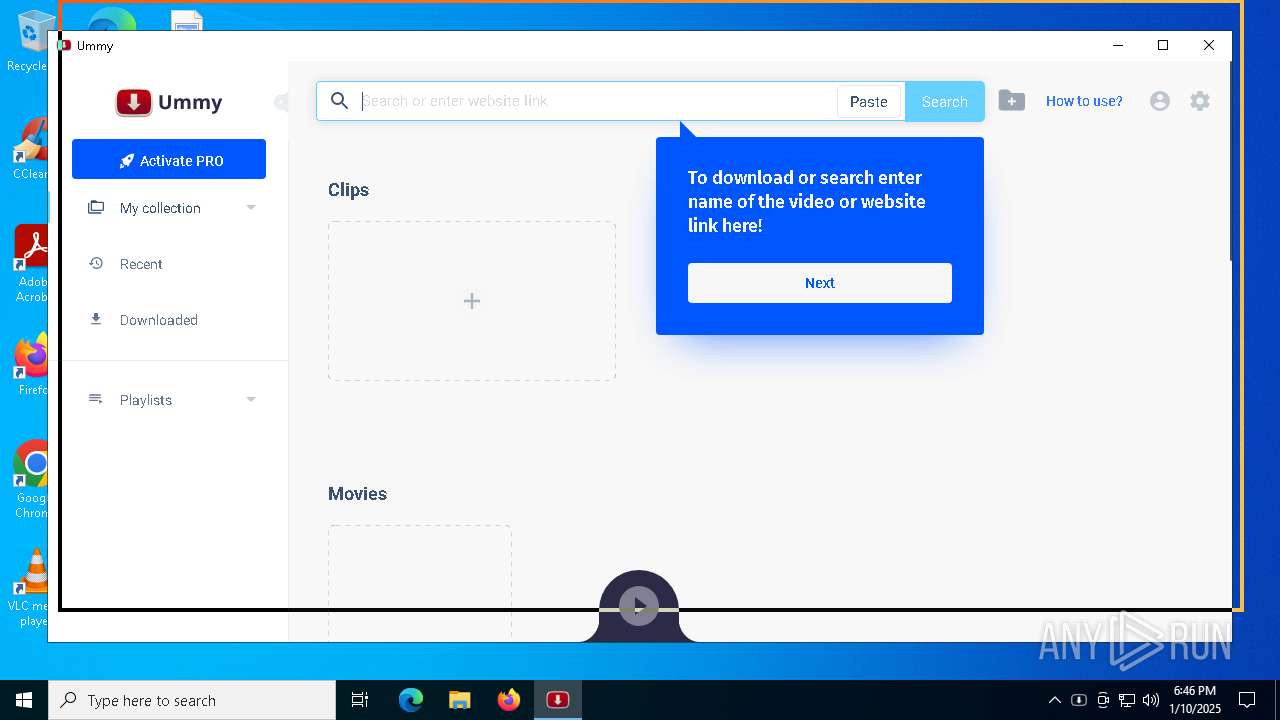
| File name: | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe |
| Full analysis: | https://app.any.run/tasks/6b783e84-8a82-47c8-b43b-80ee26ca8e50 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 18:45:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 949FAB8A38F9163BE3019D326CD2AB3C |
| SHA1: | BCC4C0E24496556C9EA72B904034FF7FAD21B40B |
| SHA256: | BD3DA4BB59C183FDC093FC526CD75BB2A7969A757A7E698598943A0D79163CF7 |
| SSDEEP: | 49152:DPNVkWShlX40vue4HyNt85q0lVlqQXO6ZCmSxbv0kFgQ0Qh1lhUq8s891D751h1O:DP/kWSA4D05zrlhO6smSlvMQ0QrTU15C |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
Executable content was dropped or overwritten
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- vcredist_x86.exe (PID: 4540)
Starts CMD.EXE for commands execution
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Ummy.exe (PID: 6552)
Get information on the list of running processes
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- cmd.exe (PID: 6892)
Reads security settings of Internet Explorer
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Setup.exe (PID: 5496)
Drops 7-zip archiver for unpacking
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
Process drops legitimate windows executable
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
Creates a software uninstall entry
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
Checks Windows Trust Settings
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Setup.exe (PID: 5496)
- msiexec.exe (PID: 6348)
The process creates files with name similar to system file names
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 4540)
- vcredist_x86.exe (PID: 836)
Creates file in the systems drive root
- vcredist_x86.exe (PID: 4540)
The process drops C-runtime libraries
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
Application launched itself
- Ummy.exe (PID: 6552)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1480)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 736)
INFO
The sample compiled with english language support
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
Checks supported languages
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- vcredist_x86.exe (PID: 4540)
- Setup.exe (PID: 5496)
- msiexec.exe (PID: 6348)
- Ummy.exe (PID: 6552)
- Ummy.exe (PID: 7072)
- Ummy.exe (PID: 4984)
- Ummy.exe (PID: 7156)
- Ummy.exe (PID: 4384)
Checks proxy server information
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Ummy.exe (PID: 6552)
Reads the machine GUID from the registry
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Setup.exe (PID: 5496)
- msiexec.exe (PID: 6348)
- Ummy.exe (PID: 6552)
Reads the computer name
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- vcredist_x86.exe (PID: 4540)
- Setup.exe (PID: 5496)
- msiexec.exe (PID: 6348)
- Ummy.exe (PID: 7156)
Reads the software policy settings
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Setup.exe (PID: 5496)
- msiexec.exe (PID: 6348)
- Ummy.exe (PID: 6552)
Creates files or folders in the user directory
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- msiexec.exe (PID: 6348)
- Ummy.exe (PID: 6552)
- Ummy.exe (PID: 7156)
The process uses the downloaded file
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
Create files in a temporary directory
- UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe (PID: 3688)
- Setup.exe (PID: 5496)
- Ummy.exe (PID: 6552)
The sample compiled with japanese language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with french language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with chinese language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with korean language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with Italian language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with german language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with spanish language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
The sample compiled with russian language support
- vcredist_x86.exe (PID: 4540)
- msiexec.exe (PID: 6348)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6348)
Manual execution by a user
- Ummy.exe (PID: 6552)
Creates a software uninstall entry
- msiexec.exe (PID: 6348)
Sends debugging messages
- Setup.exe (PID: 5496)
Process checks computer location settings
- Ummy.exe (PID: 6552)
- Ummy.exe (PID: 4984)
- Ummy.exe (PID: 4384)
Drops encrypted VBS script (Microsoft Script Encoder)
- Ummy.exe (PID: 4384)
Application launched itself
- msedge.exe (PID: 6720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.17.2.0 |
| ProductVersionNumber: | 1.17.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | ITPRODUCTDEV LTD |
| FileDescription: | Ummy Desktop |
| FileVersion: | 1.17.2 |
| LegalCopyright: | Copyright © 2024 ITPRODUCTDEV LTD |
| ProductName: | Ummy |
| ProductVersion: | 1.17.2 |
Total processes
193
Monitored processes
63
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x31c,0x320,0x324,0x314,0x32c,0x7ff822105fd8,0x7ff822105fe4,0x7ff822105ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5636 --field-trial-handle=2140,i,14456005298393803830,8768662434348839387,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /d /s /c "C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\ummy\shell\open\command" /f" | C:\Windows\SysWOW64\cmd.exe | — | Ummy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | "C:\Users\admin\AppData\Local\Temp\nse543F.tmp\vcredist_x86.exe" /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\vcredist_x86.exe | — | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2010 x86 Redistributable Setup Exit code: 3221226540 Version: 10.0.40219.325 Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4032 --field-trial-handle=2140,i,14456005298393803830,8768662434348839387,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4220 --field-trial-handle=2140,i,14456005298393803830,8768662434348839387,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1480 | C:\WINDOWS\system32\cmd.exe /d /s /c "C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\ummy" /f" | C:\Windows\SysWOW64\cmd.exe | — | Ummy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4500 --field-trial-handle=2140,i,14456005298393803830,8768662434348839387,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\ummy" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 285
Read events
19 636
Write events
607
Delete events
42
Modification events
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\ummy | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Ummy |
| Operation: | write | Name: | vid |
Value: 148 | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\ummy\uninstallerIcon.ico | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | Publisher |
Value: ITPRODUCTDEV LTD | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (3688) UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | EstimatedSize |
Value: 220981 | |||
Executable files
96
Suspicious files
463
Text files
156
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\ummy-1.17.2-ia32.nsis[1].7z | — | |
MD5:— | SHA256:— | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\package.7z | — | |
MD5:— | SHA256:— | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\nsExec.dll | executable | |
MD5:EC0504E6B8A11D5AAD43B296BEEB84B2 | SHA256:5D9CEB1CE5F35AEA5F9E5A0C0EDEEEC04DFEFE0C77890C80C70E98209B58B962 | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\Local\Temp\nse543F.tmp\INetC.dll | executable | |
MD5:38CAA11A462B16538E0A3DAEB2FC0EAF | SHA256:ED04A4823F221E9197B8F3C3DA1D6859FF5B176185BDE2F1C923A442516C810A | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:6C267D0F5E9DB296FEBA42DA9E43DEDE | SHA256:5E06E6FF173B4937A584980B2ABA178984EA8FA30822F00E70E46DC712424627 | |||
| 3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
101
DNS requests
91
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACECesG%2BlaxWWrCklg14T%2Fer4%3D | unknown | — | — | whitelisted |
3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | GET | 200 | 104.21.1.194:80 | http://cdn-televzr.com/ummy/ummy-1.17.2-ia32.nsis.7z | unknown | — | — | unknown |
3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | GET | 302 | 172.67.150.95:80 | http://desktop.televzr.com/download/updater/latest/ummy.nsis.7z/ummy-1.17.2-ia32.nsis.7z | unknown | — | — | whitelisted |
5568 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6244 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5568 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3688 | UmmyVD-[ed24b3e43be1a42842f448e769eb8152,148,,,].exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.146:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2164 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|