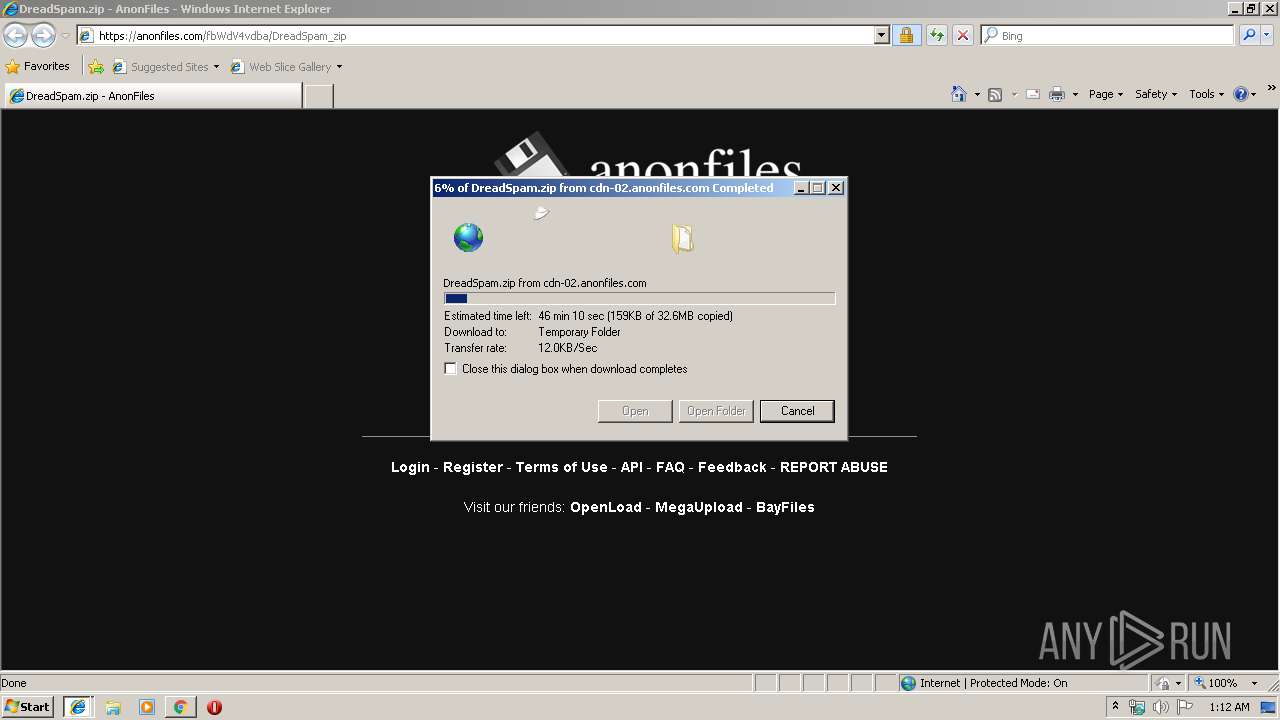
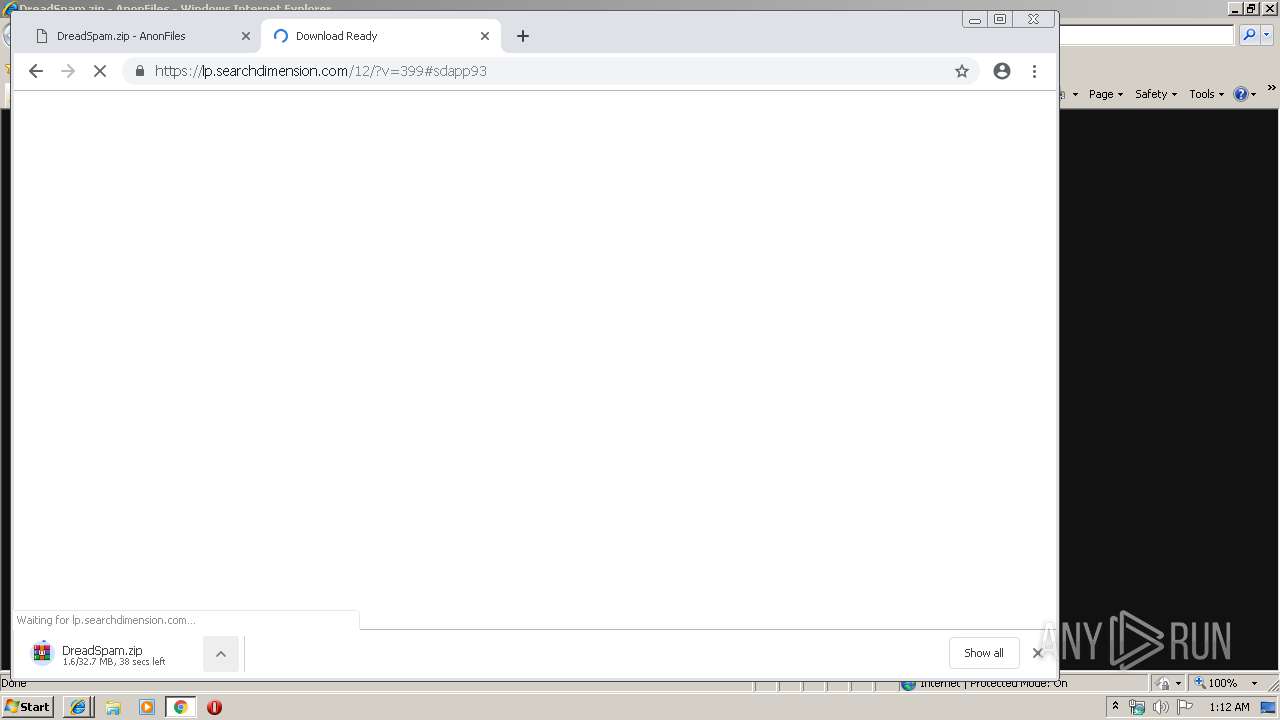
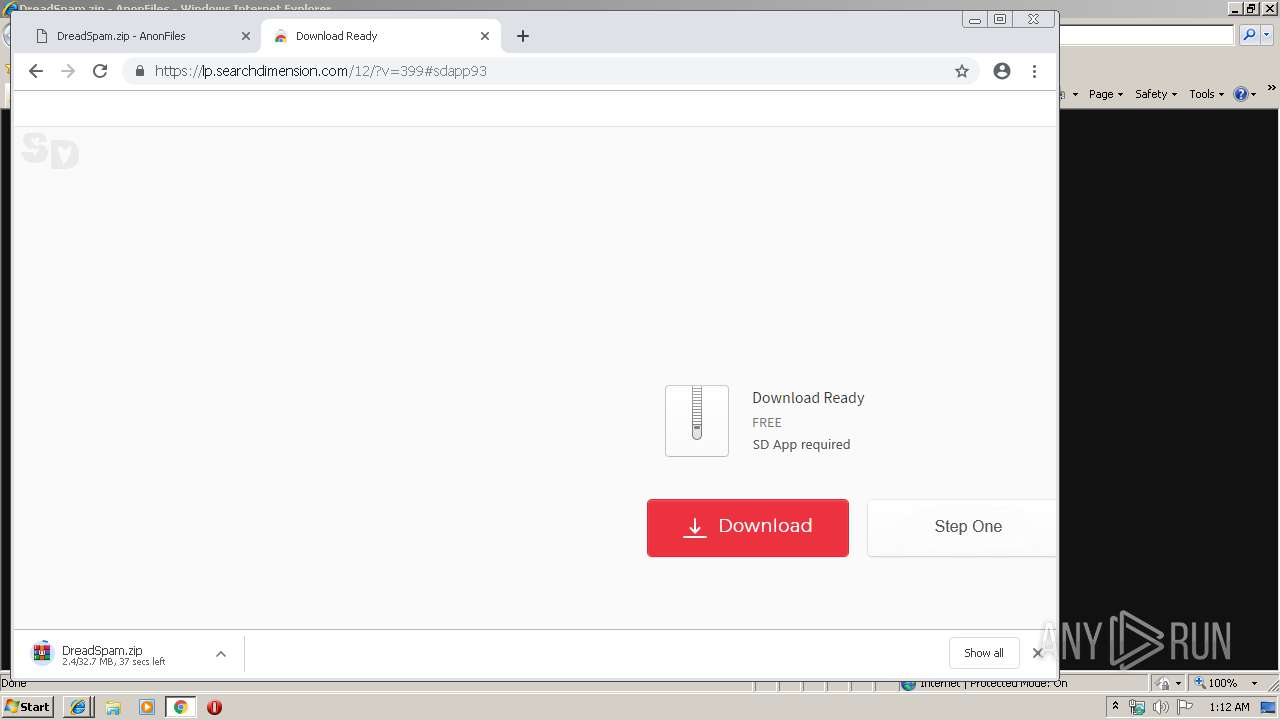
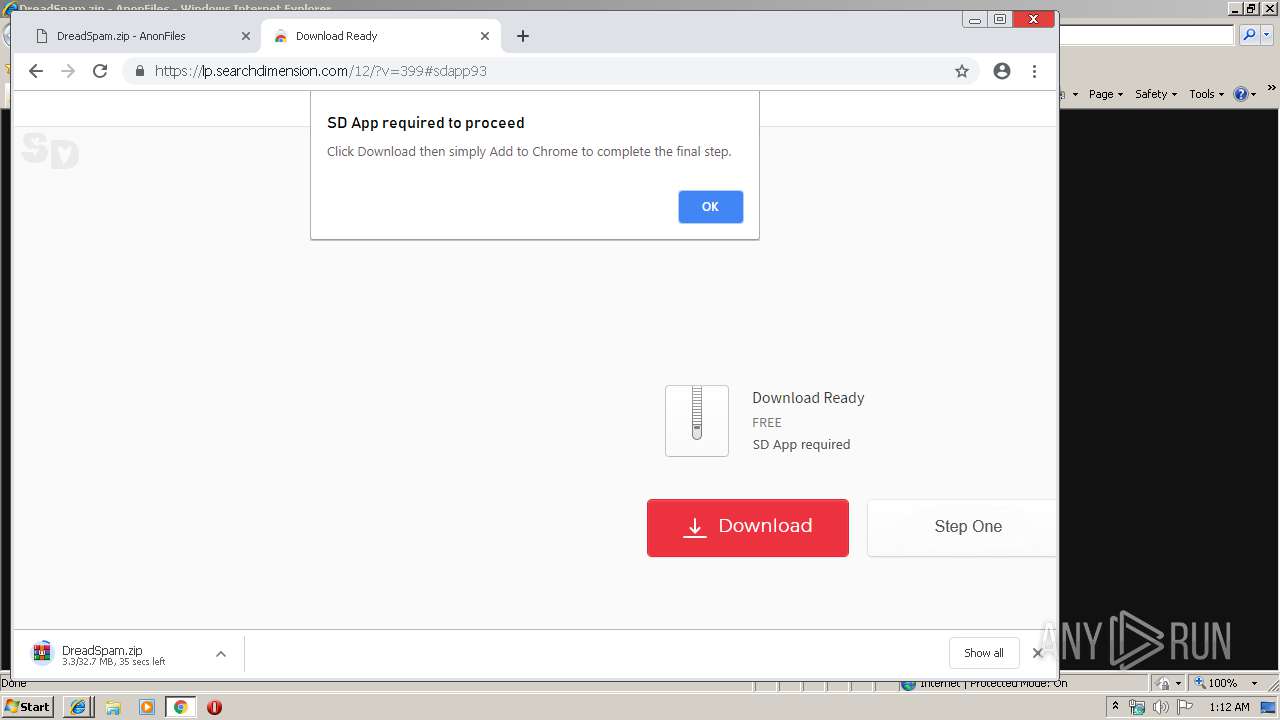
| URL: | http://bit.ly/2XI66bx |
| Full analysis: | https://app.any.run/tasks/0ae79495-2ee1-4441-867a-6d26420d8b9d |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 01:11:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7A825D11FE2FCE192FF02E5A222190F3 |
| SHA1: | 6BCB33BEF87EB974538978C2E99DE3911B9E66A9 |
| SHA256: | BDA1727D4C7639A4F7A59CF1B0C6C474F5CBCBC076785B2CC9C6A96C00FA6486 |
| SSDEEP: | 3:N1KcQ9T9sF:CcY9+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1896)
- chrome.exe (PID: 2480)
Creates files in the user directory
- iexplore.exe (PID: 2664)
- iexplore.exe (PID: 1896)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1308)
Reads Internet Cache Settings
- iexplore.exe (PID: 2664)
Changes internet zones settings
- iexplore.exe (PID: 1896)
Reads internet explorer settings
- iexplore.exe (PID: 2664)
Reads settings of System Certificates
- chrome.exe (PID: 3020)
- iexplore.exe (PID: 1896)
Changes settings of System certificates
- iexplore.exe (PID: 1896)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
23
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1308 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 1552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8317723538320936016 --mojo-platform-channel-handle=3384 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
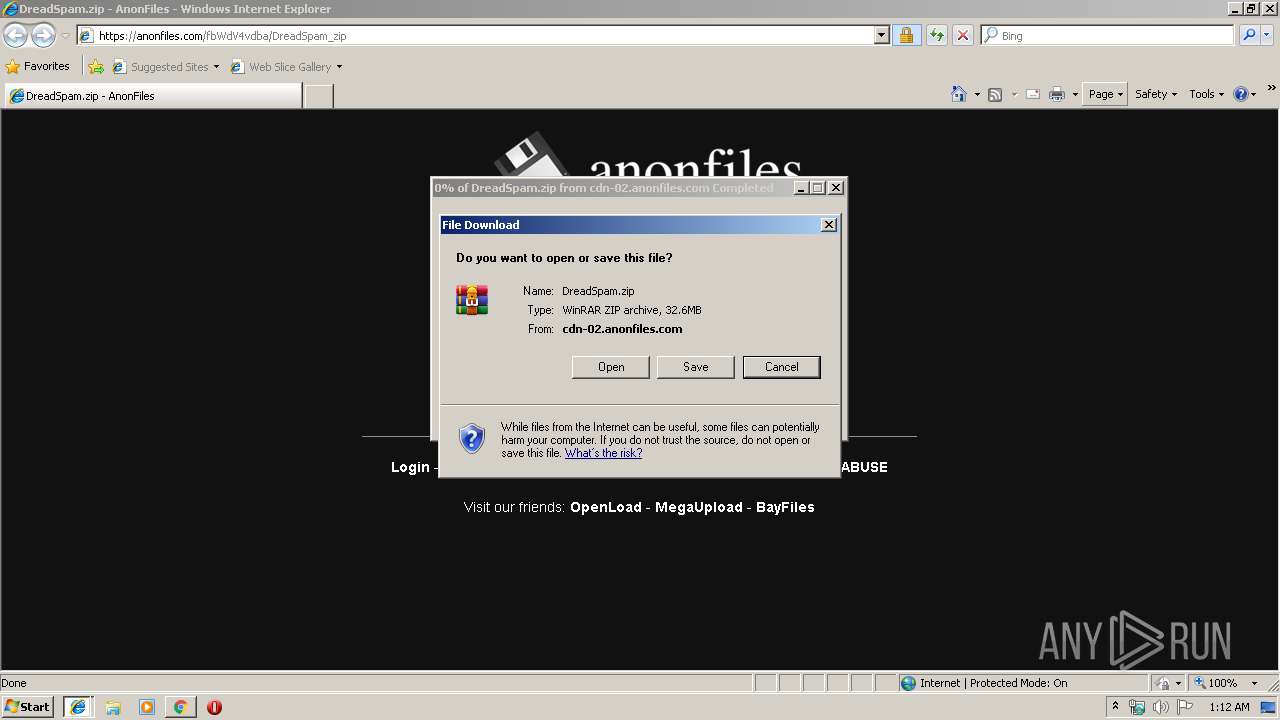
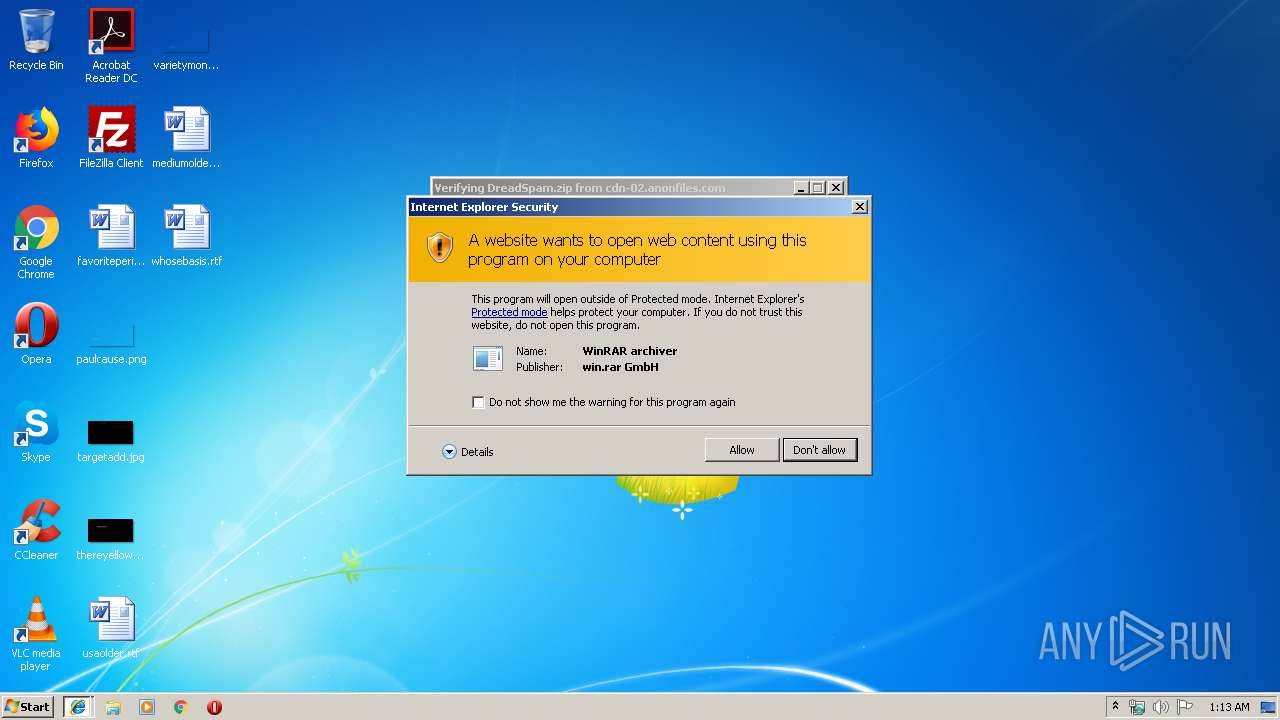
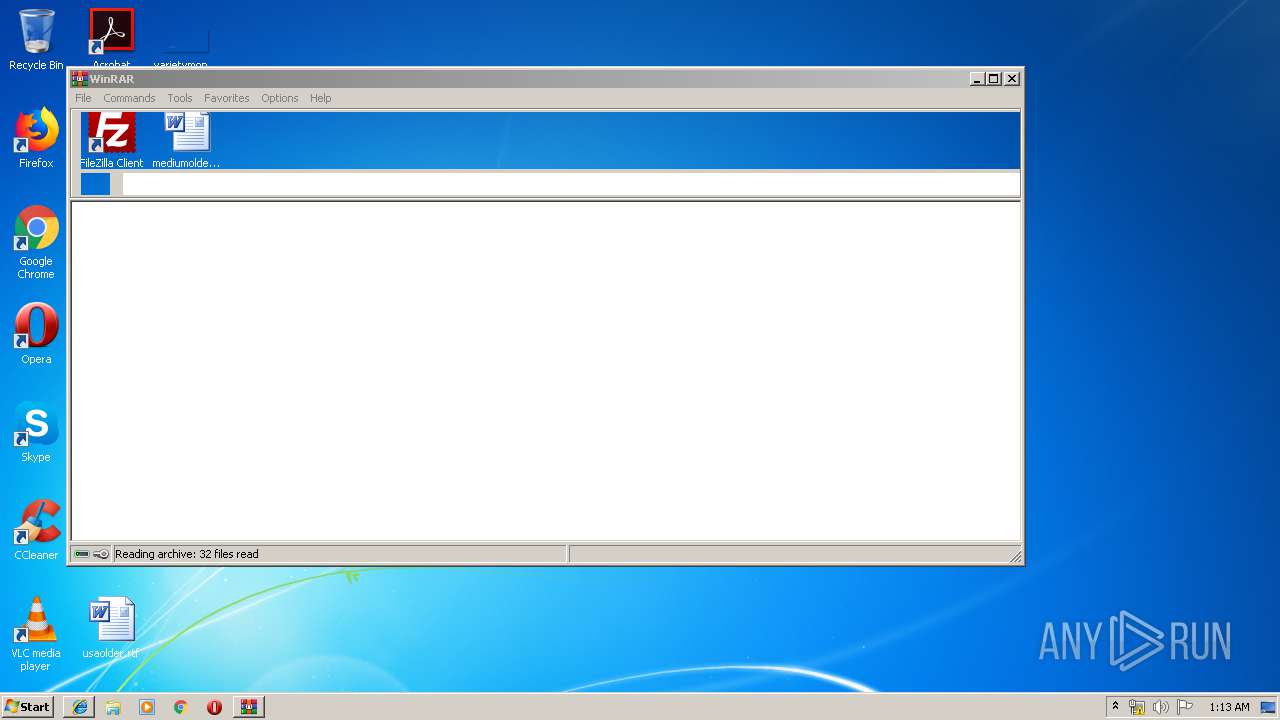
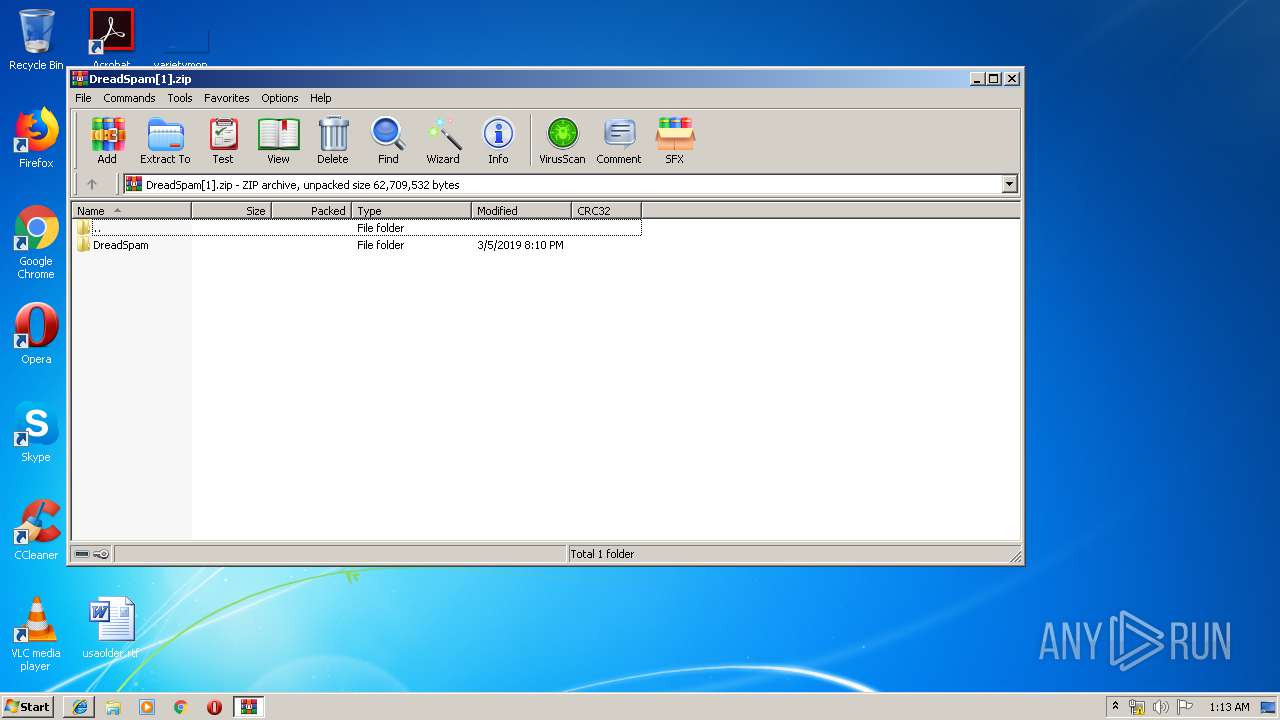
| 1576 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YNUM4JW3\DreadSpam[1].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7715150990086554195 --mojo-platform-channel-handle=3384 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8747909345178512965 --mojo-platform-channel-handle=2812 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=12952239333627703324 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12952239333627703324 --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17327268351322038397 --mojo-platform-channel-handle=3468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,12684997339045725452,16090892915763788794,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4173392682327652775 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4173392682327652775 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3376 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 657
Read events
1 367
Write events
279
Delete events
11
Modification events
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006E000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {87D080B3-4C3F-11E9-A302-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (1896) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30703000500160001000C0011002C01 | |||
Executable files
0
Suspicious files
90
Text files
187
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\TXETDQAZ\DreadSpam_zip[1].txt | — | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bit[1].txt | text | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\TXETDQAZ\DreadSpam_zip[1].htm | html | |
MD5:— | SHA256:— | |||
| 2664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\9RU1HVLX\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
68
DNS requests
58
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3020 | chrome.exe | GET | 200 | 173.194.19.183:80 | http://r1---sn-5go7yn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=82.102.22.104&mm=28&mn=sn-5go7yn7z&ms=nvh&mt=1553217085&mv=m&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2664 | iexplore.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
2664 | iexplore.exe | GET | 301 | 67.199.248.10:80 | http://bit.ly/2XI66bx | US | html | 133 b | shared |
3020 | chrome.exe | GET | 302 | 216.58.207.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
2664 | iexplore.exe | GET | 200 | 52.85.188.34:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
1896 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2664 | iexplore.exe | 194.32.146.58:443 | anonfiles.com | — | — | unknown |
2664 | iexplore.exe | 67.199.248.10:80 | bit.ly | Bitly Inc | US | shared |
1896 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2664 | iexplore.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2664 | iexplore.exe | 23.111.8.154:443 | oss.maxcdn.com | netDNA | US | unknown |
2664 | iexplore.exe | 172.217.18.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2664 | iexplore.exe | 172.217.18.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2664 | iexplore.exe | 54.230.95.12:443 | boudja.com | Amazon.com, Inc. | US | suspicious |
2664 | iexplore.exe | 205.185.216.42:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2664 | iexplore.exe | 52.71.34.61:443 | agreensdistra.info | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bit.ly |
| shared |
www.bing.com |
| whitelisted |
anonfiles.com |
| shared |
vjs.zencdn.net |
| whitelisted |
oss.maxcdn.com |
| whitelisted |
cdn-101.anonfile.com |
| suspicious |
www.googletagmanager.com |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
www.google-analytics.com |
| whitelisted |
boudja.com |
| whitelisted |