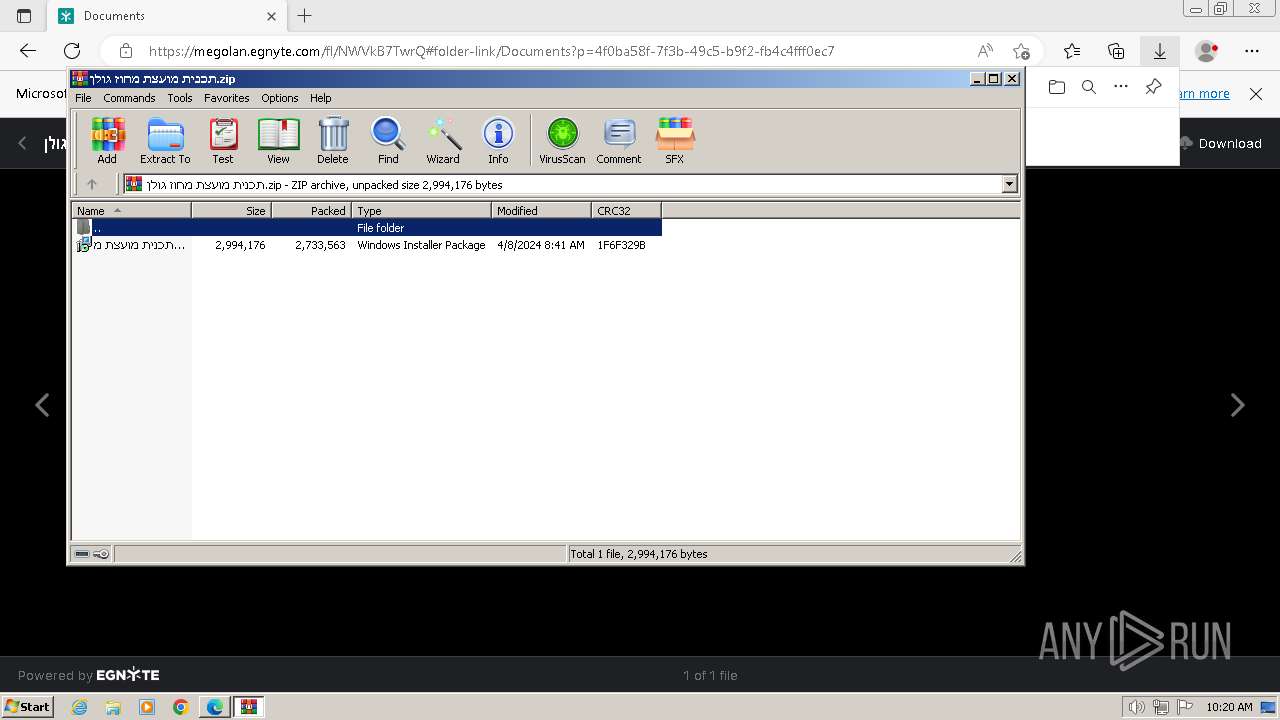
| URL: | https://megolan.egnyte.com/fl/NWVkB7TwrQ |
| Full analysis: | https://app.any.run/tasks/13826403-2372-44f0-87fc-b26d8c1f7005 |
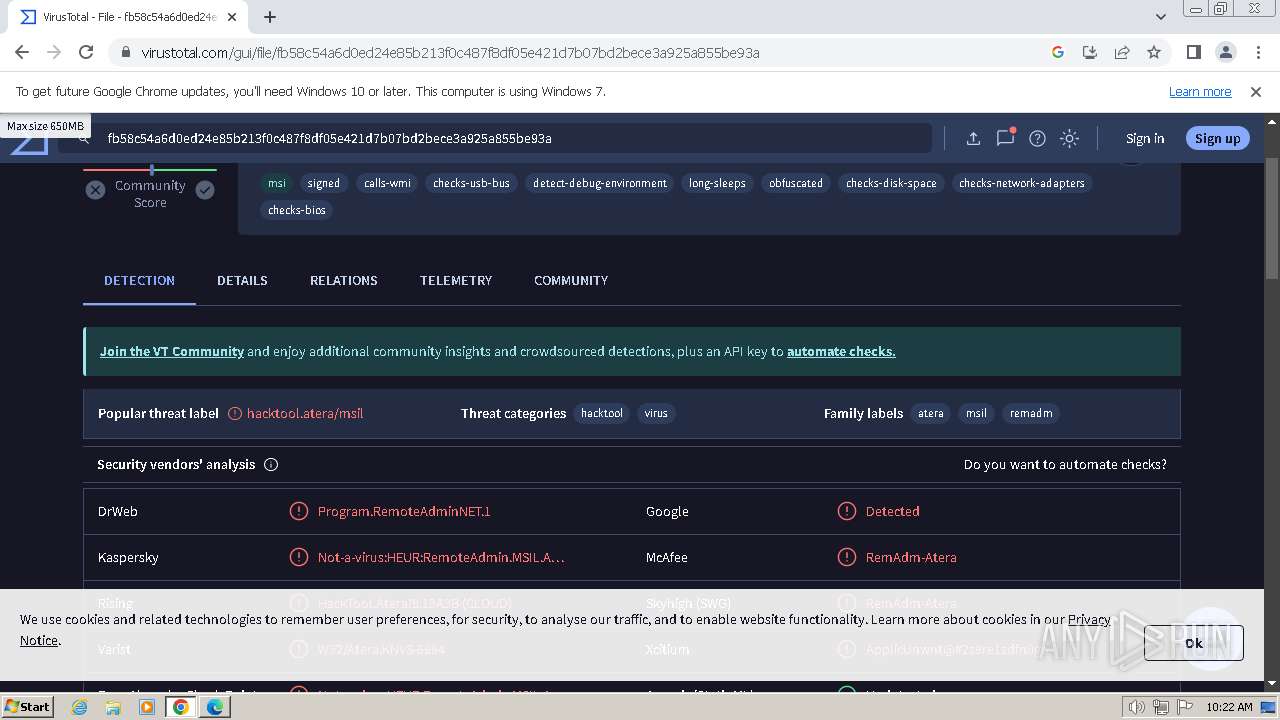
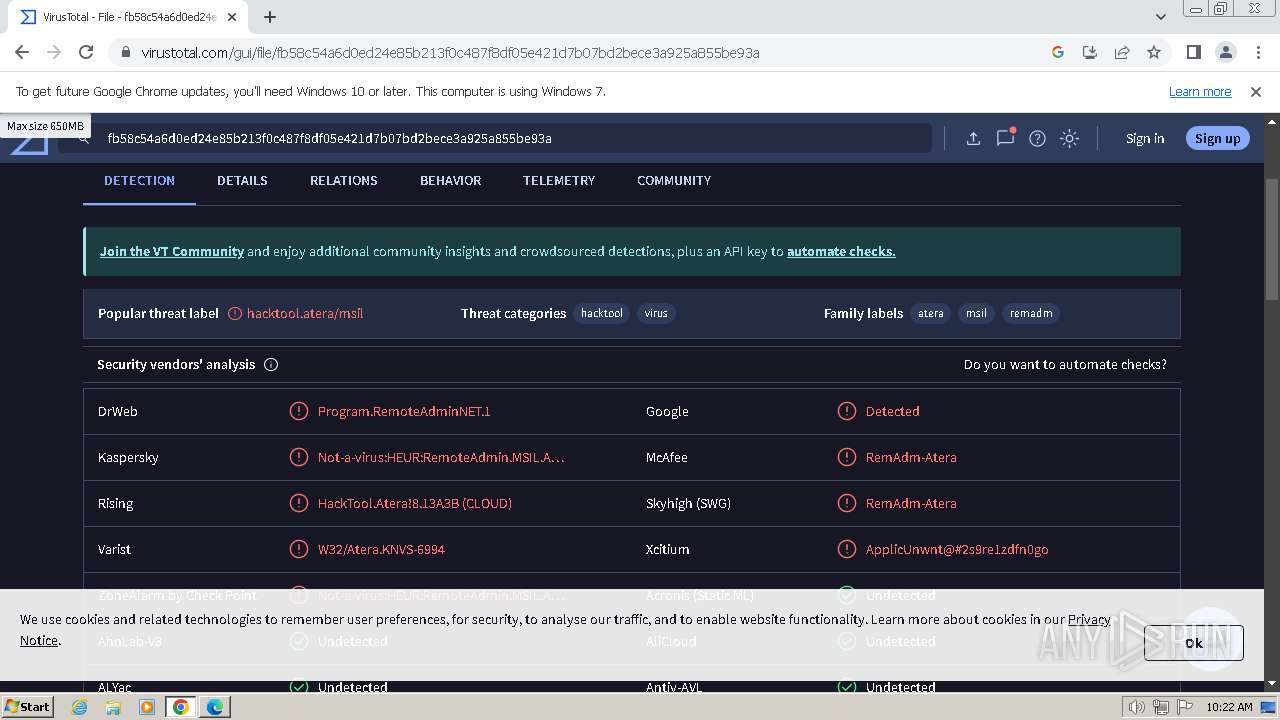
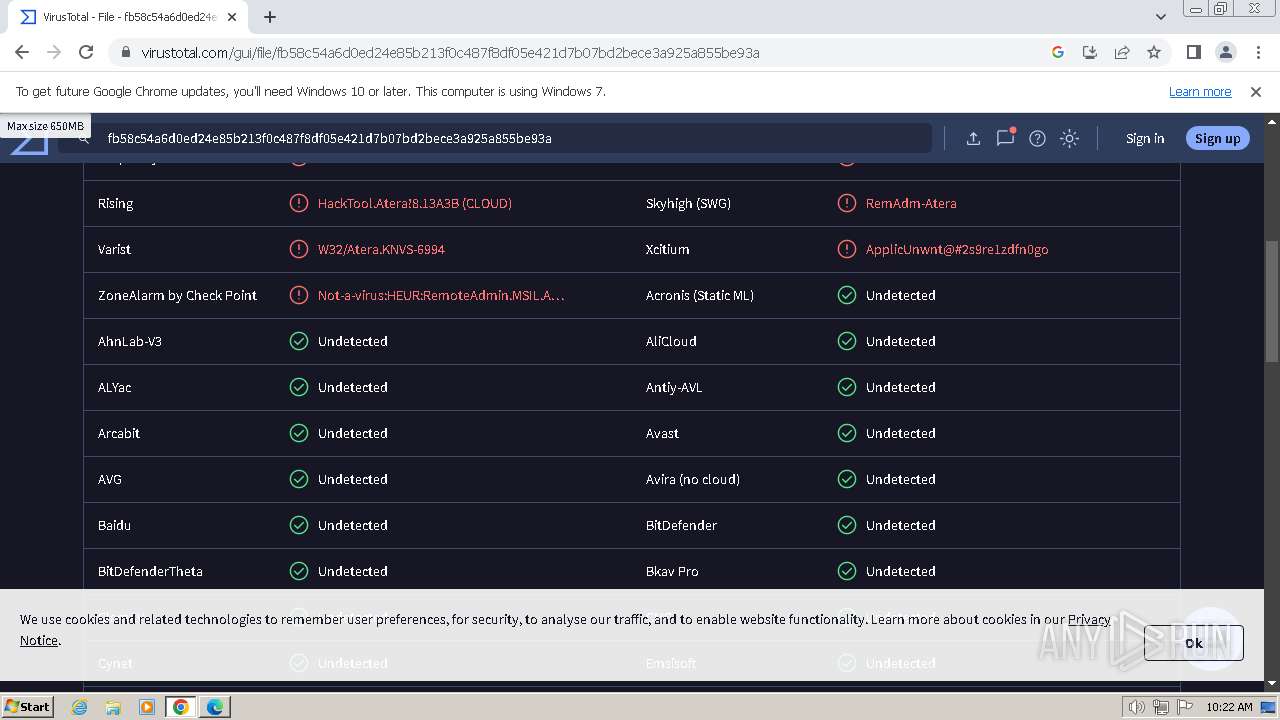
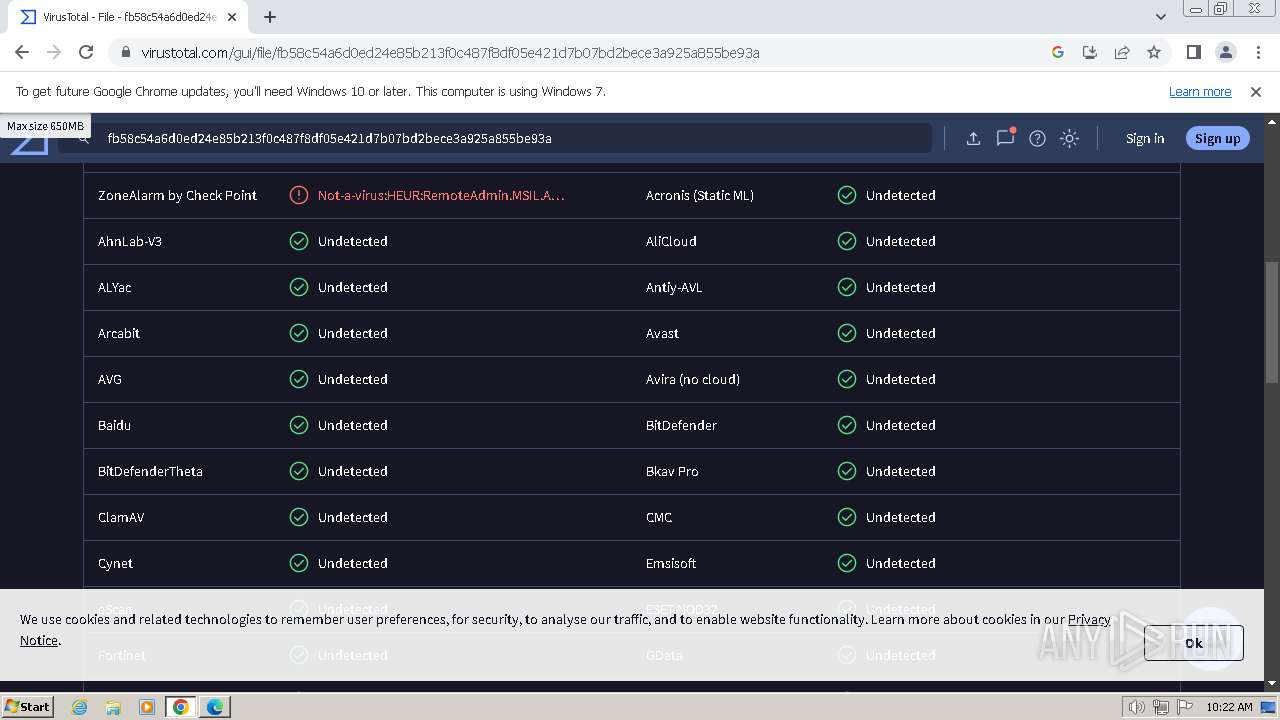
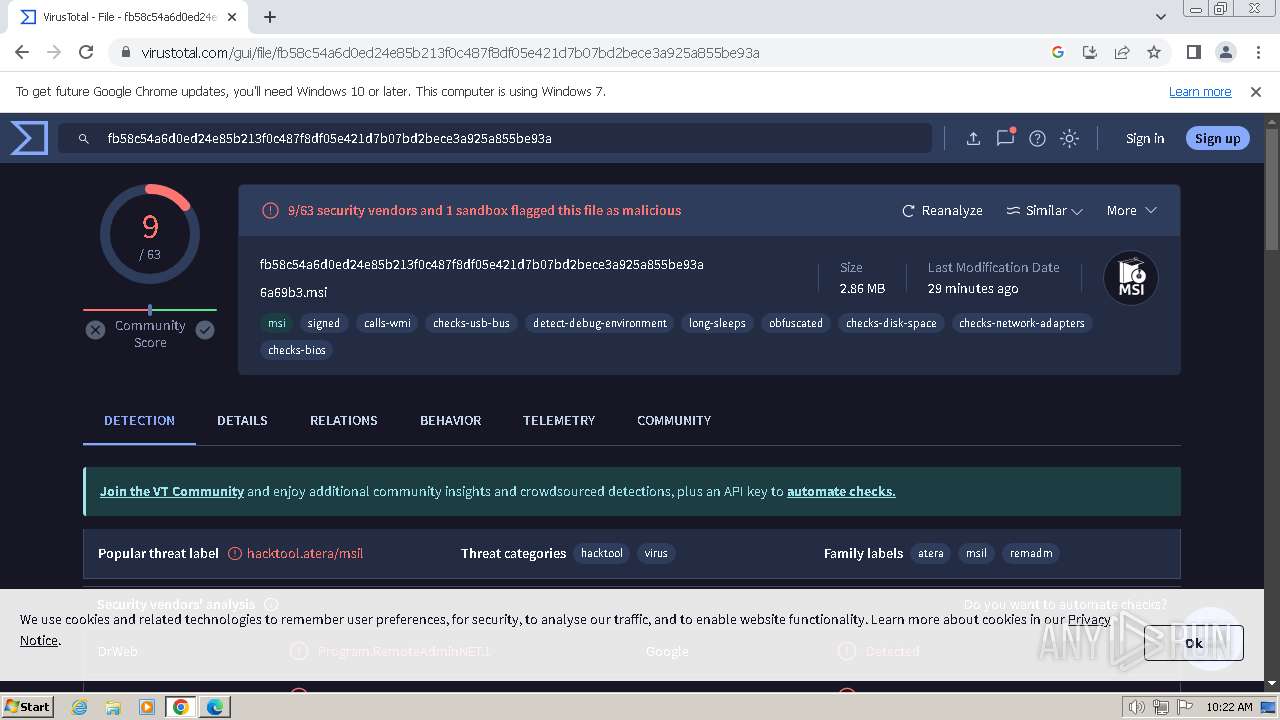
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2024, 09:19:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 97BFD38627E757B86631418DD217281C |
| SHA1: | 8E6A903A7E079496878CEE12F0D6B8B87BE1B97B |
| SHA256: | BDC91A873FBD94C3B46419867EEC42B596BB27262B203F94AA23DF7F67D840BB |
| SSDEEP: | 3:N8ZJEL0kz1Oy:23EL05y |
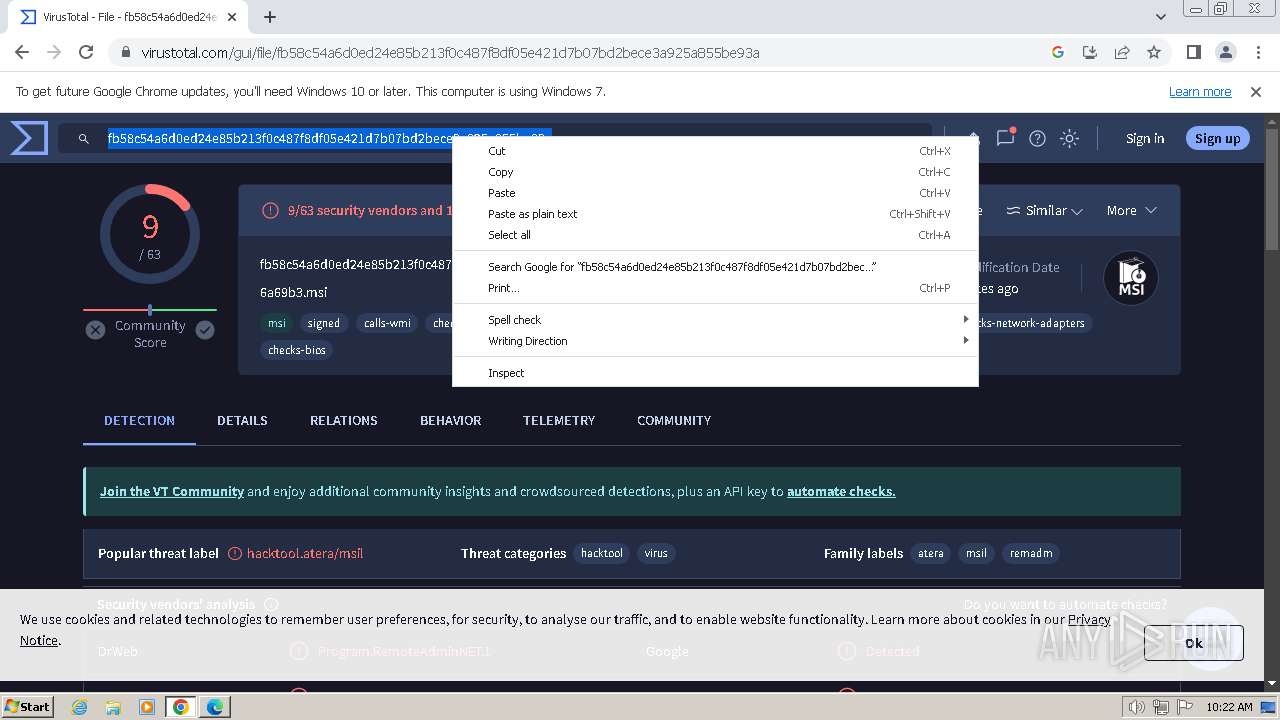
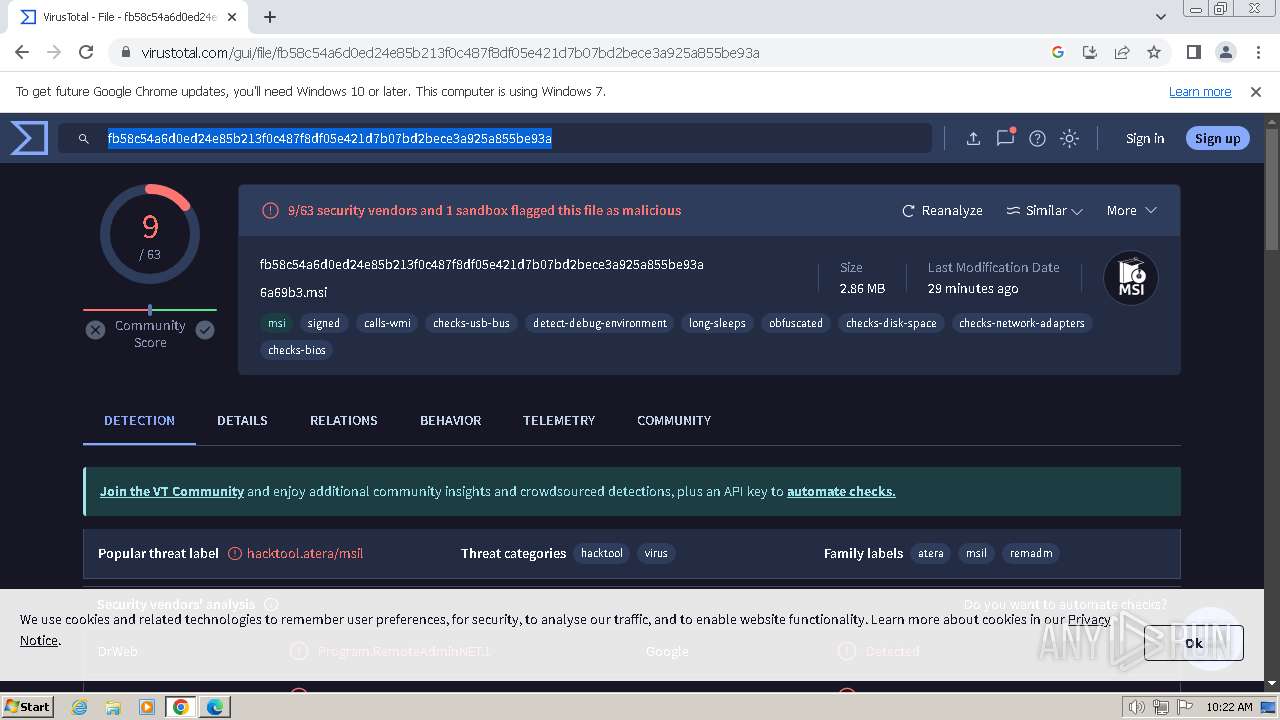
MALICIOUS
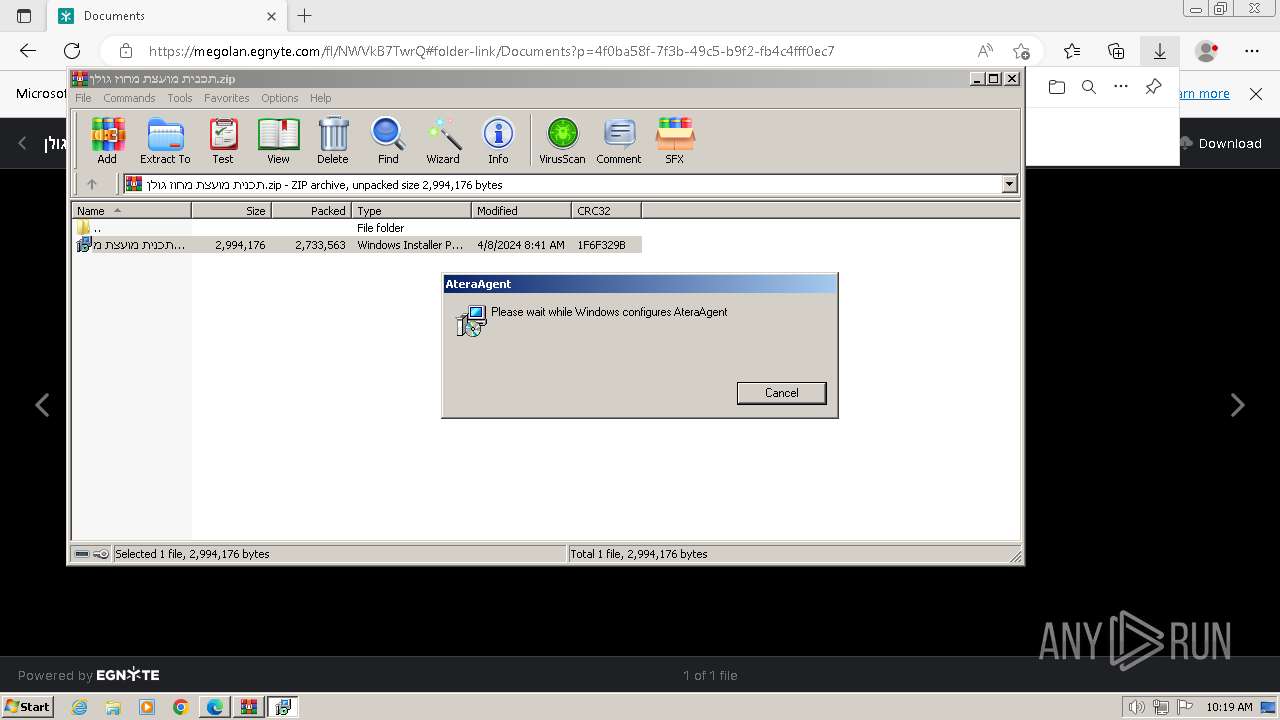
Drops the executable file immediately after the start
- AteraAgent.exe (PID: 324)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AteraAgent.exe (PID: 3788)
- AgentPackageTicketing.exe (PID: 1900)
- PreVerCheck.exe (PID: 5908)
- SplashtopStreamer.exe (PID: 5748)
- uninst.exe (PID: 5336)
- Au_.exe (PID: 5768)
Creates a writable file in the system directory
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3788)
- SRManager.exe (PID: 5316)
- SRServer.exe (PID: 5556)
- powershell.exe (PID: 4704)
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1380)
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3112)
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageAgentInformation.exe (PID: 1876)
- AteraAgent.exe (PID: 3788)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- SplashtopStreamer.exe (PID: 5748)
- SRServer.exe (PID: 5556)
- AgentPackageAgentInformation.exe (PID: 4360)
Executes as Windows Service
- VSSVC.exe (PID: 3744)
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3112)
- AteraAgent.exe (PID: 3788)
- SSUService.exe (PID: 5116)
- SRService.exe (PID: 5280)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3112)
- AteraAgent.exe (PID: 3788)
- cmd.exe (PID: 5584)
- cmd.exe (PID: 5696)
Executable content was dropped or overwritten
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3788)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AgentPackageTicketing.exe (PID: 1900)
- PreVerCheck.exe (PID: 5908)
- SplashtopStreamer.exe (PID: 5748)
- Au_.exe (PID: 5768)
- uninst.exe (PID: 5336)
The process executes VB scripts
- cmd.exe (PID: 3548)
- cmd.exe (PID: 292)
- cmd.exe (PID: 1392)
- cmd.exe (PID: 1496)
- cmd.exe (PID: 2924)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 2544)
- cmd.exe (PID: 3872)
- cmd.exe (PID: 552)
- cmd.exe (PID: 6000)
- cmd.exe (PID: 4668)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- SRServer.exe (PID: 5556)
- AgentPackageAgentInformation.exe (PID: 4360)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 3756)
Process drops legitimate windows executable
- AteraAgent.exe (PID: 324)
- AteraAgent.exe (PID: 3788)
- AgentPackageUpgradeAgent.exe (PID: 2924)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageAgentInformation.exe (PID: 4360)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3756)
- cscript.exe (PID: 3692)
- cscript.exe (PID: 3264)
- cscript.exe (PID: 1504)
- cscript.exe (PID: 3428)
- cscript.exe (PID: 3468)
- cscript.exe (PID: 4084)
- cscript.exe (PID: 2744)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 1544)
- cscript.exe (PID: 2924)
The process creates files with name similar to system file names
- AteraAgent.exe (PID: 3788)
- Au_.exe (PID: 5768)
Starts itself from another location
- AgentPackageUpgradeAgent.exe (PID: 2924)
- uninst.exe (PID: 5336)
Starts POWERSHELL.EXE for commands execution
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 3600)
- powershell.exe (PID: 4704)
Creates or modifies Windows services
- SRManager.exe (PID: 5316)
Checks Windows Trust Settings
- SRManager.exe (PID: 5316)
Process uses ARP to discover network configuration
- powershell.exe (PID: 4704)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1380)
- msedge.exe (PID: 2984)
- WinRAR.exe (PID: 2104)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2028)
- msiexec.exe (PID: 3720)
Application launched itself
- msedge.exe (PID: 3936)
- chrome.exe (PID: 3620)
Reads the software policy settings
- msiexec.exe (PID: 3720)
- msiexec.exe (PID: 2028)
- AteraAgent.exe (PID: 324)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2652)
- AteraAgent.exe (PID: 3112)
- AgentPackageMonitoring.exe (PID: 2848)
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageAgentInformation.exe (PID: 1592)
- AgentPackageAgentInformation.exe (PID: 2128)
- AgentPackageAgentInformation.exe (PID: 1876)
- AteraAgent.exe (PID: 3788)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageMarketplace.exe (PID: 2900)
- AgentPackageHeartbeat.exe (PID: 3152)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageTicketing.exe (PID: 1900)
- AgentPackageHeartbeat.exe (PID: 4660)
- AgentPackageFileExplorer.exe (PID: 4856)
- AgentPackageFileExplorer.exe (PID: 5236)
- AgentPackageFileExplorer.exe (PID: 5096)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- AgentPackageFileExplorer.exe (PID: 5632)
- AgentPackageFileExplorer.exe (PID: 5504)
- AgentPackageHeartbeat.exe (PID: 5792)
- AgentPackageFileExplorer.exe (PID: 5824)
- SRManager.exe (PID: 5316)
- AgentPackageFileExplorer.exe (PID: 752)
- AgentPackageAgentInformation.exe (PID: 4360)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
- AgentPackageHeartbeat.exe (PID: 5096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1380)
- WinRAR.exe (PID: 2104)
Reads the computer name
- AteraAgent.exe (PID: 324)
- AgentPackageAgentInformation.exe (PID: 1592)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2652)
- AgentPackageAgentInformation.exe (PID: 1796)
- AgentPackageAgentInformation.exe (PID: 1344)
- AteraAgent.exe (PID: 3112)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageMonitoring.exe (PID: 2848)
- AgentPackageAgentInformation.exe (PID: 2128)
- AteraAgent.exe (PID: 3788)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageADRemote.exe (PID: 2424)
- AgentPackageMarketplace.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageHeartbeat.exe (PID: 3152)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageSystemTools.exe (PID: 3096)
- AgentPackageOsUpdates.exe (PID: 2784)
- AgentPackageRuntimeInstaller.exe (PID: 2108)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageUpgradeAgent.exe (PID: 572)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageTicketing.exe (PID: 1900)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- AgentPackageFileExplorer.exe (PID: 4856)
- AgentPackageHeartbeat.exe (PID: 4660)
- AgentPackageFileExplorer.exe (PID: 5504)
- AgentPackageFileExplorer.exe (PID: 5096)
- AgentPackageFileExplorer.exe (PID: 5236)
- AgentPackageHeartbeat.exe (PID: 5792)
- AgentPackageFileExplorer.exe (PID: 752)
- AgentPackageFileExplorer.exe (PID: 5632)
- SplashtopStreamer.exe (PID: 5748)
- AgentPackageFileExplorer.exe (PID: 5824)
- SRManager.exe (PID: 5316)
- SRServer.exe (PID: 5556)
- SSUService.exe (PID: 5116)
- SRService.exe (PID: 5280)
- SRFeature.exe (PID: 5344)
- SRAgent.exe (PID: 5604)
- SRAppPB.exe (PID: 5504)
- Au_.exe (PID: 5768)
- uninst.exe (PID: 5336)
- AgentPackageAgentInformation.exe (PID: 4360)
- AgentPackageSTRemote.exe (PID: 4184)
- AgentPackageMonitoring.exe (PID: 5480)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
- AgentPackageHeartbeat.exe (PID: 5096)
- AgentPackageHeartbeat.exe (PID: 1600)
- AgentPackageSTRemote.exe (PID: 6028)
- AgentPackageInternalPoller.exe (PID: 4920)
Reads the machine GUID from the registry
- AteraAgent.exe (PID: 324)
- AgentPackageAgentInformation.exe (PID: 1592)
- AgentPackageAgentInformation.exe (PID: 2652)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 1796)
- AgentPackageAgentInformation.exe (PID: 1344)
- AteraAgent.exe (PID: 3112)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageMonitoring.exe (PID: 2848)
- AgentPackageAgentInformation.exe (PID: 2128)
- AgentPackageAgentInformation.exe (PID: 2332)
- AteraAgent.exe (PID: 3788)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageMarketplace.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageHeartbeat.exe (PID: 3152)
- AgentPackageADRemote.exe (PID: 2424)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageOsUpdates.exe (PID: 2784)
- AgentPackageRuntimeInstaller.exe (PID: 2108)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageSystemTools.exe (PID: 3096)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AgentPackageUpgradeAgent.exe (PID: 572)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageTicketing.exe (PID: 1900)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- AgentPackageHeartbeat.exe (PID: 4660)
- AgentPackageFileExplorer.exe (PID: 4856)
- AgentPackageFileExplorer.exe (PID: 5096)
- AgentPackageFileExplorer.exe (PID: 5236)
- AgentPackageFileExplorer.exe (PID: 5504)
- AgentPackageFileExplorer.exe (PID: 5632)
- AgentPackageHeartbeat.exe (PID: 5792)
- AgentPackageFileExplorer.exe (PID: 752)
- AgentPackageFileExplorer.exe (PID: 5824)
- SRManager.exe (PID: 5316)
- SRAgent.exe (PID: 5604)
- SSUService.exe (PID: 5116)
- AgentPackageSTRemote.exe (PID: 4184)
- AgentPackageMonitoring.exe (PID: 5480)
- AgentPackageAgentInformation.exe (PID: 4360)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
- AgentPackageHeartbeat.exe (PID: 5096)
- AgentPackageInternalPoller.exe (PID: 4920)
- AgentPackageHeartbeat.exe (PID: 1600)
- AgentPackageSTRemote.exe (PID: 6028)
Creates files in the program directory
- AteraAgent.exe (PID: 324)
- AgentPackageMonitoring.exe (PID: 2848)
- AteraAgent.exe (PID: 3788)
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageOsUpdates.exe (PID: 2784)
- AgentPackageRuntimeInstaller.exe (PID: 2108)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageTicketing.exe (PID: 1900)
- SRManager.exe (PID: 5316)
- SRServer.exe (PID: 5556)
- SRAgent.exe (PID: 5604)
- AgentPackageMonitoring.exe (PID: 5480)
- SRVirtualDisplay.exe (PID: 3612)
Checks supported languages
- AteraAgent.exe (PID: 324)
- AgentPackageAgentInformation.exe (PID: 1592)
- AgentPackageAgentInformation.exe (PID: 2128)
- AgentPackageAgentInformation.exe (PID: 2652)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 1796)
- AgentPackageAgentInformation.exe (PID: 1344)
- AteraAgent.exe (PID: 3112)
- AgentPackageMonitoring.exe (PID: 2848)
- AgentPackageAgentInformation.exe (PID: 1876)
- AteraAgent.exe (PID: 3788)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageMarketplace.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageHeartbeat.exe (PID: 3152)
- AgentPackageADRemote.exe (PID: 2424)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageSystemTools.exe (PID: 3096)
- AgentPackageOsUpdates.exe (PID: 2784)
- AgentPackageRuntimeInstaller.exe (PID: 2108)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageUpgradeAgent.exe (PID: 572)
- AgentPackageTicketing.exe (PID: 1900)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- AgentPackageHeartbeat.exe (PID: 4660)
- AgentPackageFileExplorer.exe (PID: 4856)
- AgentPackageFileExplorer.exe (PID: 5096)
- AgentPackageFileExplorer.exe (PID: 5236)
- AgentPackageFileExplorer.exe (PID: 5504)
- AgentPackageHeartbeat.exe (PID: 5792)
- SplashtopStreamer.exe (PID: 5748)
- AgentPackageFileExplorer.exe (PID: 5824)
- AgentPackageFileExplorer.exe (PID: 5632)
- AgentPackageFileExplorer.exe (PID: 752)
- PreVerCheck.exe (PID: 5908)
- SSUService.exe (PID: 5116)
- SRServer.exe (PID: 5556)
- SRManager.exe (PID: 5316)
- SRService.exe (PID: 5280)
- SRFeature.exe (PID: 5344)
- SRAgent.exe (PID: 5604)
- SRAppPB.exe (PID: 5504)
- Au_.exe (PID: 5768)
- SRUtility.exe (PID: 5500)
- SRUtility.exe (PID: 5936)
- SRDetect.exe (PID: 5400)
- uninst.exe (PID: 5336)
- AgentPackageAgentInformation.exe (PID: 4360)
- AgentPackageSTRemote.exe (PID: 4184)
- BdEpSDK_x86.exe (PID: 6012)
- AgentPackageMonitoring.exe (PID: 5480)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
- AgentPackageHeartbeat.exe (PID: 5096)
- AgentPackageInternalPoller.exe (PID: 4920)
- SRVirtualDisplay.exe (PID: 3612)
- AgentPackageSTRemote.exe (PID: 6028)
- AgentPackageHeartbeat.exe (PID: 1600)
Reads Environment values
- AteraAgent.exe (PID: 324)
- AgentPackageAgentInformation.exe (PID: 1592)
- AgentPackageAgentInformation.exe (PID: 2508)
- AgentPackageAgentInformation.exe (PID: 2128)
- AgentPackageAgentInformation.exe (PID: 1796)
- AteraAgent.exe (PID: 3112)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageMonitoring.exe (PID: 2848)
- AgentPackageAgentInformation.exe (PID: 2652)
- AgentPackageAgentInformation.exe (PID: 1344)
- AteraAgent.exe (PID: 3788)
- AgentPackageMonitoring.exe (PID: 3136)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageADRemote.exe (PID: 2424)
- AgentPackageMarketplace.exe (PID: 2900)
- AgentPackageInternalPoller.exe (PID: 3556)
- AgentPackageHeartbeat.exe (PID: 3152)
- AgentPackageProgramManagement.exe (PID: 864)
- AgentPackageSTRemote.exe (PID: 2864)
- AgentPackageOsUpdates.exe (PID: 2784)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageSystemTools.exe (PID: 3096)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageUpgradeAgent.exe (PID: 2924)
- AgentPackageUpgradeAgent.exe (PID: 572)
- AgentPackageTicketing.exe (PID: 1900)
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageRunCommandInteractive.exe (PID: 3792)
- AgentPackageHeartbeat.exe (PID: 4660)
- AgentPackageFileExplorer.exe (PID: 4856)
- AgentPackageFileExplorer.exe (PID: 5236)
- AgentPackageHeartbeat.exe (PID: 5792)
- AgentPackageFileExplorer.exe (PID: 5504)
- AgentPackageFileExplorer.exe (PID: 5096)
- AgentPackageFileExplorer.exe (PID: 5824)
- AgentPackageFileExplorer.exe (PID: 5632)
- AgentPackageFileExplorer.exe (PID: 752)
- SRManager.exe (PID: 5316)
- AgentPackageSTRemote.exe (PID: 4184)
- AgentPackageAgentInformation.exe (PID: 4360)
- AgentPackageMonitoring.exe (PID: 5480)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
- AgentPackageHeartbeat.exe (PID: 5096)
- AgentPackageHeartbeat.exe (PID: 1600)
- AgentPackageInternalPoller.exe (PID: 4920)
- AgentPackageSTRemote.exe (PID: 6028)
Reads Microsoft Office registry keys
- AgentPackageAgentInformation.exe (PID: 1344)
- AgentPackageAgentInformation.exe (PID: 1876)
- AgentPackageAgentInformation.exe (PID: 2332)
- AgentPackageAgentInformation.exe (PID: 3288)
- AgentPackageAgentInformation.exe (PID: 3464)
- AgentPackageAgentInformation.exe (PID: 4360)
Manual execution by a user
- msiexec.exe (PID: 1776)
- cmd.exe (PID: 3336)
- chrome.exe (PID: 3620)
Process checks Powershell version
- AgentPackageRunCommandInteractive.exe (PID: 1876)
- AgentPackageRunCommandInteractive.exe (PID: 4876)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3768)
- powershell.exe (PID: 4704)
Reads product name
- SRManager.exe (PID: 5316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
322
Monitored processes
151
Malicious processes
34
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3768 --field-trial-handle=1380,i,2427762336754093174,6602679930591166248,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 292 | "C:\Windows\System32\cmd.exe" /c cscript "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /dstatus | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | "C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 1 Version: 1.8.7.2 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3864 --field-trial-handle=1380,i,2427762336754093174,6602679930591166248,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\cmd.exe" /c cscript "C:\Program Files\Microsoft Office\Office14\ospp.vbs" /dstatus | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | "C:\Windows\System32\sc.exe" failure AteraAgent reset= 600 actions= restart/25000 | C:\Windows\System32\sc.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | "C:\Windows\TEMP\AteraUpgradeAgentPackage\AgentPackageUpgradeAgent.exe" "f5cdde6c-e59f-4445-8cf2-1b8a9988fee7" "1037bb60-fdf6-487d-b5d7-f59e8d1d250a" "agent-api.atera.com/Production" "443" "or8ixLi90Mf" "checkforupdates" "001Q300000BeUp3IAF" | C:\Windows\Temp\AteraUpgradeAgentPackage\AgentPackageUpgradeAgent.exe | — | AgentPackageUpgradeAgent.exe | |||||||||||
User: SYSTEM Company: Atera Networks LTD Integrity Level: SYSTEM Description: AgentPackageUpgradeAgent Exit code: 0 Version: 26.8.0.0 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --mojo-platform-channel-handle=3608 --field-trial-handle=1380,i,2427762336754093174,6602679930591166248,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 752 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageFileExplorer\AgentPackageFileExplorer.exe" f5cdde6c-e59f-4445-8cf2-1b8a9988fee7 "b93b15b7-8fcb-4ba8-9ca6-ea2f51c43af8" agent-api.atera.com/Production 443 or8ixLi90Mf "eyJjb21tYW5kIjoiR2V0RGlyZWN0b3J5IiwicGF0aCI6IkNvbXB1dGVyXFxDOlxcVXNlcnNcXGFkbWluXFxEb2N1bWVudHMifQ==" 001Q300000BeUp3IAF | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageFileExplorer\AgentPackageFileExplorer.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageFileExplorer Exit code: 0 Version: 17.0.0.0 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=1292 --field-trial-handle=1380,i,2427762336754093174,6602679930591166248,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
254 493
Read events
252 718
Write events
1 630
Delete events
145
Modification events
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 131EBD9528742F00 | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3936) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
380
Suspicious files
224
Text files
193
Unknown types
108
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:— | SHA256:— | |||
| 1692 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\003ae243-aa52-41ee-8ff9-5a8dc3de4b73.tmp | binary | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF1821fa.TMP | text | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RF182258.TMP | text | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF182267.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
186
DNS requests
125
Threats
104
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3152 | AteraAgent.exe | GET | 304 | 23.53.40.72:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?919d3e0fc4037ea5 | unknown | — | — | unknown |
3152 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
3152 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
3152 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | unknown |
324 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2440 | msedge.exe | 131.253.33.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2440 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2440 | msedge.exe | 162.216.251.231:443 | megolan.egnyte.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3936 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2440 | msedge.exe | 23.212.110.203:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
2440 | msedge.exe | 130.211.34.183:443 | api.mixpanel.com | GOOGLE | US | whitelisted |
2440 | msedge.exe | 35.186.225.159:443 | egnyte-www-static.egnyte.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
megolan.egnyte.com |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.mixpanel.com |
| whitelisted |
egnyte-www-static.egnyte.com |
| unknown |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
agent-api.atera.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2440 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (egnyte .com) |
2440 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (egnyte .com) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (egnyte .com in TLS SNI) |
2440 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (egnyte .com) |
2440 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (egnyte .com) |
59 ETPRO signatures available at the full report
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x86\SQLite.Interop.dll"...
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x86\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUtility::OSInfo] OS 6.1(7601) Service Pack 1 x64:0 (Last=0) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::UnPackFiles] FreeSpace:232933515264 FileSize:51506176 (Last=0) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::FindHeader] Name:C:\Windows\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::FindHeader] Sign Size:10248 (Last=0) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\Windows\TEMP\unpack\setup.msi (51506176) (Last=0) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::UnPackFiles] FreeSpace:232882003968 FileSize:15 (Last=183) |
SplashtopStreamer.exe | [5748]2024-04-08 10:22:37 [CUnPack::UnPackFiles] UnPack count:1 len:51506176 File:(null) (Last=0) |