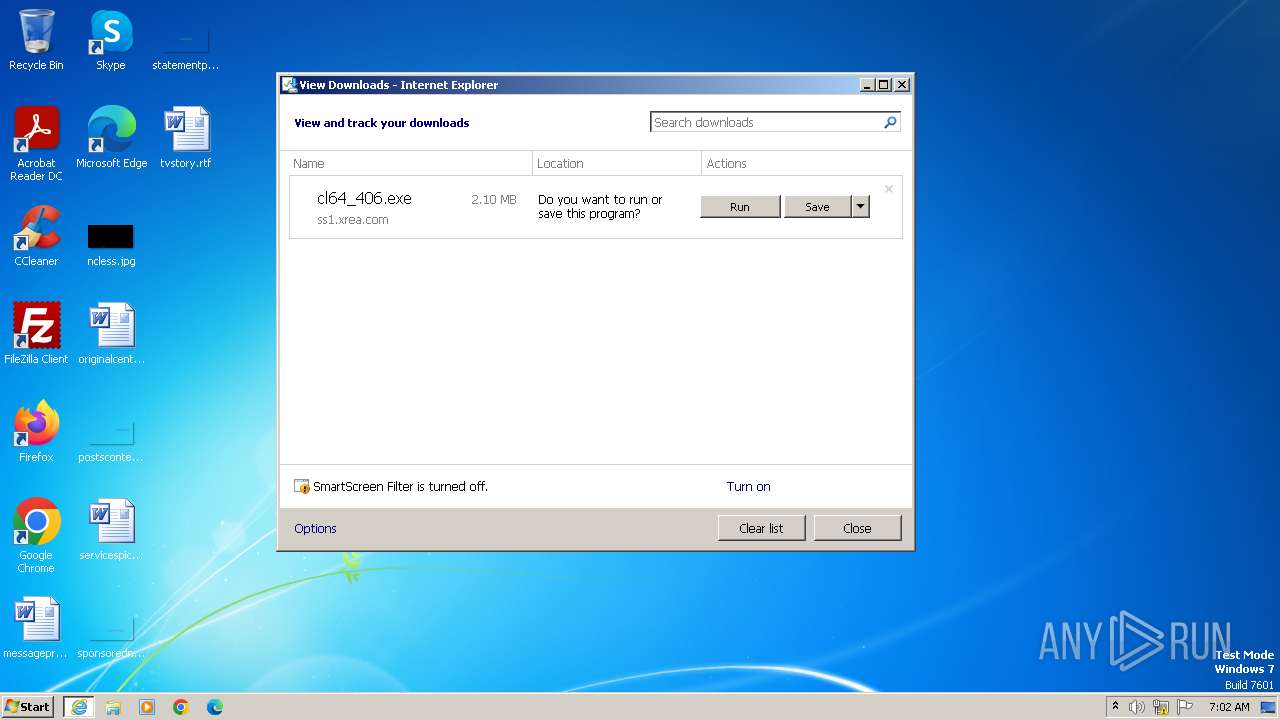
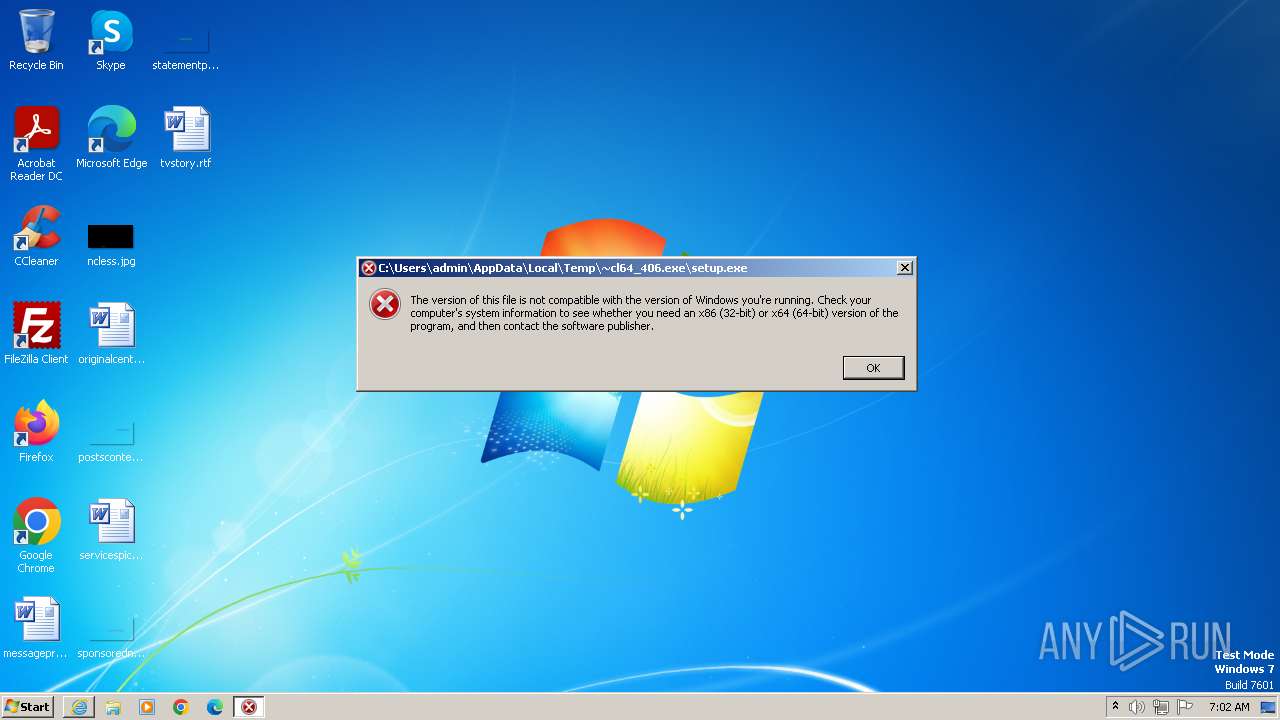
| URL: | https://ss1.xrea.com/pyonkichi.g1.xrea.com/archives/cl64_406.exe |
| Full analysis: | https://app.any.run/tasks/17bfd165-6d98-4551-a4db-a64e989930d5 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2023, 07:01:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B2BCFFECBD9FBF7E591920B3735D441E |
| SHA1: | 8ECD76D138670295EF6770B4BBB1FE5C31E9135C |
| SHA256: | BD6C4A6915738B7FF8FB29B1B5F829F602BA0AECDB7E6715FE4817E4C431665E |
| SSDEEP: | 3:N8buSKLO+LbVdMrR7C:2rb0bVdMY |
MALICIOUS
Drops the executable file immediately after the start
- cl64_406.exe (PID: 2868)
SUSPICIOUS
Reads the Internet Settings
- cl64_406.exe (PID: 2868)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 2480)
- iexplore.exe (PID: 564)
Checks supported languages
- wmpnscfg.exe (PID: 1128)
- cl64_406.exe (PID: 2868)
Manual execution by a user
- wmpnscfg.exe (PID: 1128)
Application launched itself
- iexplore.exe (PID: 564)
Reads the computer name
- wmpnscfg.exe (PID: 1128)
- cl64_406.exe (PID: 2868)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1128)
Create files in a temporary directory
- cl64_406.exe (PID: 2868)
The process uses the downloaded file
- iexplore.exe (PID: 564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://ss1.xrea.com/pyonkichi.g1.xrea.com/archives/cl64_406.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:564 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe | iexplore.exe | ||||||||||||
User: admin Company: Pyonkichi Integrity Level: HIGH Description: CLaunch Program Launcher Exit code: 4294967295 Version: 4, 0, 6, 0 Modules
| |||||||||||||||
| 3868 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe | — | iexplore.exe | |||||||||||
User: admin Company: Pyonkichi Integrity Level: MEDIUM Description: CLaunch Program Launcher Exit code: 3221226540 Version: 4, 0, 6, 0 Modules
| |||||||||||||||
Total events
15 335
Read events
15 269
Write events
63
Delete events
3
Modification events
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (564) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
13
Suspicious files
16
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | binary | |
MD5:27CCEA2474DD93024F4CB1DF7521AAE6 | SHA256:229CB2B2C42F198F1110AB688C42017303D2F4101CC7139185E713E582F89717 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4B3D1CD03E2BE9D4F9CDDE390F5EFE31_635180BB000A93EDCBAF170C8AEE95C3 | binary | |
MD5:6AD9BC1D7A75D4153C63B9E47BD68087 | SHA256:6EBB4A80E2A1A61EE3644215CD6594963E0C8D40938BF47976730FC7092AB5F2 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\cl64_406[1].exe | executable | |
MD5:30370FF5962826135DEBC076F6A1081F | SHA256:14C6578AAF71EF0218DCBB36E67A489C2D3777427D44E42EDD75BDF08695D82F | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe.nfy394c.partial | executable | |
MD5:194937A572CB41A383BF46FAC6260001 | SHA256:16C7A291D2FCEDA4942A17BDEEF55AE34FD9DB781A18E4D43DFCB8F79D13E957 | |||
| 564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\cl64_406.exe.nfy394c.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_96EEC010953ED454BBCDFA69FC071E7C | binary | |
MD5:B0FB9F17C4E4A57799EF5FA24EEAFD67 | SHA256:D367186811F96E8DE2784B183E76D230DF3EA3C097D9A010985A68771404D1EE | |||
| 564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{33CD1C41-8E85-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:8BC356ED6F119D9447A3D80A5E39D782 | SHA256:24210C4FA7E6AA5CB0BE61F0390E86866CE38FA57505EABE3A183625D54E3B86 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9ADC56B56C00F142CEA5395D0C5DF9D3 | SHA256:CBEAC1E44089B11676AB8B1CFCACF2A18029DC592137B8173EC030FAD9286363 | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4B3D1CD03E2BE9D4F9CDDE390F5EFE31_635180BB000A93EDCBAF170C8AEE95C3 | binary | |
MD5:211D74A6ABB36023F164D5056F900AEB | SHA256:04BFE8A1277BBFDE71F0BCB84C88C267A628BA4B8D1BDADE252F2F7EF5FC1718 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
15
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 200 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?df5eacd0fb157a26 | unknown | compressed | 65.2 Kb | unknown |
564 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2480 | iexplore.exe | GET | 200 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0e152650b56312b4 | unknown | compressed | 4.66 Kb | unknown |
2480 | iexplore.exe | GET | 200 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e569524345d4d114 | unknown | compressed | 4.66 Kb | unknown |
2480 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEH1NQqkrQx1%2BZFPnwZqNWHc%3D | unknown | binary | 1.41 Kb | unknown |
1080 | svchost.exe | GET | 304 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?60b2f43ad8cf70d9 | unknown | — | — | unknown |
2480 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/alphasslcasha256g4/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSPdwLcDiHQXlVfp8h37hrpMerTggQUT8usqMLvq92Db2u%2Fzpg9XFgldhUCDHiDsZvjBwzqord9Jg%3D%3D | unknown | binary | 1.40 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2480 | iexplore.exe | 203.189.105.202:443 | ss1.xrea.com | GMO Internet,Inc | JP | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2480 | iexplore.exe | 8.248.131.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
2480 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
1080 | svchost.exe | 8.248.131.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
564 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
564 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ss1.xrea.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |