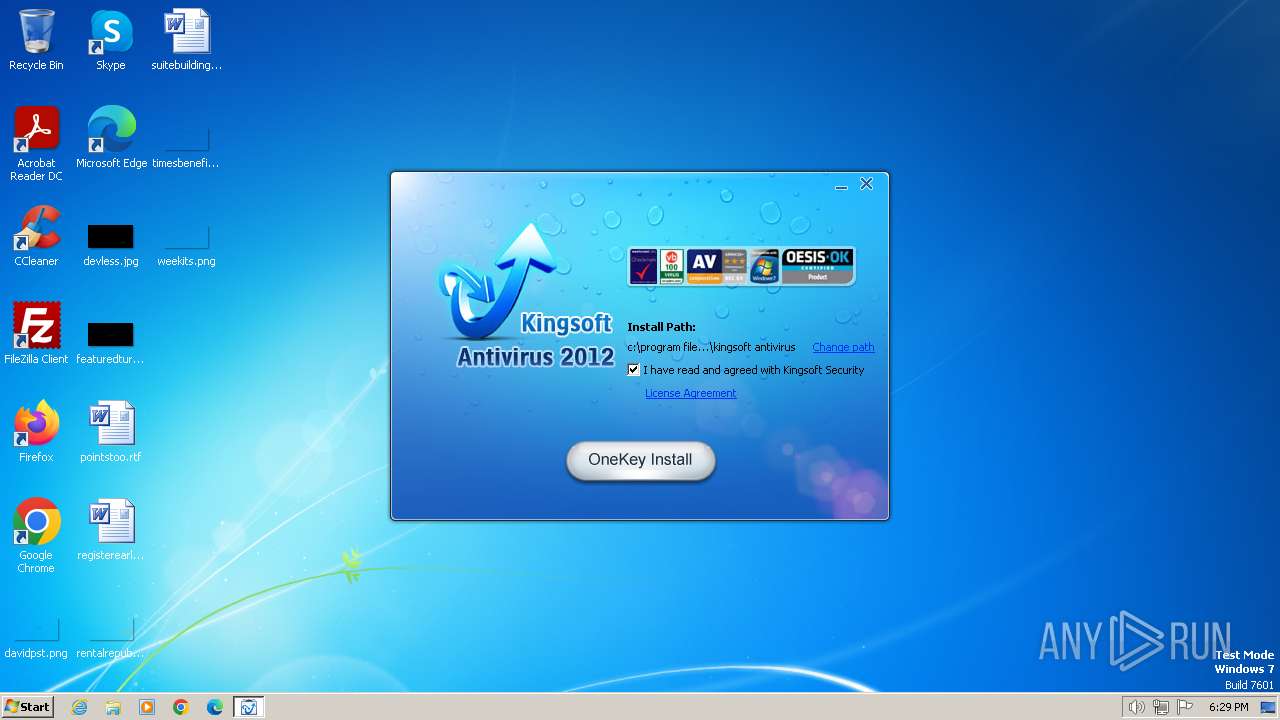
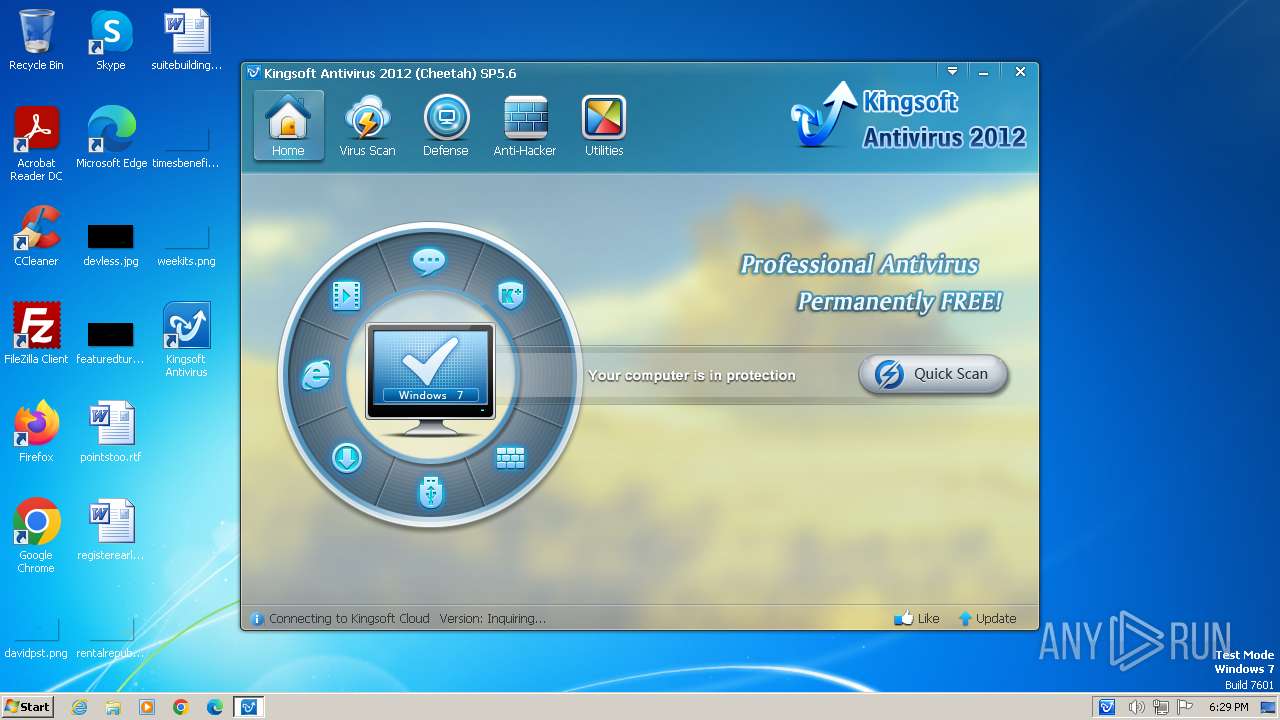
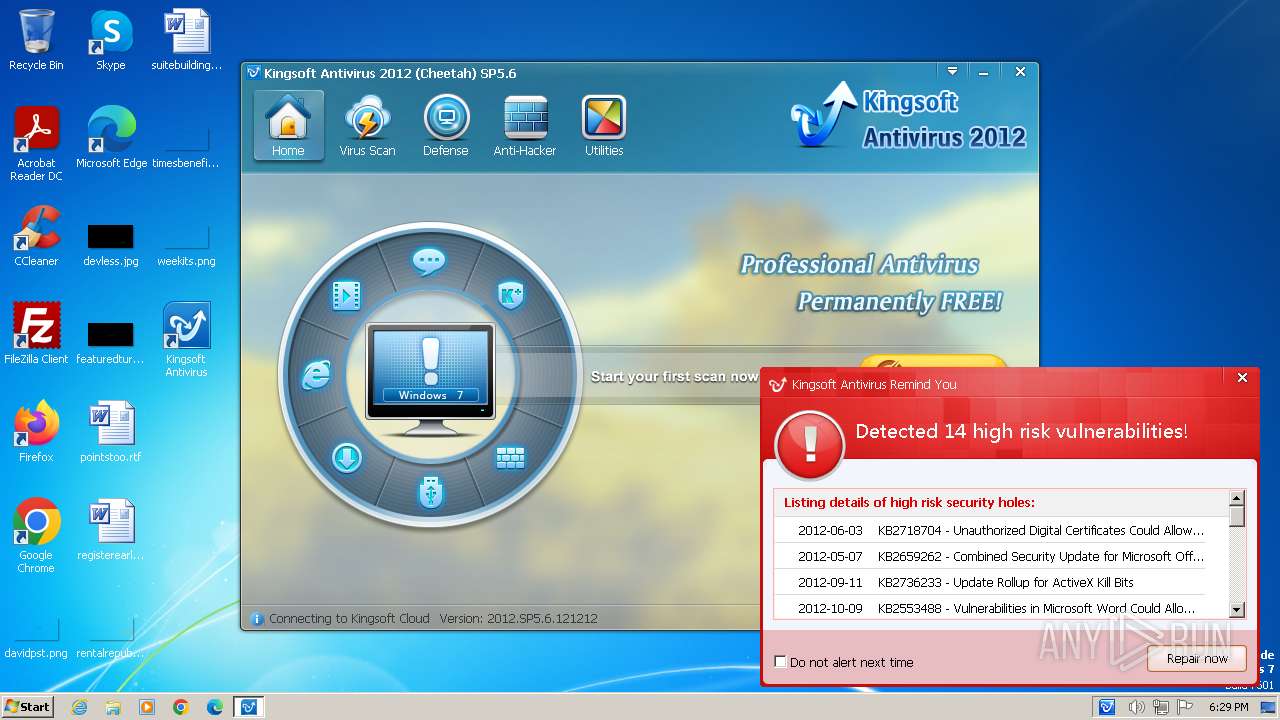
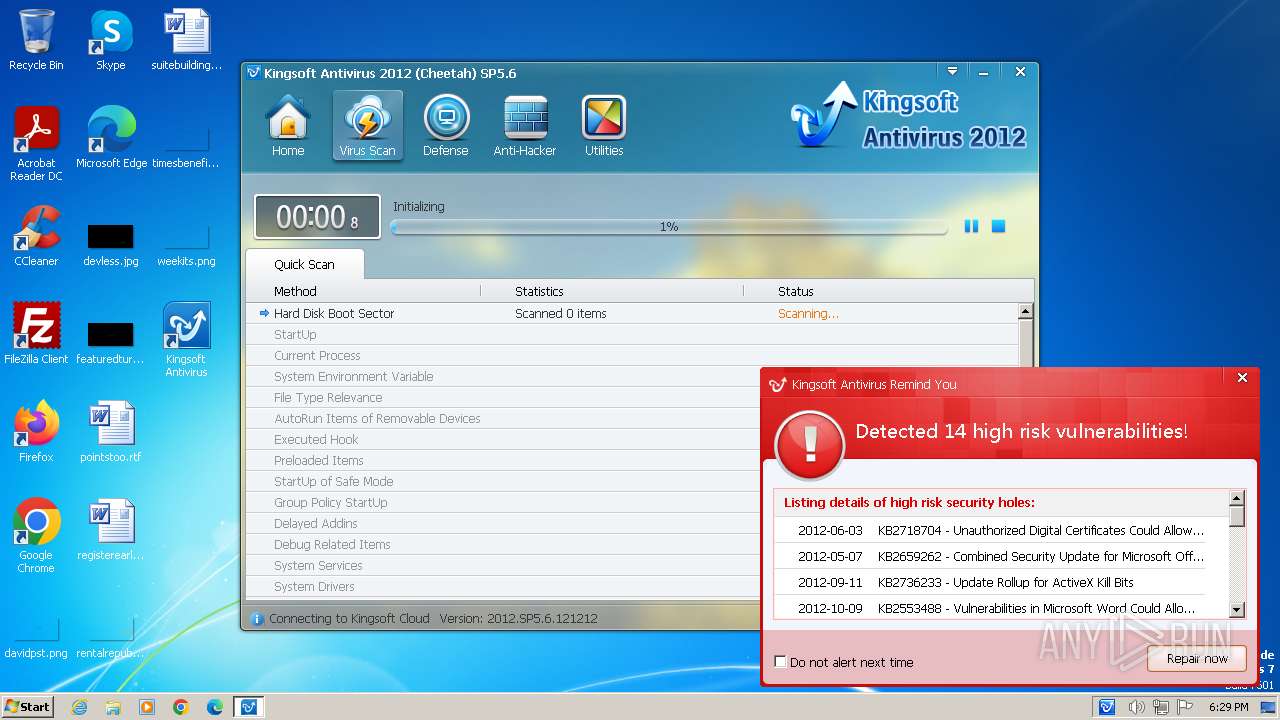
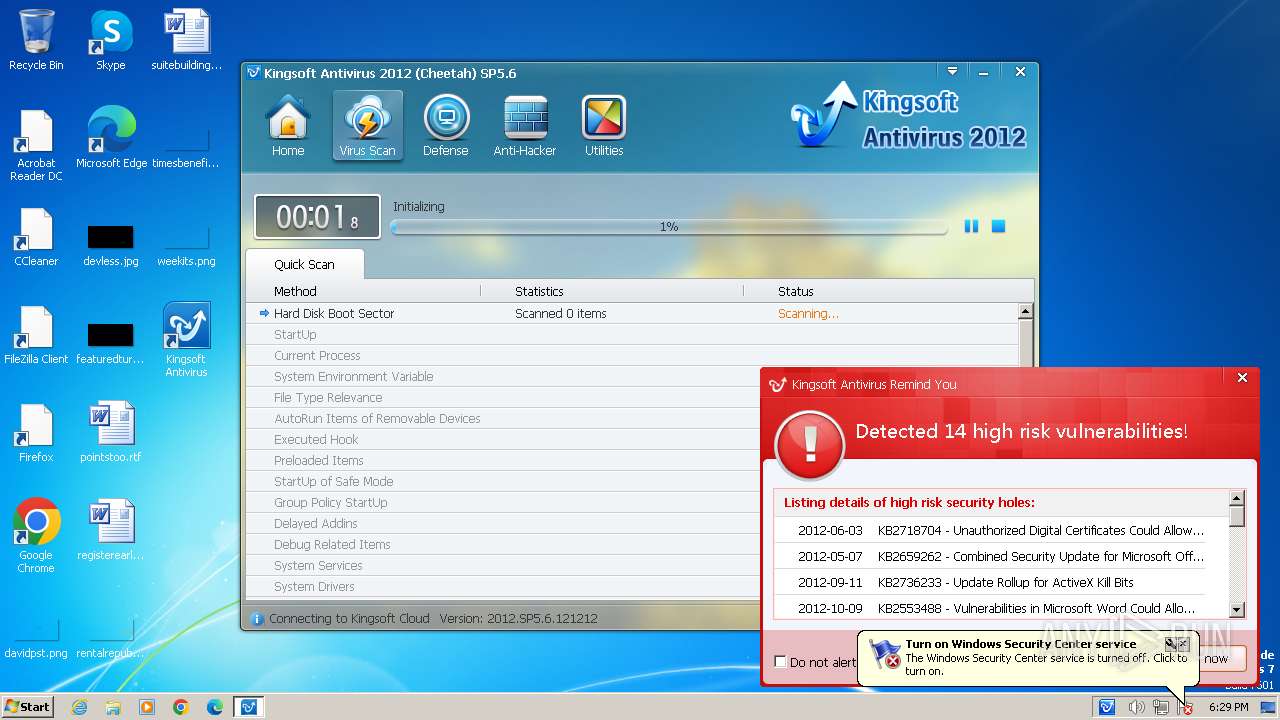
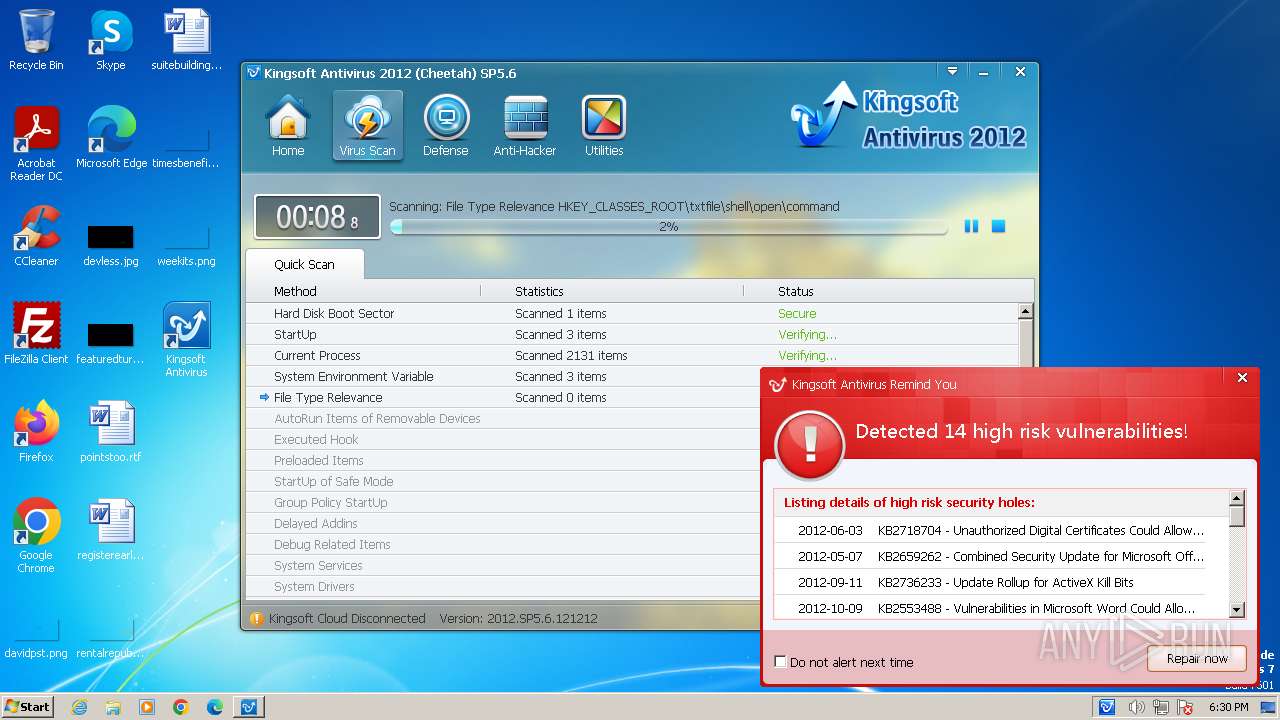
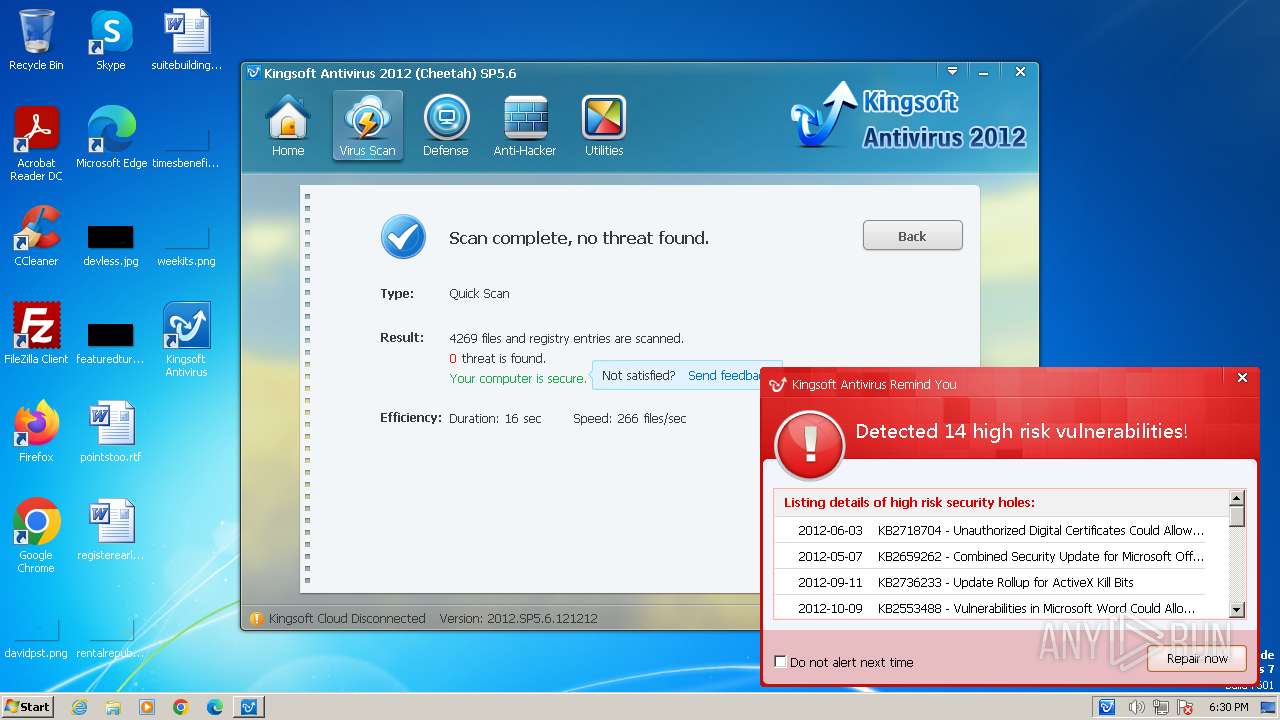
| File name: | kav_setup.exe |
| Full analysis: | https://app.any.run/tasks/70fcc16c-f975-4ab8-a798-06ce0fbf7ee6 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 17, 2024, 18:29:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 4B80EAF2288AA715354CFC42E87F6A55 |
| SHA1: | 2B2227C1135FDE2F277EEC549FAECC57020D6947 |
| SHA256: | BDF40BBC008AB151DB86ACE1B8C2385B8EED742031DB4277C4F29CE164995294 |
| SSDEEP: | 98304:ULudSMlTtgr25a5VBy6sZe26vYkbDLAfxBxSnyoxi7N8ZI3++otzYLyWxaLUtw8n:5OgfG54uKYriEMV+zVkAcq7I08iR1XK |
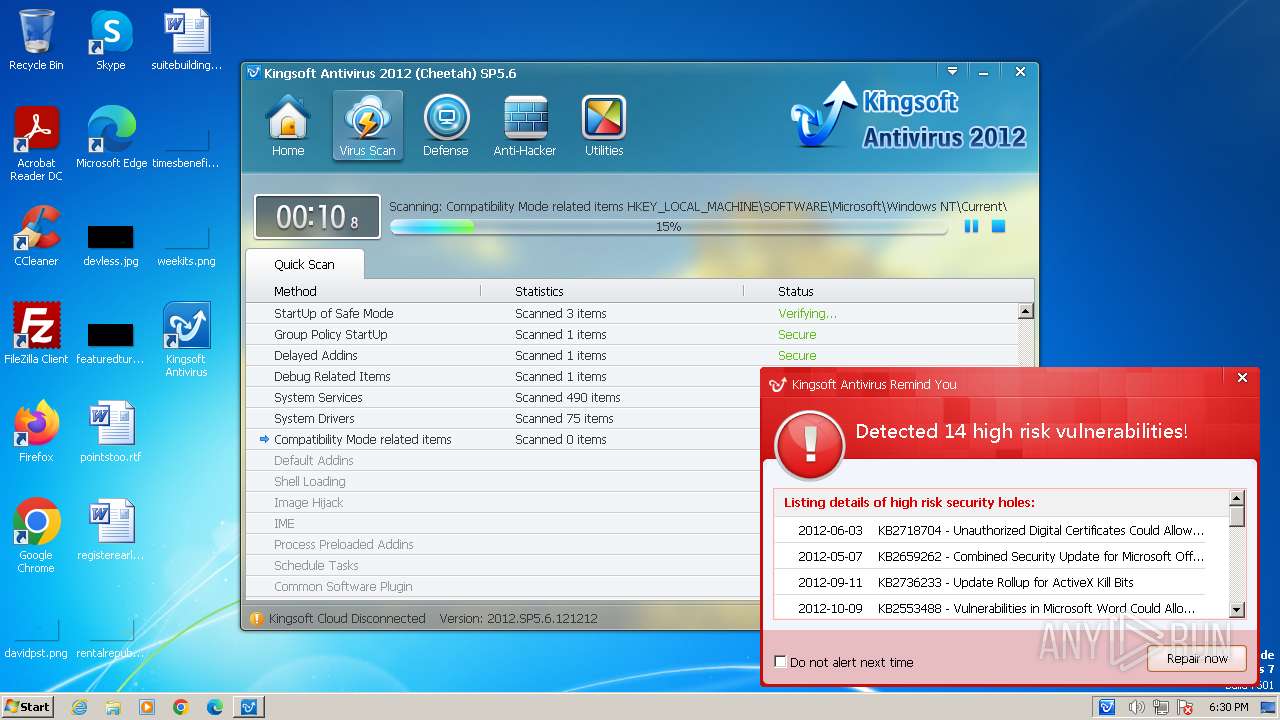
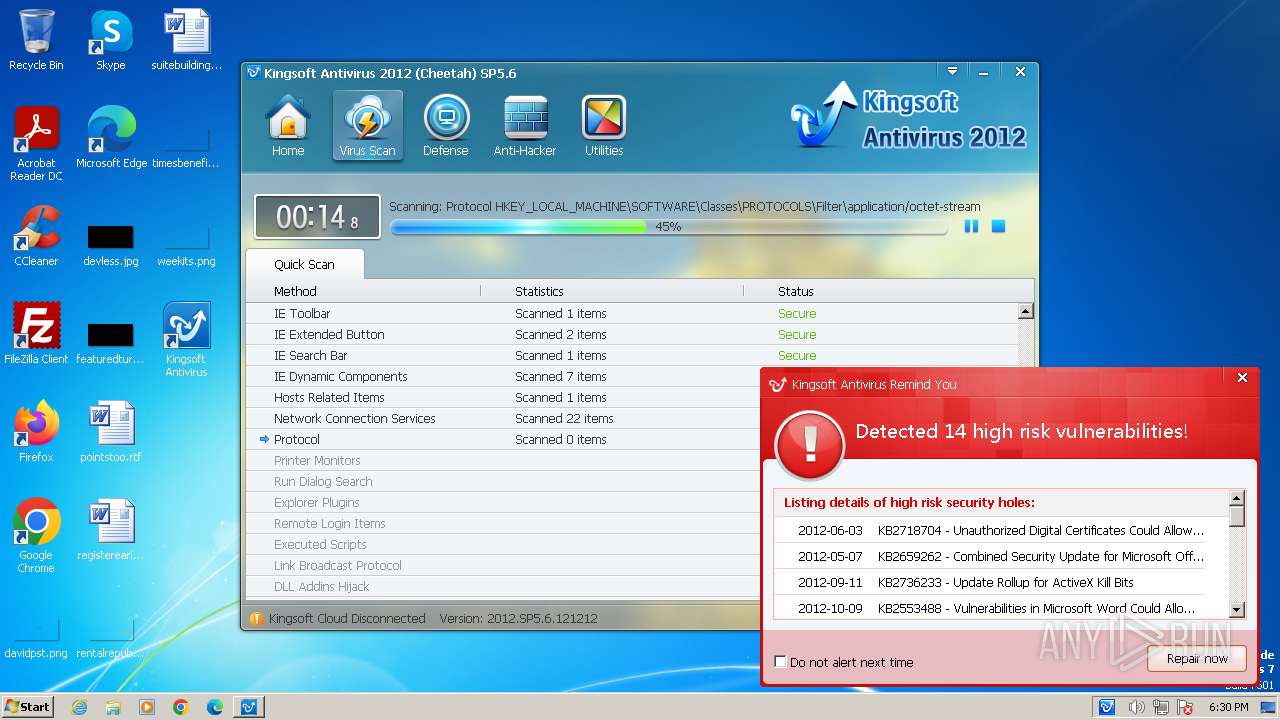
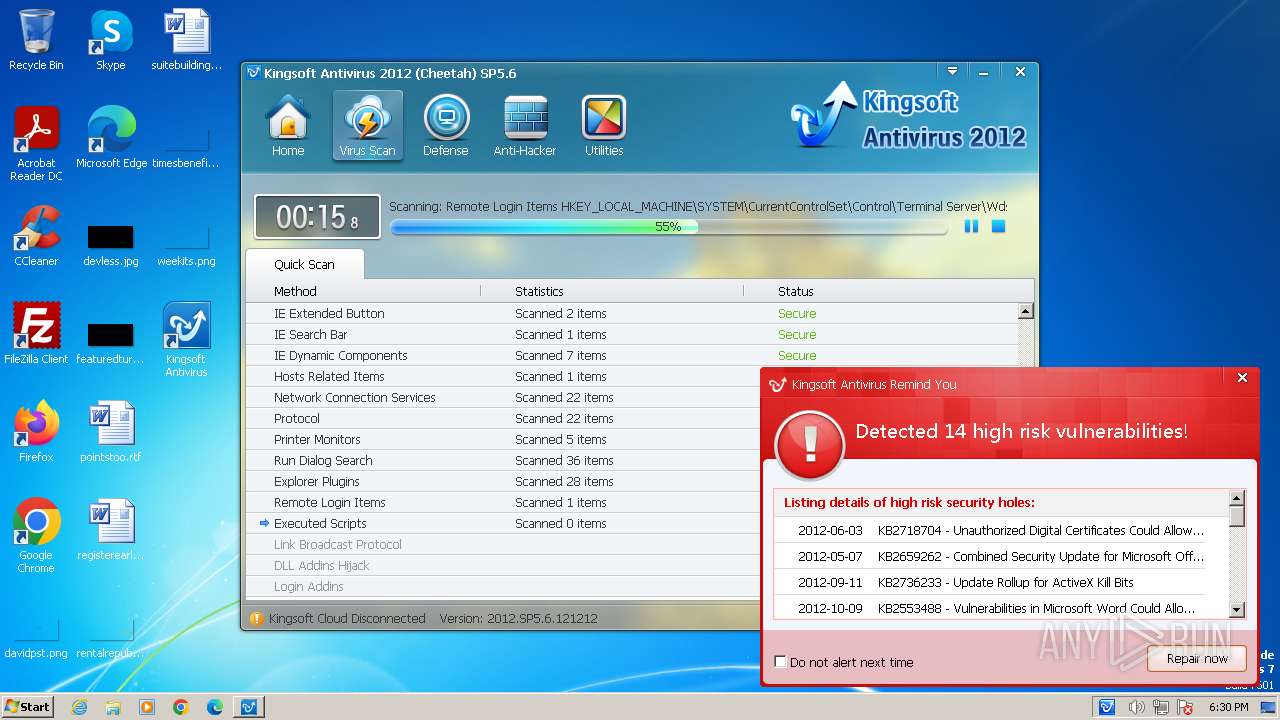
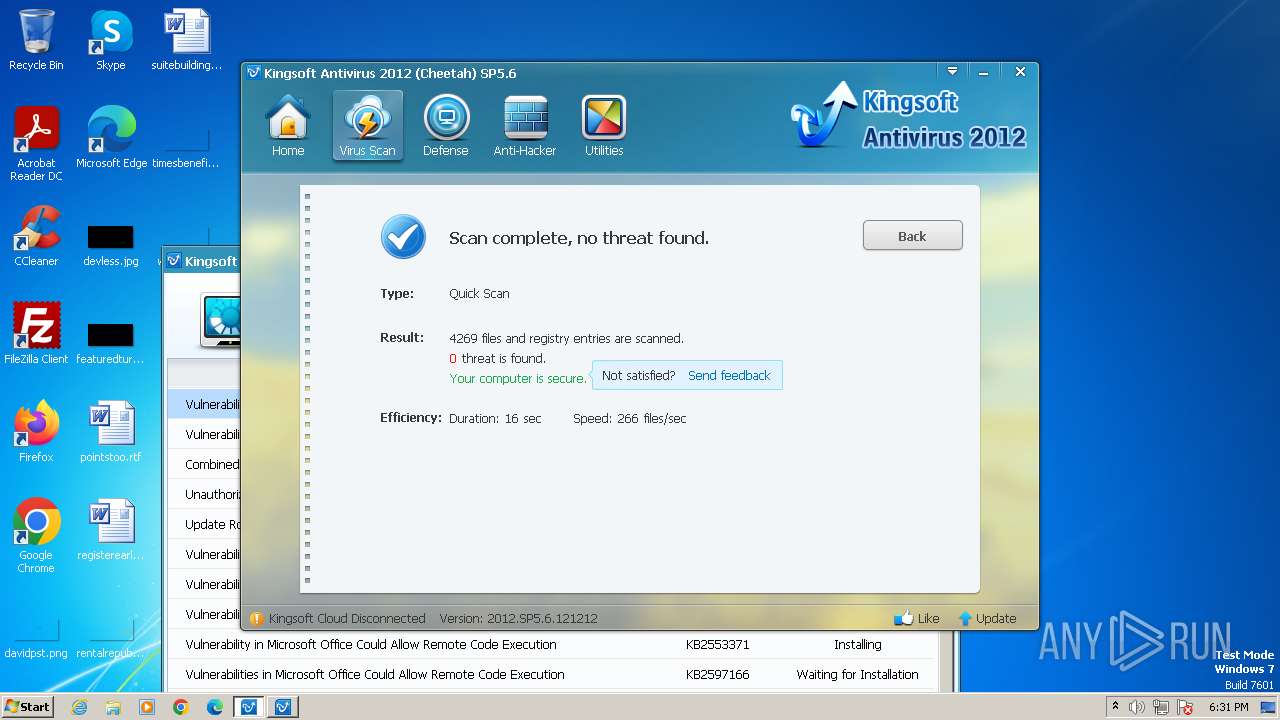
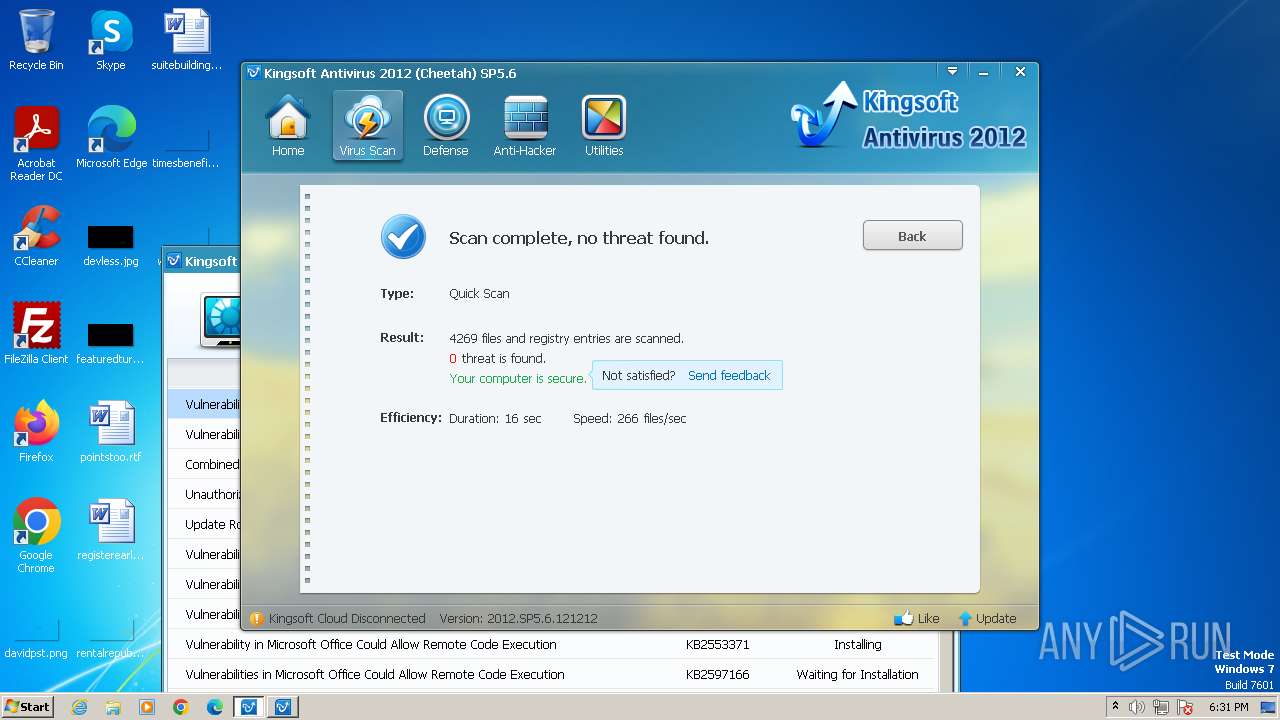
MALICIOUS
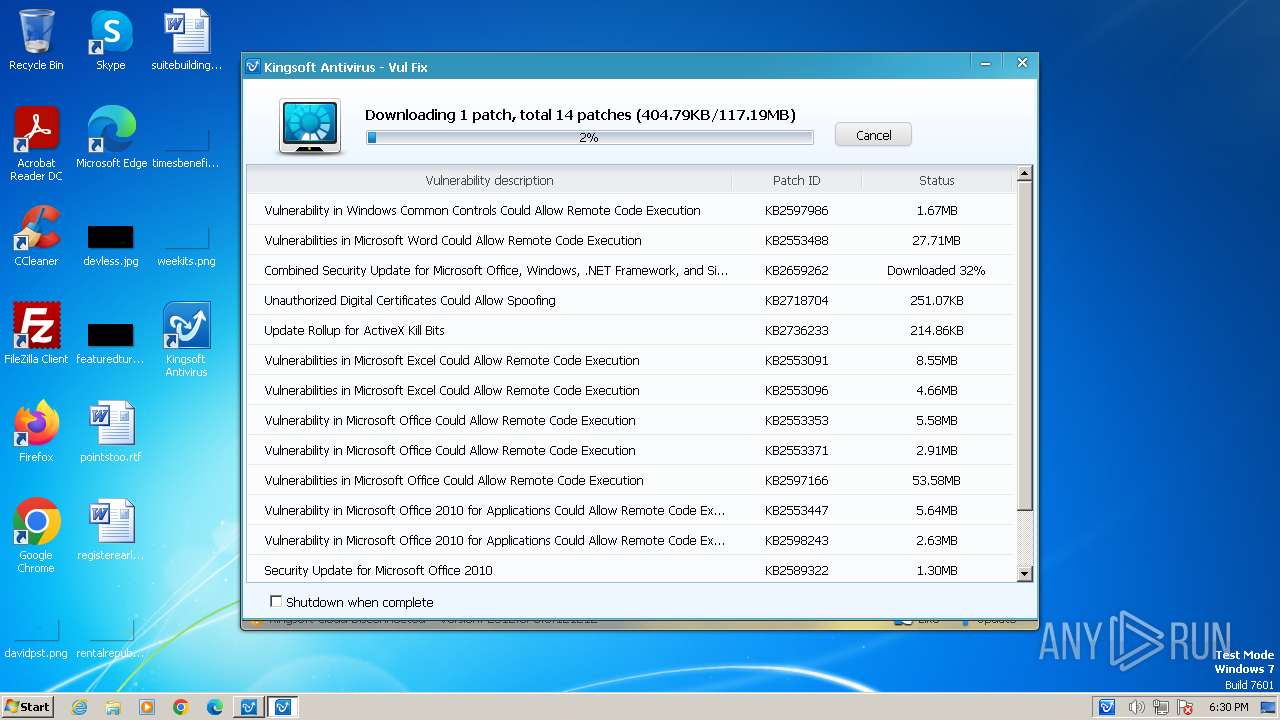
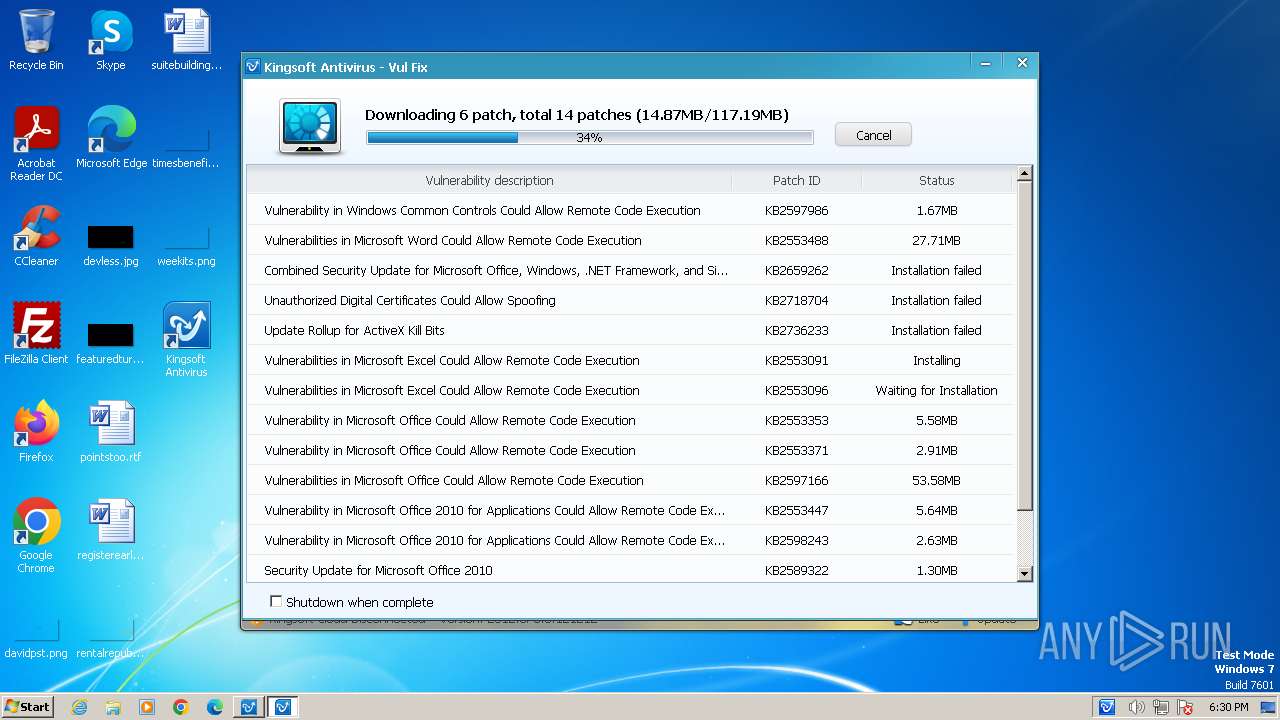
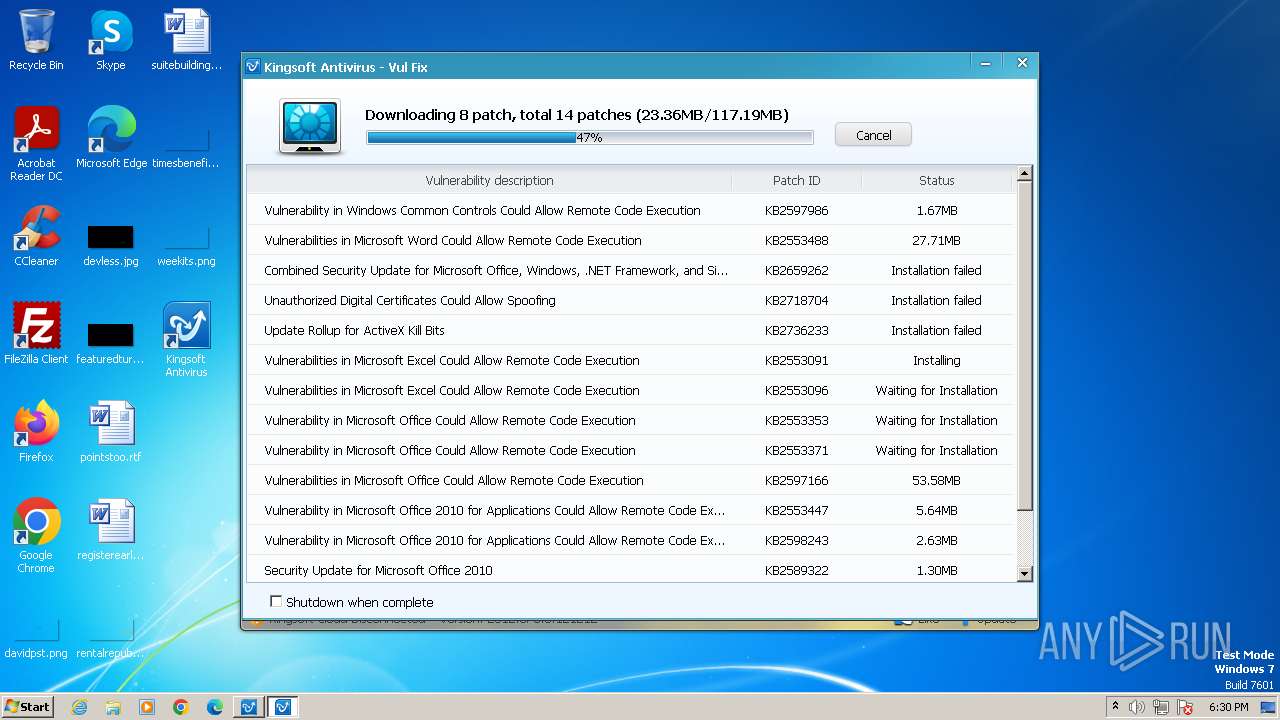
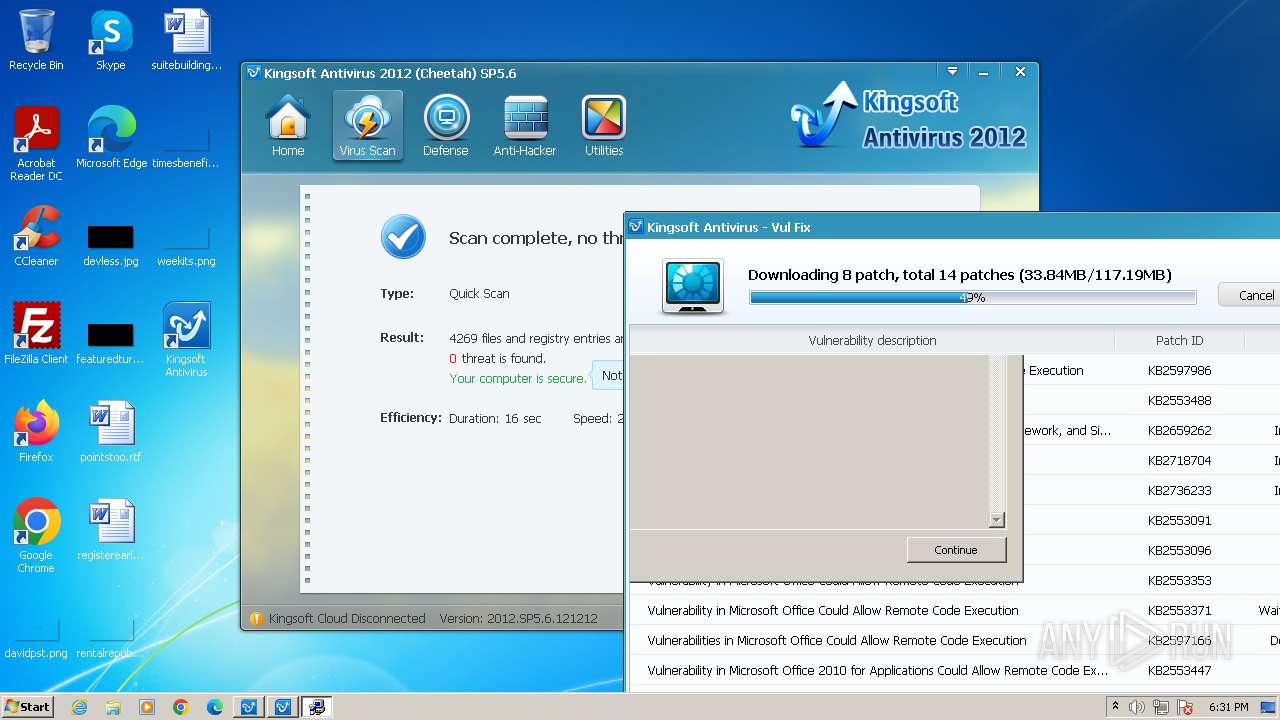
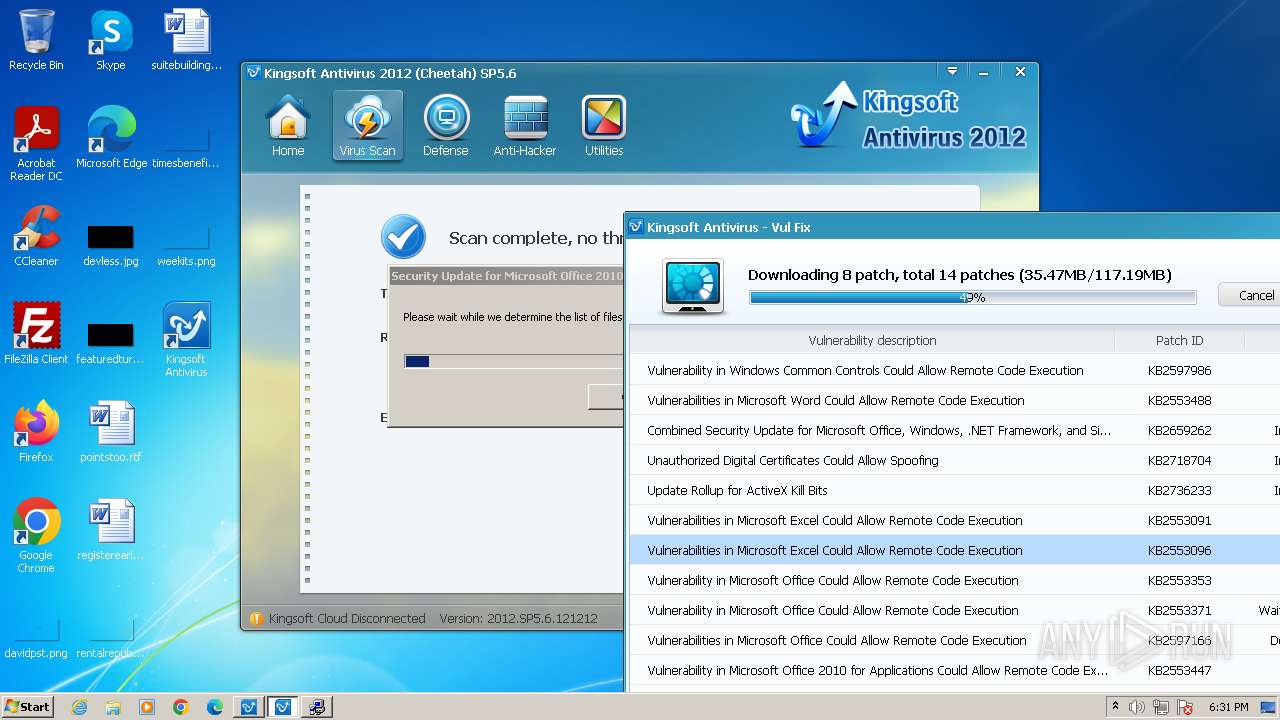
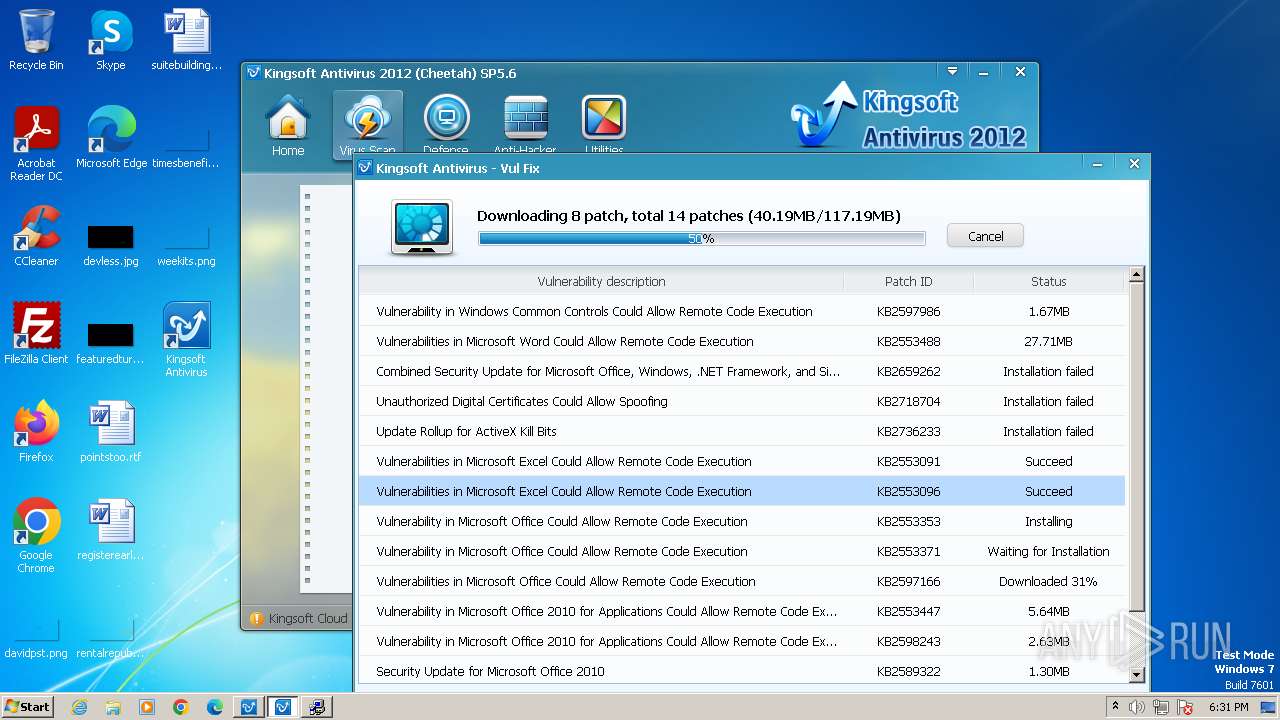
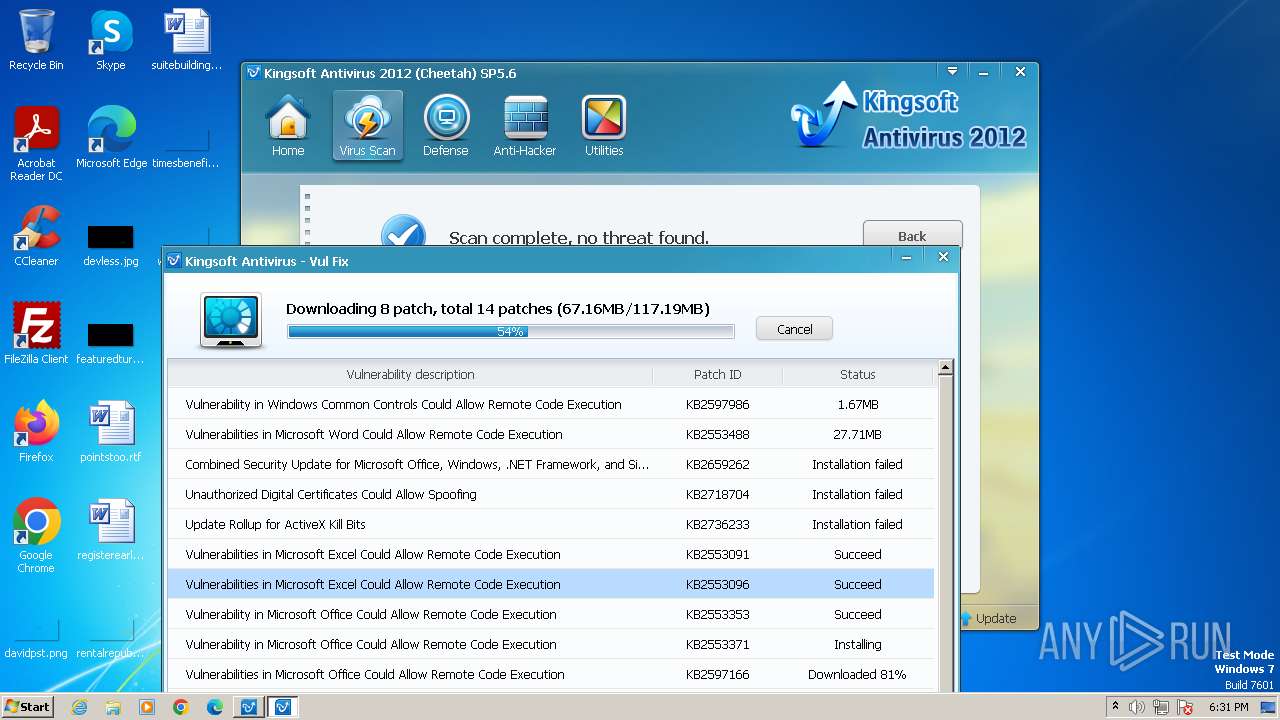
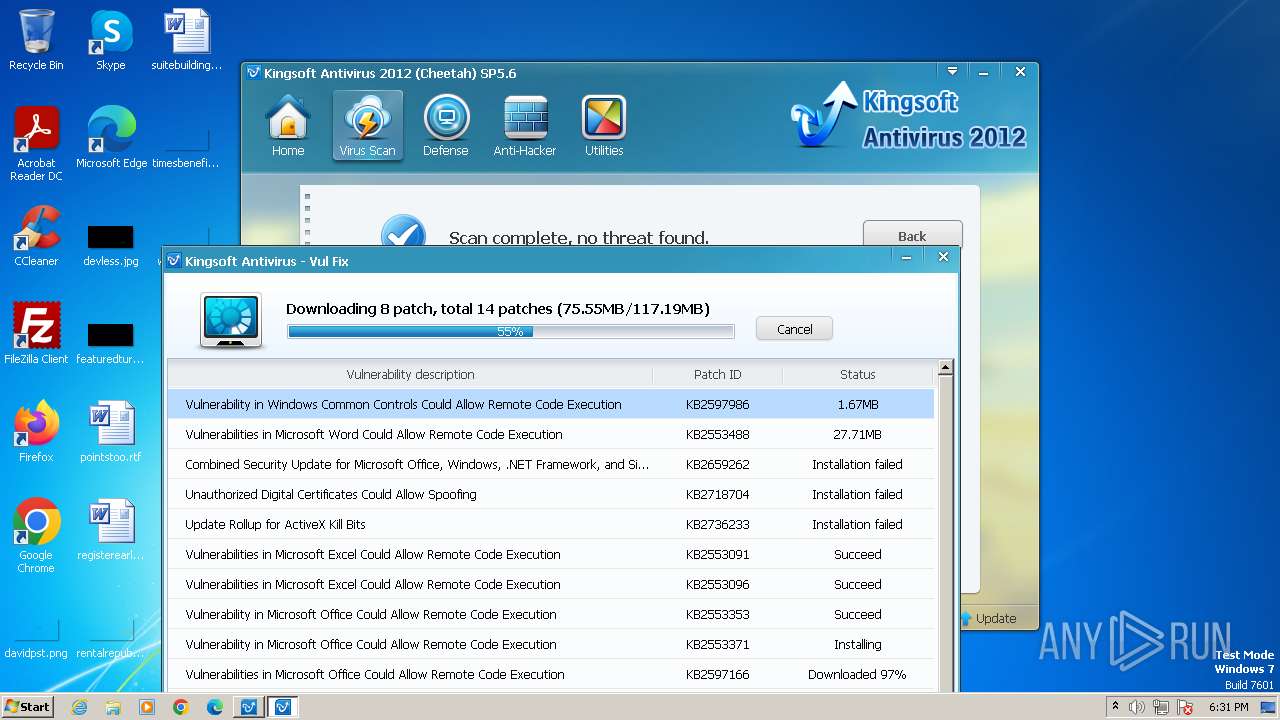
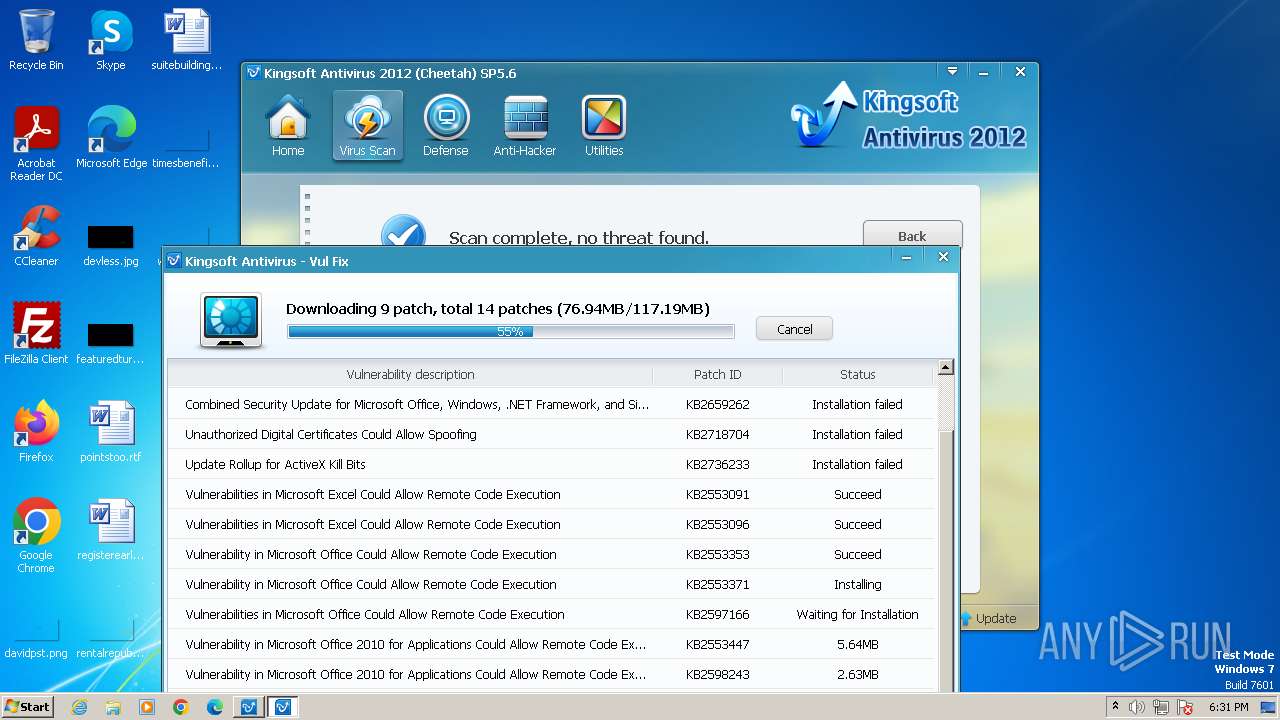
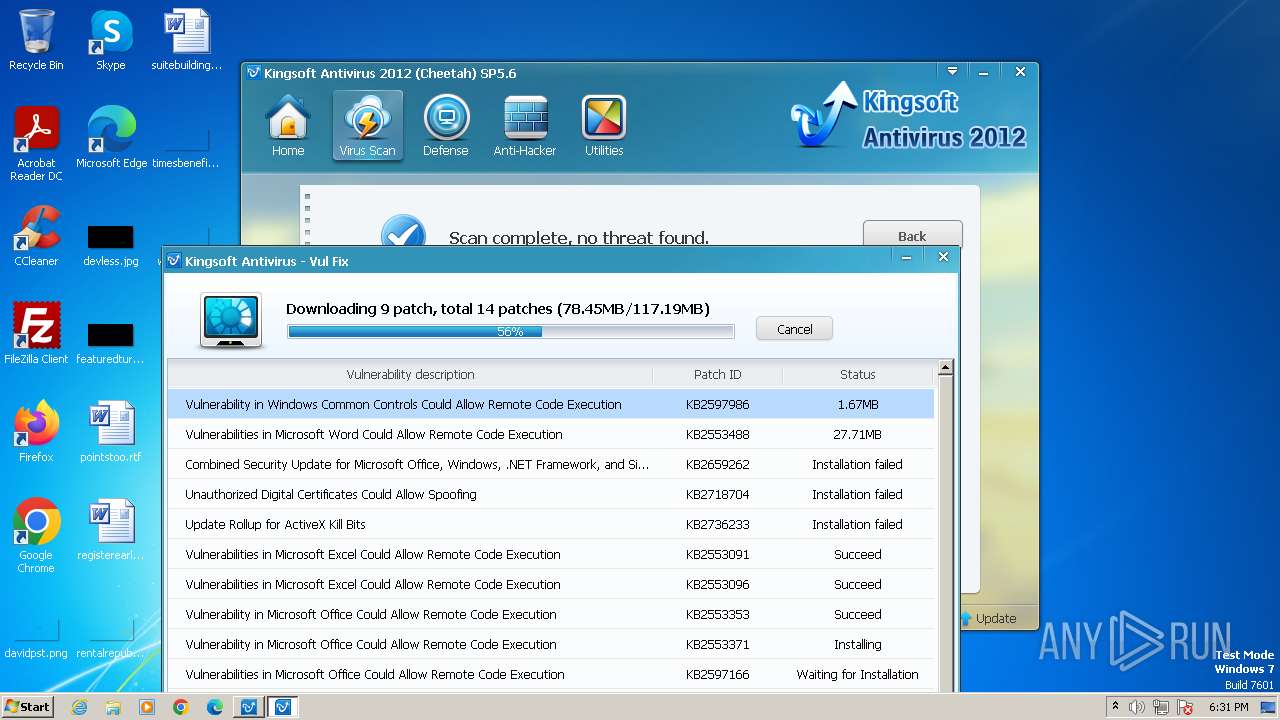
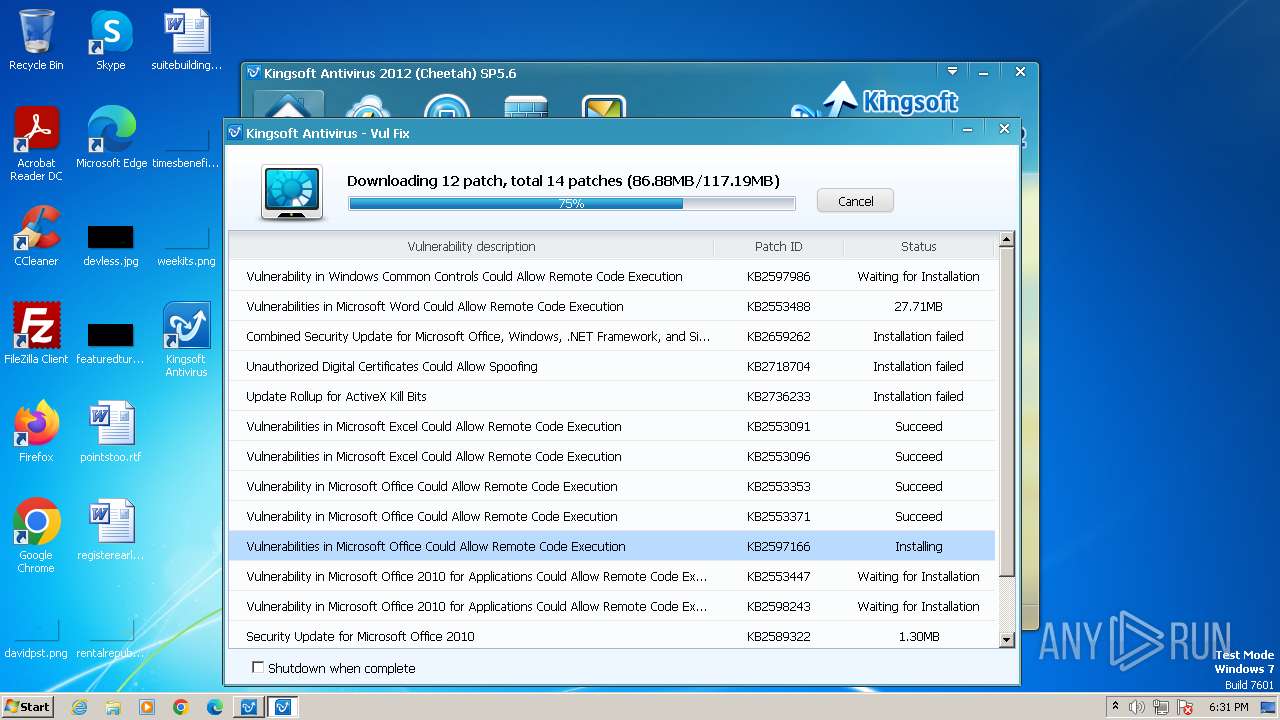
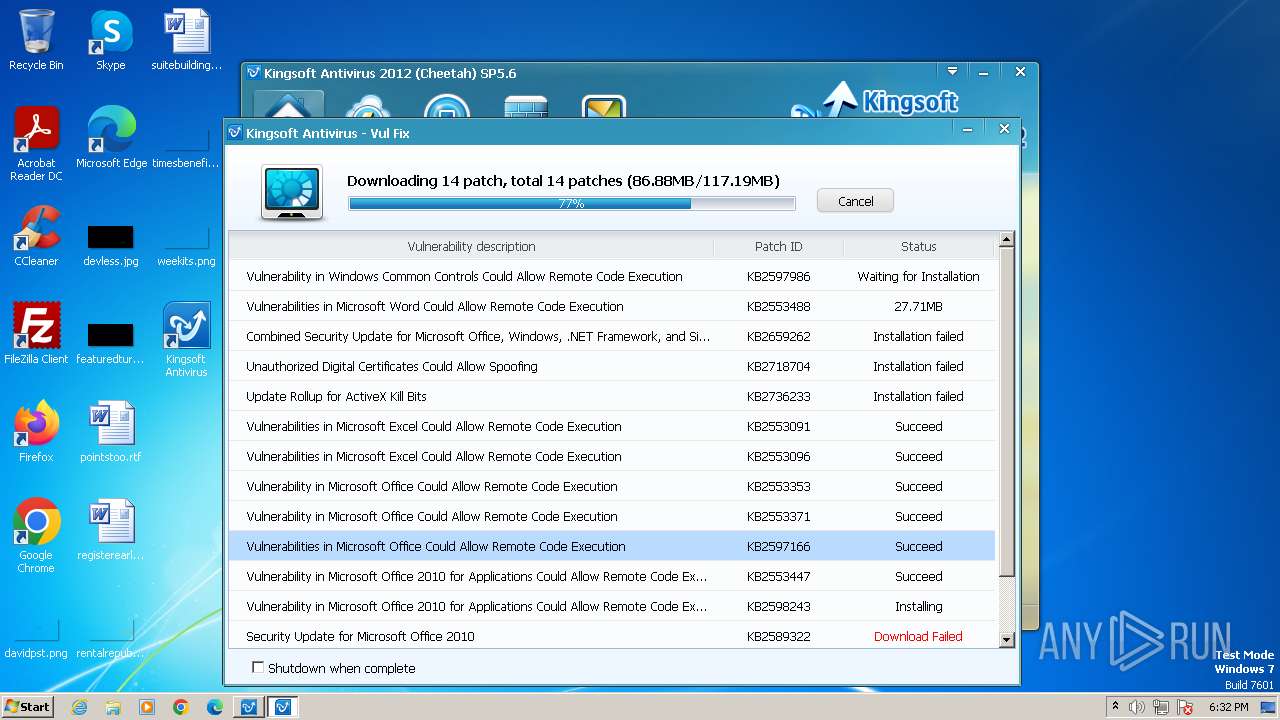
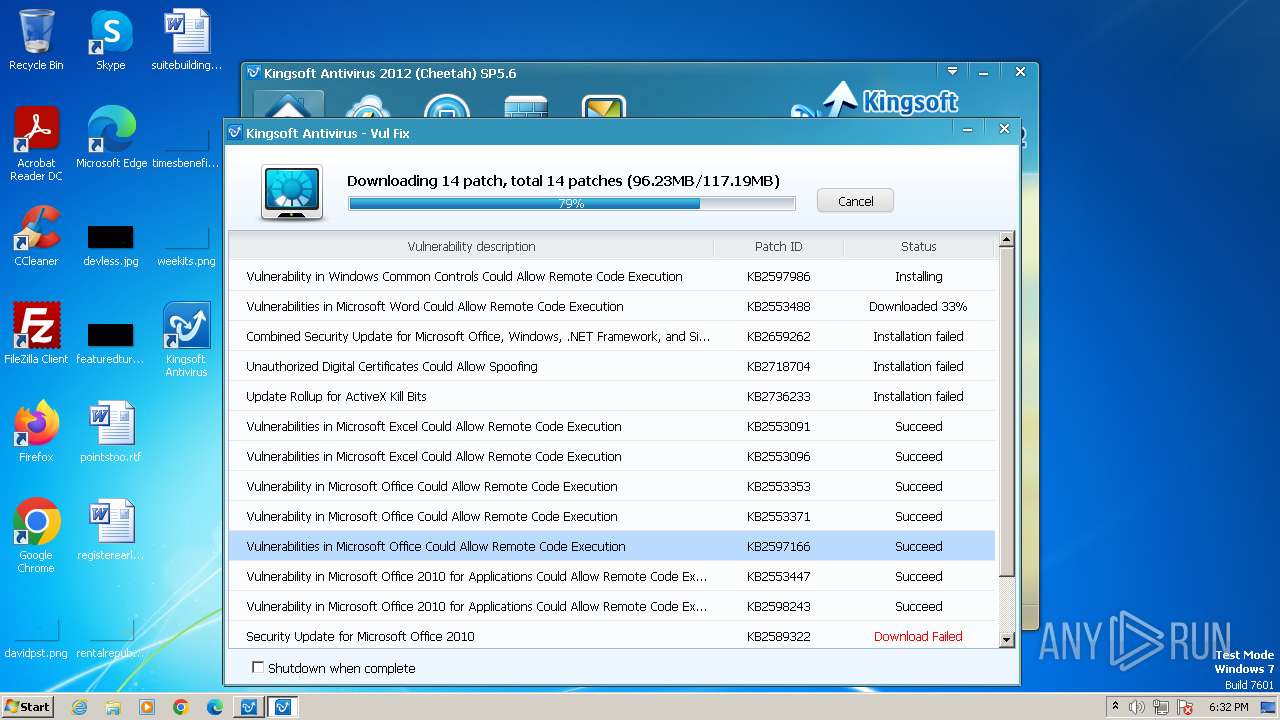
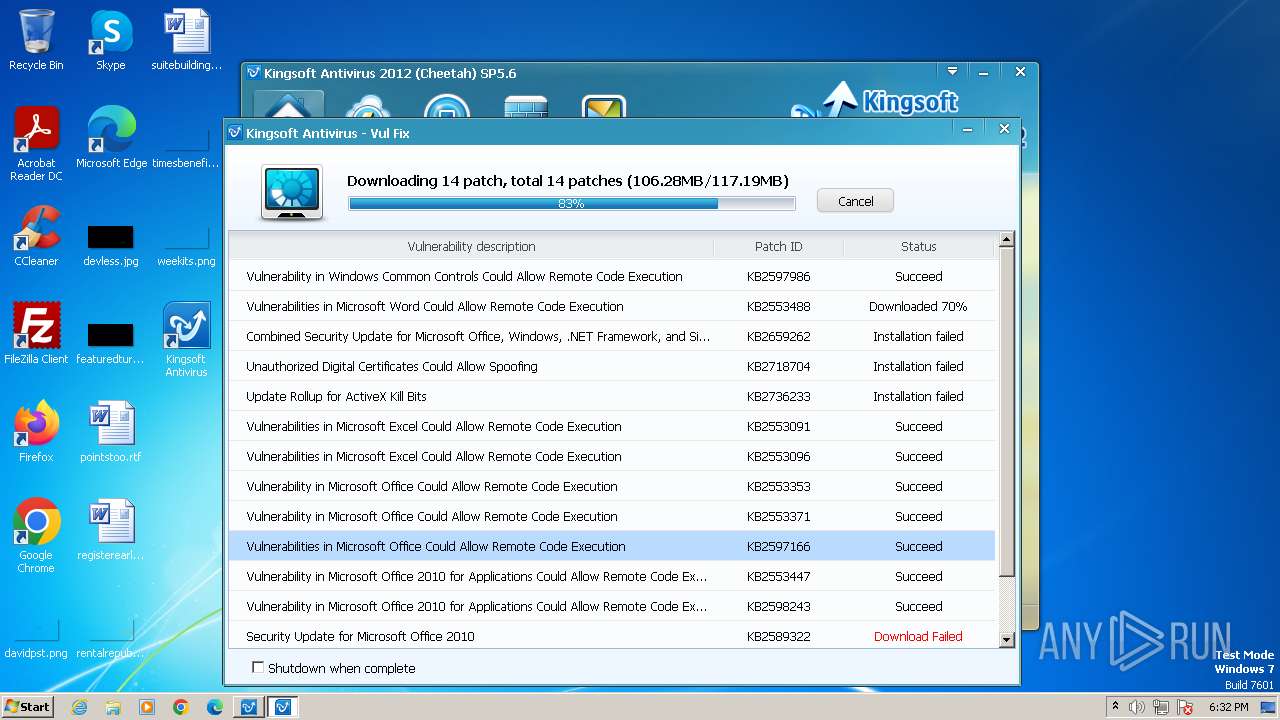
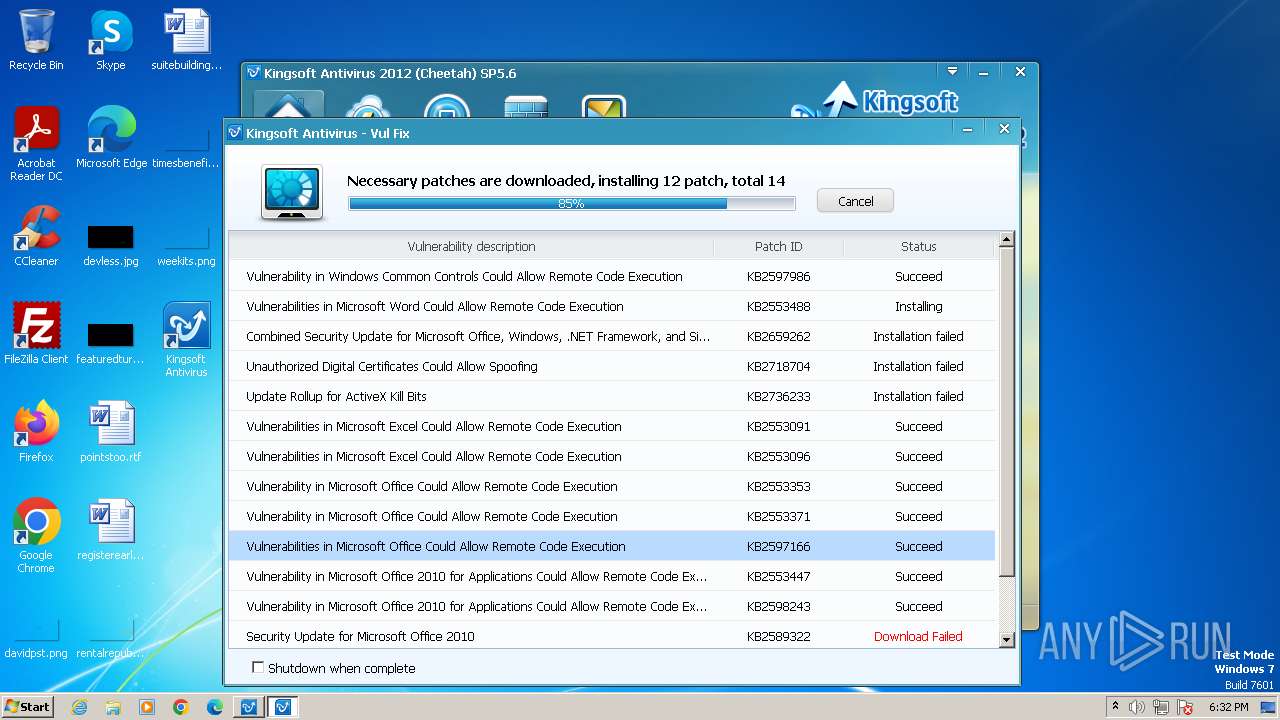
Drops the executable file immediately after the start
- kav_setup.exe (PID: 1776)
- kdrvmgr.exe (PID: 2404)
- kxescore.exe (PID: 3996)
- vulfix.exe (PID: 3392)
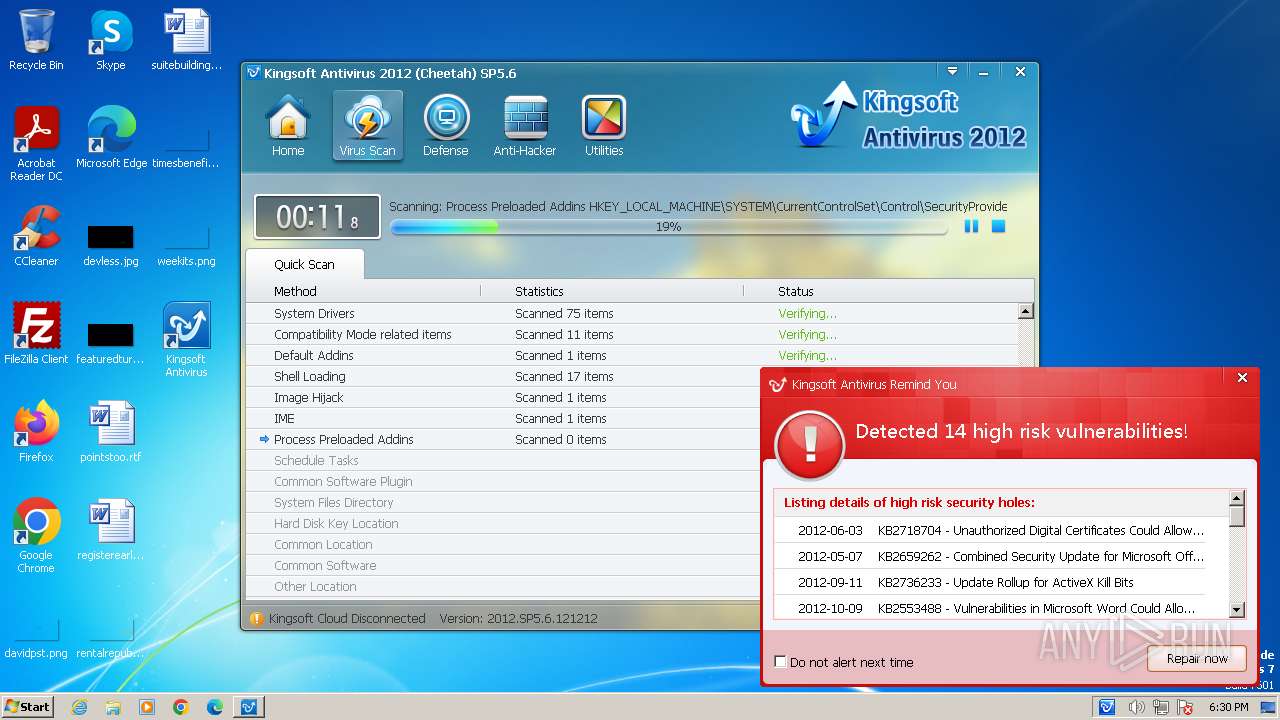
Creates a writable file in the system directory
- kav_setup.exe (PID: 1776)
- kavlog2.exe (PID: 2860)
- vulfix.exe (PID: 3392)
Changes the autorun value in the registry
- kav_setup.exe (PID: 1776)
Runs injected code in another process
- kxetray.exe (PID: 2580)
Application was injected by another process
- explorer.exe (PID: 1164)
Actions looks like stealing of personal data
- kscan.exe (PID: 1816)
The DLL Hijacking
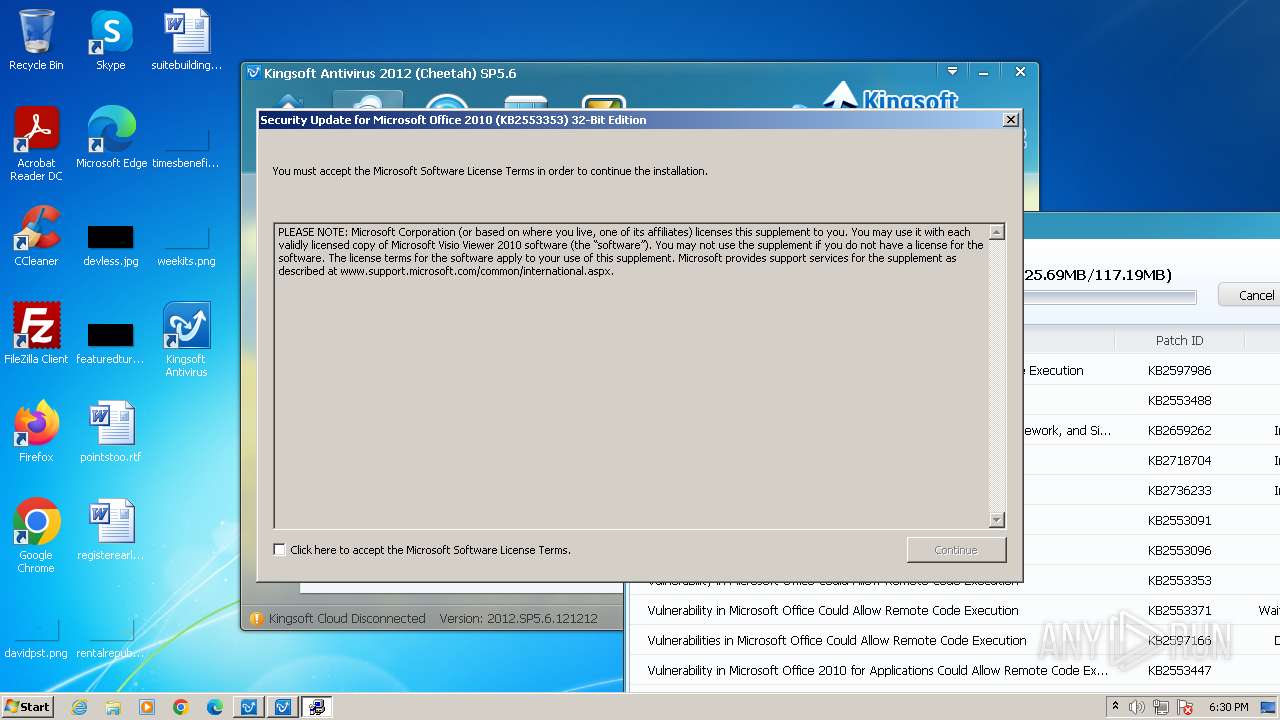
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
SUSPICIOUS
Reads the Internet Settings
- kav_setup.exe (PID: 1776)
- vulfix.exe (PID: 3392)
Creates files in the driver directory
- kav_setup.exe (PID: 1776)
Reads security settings of Internet Explorer
- kav_setup.exe (PID: 1776)
- vulfix.exe (PID: 3392)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Creates/Modifies COM task schedule object
- kav_setup.exe (PID: 1776)
Creates a software uninstall entry
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
Write to the desktop.ini file (may be used to cloak folders)
- kav_setup.exe (PID: 1776)
The process verifies whether the antivirus software is installed
- kavlog2.exe (PID: 2860)
- kxescore.exe (PID: 2856)
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- explorer.exe (PID: 1164)
- kdrvmgr.exe (PID: 2404)
- kislive.exe (PID: 2808)
- vulfix.exe (PID: 3392)
- kxescore.exe (PID: 3996)
- kscan.exe (PID: 1816)
- kdrvmgr.exe (PID: 3296)
- kislive.exe (PID: 2952)
- kxetray.exe (PID: 1956)
- wusa.exe (PID: 2100)
- wusa.exe (PID: 2848)
- kxetray.exe (PID: 3464)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- wusa.exe (PID: 3428)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2088)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2832)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Executes as Windows Service
- kxescore.exe (PID: 3996)
Creates or modifies Windows services
- kxescore.exe (PID: 3996)
Searches for installed software
- vulfix.exe (PID: 3392)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Executable content was dropped or overwritten
- kdrvmgr.exe (PID: 2404)
- kxescore.exe (PID: 3996)
- vulfix.exe (PID: 3392)
Drops a system driver (possible attempt to evade defenses)
- kdrvmgr.exe (PID: 2404)
- kxescore.exe (PID: 3996)
Read startup parameters
- kscan.exe (PID: 1816)
Checks Windows Trust Settings
- kxescore.exe (PID: 3996)
- vulfix.exe (PID: 3392)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
Starts application from unusual location
- kscan.exe (PID: 1816)
Connects to unusual port
- kscan.exe (PID: 1816)
- kxescore.exe (PID: 3996)
Reads settings of System Certificates
- vulfix.exe (PID: 3392)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Adds/modifies Windows certificates
- vulfix.exe (PID: 3392)
- kxescore.exe (PID: 3996)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
Process drops legitimate windows executable
- vulfix.exe (PID: 3392)
Connects to the server without a host name
- kscan.exe (PID: 1816)
- kxescore.exe (PID: 3996)
Process requests binary or script from the Internet
- vulfix.exe (PID: 3392)
Reads the Windows owner or organization settings
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
INFO
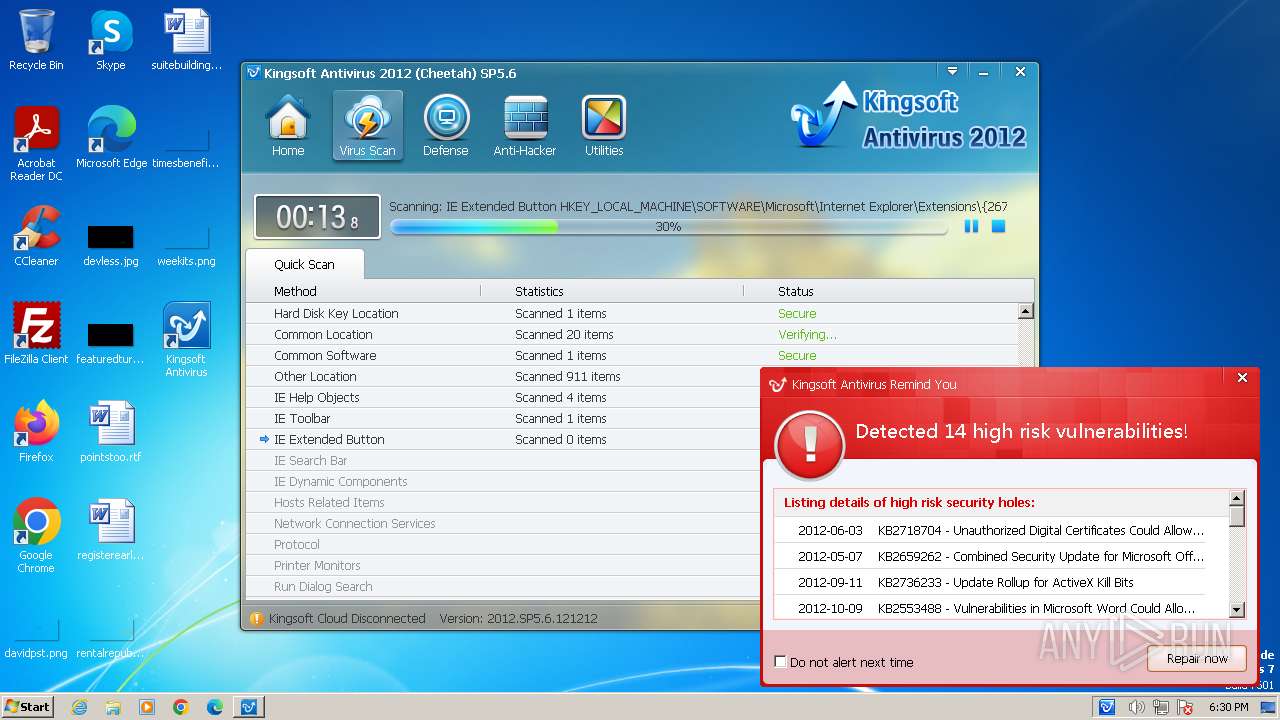
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Checks supported languages
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- kavlog2.exe (PID: 2860)
- vulfix.exe (PID: 3392)
- kxescore.exe (PID: 3996)
- kxescore.exe (PID: 2856)
- kscan.exe (PID: 1816)
- kislive.exe (PID: 2808)
- kdrvmgr.exe (PID: 2404)
- kxetray.exe (PID: 1956)
- kislive.exe (PID: 2952)
- kdrvmgr.exe (PID: 3296)
- kxetray.exe (PID: 3464)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2088)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2832)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Reads the computer name
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- kxescore.exe (PID: 2856)
- kxescore.exe (PID: 3996)
- vulfix.exe (PID: 3392)
- kscan.exe (PID: 1816)
- kislive.exe (PID: 2808)
- kdrvmgr.exe (PID: 2404)
- kxetray.exe (PID: 1956)
- kislive.exe (PID: 2952)
- kxetray.exe (PID: 3464)
- kdrvmgr.exe (PID: 3296)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2088)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2832)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
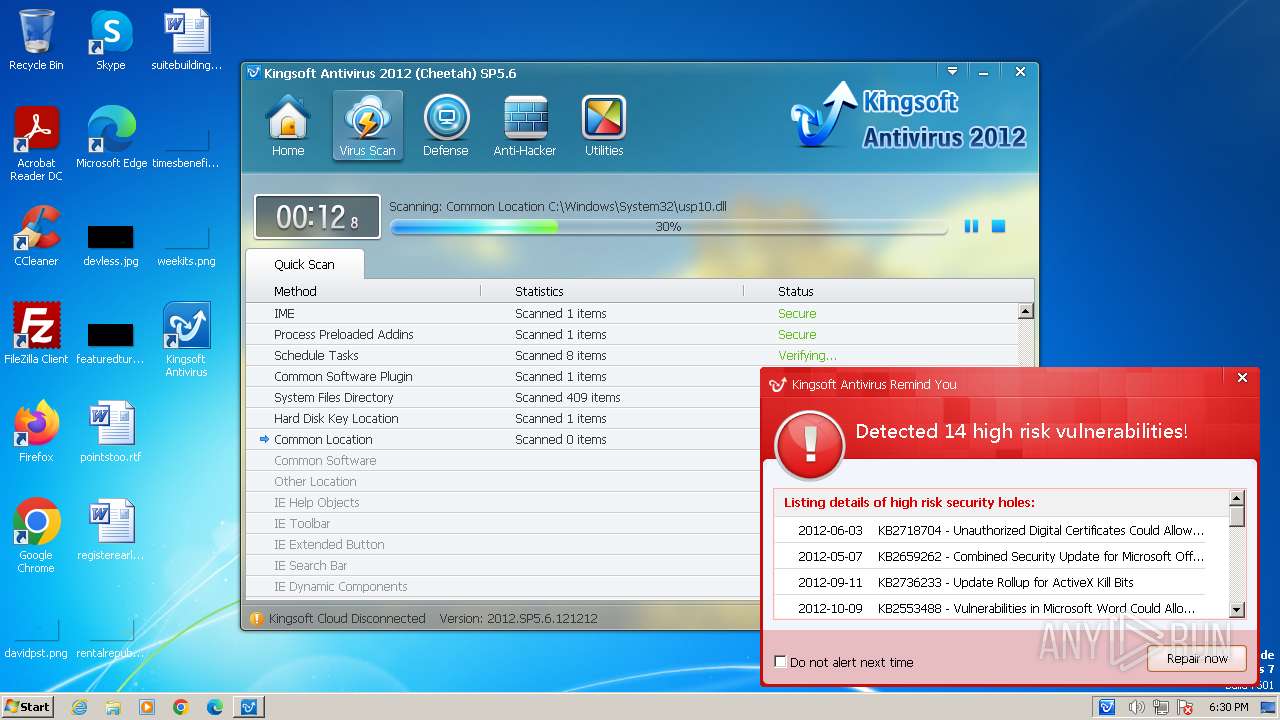
Create files in a temporary directory
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- kislive.exe (PID: 2808)
- kislive.exe (PID: 2952)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2088)
- vulfix.exe (PID: 3392)
- mscomctlocx2007-kb2687441-fullfile-x86-glb.exe (PID: 2832)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Checks proxy server information
- kav_setup.exe (PID: 1776)
- vulfix.exe (PID: 3392)
Creates files in the program directory
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- vulfix.exe (PID: 3392)
- kxescore.exe (PID: 3996)
- kscan.exe (PID: 1816)
- kislive.exe (PID: 2808)
- kislive.exe (PID: 2952)
Reads the machine GUID from the registry
- kav_setup.exe (PID: 1776)
- kxetray.exe (PID: 2580)
- kscan.exe (PID: 1816)
- kxescore.exe (PID: 3996)
- kislive.exe (PID: 2808)
- kislive.exe (PID: 2952)
- vulfix.exe (PID: 3392)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Reads Microsoft Office registry keys
- vulfix.exe (PID: 3392)
- kxetray.exe (PID: 2580)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Reads Environment values
- vulfix.exe (PID: 3392)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
Reads the software policy settings
- vulfix.exe (PID: 3392)
- kxescore.exe (PID: 3996)
- office2010-kb2553091-fullfile-x86-glb.exe (PID: 3292)
- office2010-kb2553096-fullfile-x86-glb.exe (PID: 3832)
- vviewer2010-kb2553353-fullfile-x86-glb.exe (PID: 4080)
- graph2010-kb2553371-fullfile-x86-glb.exe (PID: 2980)
- excel2010-kb2597166-fullfile-x86-glb.exe (PID: 3192)
- ace2010-kb2553447-fullfile-x86-glb.exe (PID: 492)
- vbe72010-kb2598243-fullfile-x86-glb.exe (PID: 3848)
- word2010-kb2553488-fullfile-x86-glb.exe (PID: 3524)
Creates files or folders in the user directory
- vulfix.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1970:01:05 19:37:36+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 397312 |
| InitializedDataSize: | 24576 |
| UninitializedDataSize: | 708608 |
| EntryPoint: | 0x10e160 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2013.3.27.883 |
| ProductVersionNumber: | 9.0.36828.195 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Kingsoft Corporation |
| FileDescription: | Kingsoft Antivirus Install |
| FileVersion: | 2013,03,27,195 |
| InternalName: | kpacket |
| LegalCopyright: | Copyright (C) 1998-2013 Kingsoft Corporation |
| OriginalFileName: | kpacket.exe |
| ProductName: | Kingsoft Internet Security |
| ProductVersion: | 9,0,102364,195 |
Total processes
124
Monitored processes
28
Malicious processes
27
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "c:\program files\kingsoft\kingsoft antivirus\hotfix\ace2010-kb2553447-fullfile-x86-glb.exe" /q | C:\Program Files\kingsoft\kingsoft antivirus\hotfix\ace2010-kb2553447-fullfile-x86-glb.exe | — | vulfix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Security Update for Microsoft Office 2010 (KB2553447) 32-Bit Edition Exit code: 0 Version: 14.0.6123.5001 Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\AppData\Local\Temp\kav_setup.exe" | C:\Users\admin\AppData\Local\Temp\kav_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Antivirus Install Exit code: 1 Version: 2013,03,27,195 Modules
| |||||||||||||||
| 1816 | "c:\program files\kingsoft\kingsoft antivirus\kscan.exe" | C:\Program Files\kingsoft\kingsoft antivirus\kscan.exe | kxescore.exe | ||||||||||||
User: SYSTEM Company: Kingsoft Corporation Integrity Level: SYSTEM Description: Kingsoft Scan Process Exit code: 0 Version: 2012,03,21,22 Modules
| |||||||||||||||
| 1956 | "c:\program files\kingsoft\kingsoft antivirus\kxetray.exe" /autorun /GetConnectStatus | C:\Program Files\kingsoft\kingsoft antivirus\kxetray.exe | — | kislive.exe | |||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Antivirus Tray Exit code: 2 Version: 2012,09,28,153 Modules
| |||||||||||||||
| 2088 | "c:\program files\kingsoft\kingsoft antivirus\hotfix\mscomctlocx2007-kb2687441-fullfile-x86-glb.exe" /q | C:\Program Files\kingsoft\kingsoft antivirus\hotfix\mscomctlocx2007-kb2687441-fullfile-x86-glb.exe | — | vulfix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Security Update for Microsoft Office 2007 suites (KB2687441) 32-Bit Edition Exit code: 17028 Version: 12.0.6662.5004 Modules
| |||||||||||||||
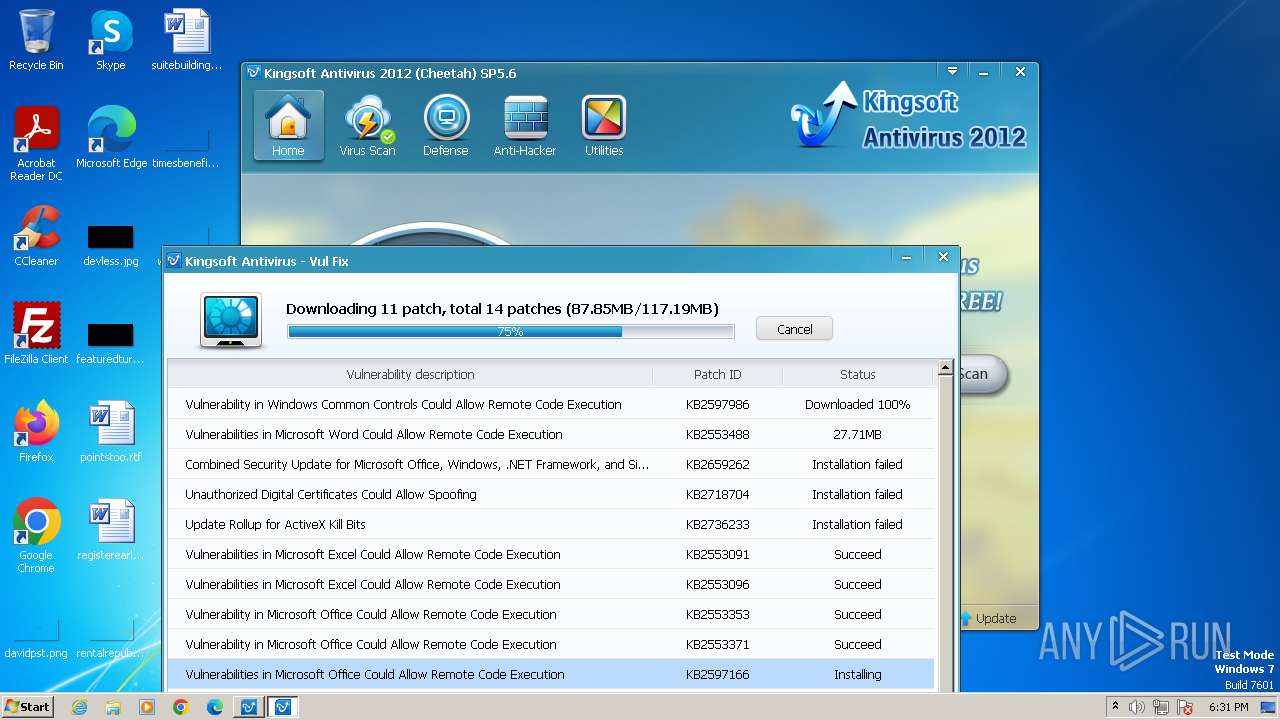
| 2100 | C:\Windows\system32\wusa.exe "c:\program files\kingsoft\kingsoft antivirus\hotfix\Windows6.1-KB2659262-x86.msu" /quiet /norestart | C:\Windows\System32\wusa.exe | — | vulfix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 1726 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "c:\program files\kingsoft\kingsoft antivirus\kdrvmgr.exe" /i /kavbootc | C:\Program Files\kingsoft\kingsoft antivirus\kdrvmgr.exe | kxetray.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Driver Manager Exit code: 1 Version: 2011,11,09,1827 Modules
| |||||||||||||||
| 2580 | "c:\program files\kingsoft\kingsoft antivirus\kxetray.exe" /kismain /autorun /kislive /devmgr | C:\Program Files\kingsoft\kingsoft antivirus\kxetray.exe | kav_setup.exe | ||||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Antivirus Tray Exit code: 0 Version: 2012,09,28,153 Modules
| |||||||||||||||
| 2808 | "kislive.exe" /autorun /std | C:\Program Files\kingsoft\kingsoft antivirus\kislive.exe | — | kxetray.exe | |||||||||||
User: admin Company: Kingsoft Corporation Integrity Level: HIGH Description: Kingsoft Antivirus Online Upgrade Exit code: 13 Version: 2012,10,18,155 Modules
| |||||||||||||||
Total events
134 996
Read events
134 153
Write events
676
Delete events
167
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C470000000002000000000010660000000100002000000046E6AD8122E9861F341A0D40D1FF4721F882F48A226CD1AF18D32C07BB5BC265000000000E80000000020000200000005F51F3BD434D51156926B174D5838199BC7567D084F65786F14DE6A76248A6C330000000991C275E3964C9BF40C213EBB05A6684B89027C1D29984947E1758C693673D79F8D1C6FC9F973AC8C80703830F2D5806400000002638093F5F86E32F006C70F181BA7A6F4E231C1D6853B2C59A890CF99AF259265193ACBDB7304910E8C445D82CCCAFBBB9E4391A3950CADDDCA350482B94FF99 | |||
| (PID) Process: | (1776) kav_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9B7A98EC-7EF9-468c-ACC8-37C793DBD7E0}\Implemented Categories\{A5F7140E-4311-4ef9-AABC-F55941B5EBE5} |
| Operation: | write | Name: | idno |
Value: 0 | |||
| (PID) Process: | (1776) kav_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9B7A98EC-7EF9-468c-ACC8-37C793DBD7E0}\Implemented Categories\{A5F7140E-4311-4ef9-AABC-F55941B5EBE5} |
| Operation: | write | Name: | idno |
Value: 1 | |||
| (PID) Process: | (1776) kav_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9B7A98EC-7EF9-468c-ACC8-37C793DBD7E0}\Implemented Categories\{A5F7140E-4311-4ef9-AABC-F55941B5EBE5} |
| Operation: | write | Name: | idex |
Value: d10fc01f9ce51b3cf625aa983bd2394c | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\NccQngn\Ybpny\Grzc\xni_frghc.rkr |
Value: 00000000000000000100000000000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004D03000042899501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\NccQngn\Ybpny\Grzc\xni_frghc.rkr |
Value: 000000000000000001000000EF140000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004D030000319E9501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (1776) kav_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1776) kav_setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
Executable files
23
Suspicious files
158
Text files
111
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\110.jpg | image | |
MD5:AC67BADDE47331706365BABD6FEBC597 | SHA256:61BDE2CE69A41B19E7F53E7E24F446550BD33677AAE174286909AE6D3991EF11 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\31.png | image | |
MD5:5A80E677EBAD1B2A47FA2FEF860F1F3E | SHA256:3148EFF9147FE775BFC60BFCE7516182439256914B4AC120F92A5C7EFB439787 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\2_newksafe.jpg | image | |
MD5:064A936DE2CC61B5A171C03112233044 | SHA256:E390B73C761C2842D58F29899B652FA9A394863C7D167EEDE34AD1E0A0C30AE6 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\1.jpg | image | |
MD5:C992B92FE34D3CBF0C1CDD86A13BE9E4 | SHA256:202586F3E85AB3D12E302F9C4AC08BFBFC076433024311AF819FFF1494590D98 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\20.png | image | |
MD5:88057614148184596A455A10721258BC | SHA256:6E1C00E95D1F6CEFE2451D3DAA873524A5F5C387C43B7F1D60CCF946EBD364F1 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\19.png | image | |
MD5:AD7C4426E0026E9A2350A9F19BD1DEC4 | SHA256:1958B4C76FC37BBB7906123434065FE6DCA25CCF2B8FC8B1E27FE4487D79276F | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\34.png | image | |
MD5:DB23EB66E739B6C292F32B737AB34F91 | SHA256:A02468AD18DD764E2290FEA9C5E4FCB115C409643AB5000FAAB03440BB3650B5 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\2_newpcmgr.jpg | image | |
MD5:1540889A696607BF13DC1E800D15D0EA | SHA256:507E0288F3A88667EE7E91F9E06EE6B09F436C1448B2E1ADE8949F36D295C739 | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\32.png | image | |
MD5:EE2AD82D4D3649EA10A99F4121A2E70D | SHA256:3A53FE097501C7241594DDFD479224A2058AC27CFE6937E610F1DA8AEC7C0C2A | |||
| 1776 | kav_setup.exe | C:\Users\admin\AppData\Local\Temp\kantivirus\~17fd3c\install_res\63.png | image | |
MD5:FAC8E40988C792FE873A76AB29F4D72A | SHA256:94BD7A78E692438FC7ABD48B168D05737C185E14AFDB6A0D767B2E89A70368FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
247
TCP/UDP connections
320
DNS requests
32
Threats
163
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | kav_setup.exe | GET | 200 | 103.235.46.40:80 | http://www.baidu.com/ | unknown | html | 2.33 Kb | unknown |
1816 | kscan.exe | GET | 200 | 104.22.54.83:80 | http://update.kingsoft.jp/duba/kis/2011/kiscommon/app/security/fsgs/kswfsign | unknown | compressed | 692 b | unknown |
3996 | kxescore.exe | POST | 200 | 110.43.89.23:80 | http://110.43.89.23/kns-query | unknown | text | 36 b | unknown |
3996 | kxescore.exe | POST | 200 | 120.92.73.121:80 | http://cf.duba.net/query3 | unknown | binary | 75 b | unknown |
1816 | kscan.exe | POST | 405 | 58.222.51.1:80 | http://cu003.www.duba.net/duba/tools/dubatools/qsindex.dat | unknown | html | 166 b | unknown |
3996 | kxescore.exe | POST | 200 | 120.92.73.121:80 | http://cf.duba.net/query3 | unknown | binary | 149 b | unknown |
2580 | kxetray.exe | GET | 200 | 58.222.51.1:80 | http://cu003.www.duba.net/duba/tools/dubatools/usb/scanquestionnaire.ini | unknown | text | 585 b | unknown |
1816 | kscan.exe | GET | 200 | 111.62.34.100:80 | http://fsigns.duba.net/df/fm | unknown | compressed | 879 b | unknown |
3996 | kxescore.exe | POST | 200 | 110.43.89.23:80 | http://kns.duba.net/kns-query | unknown | text | 36 b | unknown |
1776 | kav_setup.exe | POST | 200 | 139.9.39.206:80 | http://infoc2.duba.net/c/ | unknown | text | 36 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1776 | kav_setup.exe | 103.235.46.40:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
1776 | kav_setup.exe | 139.9.39.206:80 | infoc2.duba.net | Huawei Cloud Service data center | CN | unknown |
3996 | kxescore.exe | 122.209.126.122:80 | — | ARTERIA Networks Corporation | JP | unknown |
3996 | kxescore.exe | 110.43.89.23:80 | kns.duba.net | IDC, China Telecommunications Corporation | CN | unknown |
3996 | kxescore.exe | 120.52.95.239:80 | cv.duba.net | China Unicom IP network | CN | unknown |
2580 | kxetray.exe | 120.92.75.29:80 | b.api.pc120.com | Beijing Kingsoft Cloud Internet Technology Co., Ltd | CN | unknown |
2580 | kxetray.exe | 218.12.76.156:80 | download.duba.net | CHINA UNICOM China169 Backbone | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.baidu.com |
| whitelisted |
softdl.pcdoctor.kingsoft.com |
| unknown |
infoc2.duba.net |
| malicious |
kns.duba.net |
| unknown |
cloud-q.kingsoft.jp |
| unknown |
cv.duba.net |
| whitelisted |
download.duba.net |
| unknown |
b.api.pc120.com |
| unknown |
stat.ijinshan.com |
| unknown |
cloud-api.duba.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2580 | kxetray.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
1816 | kscan.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
2580 | kxetray.exe | Potentially Bad Traffic | ET HUNTING Suspicious Mozilla User-Agent - Likely Fake (Mozilla/4.0) |
3996 | kxescore.exe | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
3392 | vulfix.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3392 | vulfix.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3392 | vulfix.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3392 | vulfix.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
155 ETPRO signatures available at the full report
Process | Message |
|---|---|
kavlog2.exe | _tWinMain Start. |