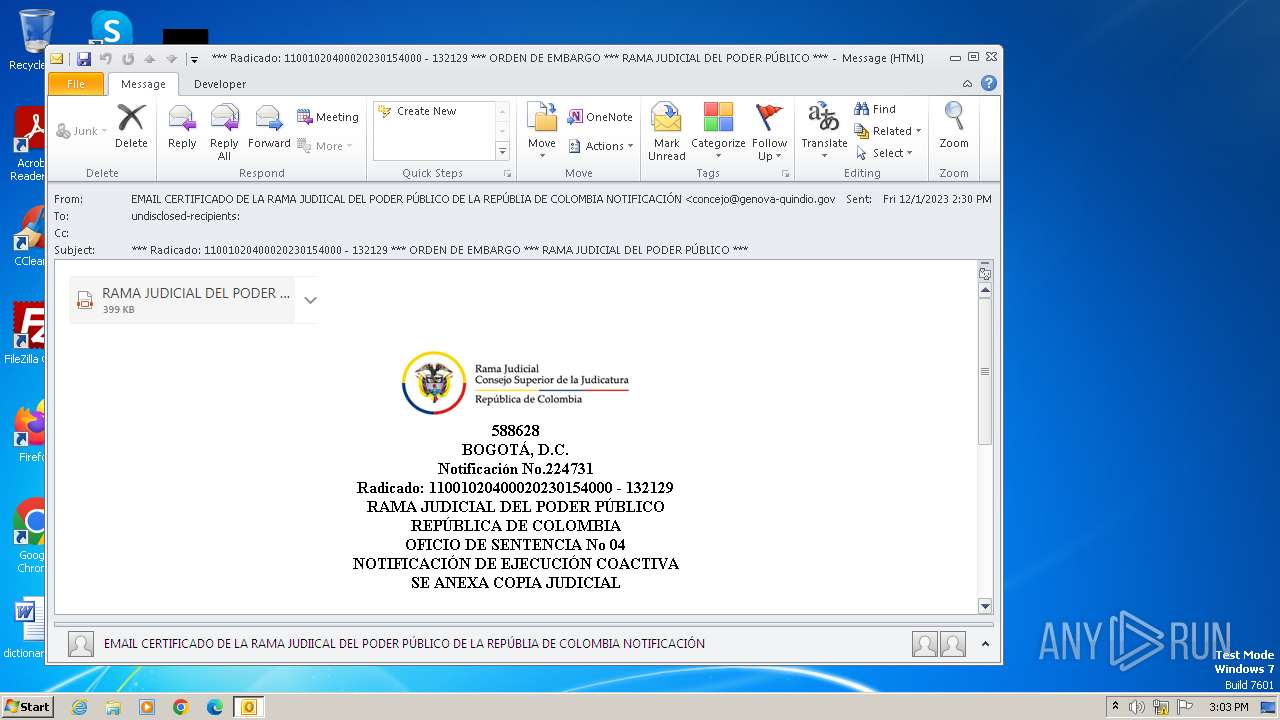
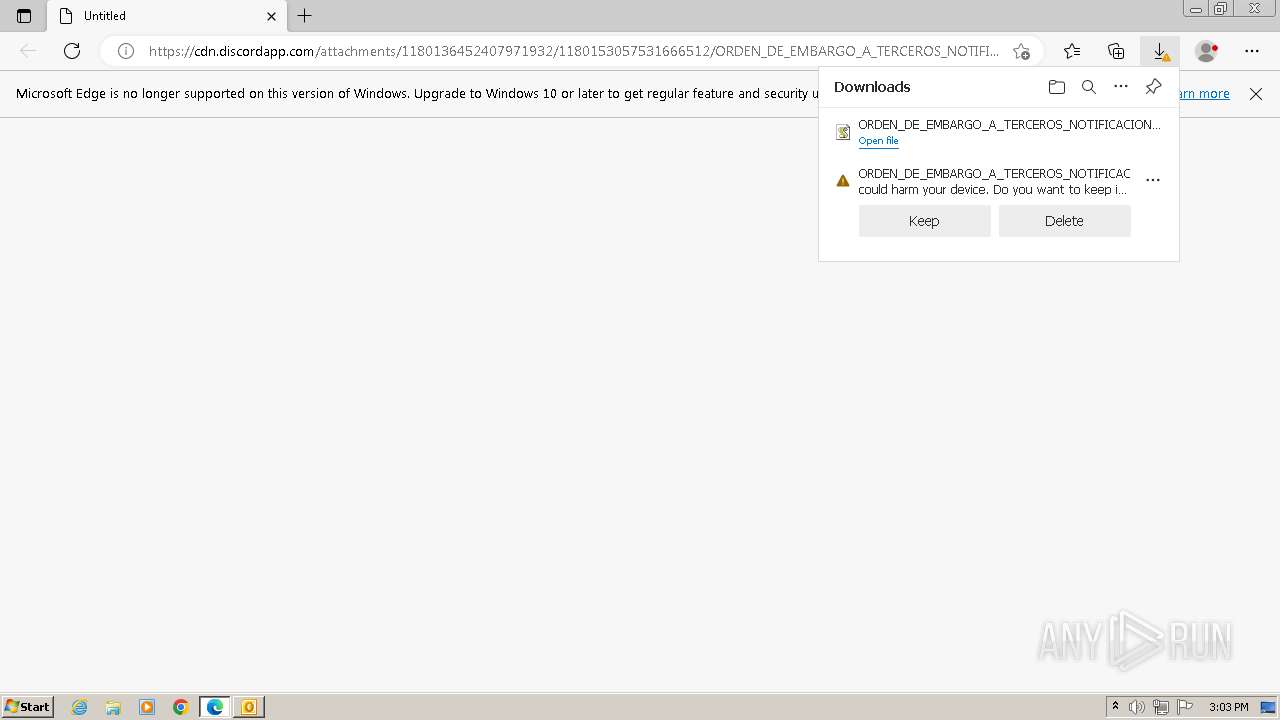
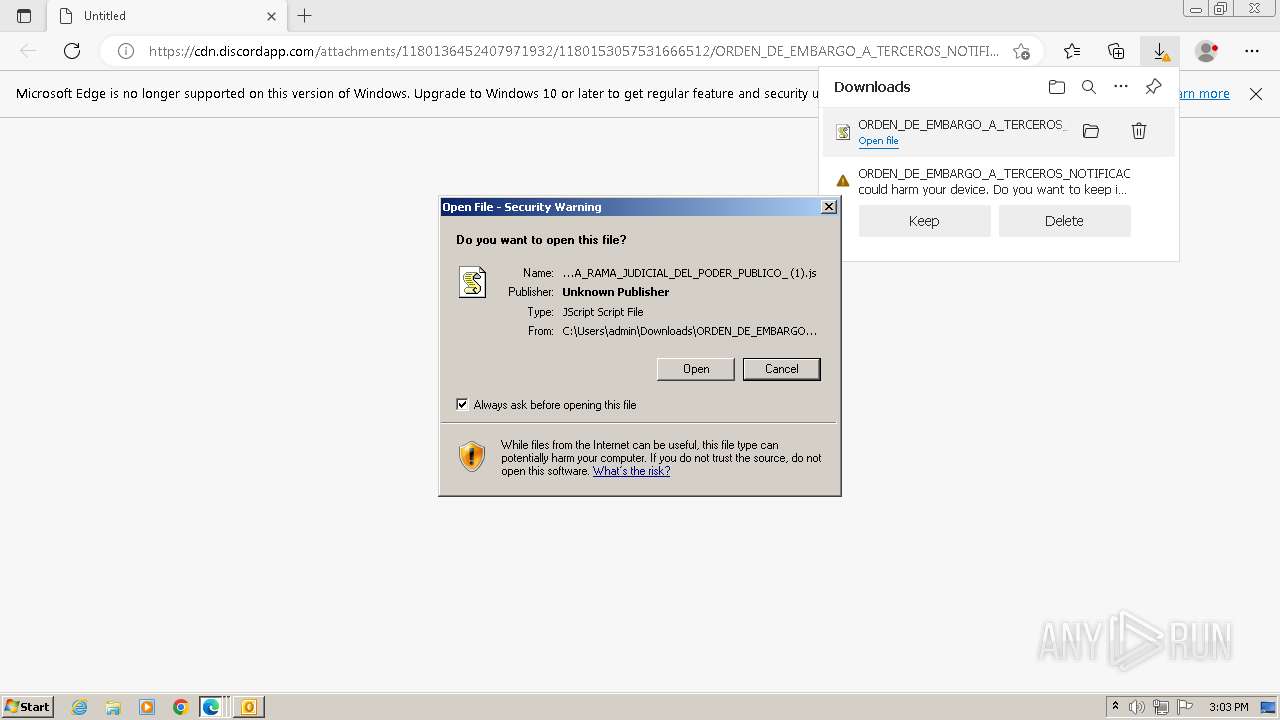
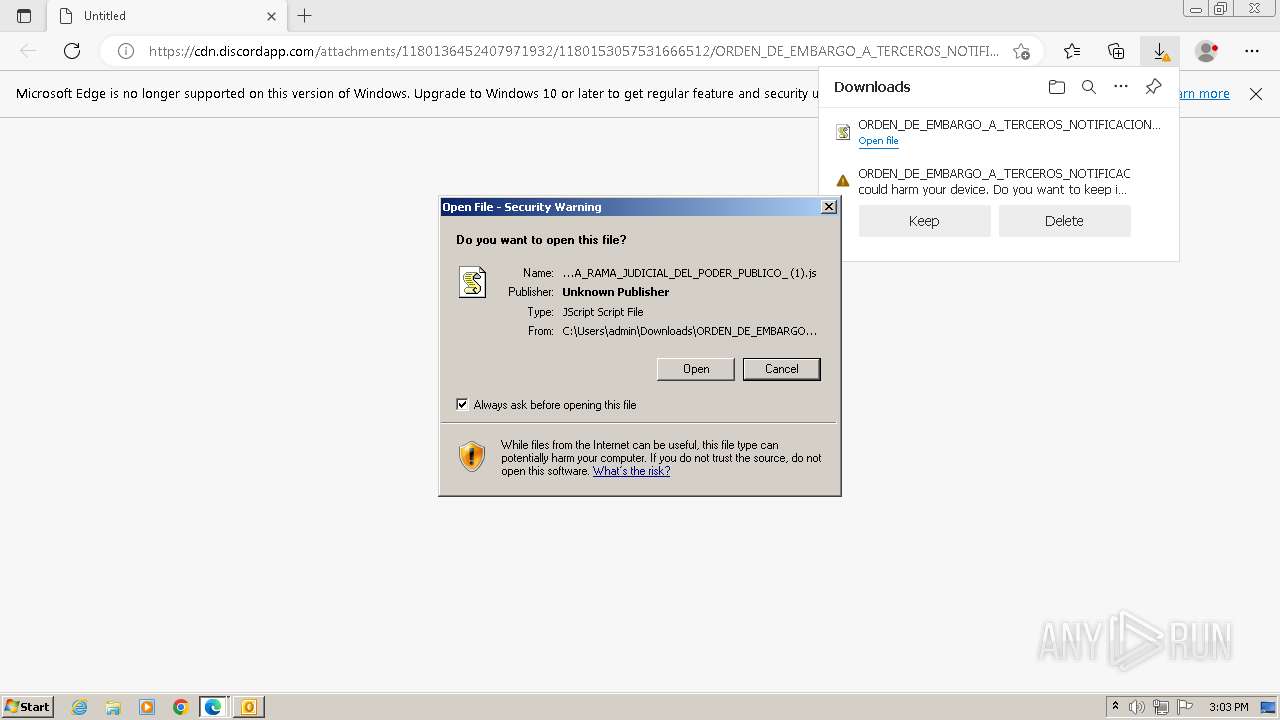
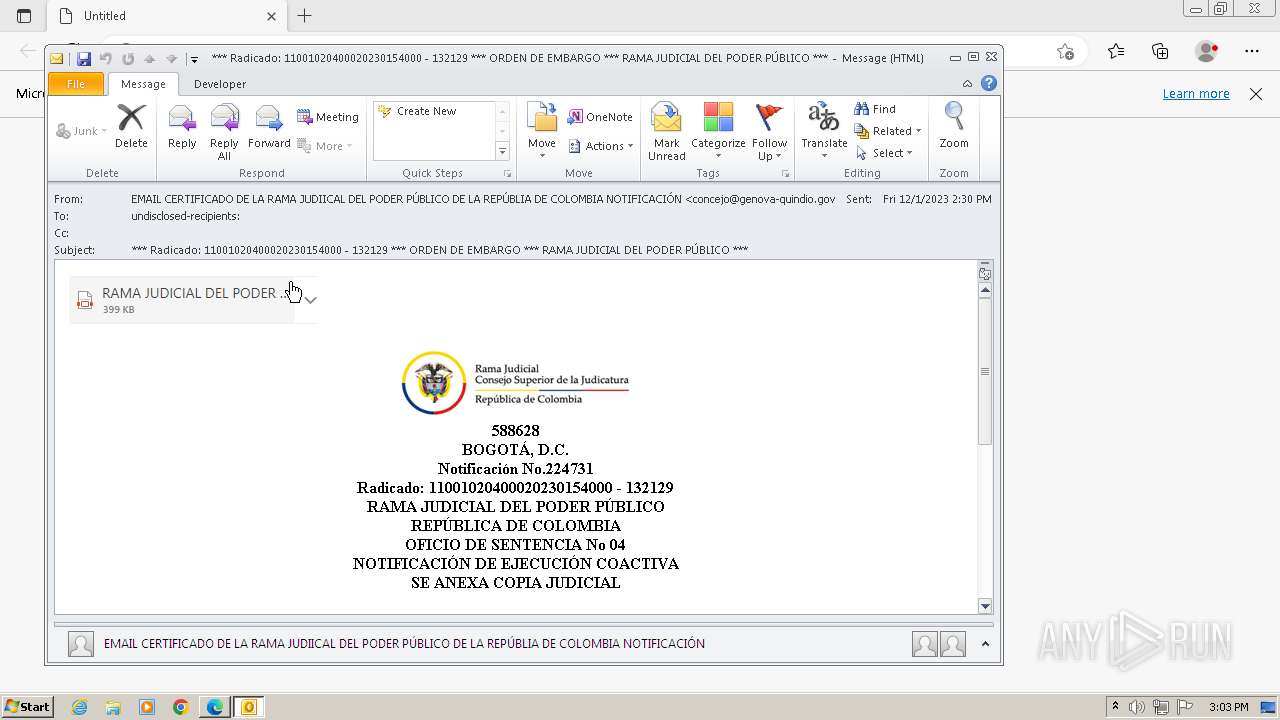
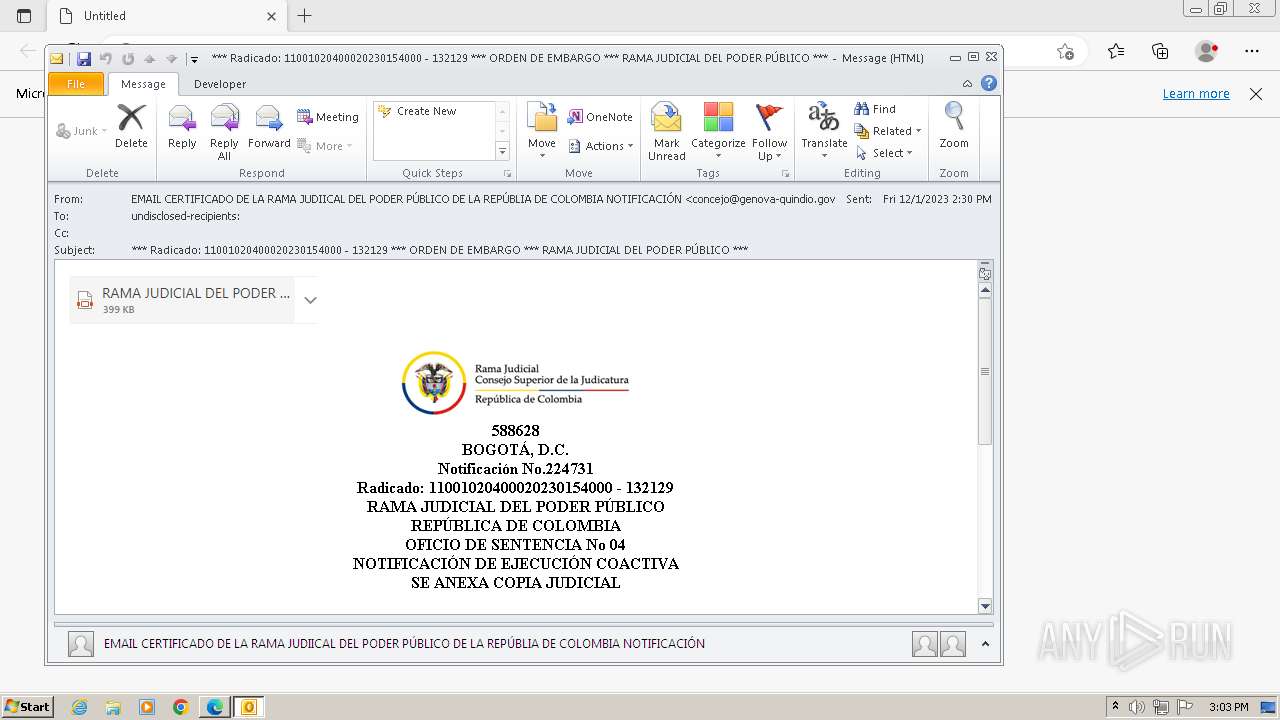
| File name: | ___ Radicado_ 11001020400020230154000 - 132129 ___ ORDEN DE EMBARGO ___ RAMA JUDICIAL DEL PODER PÚBLICO ___.eml |
| Full analysis: | https://app.any.run/tasks/d24fbf09-b7d2-4e60-92ff-9525867a69d6 |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2023, 15:03:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 9F3BDF14DC198F7FD7958BB1CB1D3B86 |
| SHA1: | 12B3D98C291FB7FDE8A05C38E22F63066BBF5054 |
| SHA256: | BDD260094E258CD80D6A7A454AD9C0DDA7B36714A476C21A7CF35CD6D15D7EBB |
| SSDEEP: | 768:43KGSbRVkGyq0qx8Y2FKRd23N44b6NVZAMFau:bbRVkvif2FKR4yvyM4u |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1088)
- wscript.exe (PID: 1864)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1088)
- wscript.exe (PID: 1864)
Unusual connection from system programs
- wscript.exe (PID: 1088)
- wscript.exe (PID: 1864)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1864)
- wscript.exe (PID: 1088)
Bypass execution policy to execute commands
- powershell.exe (PID: 4044)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 3052)
Run PowerShell with an invisible window
- powershell.exe (PID: 4044)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 3052)
Stego campaign has been detected
- powershell.exe (PID: 4044)
- powershell.exe (PID: 4088)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 1864)
- powershell.exe (PID: 4044)
- wscript.exe (PID: 1088)
- powershell.exe (PID: 4088)
SUSPICIOUS
Discord domain found in command line (probably downloading payload)
- msedge.exe (PID: 2220)
- msedge.exe (PID: 3144)
- msedge.exe (PID: 2120)
The process executes JS scripts
- msedge.exe (PID: 3144)
Reads the Internet Settings
- wscript.exe (PID: 1864)
- powershell.exe (PID: 2492)
- wscript.exe (PID: 1088)
- powershell.exe (PID: 3052)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 1864)
- powershell.exe (PID: 4044)
- wscript.exe (PID: 1088)
- powershell.exe (PID: 4088)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1864)
- wscript.exe (PID: 1088)
Powershell version downgrade attack
- powershell.exe (PID: 4044)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 3052)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 1864)
- wscript.exe (PID: 1088)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 1864)
- powershell.exe (PID: 4044)
- wscript.exe (PID: 1088)
- powershell.exe (PID: 4088)
Application launched itself
- powershell.exe (PID: 4044)
- powershell.exe (PID: 4088)
Probably download files using WebClient
- powershell.exe (PID: 4044)
- powershell.exe (PID: 4088)
Unusual connection from system programs
- powershell.exe (PID: 2492)
- powershell.exe (PID: 3052)
The Powershell connects to the Internet
- powershell.exe (PID: 2492)
- powershell.exe (PID: 3052)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 824)
Reads the computer name
- wmpnscfg.exe (PID: 824)
Checks supported languages
- wmpnscfg.exe (PID: 824)
Application launched itself
- msedge.exe (PID: 2220)
- msedge.exe (PID: 3144)
- msedge.exe (PID: 2120)
The process uses the downloaded file
- msedge.exe (PID: 1736)
- msedge.exe (PID: 3144)
- msedge.exe (PID: 2028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
78
Monitored processes
37
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4320 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x600ef598,0x600ef5a8,0x600ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1552 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4384 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
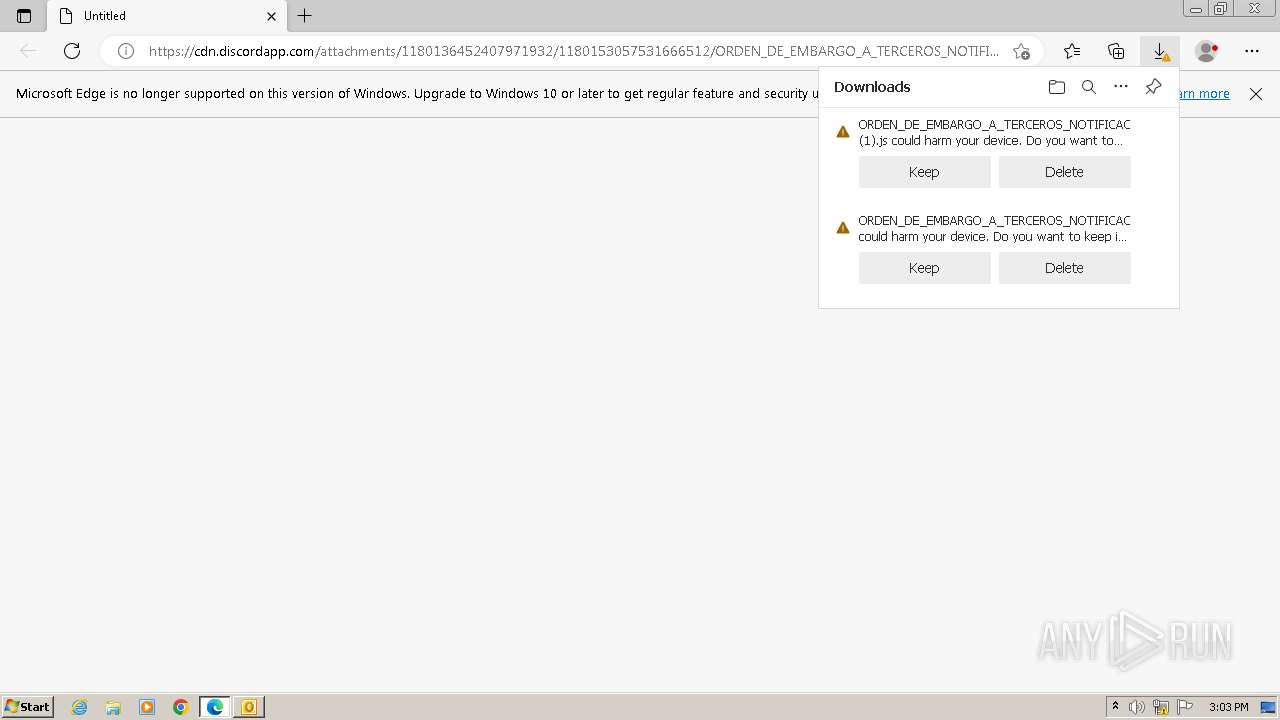
| 1088 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\ORDEN_DE_EMBARGO_A_TERCEROS_NOTIFICACION_ELECTRONICA_RAMA_JUDICIAL_DEL_PODER_PUBLICO_ (1).js" | C:\Windows\System32\wscript.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1360 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x600ef598,0x600ef5a8,0x600ef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2320 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4284 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4076 --field-trial-handle=1228,i,13702130890774384085,11039719554970581173,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
26 647
Read events
25 898
Write events
729
Delete events
20
Modification events
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2644) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
68
Text files
48
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR62D5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2644 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3964 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF207b2f.TMP | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF207b7d.TMP | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF207b8d.TMP | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF207beb.TMP | — | |
MD5:— | SHA256:— | |||
| 3144 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
35
DNS requests
29
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2492 | powershell.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0c669870c6a5d678 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2644 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3144 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3204 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3204 | msedge.exe | 162.159.130.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
3204 | msedge.exe | 20.105.95.163:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3204 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
cdn.discordapp.com |
| shared |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
dl-edge.smartscreen.microsoft.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
app-edge.smartscreen.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3204 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3204 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3204 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
3204 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3204 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1088 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
1864 | wscript.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
Process | Message |
|---|---|
msedge.exe | [1201/150352.080:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|