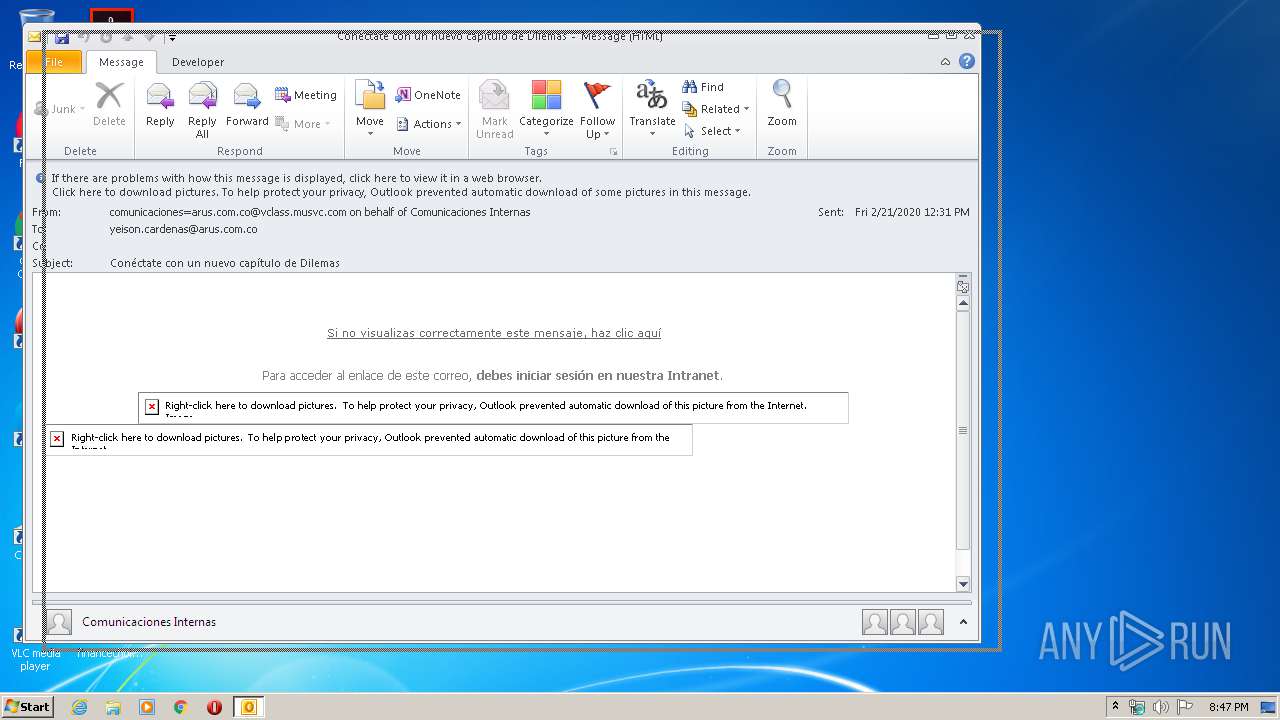
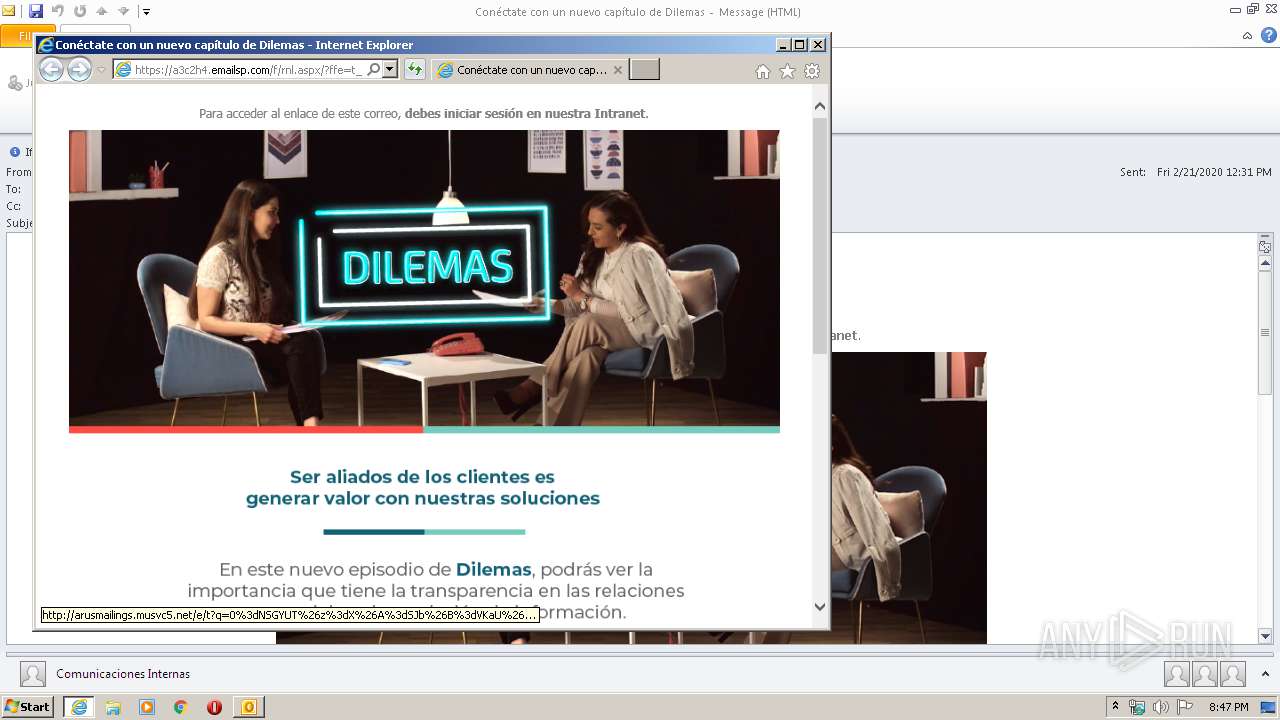
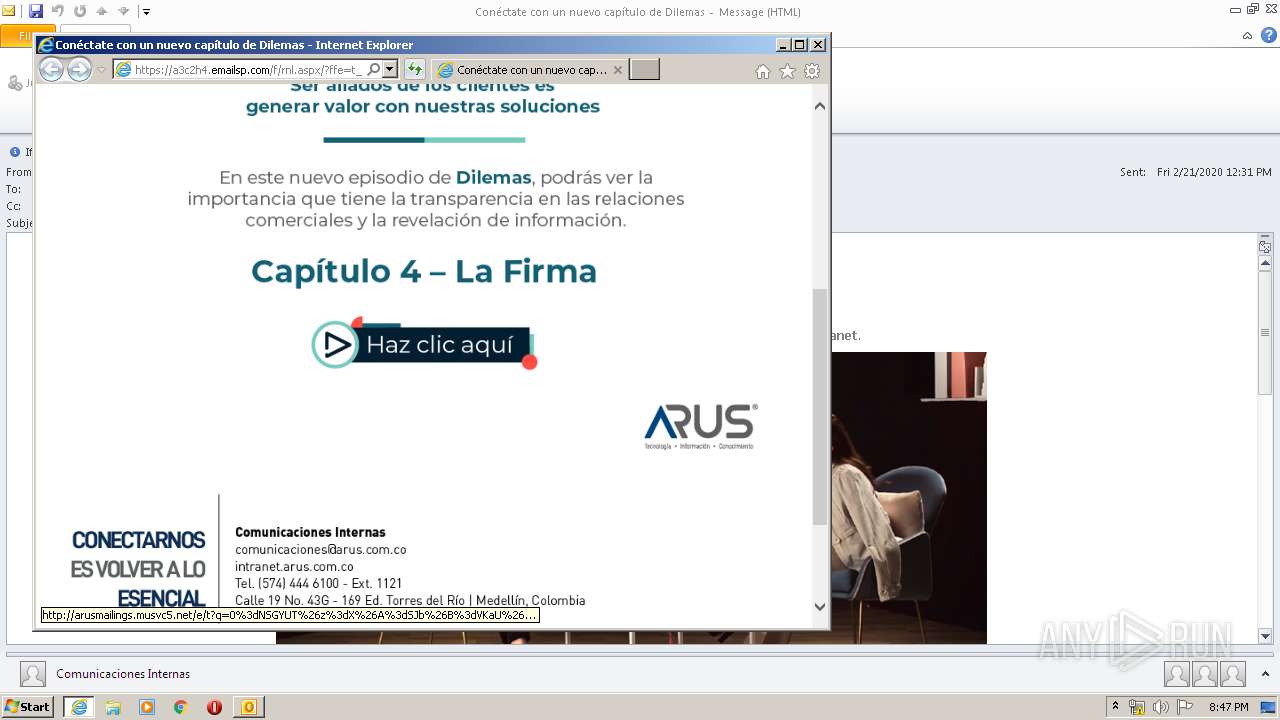
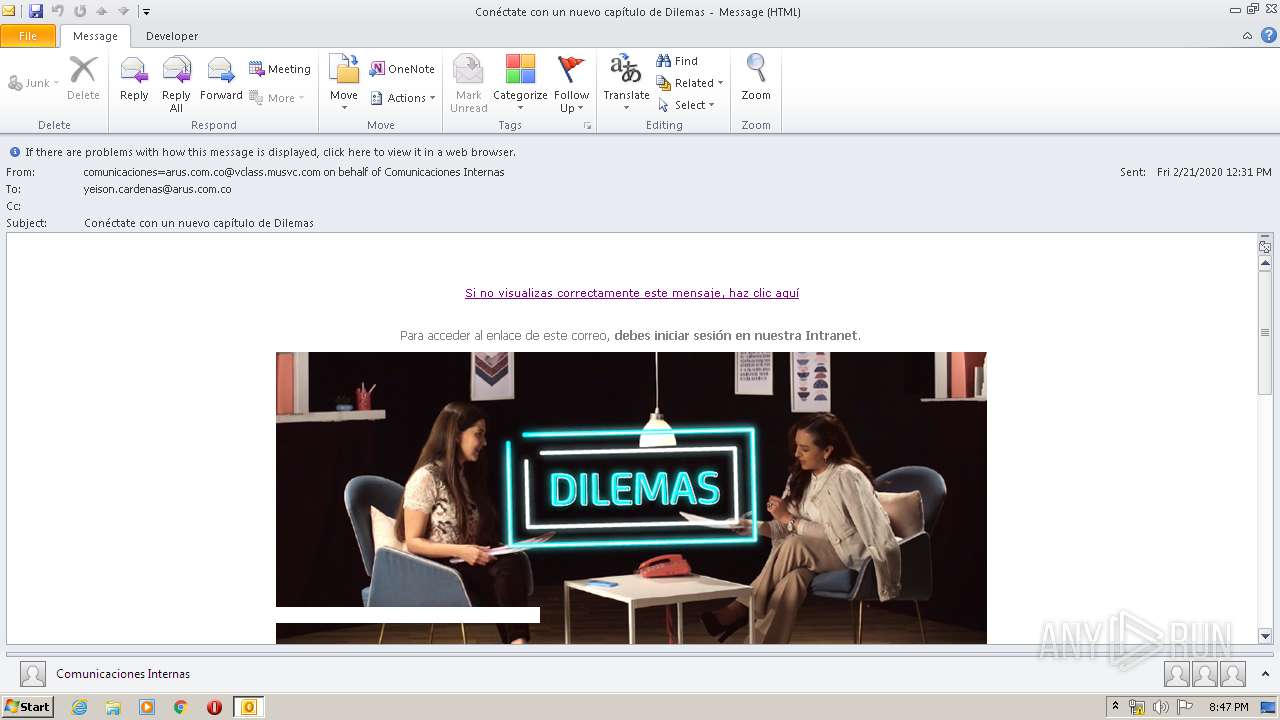
| File name: | Conéctate con un nuevo capítulo de Dilemas.msg |
| Full analysis: | https://app.any.run/tasks/1ba4f60b-1a21-441c-9acb-ed633f43e805 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 20:46:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 19DB2D8E08A1E5CB2AE915EC376D8F8B |
| SHA1: | 2406F2461F81A6F185B424CD2344BAA7DED4978D |
| SHA256: | BDD1626C4C7E14BEC3D8C3D0BE7042FE464363B9575DAC44609B9C321C73F006 |
| SSDEEP: | 384:VnOMxcw3GagSm1oN9N7E4HdEx0wvjktUN2q3byFTmhMaeEaiNP0D3yP:VnH3WF1o3N7E4a5AUoVBmhMaeNihP |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 304)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 304)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 304)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 304)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 536)
- iexplore.exe (PID: 576)
Changes internet zones settings
- iexplore.exe (PID: 576)
Reads internet explorer settings
- iexplore.exe (PID: 536)
Reads settings of System Certificates
- iexplore.exe (PID: 576)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 304)
Changes settings of System certificates
- iexplore.exe (PID: 576)
Adds / modifies Windows certificates
- iexplore.exe (PID: 576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Conéctate con un nuevo capítulo de Dilemas.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:576 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
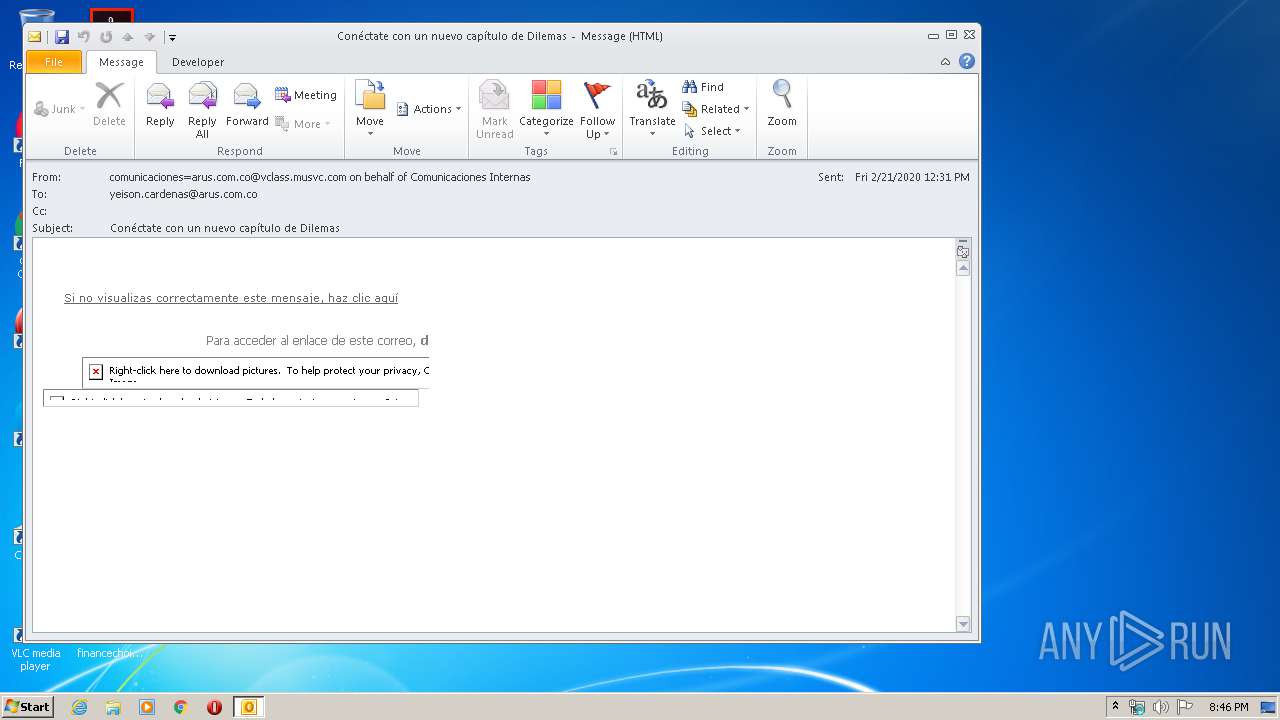
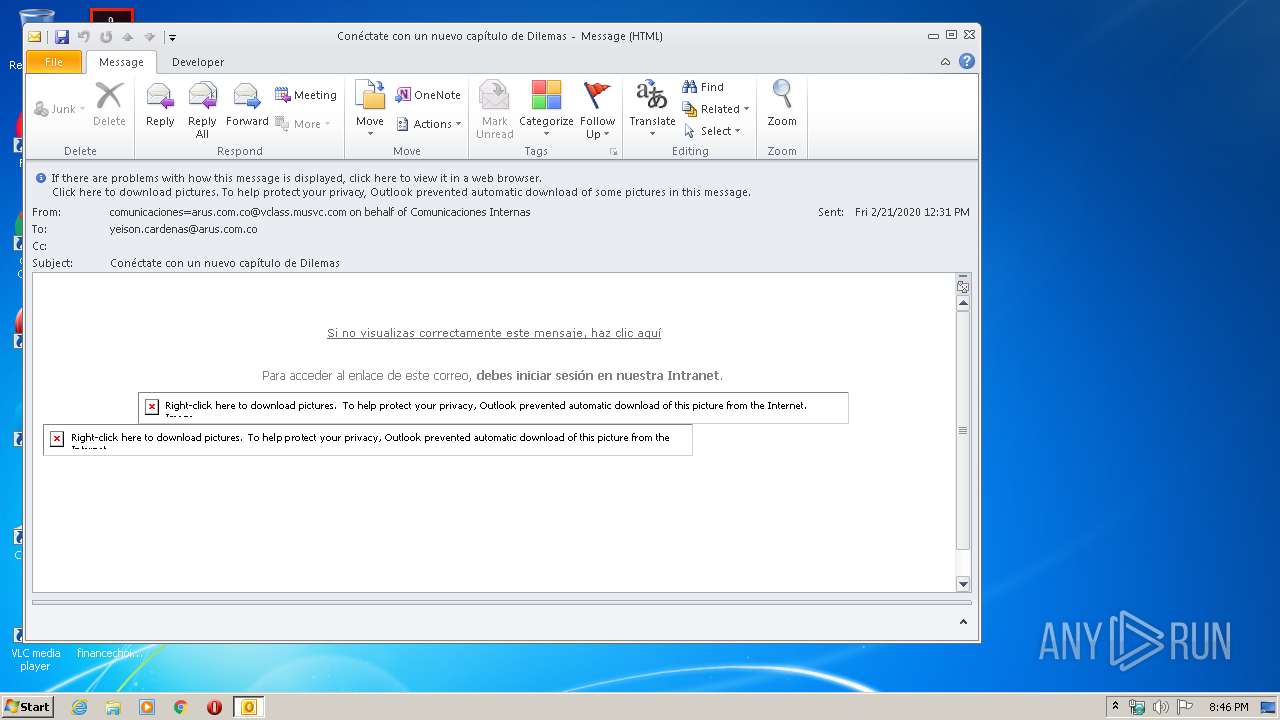
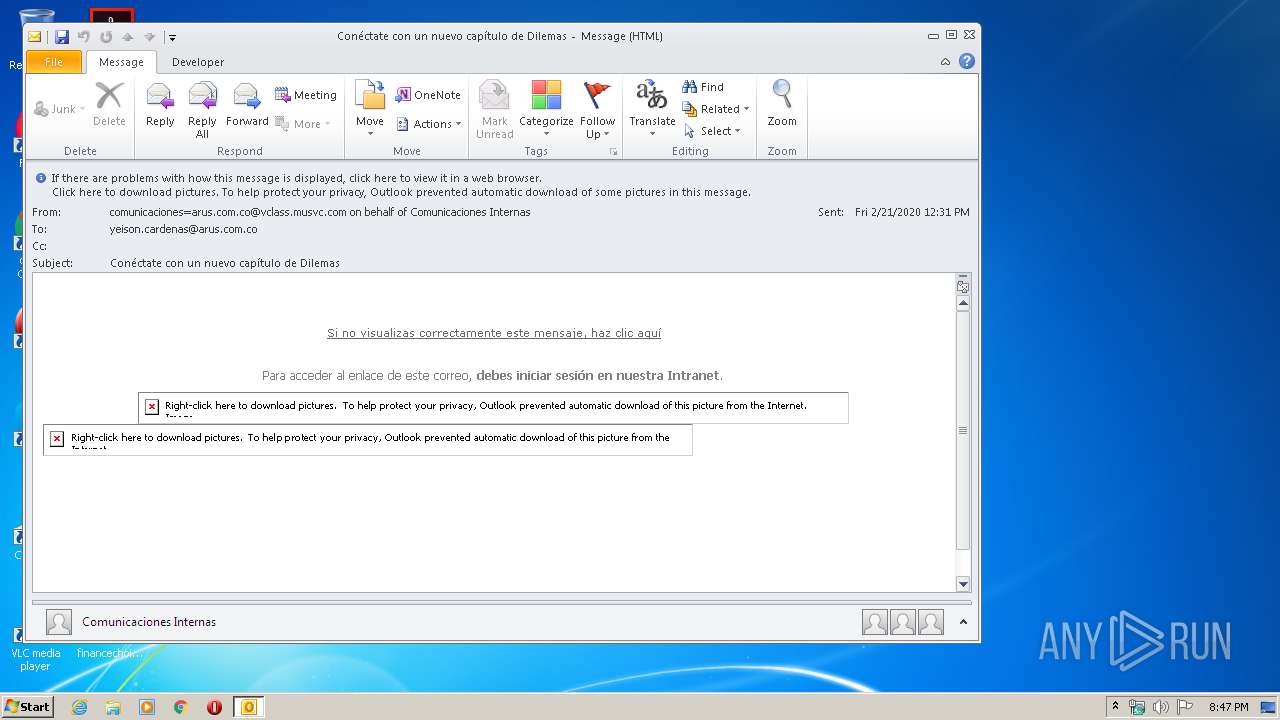
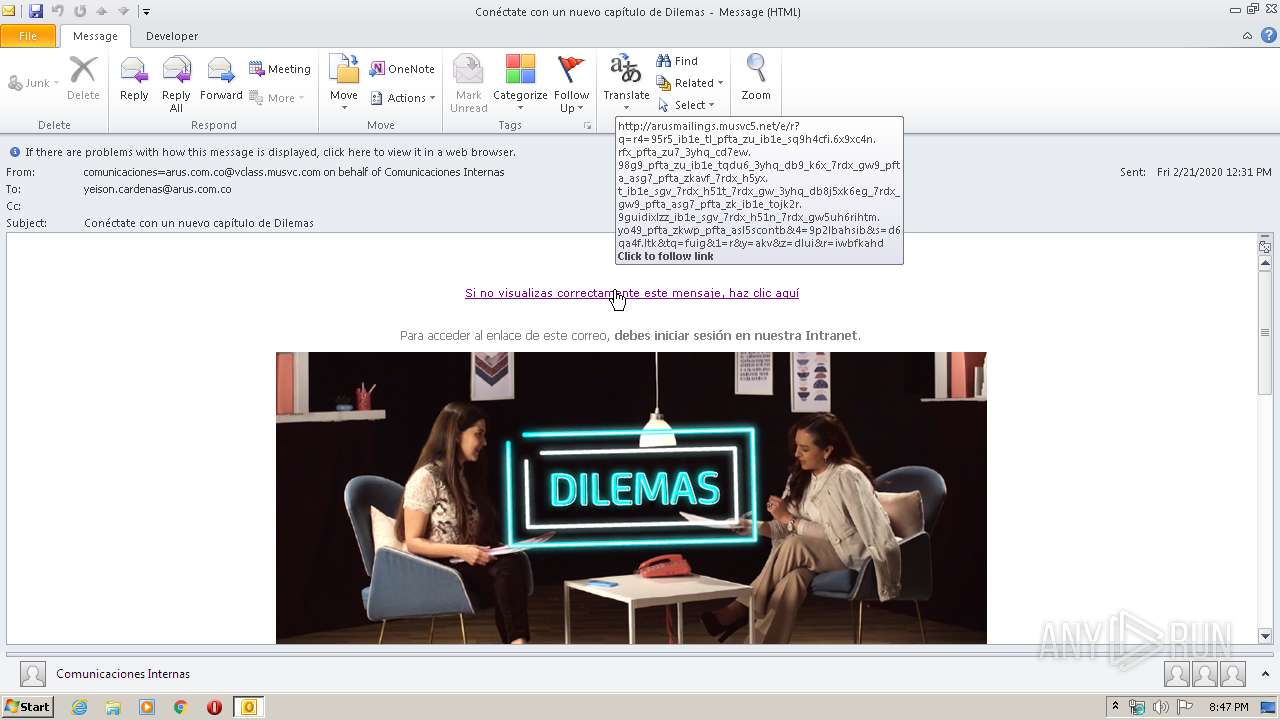
| 576 | "C:\Program Files\Internet Explorer\iexplore.exe" http://arusmailings.musvc5.net/e/r?q=R4%3d95R5_Ib1e_Tl_Pfta_Zu_Ib1e_Sq9H4CFI.6x9xC4N.rFx_Pfta_Zu7_3yhq_CD7Ew.98G9_Pfta_Zu_Ib1e_TqDu6_3yhq_DB9_K6X_7rdx_GW9_Pfta_asG7_Pfta_ZKavF_7rdx_H5yX.t_Ib1e_SGV_7rdx_H51T_7rdx_GW_3yhq_DB8J5XK6Eg_7rdx_GW9_Pfta_asG7_Pfta_ZK_Ib1e_ToJK2r.9GUIDIXlZz_Ib1e_SGV_7rdx_H51N_7rdx_GW5UH6rIHTm.YO49_Pfta_ZKWp_Pfta_asL5SCoNtb%264%3d9p2lBaHSIb%26s%3dD6QA4F.LtK%26tQ%3dFUIg%261%3dR%26y%3daKV%26z%3ddLUI%26R%3dIWBfKaHd | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
6 660
