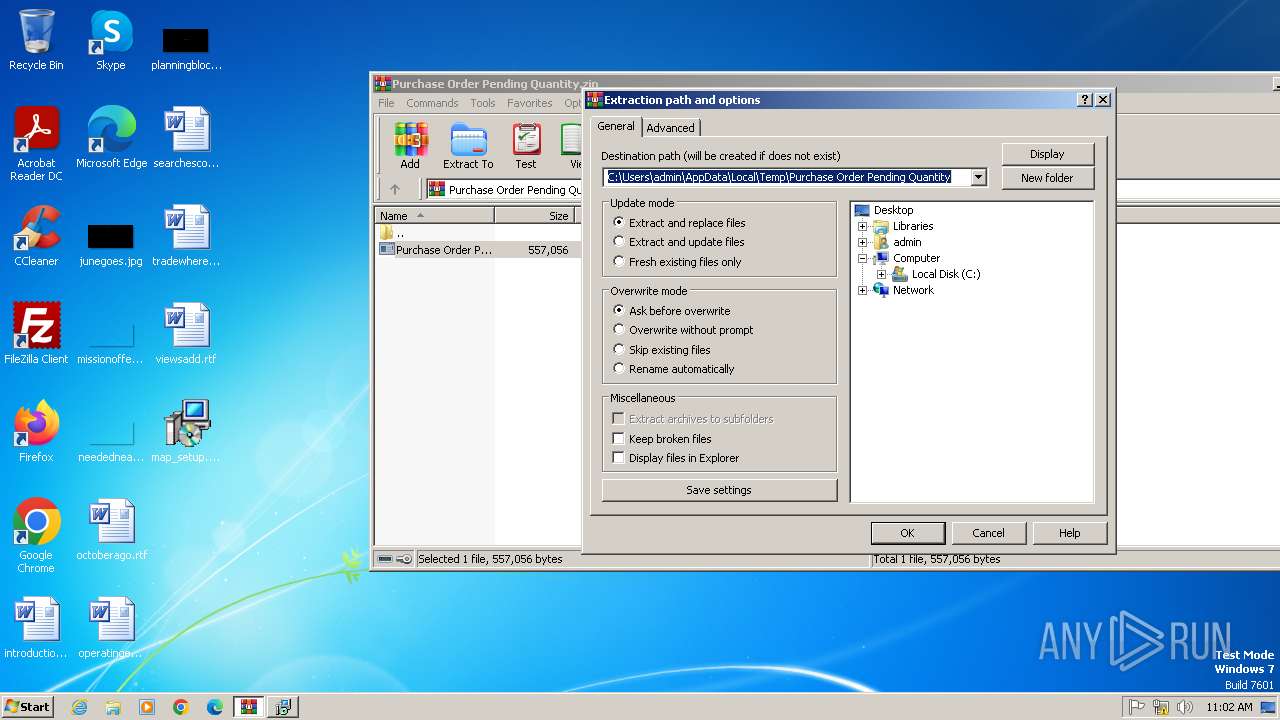
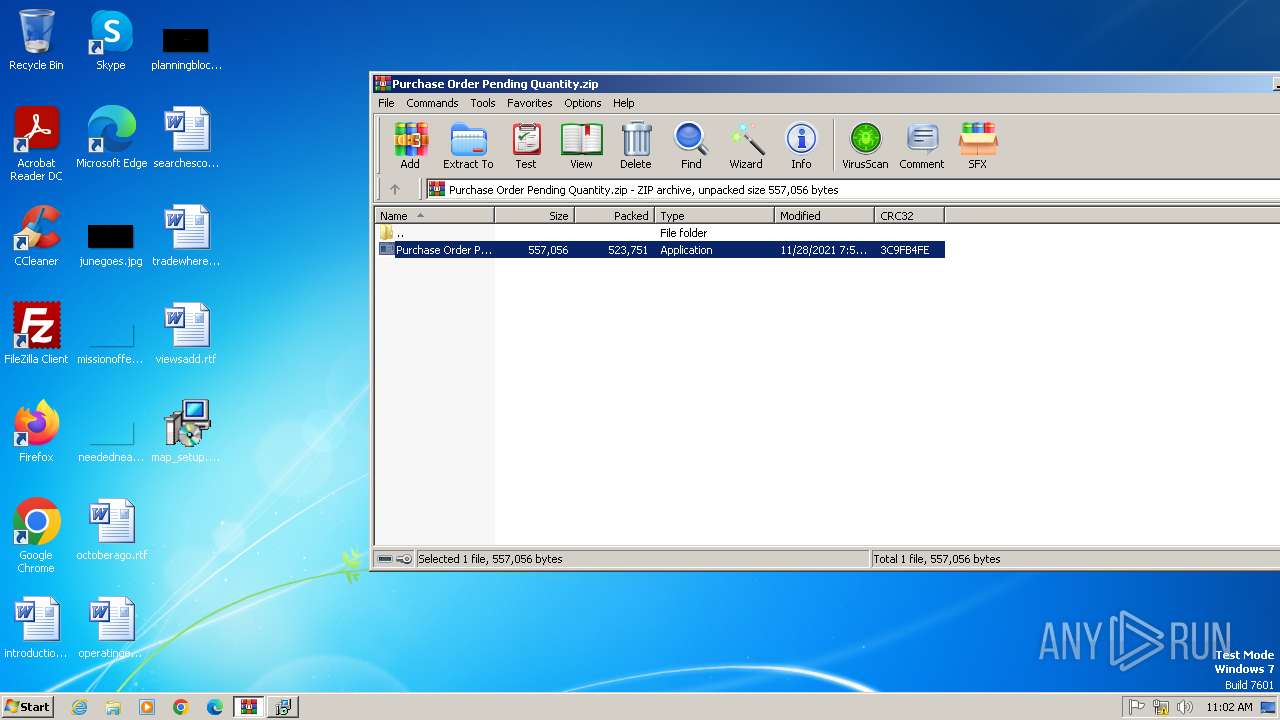
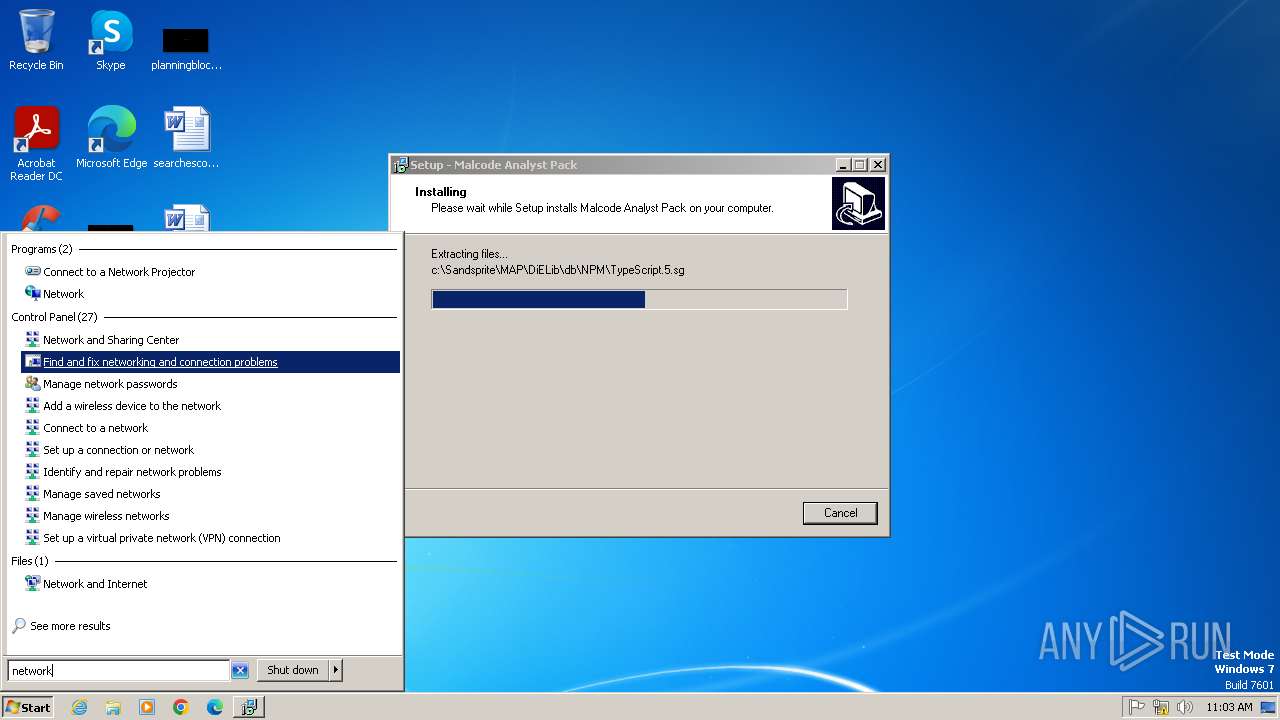
| File name: | Purchase Order Pending Quantity.zip |
| Full analysis: | https://app.any.run/tasks/0cf03bec-949b-4f4b-af69-ad755ac269c3 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 10:01:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AEBB1F67B1DD85D28DC4280C0D79F693 |
| SHA1: | 50C874EEA617A548AACEDE23A5782F175D770358 |
| SHA256: | BDAE21952C4E6367FE534A9E5A3B3EB30D045DCB93129C6CE0435C3F0C8D90D3 |
| SSDEEP: | 24576:49lPOL1fH2jIMGTX+7hfD7GNRjuPlkadnECszgspSxb5PF6mCuZrV:49lPOL1fH2jIMG2hfD7GNNutkadnECsY |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2840)
Registers / Runs the DLL via REGSVR32.EXE
- map_setup.tmp (PID: 2056)
SUSPICIOUS
Executable content was dropped or overwritten
- map_setup.exe (PID: 2368)
- map_setup.exe (PID: 972)
- map_setup.tmp (PID: 2056)
Reads the Windows owner or organization settings
- map_setup.tmp (PID: 2056)
The process drops C-runtime libraries
- map_setup.tmp (PID: 2056)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3304)
- regsvr32.exe (PID: 2852)
- regsvr32.exe (PID: 3668)
- regsvr32.exe (PID: 3200)
- regsvr32.exe (PID: 3248)
Process drops legitimate windows executable
- map_setup.tmp (PID: 2056)
Application launched itself
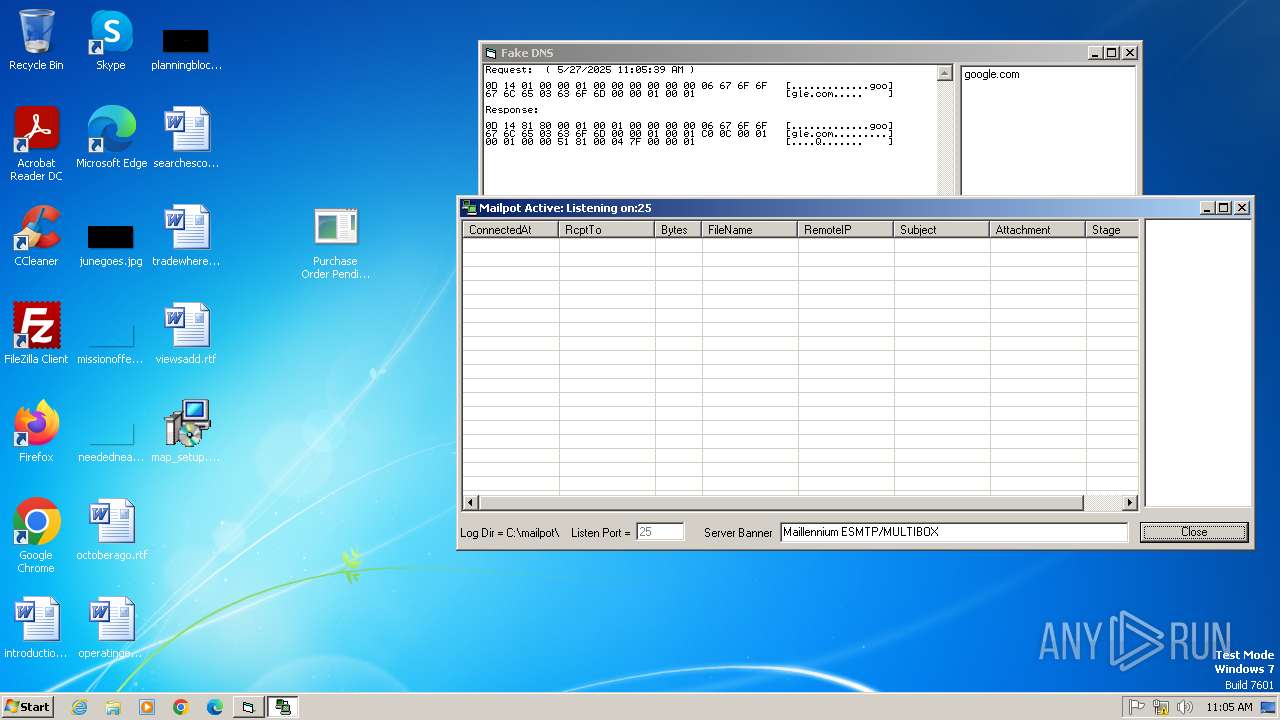
- Purchase Order Pending Quantity.exe (PID: 3536)
INFO
Checks supported languages
- map_setup.exe (PID: 2368)
- map_setup.tmp (PID: 1596)
- map_setup.exe (PID: 972)
- map_setup.tmp (PID: 2056)
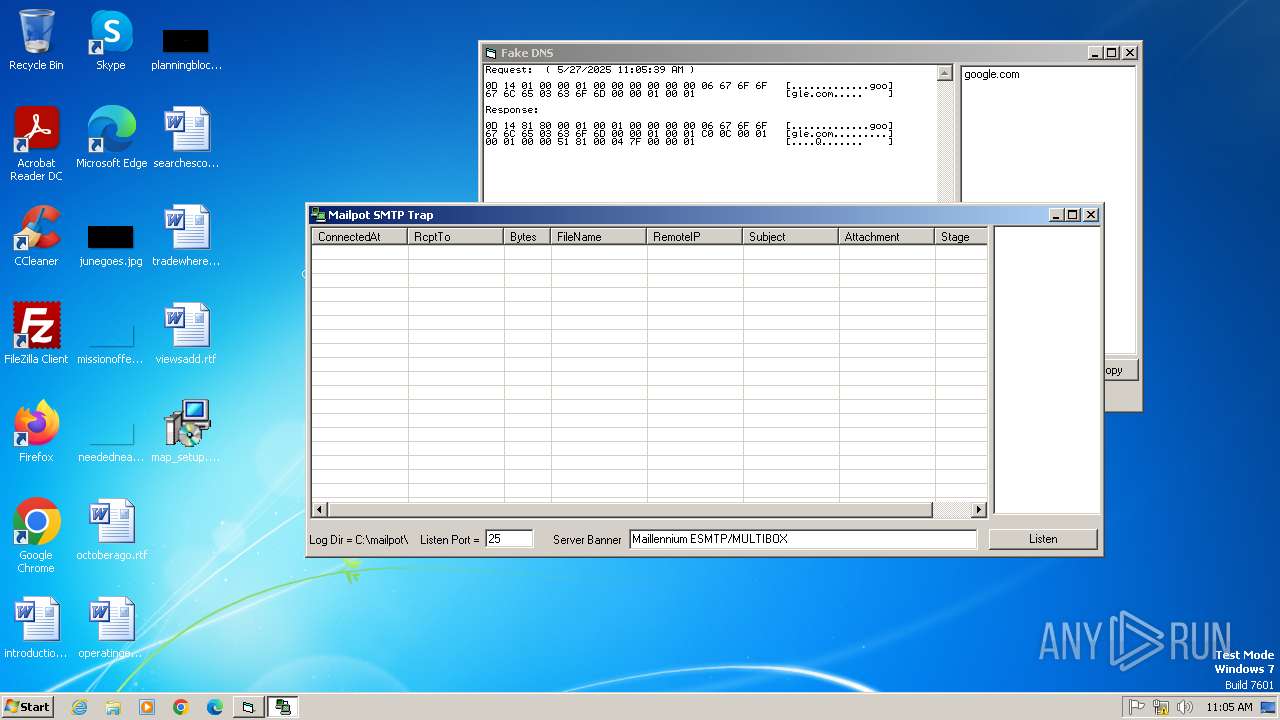
- fakeDNS.exe (PID: 2928)
- mail_pot.exe (PID: 3384)
- ShellExt.exe (PID: 3232)
- Purchase Order Pending Quantity.exe (PID: 1612)
- Purchase Order Pending Quantity.exe (PID: 2584)
- Purchase Order Pending Quantity.exe (PID: 3560)
- Purchase Order Pending Quantity.exe (PID: 3536)
- Purchase Order Pending Quantity.exe (PID: 2276)
- Purchase Order Pending Quantity.exe (PID: 2612)
- Purchase Order Pending Quantity.exe (PID: 2440)
Manual execution by a user
- map_setup.exe (PID: 2368)
- mail_pot.exe (PID: 3384)
- explorer.exe (PID: 3068)
- fakeDNS.exe (PID: 2928)
- cmd.exe (PID: 780)
- Purchase Order Pending Quantity.exe (PID: 2584)
- Purchase Order Pending Quantity.exe (PID: 3560)
- Purchase Order Pending Quantity.exe (PID: 3536)
- Purchase Order Pending Quantity.exe (PID: 1612)
- Purchase Order Pending Quantity.exe (PID: 2440)
- Purchase Order Pending Quantity.exe (PID: 2612)
Create files in a temporary directory
- map_setup.exe (PID: 2368)
- map_setup.exe (PID: 972)
- map_setup.tmp (PID: 2056)
- ShellExt.exe (PID: 3232)
- mail_pot.exe (PID: 3384)
The sample compiled with english language support
- map_setup.exe (PID: 2368)
- map_setup.exe (PID: 972)
- map_setup.tmp (PID: 2056)
Reads the computer name
- map_setup.tmp (PID: 1596)
- map_setup.tmp (PID: 2056)
- fakeDNS.exe (PID: 2928)
- Purchase Order Pending Quantity.exe (PID: 1612)
- Purchase Order Pending Quantity.exe (PID: 2584)
- Purchase Order Pending Quantity.exe (PID: 3560)
- Purchase Order Pending Quantity.exe (PID: 3536)
- Purchase Order Pending Quantity.exe (PID: 2276)
- Purchase Order Pending Quantity.exe (PID: 2612)
- Purchase Order Pending Quantity.exe (PID: 2440)
Detects InnoSetup installer (YARA)
- map_setup.tmp (PID: 1596)
- map_setup.tmp (PID: 2056)
- map_setup.exe (PID: 2368)
- map_setup.exe (PID: 972)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
Compiled with Borland Delphi (YARA)
- map_setup.tmp (PID: 2056)
- map_setup.tmp (PID: 1596)
Creates files in the program directory
- map_setup.tmp (PID: 2056)
Reads mouse settings
- regsvr32.exe (PID: 3668)
- mail_pot.exe (PID: 3384)
Creates a software uninstall entry
- map_setup.tmp (PID: 2056)
Reads the machine GUID from the registry
- ShellExt.exe (PID: 3232)
- mail_pot.exe (PID: 3384)
- Purchase Order Pending Quantity.exe (PID: 1612)
- Purchase Order Pending Quantity.exe (PID: 3560)
- Purchase Order Pending Quantity.exe (PID: 3536)
- Purchase Order Pending Quantity.exe (PID: 2584)
- Purchase Order Pending Quantity.exe (PID: 2440)
- Purchase Order Pending Quantity.exe (PID: 2612)
- Purchase Order Pending Quantity.exe (PID: 2276)
Reads Microsoft Office registry keys
- mail_pot.exe (PID: 3384)
Reads Environment values
- fakeDNS.exe (PID: 2928)
- Purchase Order Pending Quantity.exe (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:11:28 19:55:50 |
| ZipCRC: | 0x3c9fb4fe |
| ZipCompressedSize: | 523751 |
| ZipUncompressedSize: | 557056 |
| ZipFileName: | Purchase Order Pending Quantity.exe |
Total processes
79
Monitored processes
30
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225547 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
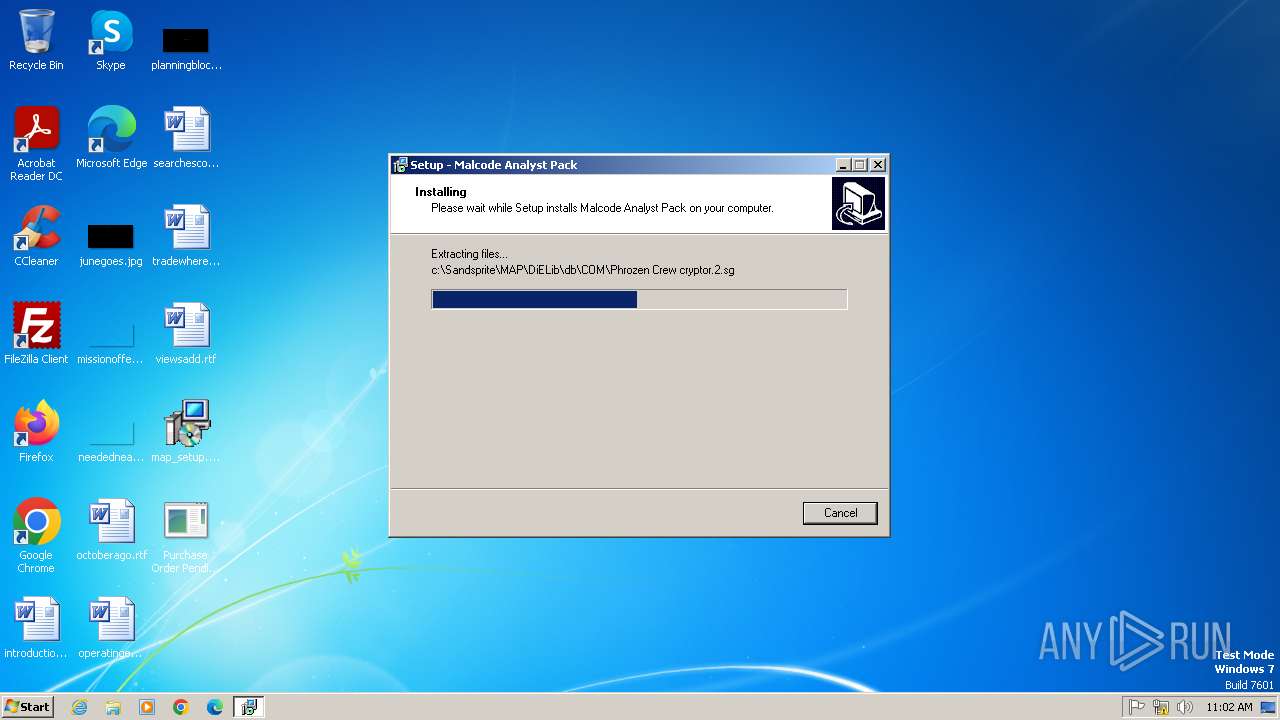
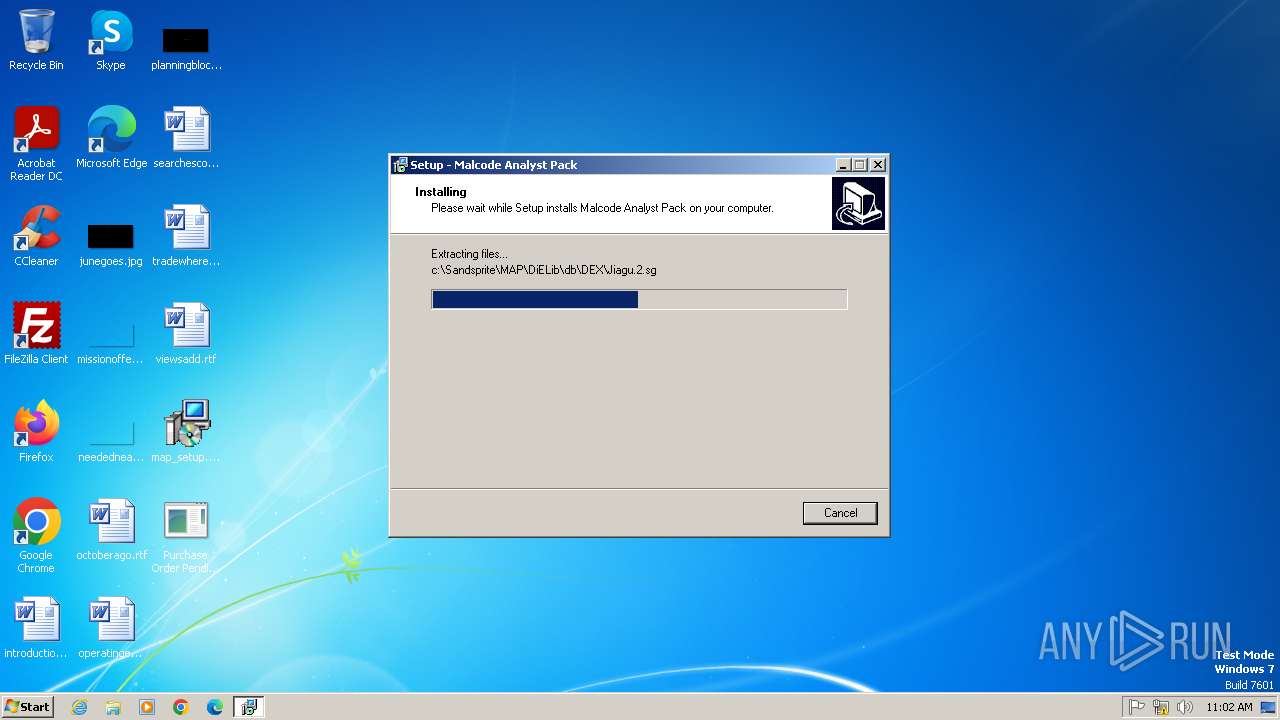
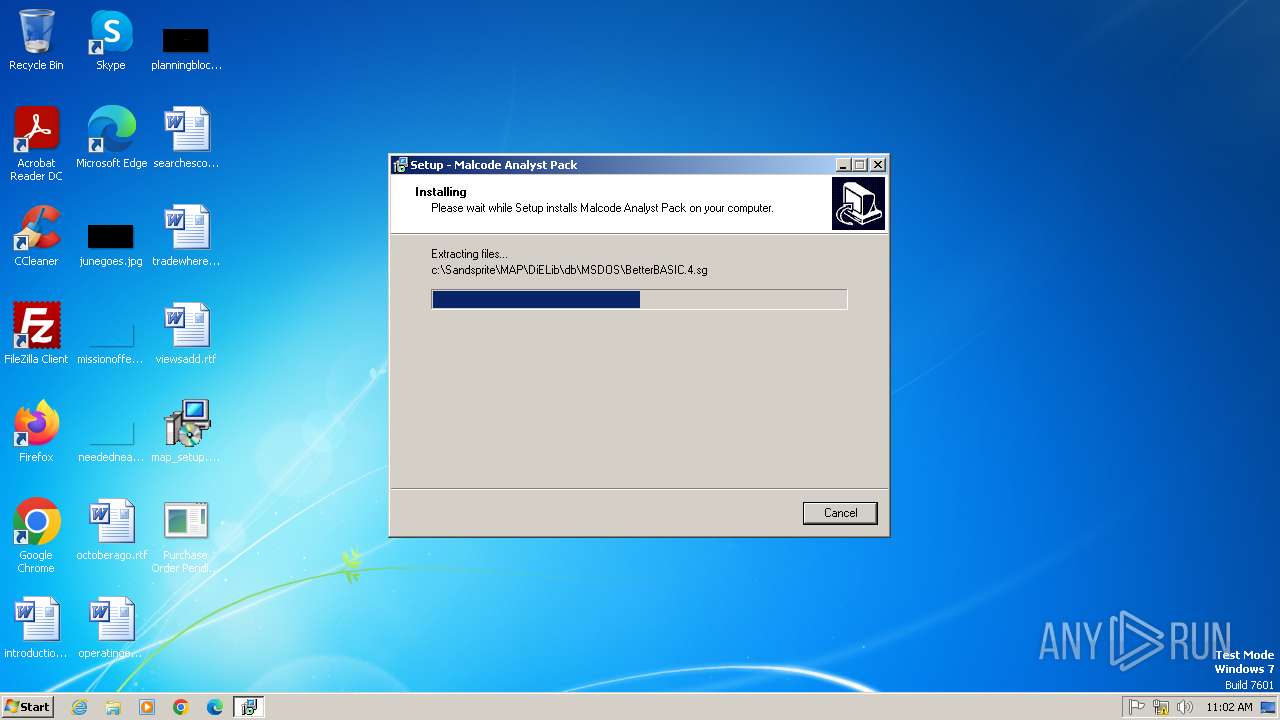
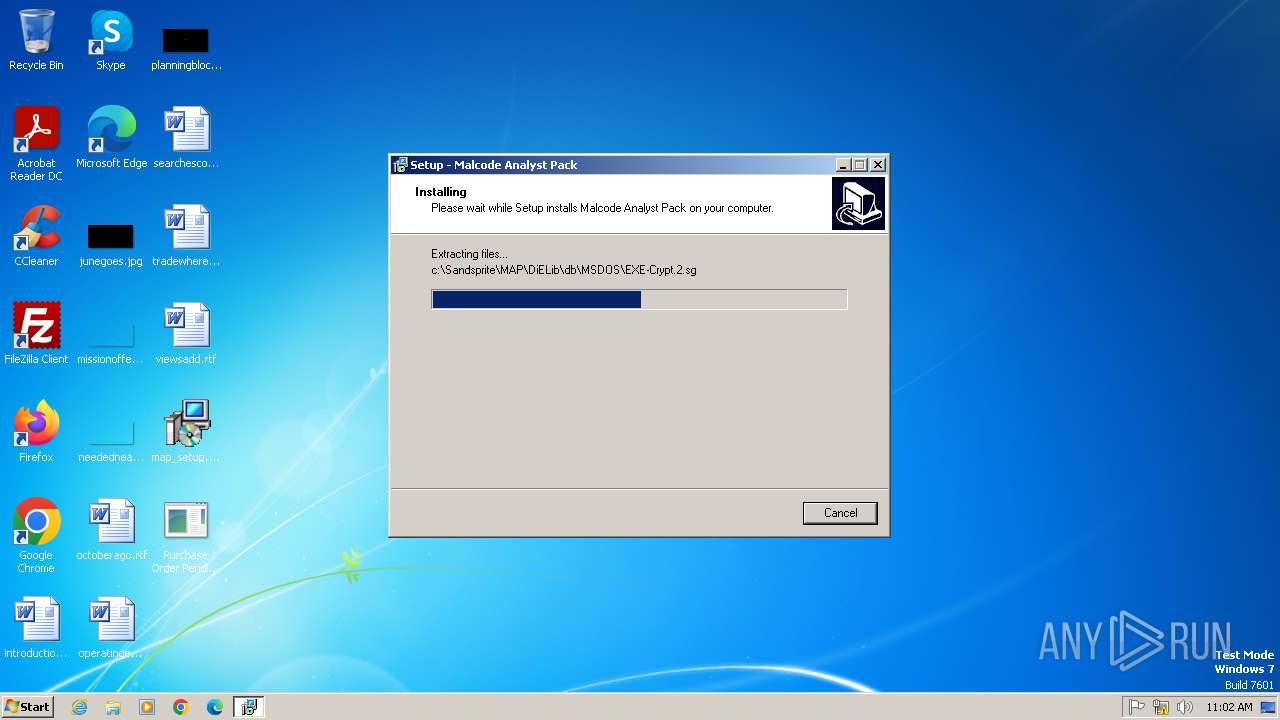
| 972 | "C:\Users\admin\Desktop\map_setup.exe" /SPAWNWND=$3018A /NOTIFYWND=$3017C | C:\Users\admin\Desktop\map_setup.exe | map_setup.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Malcode Analyst Pack Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\AppData\Local\Temp\is-A1IRP.tmp\map_setup.tmp" /SL5="$3017C,5995619,53248,C:\Users\admin\Desktop\map_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-A1IRP.tmp\map_setup.tmp | — | map_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
| 1612 | "C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe" | C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe | explorer.exe | ||||||||||||
User: admin Company: Earthworks Garden Kare Integrity Level: HIGH Description: WpfClassProject Exit code: 4294967295 Version: 5.4.0.0 Modules
| |||||||||||||||
| 2056 | "C:\Users\admin\AppData\Local\Temp\is-80GRE.tmp\map_setup.tmp" /SL5="$4018C,5995619,53248,C:\Users\admin\Desktop\map_setup.exe" /SPAWNWND=$3018A /NOTIFYWND=$3017C | C:\Users\admin\AppData\Local\Temp\is-80GRE.tmp\map_setup.tmp | map_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe" | C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe | — | Purchase Order Pending Quantity.exe | |||||||||||
User: admin Company: Earthworks Garden Kare Integrity Level: MEDIUM Description: WpfClassProject Version: 5.4.0.0 Modules
| |||||||||||||||
| 2368 | "C:\Users\admin\Desktop\map_setup.exe" | C:\Users\admin\Desktop\map_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Malcode Analyst Pack Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe" | C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe | — | explorer.exe | |||||||||||
User: admin Company: Earthworks Garden Kare Integrity Level: MEDIUM Description: WpfClassProject Exit code: 4294967295 Version: 5.4.0.0 Modules
| |||||||||||||||
| 2584 | "C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe" | C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe | — | explorer.exe | |||||||||||
User: admin Company: Earthworks Garden Kare Integrity Level: MEDIUM Description: WpfClassProject Exit code: 4294967295 Version: 5.4.0.0 Modules
| |||||||||||||||
| 2612 | "C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe" | C:\Users\admin\Desktop\Purchase Order Pending Quantity.exe | — | explorer.exe | |||||||||||
User: admin Company: Earthworks Garden Kare Integrity Level: MEDIUM Description: WpfClassProject Version: 5.4.0.0 Modules
| |||||||||||||||
Total events
11 163
Read events
10 728
Write events
289
Delete events
146
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Purchase Order Pending Quantity.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
91
Suspicious files
39
Text files
2 962
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2056 | map_setup.tmp | C:\Windows\is-JPMH0.tmp | executable | |
MD5:EF09271336B4B2BF5846929CF0DA8623 | SHA256:81776AA16A70F102E0F4BCF43713BE0BB4C09CD37086C091F91533EB6F2CFDF5 | |||
| 2056 | map_setup.tmp | C:\Windows\is-GBTQF.tmp | executable | |
MD5:764340407F32F1DE12C1388E3948C2BC | SHA256:766D9C112CE4D56C6BF80DC96110CFCC562D1F39D2730D7D863EFF01CE45226D | |||
| 2056 | map_setup.tmp | C:\Sandsprite\MAP\unins000.exe | executable | |
MD5:F92285603B19A4928AF4B0B7CD5F2403 | SHA256:6A23972E1C391BA2DADA01FEABCB7CDC8DF2DD3FCA80D7373DF08BE96B5D7A43 | |||
| 2056 | map_setup.tmp | C:\Windows\vbUtypes.dll | executable | |
MD5:EF09271336B4B2BF5846929CF0DA8623 | SHA256:81776AA16A70F102E0F4BCF43713BE0BB4C09CD37086C091F91533EB6F2CFDF5 | |||
| 2056 | map_setup.tmp | C:\Windows\is-MJCA9.tmp | executable | |
MD5:473DB5D8A5FC1FB4B5A435BCA597C3A9 | SHA256:81167418607AFD06660578E33E03995C49EA9BC29DB9095846B1022E5212F64A | |||
| 2056 | map_setup.tmp | C:\Windows\sppe3.dll | executable | |
MD5:473DB5D8A5FC1FB4B5A435BCA597C3A9 | SHA256:81167418607AFD06660578E33E03995C49EA9BC29DB9095846B1022E5212F64A | |||
| 2056 | map_setup.tmp | C:\Windows\spSubclass2.dll | executable | |
MD5:764340407F32F1DE12C1388E3948C2BC | SHA256:766D9C112CE4D56C6BF80DC96110CFCC562D1F39D2730D7D863EFF01CE45226D | |||
| 2056 | map_setup.tmp | C:\Sandsprite\MAP\is-SS3J8.tmp | executable | |
MD5:F92285603B19A4928AF4B0B7CD5F2403 | SHA256:6A23972E1C391BA2DADA01FEABCB7CDC8DF2DD3FCA80D7373DF08BE96B5D7A43 | |||
| 2368 | map_setup.exe | C:\Users\admin\AppData\Local\Temp\is-A1IRP.tmp\map_setup.tmp | executable | |
MD5:9E30AB5E3F6B43F69F928E6B4FCFD604 | SHA256:AFFBE7F0320F9602D8C51468ECB7BC7960DF4F62AB1A36C05AC2FE2816D175BA | |||
| 972 | map_setup.exe | C:\Users\admin\AppData\Local\Temp\is-80GRE.tmp\map_setup.tmp | executable | |
MD5:9E30AB5E3F6B43F69F928E6B4FCFD604 | SHA256:AFFBE7F0320F9602D8C51468ECB7BC7960DF4F62AB1A36C05AC2FE2816D175BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
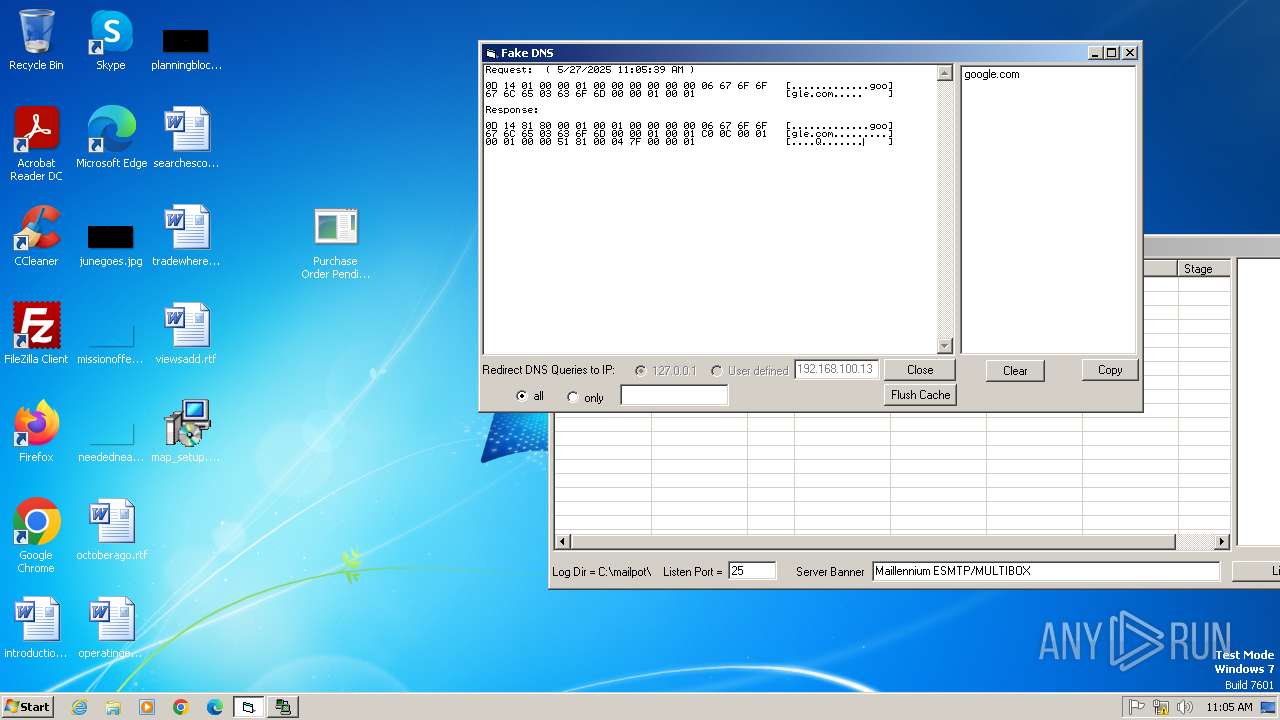
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |