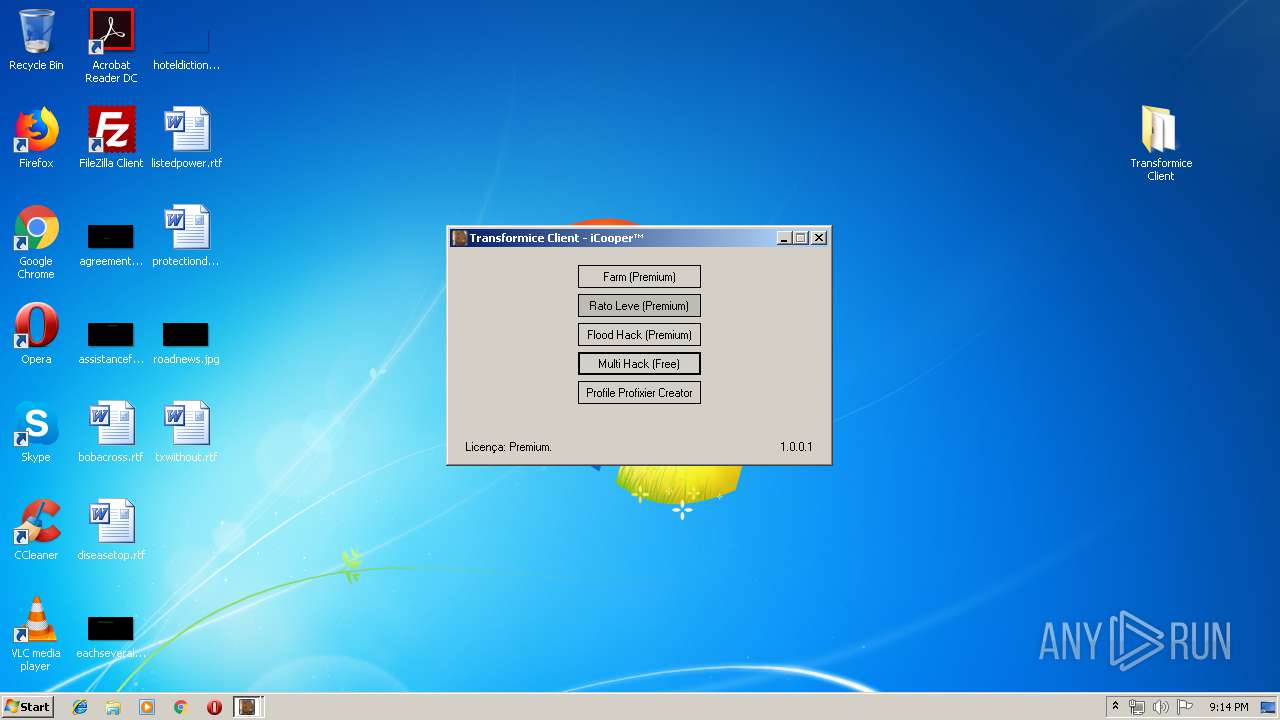
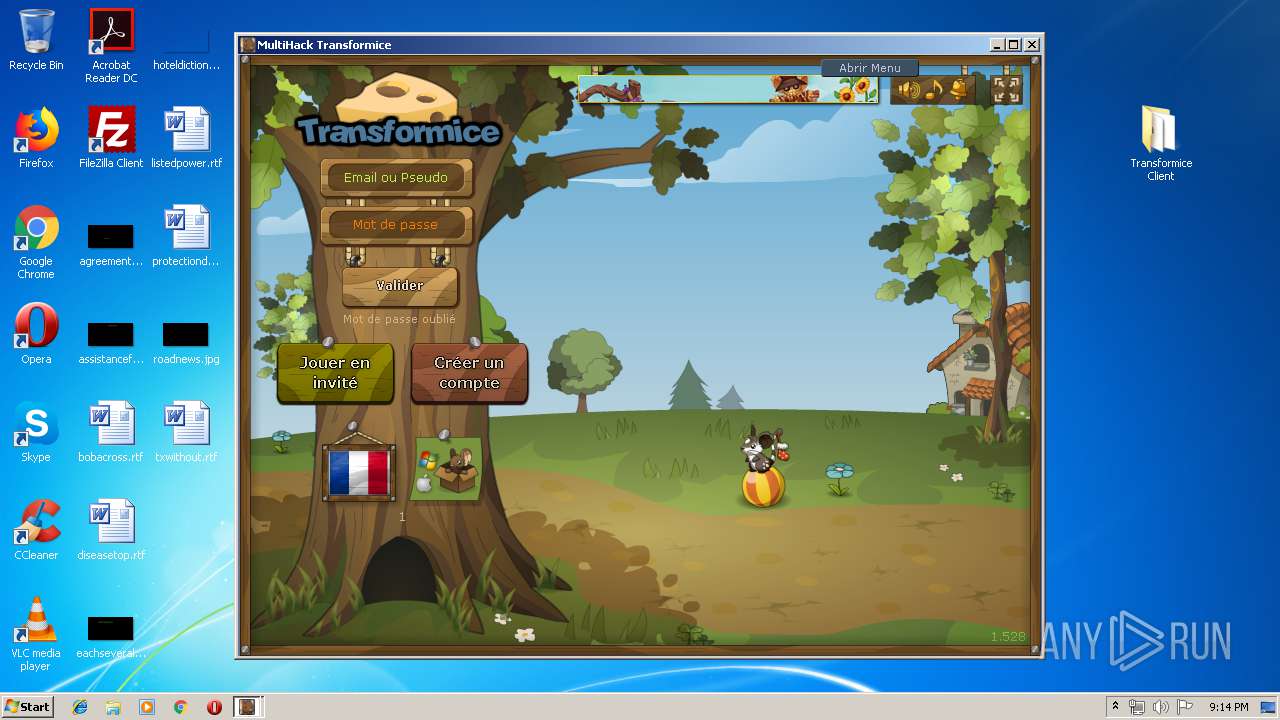
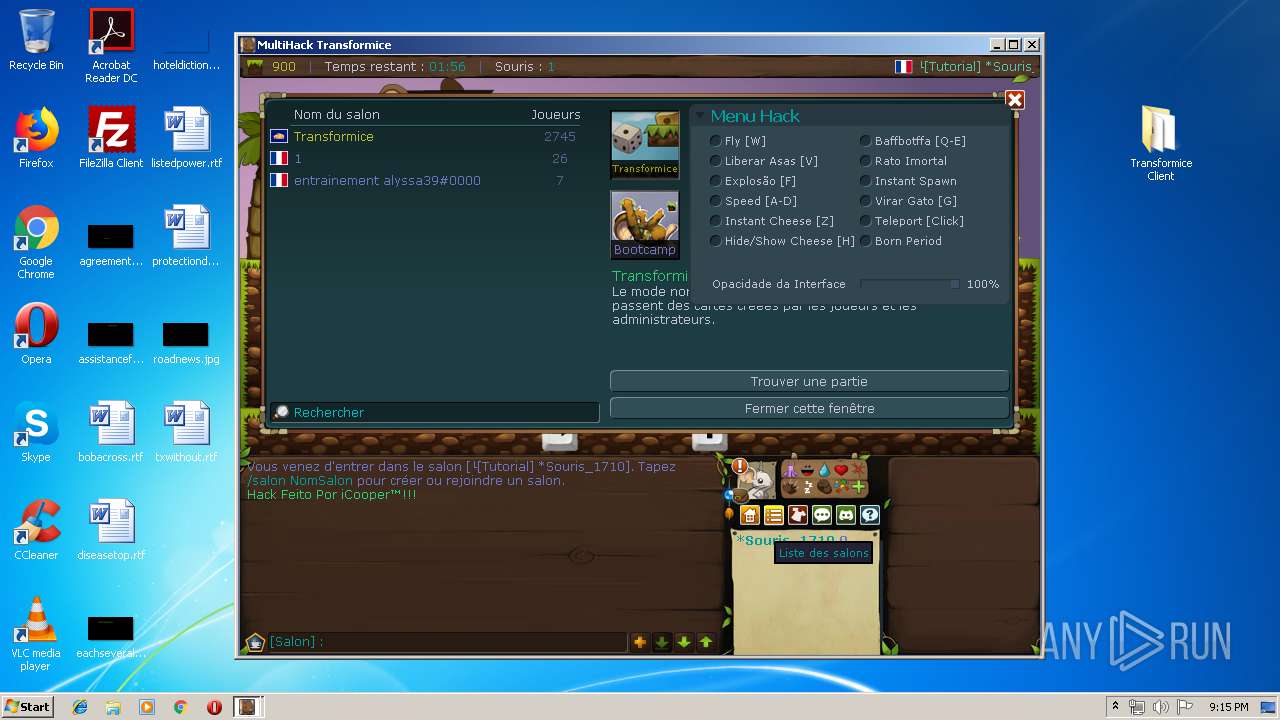
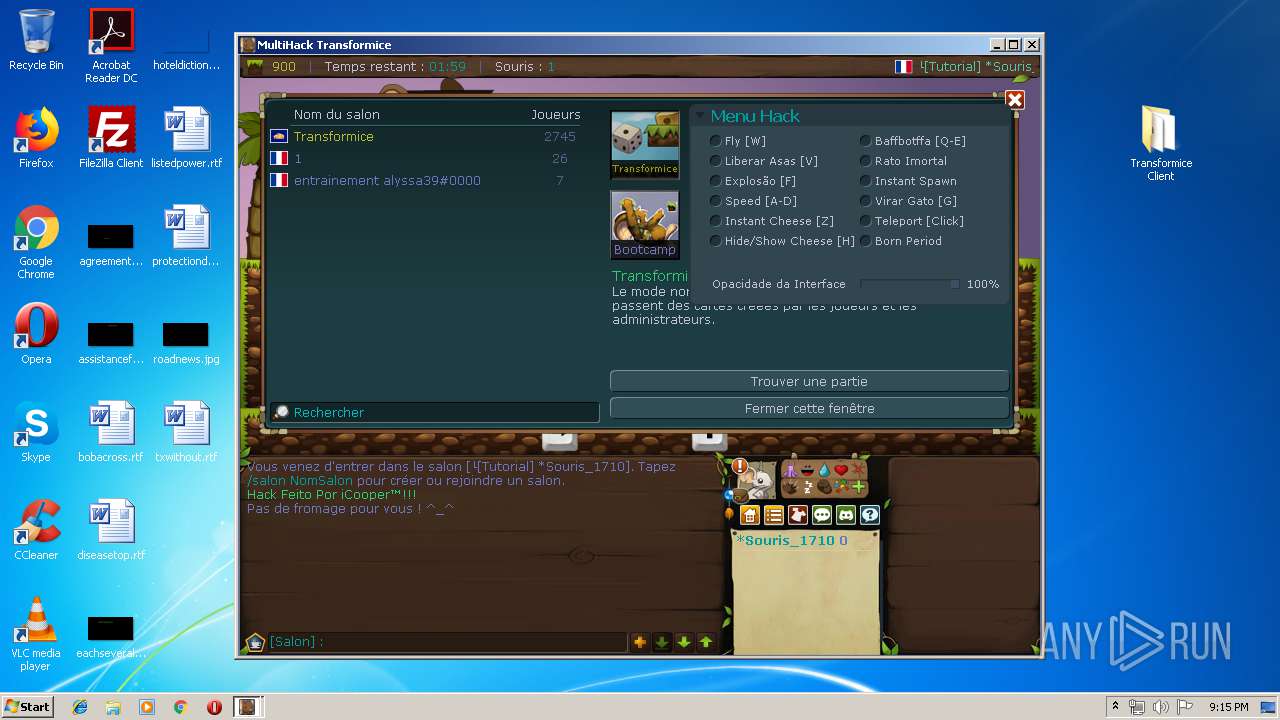
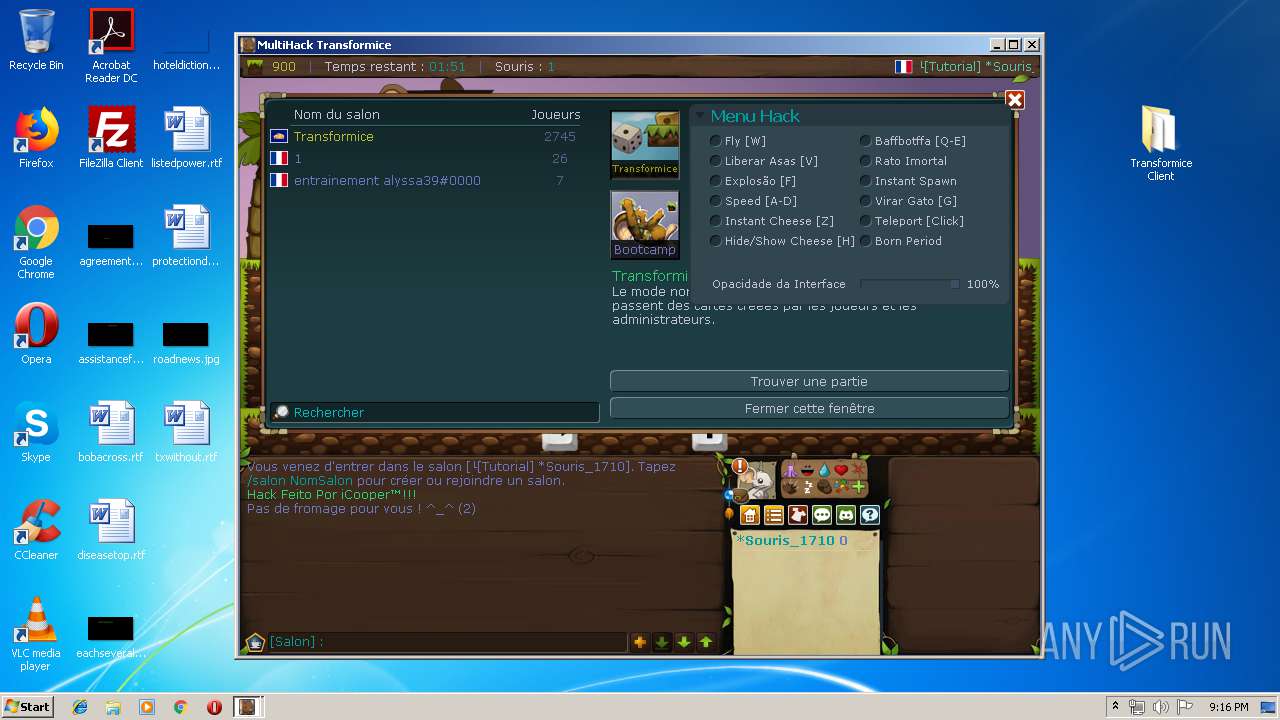
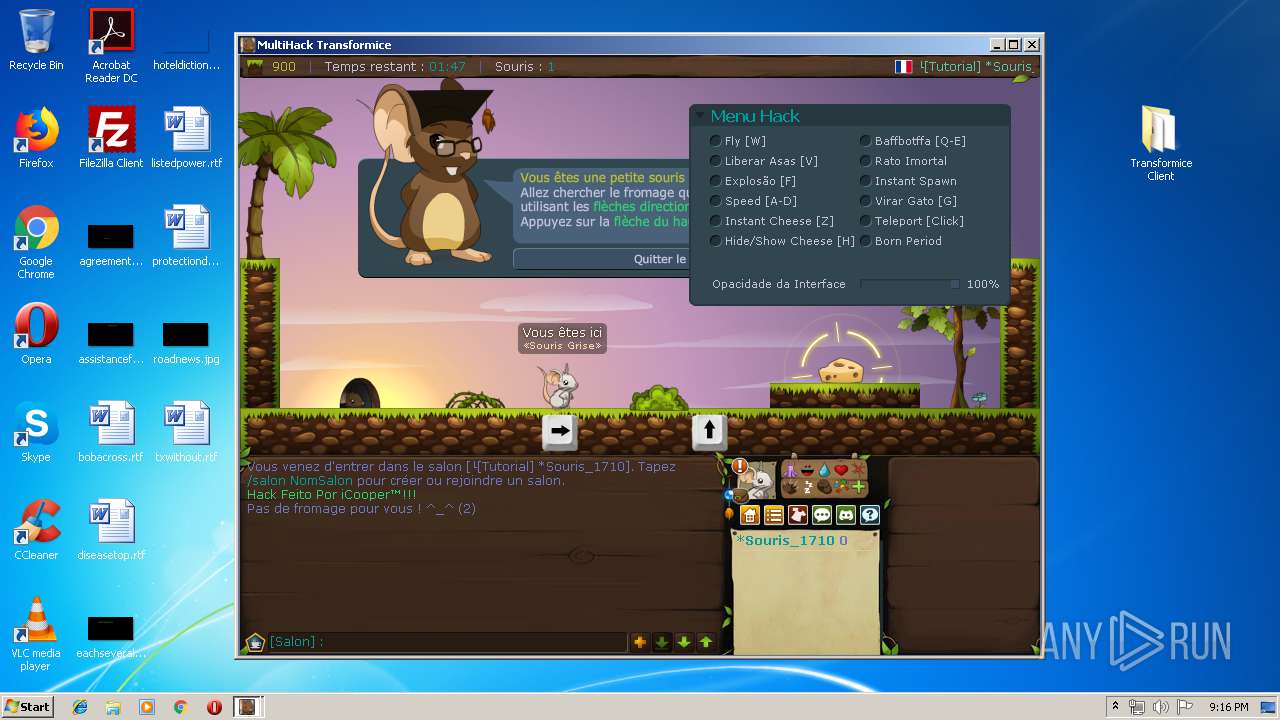
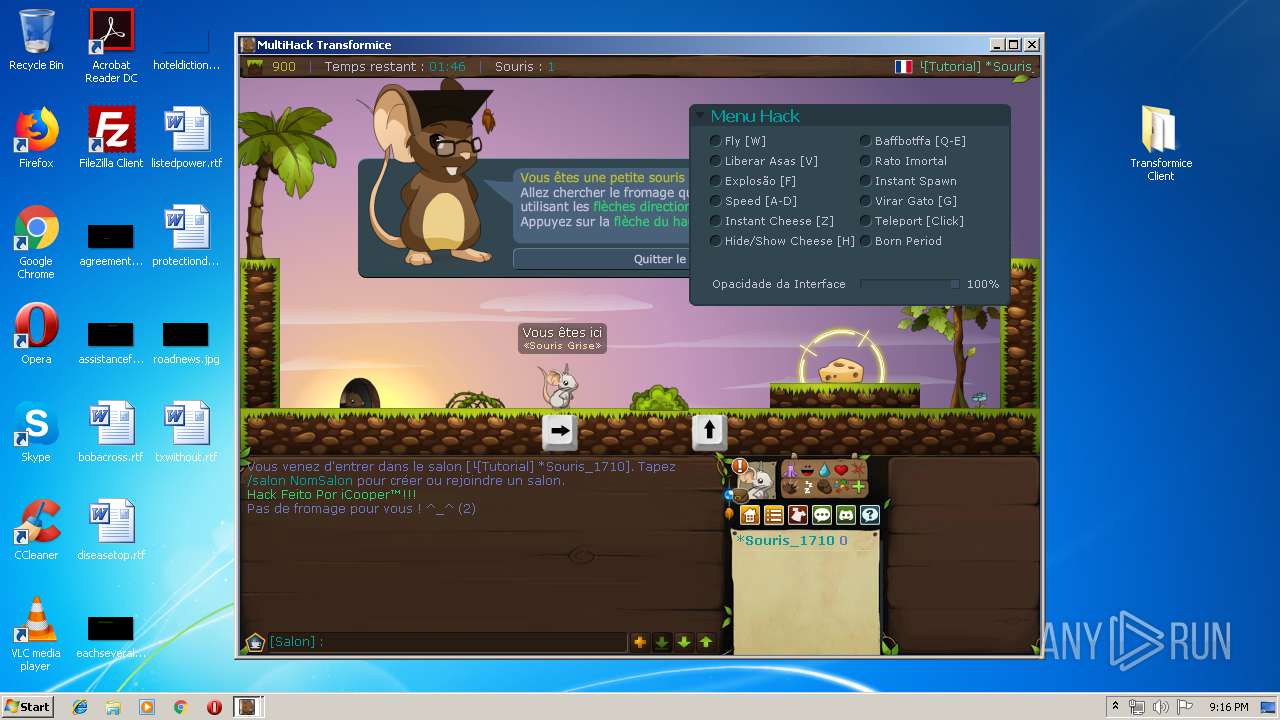
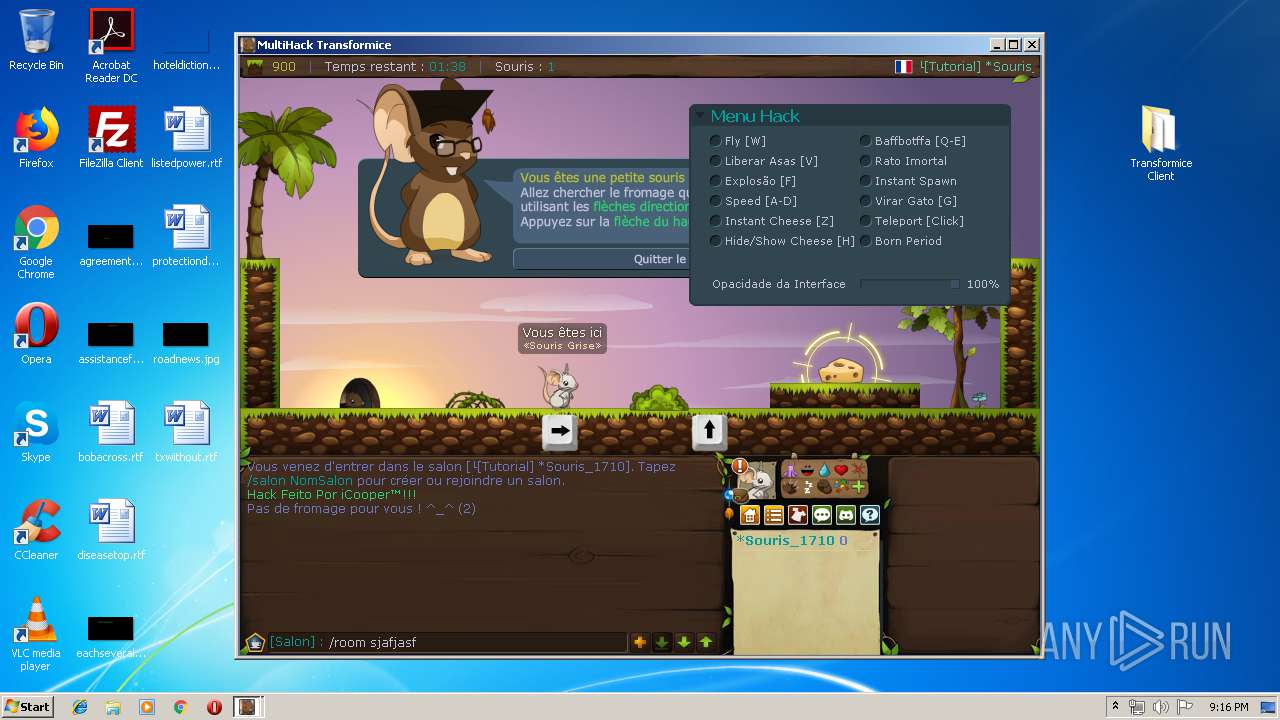
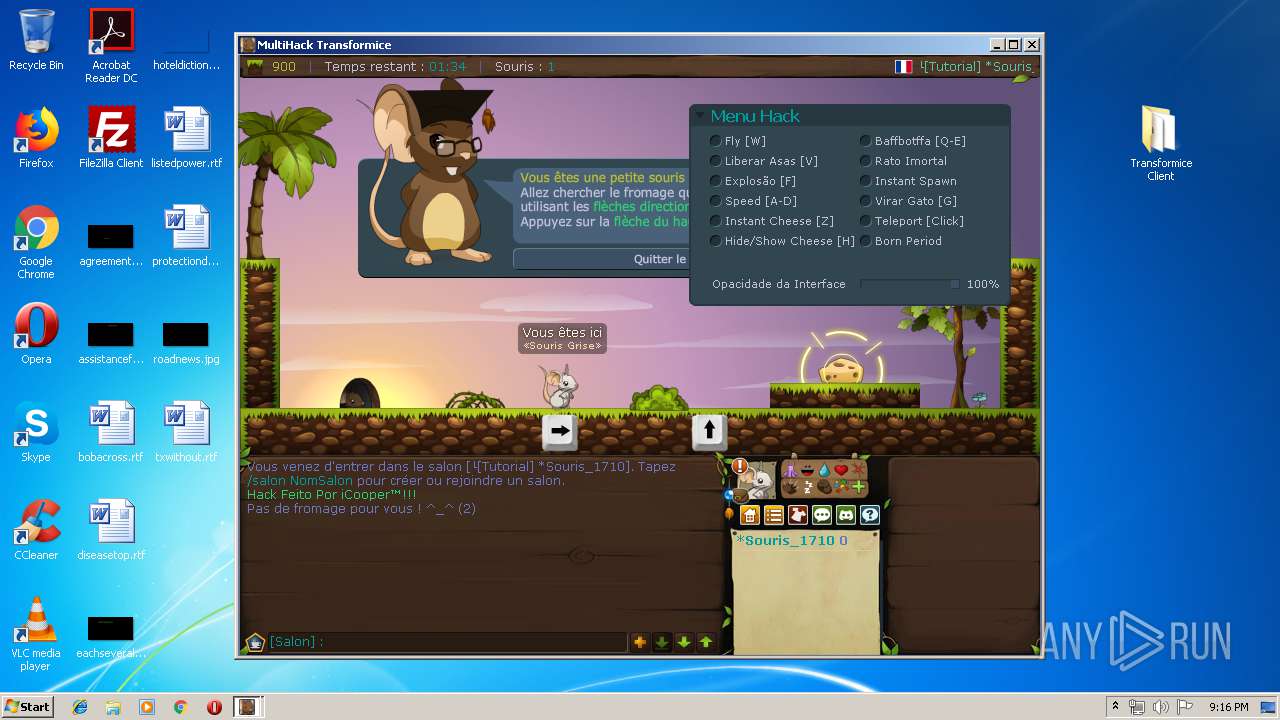
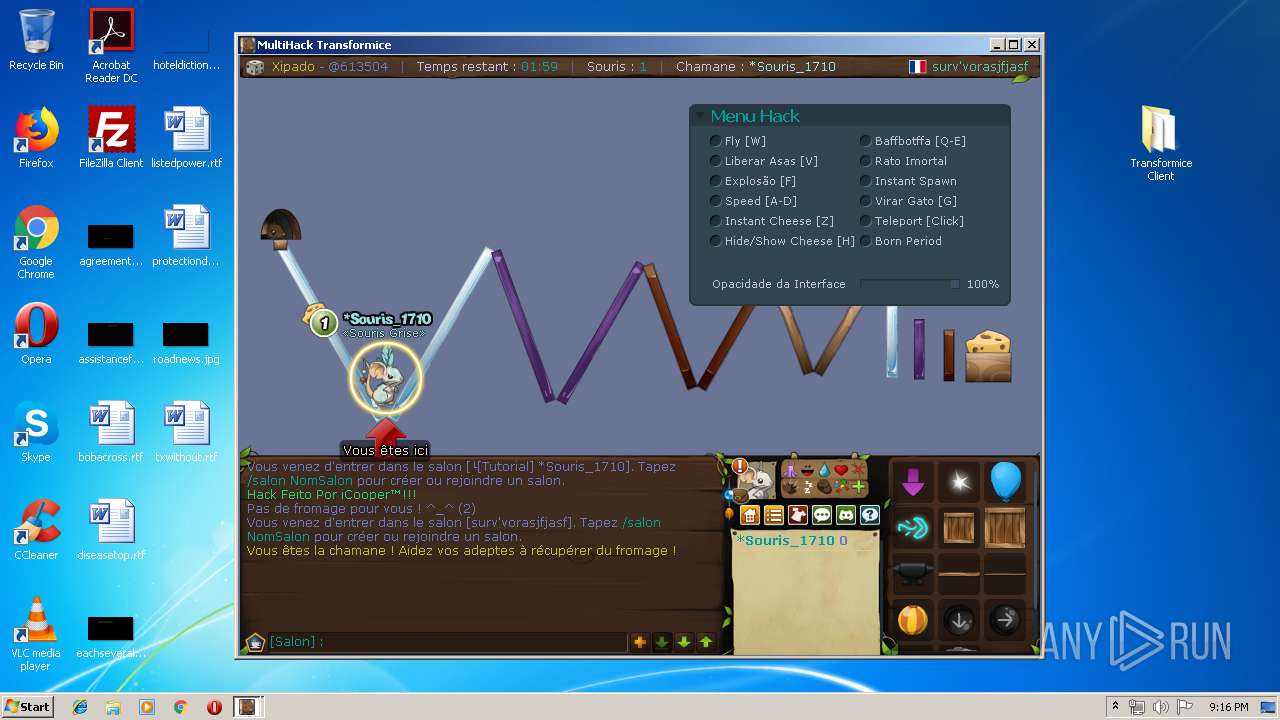
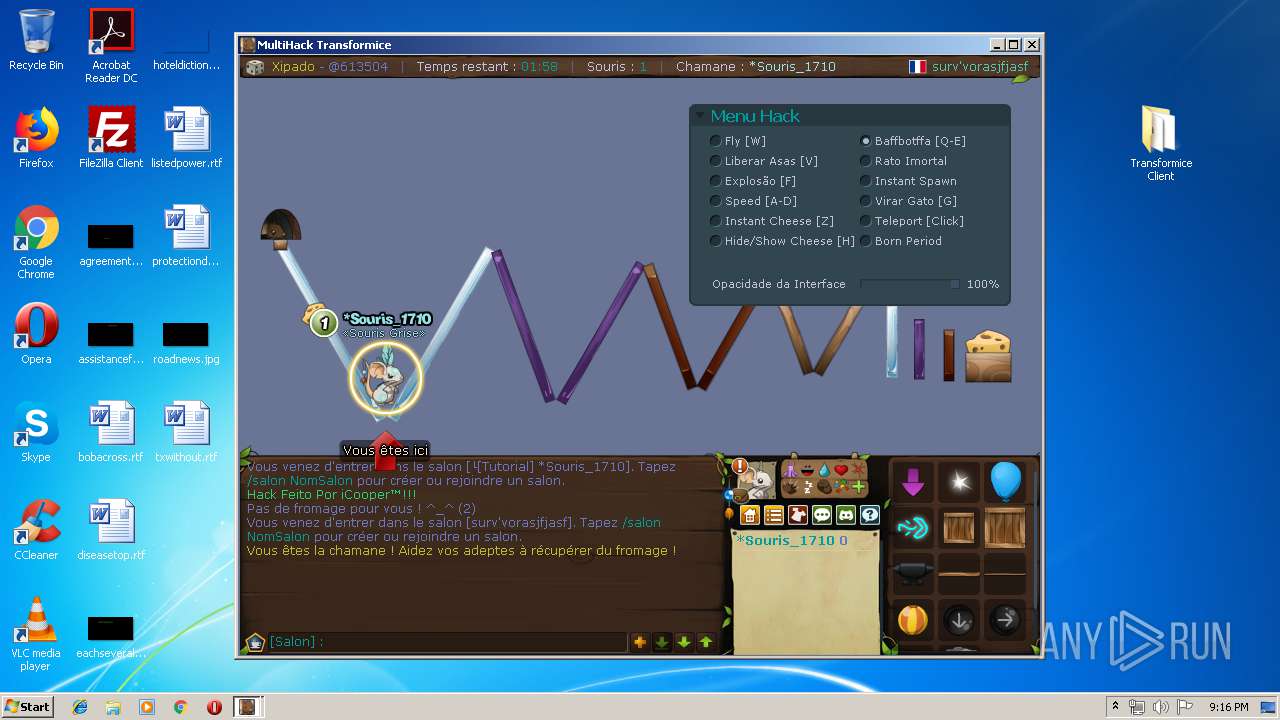