Read events
1 515
Write events
3 614
Delete events
1 531
Modification events
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (304) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
23
Text files
36
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A99.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ECARD%204[1].png | image | |
MD5:— | SHA256:— | |||
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\FIRMA%20CORREO%20COMUNICACIONES-05[1].png | image | |
MD5:— | SHA256:— | |||
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF84.tmp | — | |
MD5:— | SHA256:— | |||
| 536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF85.tmp | — | |
MD5:— | SHA256:— | |||
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 304 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_8EE0D0266547464397B6103E7FCCE562.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
24
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
304 | OUTLOOK.EXE | GET | 200 | 13.35.254.170:80 | http://arusmailings.img.musvc5.net/static/133284/assets/1/Firmas-Footers/FIRMA%20CORREO%20COMUNICACIONES-05.png | US | image | 32.7 Kb | malicious |
536 | iexplore.exe | GET | 200 | 143.204.208.90:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
536 | iexplore.exe | GET | 200 | 143.204.208.127:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
536 | iexplore.exe | GET | 200 | 143.204.208.192:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
536 | iexplore.exe | GET | 301 | 13.35.253.115:80 | http://a3c2h4.emailsp.com/f/rnl.aspx/?ffe=t_tuz&x=pv&0kh=nz.e&x=pv&=sstz6e49&x=pv&=l6ag.a248f47a2k&x=pp&tw3egk33b.10cx&6e=utuxNCLM | US | html | 183 b | suspicious |
576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
536 | iexplore.exe | GET | 200 | 34.250.108.164:80 | http://arusmailings.musvc5.net/e/c?q=6%3d1ULU8V%265%3dT%26n%3dUOX%26o%3dXPW8%260%3dO4a3t76WNW17-N9dV-MU9Z-t4eU-Qbbat83ZLW0Z%262L%3d1VQb%26d%3dEDLv5N.GeL%26C%3dW1VPW7VKZ | IE | image | 158 b | suspicious |
576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
304 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
304 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
304 | OUTLOOK.EXE | 34.250.108.164:80 | arusmailings.musvc5.net | Amazon.com, Inc. | IE | suspicious |
304 | OUTLOOK.EXE | 13.35.254.170:80 | arusmailings.img.musvc5.net | — | US | suspicious |
536 | iexplore.exe | 34.250.108.164:80 | arusmailings.musvc5.net | Amazon.com, Inc. | IE | suspicious |
536 | iexplore.exe | 143.204.208.127:80 | o.ss2.us | — | US | malicious |
536 | iexplore.exe | 13.35.253.115:80 | a3c2h4.emailsp.com | — | US | suspicious |
536 | iexplore.exe | 13.35.253.115:443 | a3c2h4.emailsp.com | — | US | suspicious |
576 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
576 | iexplore.exe | 13.35.253.115:443 | a3c2h4.emailsp.com | — | US | suspicious |
576 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
arusmailings.musvc5.net |
| suspicious |
arusmailings.img.musvc5.net |
| malicious |
a3c2h4.emailsp.com |
| suspicious |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |