| File name: | takeover.exe |
| Full analysis: | https://app.any.run/tasks/d792f6c2-a5a7-4d4c-a65d-3078433e14b2 |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 16:52:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 7E4881D42D244ED581E7BF87346CE699 |
| SHA1: | FACB1FF39A735D7F8EEBDEC5FB1867C1C1BB0EE4 |
| SHA256: | BDE8EC4D9E311D9A8E473C1827C51ED2844532C2A8EEAB4AD274CF01E30722FE |
| SSDEEP: | 3072:FPML5Ch5uLb3pW6SQ329JmyxCPPMivT1bMH6IR:wWreEbihbM6m |
MALICIOUS
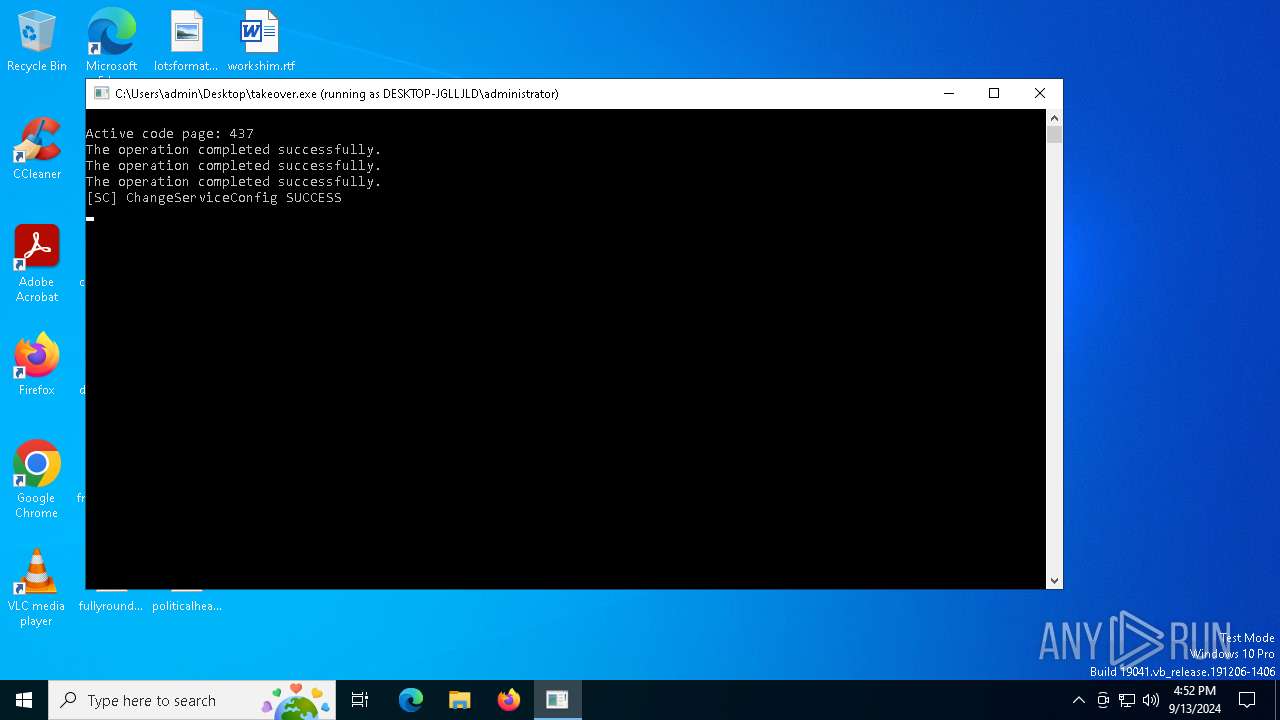
Starts NET.EXE to view/add/change user profiles
- net.exe (PID: 5940)
- cmd.exe (PID: 5720)
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 5468)
- cmd.exe (PID: 5720)
- net.exe (PID: 1812)
- net.exe (PID: 6924)
SUSPICIOUS
Starts CMD.EXE for commands execution
- takeover.exe (PID: 4976)
- cmd.exe (PID: 5720)
Starts application with an unusual extension
- cmd.exe (PID: 5720)
Executing commands from a ".bat" file
- takeover.exe (PID: 4976)
Starts SC.EXE for service management
- cmd.exe (PID: 5720)
Application launched itself
- cmd.exe (PID: 5720)
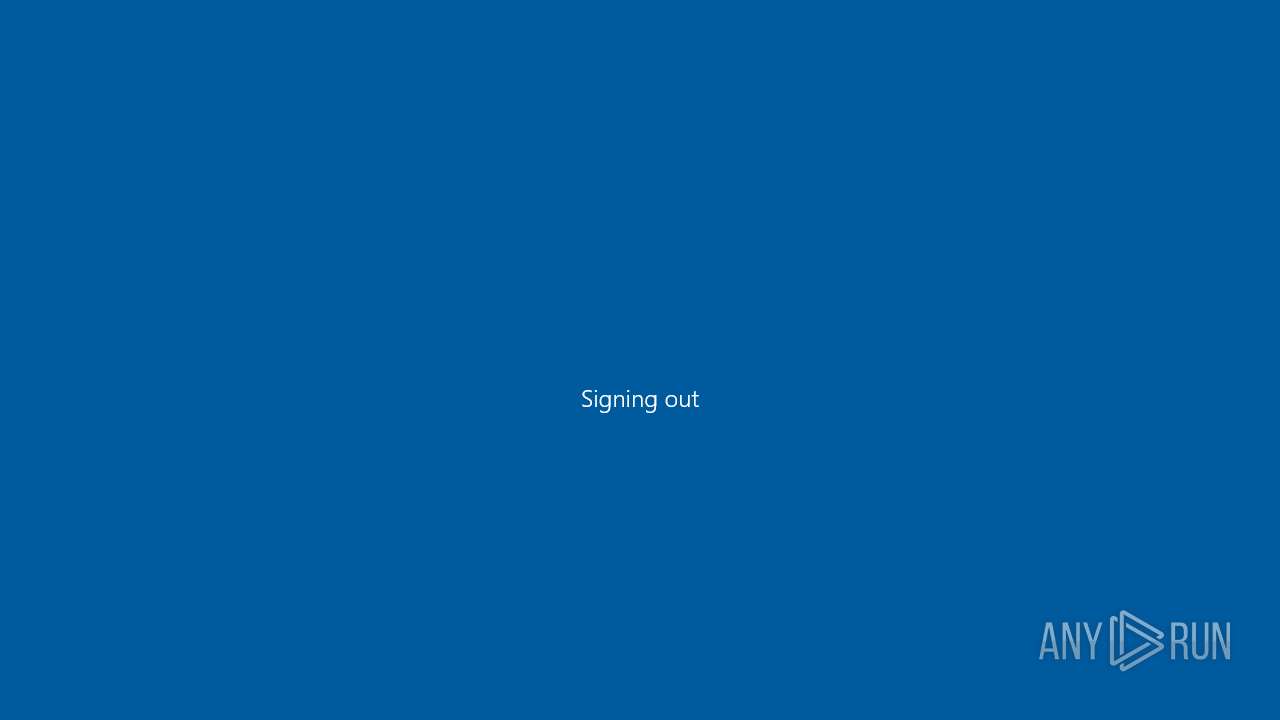
The system shut down or reboot
- cmd.exe (PID: 5720)
Reads security settings of Internet Explorer
- GameBar.exe (PID: 6240)
- StartMenuExperienceHost.exe (PID: 5688)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5688)
- SearchApp.exe (PID: 1644)
- SystemSettings.exe (PID: 3852)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5720)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 5720)
Checks supported languages
- takeover.exe (PID: 4976)
- GameBar.exe (PID: 6240)
- StartMenuExperienceHost.exe (PID: 5688)
- SearchApp.exe (PID: 1644)
- SystemSettings.exe (PID: 3852)
- chcp.com (PID: 5124)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4952)
- dllhost.exe (PID: 6956)
- ApplicationFrameHost.exe (PID: 2136)
Reads the computer name
- StartMenuExperienceHost.exe (PID: 5688)
- GameBar.exe (PID: 6240)
- SearchApp.exe (PID: 1644)
- SystemSettings.exe (PID: 3852)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5688)
- SearchApp.exe (PID: 1644)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 5688)
Checks proxy server information
- SearchApp.exe (PID: 1644)
Creates files or folders in the user directory
- dllhost.exe (PID: 4952)
- dllhost.exe (PID: 6956)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 1644)
Reads the software policy settings
- SearchApp.exe (PID: 1644)
Reads Environment values
- SearchApp.exe (PID: 1644)
The process uses the downloaded file
- SystemSettings.exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:18:05+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70144 |
| InitializedDataSize: | 21504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
191
Monitored processes
33
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | SC CONFIG RmSvc START= DISABLED | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 252 | NET FILE | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | C:\WINDOWS\system32\net1 localgroup Users Administrator /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | net localgroup Users Administrator /add | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | shutdown -L | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
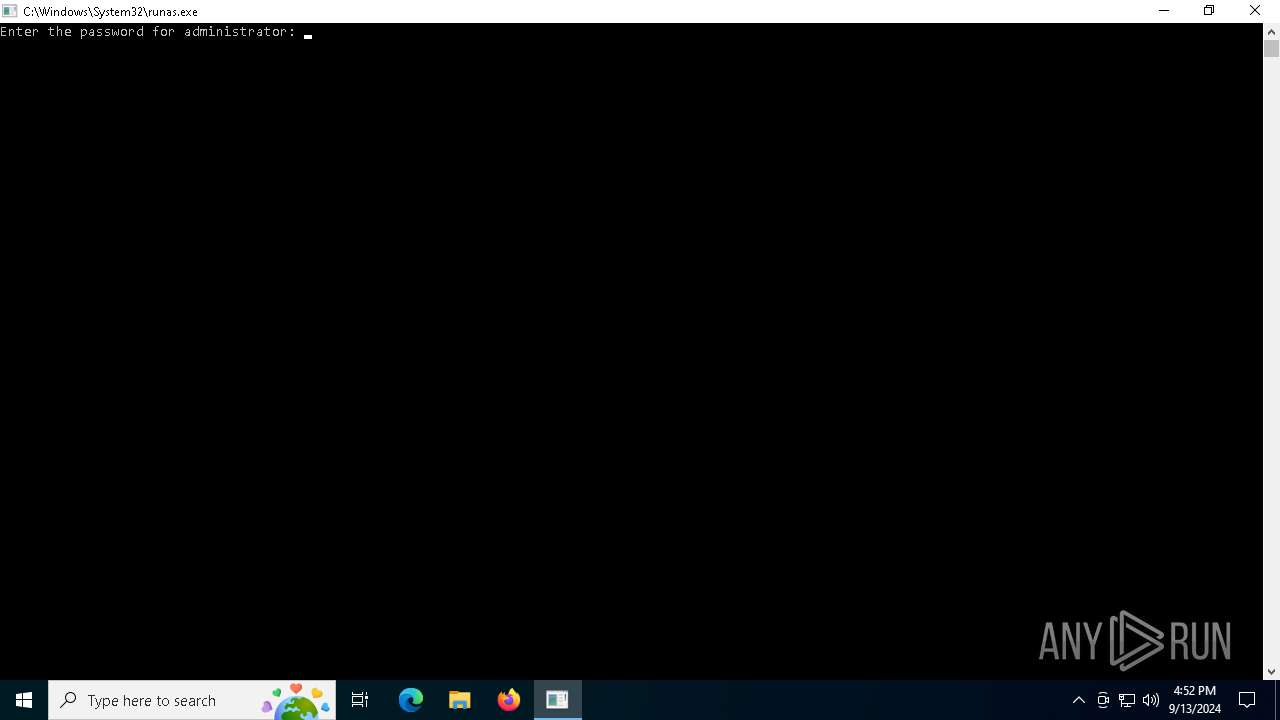
| 2456 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\takeover.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3044 | C:\WINDOWS\system32\DllHost.exe /Processid:{7966B4D8-4FDC-4126-A10B-39A3209AD251} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3308 | C:\WINDOWS\system32\net1 user 66541 foxxopower63 /add | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 739
Read events
18 595
Write events
136
Delete events
8
Modification events
| (PID) Process: | (5544) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore |
| Operation: | write | Name: | Disable Restore |
Value: 1 | |||
| (PID) Process: | (5244) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticecaption |
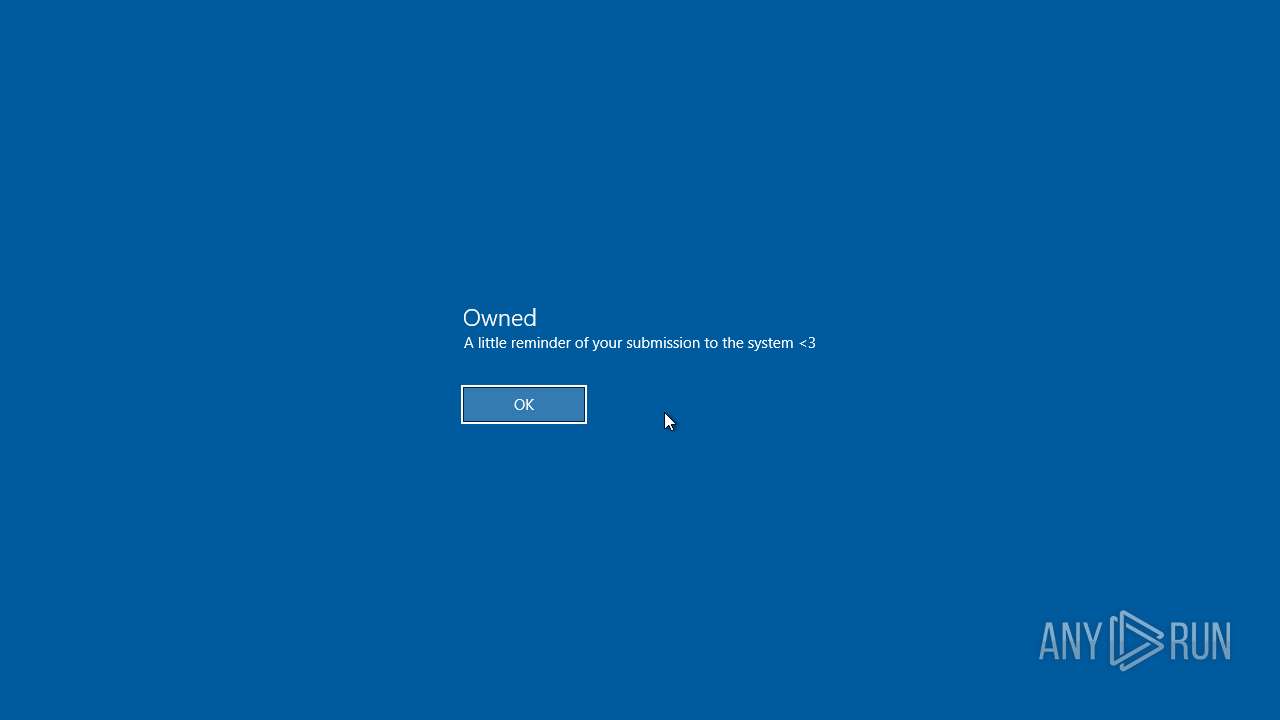
Value: Owned | |||
| (PID) Process: | (3852) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticetext |
Value: A little reminder of your submission to the system <3 | |||
| (PID) Process: | (5688) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{c6b18aa3-c425-7487-744d-b6c657dcd7e8}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 01000000E929E351FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | InstalledVersionMajor |
Value: 0200958EE551FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | InstalledVersionMinor |
Value: 22009FF2E751FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | InstalledVersionBuild |
Value: 616D9FF2E751FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | InstalledVersionRevision |
Value: 00009FF2E751FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | PreviousAppTerminationFromSuspended |
Value: 009FF2E751FD05DB01 | |||
| (PID) Process: | (6240) GameBar.exe | Key: | \REGISTRY\A\{a42095c9-b64d-57c1-3d7b-f7ed297b6a55}\LocalState |
| Operation: | write | Name: | CurrentDisplayMonitor |
Value: 670061006D006500000087BAEC51FD05DB01 | |||
Executable files
2
Suspicious files
112
Text files
171
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4952 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | — | |
MD5:— | SHA256:— | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:676FEE16D97DC73B2C5B173614161536 | SHA256:DC881A215651B4064865D9759E052ED1787B7F393F78DA5A4540000B2FD5078E | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\-UAIppANYxiGpRWJy2NDph4qOEw.gz[1].js | s | |
MD5:9E527B91C2D8B31B0017B76049B5E4E3 | SHA256:38EDF0F961C1CCB287880B88F12F370775FC65B2E28227EEE215E849CDBE9BBC | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\4-xJy3tX6bM2BGl5zKioiEcQ1TU[1].css | text | |
MD5:94D8383805B336E533D1D234AAA98A21 | SHA256:699D6C87C646D3875C45FAB214BFE2E385B54F325F25818C72C2C45C1A5F6897 | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:120268F0C8906E9CC549E16FC741A298 | SHA256:A034E9028D0E68DECCF1308AABDF0001EBB7E524268C6A11DEFE44321230F8DA | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:EFA98D03F143481FF435063F41EE6D6F | SHA256:19634356D7361A3EECABC43D9AD613AF314779BCEF6579E32898B7828FDEEF98 | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\4bnLx4S3ZRMpYV30k3R5vRy8JVg[1].js | s | |
MD5:97540BC45CFB7C7C4D859A7E1CE839BA | SHA256:4AE944B4A382D05A8A5B657105ADD88DD8B8F59D6309567E179CA64DF19F6075 | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\CYGXBN1kkA_ojDY5vKbCoG4Zy0E[1].css | text | |
MD5:DF25912CCFEE50A9E57BC97B4D05B5C0 | SHA256:3CA3D1262A62E919C72A641F7491B38769CFB8149704E69CB6C960836DD9C6F8 | |||
| 1644 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\_BjeFNPDJ-N9umMValublyrbq4Y[1].css | text | |
MD5:15DC838A1A66277F9F4D915124DFFBBC | SHA256:9C947D5F732431197DA9DB1F159CB3D4CDC5DBFE55FDC0A9513E571FF31236A1 | |||
| 4952 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.jfm | dbf | |
MD5:D5EC0E16E7D7E892B953082E40AC4A54 | SHA256:5BBBC348E9EDCF9F62282704E5446AC3FD28370FA51ABB7F3D86D8D91D6C0C75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5796 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3896 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1644 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1752 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3896 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6164 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5796 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1752 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1752 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |