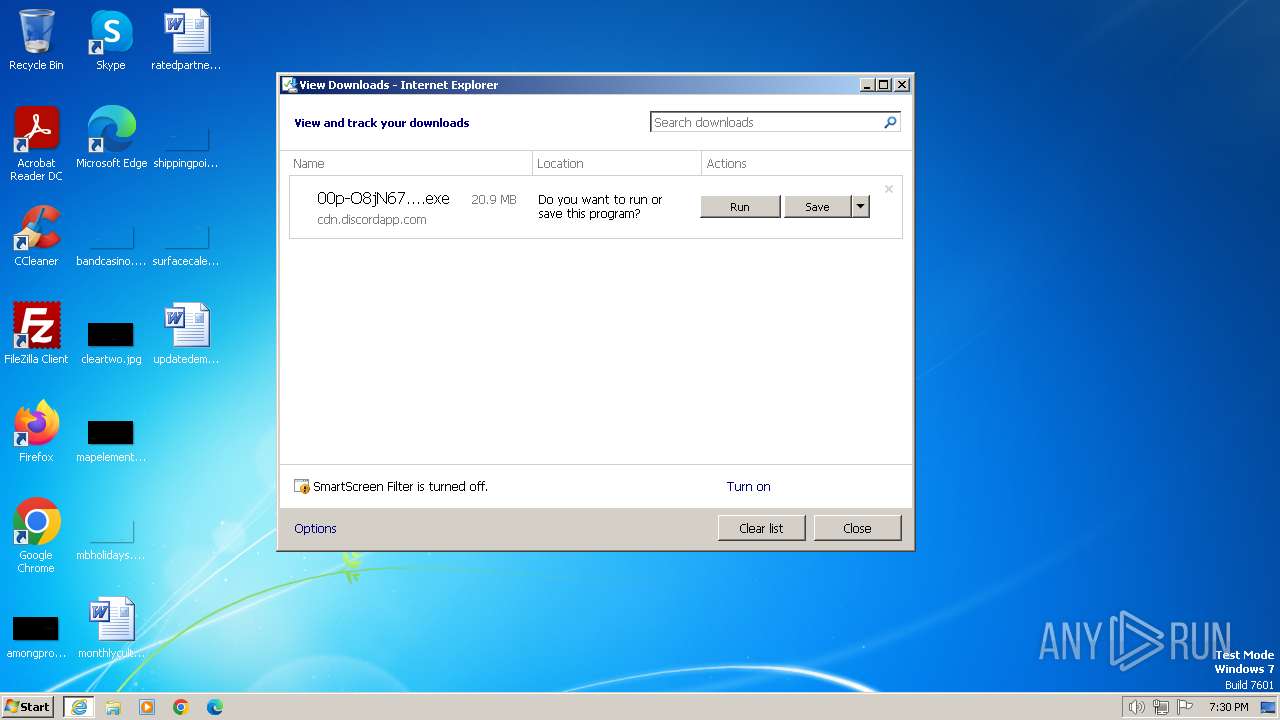
| URL: | https://cdn.discordapp.com/attachments/1197975398387036281/1203422107036553256/00p-O8jN67Hhy.exe?ex=65d1092c&is=65be942c&hm=9ec5f74b8e5ae43b0070a899149428894b783bea95945d29676934dfbcad2cd0& |
| Full analysis: | https://app.any.run/tasks/ae1ea69d-3064-411a-b6a9-fb921b4735f1 |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2024, 19:30:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AA9EBBAE914C11F5F5D442D8DE34375B |
| SHA1: | CC60C034019DAAE38563B2926B403CC9FF3812AD |
| SHA256: | BD046B936B21DDD8DADCED84EA26B0600502C7B700359B3AE3E4DDCD5C109D87 |
| SSDEEP: | 3:N8cCWdy6//NcSHzRUwXXTTQQQ7mTeUkwMFIcRWBw1/A/m0ccUMOydeMMNNXG/:2cry6XNc8zR7XTTLQmTRMFXMaYC1ObM0 |
MALICIOUS
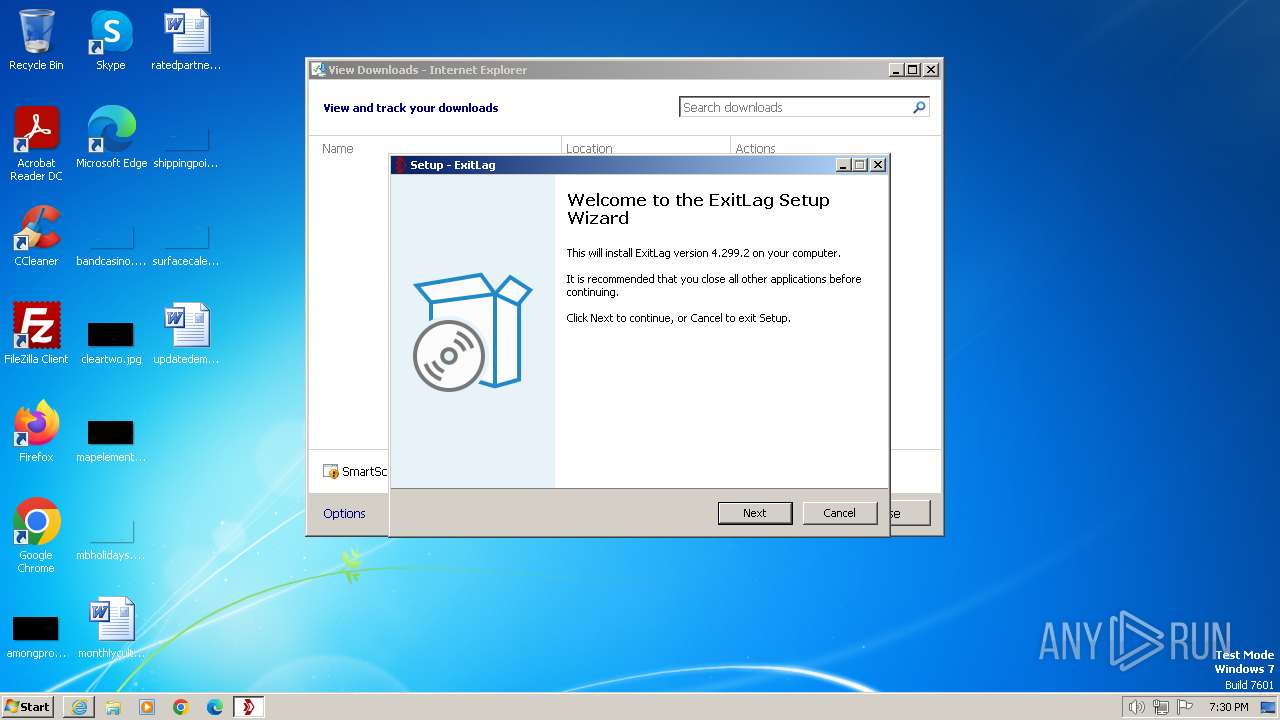
Drops the executable file immediately after the start
- 00p-O8jN67Hhy.exe (PID: 3020)
- 00p-O8jN67Hhy.exe (PID: 3568)
- snetcfg.exe (PID: 3928)
- drvinst.exe (PID: 3816)
- 00p-O8jN67Hhy.tmp (PID: 3576)
Creates a writable file in the system directory
- snetcfg.exe (PID: 3928)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- drvinst.exe (PID: 3816)
SUSPICIOUS
Discord domain found in command line (probably downloading payload)
- iexplore.exe (PID: 1504)
Executable content was dropped or overwritten
- 00p-O8jN67Hhy.exe (PID: 3020)
- 00p-O8jN67Hhy.exe (PID: 3568)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- snetcfg.exe (PID: 3928)
- drvinst.exe (PID: 3816)
Reads the Windows owner or organization settings
- 00p-O8jN67Hhy.tmp (PID: 3576)
Creates files in the driver directory
- drvinst.exe (PID: 3816)
- snetcfg.exe (PID: 3928)
- 00p-O8jN67Hhy.tmp (PID: 3576)
Drops a system driver (possible attempt to evade defenses)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- snetcfg.exe (PID: 3928)
- drvinst.exe (PID: 3816)
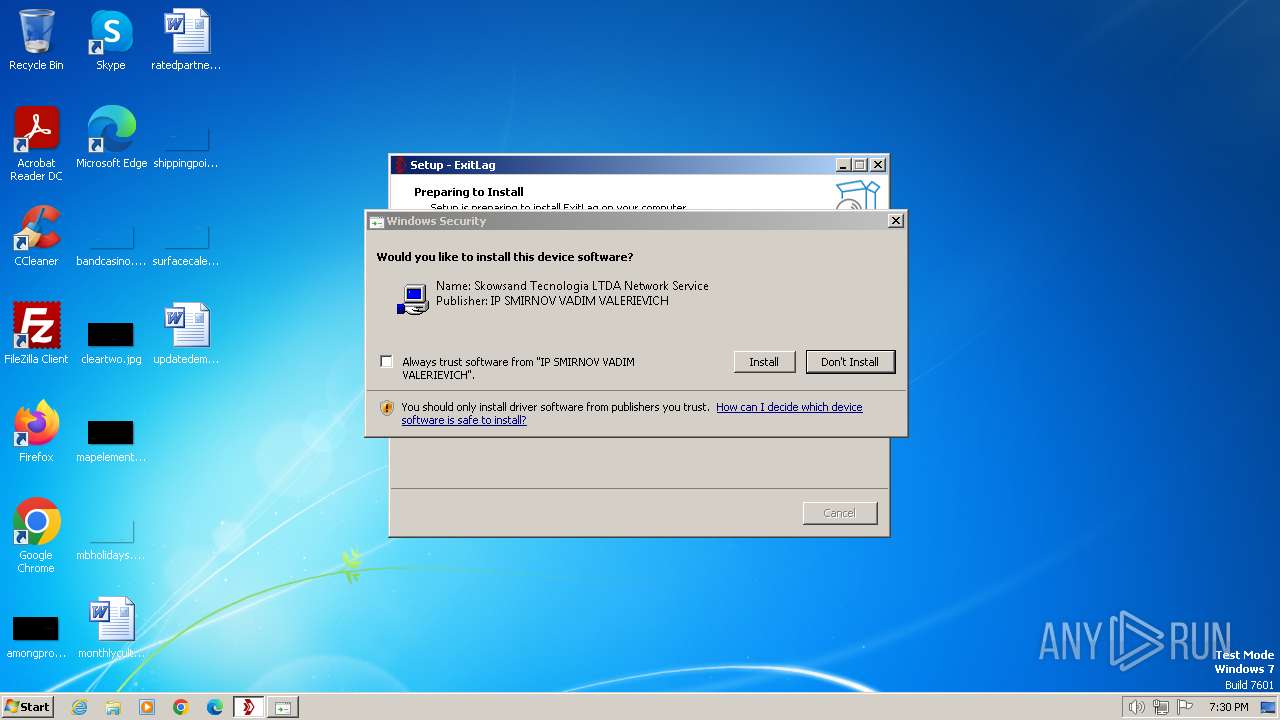
Checks Windows Trust Settings
- drvinst.exe (PID: 3816)
- snetcfg.exe (PID: 3928)
Reads settings of System Certificates
- rundll32.exe (PID: 4020)
- snetcfg.exe (PID: 3928)
Reads security settings of Internet Explorer
- snetcfg.exe (PID: 3928)
Process drops legitimate windows executable
- 00p-O8jN67Hhy.tmp (PID: 3576)
The process drops C-runtime libraries
- 00p-O8jN67Hhy.tmp (PID: 3576)
INFO
Application launched itself
- iexplore.exe (PID: 1504)
Checks supported languages
- 00p-O8jN67Hhy.exe (PID: 3020)
- 00p-O8jN67Hhy.tmp (PID: 3016)
- 00p-O8jN67Hhy.exe (PID: 3568)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- DriverCacheCleaner.exe (PID: 3756)
- snetcfg.exe (PID: 3928)
- drvinst.exe (PID: 3816)
- nfregdrv.exe (PID: 3732)
- wmpnscfg.exe (PID: 2840)
- wmpnscfg.exe (PID: 1876)
- ExitLag.exe (PID: 3180)
- exitlag_reboot_required.exe (PID: 3428)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1172)
- iexplore.exe (PID: 1504)
Drops the executable file immediately after the start
- iexplore.exe (PID: 1172)
- iexplore.exe (PID: 1504)
The process uses the downloaded file
- iexplore.exe (PID: 1504)
Reads the computer name
- 00p-O8jN67Hhy.tmp (PID: 3016)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- snetcfg.exe (PID: 3928)
- drvinst.exe (PID: 3816)
- nfregdrv.exe (PID: 3732)
- wmpnscfg.exe (PID: 1876)
- ExitLag.exe (PID: 3180)
- wmpnscfg.exe (PID: 2840)
Create files in a temporary directory
- 00p-O8jN67Hhy.exe (PID: 3568)
- 00p-O8jN67Hhy.exe (PID: 3020)
- 00p-O8jN67Hhy.tmp (PID: 3576)
- snetcfg.exe (PID: 3928)
Reads the machine GUID from the registry
- drvinst.exe (PID: 3816)
- snetcfg.exe (PID: 3928)
- ExitLag.exe (PID: 3180)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 4020)
Creates files in the program directory
- 00p-O8jN67Hhy.tmp (PID: 3576)
Adds/modifies Windows certificates
- drvinst.exe (PID: 3816)
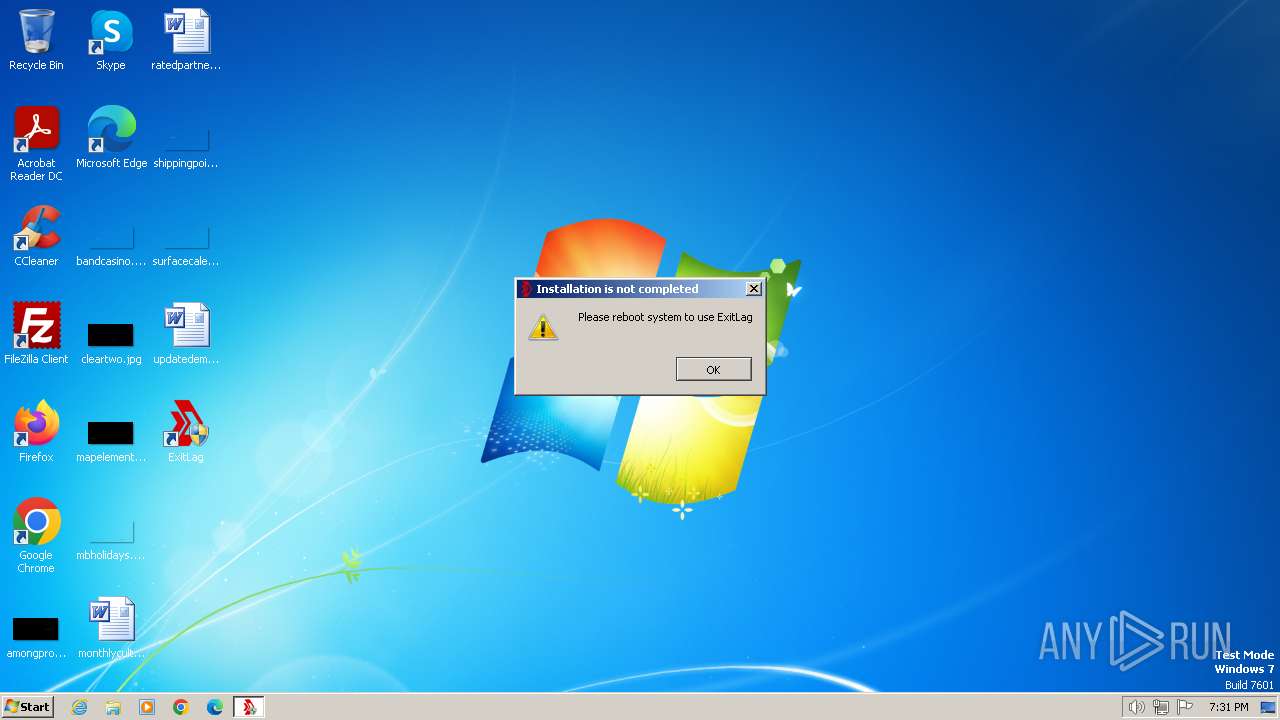
Manual execution by a user
- wmpnscfg.exe (PID: 1876)
- ExitLag.exe (PID: 2860)
- ExitLag.exe (PID: 3180)
- wmpnscfg.exe (PID: 2840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
16
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1172 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1504 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cdn.discordapp.com/attachments/1197975398387036281/1203422107036553256/00p-O8jN67Hhy.exe?ex=65d1092c&is=65be942c&hm=9ec5f74b8e5ae43b0070a899149428894b783bea95945d29676934dfbcad2cd0&" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2860 | "C:\Program Files\ExitLag\ExitLag.exe" | C:\Program Files\ExitLag\ExitLag.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\AppData\Local\Temp\is-BJU00.tmp\00p-O8jN67Hhy.tmp" /SL5="$E018C,21137400,887296,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe" | C:\Users\admin\AppData\Local\Temp\is-BJU00.tmp\00p-O8jN67Hhy.tmp | — | 00p-O8jN67Hhy.exe | |||||||||||
User: admin Company: ExitLag Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3020 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe | iexplore.exe | ||||||||||||
User: admin Company: ExitLag Integrity Level: MEDIUM Description: ExitLag Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3180 | "C:\Program Files\ExitLag\ExitLag.exe" | C:\Program Files\ExitLag\ExitLag.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3010 Modules
| |||||||||||||||
| 3428 | "C:\Program Files\ExitLag\exitlag_reboot_required.exe" | C:\Program Files\ExitLag\exitlag_reboot_required.exe | — | 00p-O8jN67Hhy.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 3568 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe" /SPAWNWND=$E0168 /NOTIFYWND=$E018C | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe | 00p-O8jN67Hhy.tmp | ||||||||||||
User: admin Company: ExitLag Integrity Level: HIGH Description: ExitLag Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
25 856
Read events
25 660
Write events
186
Delete events
10
Modification events
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1504) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
231
Suspicious files
100
Text files
3
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:500B6F1D62C9AD7911C784AD8E5C8B7F | SHA256:846A5579D74A6674EA9E6C8205DD63F4672860F3788D3E1FC0071DE129C0FB41 | |||
| 1172 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YC3GKRMJ.txt | text | |
MD5:F000E739C7FD40BDB97115480986A691 | SHA256:34F104D4468E9512A44F7EB54651429F6CCB819467D0BF442023B87F7307B288 | |||
| 1172 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\00p-O8jN67Hhy[1].exe | executable | |
MD5:7CA28BF9FCB328DE022AF68413846A3E | SHA256:2A69B93C31C7EE264CCC8135CC346B817732D3CE295FA5A3C11B5818472297B4 | |||
| 1172 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\00p-O8jN67Hhy.exe.t2vq8gz.partial | executable | |
MD5:ADD0B0457C0BB673C09AD83639446C8F | SHA256:9D7378349C26CF1A1851D58C07F84620E0A31DC596B390E41FE8CFD0BEE9FAD9 | |||
| 1172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:5014754EEFB023DC992290C871353C4A | SHA256:562135A004F45B7C721F1E419A0250CB2CD92BBF8E8E887A2FA929917747E460 | |||
| 1172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:10326785D5452771F95E30BFBBD7374B | SHA256:BDD0510C10C9CED39C9FEE3656FB117F52D3DF53FBCA178886797EE89B88D810 | |||
| 1504 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB81162D311877752.TMP | binary | |
MD5:359211DA581C22A760ADDDCE09106ED3 | SHA256:02DBA6DBD9FB376FF09F78A8823BCAF36549755DD142F18EB71EC9F922C4F027 | |||
| 3568 | 00p-O8jN67Hhy.exe | C:\Users\admin\AppData\Local\Temp\is-F9MCA.tmp\00p-O8jN67Hhy.tmp | executable | |
MD5:4CC8D57781FB17CFA0E49A3563DB6459 | SHA256:90B1B5537496F1C472124D47516C5127F5C8336E11E2331EDFF9F2F631C9DC93 | |||
| 1504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{A491BE43-C2CA-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:3D268156510397E426BC1E57DFAEEF46 | SHA256:6CAD590346CEE9F760404811181E4B6E502F965040D3B1C0F4181B497DF563AD | |||
| 3576 | 00p-O8jN67Hhy.tmp | C:\Users\admin\AppData\Local\Temp\is-TN8NG.tmp\Nfsdk\nfregdrv.exe | executable | |
MD5:C751F32EE951A89222121EDECEC26B34 | SHA256:EDE186FC9038971FCB70C9C6C379C5D21F7CE6FDEDC7BA7A49C0C2DCECAA9DCC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
15
DNS requests
5
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1172 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?98084960eae7a2ec | unknown | — | — | unknown |
1172 | iexplore.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c23cd8118a42bc | unknown | — | — | unknown |
1172 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
1080 | svchost.exe | GET | 200 | 2.22.242.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89bca2e7018c82c0 | unknown | compressed | 65.2 Kb | unknown |
1080 | svchost.exe | GET | 304 | 2.22.242.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1b8fee253118cbef | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1172 | iexplore.exe | 162.159.129.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
1172 | iexplore.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
1172 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 2.22.242.105:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1172 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1172 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |