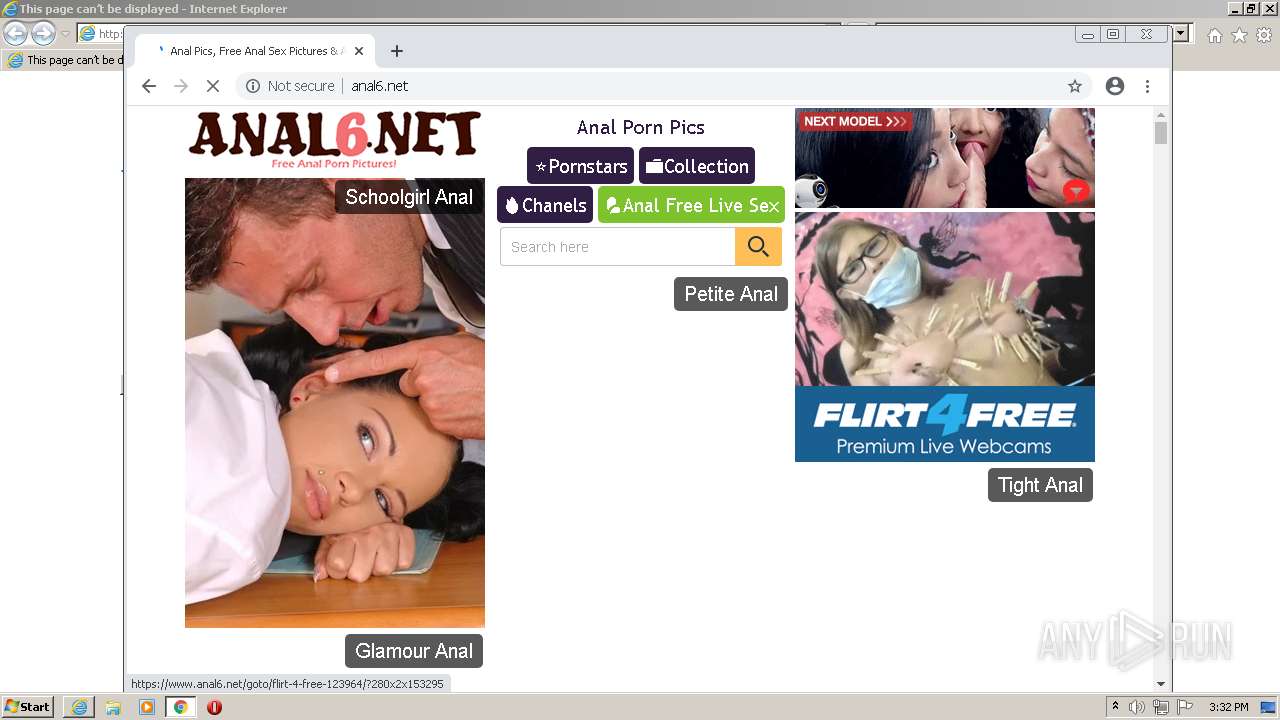
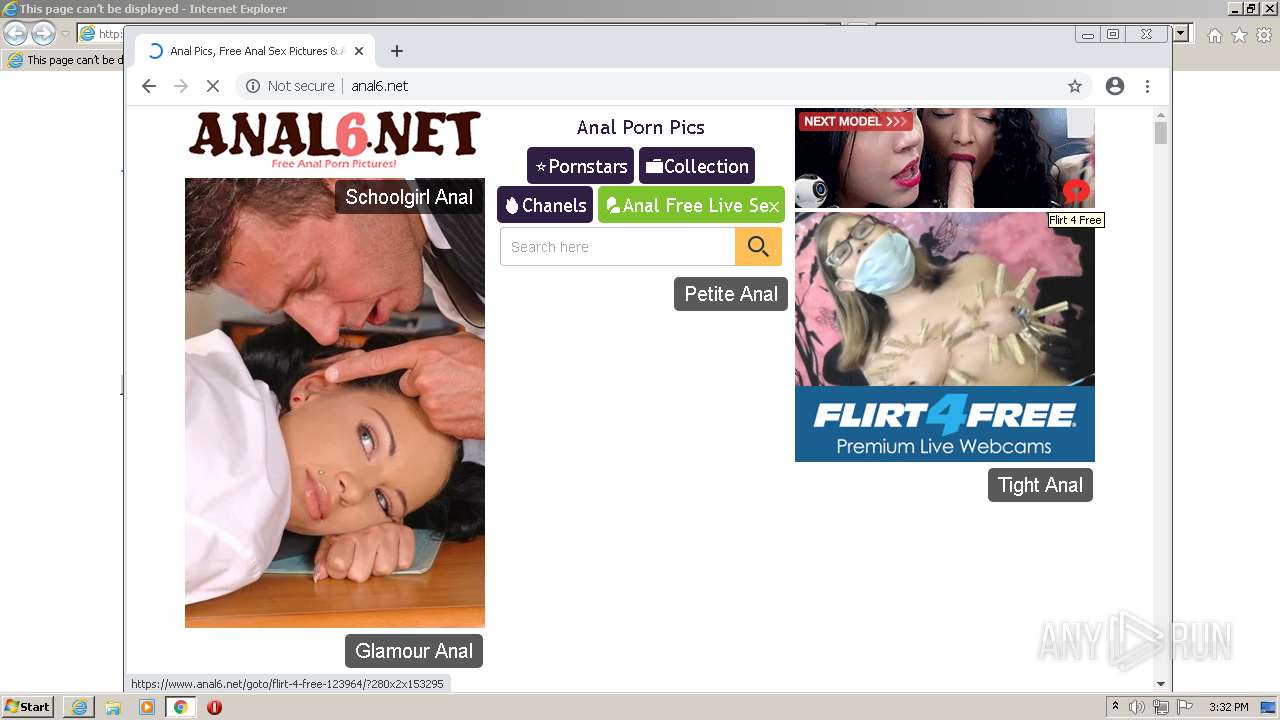
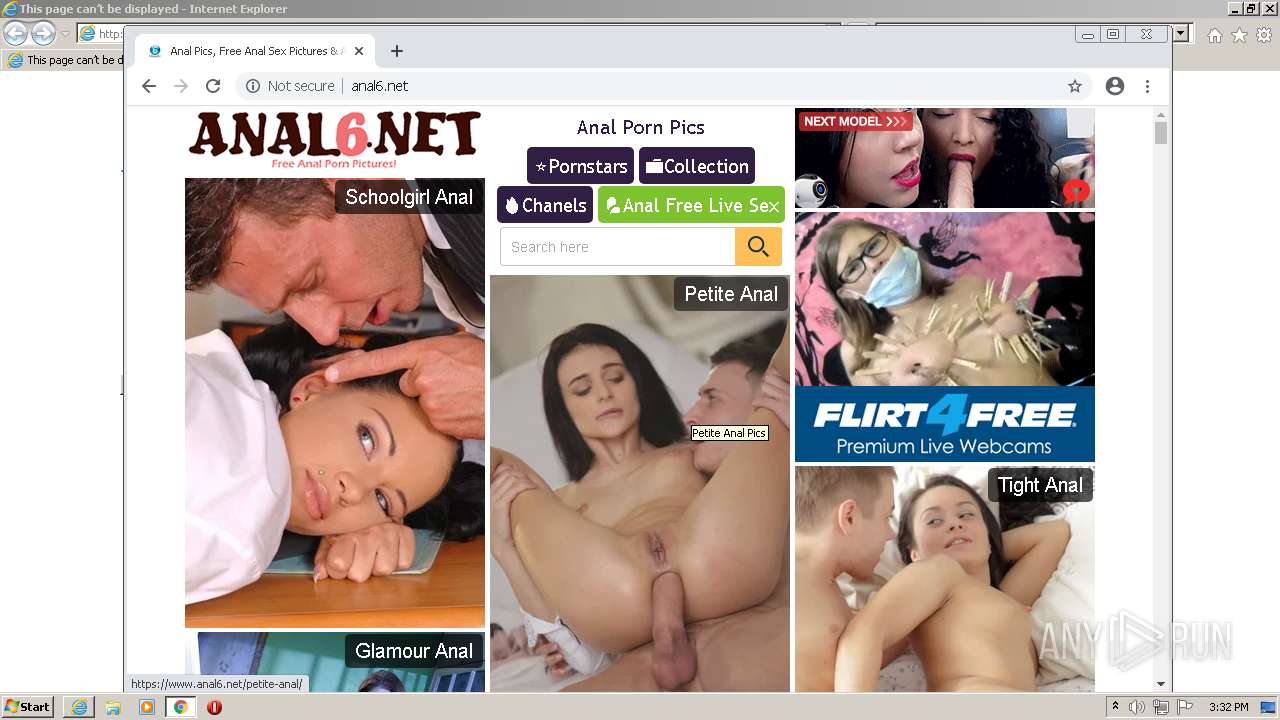
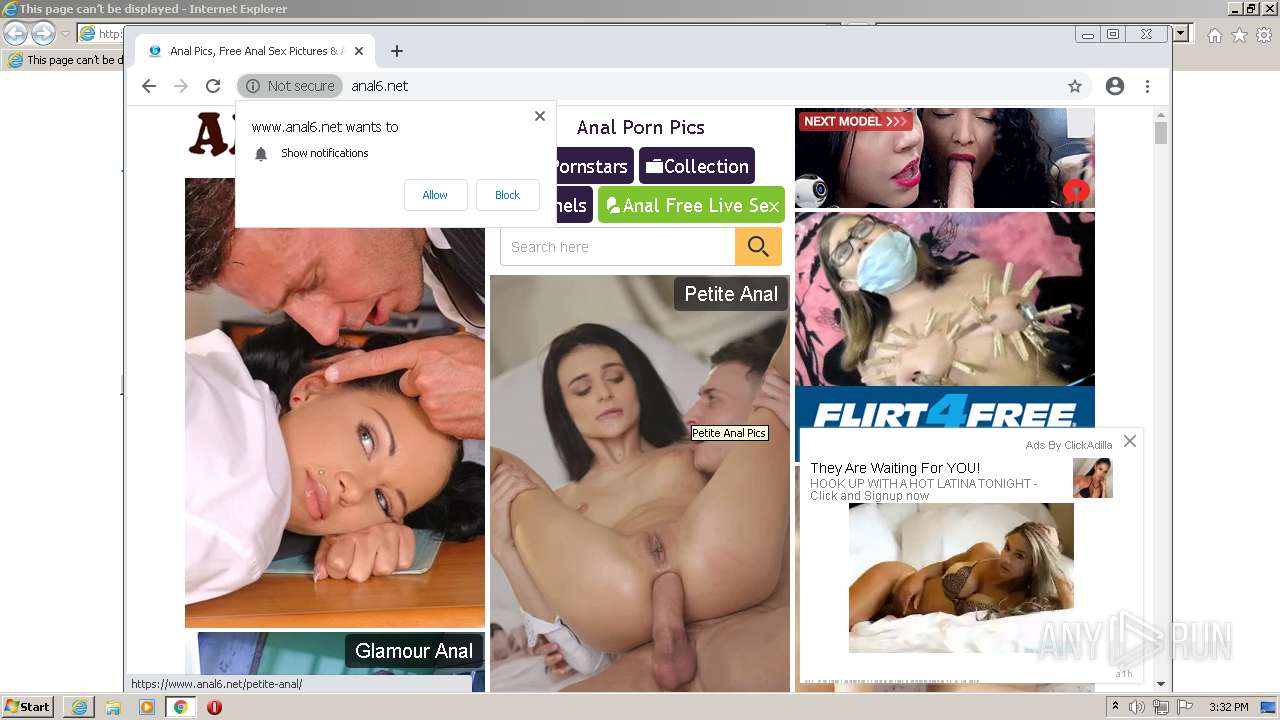
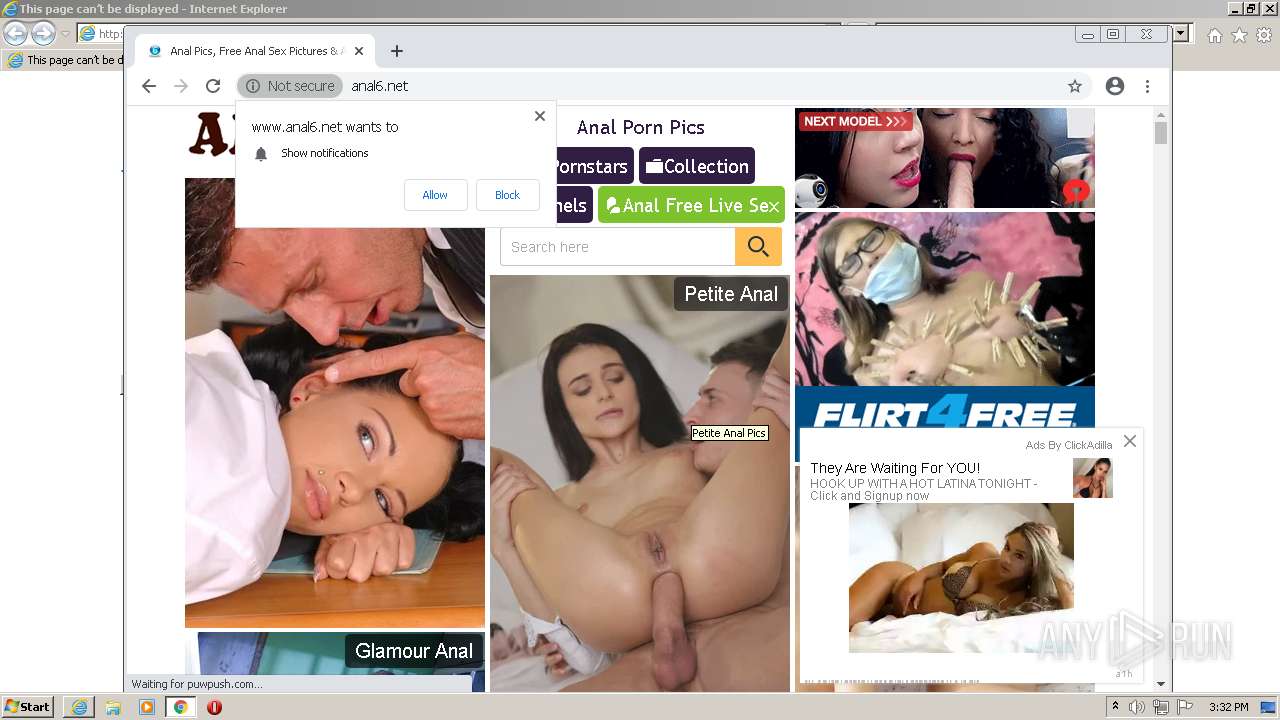
| URL: | HTTP://www.anal6.net/pics/ |
| Full analysis: | https://app.any.run/tasks/c4a1a768-0844-4b31-8bfc-10367bd6aad4 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 15:29:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4AC909CFEC4ECC5DBD033053D9A47F42 |
| SHA1: | 78ADD0F8A57278BB4980C6CB0AF09916144B9D69 |
| SHA256: | BD3C0A479A76A6A4E341453BA42B90BE3F5990F2D8C9BDE566A3FFB1DCDD822C |
| SSDEEP: | 3:CKSdJlMGNn:C3JW8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3452)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3776)
INFO
Checks supported languages
- iexplore.exe (PID: 3452)
- iexplore.exe (PID: 3576)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 2256)
- chrome.exe (PID: 3420)
- chrome.exe (PID: 2220)
- chrome.exe (PID: 4080)
- chrome.exe (PID: 1672)
- chrome.exe (PID: 1000)
- chrome.exe (PID: 1544)
- chrome.exe (PID: 2100)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 2588)
- chrome.exe (PID: 3276)
- chrome.exe (PID: 4056)
- chrome.exe (PID: 2752)
- chrome.exe (PID: 2412)
- chrome.exe (PID: 1400)
- chrome.exe (PID: 4040)
- chrome.exe (PID: 2208)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 2024)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 3184)
Checks Windows Trust Settings
- iexplore.exe (PID: 3576)
- iexplore.exe (PID: 3452)
Reads internet explorer settings
- iexplore.exe (PID: 3452)
Changes internet zones settings
- iexplore.exe (PID: 3576)
Manual execution by user
- chrome.exe (PID: 3776)
Reads settings of System Certificates
- iexplore.exe (PID: 3452)
- iexplore.exe (PID: 3576)
- chrome.exe (PID: 1672)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3576)
Reads the computer name
- chrome.exe (PID: 3776)
- iexplore.exe (PID: 3576)
- iexplore.exe (PID: 3452)
- chrome.exe (PID: 1672)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 2588)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 4040)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 2220)
Application launched itself
- iexplore.exe (PID: 3576)
- chrome.exe (PID: 3776)
Creates files in the user directory
- iexplore.exe (PID: 3576)
Changes settings of System certificates
- iexplore.exe (PID: 3576)
Reads the date of Windows installation
- chrome.exe (PID: 4040)
Reads the hosts file
- chrome.exe (PID: 3776)
- chrome.exe (PID: 1672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
62
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1880 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2728 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2840 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1416 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=660 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1068 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x71a3d988,0x71a3d998,0x71a3d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7583076304895497318,8256247647554175293,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1144 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
23 791
Read events
23 551
Write events
236
Delete events
4
Modification events
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 594296896 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937399 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 894458146 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937399 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3576) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
189
Text files
142
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\XOHEDFLL.txt | text | |
MD5:— | SHA256:— | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\CWSRUT1G.txt | text | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3452 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\pics[1] | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\7K77UKQ5.txt | text | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\BSEYD1L5.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
105
DNS requests
71
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1672 | chrome.exe | GET | 301 | 172.67.219.183:80 | http://www.anal6.net/pics/ | US | — | — | suspicious |
3452 | iexplore.exe | GET | 301 | 104.21.38.65:80 | http://www.anal6.net/pics/ | US | — | — | suspicious |
3452 | iexplore.exe | GET | 200 | 95.101.89.75:80 | http://e1.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTvkAFw3ViPKmUeIVEf3NC7b1ErqwQUWvPtK%2Fw2wjd5uVIw6lRvz1XLLqwCEgPcCrTWsSXpnT5WgeGDdHVAKA%3D%3D | unknown | der | 345 b | whitelisted |
1672 | chrome.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 556 b | whitelisted |
3576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1672 | chrome.exe | GET | 301 | 64.79.78.74:80 | http://counter.24log.de/counter?redir=1&id=7961&t=47&st=1&d=6&nojs=1 | US | html | 169 b | suspicious |
3576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3576 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3452 | iexplore.exe | GET | 200 | 104.89.32.83:80 | http://x2.c.lencr.org/ | NL | der | 299 b | whitelisted |
3452 | iexplore.exe | GET | 200 | 104.89.32.83:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3452 | iexplore.exe | 104.21.38.65:80 | www.anal6.net | Cloudflare Inc | US | suspicious |
3452 | iexplore.exe | 104.21.38.65:443 | www.anal6.net | Cloudflare Inc | US | suspicious |
3576 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3576 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3576 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3452 | iexplore.exe | 172.67.219.183:80 | www.anal6.net | — | US | unknown |
3576 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3452 | iexplore.exe | 172.67.219.183:443 | www.anal6.net | — | US | unknown |
3452 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3452 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.anal6.net |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
x2.c.lencr.org |
| whitelisted |