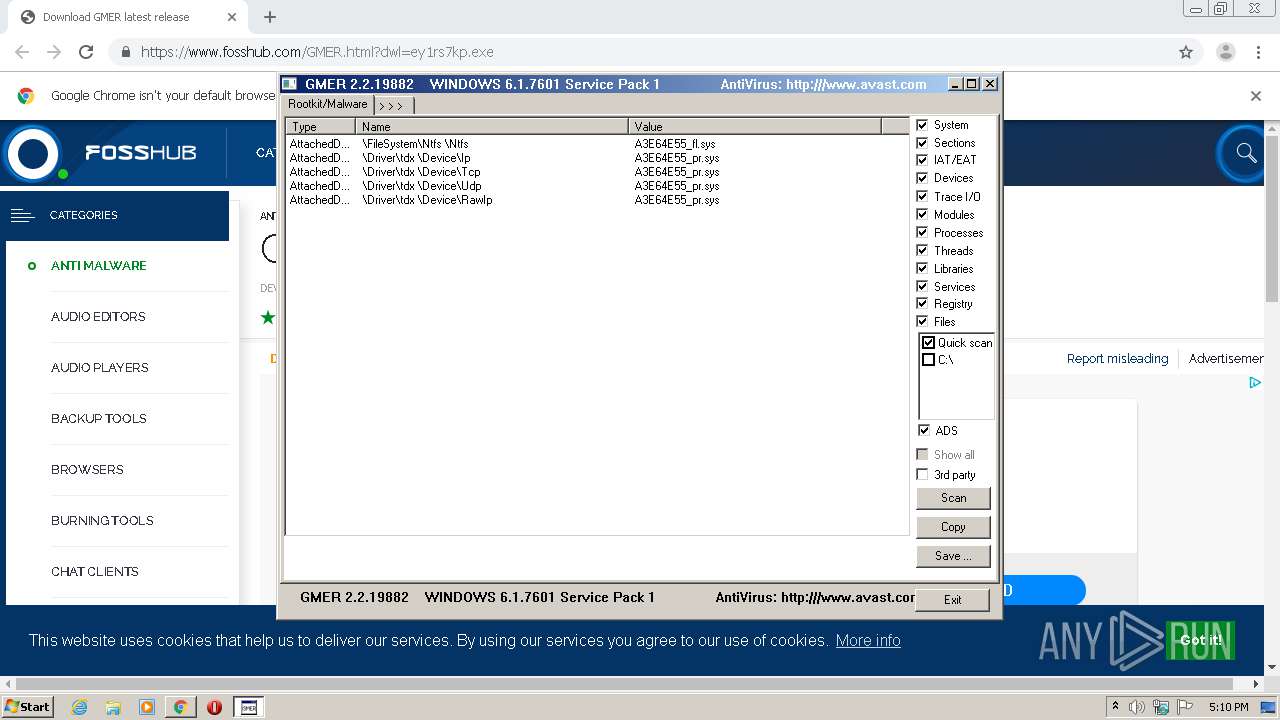
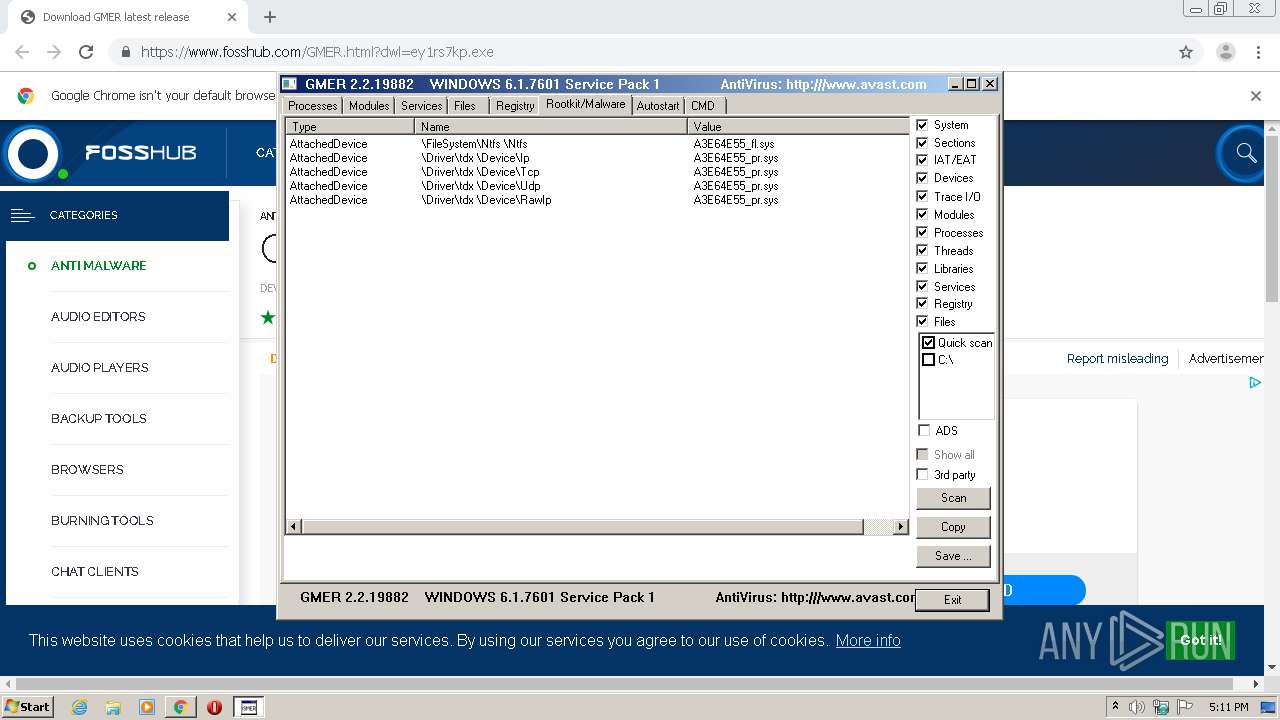
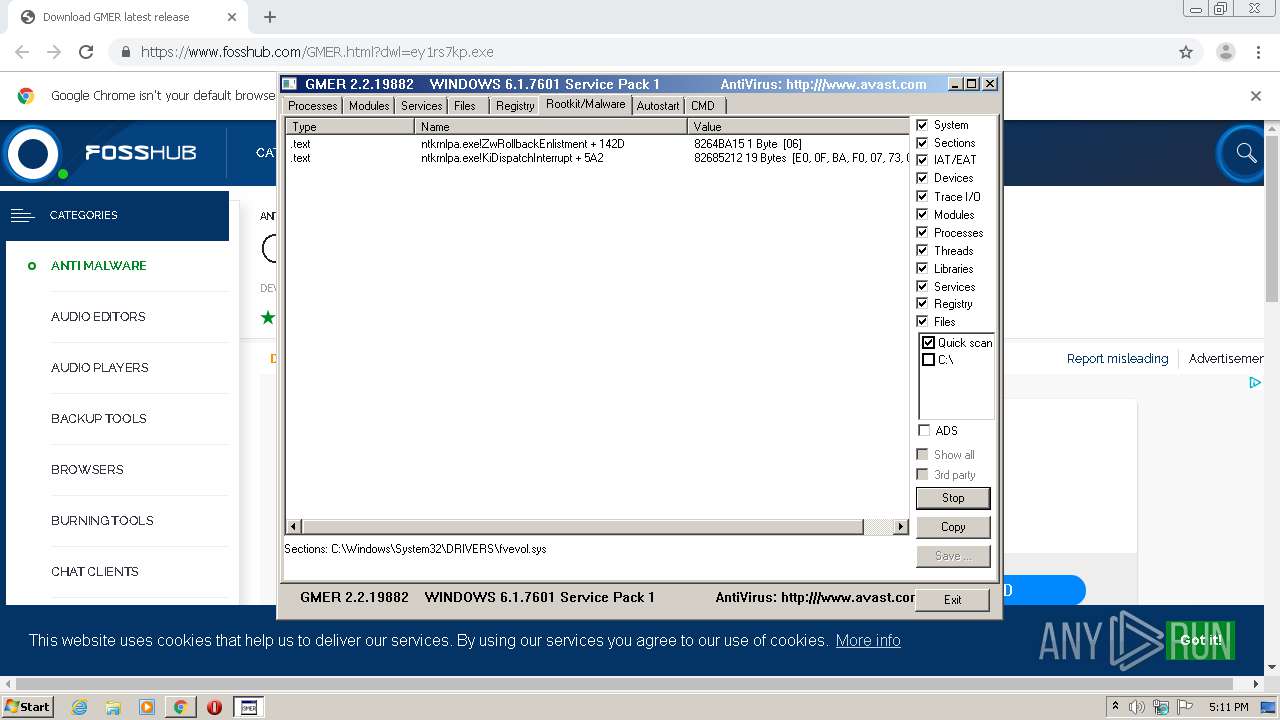
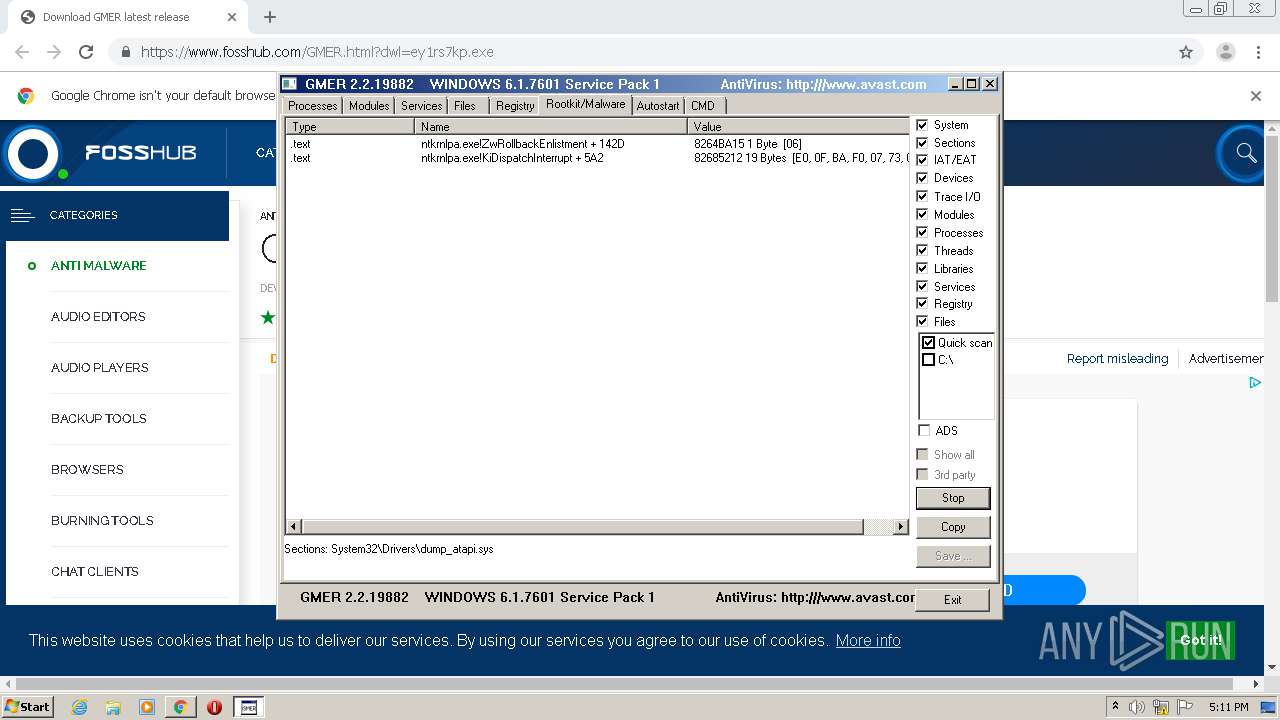
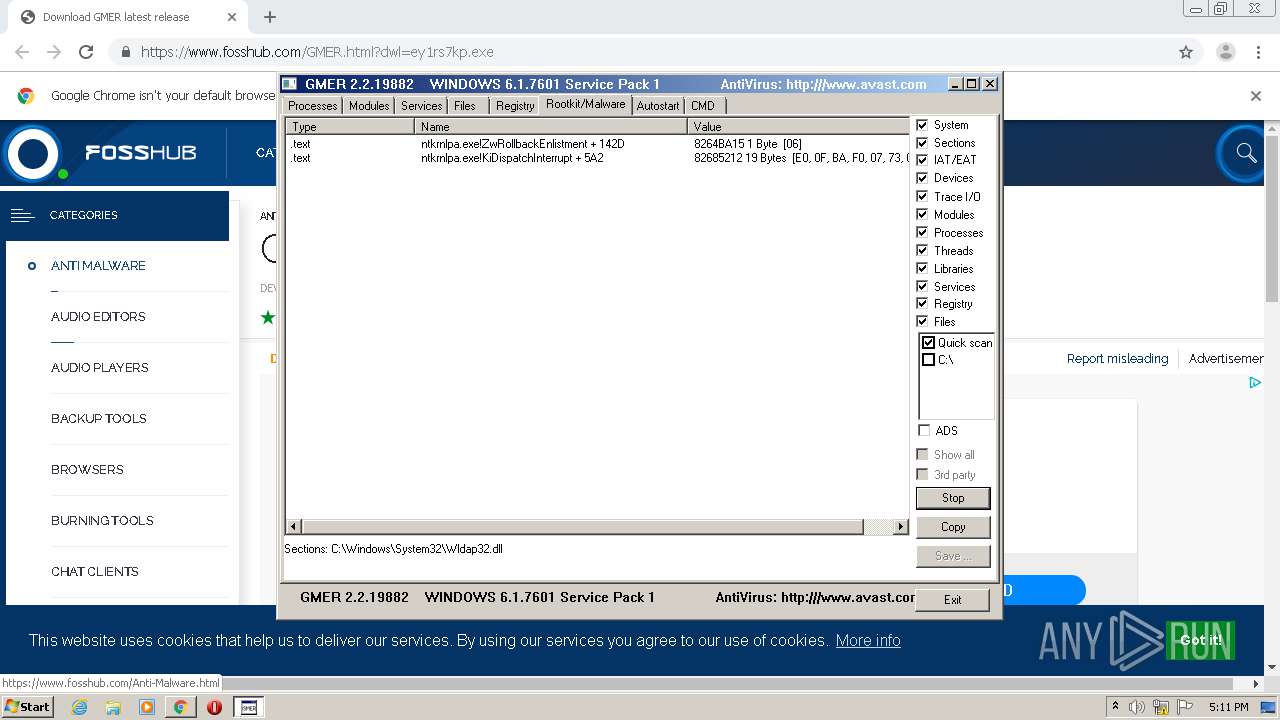
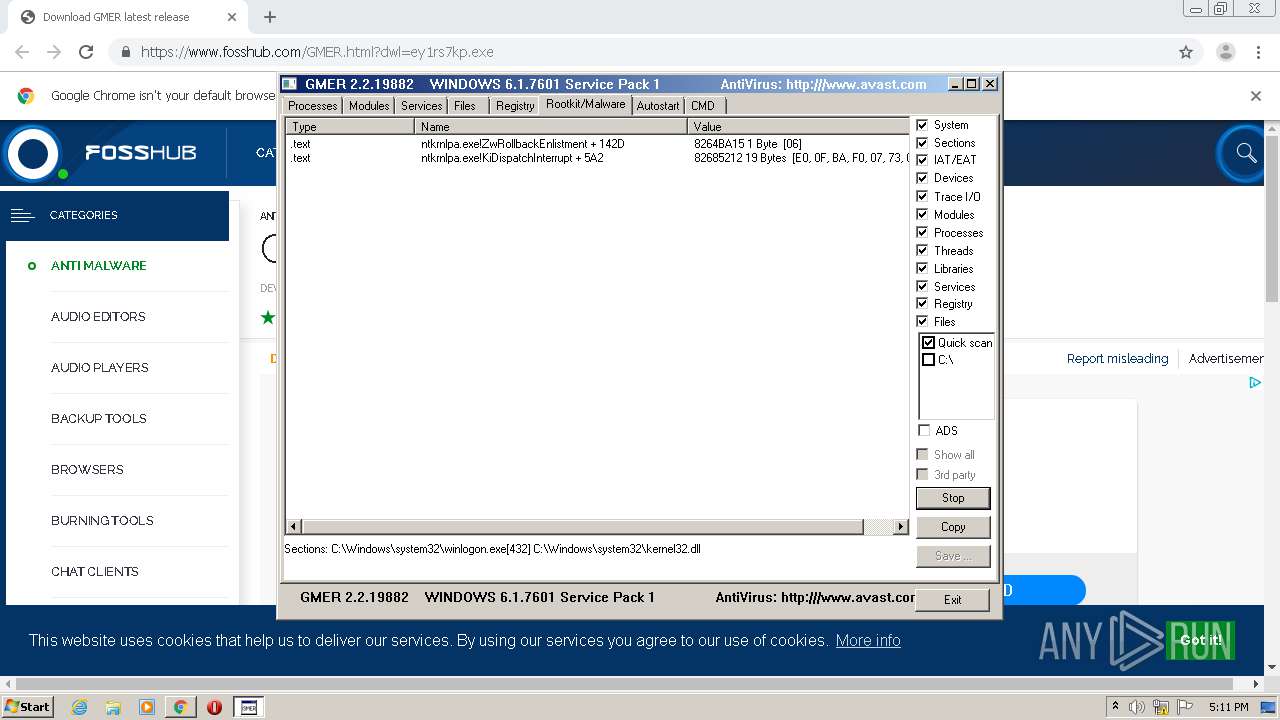
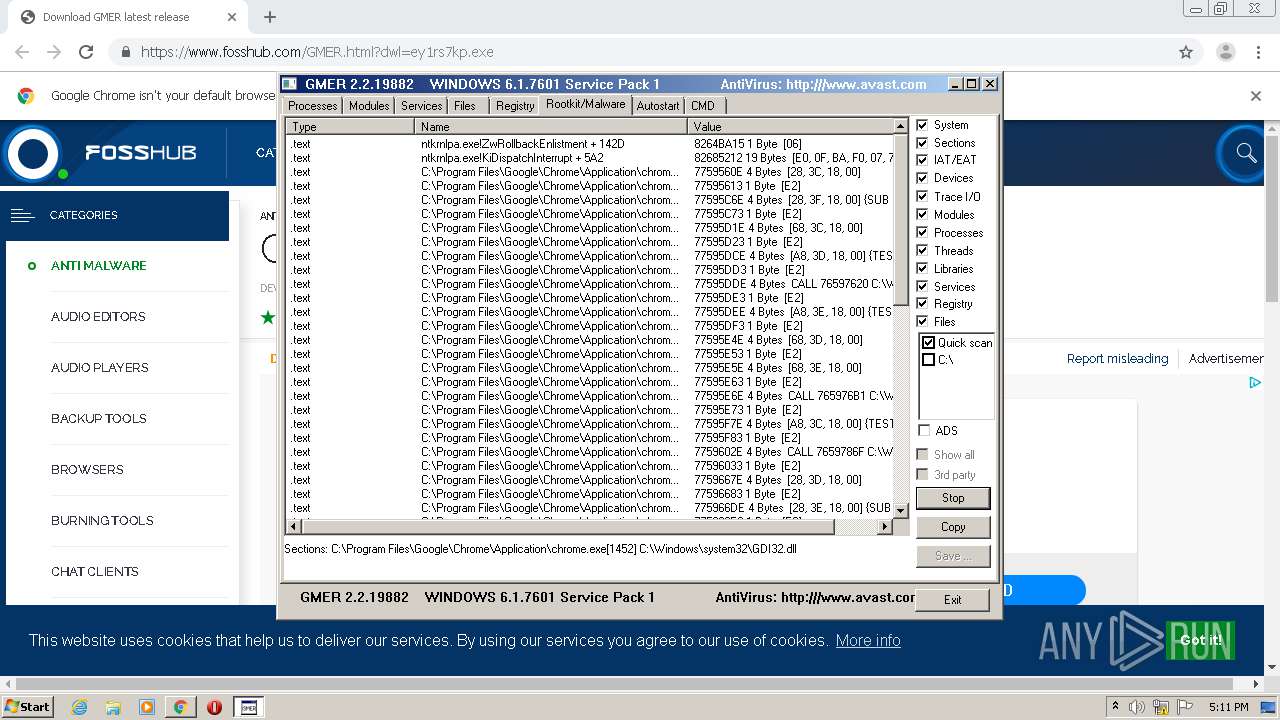
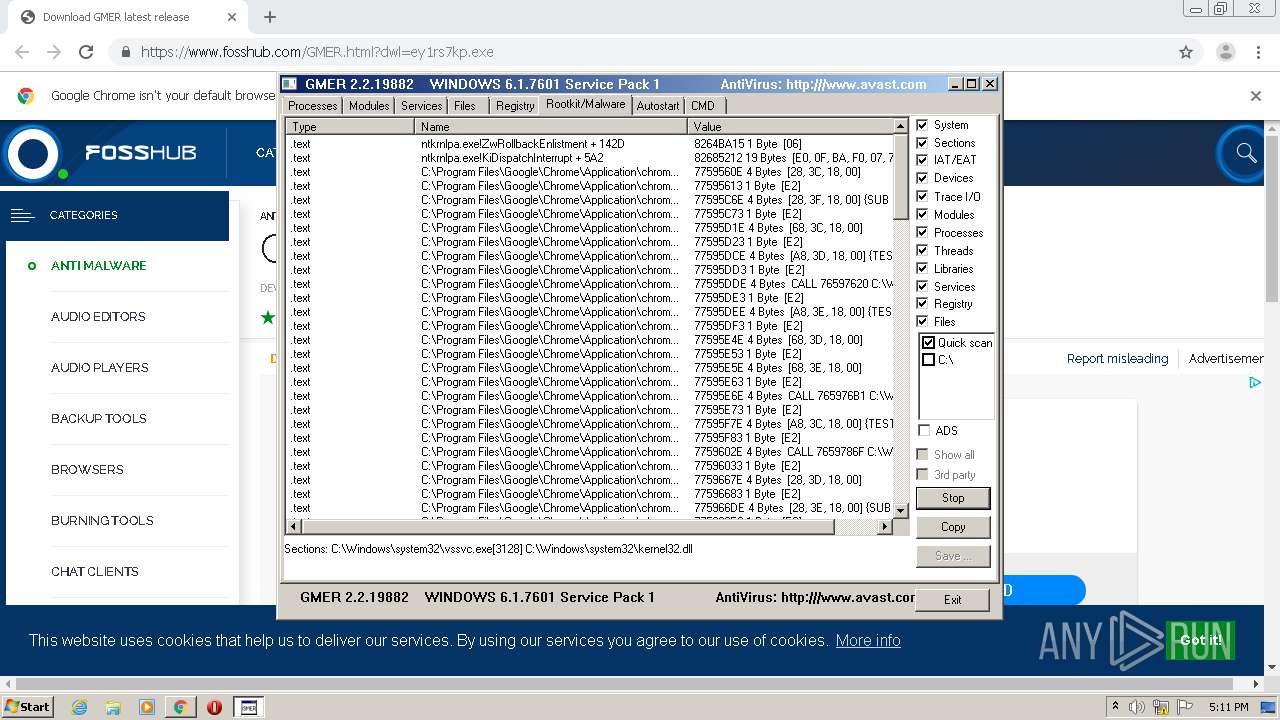
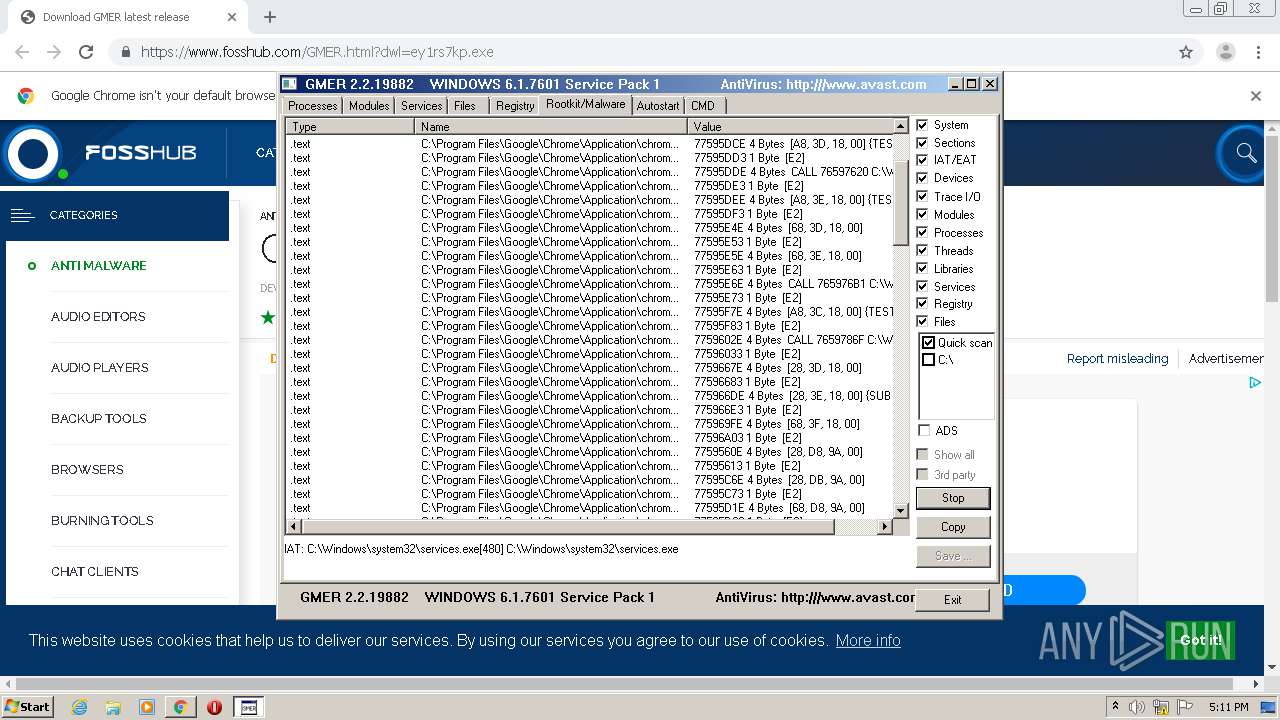
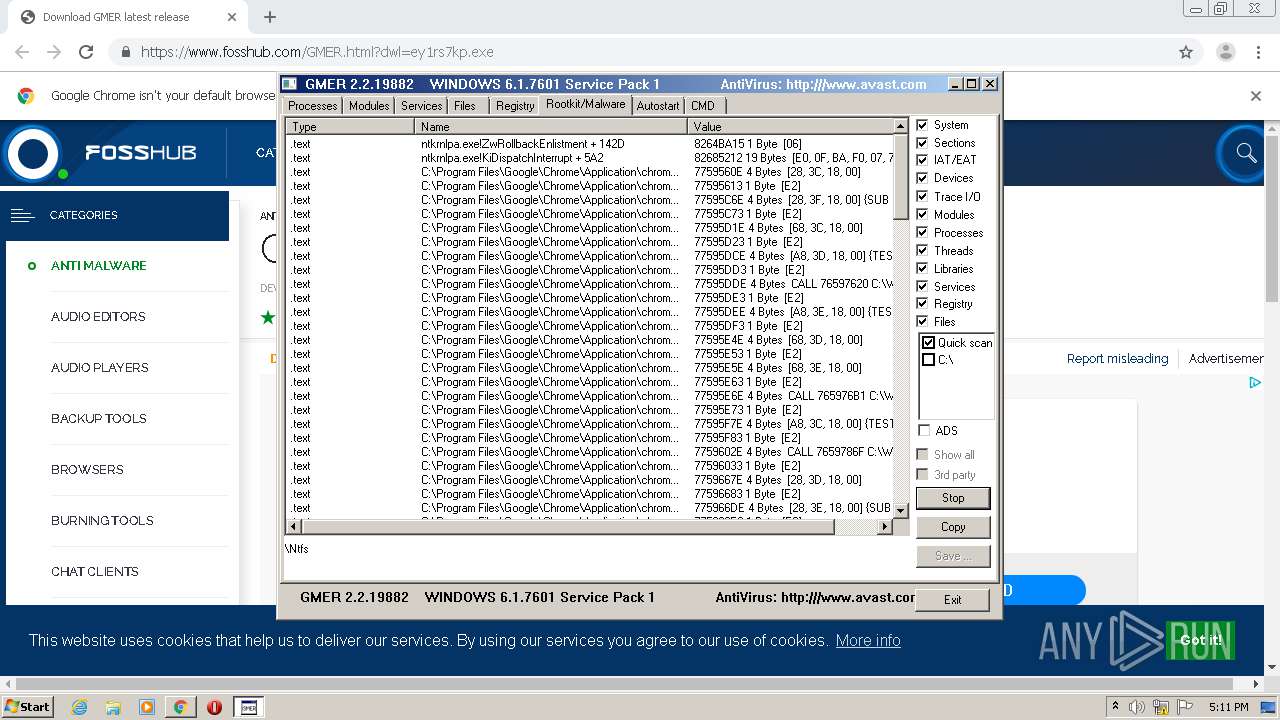
| URL: | https://www.fosshub.com/GMER.html?dwl=ey1rs7kp.exe |
| Full analysis: | https://app.any.run/tasks/3f6c5fd1-4456-4f01-82fa-d9b01cbc37ff |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2021, 16:10:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 94ADB3F7AEA9F0F4D3E48FC405B7C259 |
| SHA1: | 79721A883E00288C45E66CB152623B2766EA8AC7 |
| SHA256: | BD64B59C30D90C3A83F4621D952985D64265C4379B365E00FD2A4C7714D2682D |
| SSDEEP: | 3:N8DSLWWKS9YNRIYSFF6LAC:2OLWWzOwuLAC |
MALICIOUS
Application was dropped or rewritten from another process
- ey1rs7kp.exe (PID: 2352)
- ey1rs7kp.exe (PID: 2788)
Loads dropped or rewritten executable
- chrome.exe (PID: 1452)
- host.exe (PID: 320)
- chrome.exe (PID: 2408)
- chrome.exe (PID: 2420)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 2696)
- chrome.exe (PID: 3464)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 1696)
- ey1rs7kp.exe (PID: 2788)
- chrome.exe (PID: 3680)
- consent.exe (PID: 2500)
- chrome.exe (PID: 1420)
- WmiPrvSE.exe (PID: 2504)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 2388)
Changes settings of System certificates
- ey1rs7kp.exe (PID: 2788)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2420)
- ey1rs7kp.exe (PID: 2788)
Creates or modifies windows services
- ey1rs7kp.exe (PID: 2788)
Drops a file that was compiled in debug mode
- ey1rs7kp.exe (PID: 2788)
Adds / modifies Windows certificates
- ey1rs7kp.exe (PID: 2788)
Drops a file with too old compile date
- ey1rs7kp.exe (PID: 2788)
Low-level read access rights to disk partition
- ey1rs7kp.exe (PID: 2788)
INFO
Application launched itself
- chrome.exe (PID: 2420)
Reads the hosts file
- chrome.exe (PID: 2420)
- chrome.exe (PID: 1696)
Reads settings of System Certificates
- ey1rs7kp.exe (PID: 2788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "host.exe" | C:\Windows\system32\host.exe | — | srvpost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,3530488662524916537,11177196229263253025,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16763927147042775076 --mojo-platform-channel-handle=1072 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3530488662524916537,11177196229263253025,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10872128065377338382 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,3530488662524916537,11177196229263253025,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=7388555702185350623 --mojo-platform-channel-handle=1420 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3530488662524916537,11177196229263253025,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2965237918726015057 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3760 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
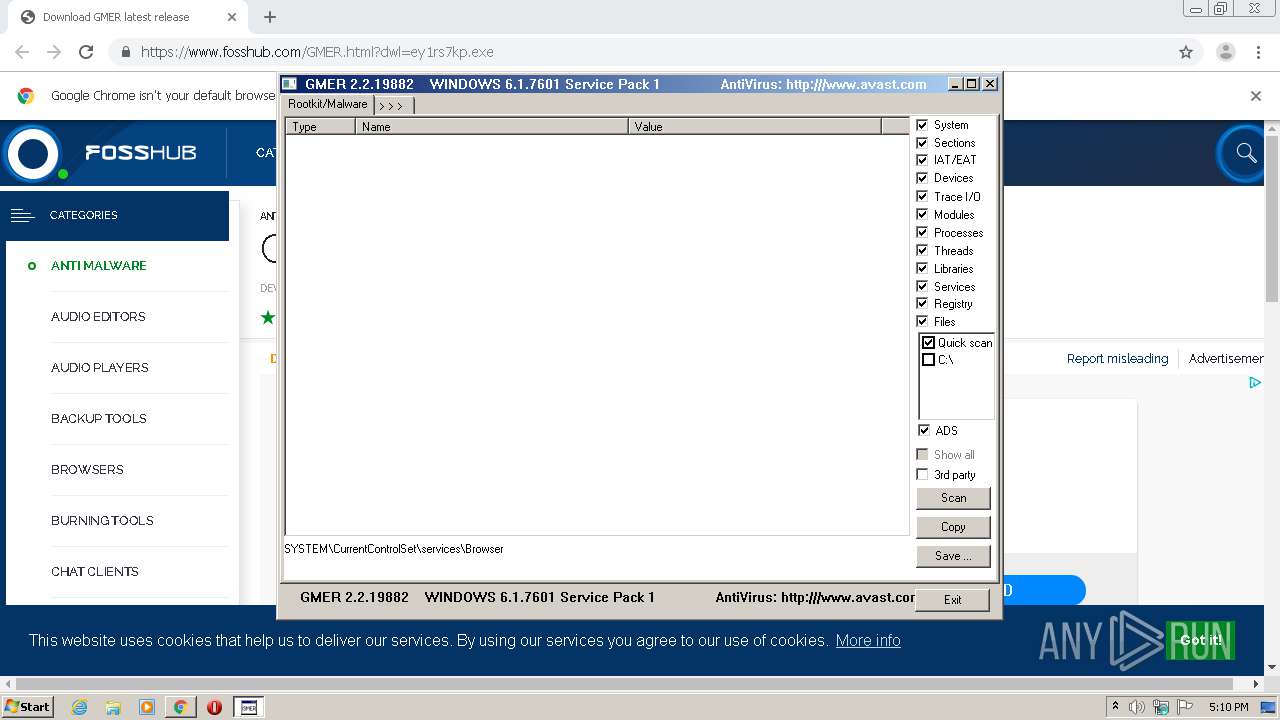
| 2352 | "C:\Users\admin\Downloads\ey1rs7kp.exe" | C:\Users\admin\Downloads\ey1rs7kp.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 2, 2, 19882 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,3530488662524916537,11177196229263253025,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13190231544734382288 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2180 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2180 --on-initialized-event-handle=316 --parent-handle=320 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://www.fosshub.com/GMER.html?dwl=ey1rs7kp.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
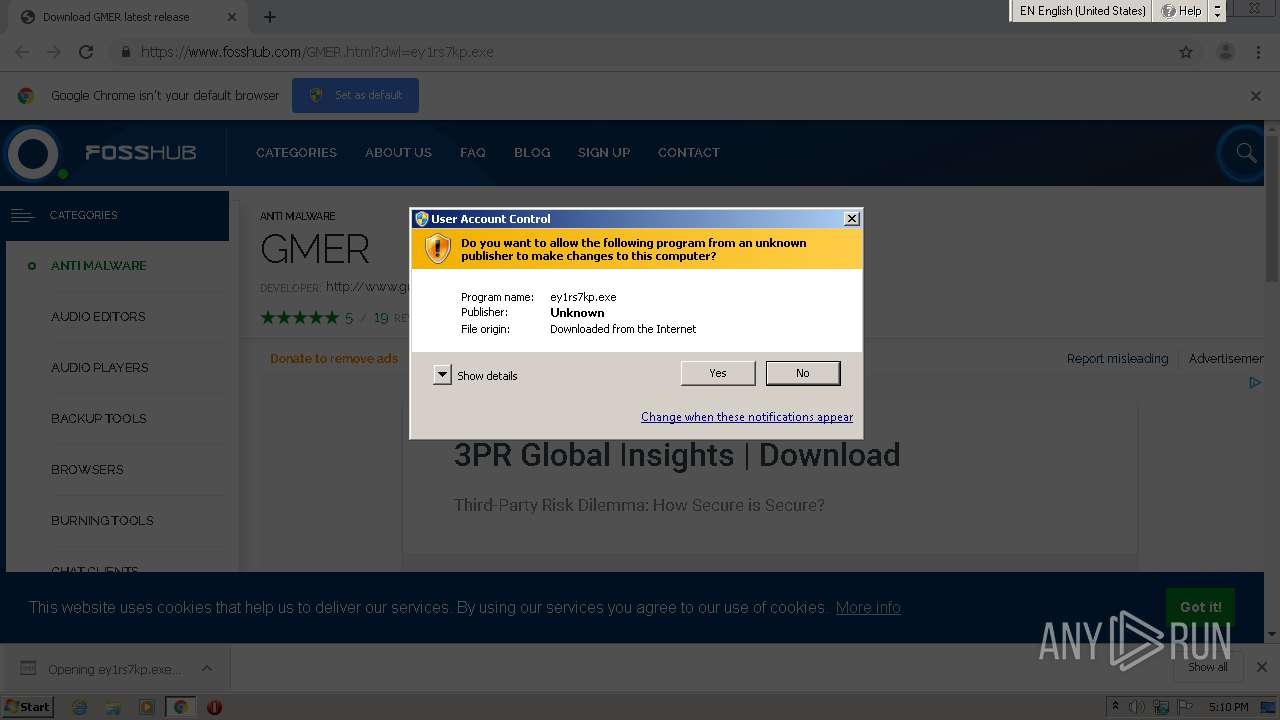
| 2500 | consent.exe 868 300 02881400 | C:\Windows\system32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 3221225547 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 305
Read events
1 184
Write events
118
Delete events
3
Modification events
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | APPSTARTING |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | ARROW |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | CROSS |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | HAND |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | HELP |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | IBEAM |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | NO |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZEALL |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZENESW |
Value: %SystemRoot%\cursors\clearcur.cur | |||
| (PID) Process: | (320) host.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | SIZENS |
Value: %SystemRoot%\cursors\clearcur.cur | |||
Executable files
24
Suspicious files
57
Text files
73
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6060AA6F-974.pma | — | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d10dcad7-16ee-4d7c-8ac5-b8537a1e2d74.tmp | — | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFcfaa1.TMP | text | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2420 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFcfca5.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
34
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2788 | ey1rs7kp.exe | GET | 200 | 23.46.123.27:80 | http://ocsp.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQJ1TBLBrQ9OnPHXPVaWb87MxkNlgQUwu79F9f%2Btw%2FGciJ7fvbA4gIz7D4CEH6T6%2Ft8xk5Z6kuad9QG%2FDs%3D | NL | der | 1.30 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 23.46.123.27:80 | http://sf.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CEFbG0met4H9y7rRgO7%2BEzqU%3D | NL | der | 1.62 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 23.46.123.27:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | NL | der | 1.71 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 304 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
2788 | ey1rs7kp.exe | GET | 304 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 23.46.123.27:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQJ1TBLBrQ9OnPHXPVaWb87MxkNlgQUwu79F9f%2Btw%2FGciJ7fvbA4gIz7D4CEEe%2FGZXfjVJGQ%2FfbbUgNMaQ%3D | NL | der | 1.30 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 200 | 23.46.123.27:80 | http://ts-ocsp.ws.symantec.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRi82PVYYKWGJWdgVNyePy5kYTdqQQUX5r1blzMzHSa1N197z%2Fb7EyALt0CEA7P9DjI%2Fr81bgTYapgbGlA%3D | NL | der | 1.45 Kb | whitelisted |
2788 | ey1rs7kp.exe | GET | 304 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1696 | chrome.exe | 142.250.186.45:443 | accounts.google.com | Google Inc. | US | suspicious |
1696 | chrome.exe | 104.20.136.9:443 | www.fosshub.com | Cloudflare Inc | US | shared |
1696 | chrome.exe | 142.250.185.162:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
1696 | chrome.exe | 142.250.74.200:443 | ssl.google-analytics.com | Google Inc. | US | suspicious |
1696 | chrome.exe | 142.250.74.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1696 | chrome.exe | 104.16.18.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
1696 | chrome.exe | 142.250.185.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1696 | chrome.exe | 205.234.175.175:443 | download.fosshub.com | CacheNetworks, Inc. | US | suspicious |
1696 | chrome.exe | 142.250.186.162:443 | www.googletagservices.com | Google Inc. | US | whitelisted |
1696 | chrome.exe | 142.250.186.129:443 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.fosshub.com |
| malicious |
accounts.google.com |
| shared |
cdnjs.cloudflare.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
clients1.google.com |
| whitelisted |
api.fosshub.com |
| unknown |
googleads.g.doubleclick.net |
| whitelisted |