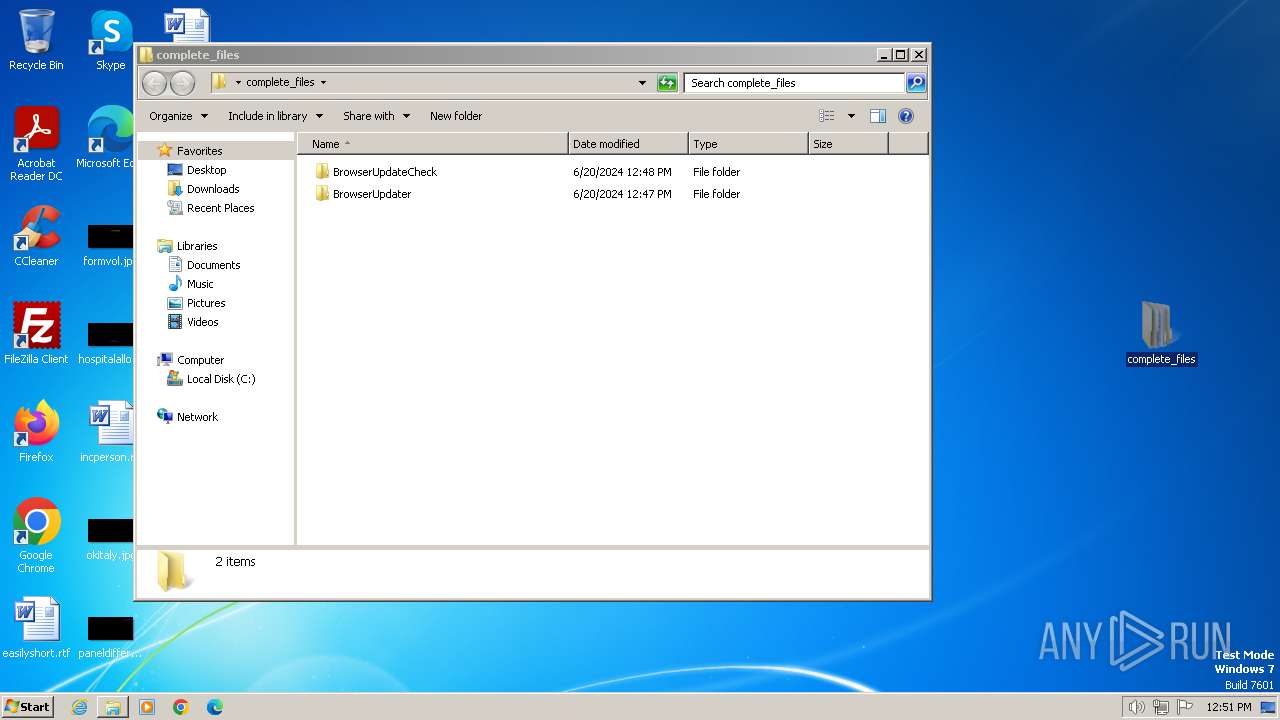
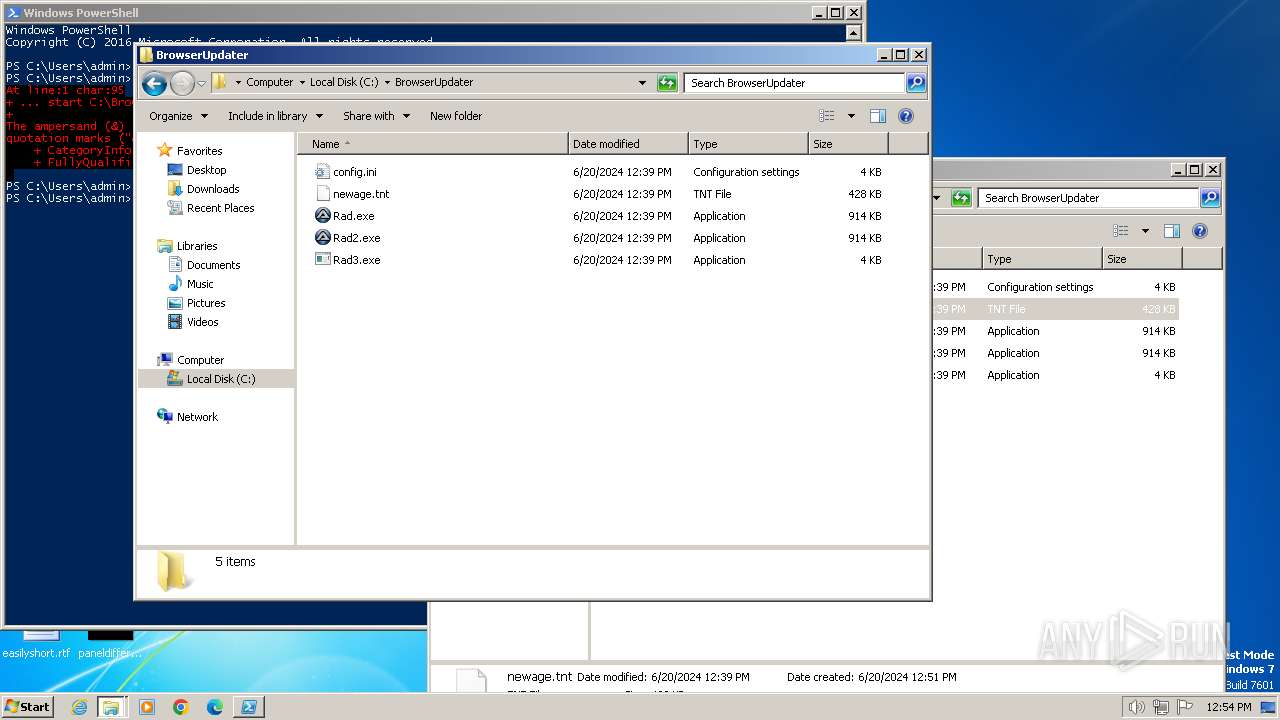
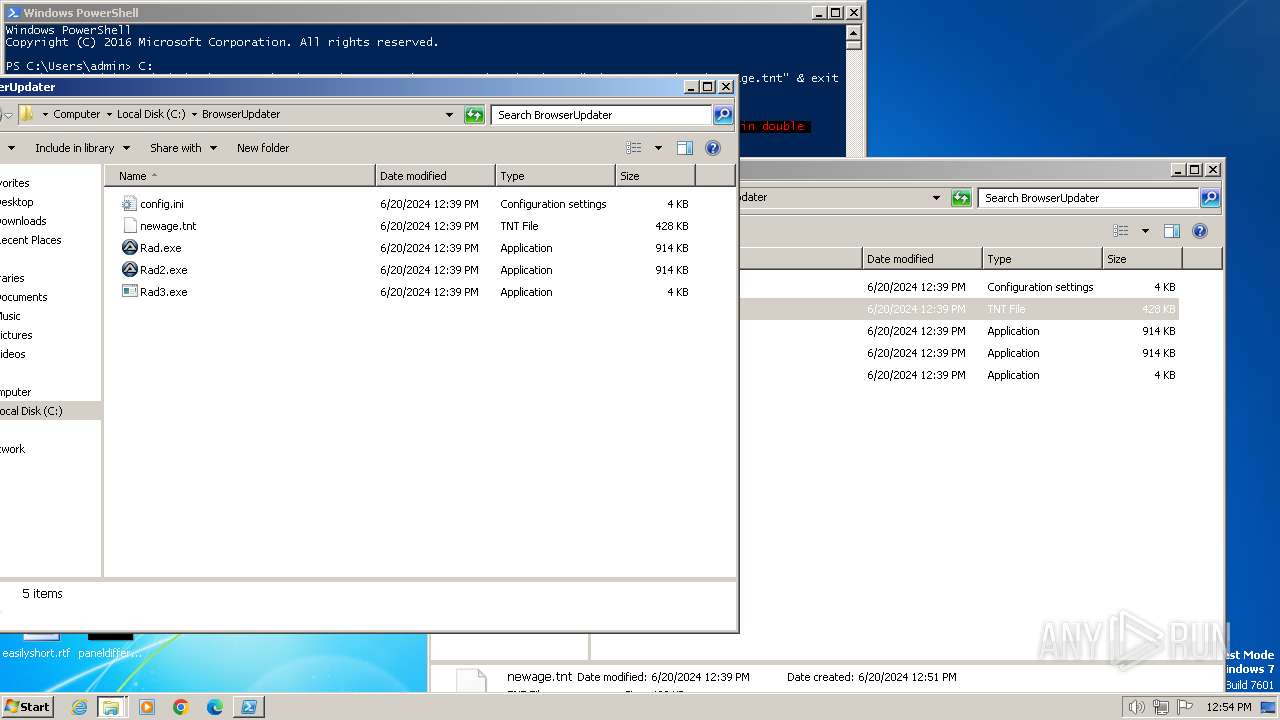
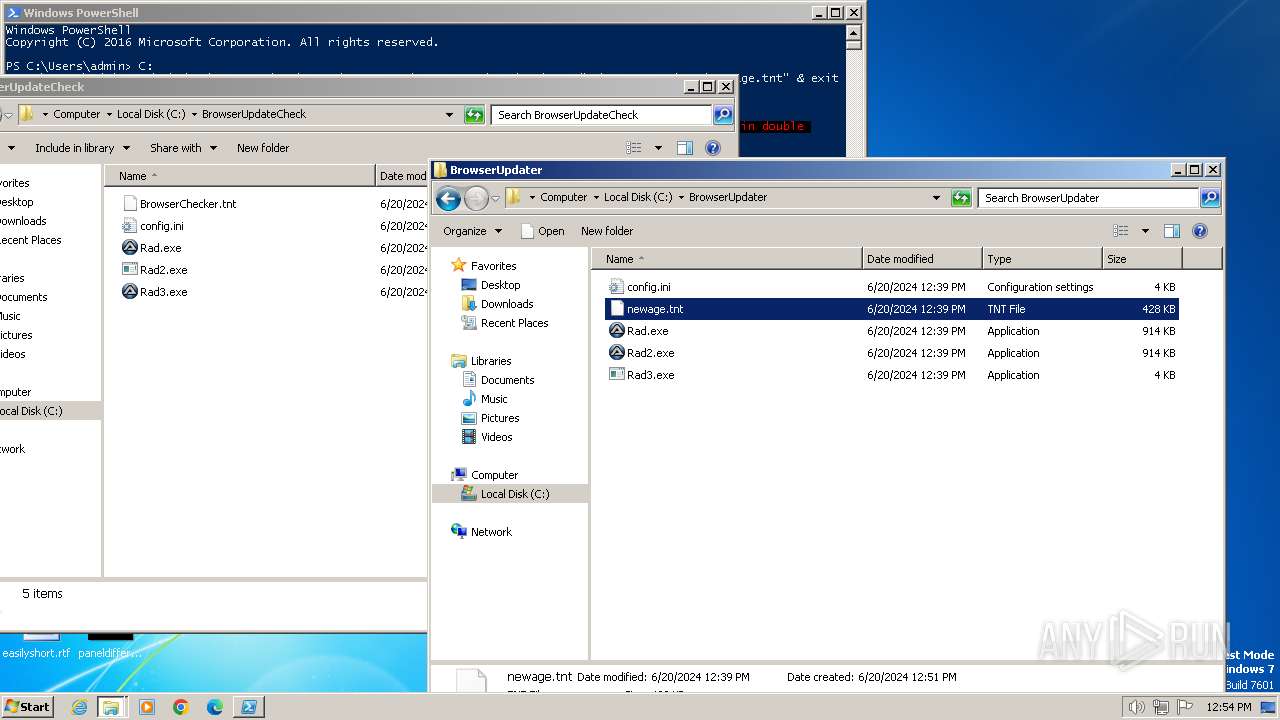
| File name: | complete_files.zip |
| Full analysis: | https://app.any.run/tasks/3b67ab49-64f5-4b6a-ac4b-a45a6cc9c96f |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2024, 11:50:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 6026279BA6ADAEA3B1B60AA2ACDB2C07 |
| SHA1: | 4D73FDEB547A489F4837FF392AA5B210BEE18825 |
| SHA256: | BDED95B698B5DBDA739E259205EE17216A77616B41D9A4E765062C6E4F055F56 |
| SSDEEP: | 98304:es6wS5Zo1KxX/tMbo0jaUAT1KxX/tMbo0jaUAuRWCp9XLs4oOumKyZVqxOqQXCQy:k6J |
MALICIOUS
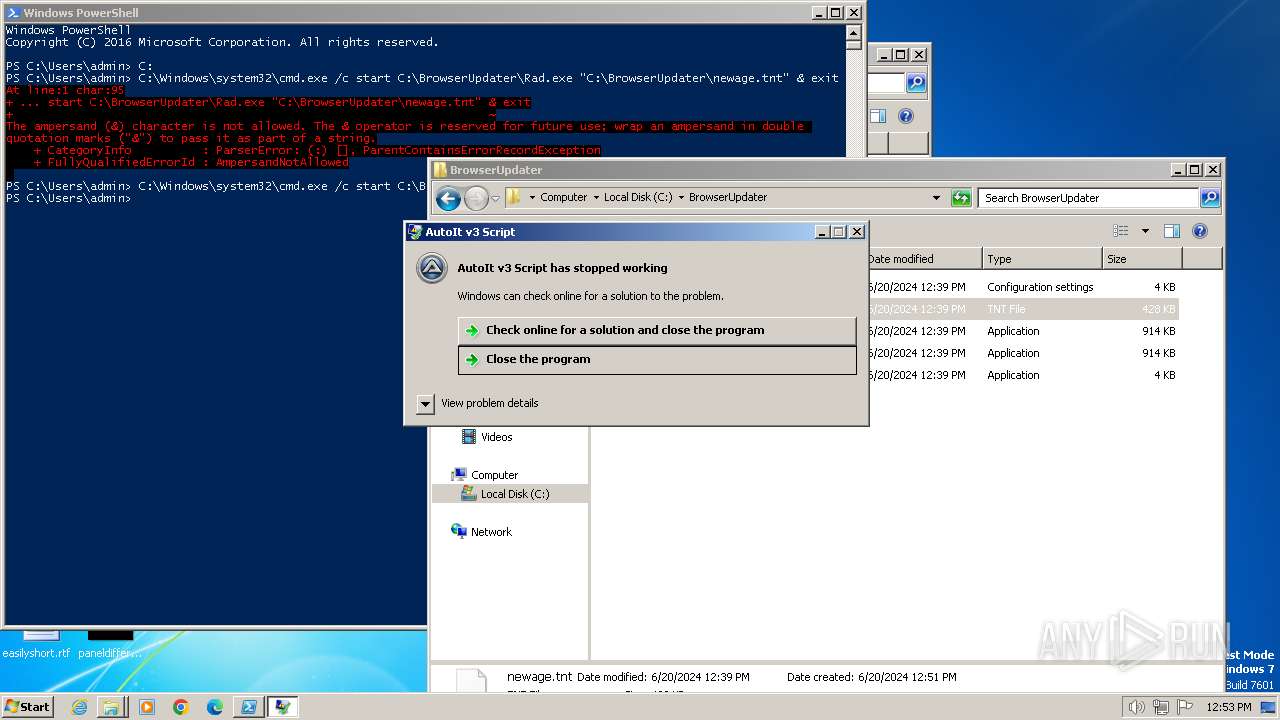
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3384)
Changes the autorun value in the registry
- Rad3.exe (PID: 1580)
SUSPICIOUS
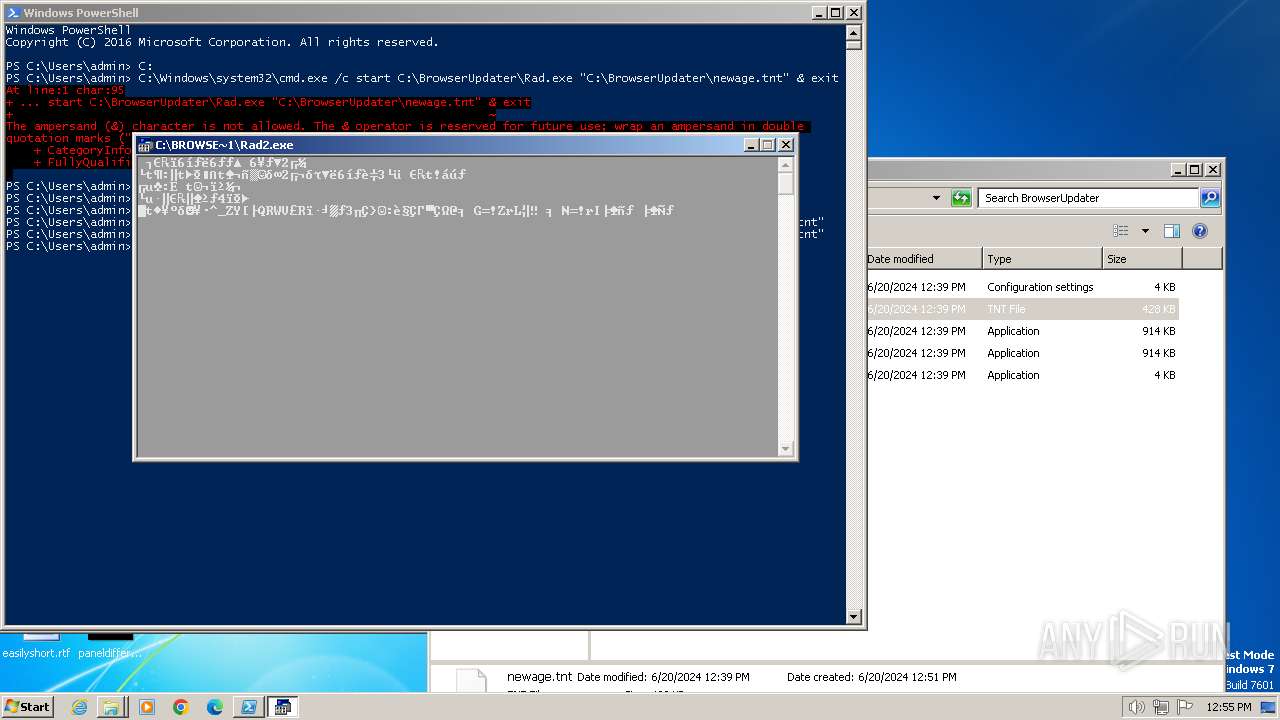
Detected use of alternative data streams (AltDS)
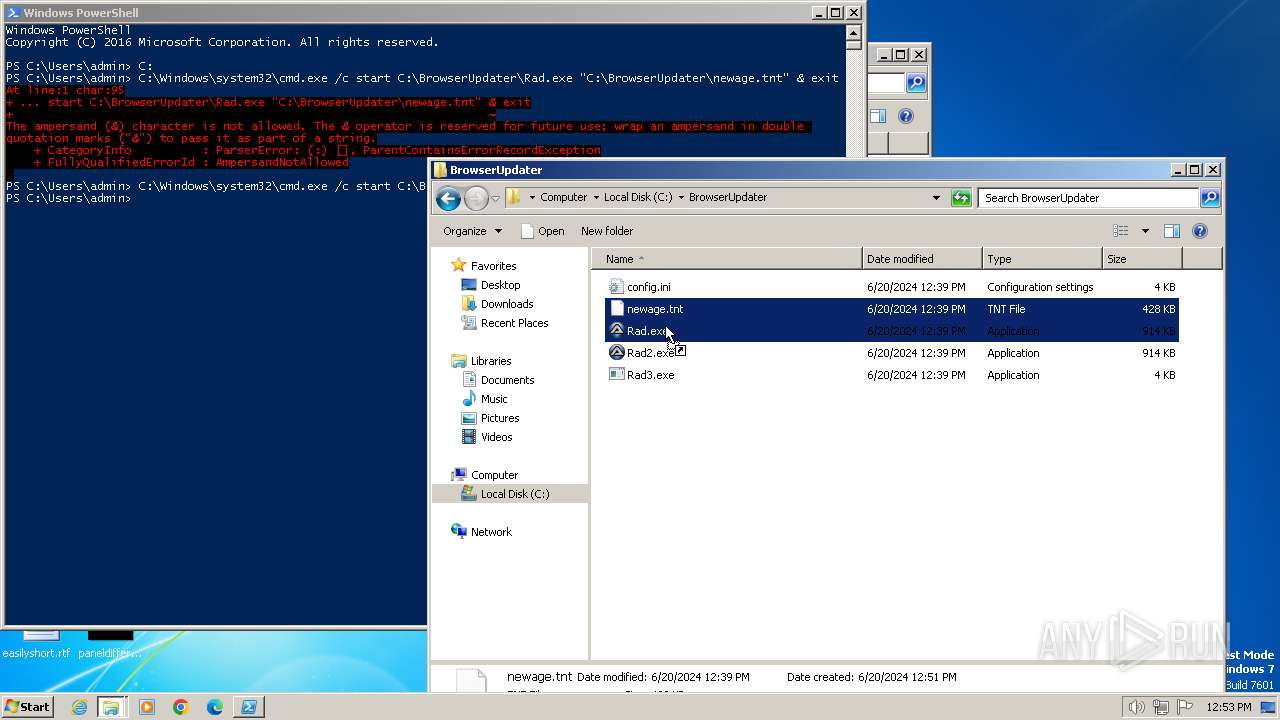
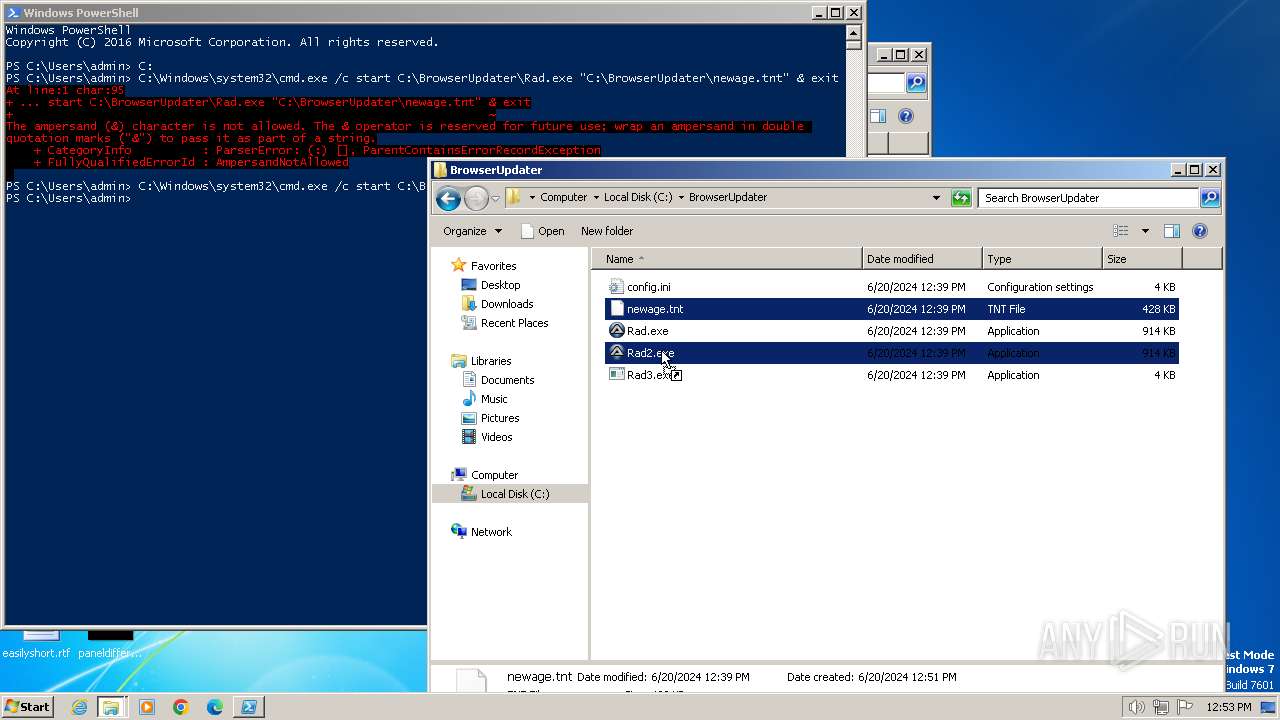
- Rad.exe (PID: 2740)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad2.exe (PID: 1980)
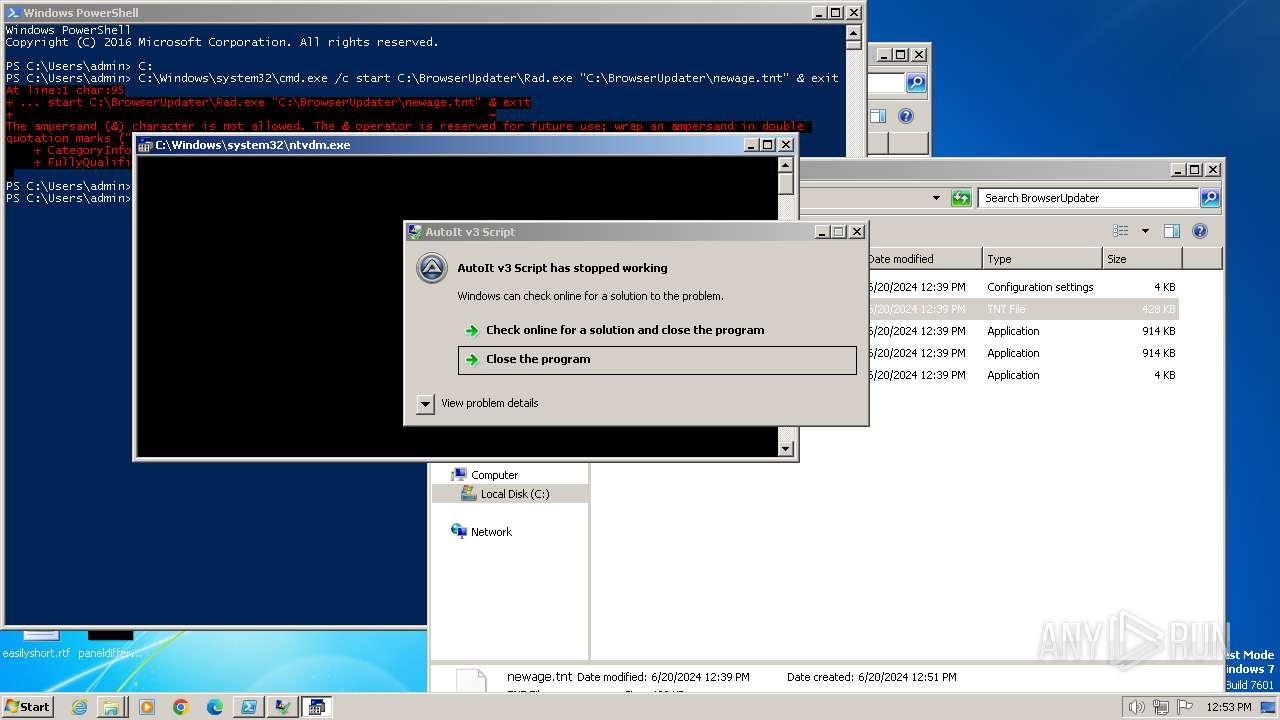
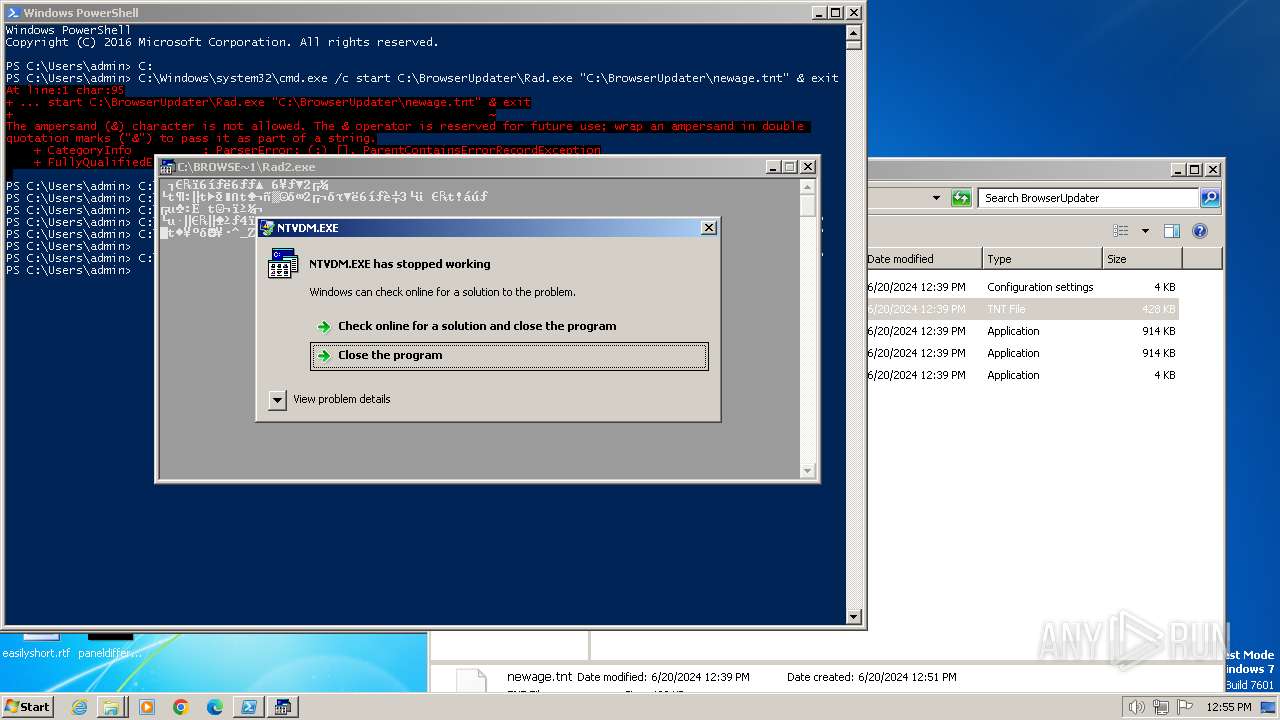
Creates file in the systems drive root
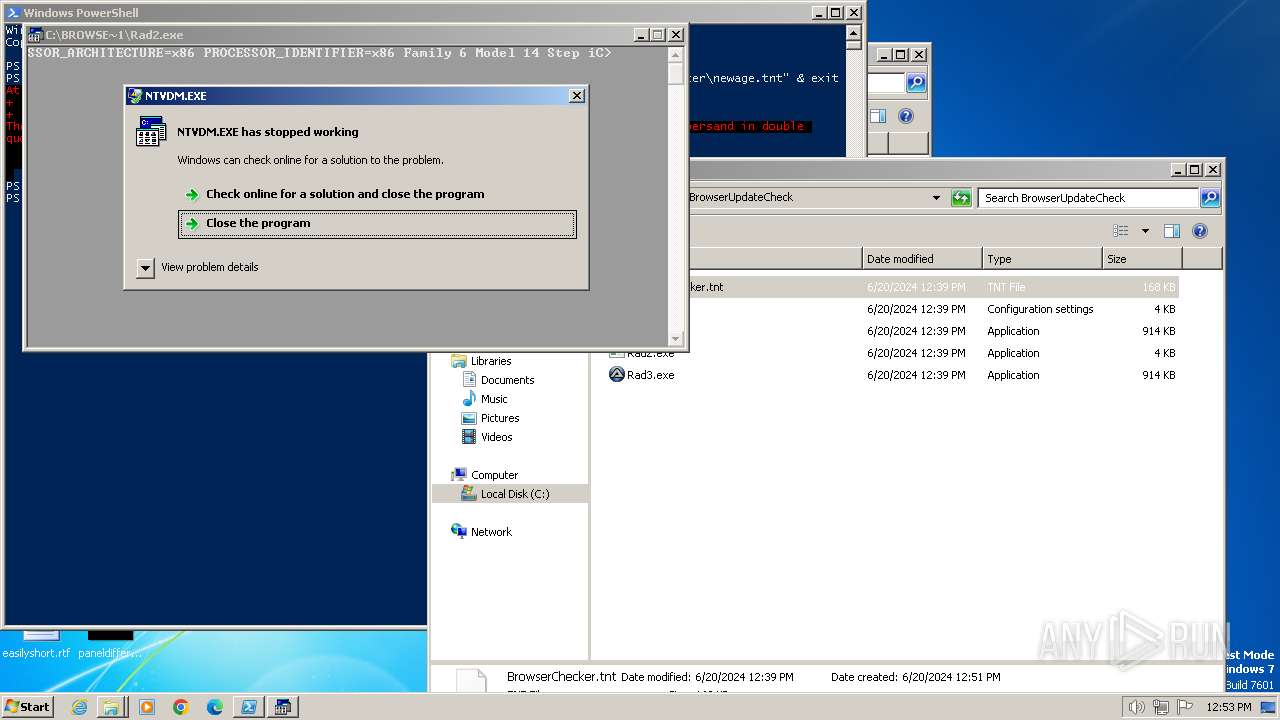
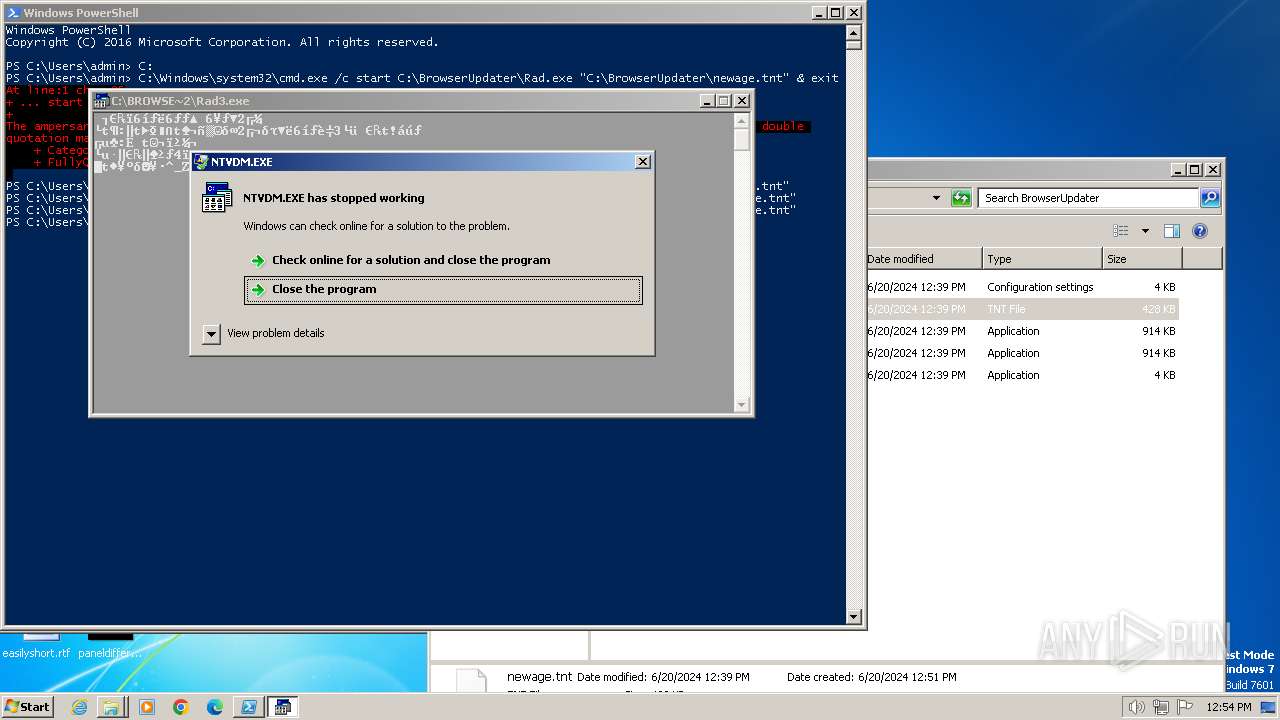
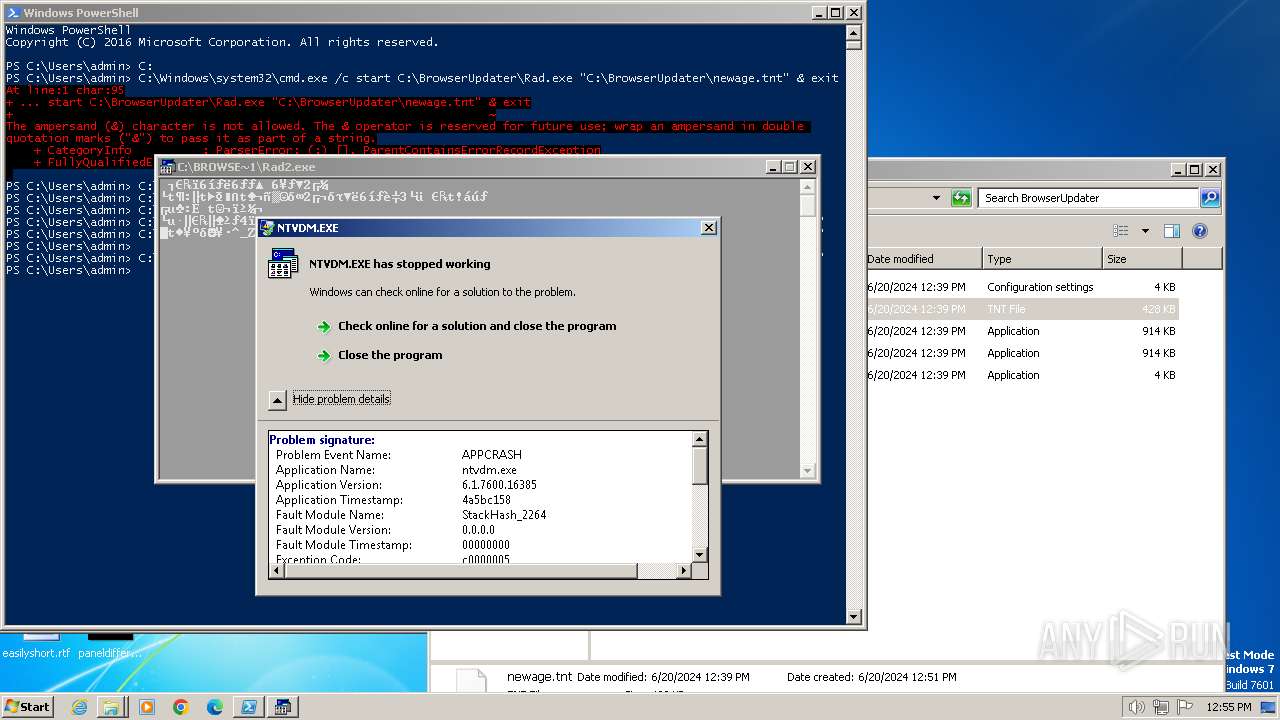
- ntvdm.exe (PID: 3832)
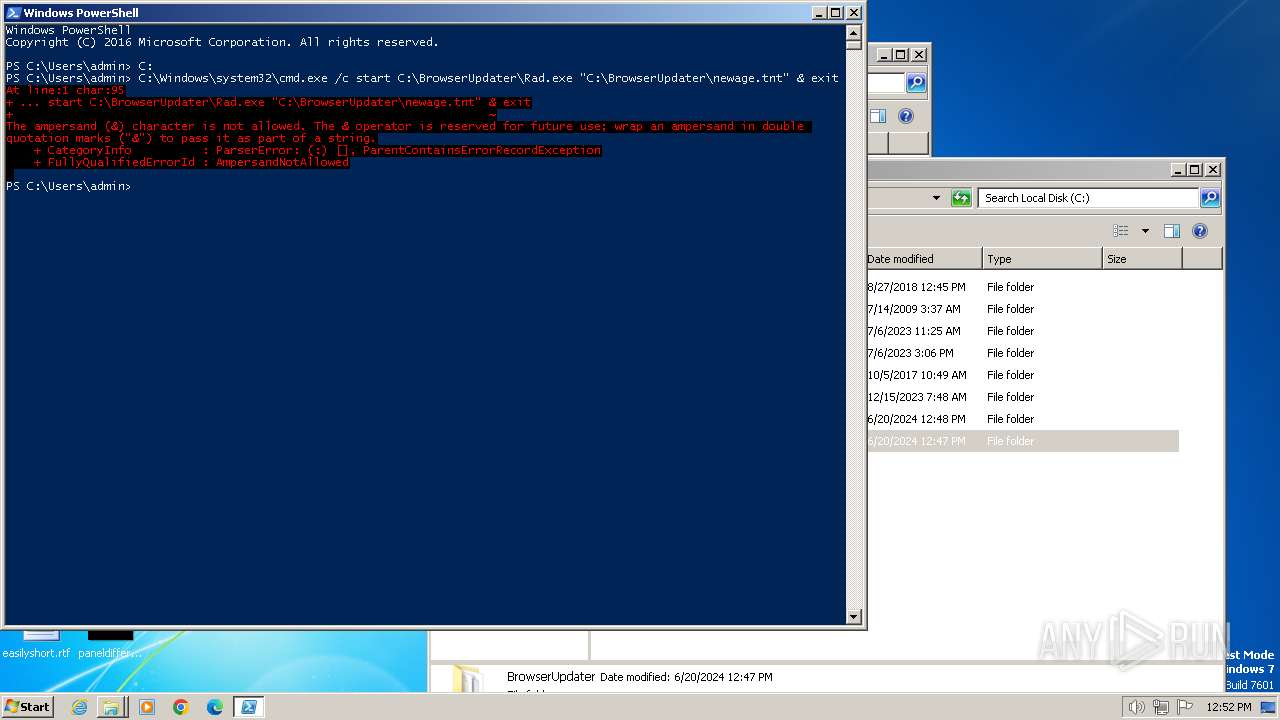
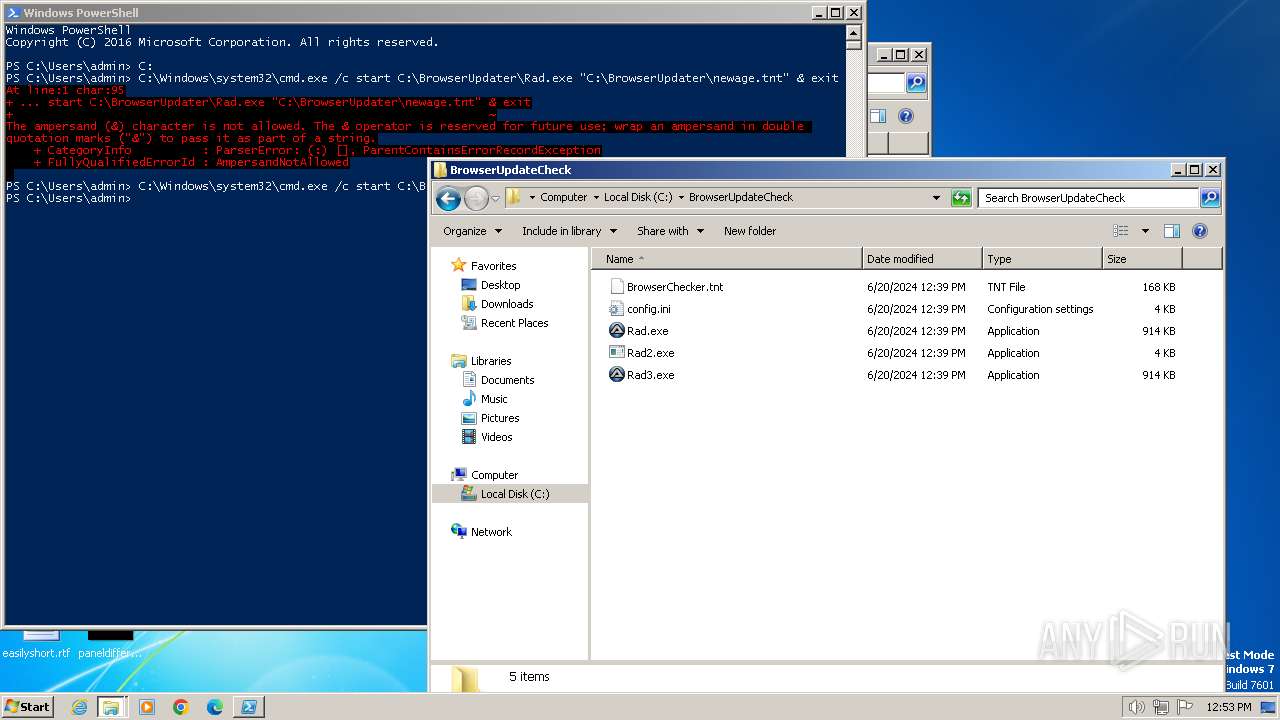
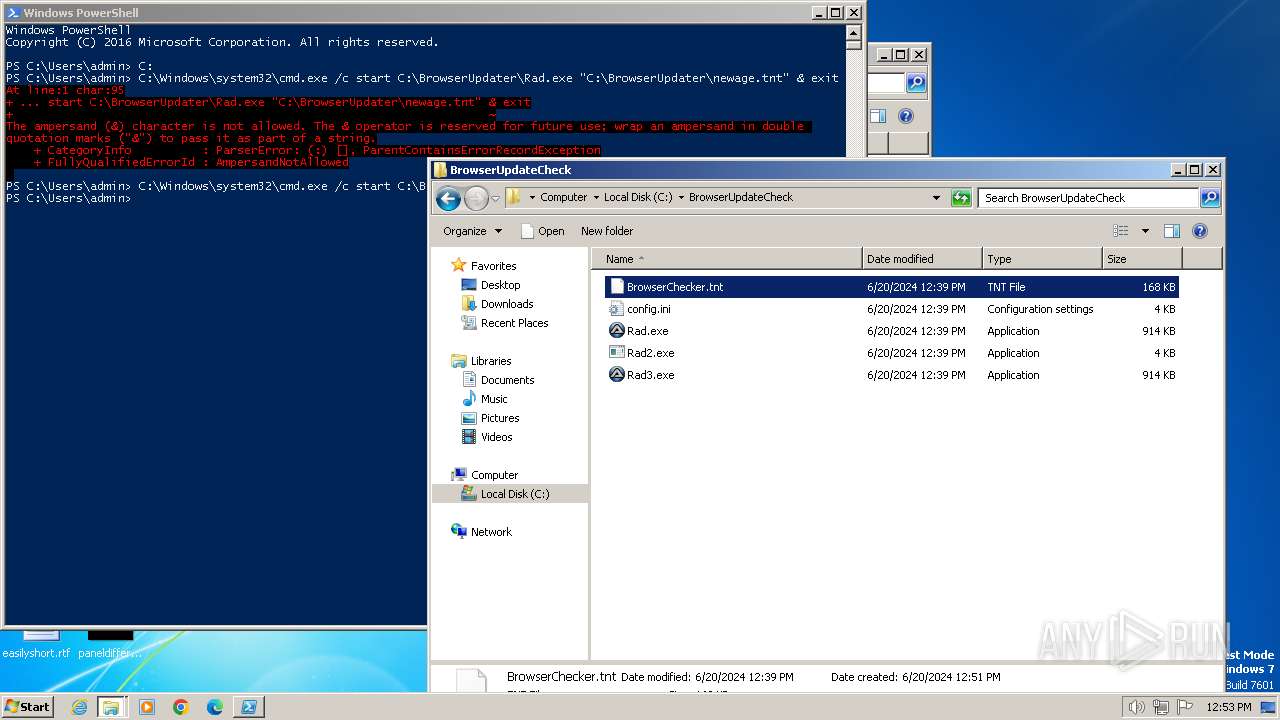
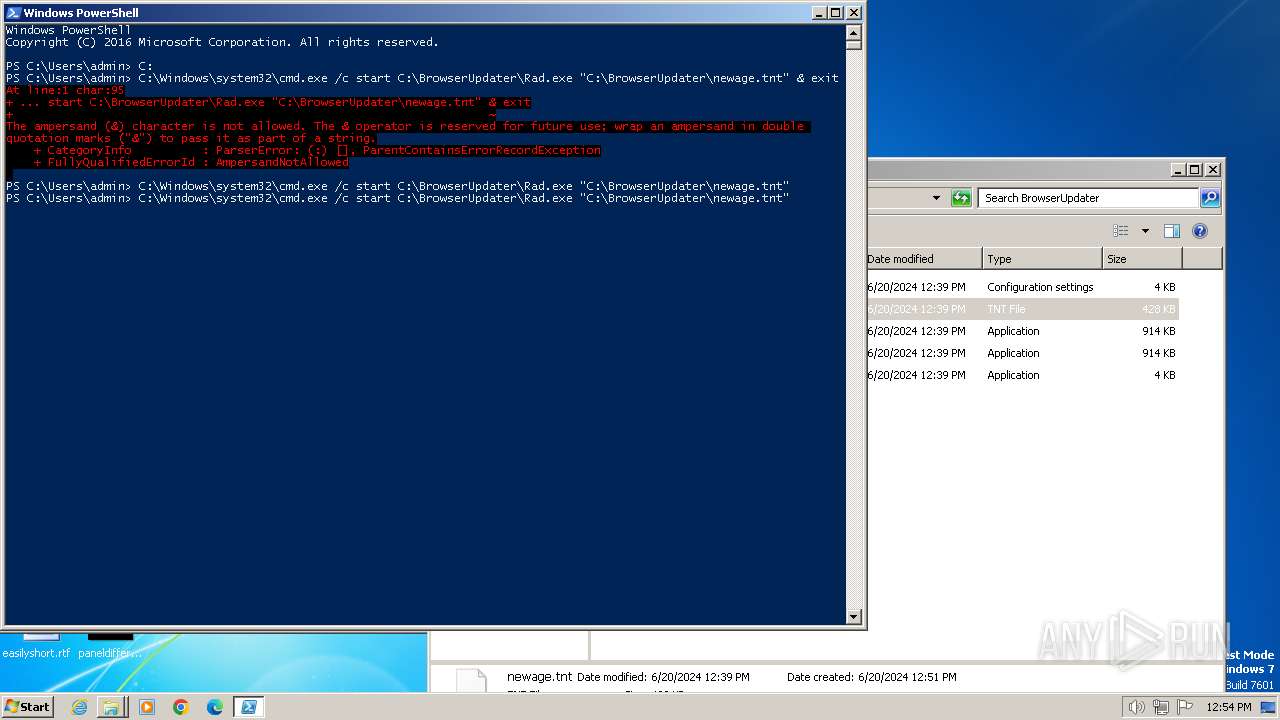
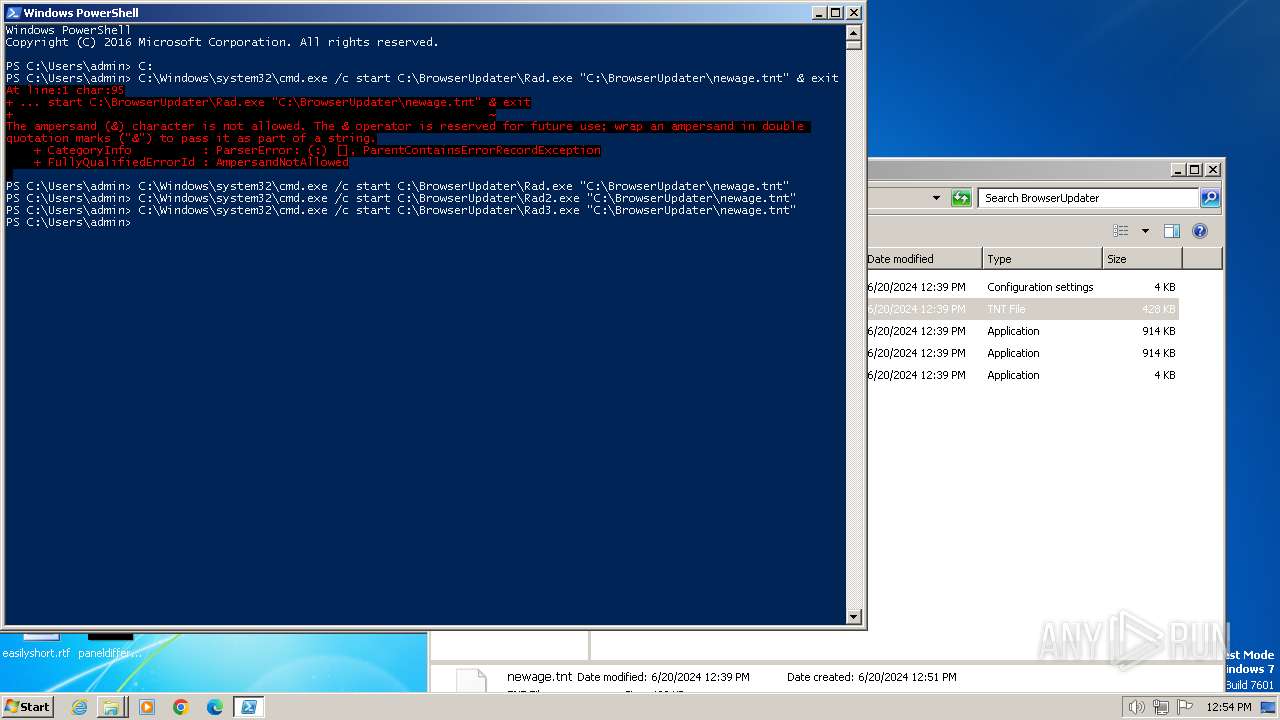
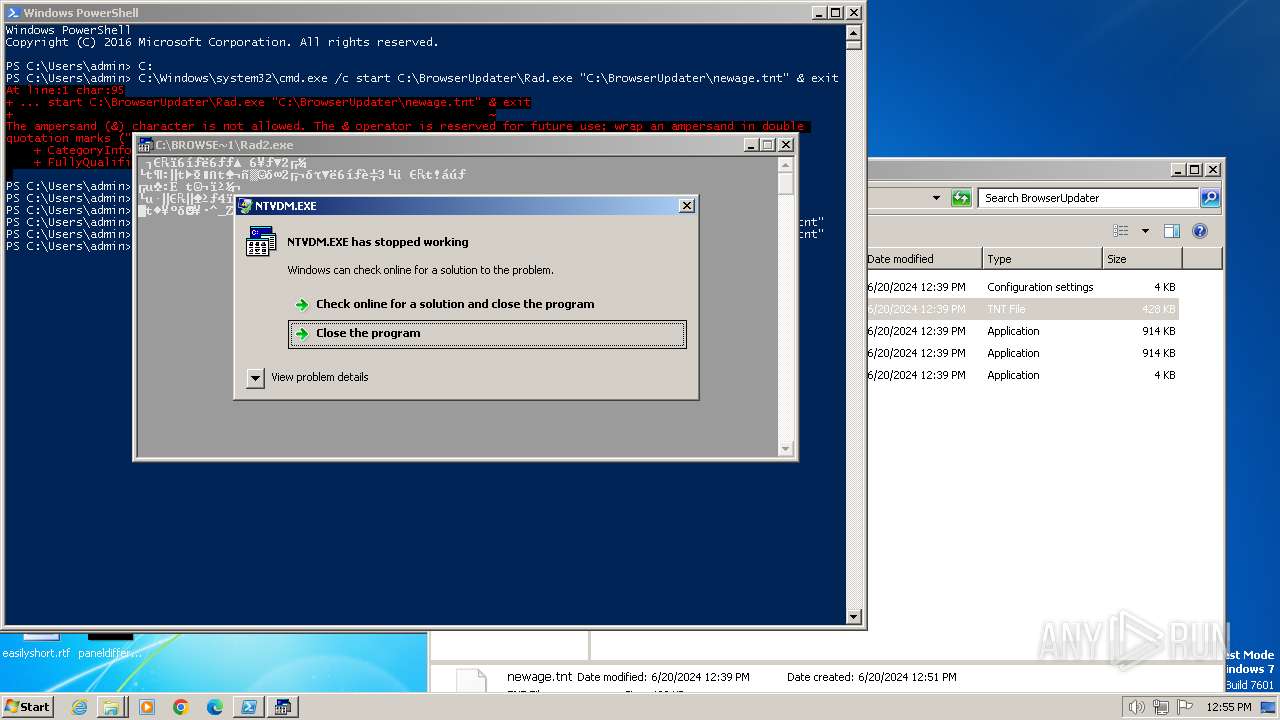
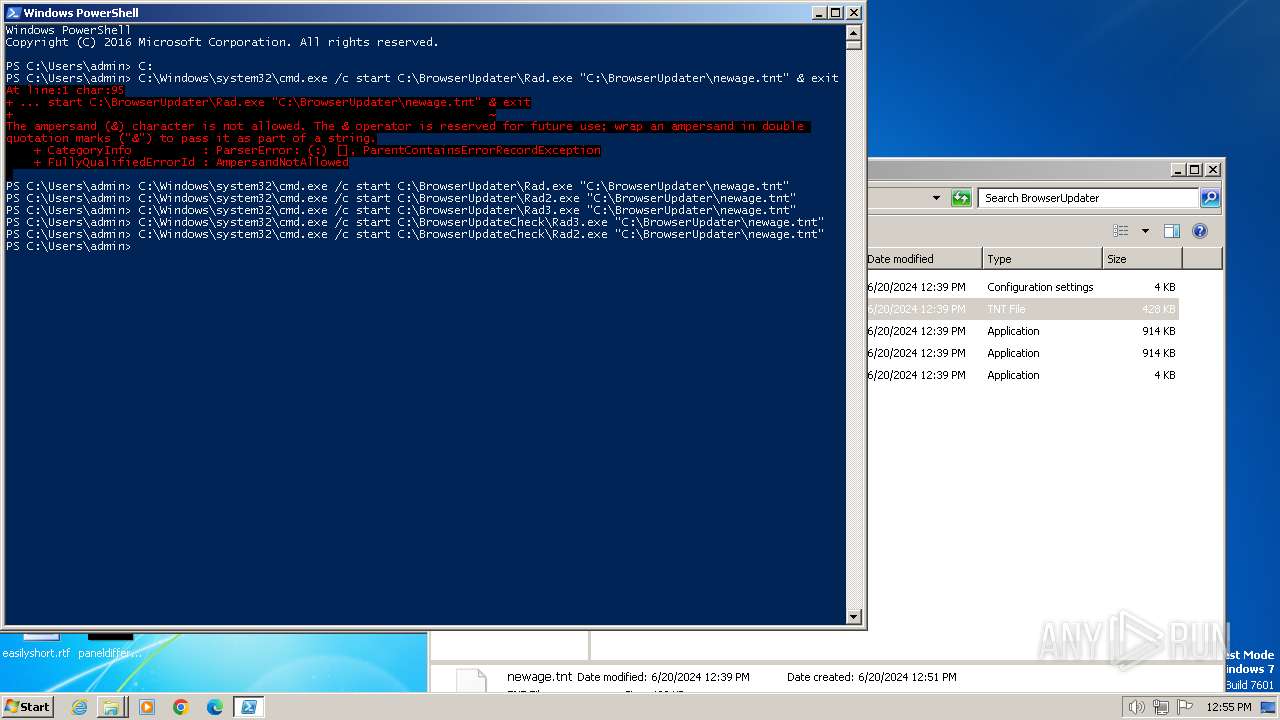
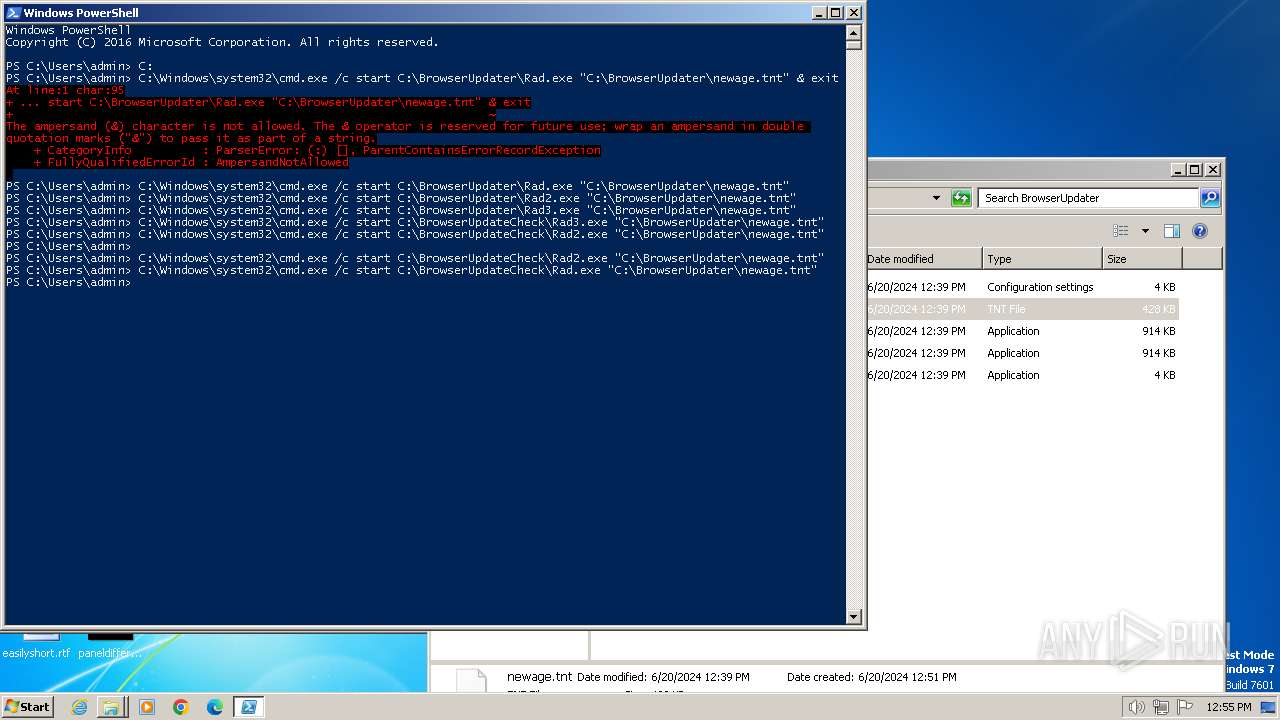
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1856)
INFO
Manual execution by a user
- powershell.exe (PID: 1856)
- explorer.exe (PID: 3372)
- ntvdm.exe (PID: 3832)
- Rad3.exe (PID: 1580)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad.exe (PID: 3816)
- ntvdm.exe (PID: 3528)
- Rad.exe (PID: 3688)
- ntvdm.exe (PID: 1916)
- Rad3.exe (PID: 400)
Checks supported languages
- Rad.exe (PID: 2740)
- Rad3.exe (PID: 1580)
- Rad2.exe (PID: 2280)
- Rad.exe (PID: 3816)
- Rad.exe (PID: 3028)
- Rad3.exe (PID: 400)
- Rad.exe (PID: 3688)
- Rad2.exe (PID: 1980)
- Rad.exe (PID: 1800)
- Rad3.exe (PID: 2928)
Reads mouse settings
- Rad.exe (PID: 2740)
- Rad3.exe (PID: 1580)
- Rad.exe (PID: 3816)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad3.exe (PID: 400)
- Rad.exe (PID: 3688)
- Rad2.exe (PID: 1980)
- Rad3.exe (PID: 2928)
- Rad.exe (PID: 1800)
Reads the computer name
- Rad.exe (PID: 2740)
- Rad3.exe (PID: 1580)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad3.exe (PID: 400)
- Rad.exe (PID: 3688)
- Rad2.exe (PID: 1980)
- Rad3.exe (PID: 2928)
- Rad.exe (PID: 1800)
Checks Windows language
- Rad.exe (PID: 2740)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad3.exe (PID: 400)
- Rad.exe (PID: 3688)
- Rad2.exe (PID: 1980)
- Rad3.exe (PID: 2928)
- Rad.exe (PID: 1800)
Reads the machine GUID from the registry
- Rad.exe (PID: 2740)
- Rad.exe (PID: 3028)
- Rad2.exe (PID: 2280)
- Rad3.exe (PID: 400)
- Rad.exe (PID: 3688)
- Rad2.exe (PID: 1980)
- Rad3.exe (PID: 2928)
- Rad.exe (PID: 1800)
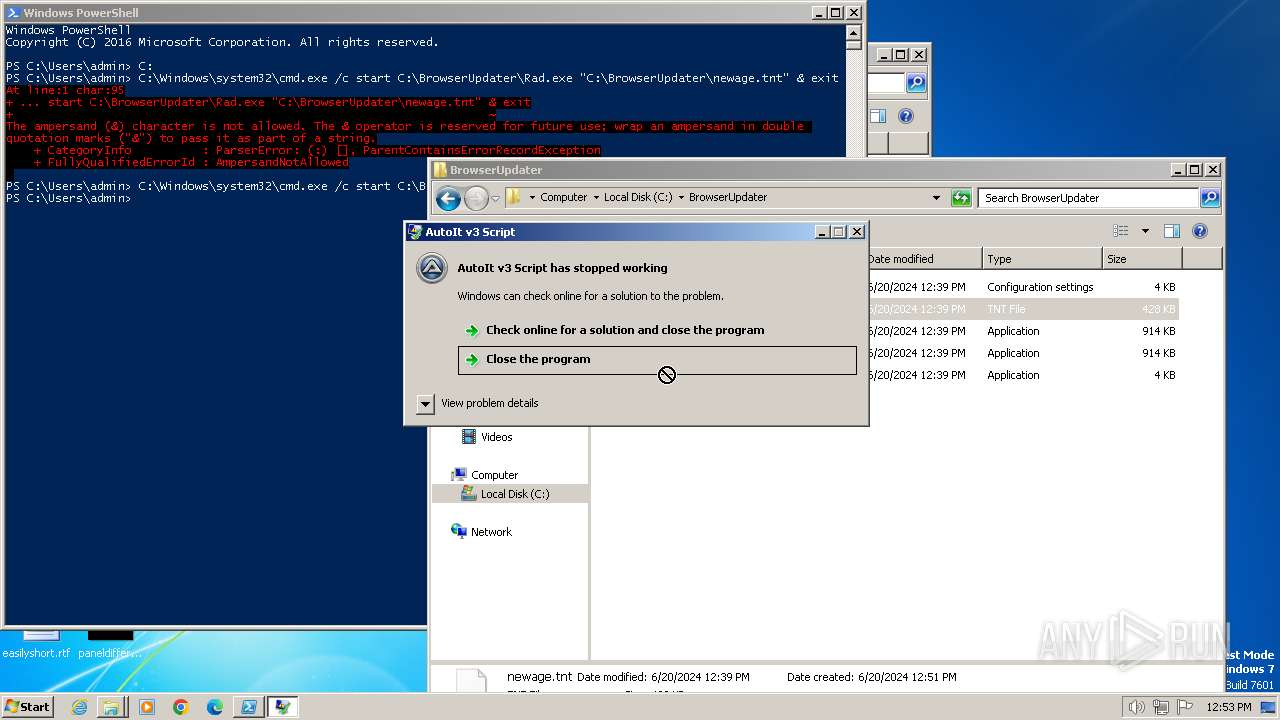
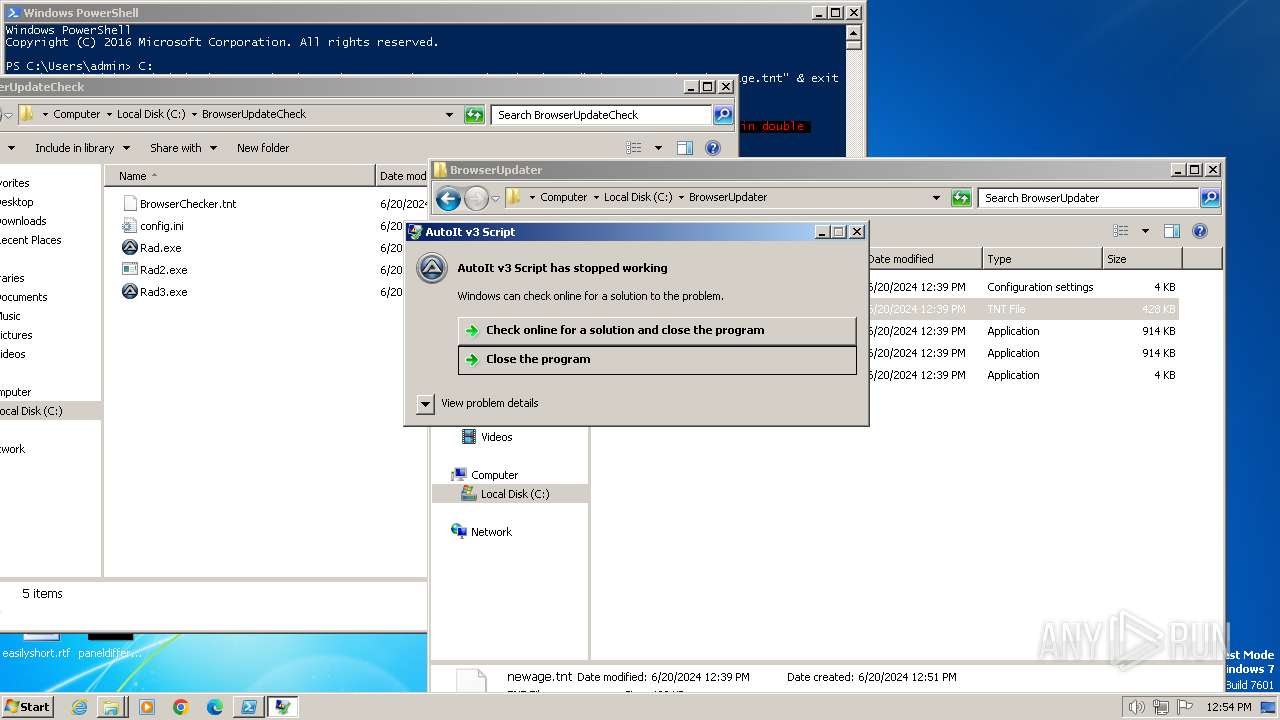
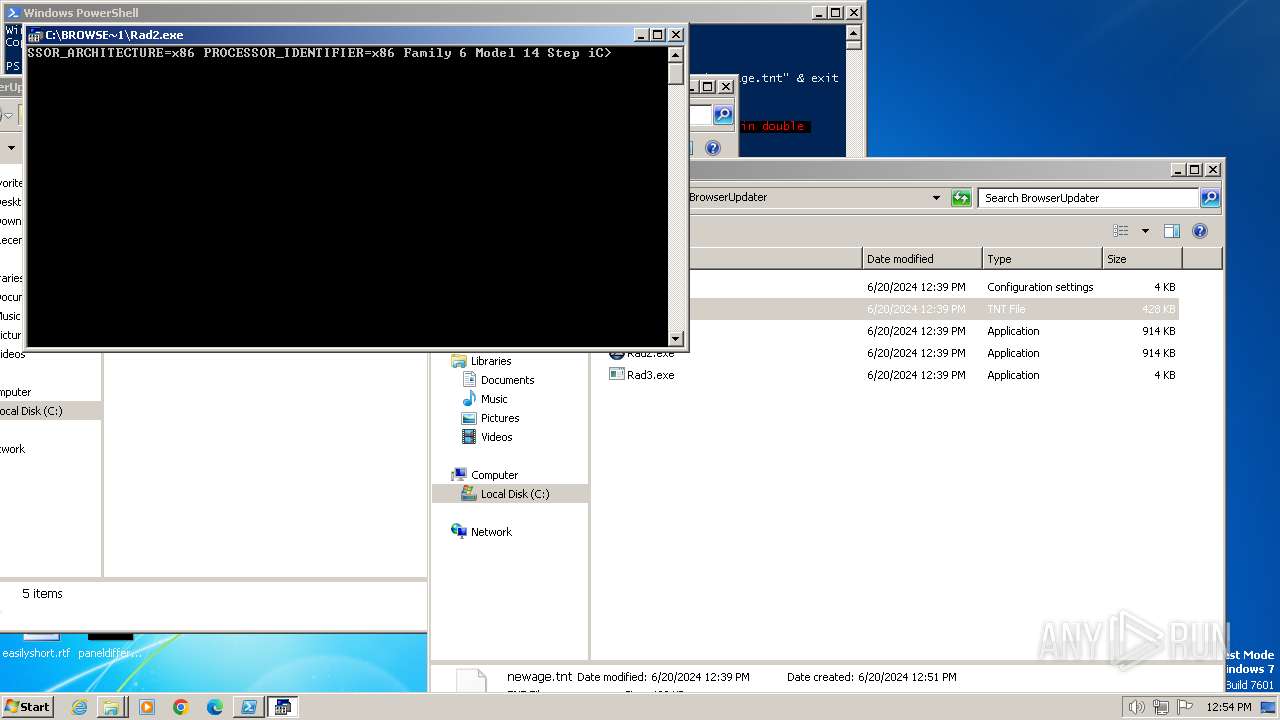
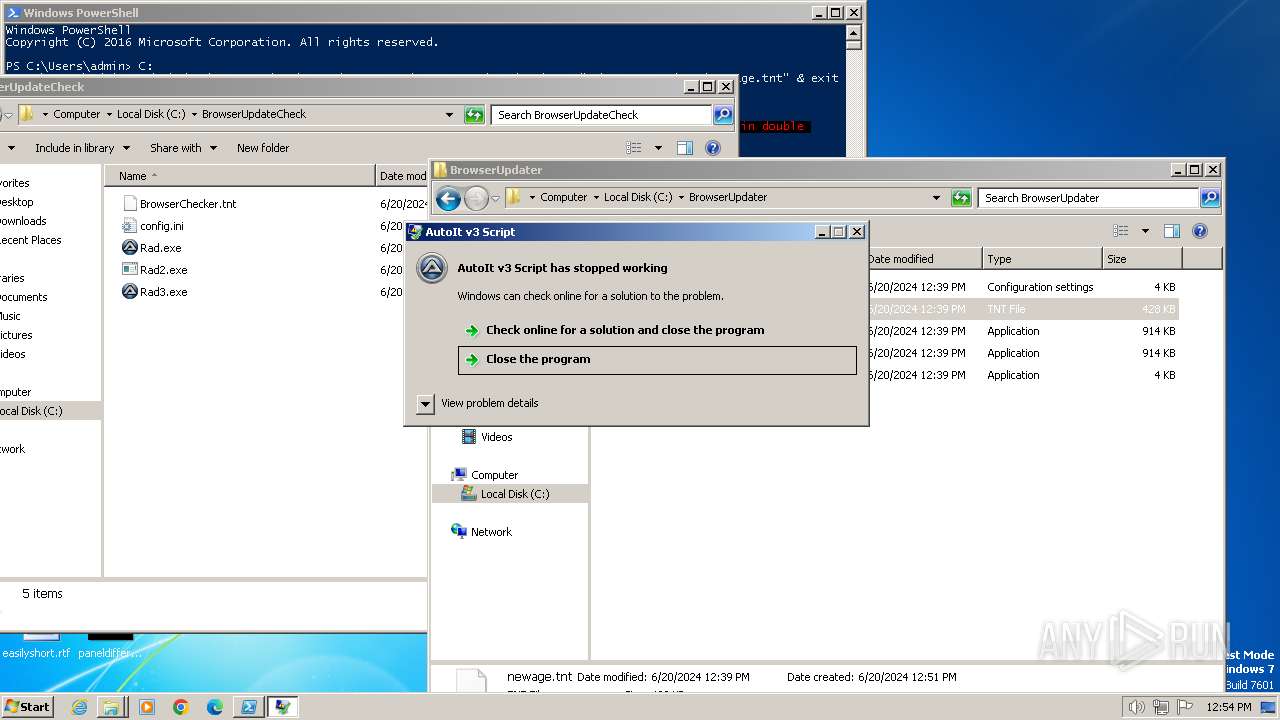
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1856)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3384)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:06:20 13:49:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | complete_files/ |
Total processes
89
Monitored processes
26
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
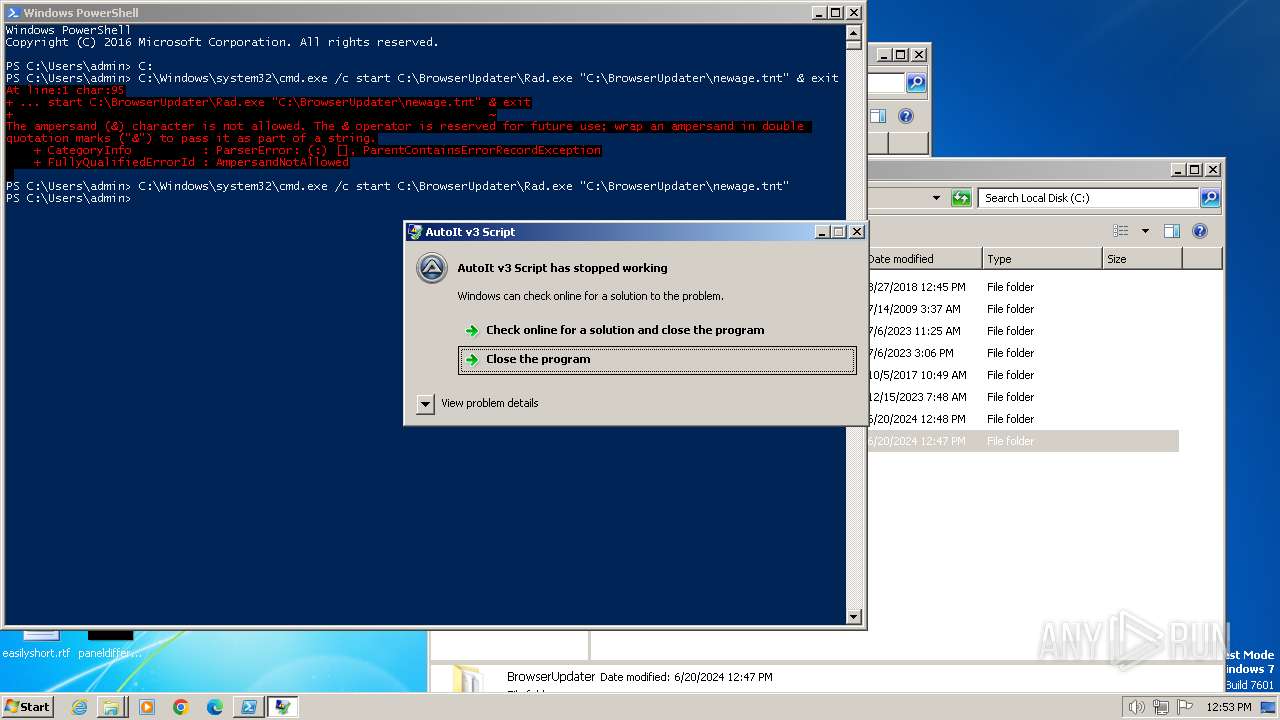
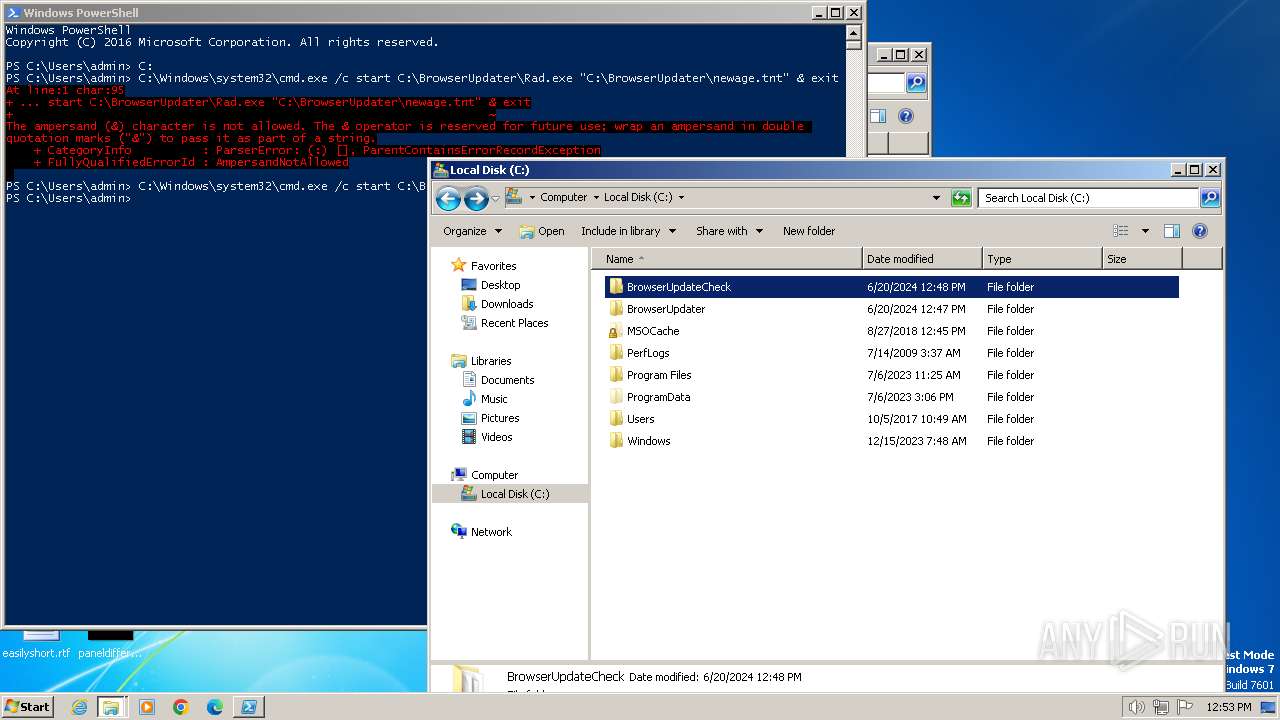
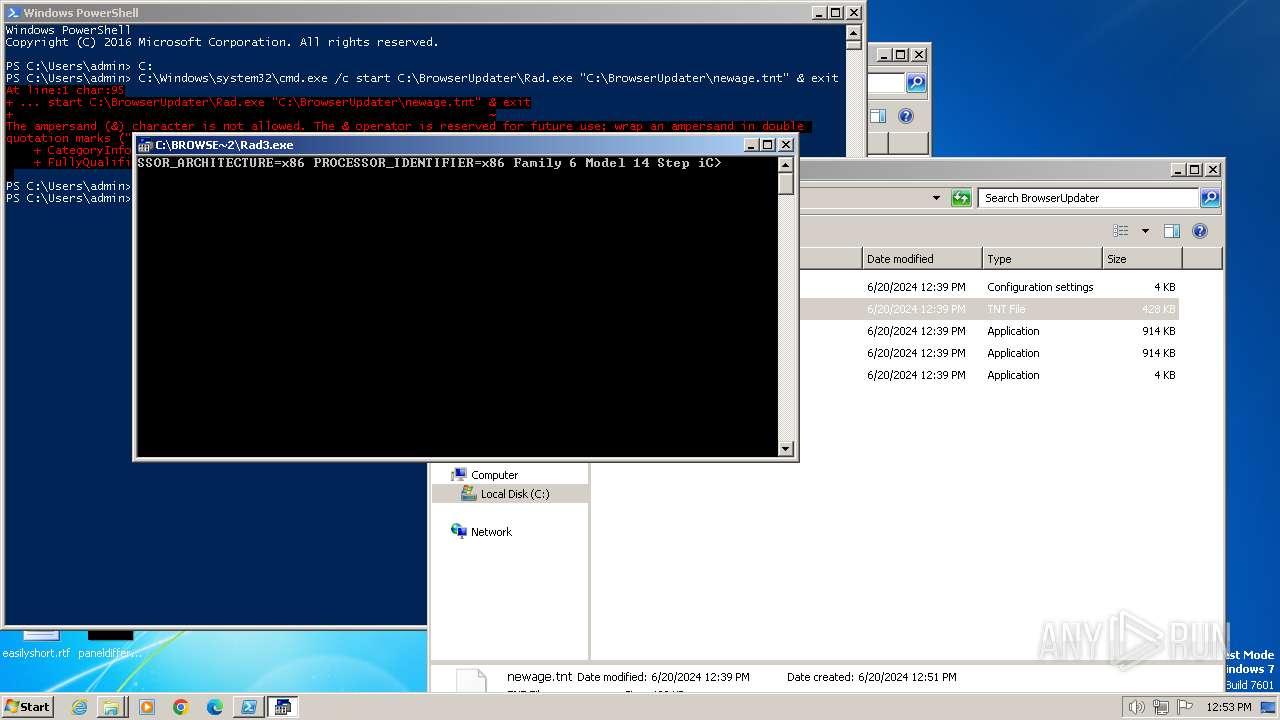
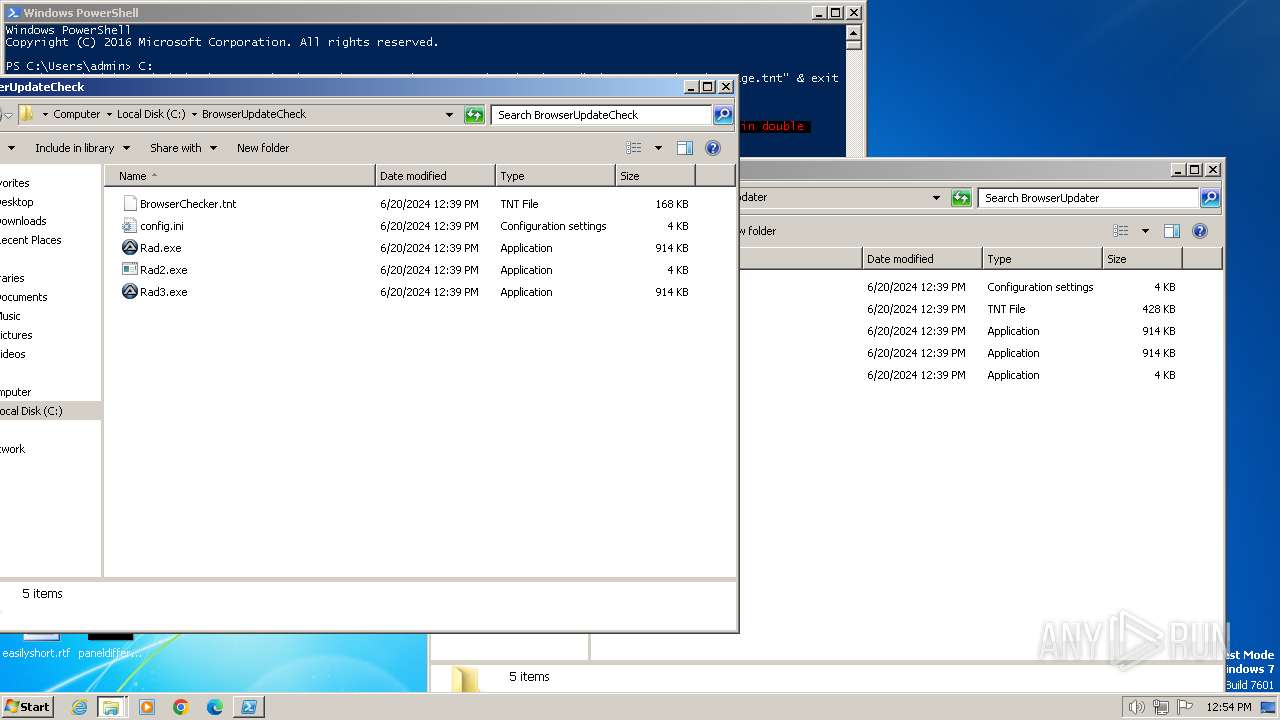
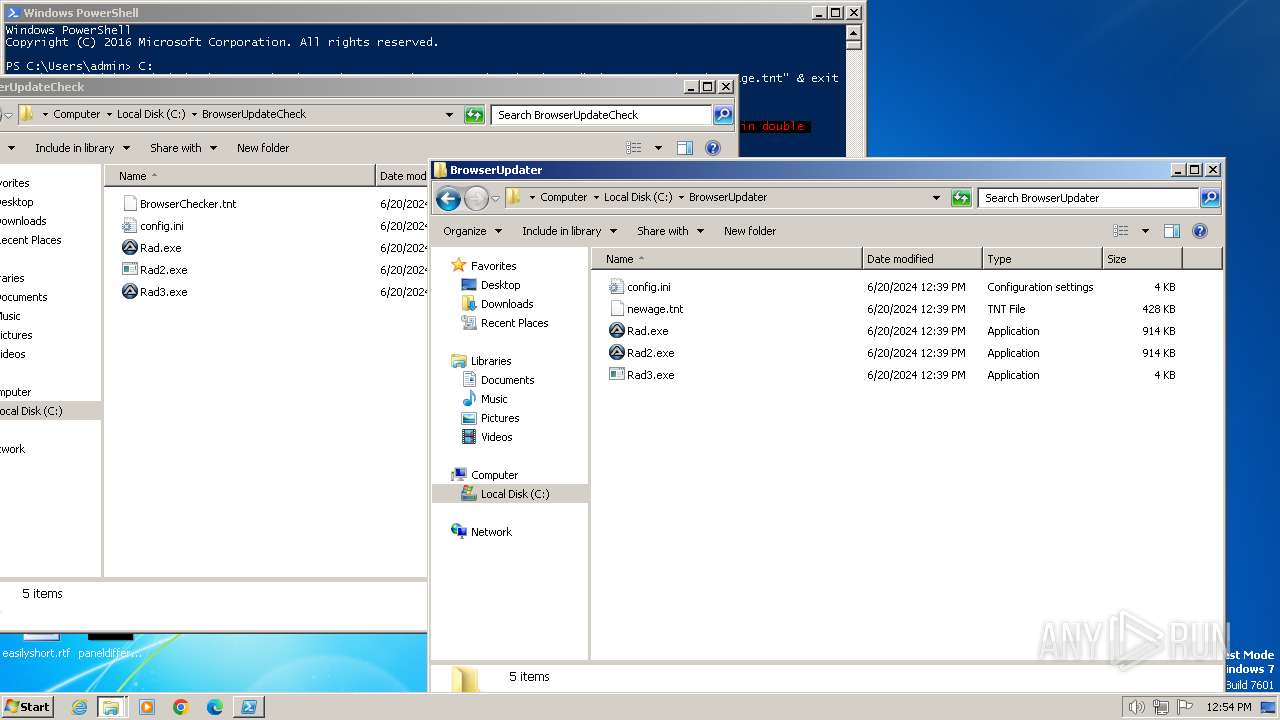
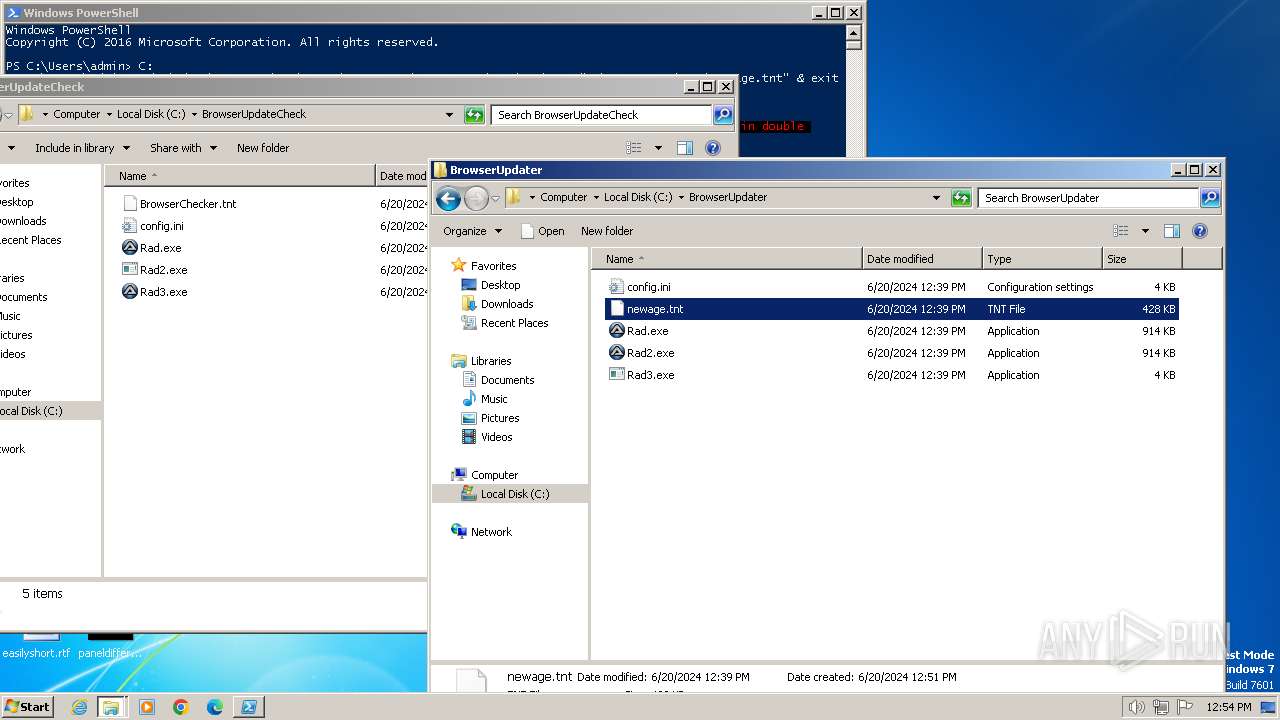
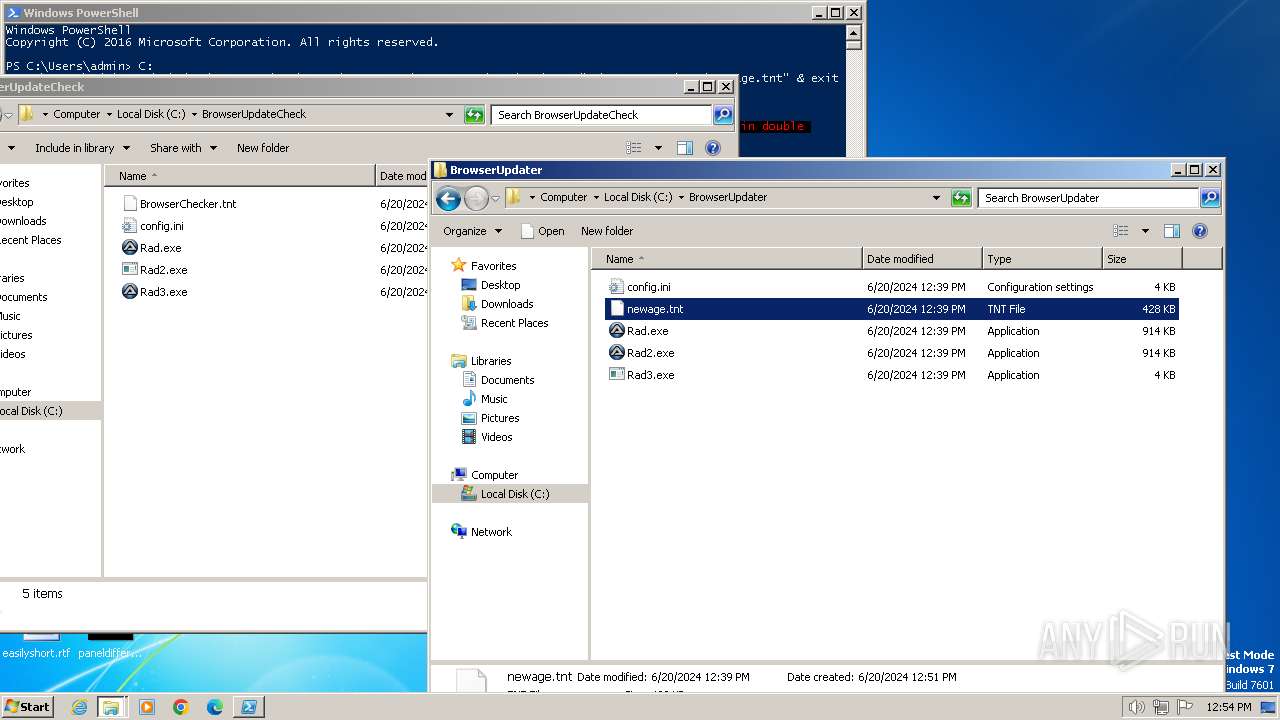
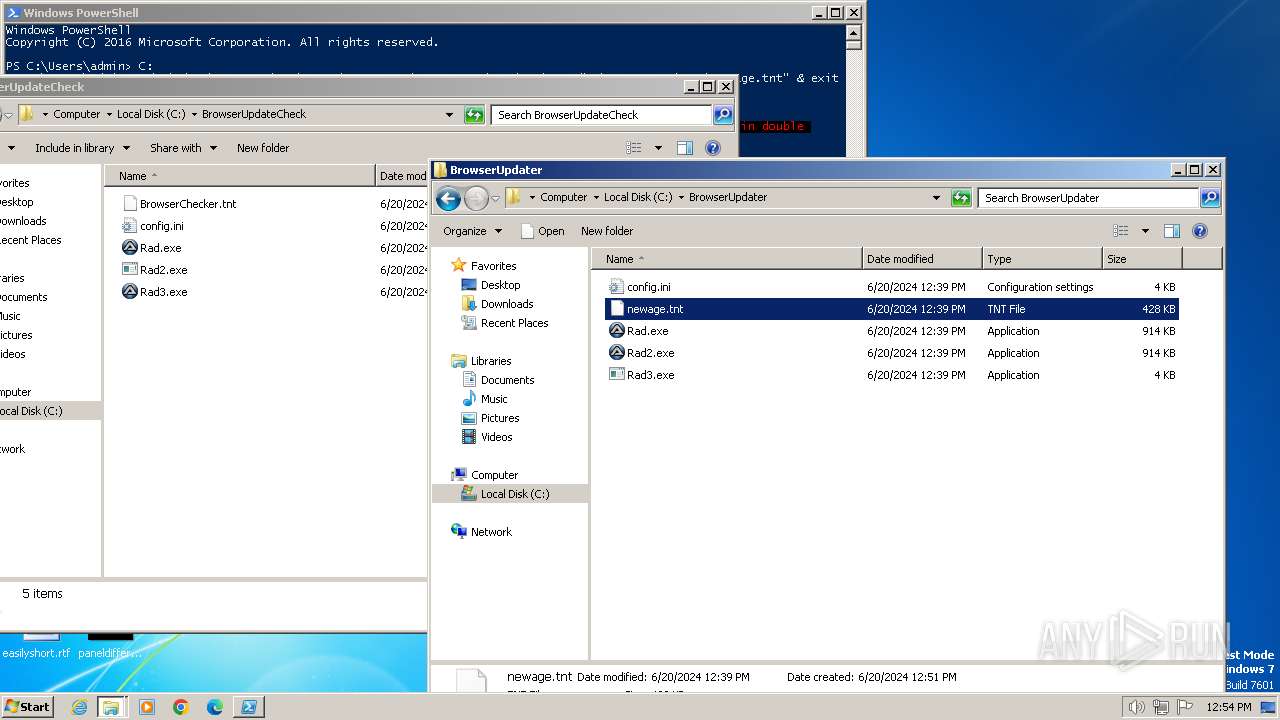
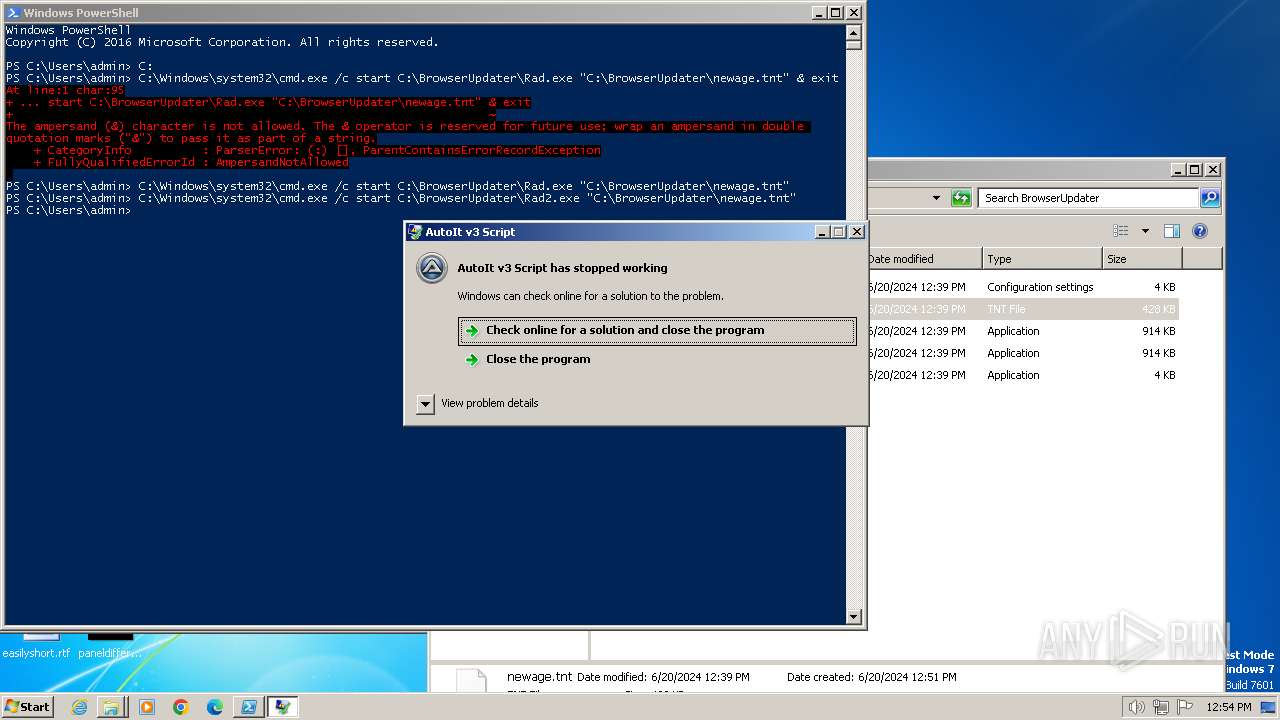
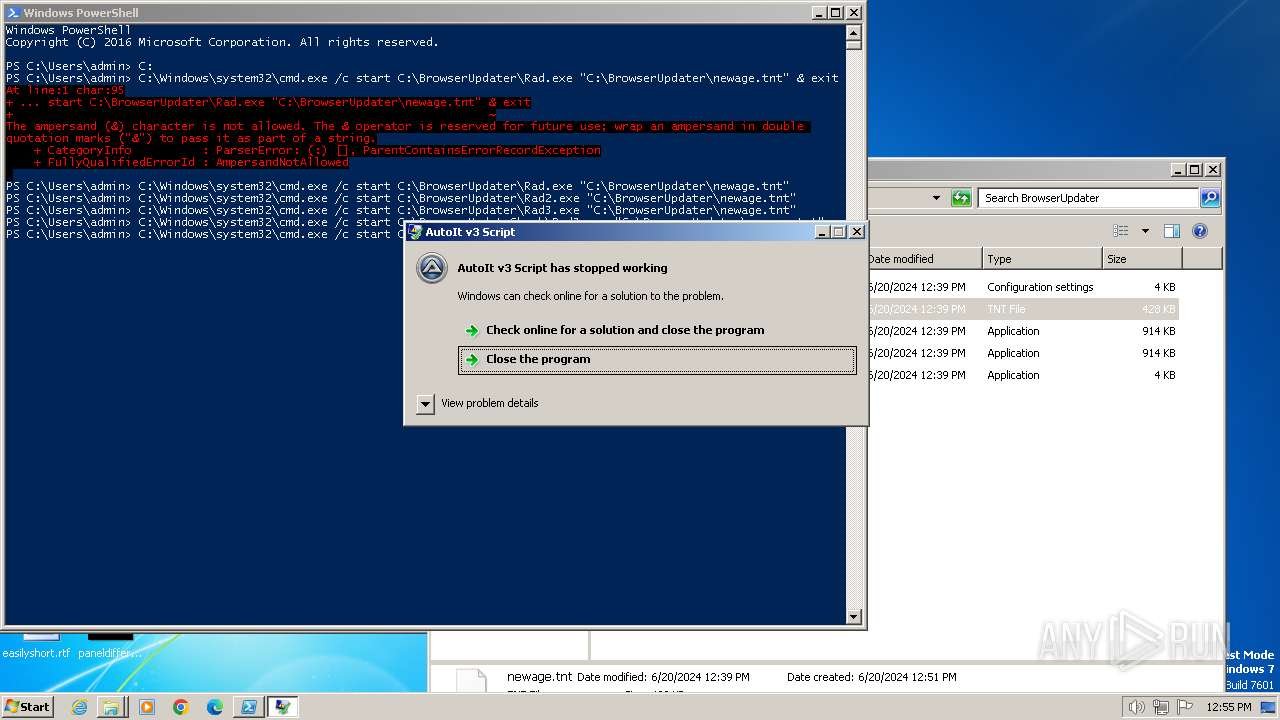
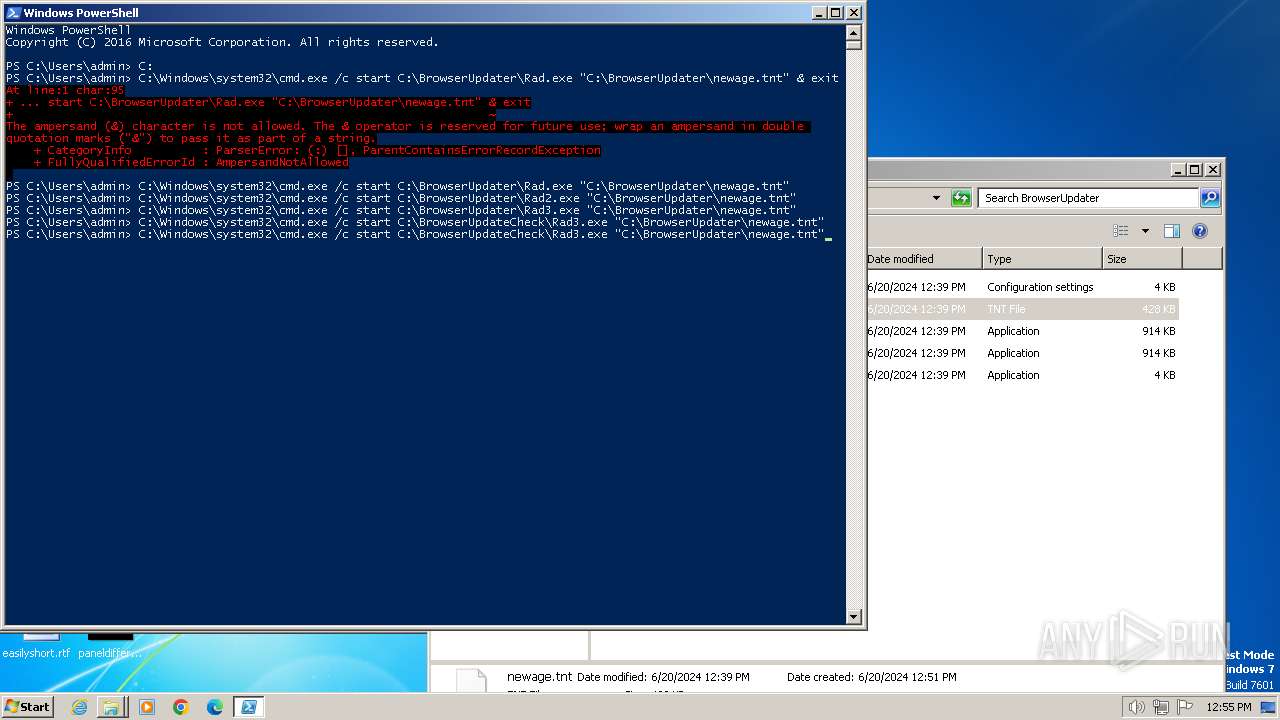
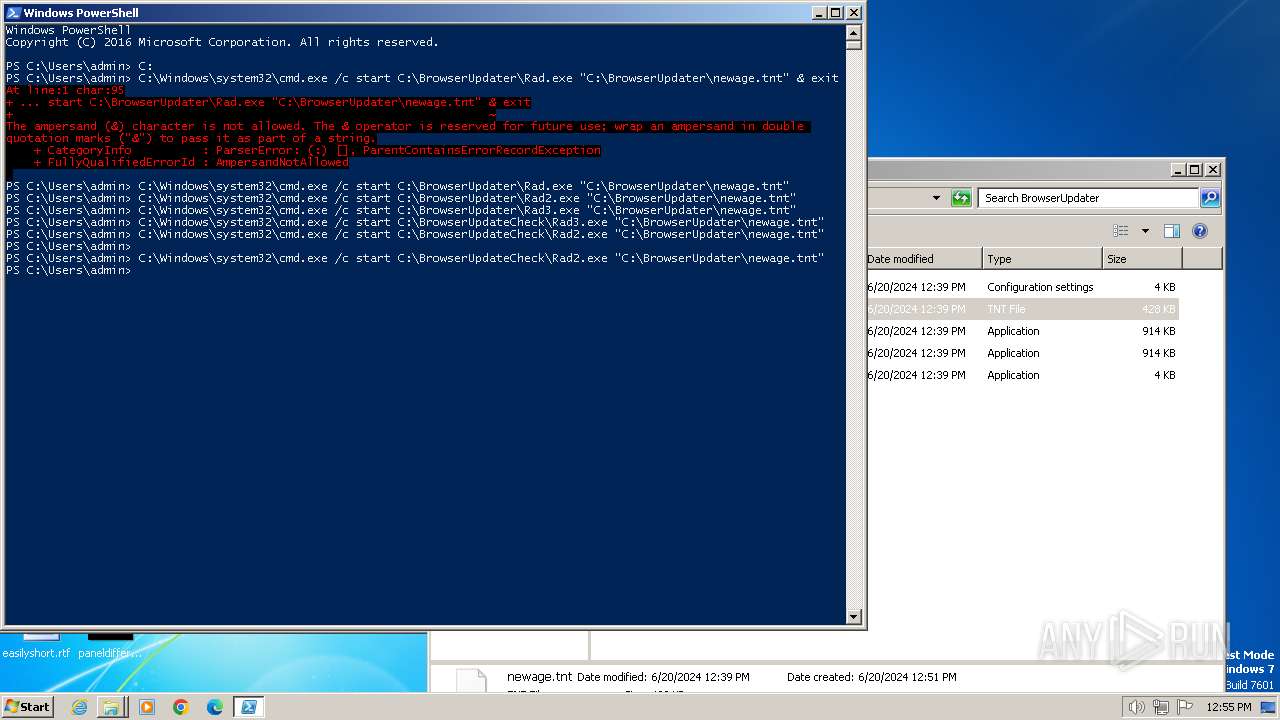
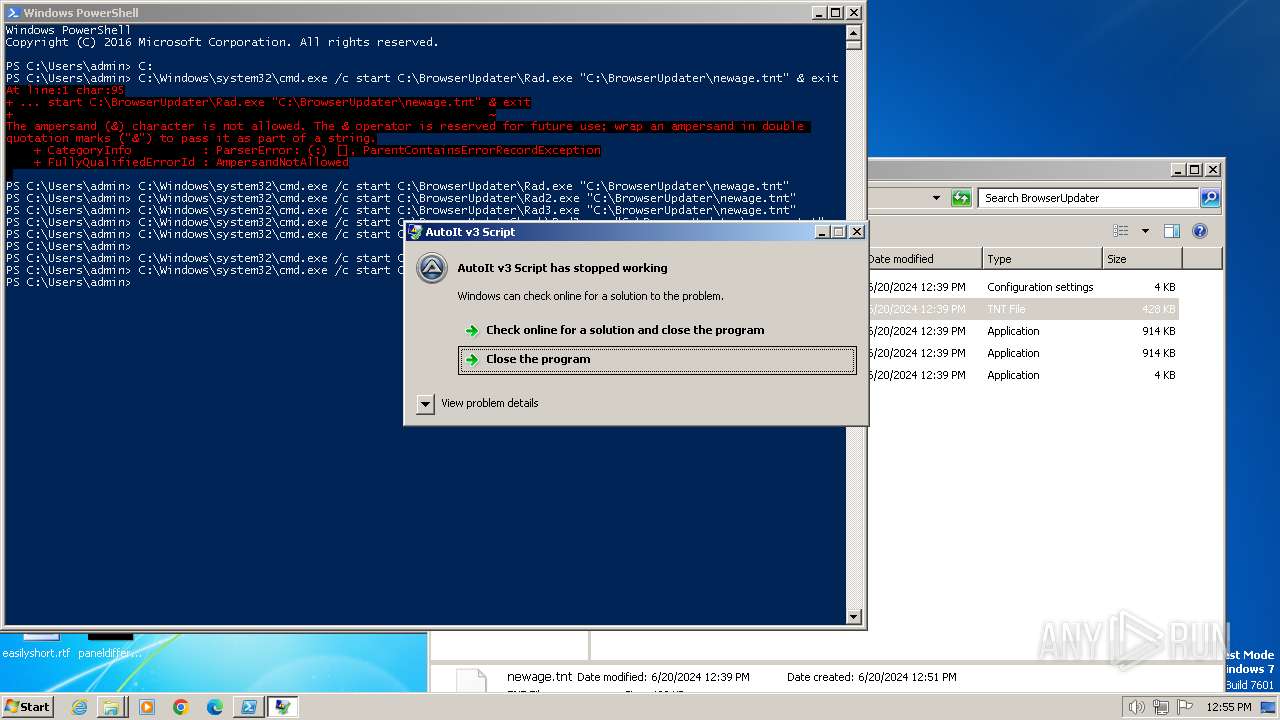
| 400 | "C:\BrowserUpdateCheck\Rad3.exe" C:\BrowserUpdater\newage.tnt | C:\BrowserUpdateCheck\Rad3.exe | explorer.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225477 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
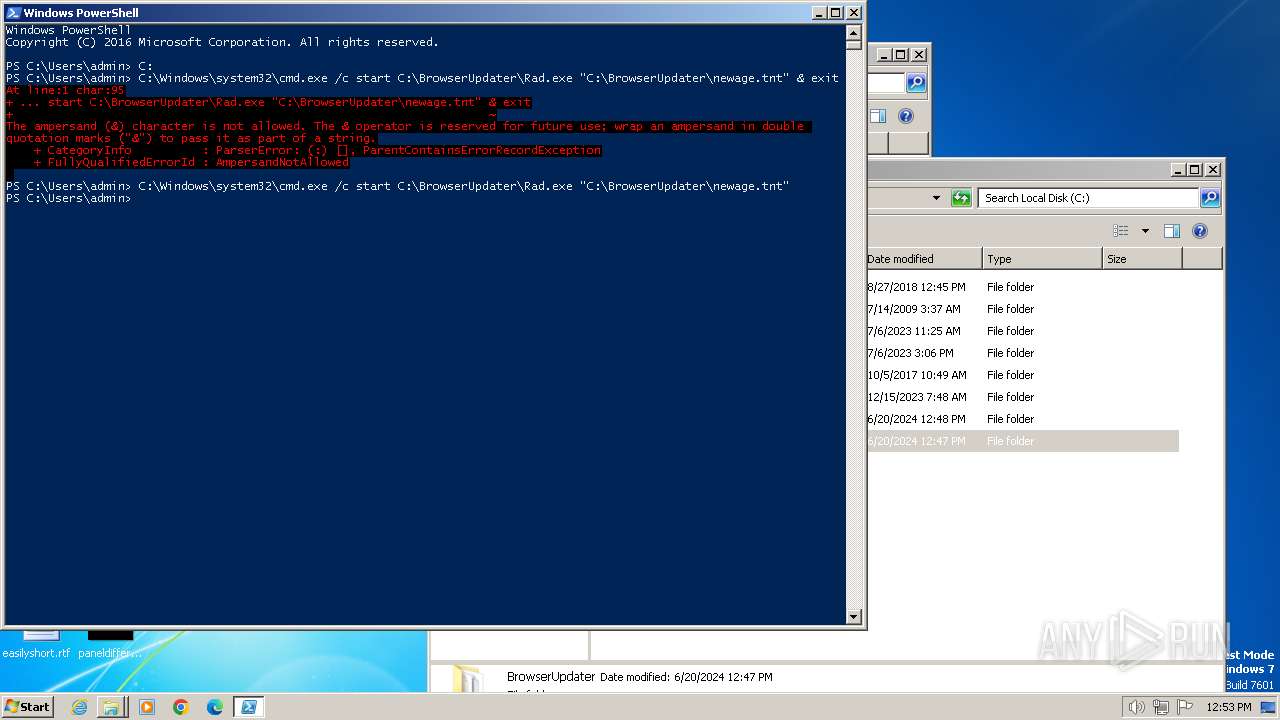
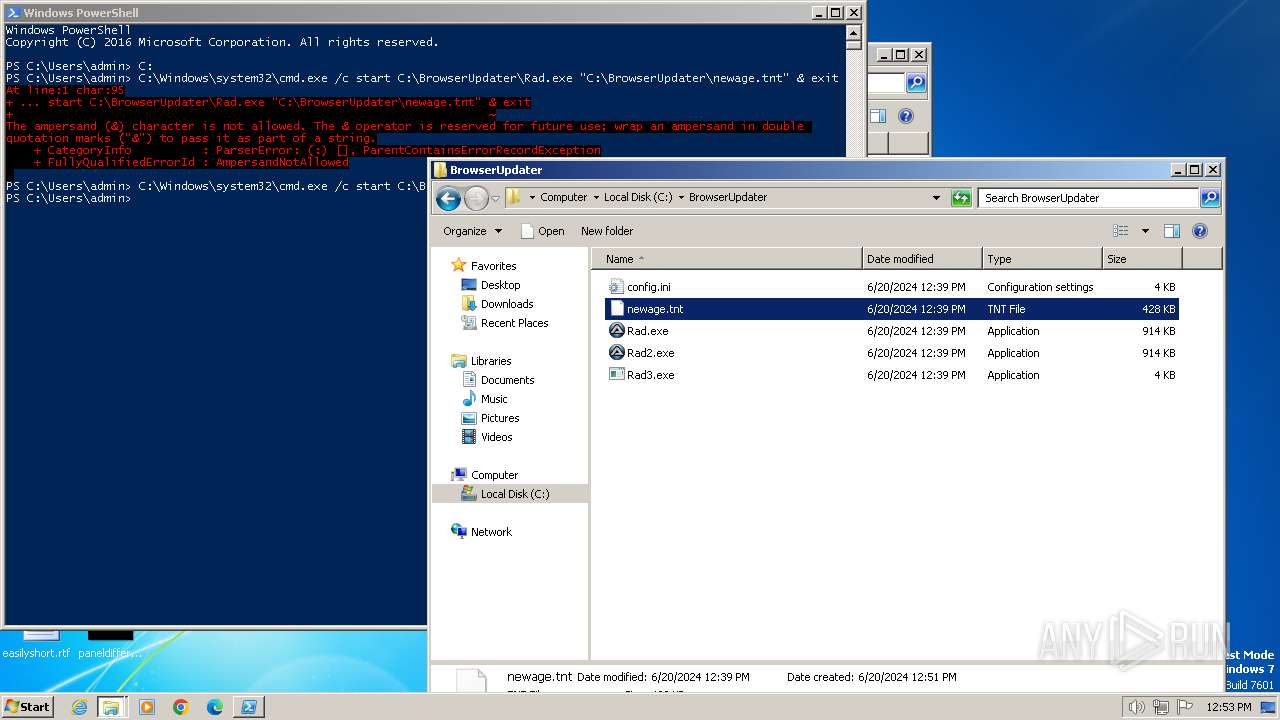
| 856 | "C:\Windows\system32\cmd.exe" /c start C:\BrowserUpdateCheck\Rad3.exe C:\BrowserUpdater\newage.tnt | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1580 | "C:\BrowserUpdateCheck\Rad3.exe" C:\BrowserUpdateCheck\BrowserChecker.tnt | C:\BrowserUpdateCheck\Rad3.exe | explorer.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Version: 3, 3, 14, 2 Modules
| |||||||||||||||
| 1800 | C:\BrowserUpdateCheck\Rad.exe C:\BrowserUpdater\newage.tnt | C:\BrowserUpdateCheck\Rad.exe | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225477 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
| 1856 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1916 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
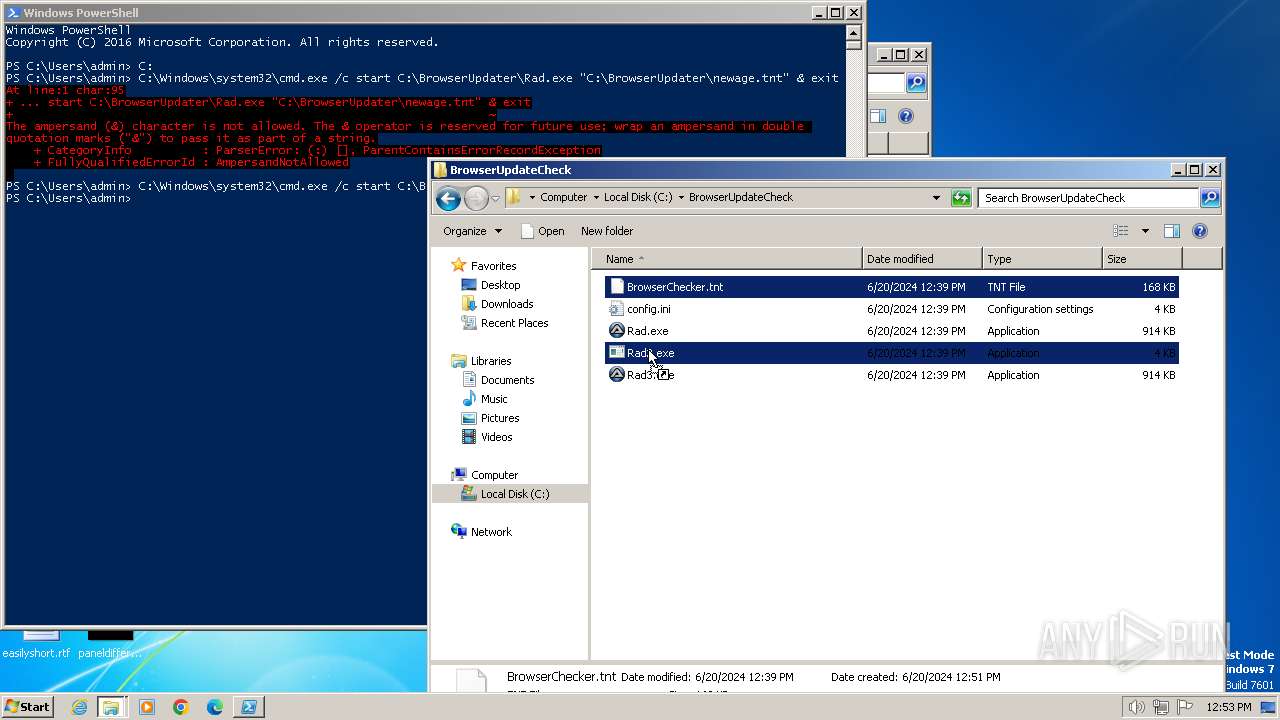
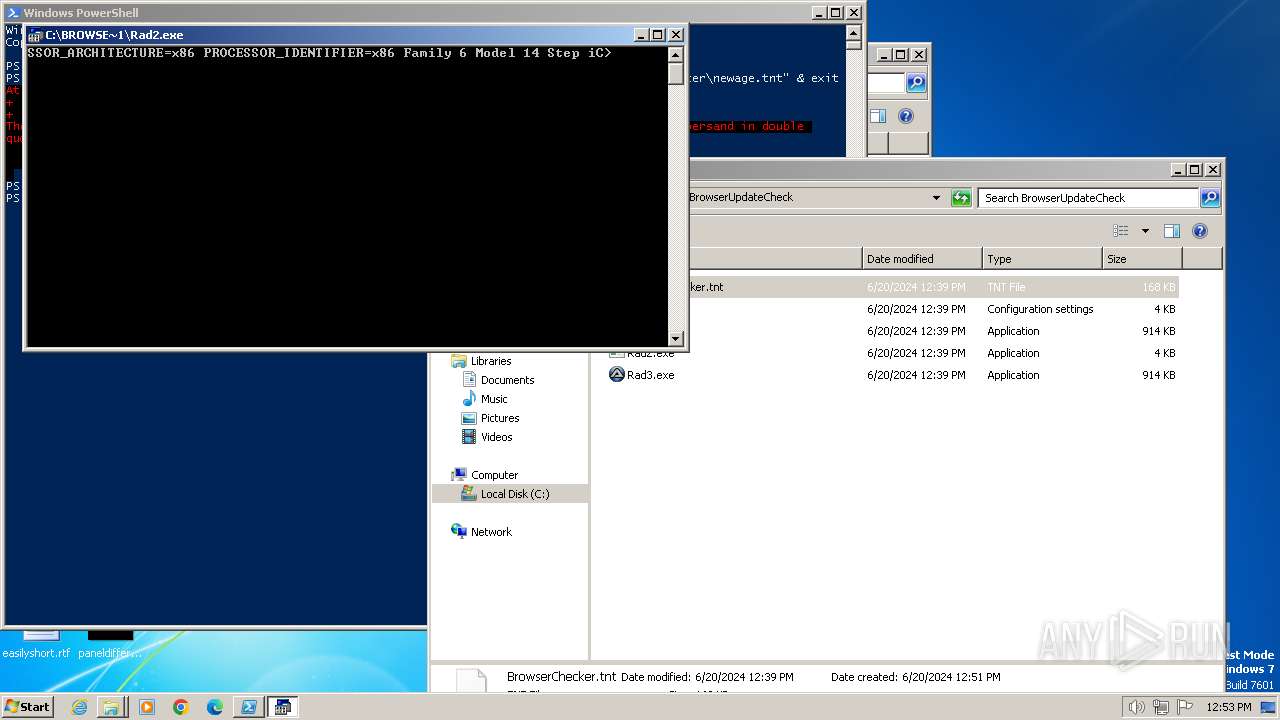
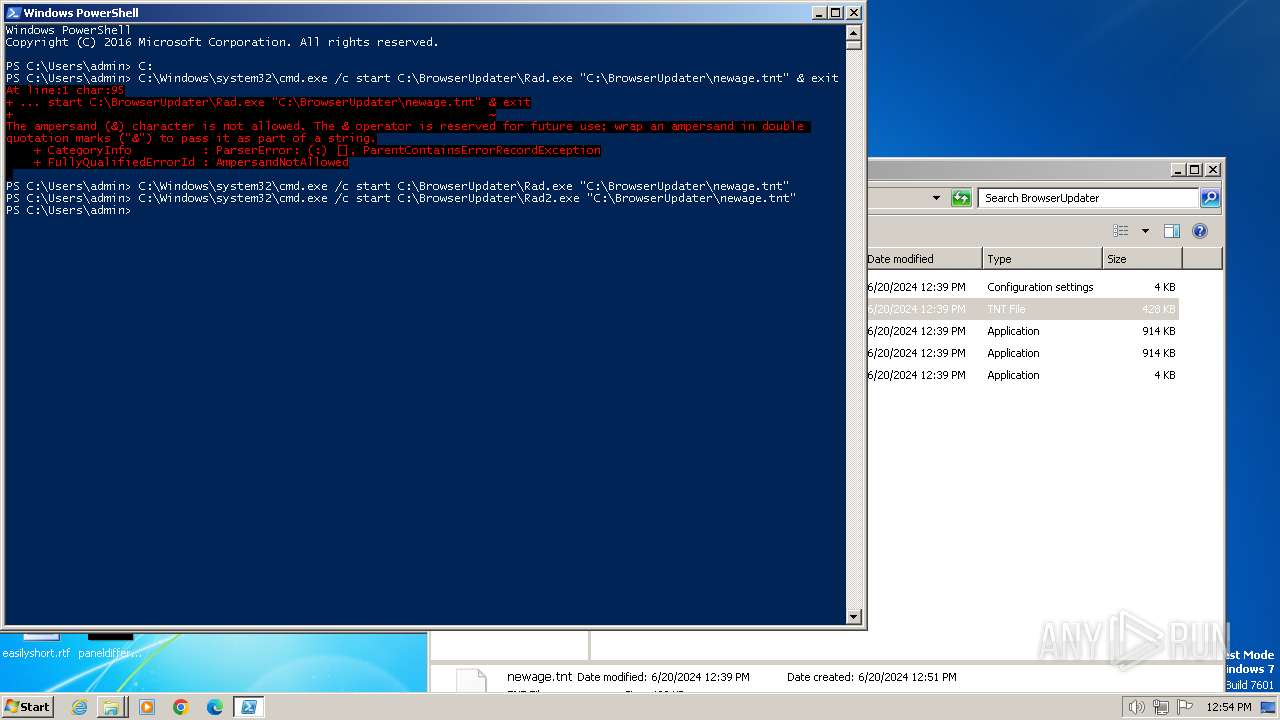
| 1980 | C:\BrowserUpdater\Rad2.exe C:\BrowserUpdater\newage.tnt | C:\BrowserUpdater\Rad2.exe | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225477 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
| 2192 | "C:\Windows\system32\cmd.exe" /c start C:\BrowserUpdater\Rad2.exe C:\BrowserUpdater\newage.tnt | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2280 | "C:\BrowserUpdater\Rad2.exe" C:\BrowserUpdater\newage.tnt | C:\BrowserUpdater\Rad2.exe | explorer.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225622 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
| 2740 | C:\BrowserUpdater\Rad.exe C:\BrowserUpdater\newage.tnt | C:\BrowserUpdater\Rad.exe | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225622 Version: 3, 3, 14, 2 Modules
| |||||||||||||||
Total events
9 687
Read events
9 611
Write events
76
Delete events
0
Modification events
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\complete_files.zip | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
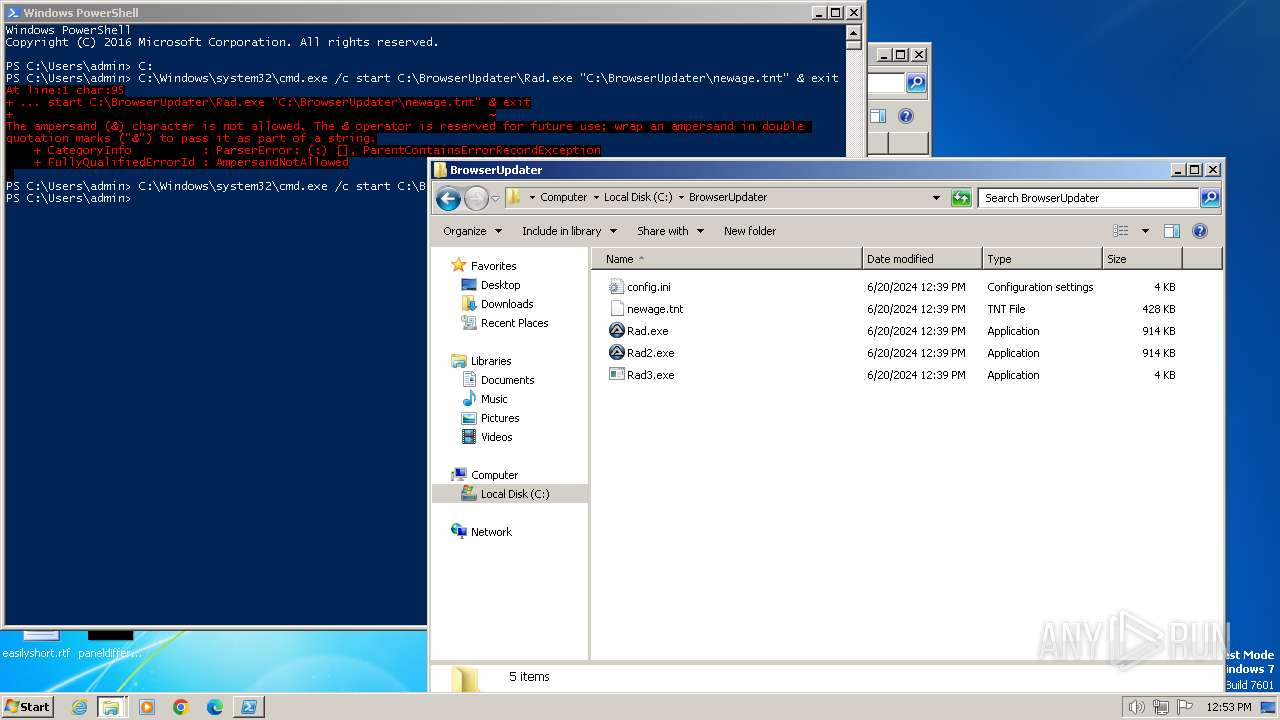
Executable files
4
Suspicious files
9
Text files
14
Unknown types
0
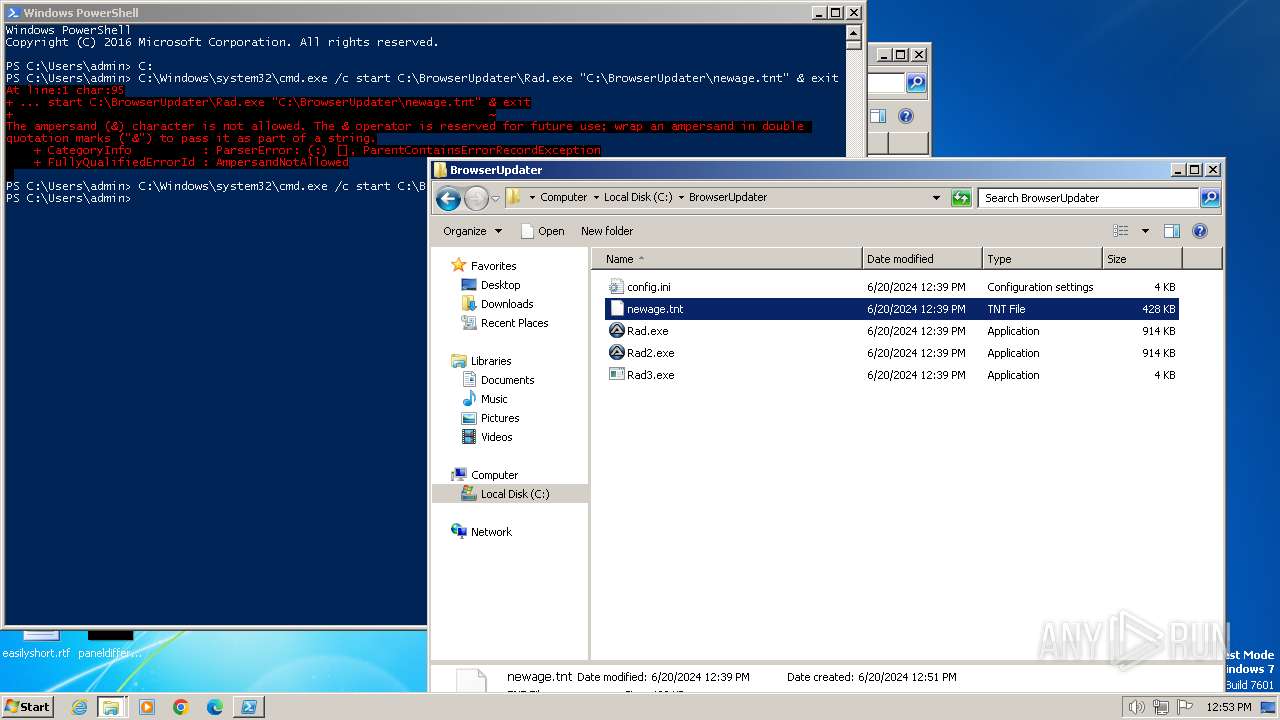
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdateCheck\Rad3.exe | executable | |
MD5:B6AB6A7F5C2A3C26A9400121149E759A | SHA256:5E5A1D3ADA76B63FC497A117390B29BB1503F17EA72D7C7F575EBF2EB8257B83 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdateCheck\config.ini | binary | |
MD5:514B372AB96214B1D67DAF7A2C3738F8 | SHA256:5BC5D7079F156599FFE11D21EAD93292C8AF3DDD058DF0EB2EB8E572DEFC9DE6 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdateCheck\Rad2.exe | text | |
MD5:B05E889E8436ED89157A2AA0CB8CDAA6 | SHA256:34358161D294CAB2AAC611EC14754204737B50C32BC2E74EC17B4C54B96A9C7A | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdater\Rad3.exe | text | |
MD5:B05E889E8436ED89157A2AA0CB8CDAA6 | SHA256:34358161D294CAB2AAC611EC14754204737B50C32BC2E74EC17B4C54B96A9C7A | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdateCheck\Rad.exe | executable | |
MD5:B6AB6A7F5C2A3C26A9400121149E759A | SHA256:5E5A1D3ADA76B63FC497A117390B29BB1503F17EA72D7C7F575EBF2EB8257B83 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdater\Rad.exe | executable | |
MD5:56EB7BF71F78DC0793D2090679C4E6D0 | SHA256:0259E374F6AAF7A7DA314AA152974666CC5FFBFC313CD278227AD85EEF47BE74 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdater\Rad2.exe | executable | |
MD5:56EB7BF71F78DC0793D2090679C4E6D0 | SHA256:0259E374F6AAF7A7DA314AA152974666CC5FFBFC313CD278227AD85EEF47BE74 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdater\newage.tnt | a3x | |
MD5:C0D3250CABC2DE36DB4E5866EB2248FA | SHA256:2325C5074D1EF57EC9BE47AC2A8CB810757B88B694A812D35132DCC1D0A0241B | |||
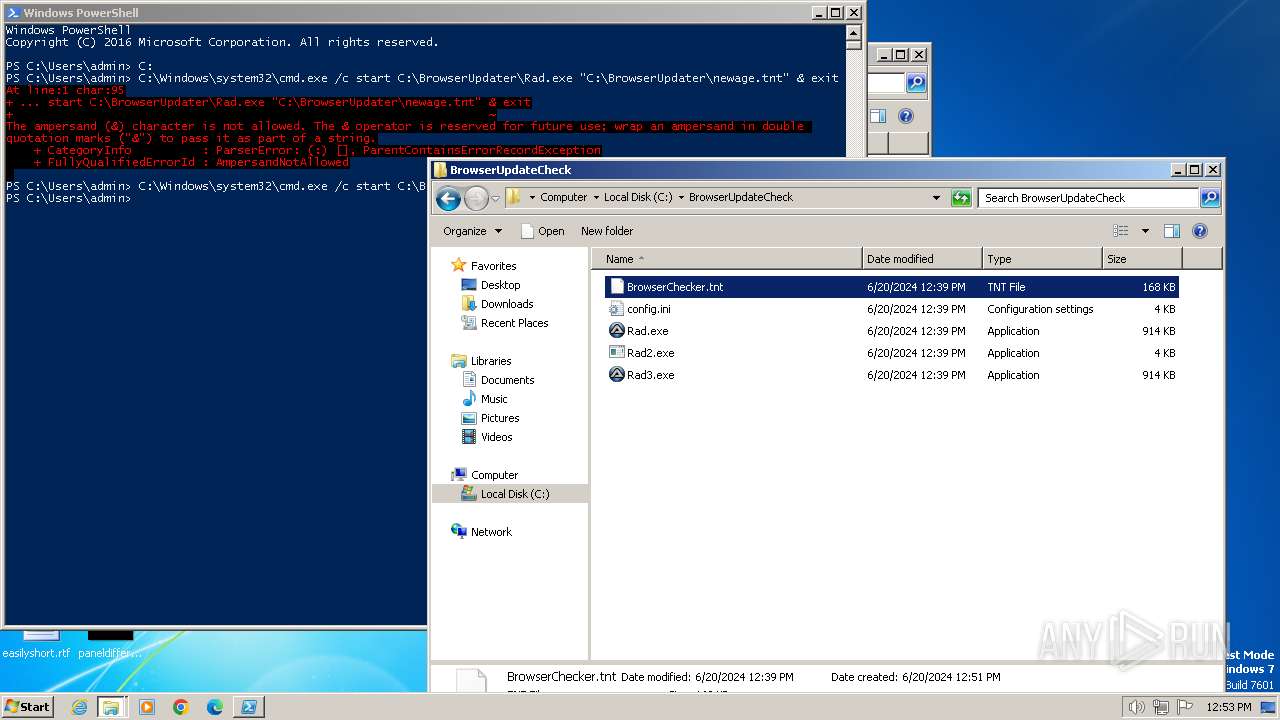
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3384.6841\complete_files\BrowserUpdateCheck\BrowserChecker.tnt | a3x | |
MD5:E6C11DF5937BC6FB8186D3784D21CDD4 | SHA256:51E9A653F581E96FE920BC5CE8E28F742BEC8E84AF8777D9D5B0EDC5B7FEF835 | |||
| 1856 | powershell.exe | C:\Users\admin\AppData\Local\Temp\h41hso0a.4q2.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 2.16.164.34:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |