| File name: | Dark Bot.exe |
| Full analysis: | https://app.any.run/tasks/d6aaf644-50ea-4d8d-b7e1-bdde56104de9 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 11:08:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4B490DE2B9738D99329D210799B0FA8F |
| SHA1: | 3BF5541C127457F81950574D80FE7CF12D146F4F |
| SHA256: | BCE163EB292303DF9353BCE052FC7242BF573F24ED9751444D3A35EC3A2985E0 |
| SSDEEP: | 49152:M/ZcOUcLRPgex104XINqmFUAhHjuxDjYFibnsLx:MjUcLR3XHmF1jIvC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- Dark Bot.exe (PID: 2372)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:06:21 20:26:03+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 1142784 |
| InitializedDataSize: | 544768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc3508 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.8.0.0 |
| ProductVersionNumber: | 12.8.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
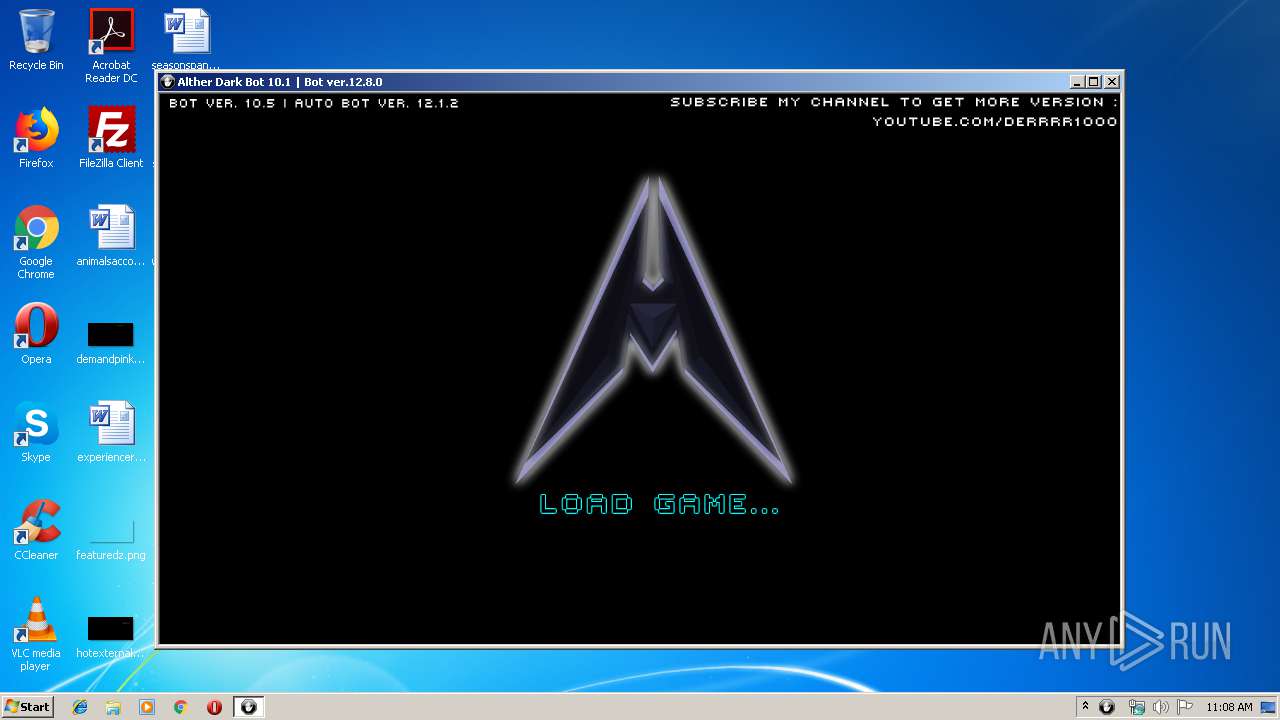
| Comments: | Alther Dark Bot 10.1- Full Version Developed and Created by Giray DE |
| CompanyName: | Alther Dark Bot - by Giray DE |
| FileDescription: | Alther Dark Bot 10.1 - Full Version |
| FileVersion: | 12.8 |
| InternalName: | Alther Dark Bot 10.1 |
| LegalCopyright: | Copyright 2011-2019 |
| LegalTrademarks: | Alther Dark Bot 10.1 - Full Version - by Giray DE |
| OriginalFileName: | Alther Dark Bot 10.1.exe |
| PrivateBuild: | - |
| ProductName: | Alther Dark Bot 10.1 - Full Version - by Giray DE |
| ProductVersion: | 12.8 |
| SpecialBuild: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 21-Jun-2009 18:26:03 |
| Detected languages: |
|
| Comments: | Alther Dark Bot 10.1- Full Version Developed and Created by Giray DE |
| CompanyName: | Alther Dark Bot - by Giray DE |
| FileDescription: | Alther Dark Bot 10.1 - Full Version |
| FileVersion: | 12.8 |
| InternalName: | Alther Dark Bot 10.1 |
| LegalCopyright: | Copyright 2011-2019 |
| LegalTrademarks: | Alther Dark Bot 10.1 - Full Version - by Giray DE |
| OriginalFilename: | Alther Dark Bot 10.1.exe |
| PrivateBuild: | - |
| ProductName: | Alther Dark Bot 10.1 - Full Version - by Giray DE |
| ProductVersion: | 12.8 |
| SpecialBuild: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 21-Jun-2009 18:26:03 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00116A52 | 0x00117000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.67927 |
.rdata | 0x00118000 | 0x0004DE36 | 0x0004E000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.89897 |
.data | 0x00166000 | 0x00010624 | 0x00007000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.61208 |
.rsrc | 0x00177000 | 0x0002FCD4 | 0x00030000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.49114 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.42039 | 1268 | Latin 1 / Western European | English - United States | RT_VERSION |
2 | 4.13758 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.85855 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.78663 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 3.63763 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 2.4028 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 2.68898 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 3.79395 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 2.18351 | 92 | Latin 1 / Western European | English - United States | RT_STRING |
10 | 4.04174 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll (delay-loaded) |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
VERSION.dll |
WINMM.dll |
Total processes
30
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2372 | "C:\Users\admin\AppData\Local\Temp\Dark Bot.exe" | C:\Users\admin\AppData\Local\Temp\Dark Bot.exe | explorer.exe | ||||||||||||
User: admin Company: Alther Dark Bot - by Giray DE Integrity Level: MEDIUM Description: Alther Dark Bot 10.1 - Full Version Exit code: 0 Version: 12.8 Modules
| |||||||||||||||
Total events
80
Read events
60
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_CURRENT_USER\Software\Alther Dark Bot - by Giray DE\Alther Dark Bot 10.1\V12.8\Settings |
| Operation: | write | Name: | crc |
Value: 7CA54CCF350406D799A66715232D9B06 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_CURRENT_USER\Software\Alther Dark Bot - by Giray DE\Alther Dark Bot 10.1\V12.8\Settings |
| Operation: | write | Name: | Options |
Value: 3200000041006C00740068006500720020004400610072006B00200042006F0074002000310030002E00310020002D002000460075006C006C002000560065007200730069006F006E0020002D0020006200790020004700690072006100790020004400450000002400000041006C00740068006500720020004400610072006B00200042006F0074002000310030002E00310020002D002000460075006C006C002000560065007200730069006F006E0000001E00000041006C00740068006500720020004400610072006B00200042006F00740020002D0020006200790020004700690072006100790020004400450000001400000043006F007000790072006900670068007400200032003000310031002D00320030003100390000003200000041006C00740068006500720020004400610072006B00200042006F0074002000310030002E00310020002D002000460075006C006C002000560065007200730069006F006E0020002D0020006200790020004700690072006100790020004400450000004500000041006C00740068006500720020004400610072006B00200042006F0074002000310030002E0031002D002000460075006C006C002000560065007200730069006F006E00200044006500760065006C006F00700065006400200061006E00640020004300720065006100740065006400200062007900200047006900720061007900200044004500000005000000310032002E0038000000000000000001000011010000010000000100000000002600000041006C00740068006500720020004400610072006B00200042006F0074002000310030002E00310020007C00200042006F00740020007600650072002E00310032002E0038002E00300000000000000000000000040000000000000000000000000000000000000001000000000000000000000045000200000100000210000062B337D1934458DCD7D6A81CEA8E76D47C4B3649D470D07C7AD34F776F409823311DE67942FCE9E705693998CC847A4C3F68FBA30BA991C7E5F61BFFFC79E1DD9E5DF46804968BF19D67B539E72AAFAF07010000540068006900730020006A007500730074002000540065007300740069006E0067002000760065007200730069006F006E002C00200070006C006500610073006500200064006F0077006E006C006F006100640020007400680065002000520065006C00650061007300650064002000660075006C006C0020007600650072006900730069006F006E002E00200079006F0075002000630061006E002000660069006E00640020006900740020006F006E00200053004100590020004E004F0020004E0041004D00450020004700550049004C0044002000660061006300650062006F006F006B002000470072006F007500700020003A002000660061006300650062006F006F006B002E0063006F006D002F00670072006F007500700073002F007300610079006E006F006E0061006D00650063006C0061006E00730020006F007200200063006F006E00740061006300740020006D006500200077006900740068002000460061006300650062006F006F006B0020006F007200200045006D00610069006C0020003A0020004700690072006100790064006500760020002D0020006700690072006100790061006C006F006E0073006F00400067006D00610069006C002E0063006F006D002E0020005400680061006E006B007300200066006F00720020007500730069006E0067002000740068006500200041007000700073002E0020003A00440000000000000000000000010000000000000000001300000043006F006E00740061006300740020004D00650020006F006E0020004600420020003A0000001D00000068007400740070003A002F002F00660061006300650062006F006F006B002E0063006F006D002F006700690072006100790064006500760000001800000043006F006E00740061006300740020004D00650020007700690074006800200045006D00610069006C0020003A000000160000006700690072006100790061006C006F006E0073006F00400067006D00610069006C002E0063006F006D0000000000FF000000FF00F5FFFFFF0000000000000000000000009001000000000000010201220E0000004D0053002000530061006E0073002000530065007200690066000000F5FFFFFF0000000000000000000000009001000000000000010201220E0000004D0053002000530061006E0073002000530065007200690066000000101000000000000001000000000000000000010000000000000000000000000000000000E30701000500190011000A00340021010000000001000000000050000000 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2372) Dark Bot.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Dark Bot_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
62
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\#game.aqworlds.com\settings.sxx | — | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\#SharedObjects\8DF5U6SM\game.aqworlds.com\game\gamefiles\Game_20190305.swf\FBTSA.sxx | — | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\#SharedObjects\8DF5U6SM\game.aqworlds.com\AQWUserPref.sxx | — | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\Game_20190305[1].swf | swf | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\#game.aqworlds.com\settings.sol | sol | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Local\Temp\{2EF13A0C-63F8-488C-9377-AC635F28BE46}\_extra\ADB v10.1.swf | swf | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | sol | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\Generic2[1].swf | swf | |
MD5:— | SHA256:— | |||
| 2372 | Dark Bot.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\gameversion[1].htm | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
3
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
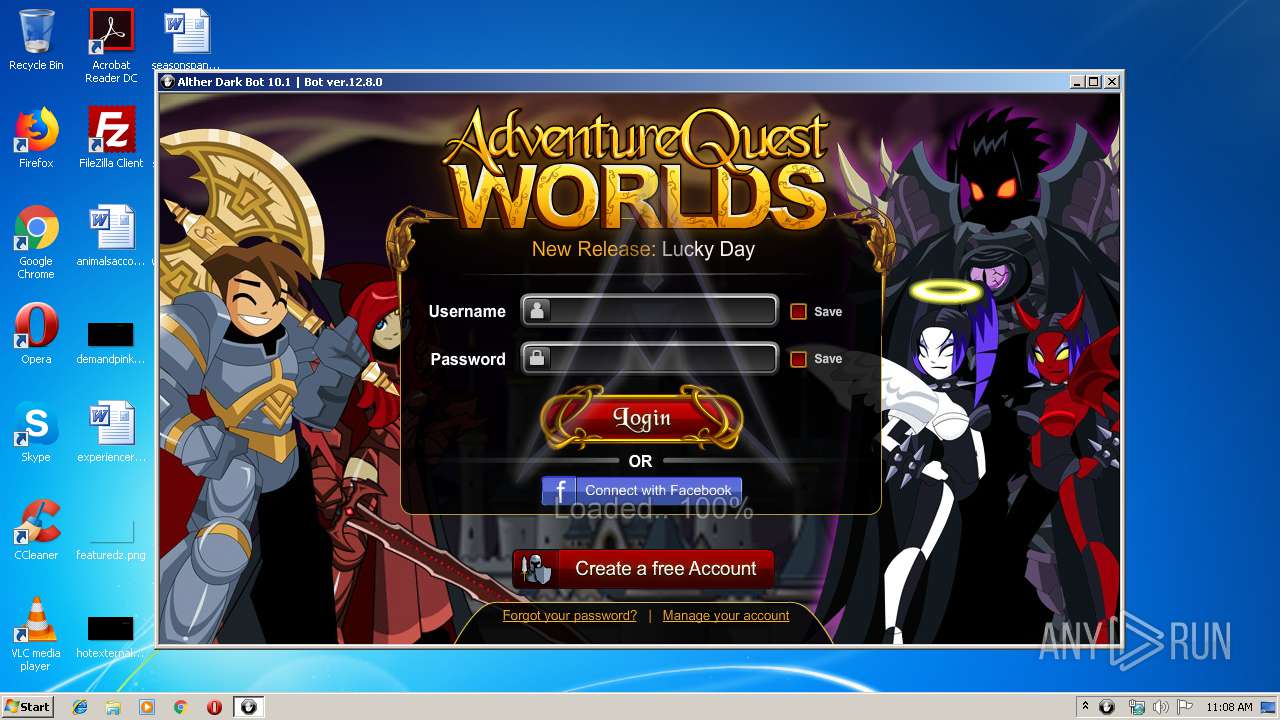
2372 | Dark Bot.exe | GET | 200 | 151.139.128.10:80 | http://aqworldscdn.aq.com/game/gameversion.asp | US | text | 177 b | malicious |
2372 | Dark Bot.exe | GET | 200 | 151.139.128.10:80 | http://aqworldscdn.aq.com/crossdomain.xml | US | xml | 564 b | malicious |
2372 | Dark Bot.exe | GET | 200 | 75.126.77.25:80 | http://game.aqworlds.com/game/gamefiles/Game_20190305.swf | US | swf | 1.67 Mb | suspicious |
2372 | Dark Bot.exe | POST | 413 | 151.139.128.10:80 | http://aqworldscdn.aq.com/game/cf-userlogin.asp?ran=0.4652725604666735 | US | xml | 564 b | malicious |
2372 | Dark Bot.exe | GET | 200 | 75.126.77.25:80 | http://game.aqworlds.com/game/gamefiles/title/Generic2.swf | US | swf | 166 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2372 | Dark Bot.exe | 151.139.128.10:80 | aqworldscdn.aq.com | Highwinds Network Group, Inc. | US | malicious |
2372 | Dark Bot.exe | 75.126.77.25:80 | game.aqworlds.com | SoftLayer Technologies Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aqworldscdn.aq.com |
| malicious |
game.aqworlds.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2372 | Dark Bot.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
2372 | Dark Bot.exe | Potential Corporate Privacy Violation | ET POLICY Http Client Body contains pass= in cleartext |
2372 | Dark Bot.exe | Potential Corporate Privacy Violation | ET POLICY Http Client Body contains pwd= in cleartext |