| File name: | NDP452-KB2901954-Web.exe |
| Full analysis: | https://app.any.run/tasks/38c7f58b-9c8c-4155-9490-a66083bdef50 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2021, 10:56:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CA41DBA55A727F01104871B160CD5B1D |
| SHA1: | 5B71B20A455F6EEAB79DD1EDCAB0BA66AD0D2208 |
| SHA256: | BD173D14A371E6786C4AE90BE1F2C560458D672BA4CBEB3CF55BEBFEF2E2778A |
| SSDEEP: | 24576:Jz9m04PLdUcyezFSjaggwdRTw28Z4Qn+dwVY0YbxYRyUwuGqq:59m04DGexmLTQn+dwZYMyXd |
MALICIOUS
Drops executable file immediately after starts
- NDP452-KB2901954-Web.exe (PID: 2320)
Actions looks like stealing of personal data
- NDP452-KB2901954-Web.exe (PID: 2320)
Loads dropped or rewritten executable
- Setup.exe (PID: 2592)
Application was dropped or rewritten from another process
- Setup.exe (PID: 2592)
SUSPICIOUS
Executable content was dropped or overwritten
- NDP452-KB2901954-Web.exe (PID: 2320)
Drops a file that was compiled in debug mode
- NDP452-KB2901954-Web.exe (PID: 2320)
Drops a file with too old compile date
- NDP452-KB2901954-Web.exe (PID: 2320)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| ProductVersion: | 4.5.51209.34209 |
|---|---|
| ProductName: | Microsoft .NET Framework 4.5.2 |
| OriginalFileName: | NDP452-KB2901954-Web.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| InternalName: | NDP452-KB2901954-Web.exe |
| FileVersion: | 4.5.51209.34209 |
| FileDescription: | Microsoft .NET Framework 4.5.2 Setup |
| CompanyName: | Microsoft Corporation |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 4.5.51209.34209 |
| FileVersionNumber: | 4.5.51209.34209 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5.1 |
| ImageVersion: | 10 |
| OSVersion: | 5.1 |
| EntryPoint: | 0x18976 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 29696 |
| CodeSize: | 157696 |
| LinkerVersion: | 10 |
| PEType: | PE32 |
| TimeStamp: | 2013:12:26 01:13:26+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Dec-2013 00:13:26 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | Microsoft Corporation |
| FileDescription: | Box Stub |
| FileVersion: | 12.0.52552.34107 built by: FX452RTMGDR(MGHAZNAWKS-MGHAZNA) |
| InternalName: | BoxStub.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFilename: | BoxStub.exe |
| ProductName: | Microsoft® .NET Framework |
| ProductVersion: | 12.0.52552.34107 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 26-Dec-2013 00:13:26 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002670A | 0x00026800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.56437 |
.data | 0x00028000 | 0x00003700 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.4157 |
.idata | 0x0002C000 | 0x0000122A | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.18948 |
.boxld01\xb6 | 0x0002E000 | 0x000000B6 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.66081 |
.rsrc | 0x0002F000 | 0x00001EE8 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.27514 |
.reloc | 0x00031000 | 0x0000286A | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.91342 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18631 | 1338 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.65184 | 180 | Latin 1 / Western European | English - United States | RT_STRING |
32 | 1.85835 | 64 | Latin 1 / Western European | English - United States | RT_STRING |
107 | 2.37086 | 34 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
129 | 3.13202 | 268 | Latin 1 / Western European | English - United States | RT_DIALOG |
130 | 3.33978 | 368 | Latin 1 / Western European | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
Cabinet.dll |
KERNEL32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
VERSION.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
?dwPlaceholder@@3PAEA | 1 | 0x0002E000 |
_DecodePointerInternal@4 | 2 | 0x0000B60E |
_EncodePointerInternal@4 | 3 | 0x0000B5F3 |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1708 | "C:\Users\admin\AppData\Local\Temp\NDP452-KB2901954-Web.exe" | C:\Users\admin\AppData\Local\Temp\NDP452-KB2901954-Web.exe | — | explorer.exe | |||||||||||
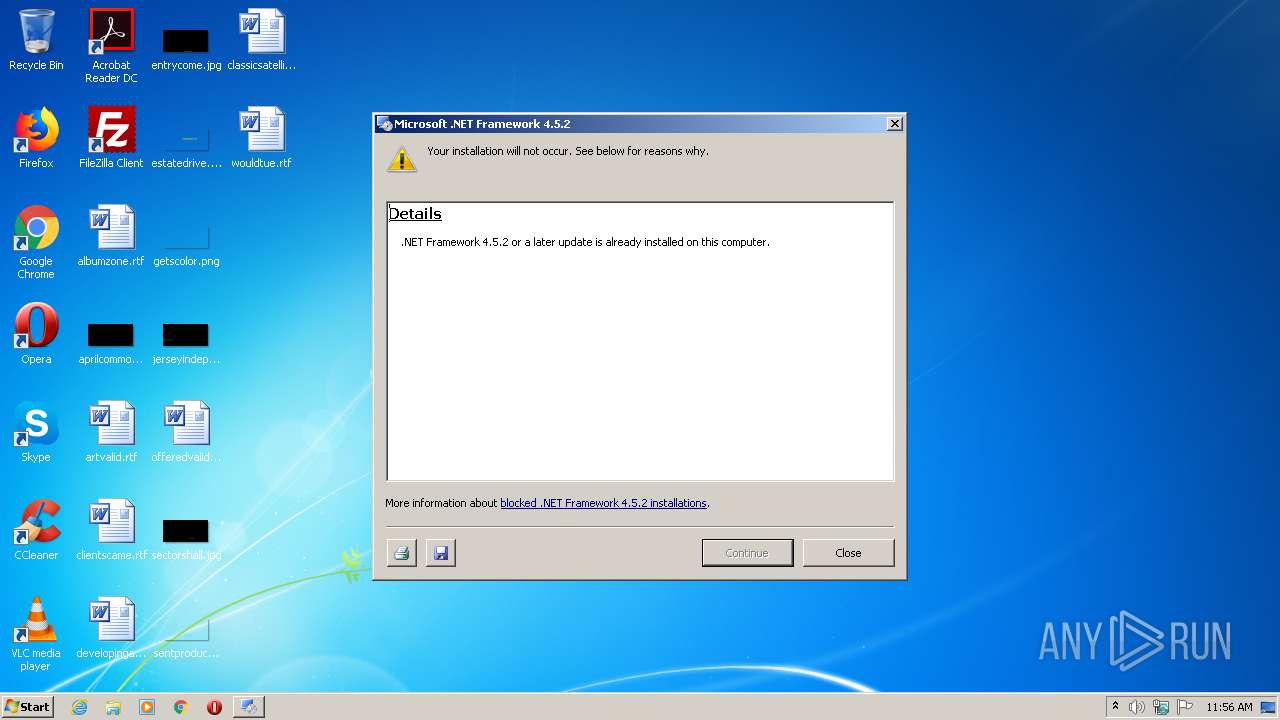
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.5.2 Setup Exit code: 3221226540 Version: 4.5.51209.34209 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Local\Temp\NDP452-KB2901954-Web.exe" | C:\Users\admin\AppData\Local\Temp\NDP452-KB2901954-Web.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5.2 Setup Exit code: 0 Version: 4.5.51209.34209 Modules
| |||||||||||||||
| 2592 | C:\2844a04f0ccf818cda\\Setup.exe /x86 /x64 /web | C:\2844a04f0ccf818cda\Setup.exe | — | NDP452-KB2901954-Web.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 12.0.51209.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
9
Read events
9
Write events
0
Delete events
0
Modification events
Executable files
29
Suspicious files
0
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Print.ico | image | |
MD5:7E55DDC6D611176E697D01C90A1212CF | SHA256:FF542E32330B123486797B410621E19EAFB39DF3997E14701AFA4C22096520ED | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Rotate5.ico | image | |
MD5:3B4861F93B465D724C60670B64FCCFCF | SHA256:7237051D9AF5DB972A1FECF0B35CD8E9021471740782B0DBF60D3801DC9F5F75 | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\SplashScreen.bmp | image | |
MD5:0966FCD5A4AB0DDF71F46C01EFF3CDD5 | SHA256:31C13ECFC0EB27F34036FB65CC0E735CD444EEC75376EEA2642F926AC162DCB3 | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Rotate4.ico | image | |
MD5:BB55B5086A9DA3097FB216C065D15709 | SHA256:8D82FF7970C9A67DA8134686560FE3A6C986A160CED9D1CC1392F2BA75C698AB | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Rotate2.ico | image | |
MD5:8419CAA81F2377E09B7F2F6218E505AE | SHA256:DB89D8A45C369303C04988322B2774D2C7888DA5250B4DAB2846DEEF58A7DE22 | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\header.bmp | image | |
MD5:514BFCD8DA66722A9639EB41ED3988B7 | SHA256:6B8201ED10CE18FFADE072B77C6D1FCACCF1D29ACB47D86F553D9BEEBD991290 | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Rotate1.ico | image | |
MD5:26A00597735C5F504CF8B3E7E9A7A4C1 | SHA256:37026C4EA2182D7908B3CF0CEF8A6F72BDDCA5F1CFBC702F35B569AD689CF0AF | |||
| 2320 | NDP452-KB2901954-Web.exe | C:\2844a04f0ccf818cda\Graphics\Rotate3.ico | image | |
MD5:924FD539523541D42DAD43290E6C0DB5 | SHA256:02A7FE932029C6FA24D1C7CC06D08A27E84F43A0CBC47B7C43CAC59424B3D1F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report