| download: | uc |
| Full analysis: | https://app.any.run/tasks/f04fc987-387e-49fb-9cb9-a5d8211e6934 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 19:55:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D1A31ACA2A26878914FE05416DEBA1F5 |
| SHA1: | 9144A485183DE48BFC5147149F46AD18A7D473B9 |
| SHA256: | BD54F41A3D5981F80F2B05F272E397693B546F74E1F00BC75646EBF73C2ECB47 |
| SSDEEP: | 768:lGIMuJkvBMUv36ZpuWRyzntvqdIs9gia/dGy49w:QI0aUv36UrtvEIs9/a0W |
MALICIOUS
Changes the autorun value in the registry
- WScript.exe (PID: 236)
- wscript.exe (PID: 2416)
- wscript.exe (PID: 2956)
- WScript.exe (PID: 3796)
Writes to a start menu file
- WScript.exe (PID: 236)
- wscript.exe (PID: 2416)
- wscript.exe (PID: 2956)
- WScript.exe (PID: 3796)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3928)
- cmd.exe (PID: 3832)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3076)
- schtasks.exe (PID: 272)
SUSPICIOUS
Application launched itself
- WScript.exe (PID: 236)
- wscript.exe (PID: 2416)
- WScript.exe (PID: 3796)
Executes scripts
- WinRAR.exe (PID: 3376)
- WScript.exe (PID: 236)
- wscript.exe (PID: 2416)
- WScript.exe (PID: 3796)
Creates files in the user directory
- WScript.exe (PID: 236)
- wscript.exe (PID: 2956)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2956)
- wscript.exe (PID: 1892)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
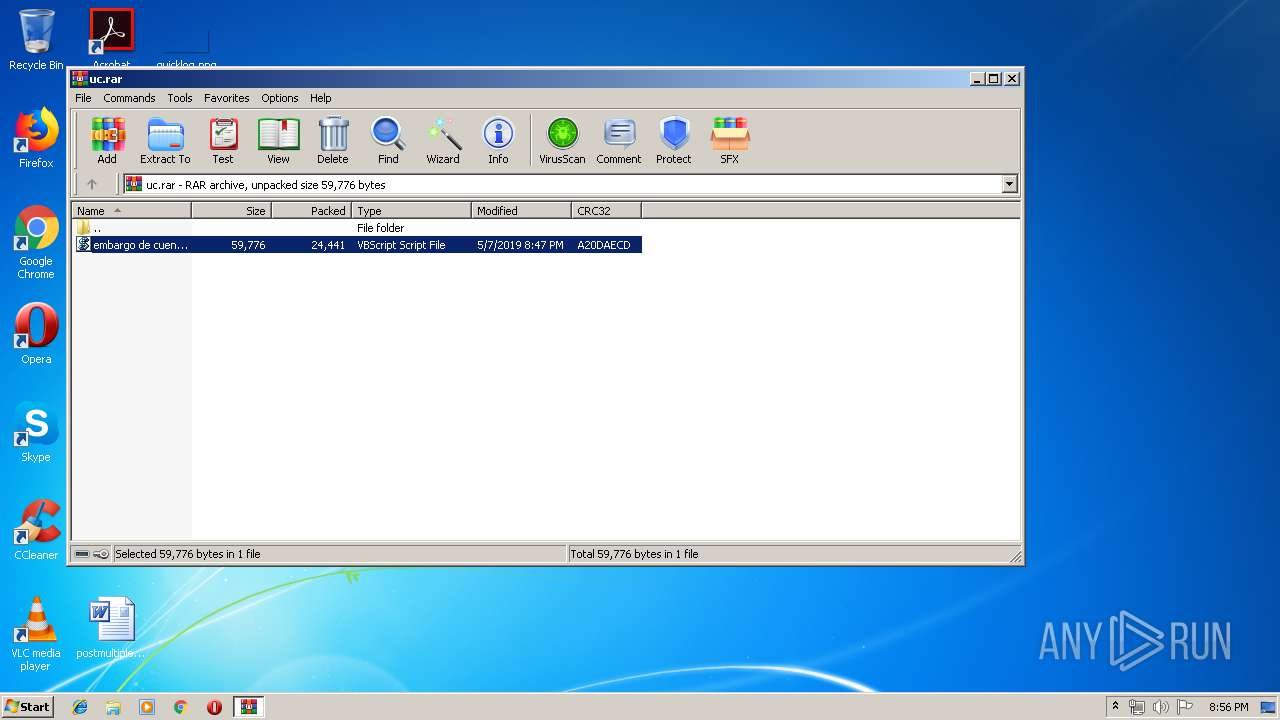
| 236 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3376.17763\embargo de cuenta corriente sobre giro en mora.vbs" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 272 | schtasks /create /sc minute /mo 30 /tn Skypee /tr "C:\Users\admin\AppData\Local\Temp\meee.vbs" | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs" | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2416 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Local\Temp\embargo de cuenta corriente sobre giro en mora.vbs" | C:\Windows\System32\wscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2956 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs" | C:\Windows\System32\wscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2980 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs" | C:\Windows\System32\wscript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3020 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Local\Temp\embargo de cuenta corriente sobre giro en mora.vbs" | C:\Windows\System32\wscript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3076 | schtasks /create /sc minute /mo 30 /tn Skypee /tr "C:\Users\admin\AppData\Local\Temp\meee.vbs" | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
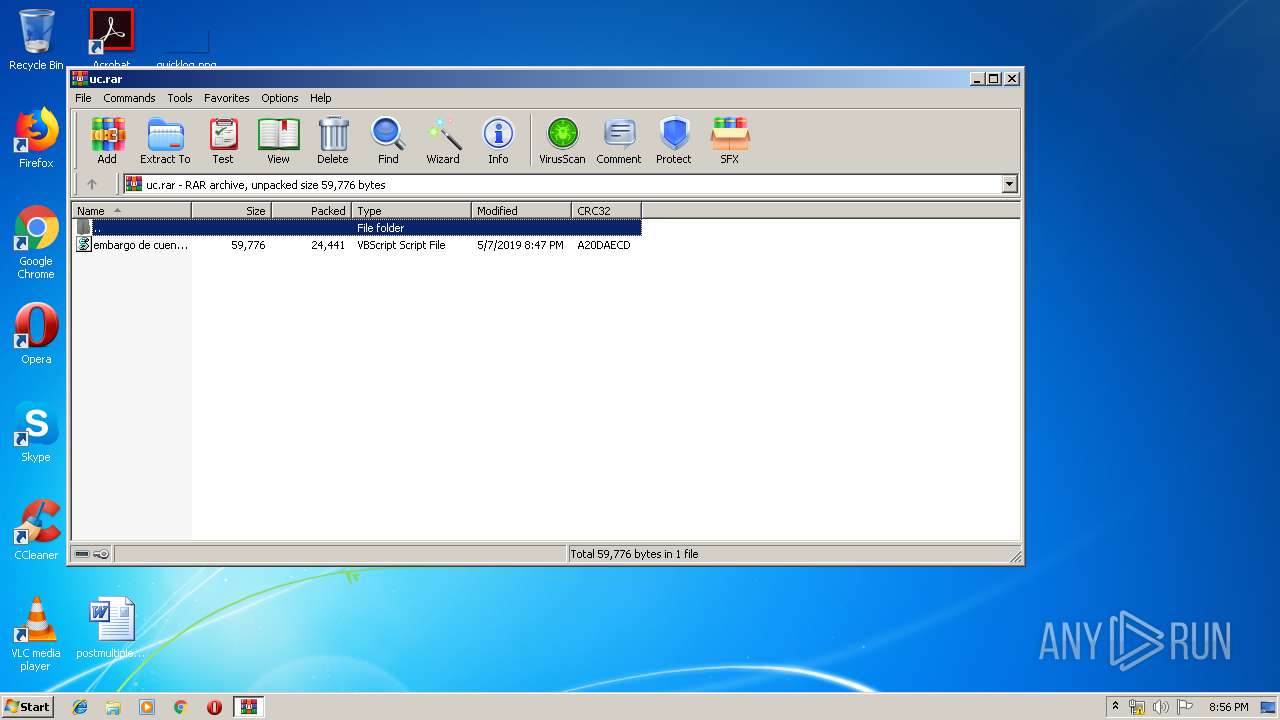
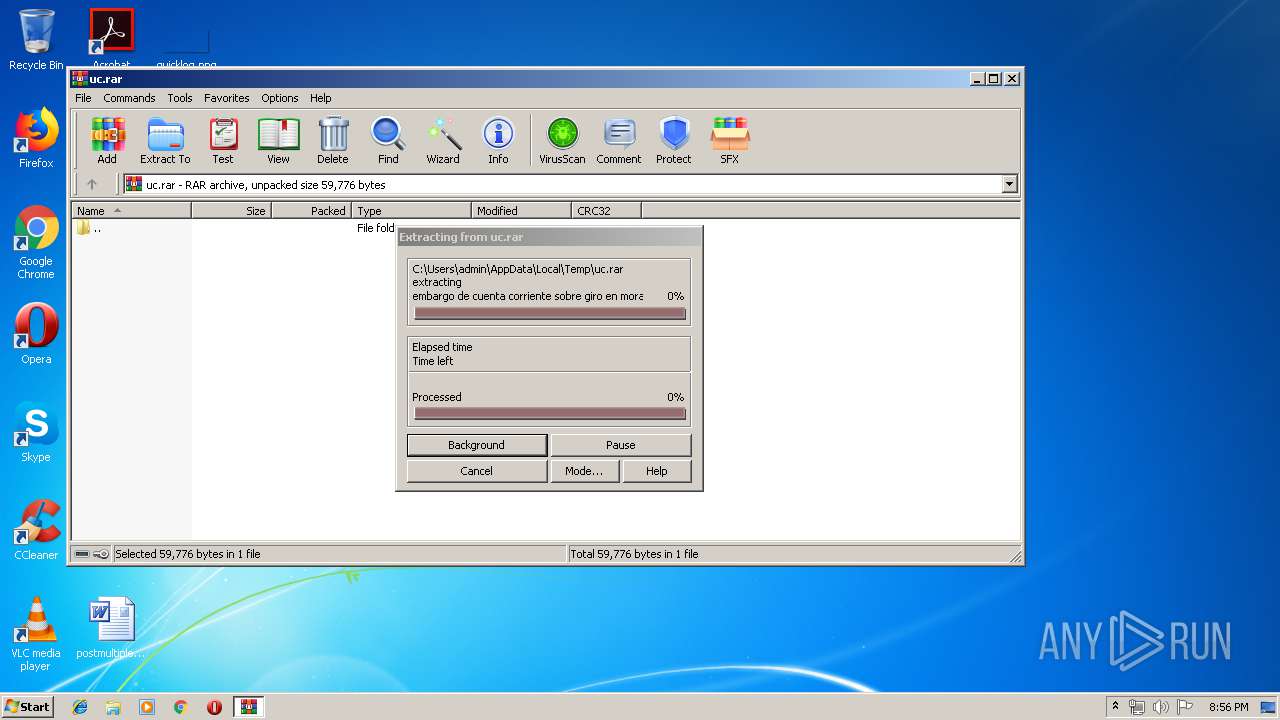
| 3376 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\uc.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3796 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3376.19356\embargo de cuenta corriente sobre giro en mora.vbs" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
1 116
Read events
1 026
Write events
90
Delete events
0
Modification events
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\uc.rar | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4802 |
Value: VBScript Script File | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | wscript.exe | C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs | text | |
MD5:— | SHA256:— | |||
| 236 | WScript.exe | C:\Users\admin\AppData\Local\Temp\embargo de cuenta corriente sobre giro en mora.vbs | text | |
MD5:— | SHA256:— | |||
| 236 | WScript.exe | C:\Users\admin\AppData\Roaming\hDJmPnyWmy.vbs | text | |
MD5:— | SHA256:— | |||
| 236 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\embargo de cuenta corriente sobre giro en mora.vbs | text | |
MD5:— | SHA256:— | |||
| 2956 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\hDJmPnyWmy.vbs | text | |
MD5:— | SHA256:— | |||
| 2956 | wscript.exe | C:\Users\admin\AppData\Local\Temp\meee.vbs | text | |
MD5:— | SHA256:— | |||
| 3376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3376.17763\embargo de cuenta corriente sobre giro en mora.vbs | text | |
MD5:— | SHA256:— | |||
| 1892 | wscript.exe | C:\Users\admin\AppData\Local\Temp\meee.vbs | text | |
MD5:— | SHA256:— | |||
| 2416 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\embargo de cuenta corriente sobre giro en mora.vbs | text | |
MD5:— | SHA256:— | |||
| 3796 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\embargo de cuenta corriente sobre giro en mora.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
15
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
2416 | wscript.exe | POST | — | 192.169.69.25:5561 | http://ofinuevamayo.duckdns.org:5561/is-ready | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2956 | wscript.exe | 23.105.131.223:6677 | brothersjoy.nl | Nobis Technology Group, LLC | US | malicious |
2416 | wscript.exe | 192.169.69.25:5561 | ofinuevamayo.duckdns.org | Wowrack.com | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
brothersjoy.nl |
| unknown |
ofinuevamayo.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |