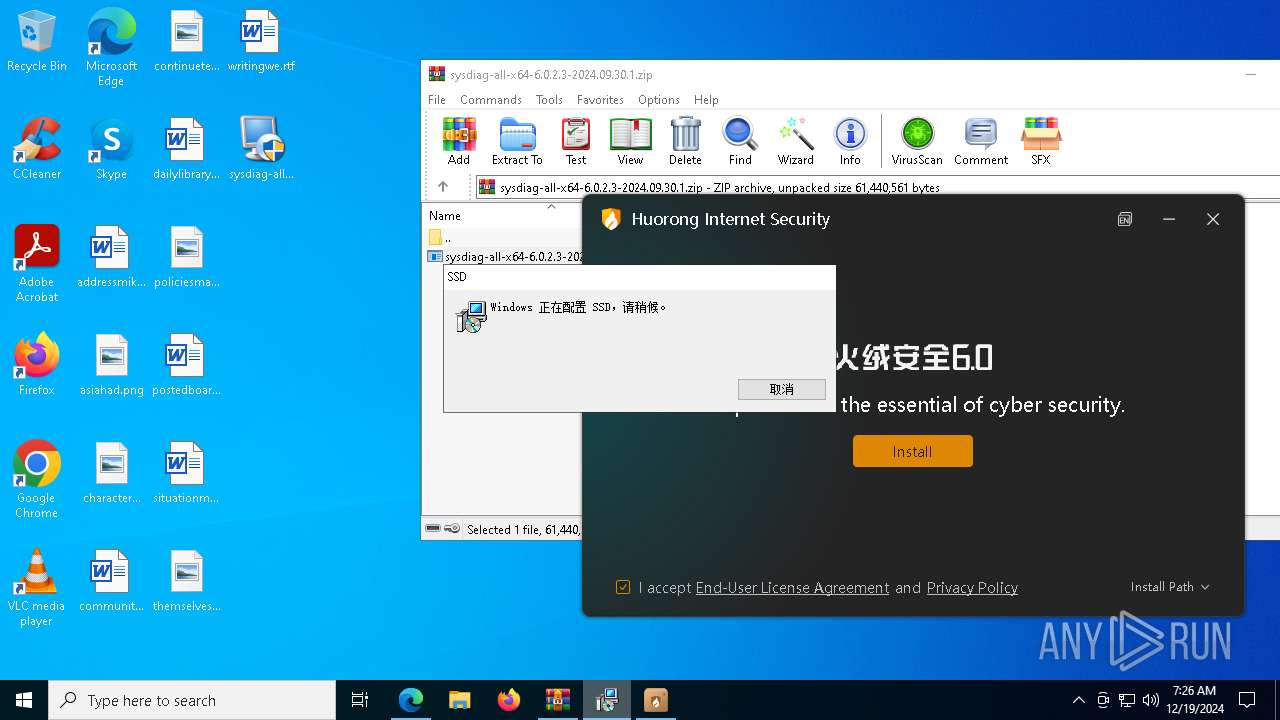
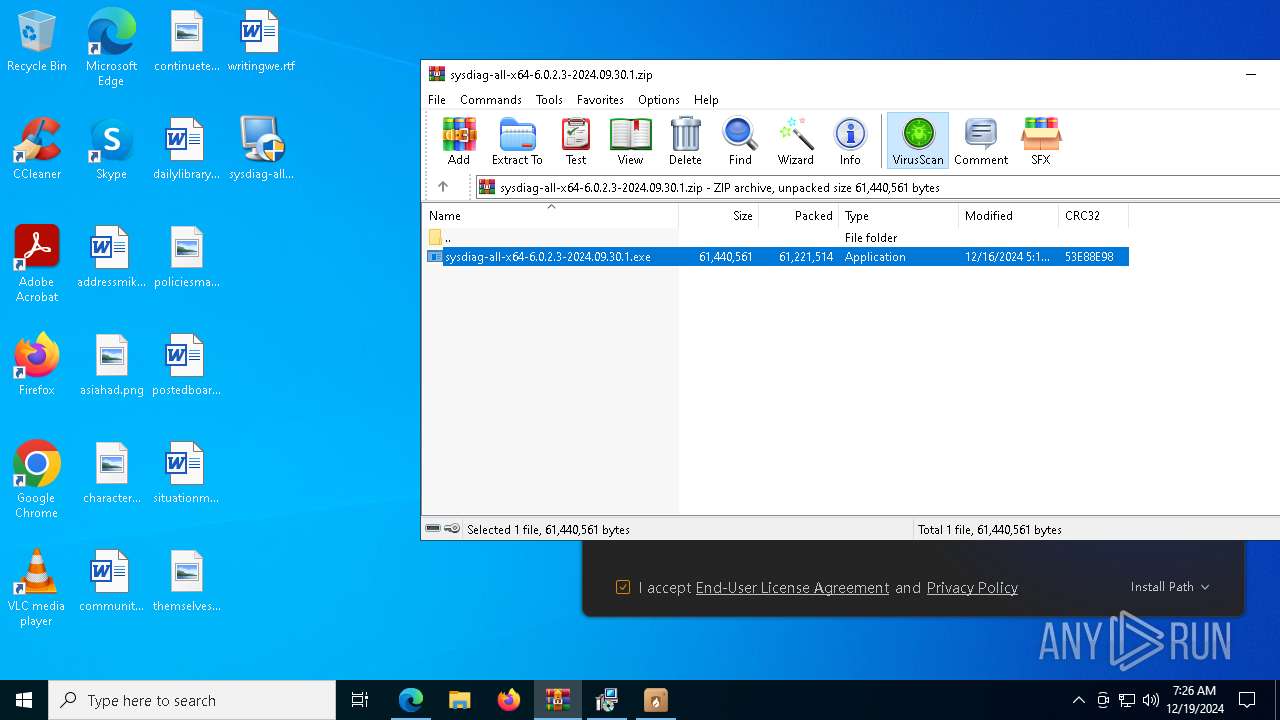
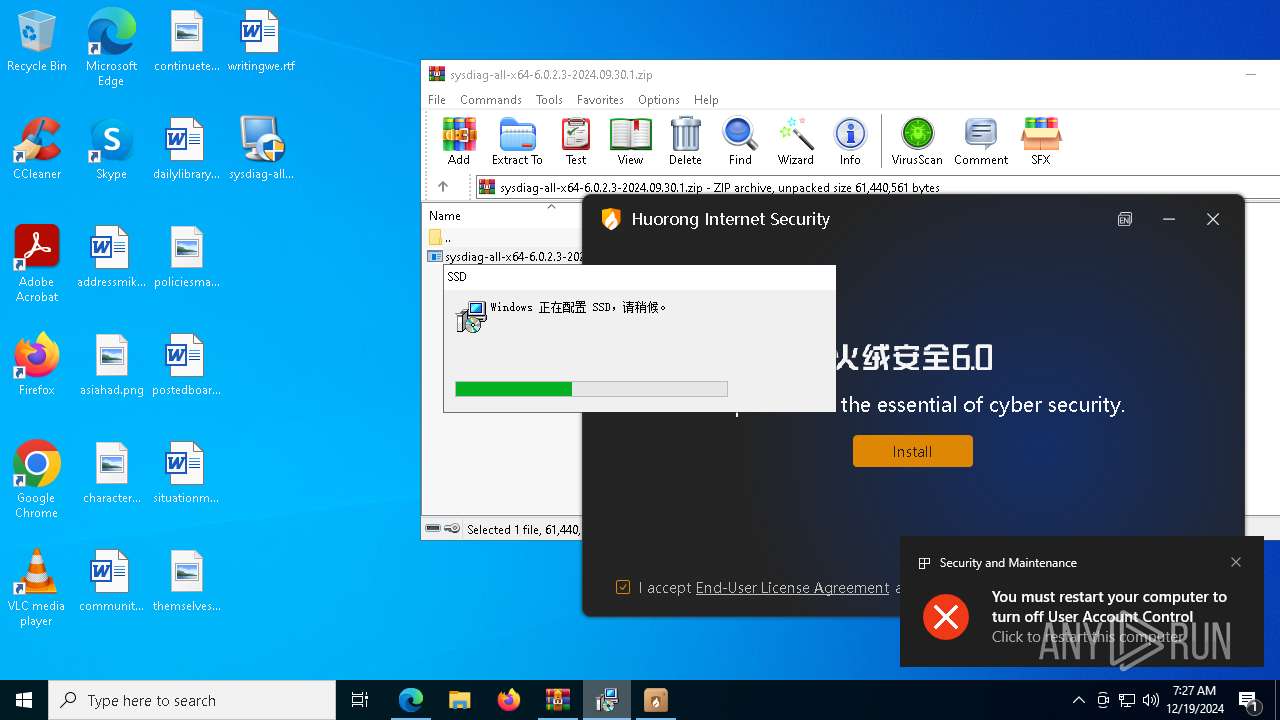
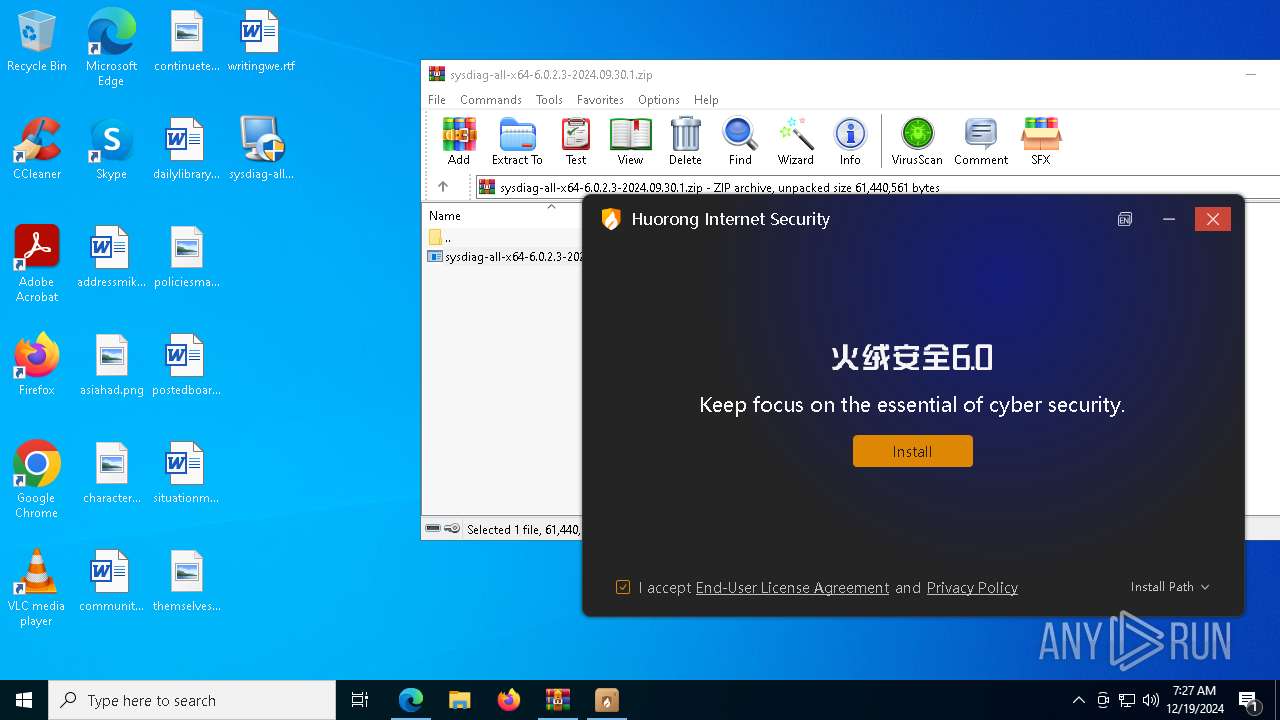
| URL: | https://huorong.work/ |
| Full analysis: | https://app.any.run/tasks/6d6c44e8-81f9-47f3-8b20-695c0151ea1e |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2024, 07:25:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FE85F302D93874780C0BFCCB3D378870 |
| SHA1: | 1391073D176F065C65328F5057137987C9E5D542 |
| SHA256: | BD735403F24BC9CEF8E54D7AE5E827DCF6CCBFC1F8E7385BA3BD94F05F7628E5 |
| SSDEEP: | 3:N8sMQCjn:2sSn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
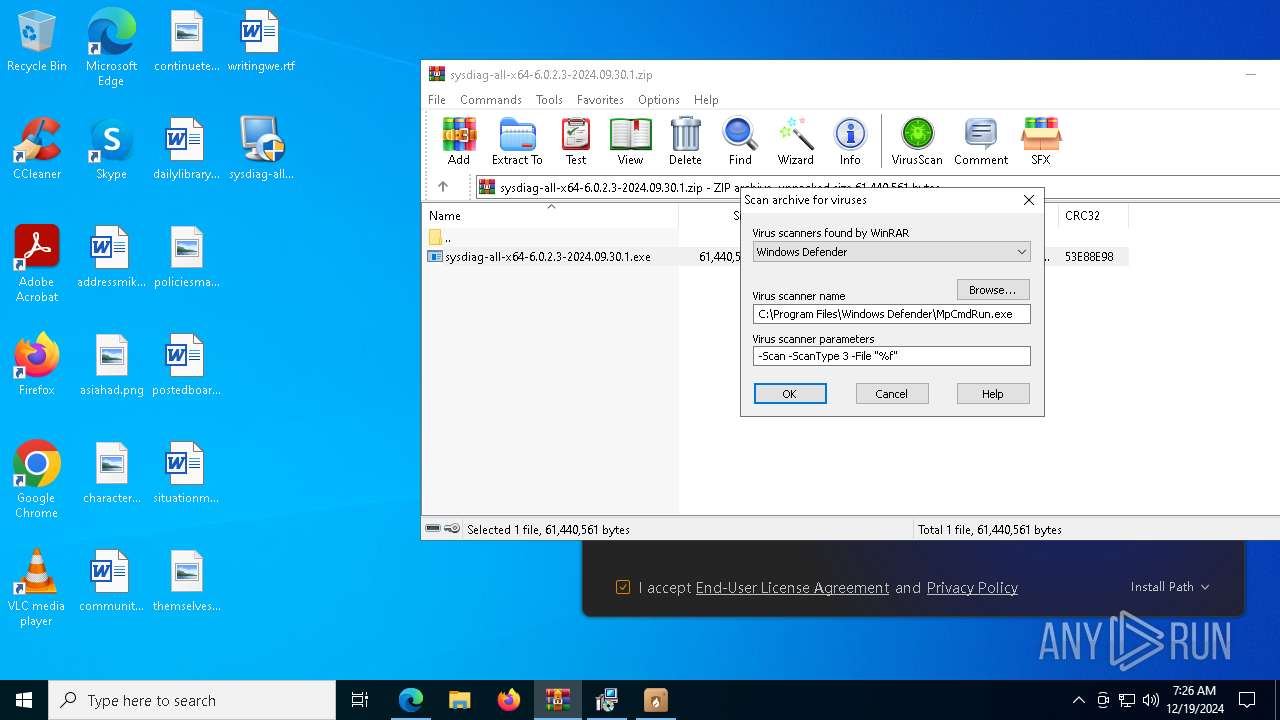
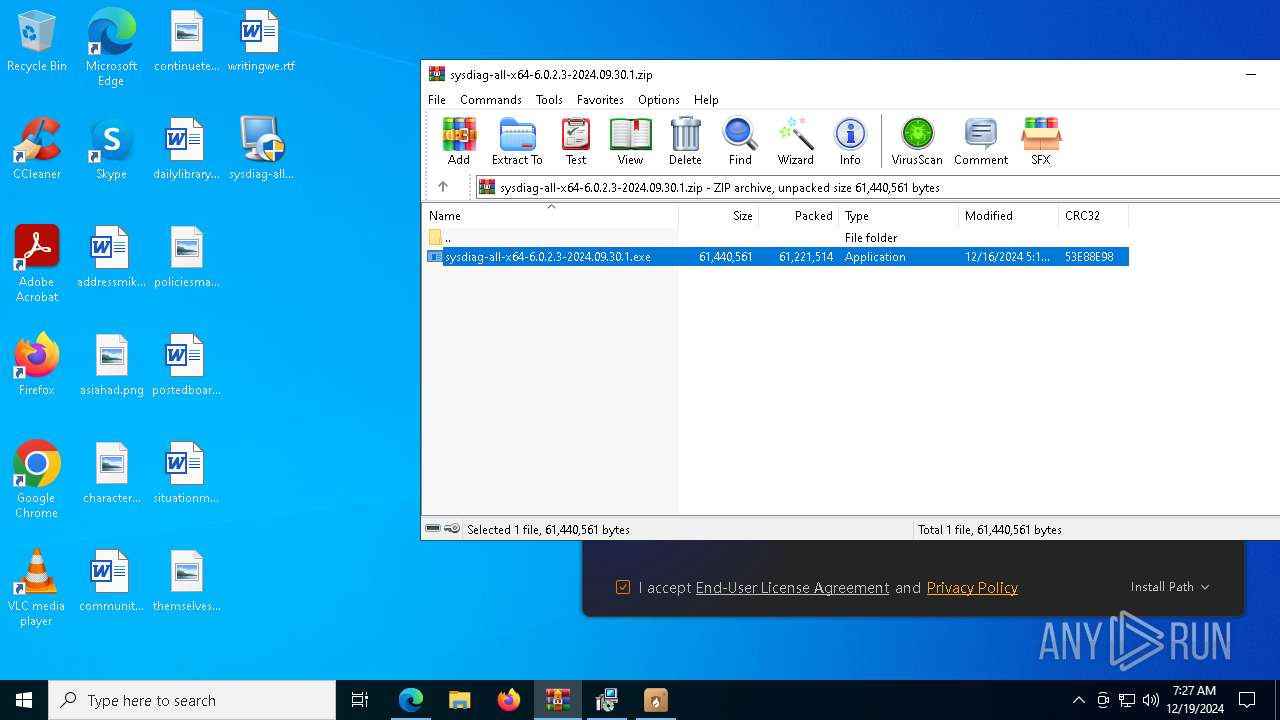
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 2600)
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 7440)
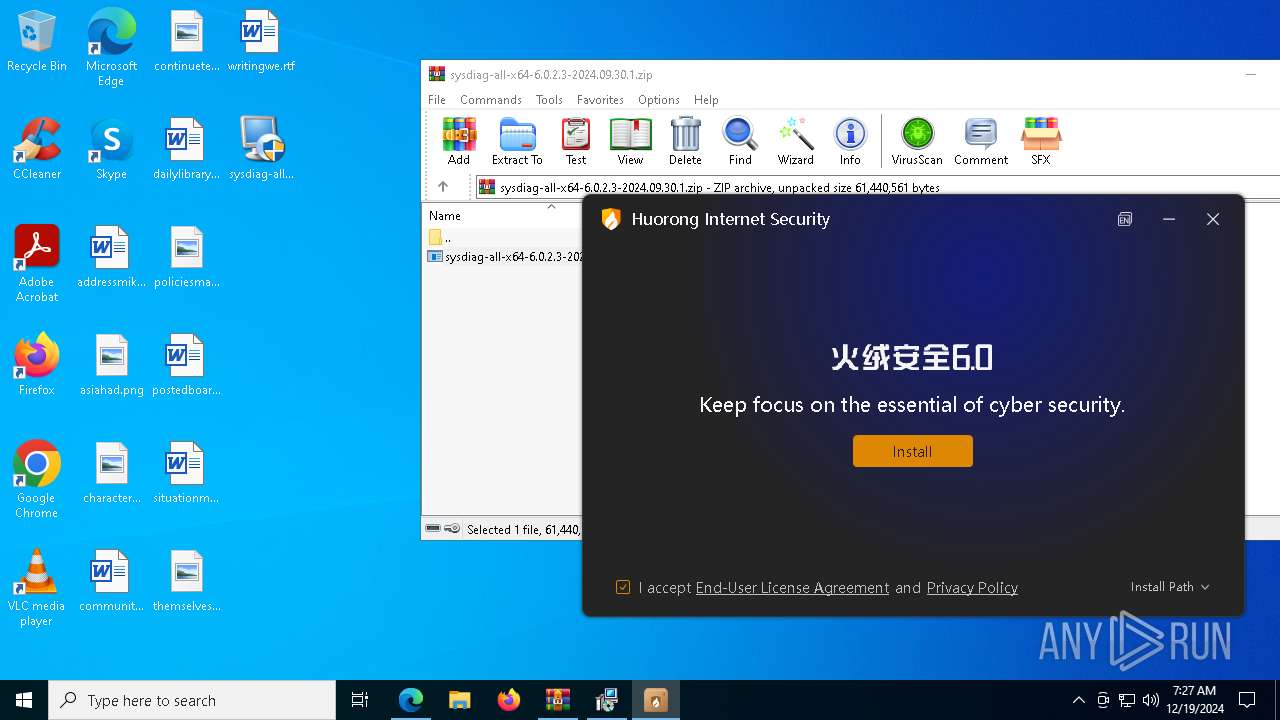
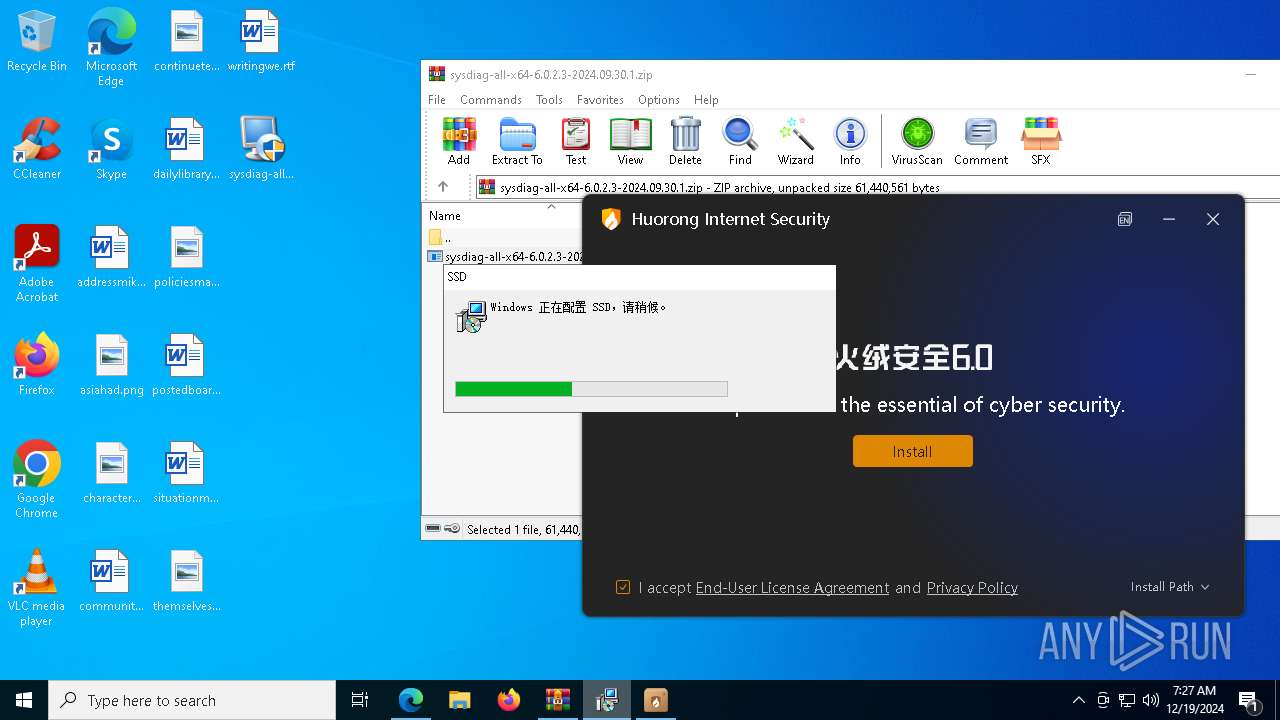
- MSIBDF4.tmp (PID: 1944)
- cmd.exe (PID: 1144)
- HttpDownloaderUI.exe (PID: 7784)
Reads security settings of Internet Explorer
- irsetup.exe (PID: 5252)
- MSIBDF4.tmp (PID: 1944)
Searches for installed software
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 7440)
Malware-specific behavior (creating "System.dll" in Temp)
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 7440)
Executes as Windows Service
- VSSVC.exe (PID: 1920)
Mutex name with non-standard characters
- MSIBDF4.tmp (PID: 1944)
- HttpDownloaderUI.exe (PID: 7784)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2904)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 8012)
- cmd.exe (PID: 4036)
Suspicious use of NETSH.EXE
- MSIBDF4.tmp (PID: 1944)
Executing commands from a ".bat" file
- MSIBDF4.tmp (PID: 1944)
Process drops legitimate windows executable
- MSIBDF4.tmp (PID: 1944)
- HttpDownloaderUI.exe (PID: 7784)
The process drops C-runtime libraries
- MSIBDF4.tmp (PID: 1944)
- HttpDownloaderUI.exe (PID: 7784)
Starts CMD.EXE for commands execution
- HttpDownloaderUI.exe (PID: 7784)
- MSIBDF4.tmp (PID: 1944)
Connects to unusual port
- HttpDownloaderUI.exe (PID: 7784)
INFO
Application launched itself
- msedge.exe (PID: 6464)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6464)
Checks supported languages
- identity_helper.exe (PID: 8132)
- irsetup.exe (PID: 5252)
- msiexec.exe (PID: 8168)
Reads Environment values
- identity_helper.exe (PID: 8132)
Reads the computer name
- identity_helper.exe (PID: 8132)
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 2600)
- irsetup.exe (PID: 5252)
- msiexec.exe (PID: 8168)
- MSIBDF4.tmp (PID: 1944)
The process uses the downloaded file
- WinRAR.exe (PID: 4908)
- msedge.exe (PID: 6464)
- MSIBDF4.tmp (PID: 1944)
Manual execution by a user
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 2600)
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 1200)
The sample compiled with english language support
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 2600)
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 7440)
- msiexec.exe (PID: 8168)
- MSIBDF4.tmp (PID: 1944)
- HttpDownloaderUI.exe (PID: 7784)
Creates files or folders in the user directory
- irsetup.exe (PID: 5252)
- MSIBDF4.tmp (PID: 1944)
Process checks computer location settings
- irsetup.exe (PID: 5252)
Create files in a temporary directory
- sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe (PID: 7440)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8168)
Manages system restore points
- SrTasks.exe (PID: 5964)
Starts application with an unusual extension
- msiexec.exe (PID: 8168)
Creates files in the program directory
- MSIBDF4.tmp (PID: 1944)
The sample compiled with chinese language support
- cmd.exe (PID: 1144)
- HttpDownloaderUI.exe (PID: 7784)
- MSIBDF4.tmp (PID: 1944)
Reads security settings of Internet Explorer
- mmc.exe (PID: 4360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
208
Monitored processes
73
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | "C:\Windows\System32\cmd.exe" /c copy /b C:\ProgramData\r4wKA\Q74pf~ww\p+C:\ProgramData\r4wKA\Q74pf~ww\w C:\ProgramData\r4wKA\Q74pf~ww\HttpDownloader.dll | C:\Windows\System32\cmd.exe | MSIBDF4.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Users\admin\Desktop\sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe" | C:\Users\admin\Desktop\sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Application Exit code: 3221226540 Version: 9.1.0.0 Modules
| |||||||||||||||
| 1920 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "C:\WINDOWS\Installer\MSIBDF4.tmp" | C:\Windows\Installer\MSIBDF4.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7608 --field-trial-handle=2248,i,16816617027783994810,9386572361125631950,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\Desktop\sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe" | C:\Users\admin\Desktop\sysdiag-all-x64-6.0.2.3-2024.09.30.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.1.0.0 Modules
| |||||||||||||||
| 2904 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\AppData\Roaming\7eeM8.bat" | C:\Windows\System32\cmd.exe | MSIBDF4.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4784 --field-trial-handle=2248,i,16816617027783994810,9386572361125631950,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
15 529
Read events
15 227
Write events
285
Delete events
17
Modification events
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 75873CB830882F00 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 410D64B830882F00 | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262894 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B9A1686A-EFB6-4ED3-9912-FAD128122956} | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262894 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F0733B92-D82E-4EC0-B4C7-EF872DC9961A} | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262894 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D16B4EF8-A404-4E89-ACBD-0741CF87878C} | |||
| (PID) Process: | (6464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262894 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5ABF1F65-F7ED-49AF-B345-AC247365F32E} | |||
Executable files
33
Suspicious files
151
Text files
51
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135d17.TMP | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135d17.TMP | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135d17.TMP | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135d17.TMP | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135d27.TMP | — | |
MD5:— | SHA256:— | |||
| 6464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
78
DNS requests
65
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4864 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4864 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7544 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7544 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5268 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2eeaf090-5e0c-4020-a0d8-58ab3721c1c6?P1=1735115424&P2=404&P3=2&P4=iuCL4DeW%2f0a6VqPaYy%2baqM4STNTW21oqgduGD6ItKOkqtIE6kW9AK76U4bG8mH2NCcywVrrZdc40H3SgLjhhAQ%3d%3d | unknown | — | — | whitelisted |
6264 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3700 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
huorong.work |
| unknown |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6768 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6768 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6768 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6768 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
7784 | HttpDownloaderUI.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
7784 | HttpDownloaderUI.exe | Generic Protocol Command Decode | SURICATA HTTP Request line incomplete |