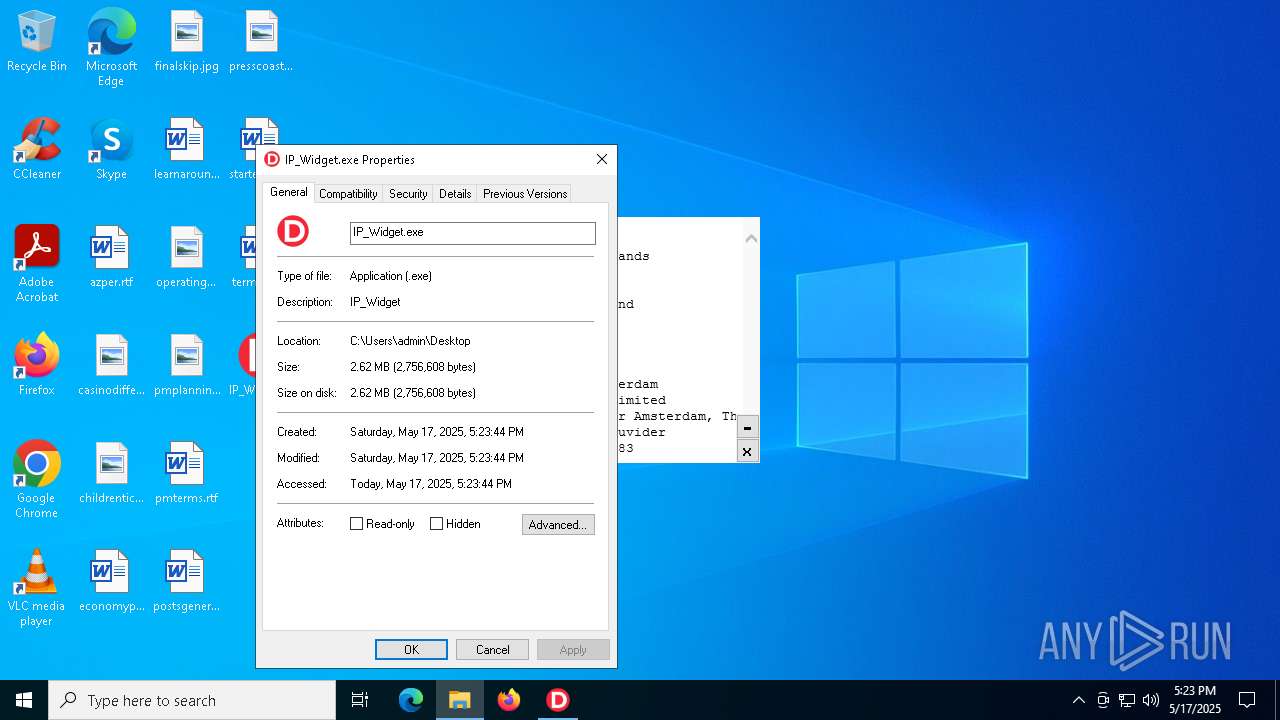
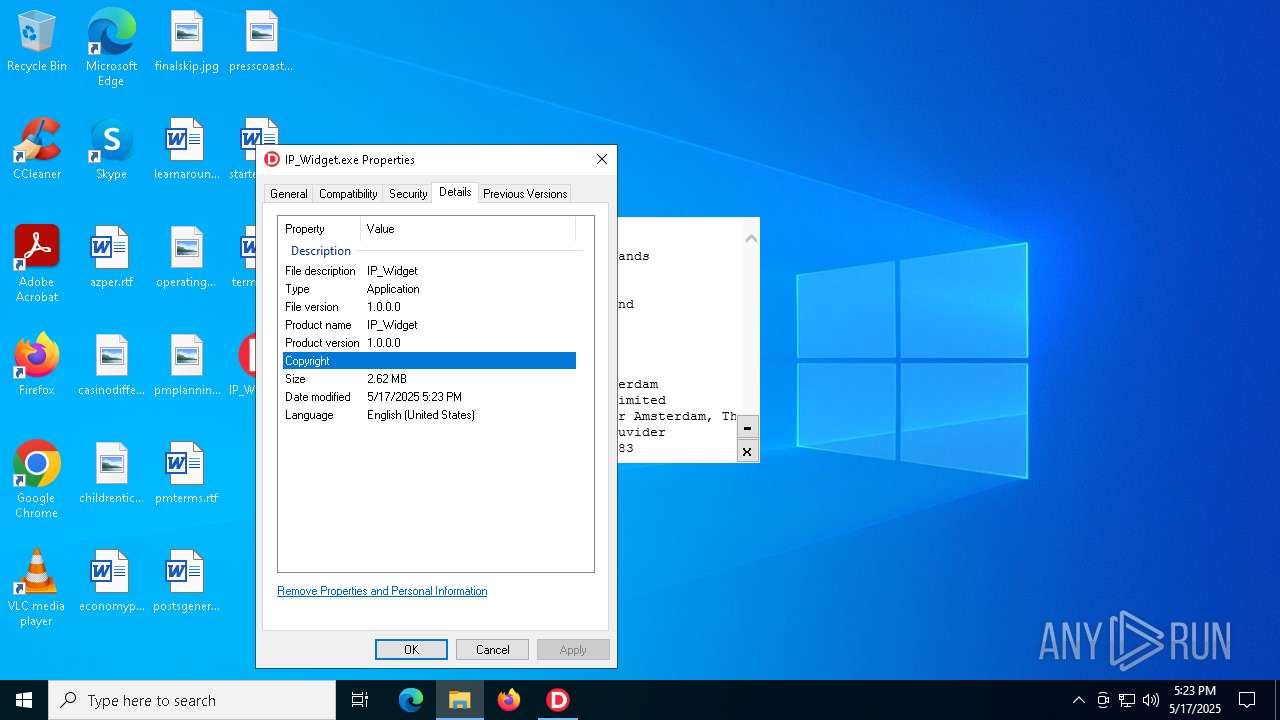
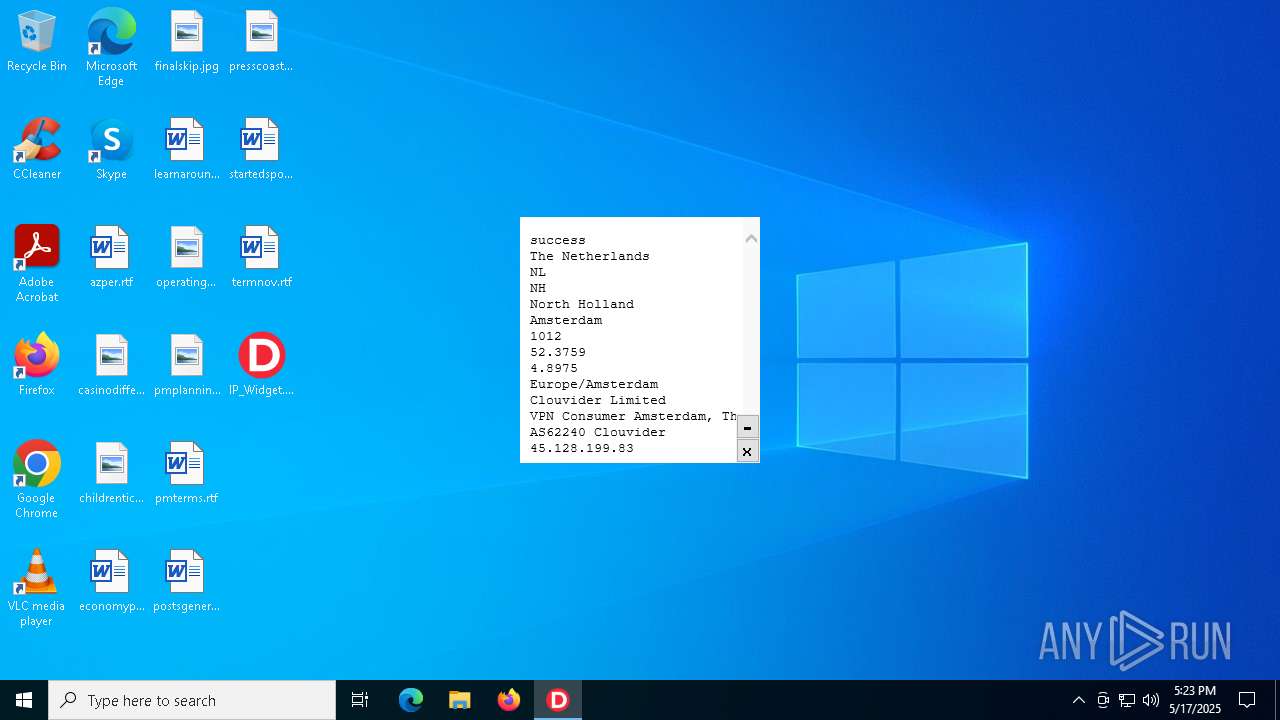
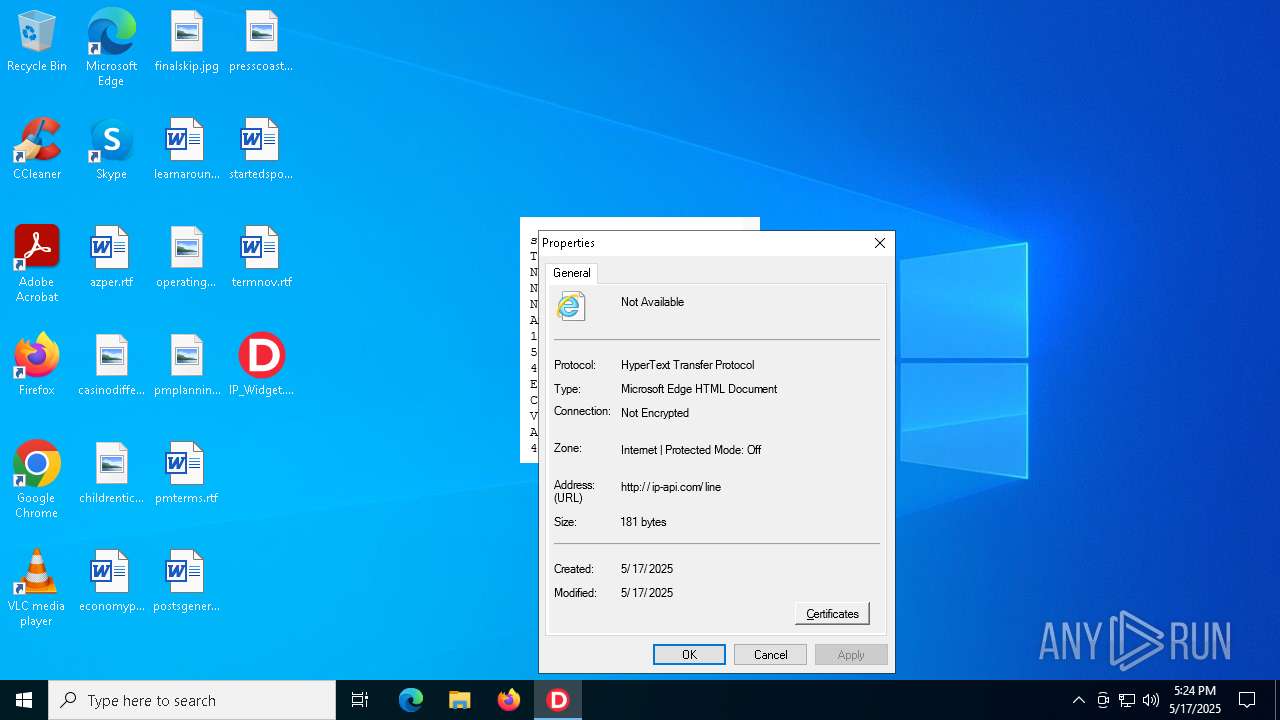
| File name: | IP_Widget.exe |
| Full analysis: | https://app.any.run/tasks/97130737-2096-470f-a3a2-1bea7c411be6 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 17:23:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 53965D0F0C1A1B8DB07B3F4F42CD1389 |
| SHA1: | 5424C6ABD151C7B75B5D97B4B4681DE59409E97F |
| SHA256: | BD8A01EB59F33B0B4A5FADA26900E85BB78068E7BDCD75CDBD71CC0E2B839CAF |
| SSDEEP: | 49152:j8x4zgjR9rSRvfkv6a4FAlYZJSTtajYwS8cuAJ0cYSdo:g6UjvSRvfkv6aMkp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- IP_Widget.exe (PID: 2320)
- IP_Widget.exe (PID: 7672)
Reads security settings of Internet Explorer
- IP_Widget.exe (PID: 2320)
- IP_Widget.exe (PID: 7672)
There is functionality for taking screenshot (YARA)
- IP_Widget.exe (PID: 2320)
Checks for external IP
- IP_Widget.exe (PID: 2320)
- svchost.exe (PID: 2196)
- IP_Widget.exe (PID: 7672)
Reads Internet Explorer settings
- IP_Widget.exe (PID: 2320)
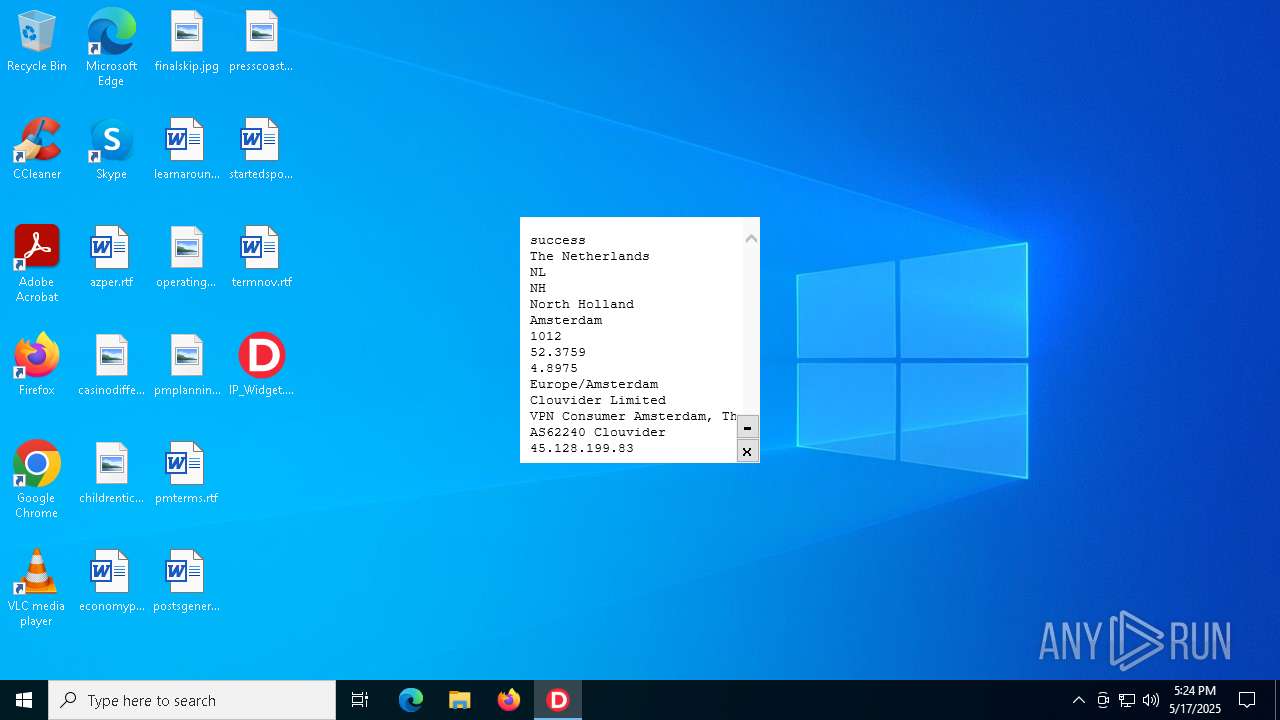
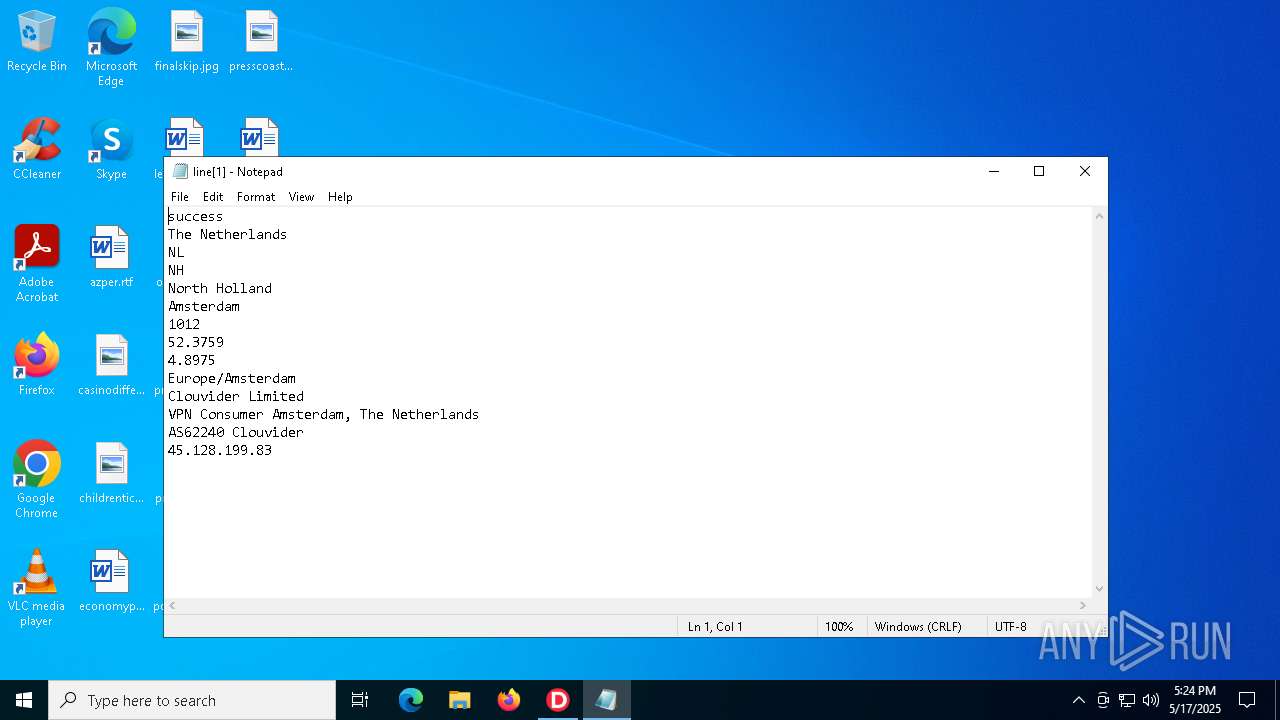
Start notepad (likely ransomware note)
- IP_Widget.exe (PID: 2320)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 856)
INFO
The sample compiled with english language support
- IP_Widget.exe (PID: 2320)
Checks supported languages
- IP_Widget.exe (PID: 2320)
- IP_Widget.exe (PID: 7672)
Creates files or folders in the user directory
- IP_Widget.exe (PID: 2320)
Reads the computer name
- IP_Widget.exe (PID: 2320)
- IP_Widget.exe (PID: 7672)
Checks proxy server information
- IP_Widget.exe (PID: 2320)
- IP_Widget.exe (PID: 7672)
- slui.exe (PID: 2516)
Manual execution by a user
- Acrobat.exe (PID: 2148)
- IP_Widget.exe (PID: 7672)
Reads security settings of Internet Explorer
- printfilterpipelinesvc.exe (PID: 684)
- notepad.exe (PID: 1324)
- splwow64.exe (PID: 856)
- dllhost.exe (PID: 5548)
Process checks computer location settings
- IP_Widget.exe (PID: 2320)
Compiled with Borland Delphi (YARA)
- IP_Widget.exe (PID: 2320)
- notepad.exe (PID: 1324)
- splwow64.exe (PID: 856)
Reads the machine GUID from the registry
- IP_Widget.exe (PID: 2320)
Create files in a temporary directory
- IP_Widget.exe (PID: 2320)
Reads the software policy settings
- slui.exe (PID: 2516)
- slui.exe (PID: 3884)
Application launched itself
- Acrobat.exe (PID: 2148)
- AcroCEF.exe (PID: 5892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:11 23:14:50+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2350080 |
| InitializedDataSize: | 405504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x23f78c |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | IP_Widget |
| FileVersion: | 1.0.0.0 |
| ProgramID: | com.embarcadero.IP_Widget |
| ProductName: | IP_Widget |
| ProductVersion: | 1.0.0.0 |
Total processes
150
Monitored processes
23
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2084 --field-trial-handle=1612,i,839848740683931086,15593741205132362598,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | IP_Widget.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2164 --field-trial-handle=1612,i,839848740683931086,15593741205132362598,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1324 | "C:\WINDOWS\system32\notepad.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\line[1] | C:\Windows\SysWOW64\notepad.exe | — | IP_Widget.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Desktop\ip.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\IP_Widget.exe" | C:\Users\admin\Desktop\IP_Widget.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: IP_Widget Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2516 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Desktop\ip.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
25 921
Read events
25 642
Write events
257
Delete events
22
Modification events
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\WindowsSearch |
| Operation: | write | Name: | Version |
Value: WS not running | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (856) splwow64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\splwow64.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 2776110000000000 | |||
| (PID) Process: | (5548) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\dllhost.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 878D110000000000 | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (2320) IP_Widget.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
Executable files
0
Suspicious files
237
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 684 | printfilterpipelinesvc.exe | C:\Windows\System32\spool\PRINTERS\PPof4x2yx043b0l2sqvf_tho7ab.TMP | — | |
MD5:— | SHA256:— | |||
| 5892 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:0A2F5B69102130CCF9A623697EC7EEEB | SHA256:4129DE2D3A40190650F6F349854D885A9BAF0F2E564E0F665CD59675214843A7 | |||
| 2772 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents | binary | |
MD5:94AE5B9F05EEADD813A43AD68C6A3B7E | SHA256:627A5E5747D6DBAB97435311FB8AF6B916CC65F33A0530F6F706434D9D622806 | |||
| 5892 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:2EF1F7C0782D1A46974286420D24F629 | SHA256:D3A9BB7E09E1F4B0C41FF7808E930DDACF5DB3BACD98ECCF5BC7DB4863D1FCF5 | |||
| 2772 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 5892 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
| 5892 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF11c689.TMP | text | |
MD5:D012E5B4EB91B61F6E8AE2F8EC3C623E | SHA256:1BDA750084F20306722008016420E1912BA608CA8EFB9C661F7E7EFCF5E89673 | |||
| 2772 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 2320 | IP_Widget.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\line[1] | text | |
MD5:202139AFDB75DFB760F62D81C4996BFF | SHA256:4505AD9D683826AA8024614E6E81A438E0EE2BA4DCA50BA729C9D827AF787E06 | |||
| 2772 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:521F3A6DDD3B75CB15C3F02138E5D68E | SHA256:D4B70A8556954F9FFE87EC19DE4A11B5BBDA485407FEA8ED0489931A180F0446 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
33
DNS requests
24
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.27:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
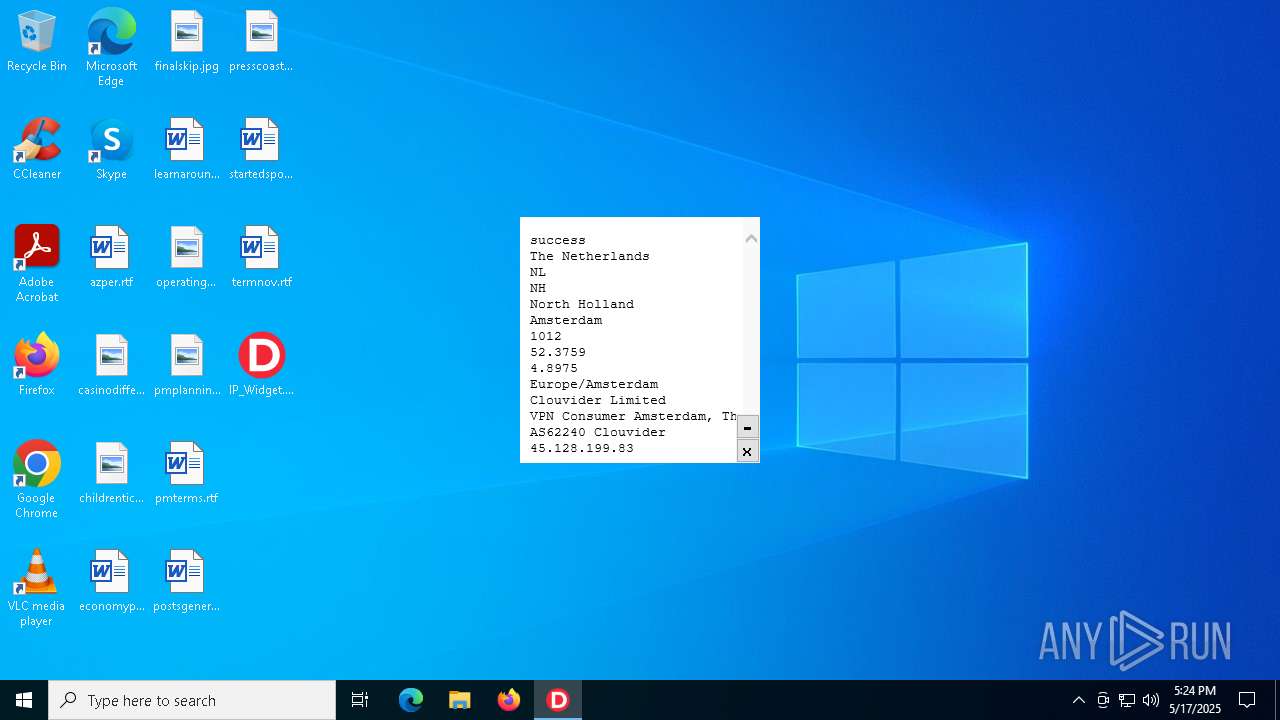
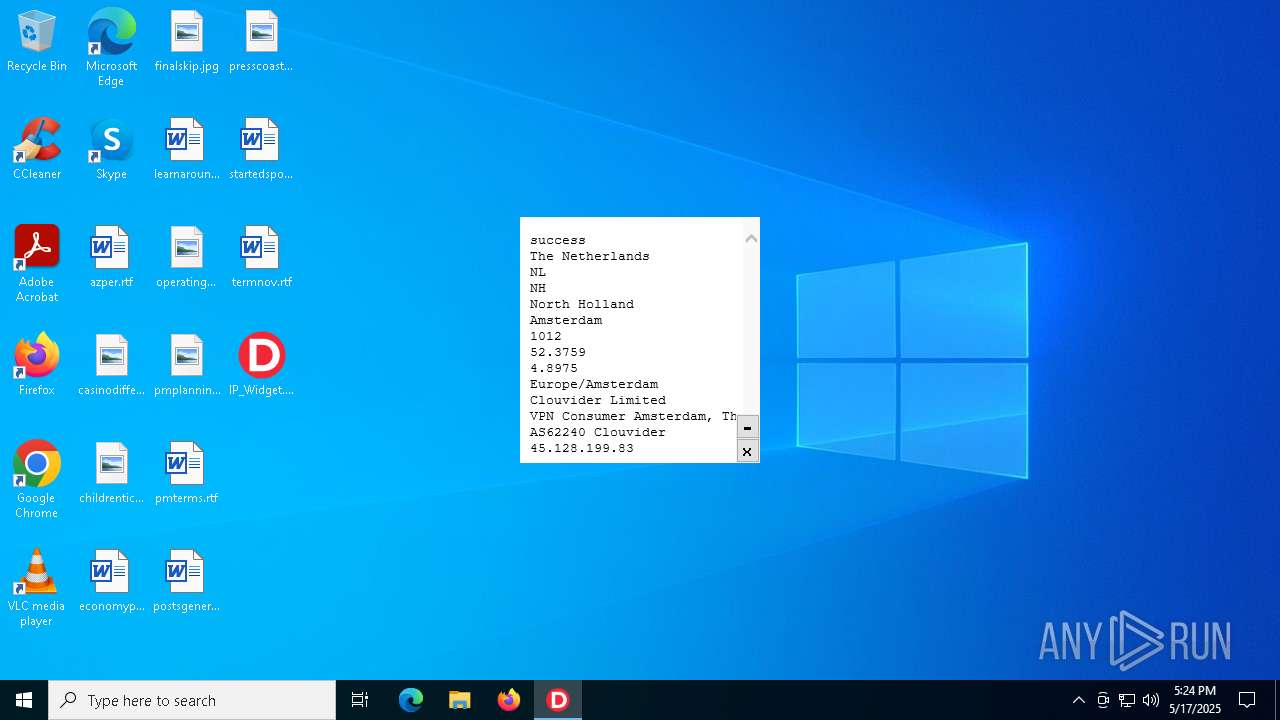
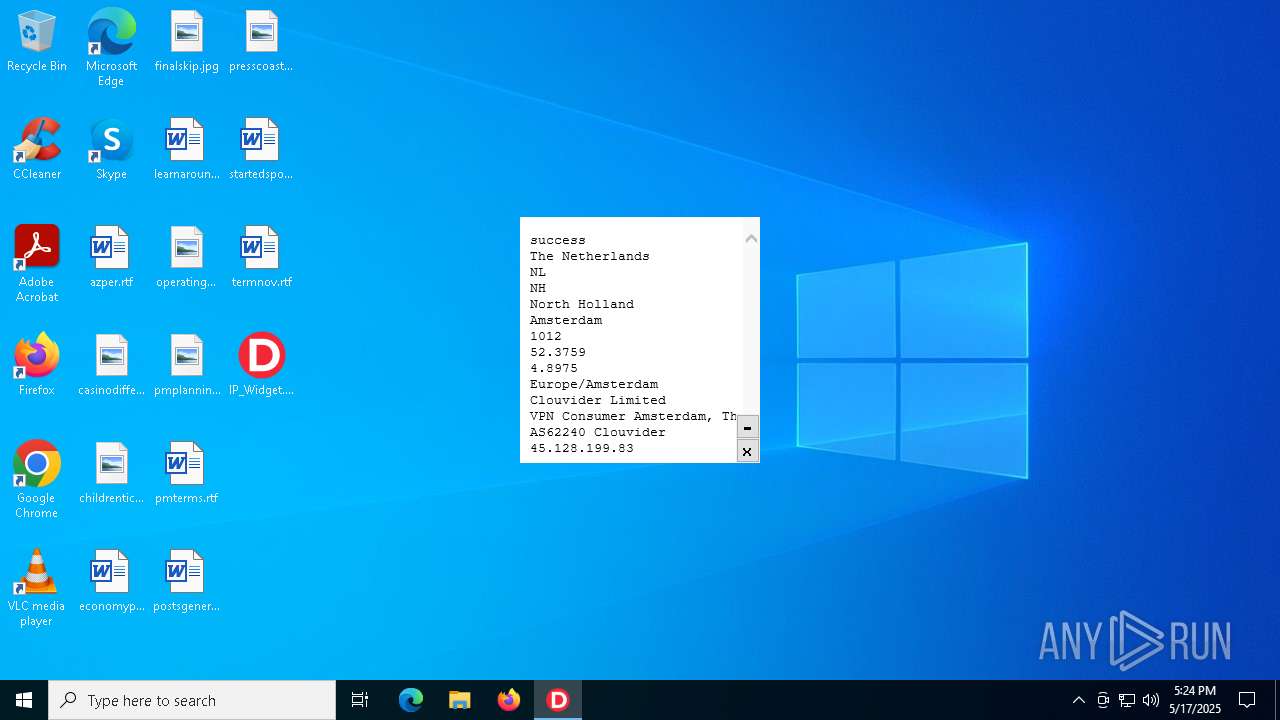
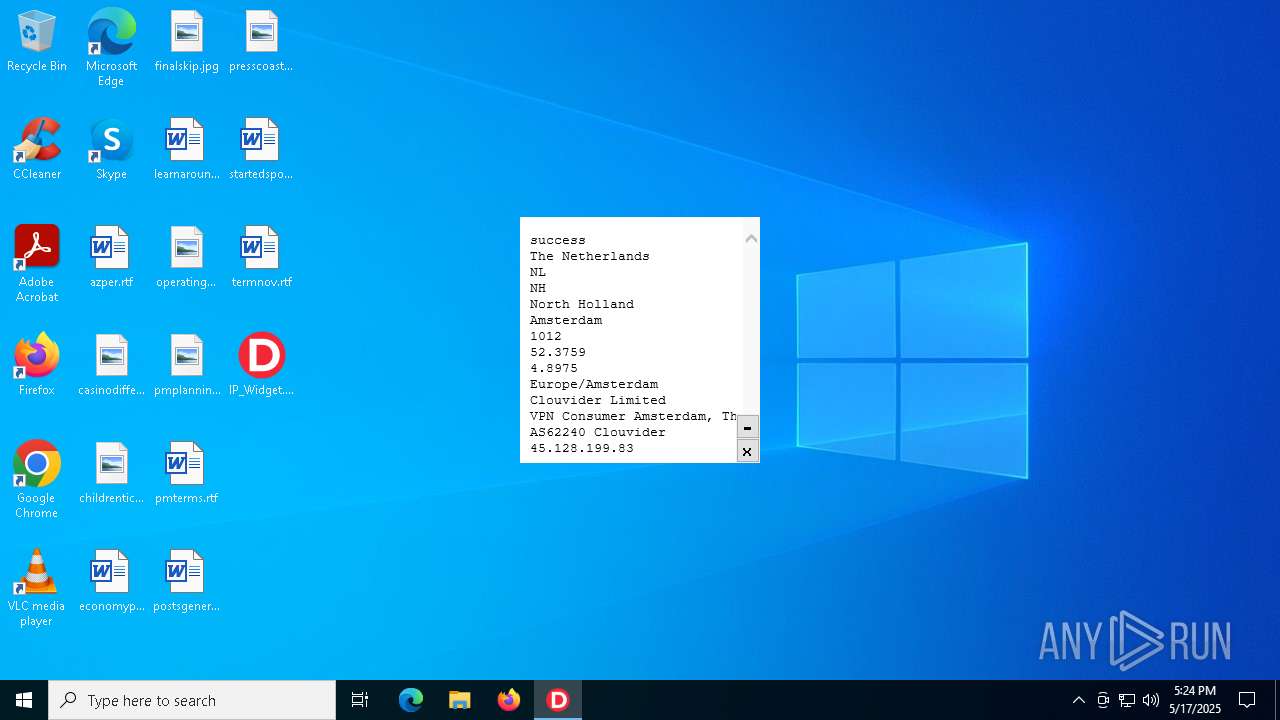
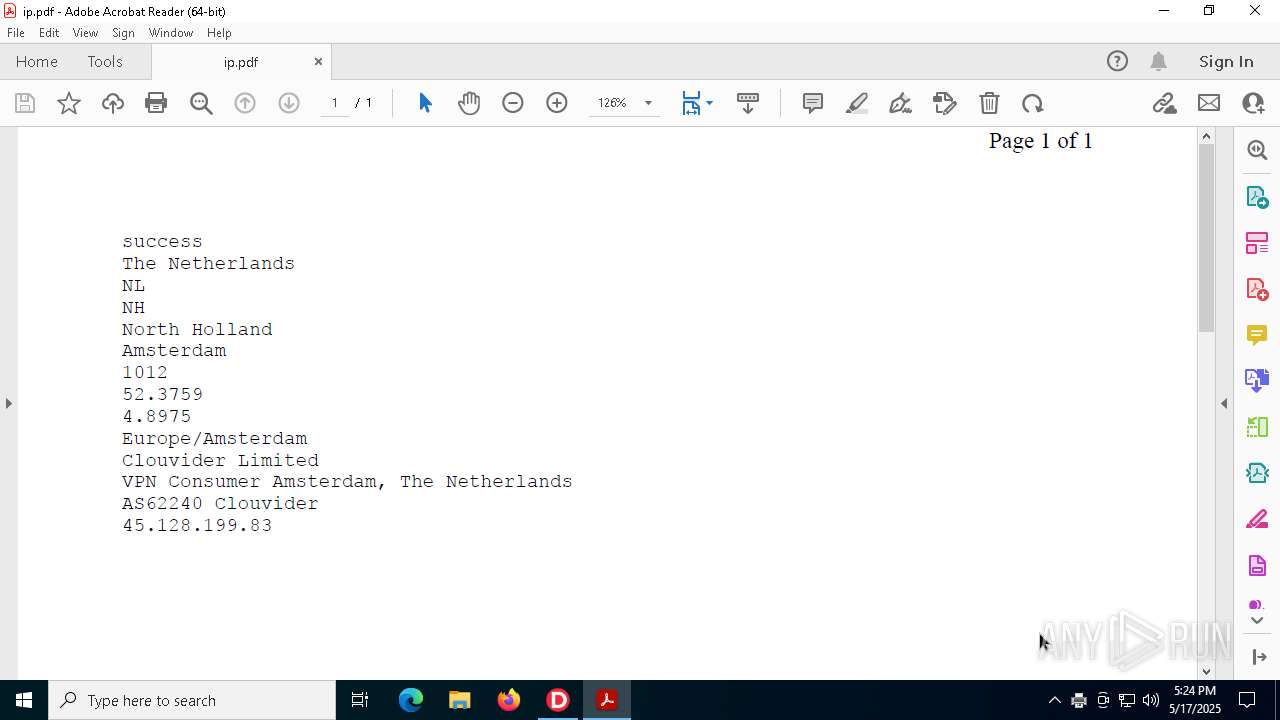
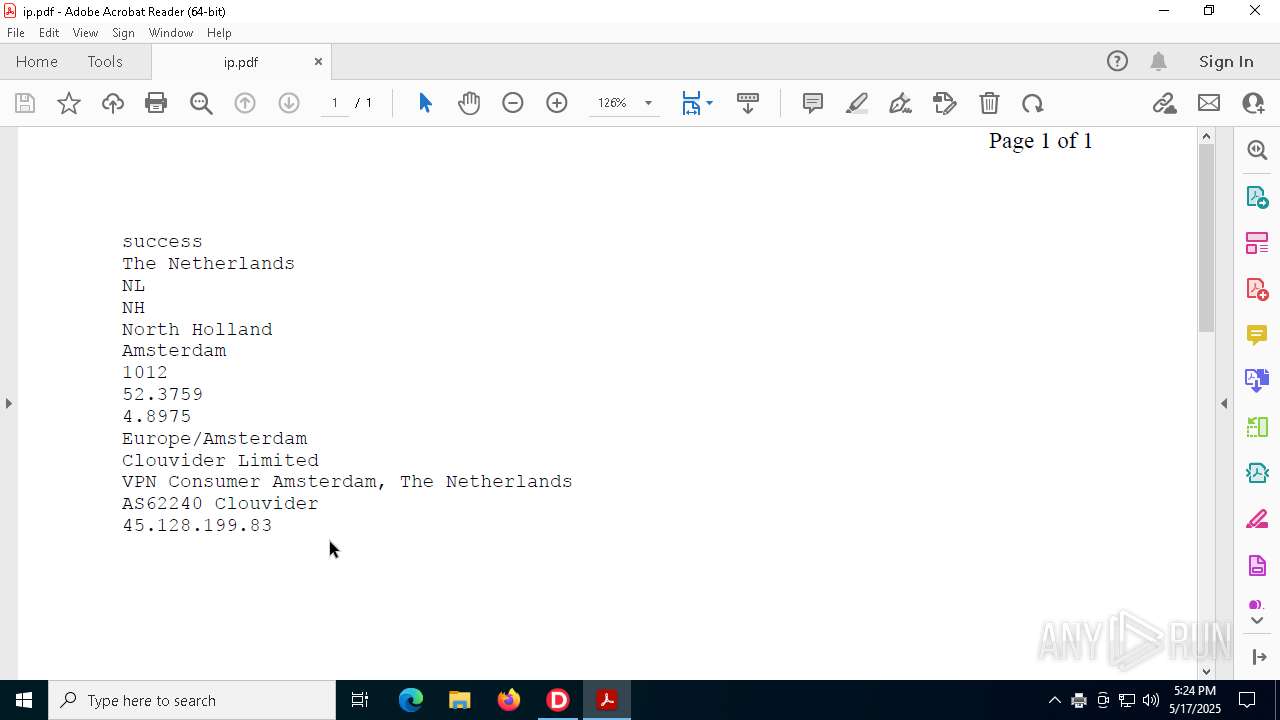
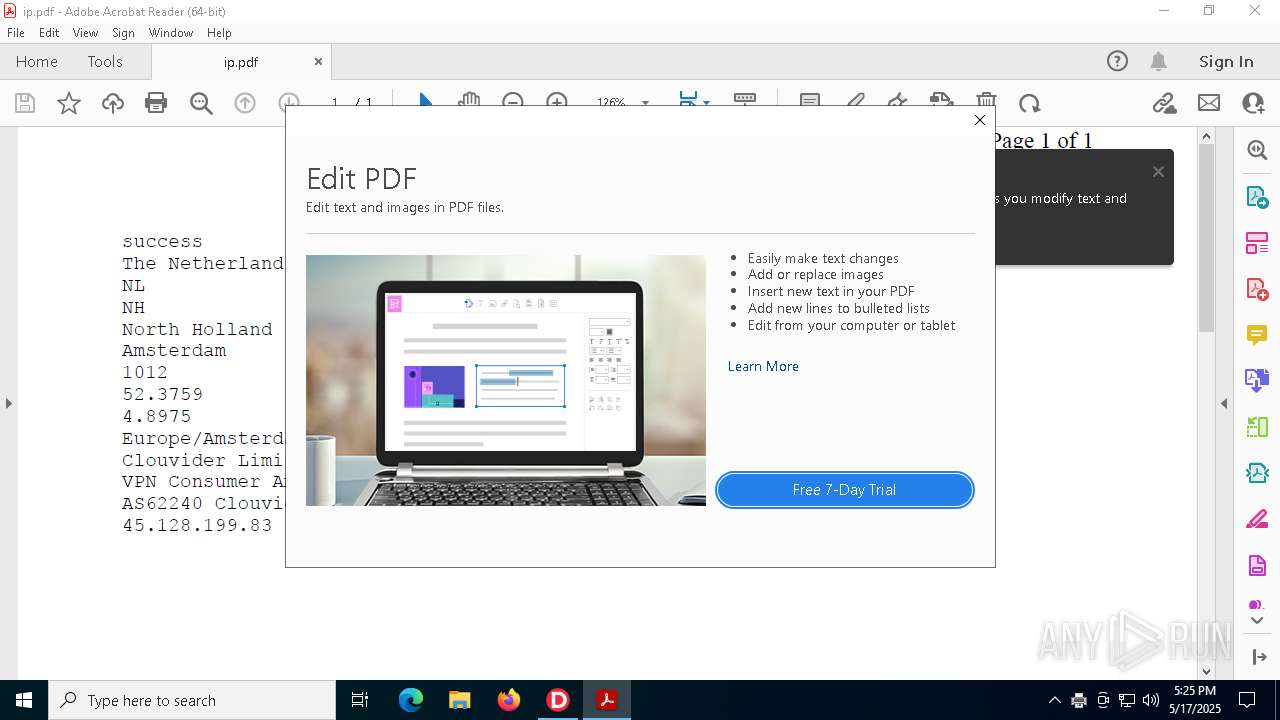
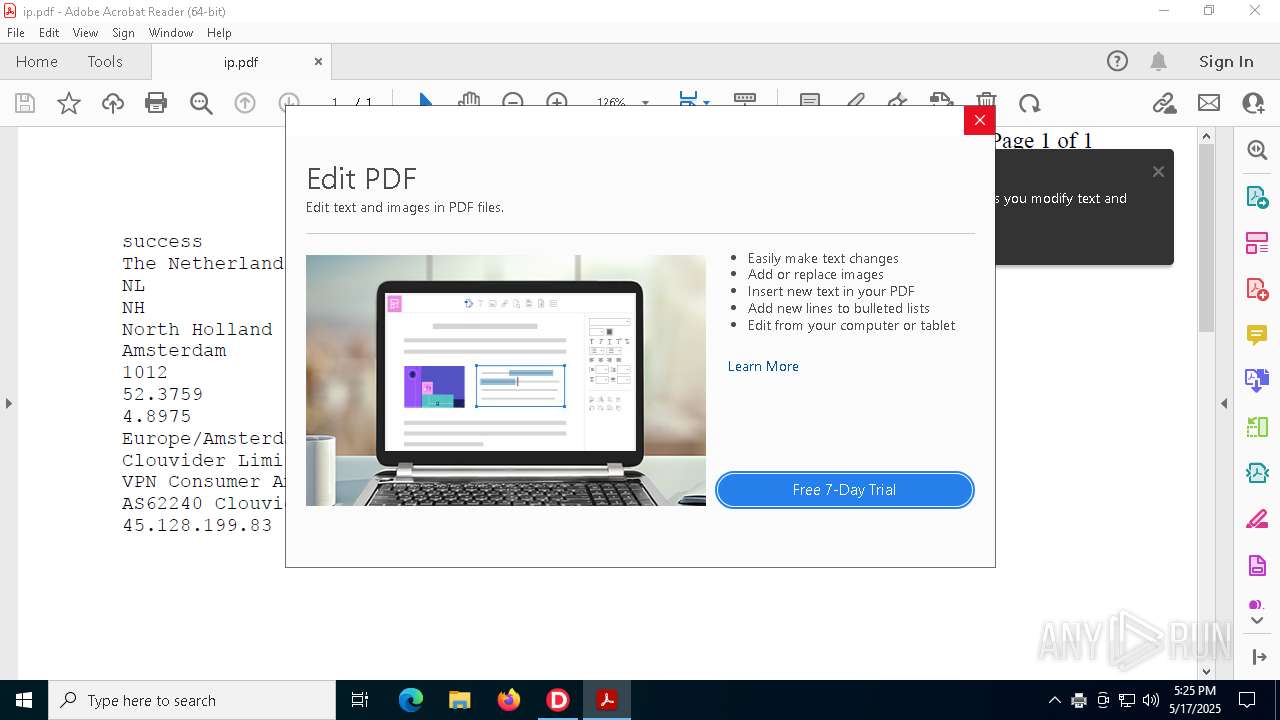
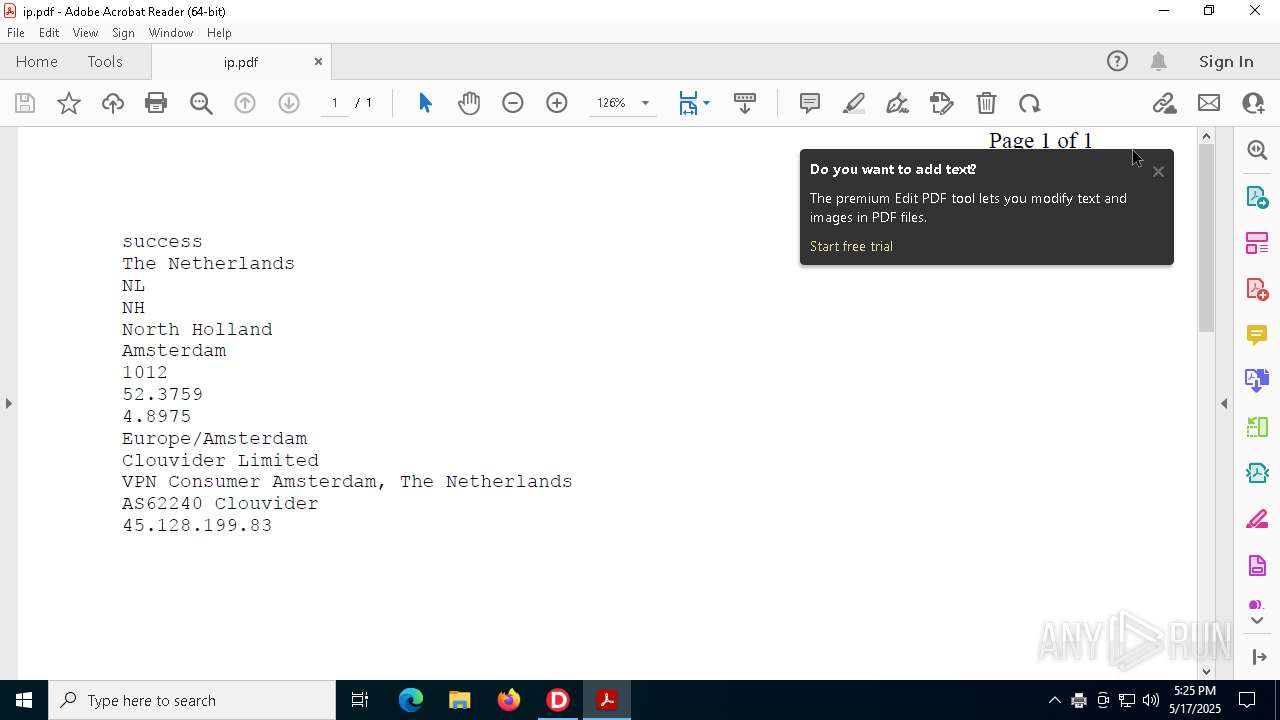
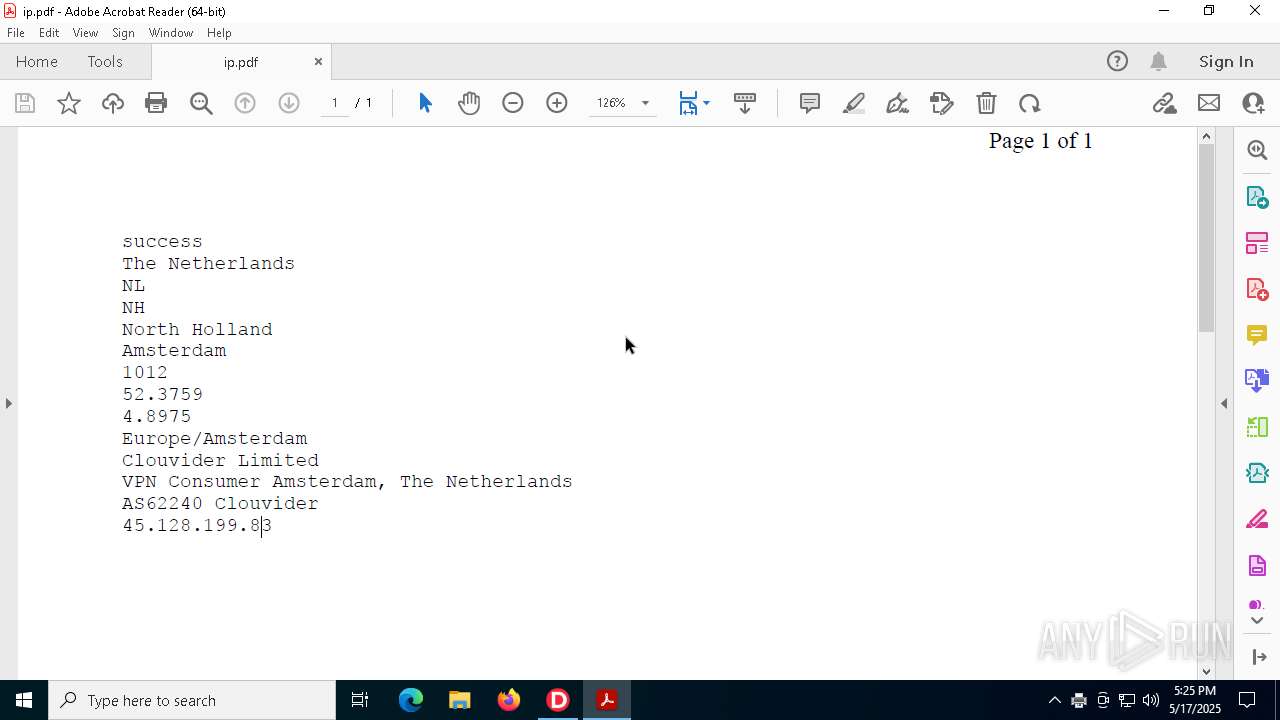
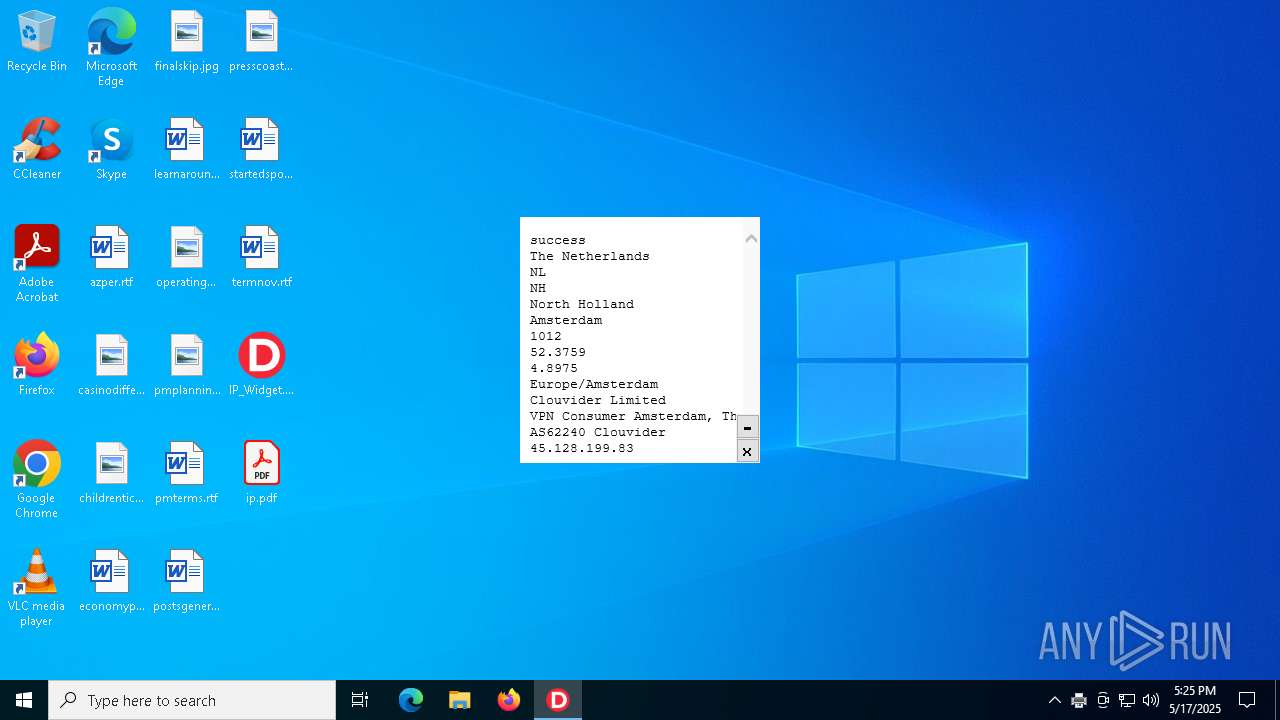
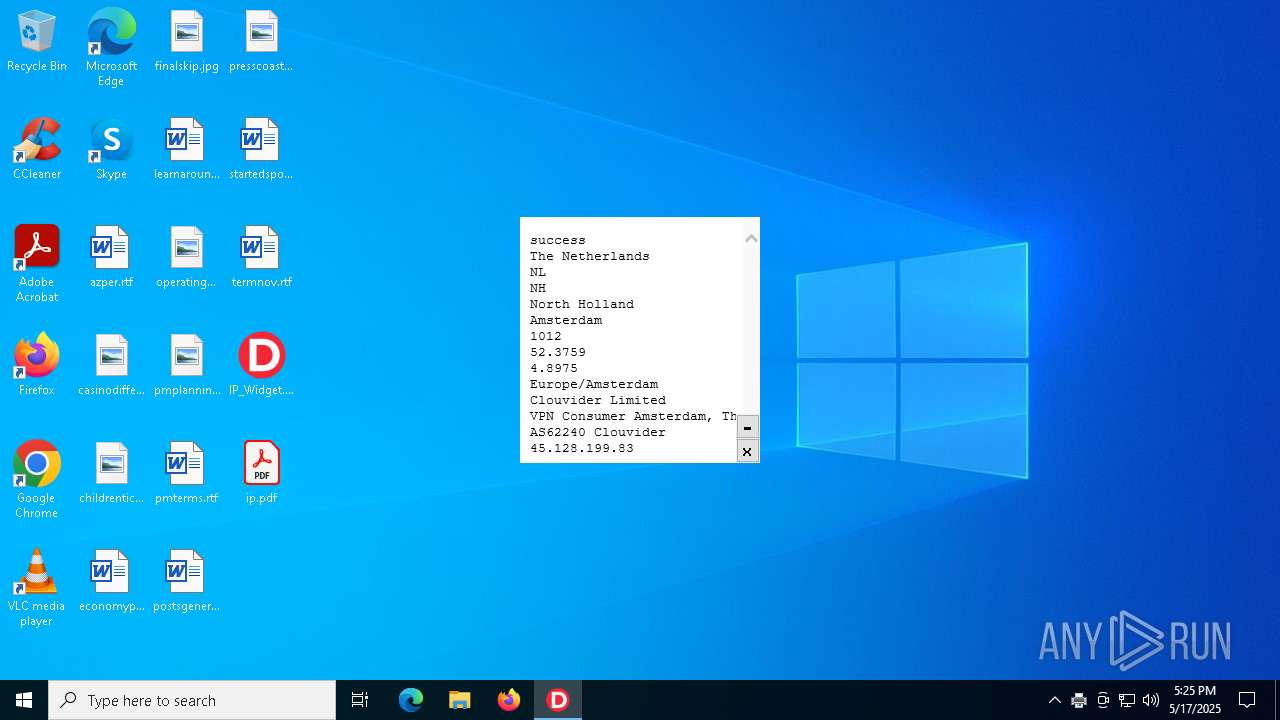
2320 | IP_Widget.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1164 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1164 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2320 | IP_Widget.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
2320 | IP_Widget.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
2320 | IP_Widget.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
2320 | IP_Widget.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.27:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2320 | IP_Widget.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ip-api.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2320 | IP_Widget.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |