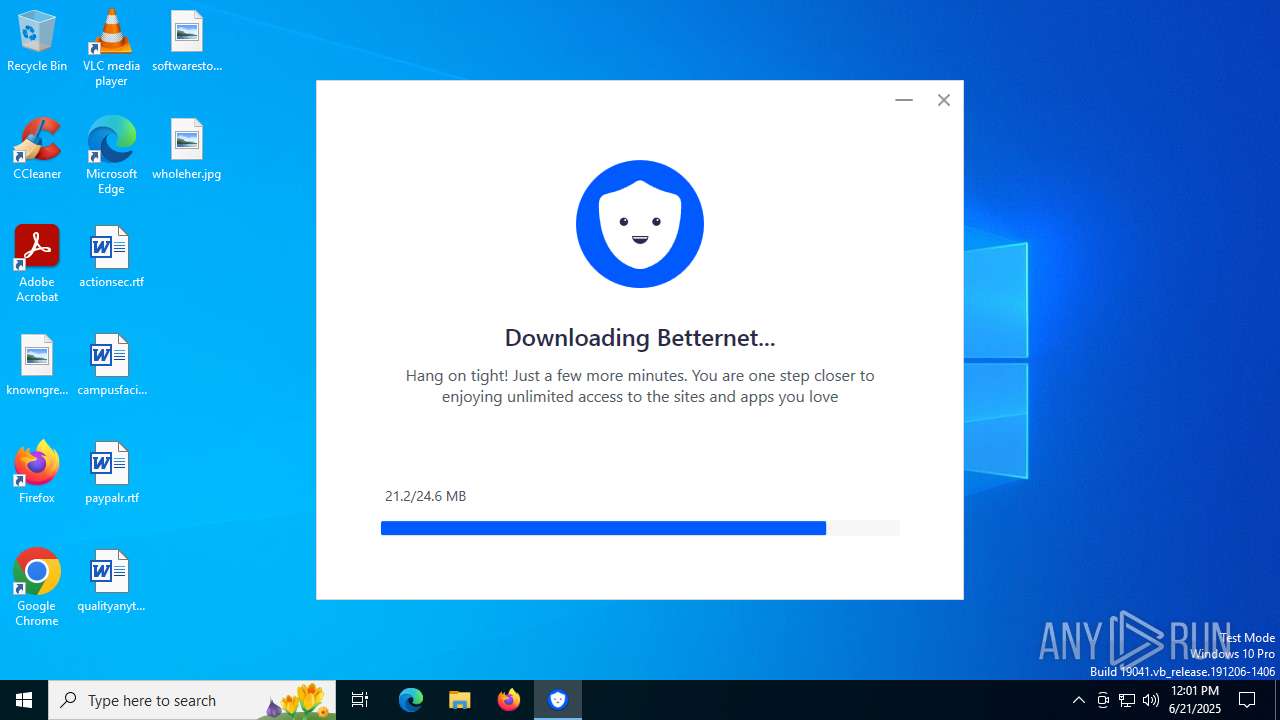
| File name: | BetternetForWindows-RSLOAD.NET-.exe |
| Full analysis: | https://app.any.run/tasks/6390eae2-705f-4ceb-9a09-ccfc32937552 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 12:00:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | A11F0B5B29F5BE05D06AC7FC0DD69029 |
| SHA1: | D6C3DE5B25701F36A57686D4EAFED1D4C0FD5197 |
| SHA256: | BE08974162AC65BF5F8B36B623F3C4D26B8ADD8ECFA537F4298A34EDE986358F |
| SSDEEP: | 24576:8pyhU07dTZra8vvcT8LfGBi3x33h/1p99:8shU0ZTZra8vvcT8Lf+i3x33h/1pn |
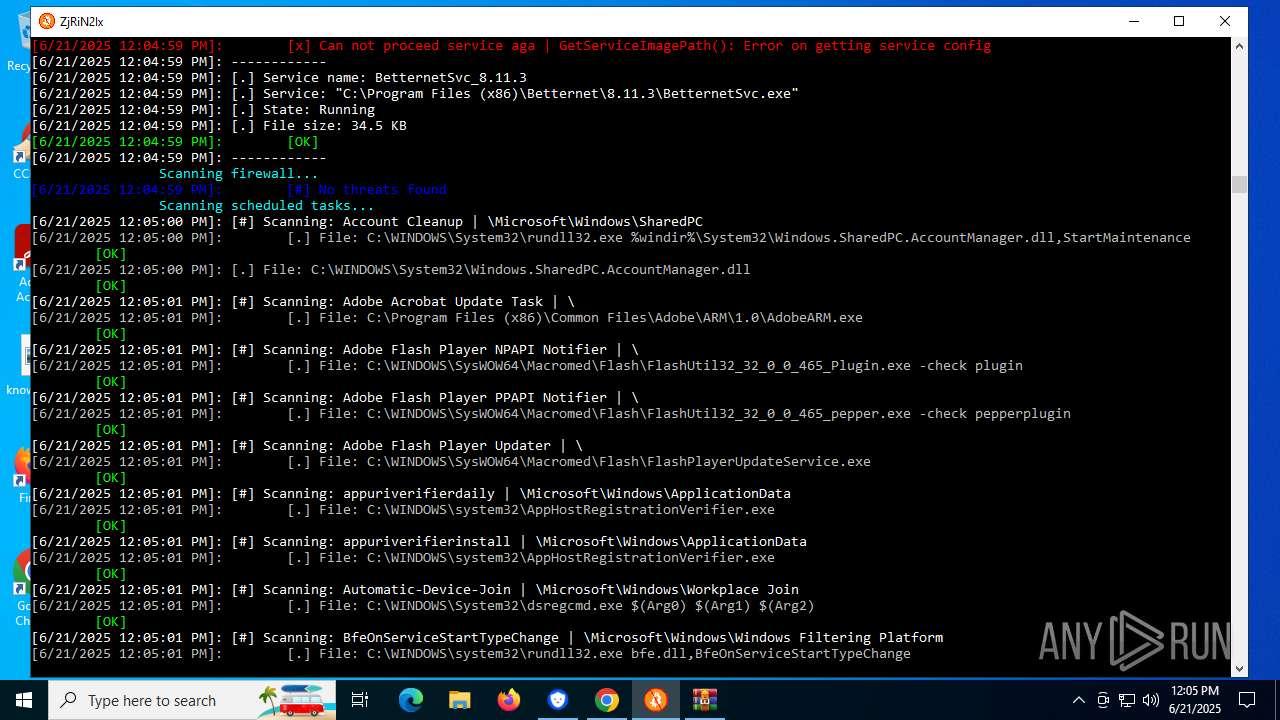
MALICIOUS
Executing a file with an untrusted certificate
- Betternet.WebInstaller.exe (PID: 1296)
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
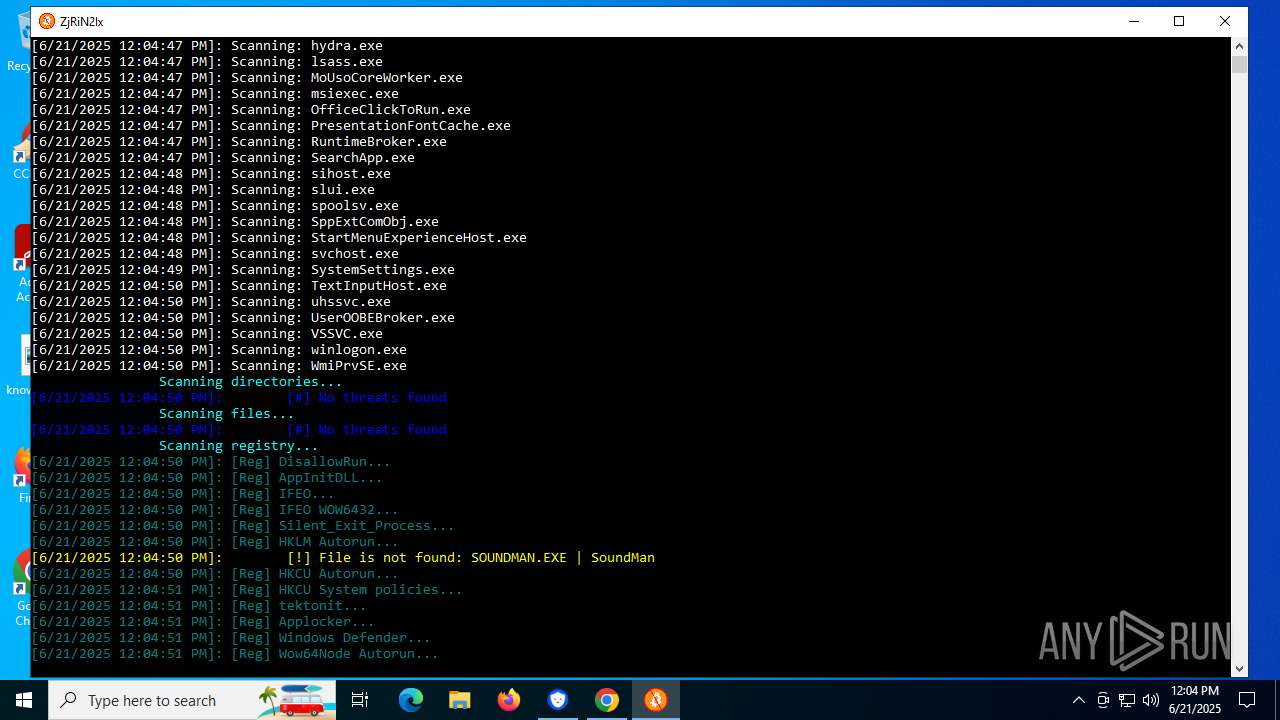
Changes the autorun value in the registry
- Betternet.exe (PID: 6656)
SUSPICIOUS
Reads security settings of Internet Explorer
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6148)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- Betternet.exe (PID: 6656)
- BetternetSvc.exe (PID: 2972)
- Betternet.exe (PID: 7100)
- Betternet.exe (PID: 4764)
- Betternet.exe (PID: 6704)
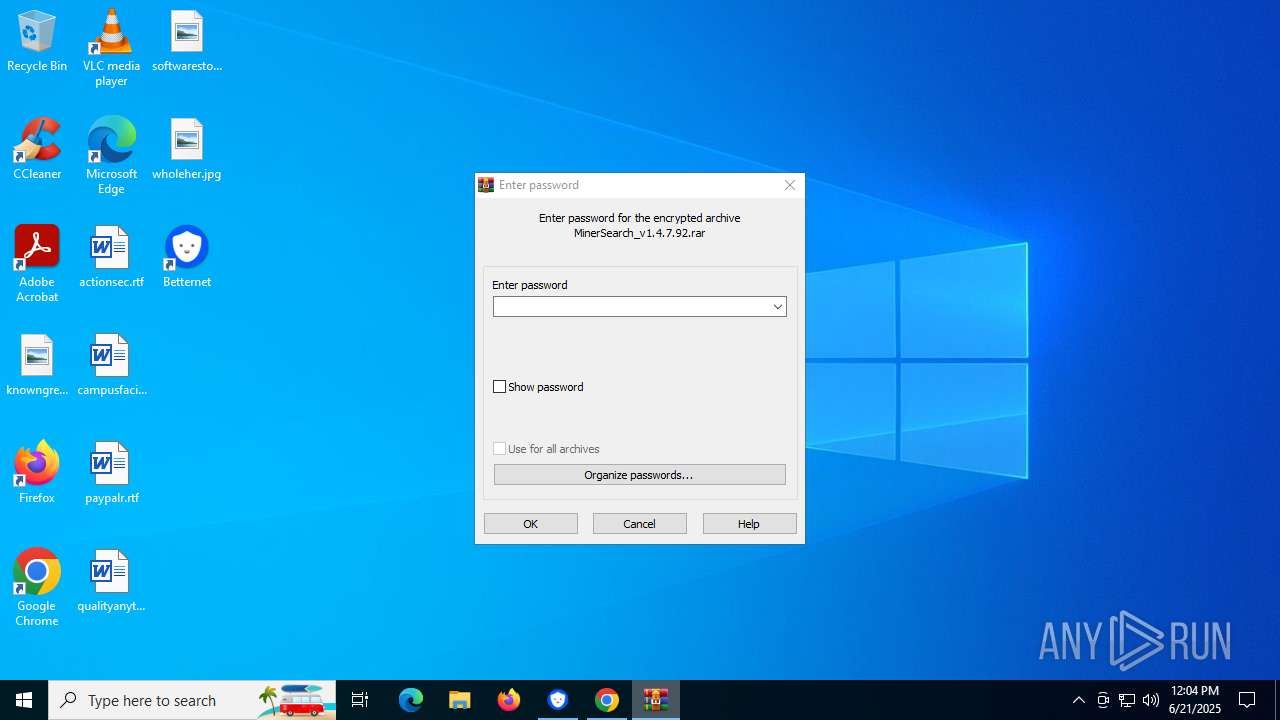
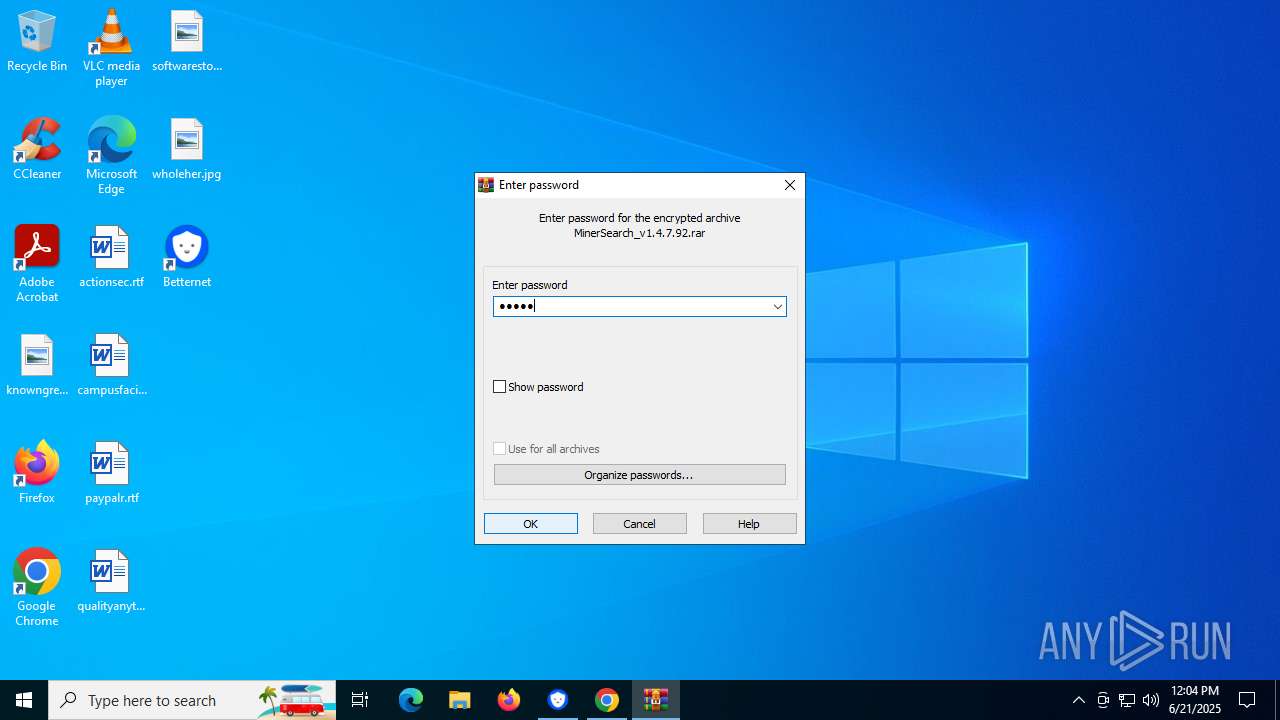
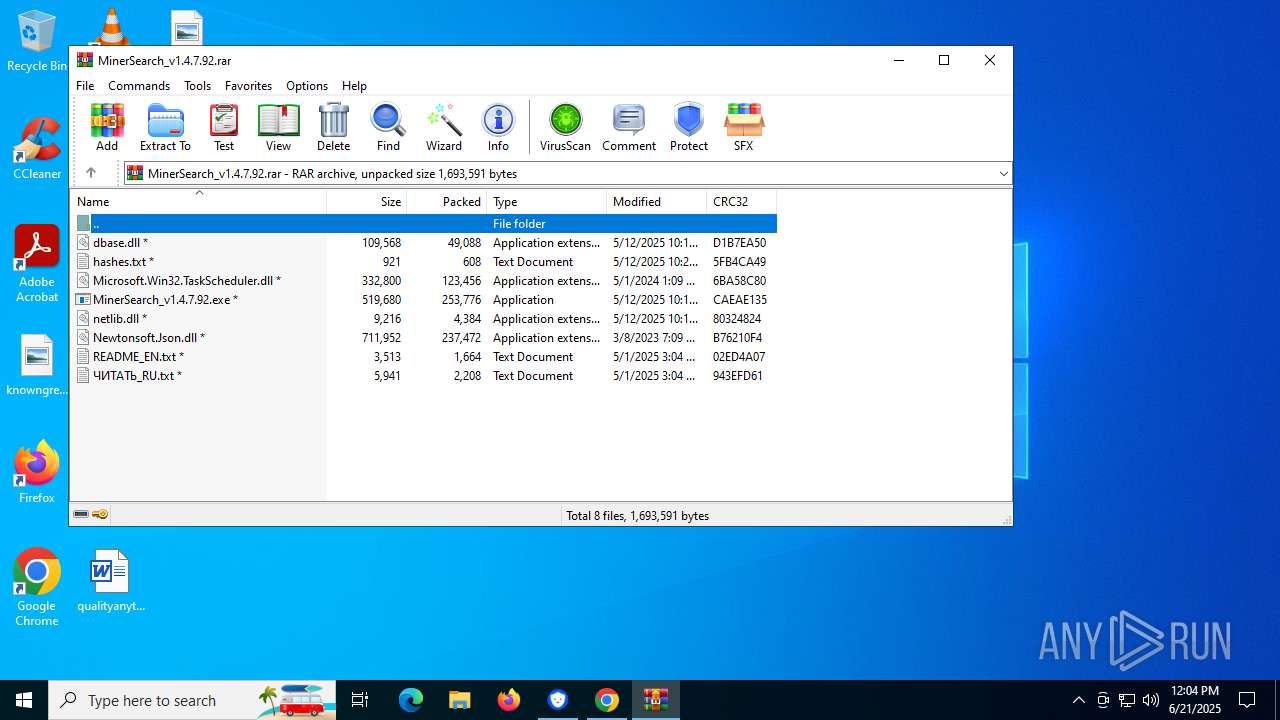
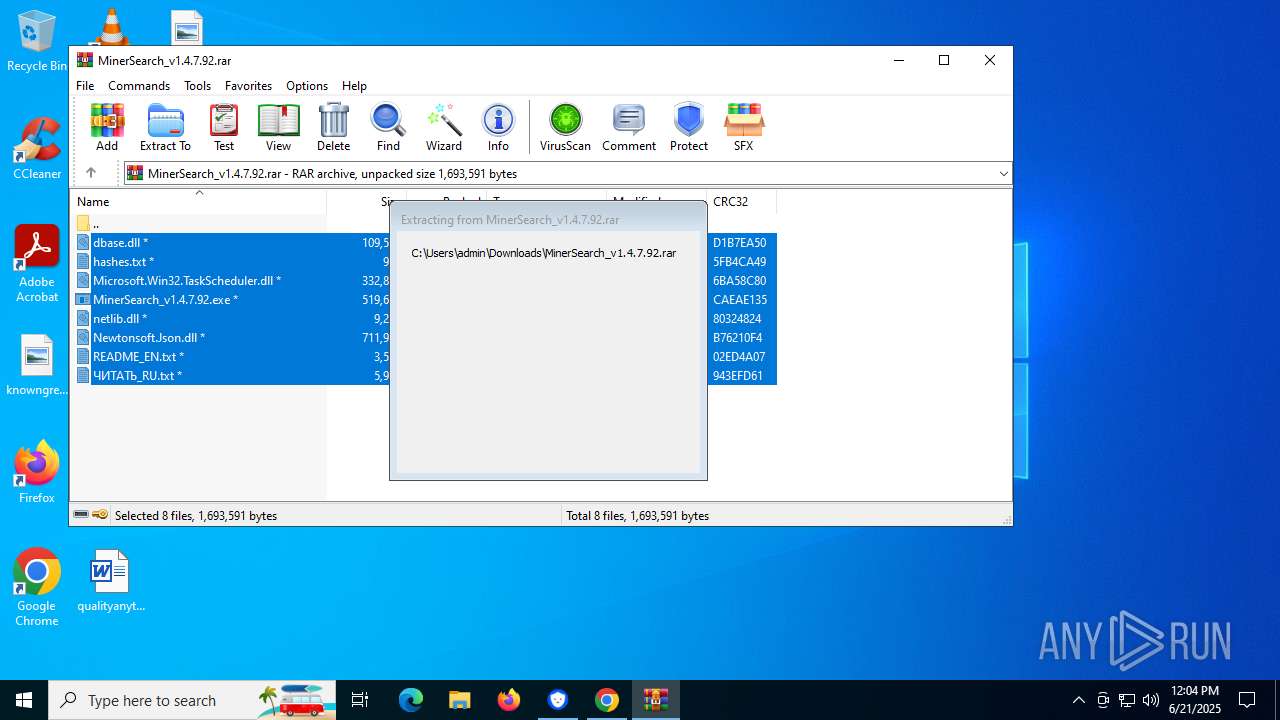
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Executes as Windows Service
- PresentationFontCache.exe (PID: 3756)
- VSSVC.exe (PID: 6292)
- BetternetSvc.exe (PID: 2972)
Malware-specific behavior (creating "System.dll" in Temp)
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- D6575FD7.exe (PID: 4832)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
Executable content was dropped or overwritten
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- Betternet.WebInstaller.exe (PID: 1296)
- D6575FD7.exe (PID: 4832)
- rundll32.exe (PID: 6360)
- rundll32.exe (PID: 2728)
- rundll32.exe (PID: 3668)
- rundll32.exe (PID: 1160)
- rundll32.exe (PID: 3160)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- drvinst.exe (PID: 6320)
- rundll32.exe (PID: 5080)
- drvinst.exe (PID: 2972)
- rundll32.exe (PID: 3980)
- rundll32.exe (PID: 3092)
- rundll32.exe (PID: 6256)
- rundll32.exe (PID: 5552)
- rundll32.exe (PID: 2296)
- WebView2Bootstrapper.exe (PID: 3108)
- rundll32.exe (PID: 5620)
- rundll32.exe (PID: 2324)
- BetternetSvc.exe (PID: 2972)
- hydra.exe (PID: 6980)
- drvinst.exe (PID: 5456)
The process creates files with name similar to system file names
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- D6575FD7.exe (PID: 4832)
- msiexec.exe (PID: 3148)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
There is functionality for taking screenshot (YARA)
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- D6575FD7.exe (PID: 4832)
Reads the date of Windows installation
- Betternet.WebInstaller.exe (PID: 1296)
Process drops legitimate windows executable
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 3148)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- WebView2Bootstrapper.exe (PID: 3108)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3148)
Uses ICACLS.EXE to modify access control lists
- msiexec.exe (PID: 1852)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 1852)
- cmd.exe (PID: 5444)
- msiexec.exe (PID: 4684)
- cmd.exe (PID: 4216)
- cmd.exe (PID: 4880)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 3148)
- rundll32.exe (PID: 1160)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- drvinst.exe (PID: 6320)
- drvinst.exe (PID: 2972)
- hydra.exe (PID: 6980)
- drvinst.exe (PID: 5456)
Creates files in the driver directory
- drvinst.exe (PID: 6320)
- tapinstall.exe (PID: 2188)
- drvinst.exe (PID: 2972)
- drvinst.exe (PID: 5456)
Creates or modifies Windows services
- drvinst.exe (PID: 2972)
- drvinst.exe (PID: 5012)
Creates a software uninstall entry
- rundll32.exe (PID: 5080)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- rundll32.exe (PID: 5620)
Suspicious use of NETSH.EXE
- rundll32.exe (PID: 3980)
- rundll32.exe (PID: 3092)
- hydra.exe (PID: 6980)
Searches for installed software
- rundll32.exe (PID: 5080)
- rundll32.exe (PID: 5620)
Application launched itself
- cmd.exe (PID: 5444)
- cmd.exe (PID: 4216)
- cmd.exe (PID: 4880)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4216)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 5444)
Windows service management via SC.EXE
- sc.exe (PID: 1964)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 7152)
Disables SEHOP
- MicrosoftEdgeUpdate.exe (PID: 7152)
Detected use of reserved device names
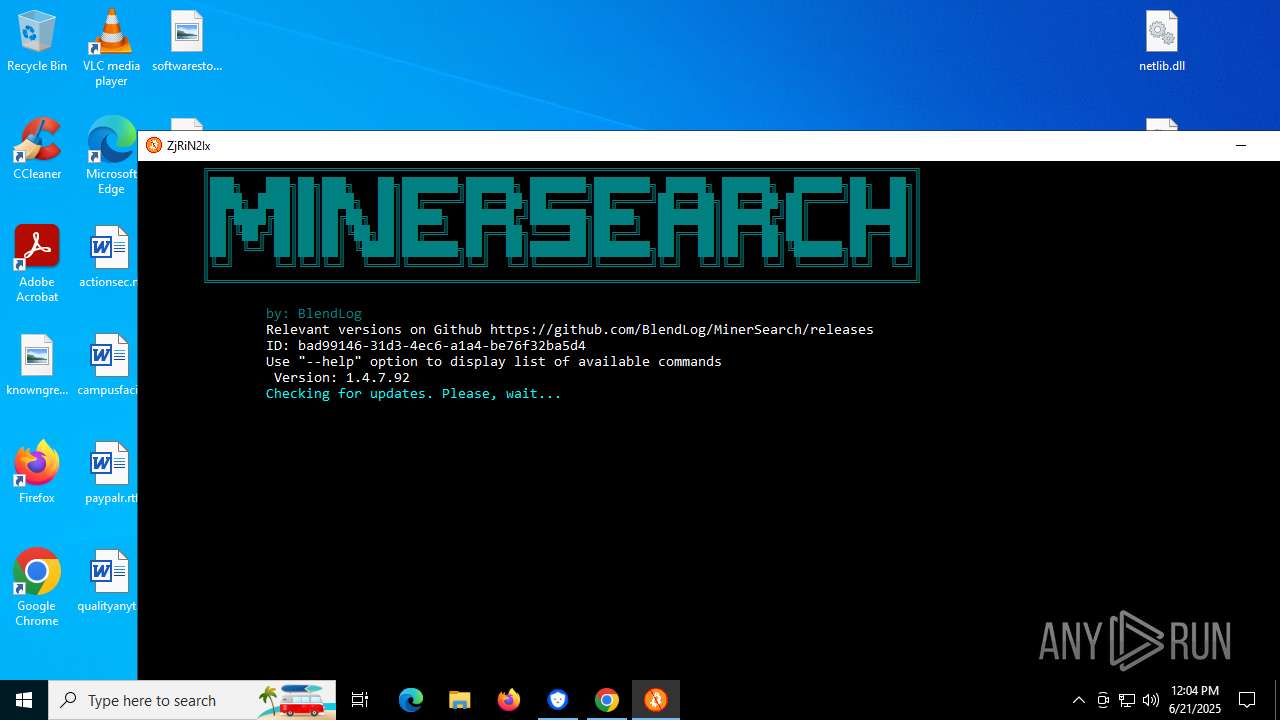
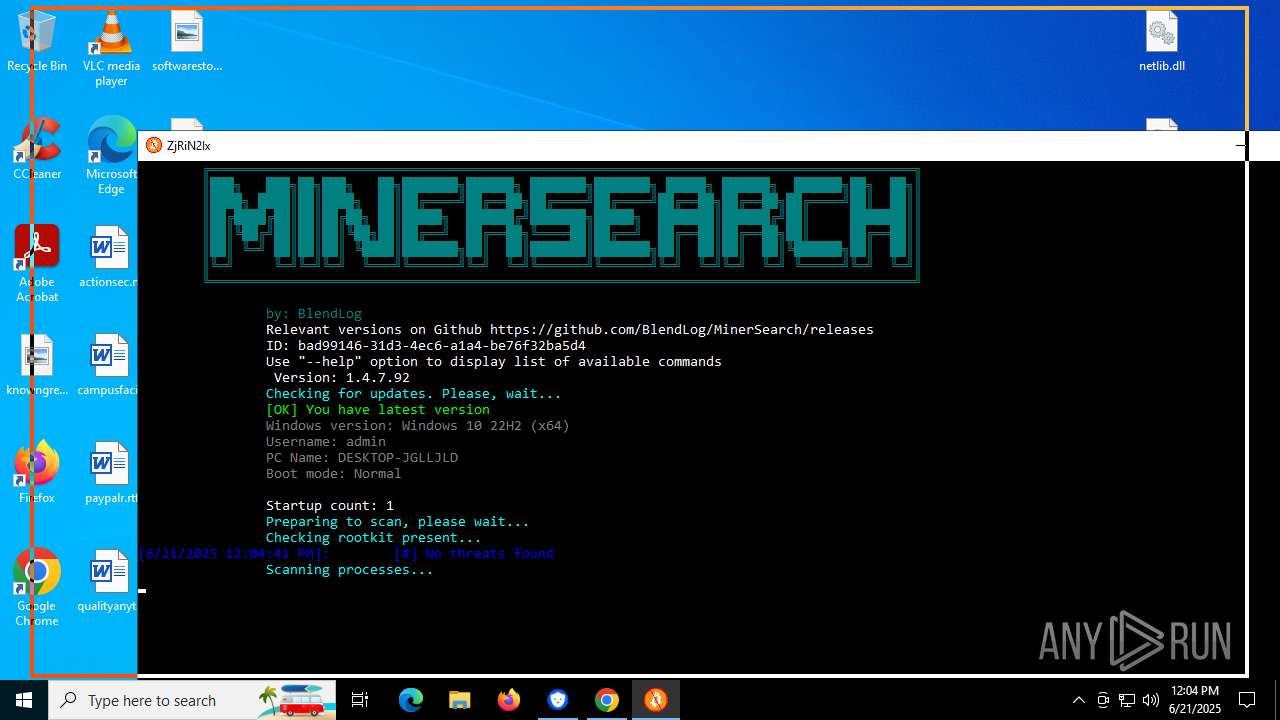
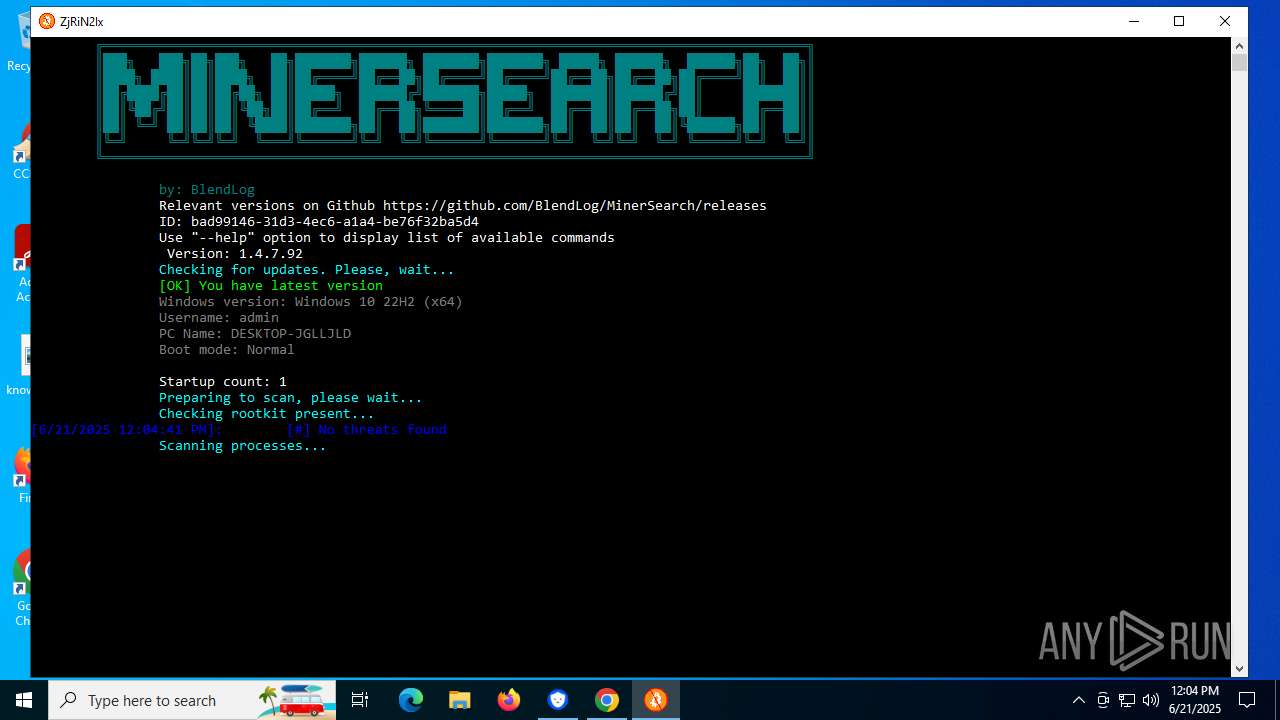
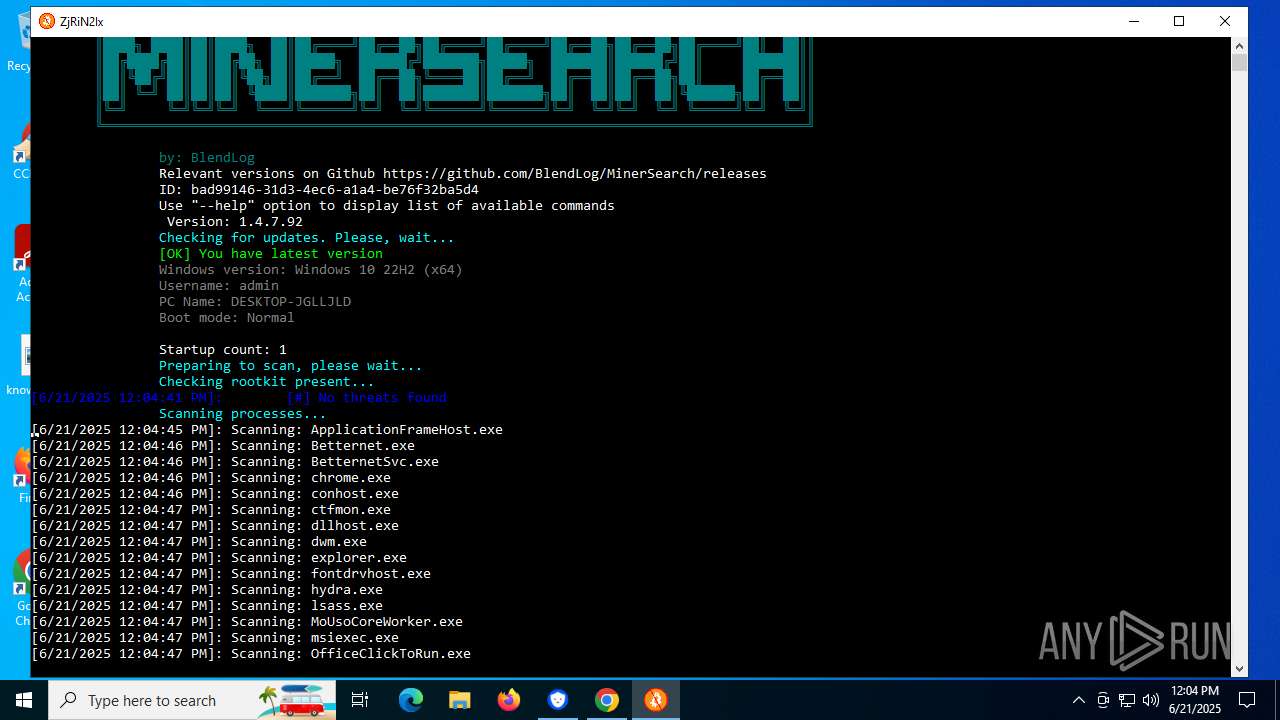
- MinerSearch_v1.4.7.92.exe (PID: 8060)
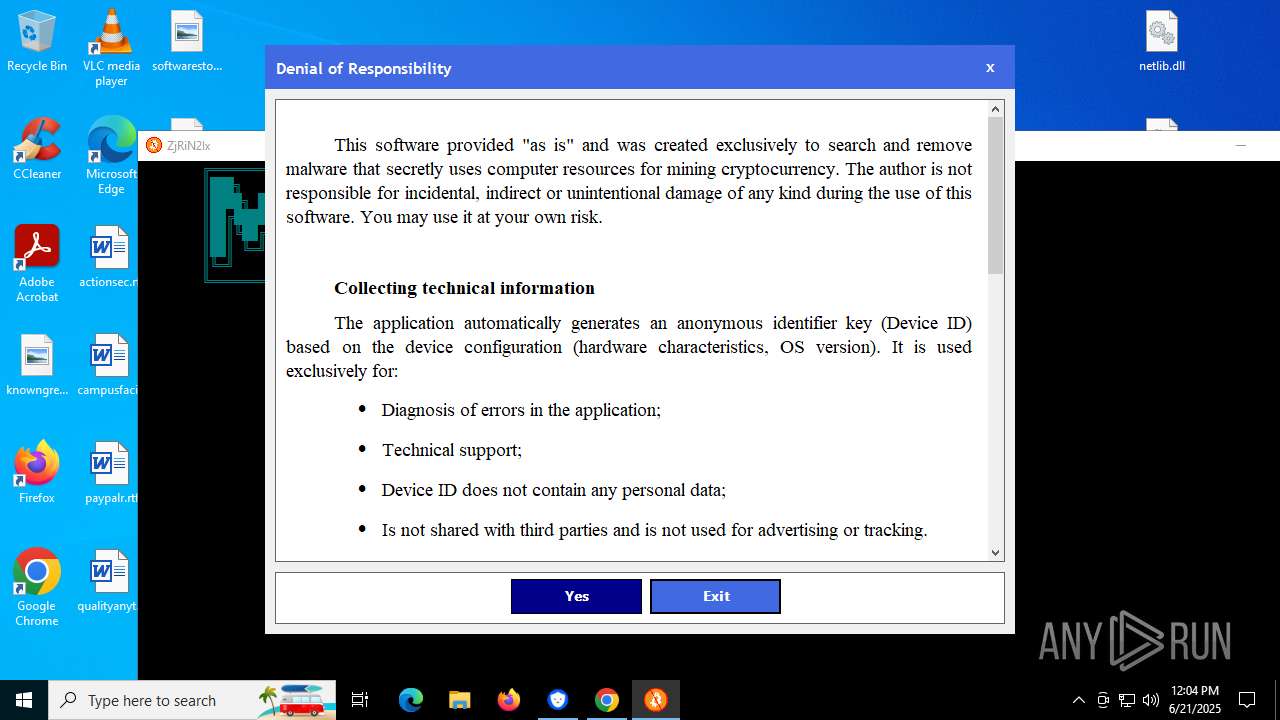
The process verifies whether the antivirus software is installed
- MinerSearch_v1.4.7.92.exe (PID: 8060)
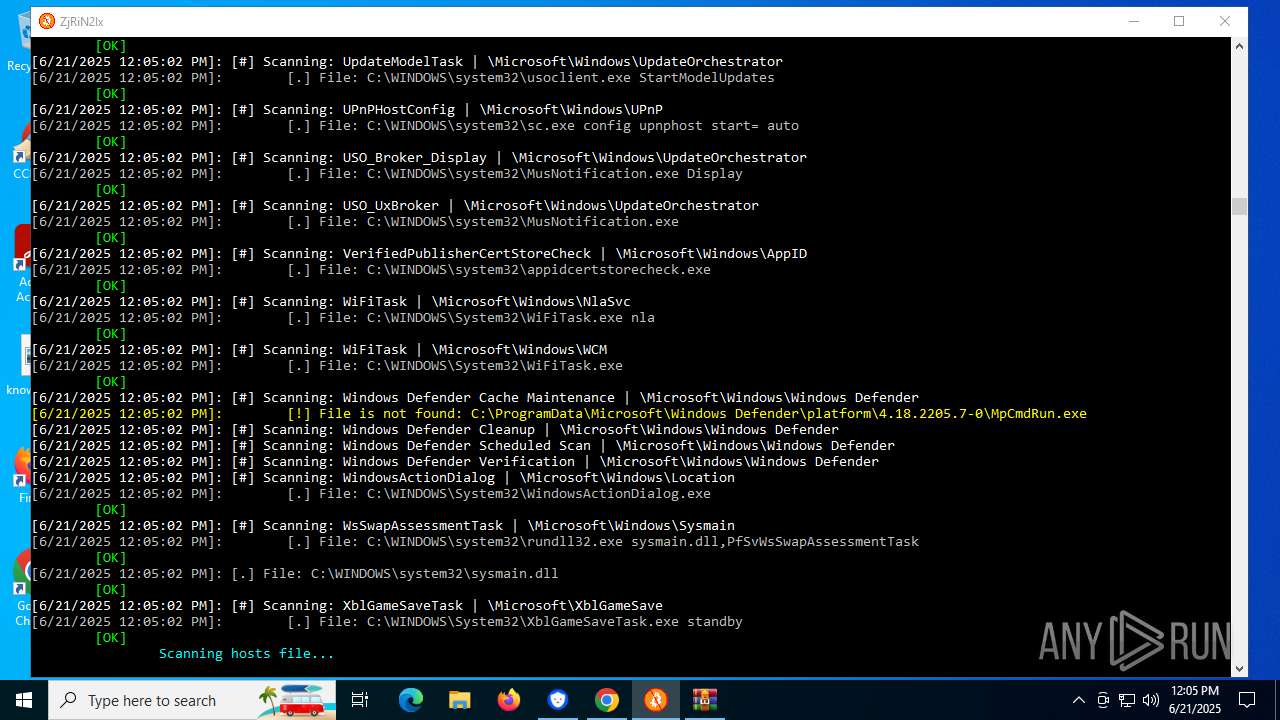
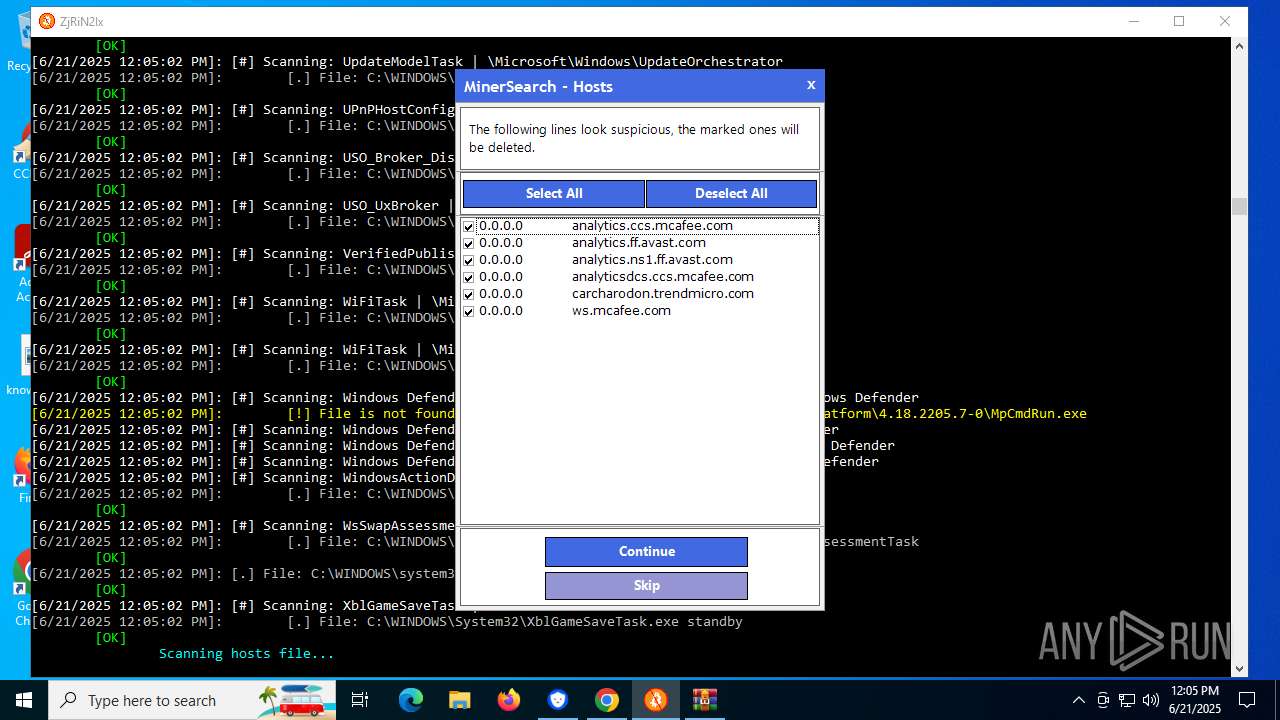
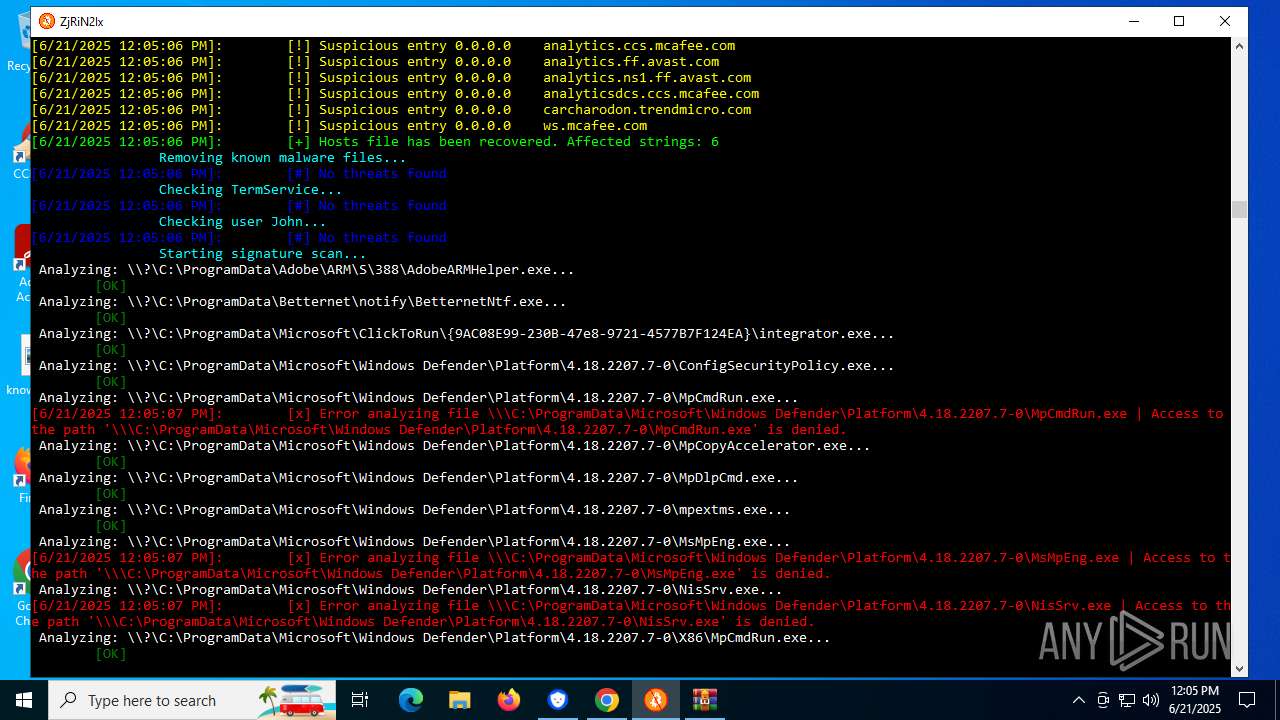
Modifies hosts file to alter network resolution
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Adds/modifies Windows certificates
- MinerSearch_v1.4.7.92.exe (PID: 8060)
INFO
Reads the machine GUID from the registry
- PresentationFontCache.exe (PID: 3756)
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 3148)
- tapinstall.exe (PID: 2188)
- drvinst.exe (PID: 6320)
- BetternetSvc.exe (PID: 2972)
- Betternet.exe (PID: 6656)
- Betternet.exe (PID: 7100)
- Betternet.exe (PID: 4764)
- Betternet.exe (PID: 6704)
- drvinst.exe (PID: 5456)
- hydra.exe (PID: 6980)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Checks supported languages
- PresentationFontCache.exe (PID: 3756)
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- Betternet.WebInstaller.exe (PID: 1296)
- D6575FD7.exe (PID: 4832)
- msiexec.exe (PID: 3148)
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 1852)
- nfregdrv.exe (PID: 7000)
- msiexec.exe (PID: 4684)
- tapinstall.exe (PID: 6684)
- tapinstall.exe (PID: 2188)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- drvinst.exe (PID: 6320)
- drvinst.exe (PID: 2972)
- WebView2Bootstrapper.exe (PID: 3108)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- Betternet.exe (PID: 4764)
- BetternetSvc.exe (PID: 2972)
- Betternet.exe (PID: 6656)
- BetternetNtf.exe (PID: 4968)
- Betternet.exe (PID: 7100)
- Betternet.exe (PID: 6704)
- hydra.exe (PID: 6980)
- drvinst.exe (PID: 5456)
- drvinst.exe (PID: 5012)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Disables trace logs
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6148)
- netsh.exe (PID: 4192)
- netsh.exe (PID: 5720)
- netsh.exe (PID: 6876)
- rundll32.exe (PID: 5552)
- Betternet.exe (PID: 6656)
- BetternetSvc.exe (PID: 2972)
- netsh.exe (PID: 1580)
- netsh.exe (PID: 1760)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Checks proxy server information
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6148)
- Betternet.exe (PID: 6656)
- slui.exe (PID: 6472)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
- slui.exe (PID: 7484)
Reads the software policy settings
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6492)
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 3148)
- tapinstall.exe (PID: 2188)
- drvinst.exe (PID: 6320)
- rundll32.exe (PID: 5552)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- wermgr.exe (PID: 7048)
- Betternet.exe (PID: 6656)
- BetternetSvc.exe (PID: 2972)
- slui.exe (PID: 6472)
- drvinst.exe (PID: 5456)
- slui.exe (PID: 7484)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Reads the computer name
- PresentationFontCache.exe (PID: 3756)
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 3148)
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 4684)
- msiexec.exe (PID: 1852)
- tapinstall.exe (PID: 2188)
- nfregdrv.exe (PID: 7000)
- drvinst.exe (PID: 6320)
- drvinst.exe (PID: 2972)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- Betternet.exe (PID: 6656)
- BetternetSvc.exe (PID: 2972)
- Betternet.exe (PID: 4764)
- BetternetNtf.exe (PID: 4968)
- Betternet.exe (PID: 7100)
- Betternet.exe (PID: 6704)
- hydra.exe (PID: 6980)
- drvinst.exe (PID: 5012)
- drvinst.exe (PID: 5456)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Reads Environment values
- Betternet.WebInstaller.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- Betternet.exe (PID: 6656)
- Betternet.exe (PID: 4764)
- BetternetSvc.exe (PID: 2972)
- Betternet.exe (PID: 6704)
- Betternet.exe (PID: 7100)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Create files in a temporary directory
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- Betternet.WebInstaller.exe (PID: 1296)
- D6575FD7.exe (PID: 4832)
- msiexec.exe (PID: 6492)
- msiexec.exe (PID: 6148)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
The sample compiled with english language support
- BetternetForWindows-RSLOAD.NET-.exe (PID: 1496)
- Betternet.WebInstaller.exe (PID: 1296)
- msiexec.exe (PID: 6148)
- msiexec.exe (PID: 3148)
- rundll32.exe (PID: 1160)
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- drvinst.exe (PID: 6320)
- drvinst.exe (PID: 2972)
- rundll32.exe (PID: 5552)
- WebView2Bootstrapper.exe (PID: 3108)
- MicrosoftEdgeUpdate.exe (PID: 7152)
- hydra.exe (PID: 6980)
- drvinst.exe (PID: 5456)
Creates files or folders in the user directory
- Betternet.WebInstaller.exe (PID: 1296)
- rundll32.exe (PID: 5552)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
.NET Reactor protector has been detected
- Betternet.WebInstaller.exe (PID: 1296)
- Betternet.exe (PID: 6656)
Process checks computer location settings
- Betternet.WebInstaller.exe (PID: 1296)
- MicrosoftEdgeUpdate.exe (PID: 7152)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6492)
- rundll32.exe (PID: 5552)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6492)
- msiexec.exe (PID: 3148)
- msiexec.exe (PID: 6148)
- WinRAR.exe (PID: 7804)
Manages system restore points
- SrTasks.exe (PID: 2348)
Creates files in the driver directory
- rundll32.exe (PID: 1160)
Creates files in the program directory
- bntap-windows-9.24.4-I601-Win10.exe (PID: 4968)
- rundll32.exe (PID: 5080)
- WebView2Bootstrapper.exe (PID: 3108)
- rundll32.exe (PID: 2324)
- Betternet.exe (PID: 6656)
- Betternet.exe (PID: 4764)
- BetternetSvc.exe (PID: 2972)
- hydra.exe (PID: 6980)
Creates a software uninstall entry
- msiexec.exe (PID: 3148)
Reads product name
- Betternet.exe (PID: 6656)
- BetternetSvc.exe (PID: 2972)
Manual execution by a user
- Betternet.exe (PID: 4764)
- Betternet.exe (PID: 7100)
- Betternet.exe (PID: 6704)
- chrome.exe (PID: 360)
- MinerSearch_v1.4.7.92.exe (PID: 8012)
- WinRAR.exe (PID: 3860)
- MinerSearch_v1.4.7.92.exe (PID: 8060)
Launching a file from a Registry key
- Betternet.exe (PID: 6656)
Application launched itself
- chrome.exe (PID: 360)
Reads Microsoft Office registry keys
- chrome.exe (PID: 360)
Launching a file from the Downloads directory
- chrome.exe (PID: 360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:01 02:44:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x35d8 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.10.2.834 |
| ProductVersionNumber: | 6.10.2.834 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Aura |
| FileDescription: | Betternet for Windows |
| FileVersion: | 6.10.2.834 |
| InternalName: | Betternet.WebInstaller.exe |
| LegalCopyright: | Copyright © 2020 Betternet Technologies Inc., All Rights Reserved |
| OriginalFileName: | Betternet.WebInstaller.exe |
| ProductName: | Betternet for Windows |
| ProductVersion: | 6.10.2.834 |
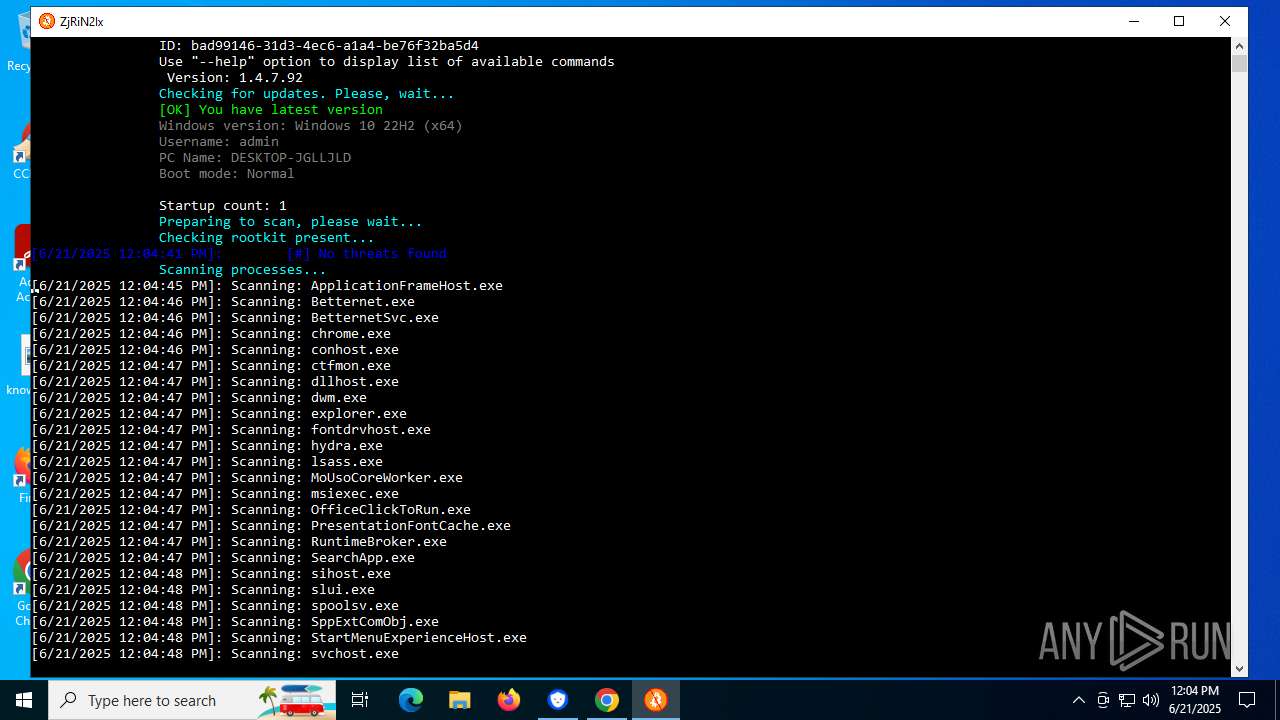
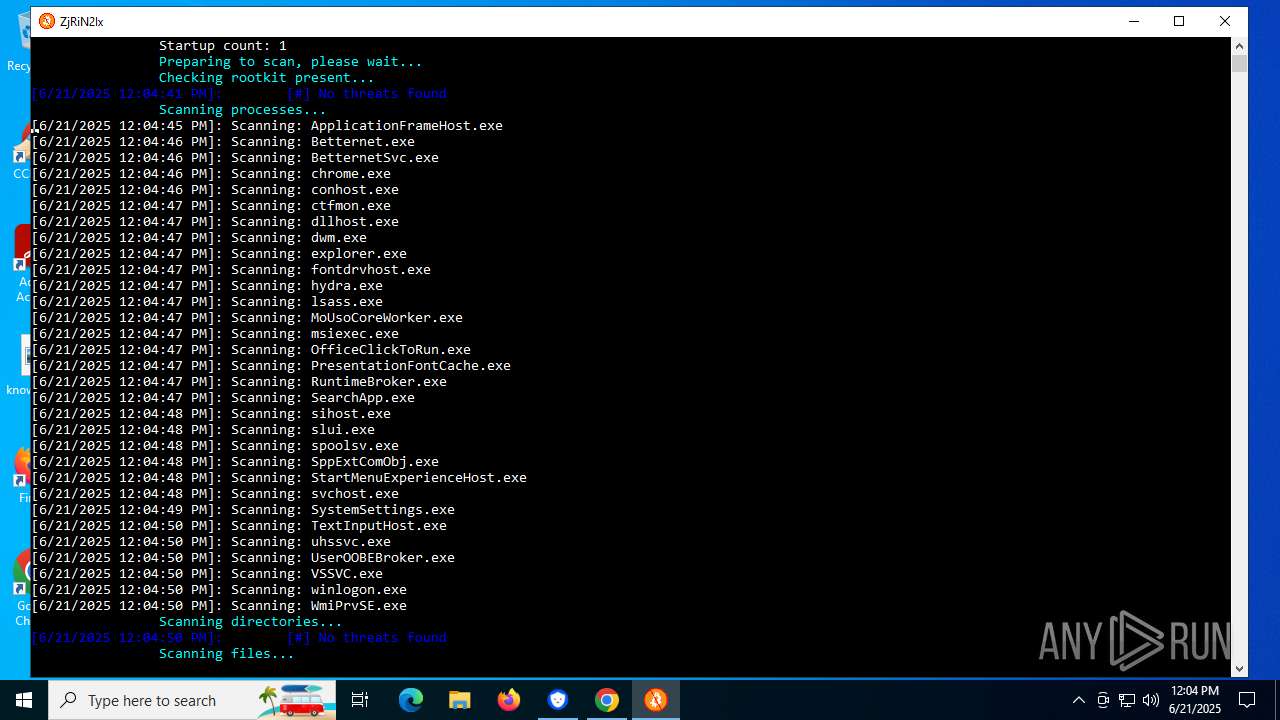
Total processes
266
Monitored processes
105
Malicious processes
12
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3152,i,4280738894496557298,16709261147219706163,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3180 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | rundll32.exe "C:\WINDOWS\Installer\MSI4A30.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1591875 79 Foundation.Installer.CustomActions!Foundation.Installer.CustomActions.NetFilter.NetFilterCustomActions.InstallNetFilterDriver | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=1780,i,4280738894496557298,16709261147219706163,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4588 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1296 | "C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Betternet.WebInstaller.exe" | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Betternet.WebInstaller.exe | BetternetForWindows-RSLOAD.NET-.exe | ||||||||||||
User: admin Company: Betternet Technologies Inc. Integrity Level: MEDIUM Description: Betternet.WebInstaller Exit code: 0 Version: 6.10.2.834 Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\AppData\Local\Temp\BetternetForWindows-RSLOAD.NET-.exe" | C:\Users\admin\AppData\Local\Temp\BetternetForWindows-RSLOAD.NET-.exe | explorer.exe | ||||||||||||
User: admin Company: Aura Integrity Level: MEDIUM Description: Betternet for Windows Exit code: 0 Version: 6.10.2.834 Modules
| |||||||||||||||
| 1568 | "C:\WINDOWS\SysWOW64\REG.exe" ADD "HKLM\Software\Betternet" /v channel /d 1 | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "C:\WINDOWS\system32\netsh.exe" interface ip set address "Betternet WinTun" static 100.127.255.253 255.255.255.252 100.127.255.254 | C:\Windows\System32\netsh.exe | — | hydra.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\WINDOWS\SysWOW64\REG.exe" ADD "HKLM\Software\Betternet" /v hash_v /d 4 /t REG_DWORD | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
486 743
Read events
485 859
Write events
842
Delete events
42
Modification events
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1296) Betternet.WebInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Betternet_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
675
Suspicious files
396
Text files
100
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1496 | BetternetForWindows-RSLOAD.NET-.exe | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Newtonsoft.Json.dll | executable | |
MD5:1390B082700AFC53A7AA320F3259325E | SHA256:7BEB6A951B92AF14322A382CF105FFF8D0DC63518B33556B98E09DACA0CB6D07 | |||
| 1496 | BetternetForWindows-RSLOAD.NET-.exe | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Vpn.WebInstaller.Common.dll | executable | |
MD5:2C689A649BC2F6AF438DCACC5A293157 | SHA256:6D2B1F0899D8E9BE28E5C63272C0BBADC511772EDB17A276F9037444002952CC | |||
| 1496 | BetternetForWindows-RSLOAD.NET-.exe | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Betternet.WebInstaller.exe.config | xml | |
MD5:B5216C3AF56142CA8618D4C9B72FBA6E | SHA256:5F0D941557AEBC77E55D0B0AF4D0B17E11F3BDEE6DF5B60651061E027F90D76D | |||
| 1296 | Betternet.WebInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 1496 | BetternetForWindows-RSLOAD.NET-.exe | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\Betternet.WebInstaller.exe | executable | |
MD5:7697634757428FFBE8C5691E8004E0F5 | SHA256:FCC6A480F0F2A291263301C0436045F699E140451B5F003C800708C6310FCDAC | |||
| 1496 | BetternetForWindows-RSLOAD.NET-.exe | C:\Users\admin\AppData\Local\Temp\nsi5778.tmp\System.dll | executable | |
MD5:564BB0373067E1785CBA7E4C24AAB4BF | SHA256:7A9DDEE34562CD3703F1502B5C70E99CD5BBA15DE2B6845A3555033D7F6CB2A5 | |||
| 1296 | Betternet.WebInstaller.exe | C:\Users\admin\AppData\Local\Temp\Tmp664E.tmp | text | |
MD5:B75FDCB58153F77358F11C2F21C9CC95 | SHA256:63BED24F4C3DD97AADFB055CEE41AF5D15512234E7D353550361C3D7FA5E13E4 | |||
| 1296 | Betternet.WebInstaller.exe | C:\Users\admin\AppData\Local\Temp\Tmp5AE1.tmp | text | |
MD5:BC814B85FD324ED82A1F6A5489E1FFC9 | SHA256:04493B0C31B139F4373EFAEC4416E955CD991AAD901738D5EB17716616899E96 | |||
| 1296 | Betternet.WebInstaller.exe | C:\Users\admin\AppData\Local\Temp\Tmp664D.tmp | text | |
MD5:B75FDCB58153F77358F11C2F21C9CC95 | SHA256:63BED24F4C3DD97AADFB055CEE41AF5D15512234E7D353550361C3D7FA5E13E4 | |||
| 1296 | Betternet.WebInstaller.exe | C:\Users\admin\AppData\Local\Temp\Tmp664C.tmp | text | |
MD5:BC814B85FD324ED82A1F6A5489E1FFC9 | SHA256:04493B0C31B139F4373EFAEC4416E955CD991AAD901738D5EB17716616899E96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
118
DNS requests
82
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.17.189.192:80 | http://s1.symcb.com/pca3-g5.crl | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEE%2FmH6UPQLuoQS8N9BFbQPA%3D | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEE%2FmH6UPQLuoQS8N9BFbQPA%3D | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcb.com/sv.crl | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT5hgD4pKvs0jFFLEKNQ1CjblLIPQQU9LbhIB3%2BKa7S5GGlsqIlssgXNW4CEA1CSuC%2BOoj%2FYEAhzhQA8N0%3D | unknown | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAqhJdbWMht%2BQeQF2jaXwhU%3D | unknown | — | — | whitelisted |
5848 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6356 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1296 | Betternet.WebInstaller.exe | 18.172.111.173:443 | d21j7etzkdo9k9.cloudfront.net | — | US | whitelisted |
1296 | Betternet.WebInstaller.exe | 2.23.79.3:80 | s2.symcb.com | AKAMAI-AS | DE | whitelisted |
1296 | Betternet.WebInstaller.exe | 2.17.189.192:80 | s1.symcb.com | AKAMAI-AS | DE | whitelisted |
1296 | Betternet.WebInstaller.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1296 | Betternet.WebInstaller.exe | 52.217.129.128:443 | s3.amazonaws.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
d21j7etzkdo9k9.cloudfront.net |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
sv.symcd.com |
| whitelisted |
sv.symcb.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
s3.amazonaws.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Betternet.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
hydra.exe | HYDRA_STATE
|
hydra.exe | HYDRA_STATE_CONNECTING
|
hydra.exe | HYDRA_STATE_CONNECTED
|