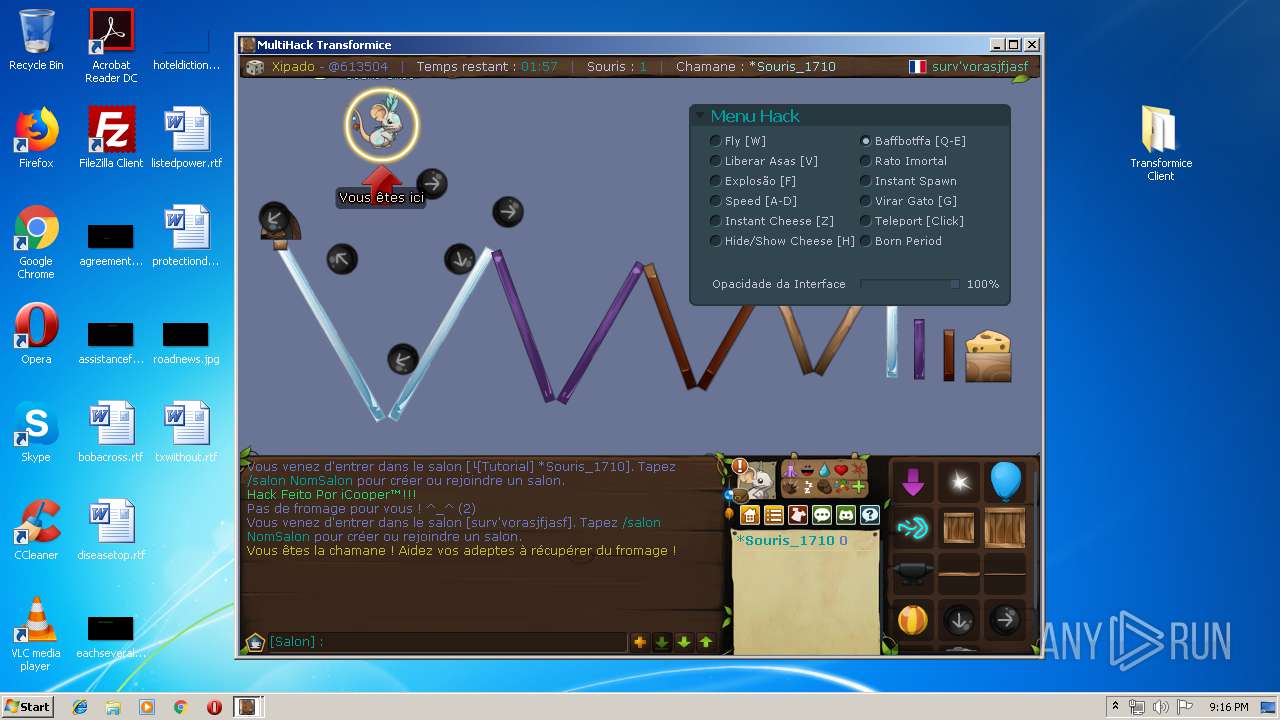
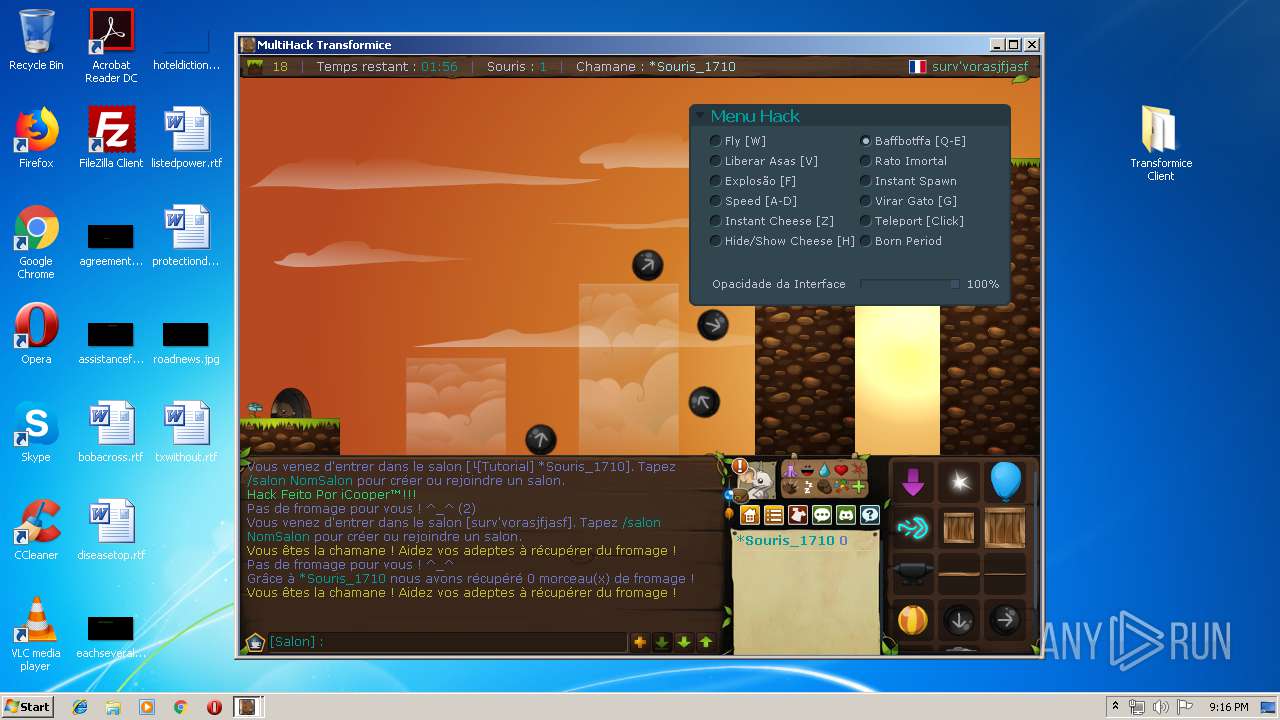
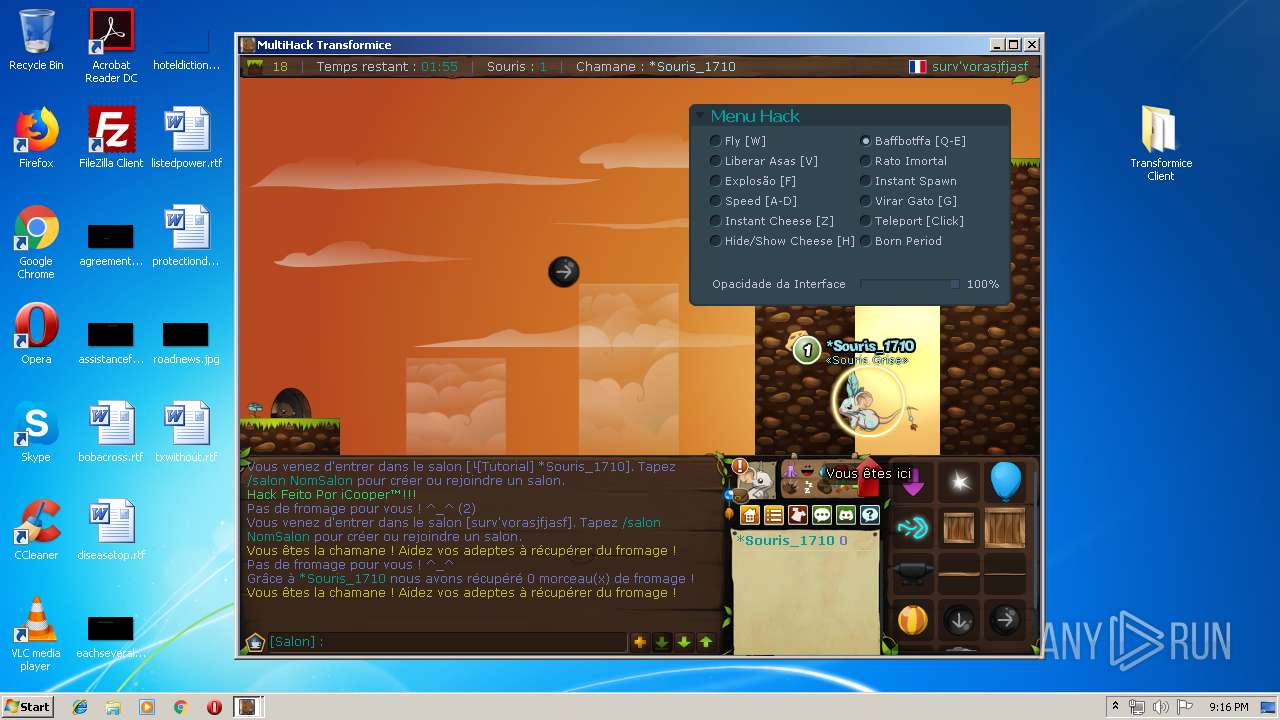
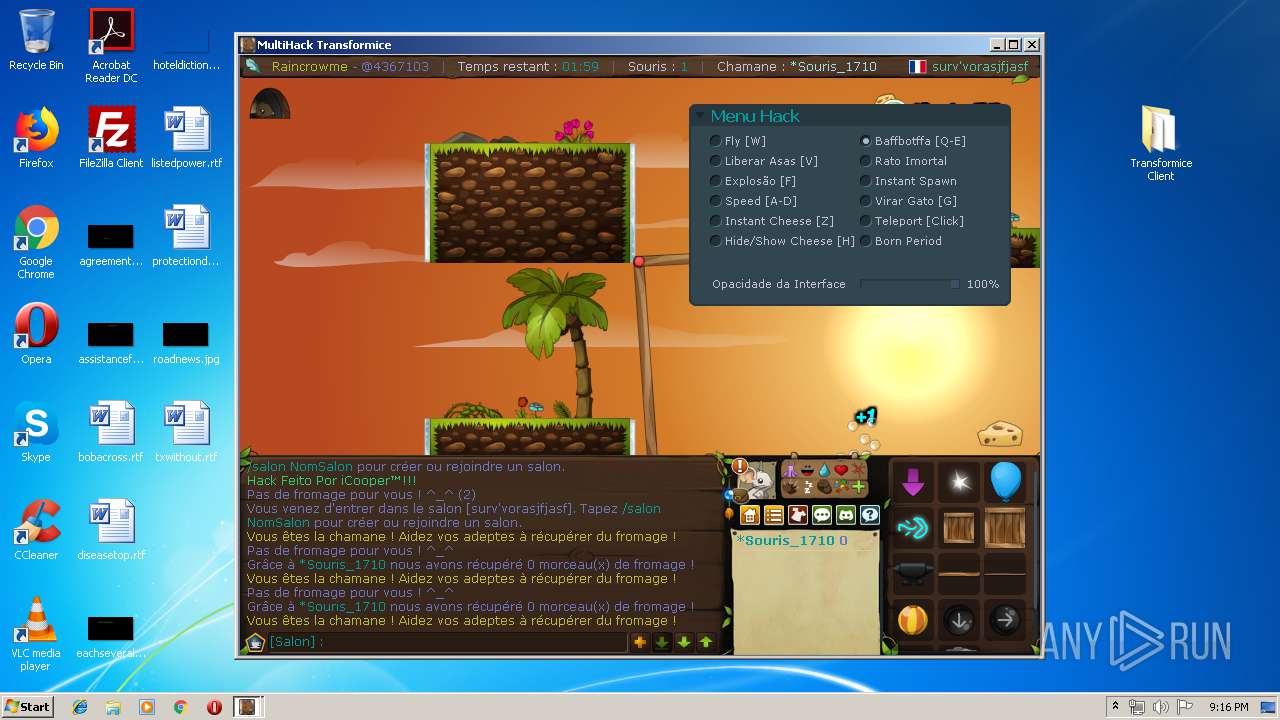
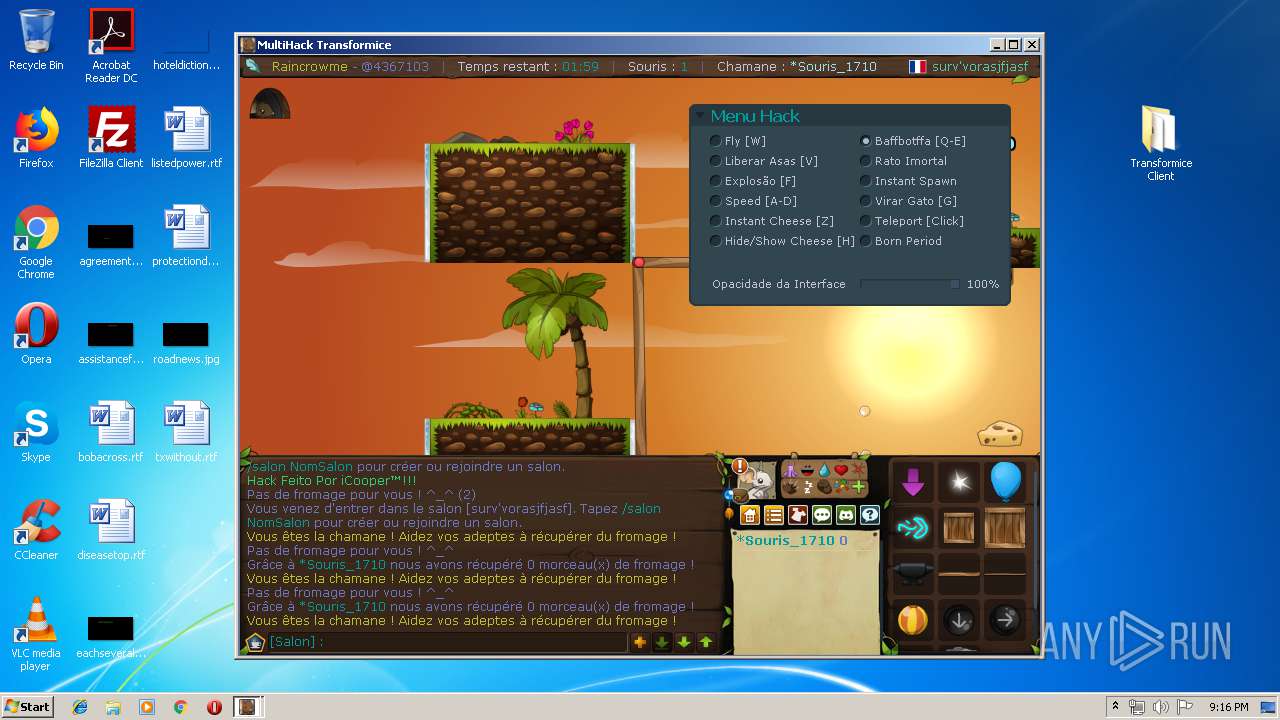
| File name: | TransformiceClient.rar |
| Full analysis: | https://app.any.run/tasks/80a11a0b-da3c-49f2-ba8d-9319b6eef324 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 20:13:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 591B852995418A6100A965A7E98A0737 |
| SHA1: | C809DFFCD912237400EE36F6233FC04DEF90D61D |
| SHA256: | BCE00529092236DADE7F702C5E16868B3C6C4EF6202F4A3CA5AFF38ED26FB4EA |
| SSDEEP: | 49152:cFKPQBtqHZJ1ZUzcSYw7vrHpskyBbZNJyQDyF3tSVH8Q:GKPQBtqHFy4StvjKk87DugVH8Q |
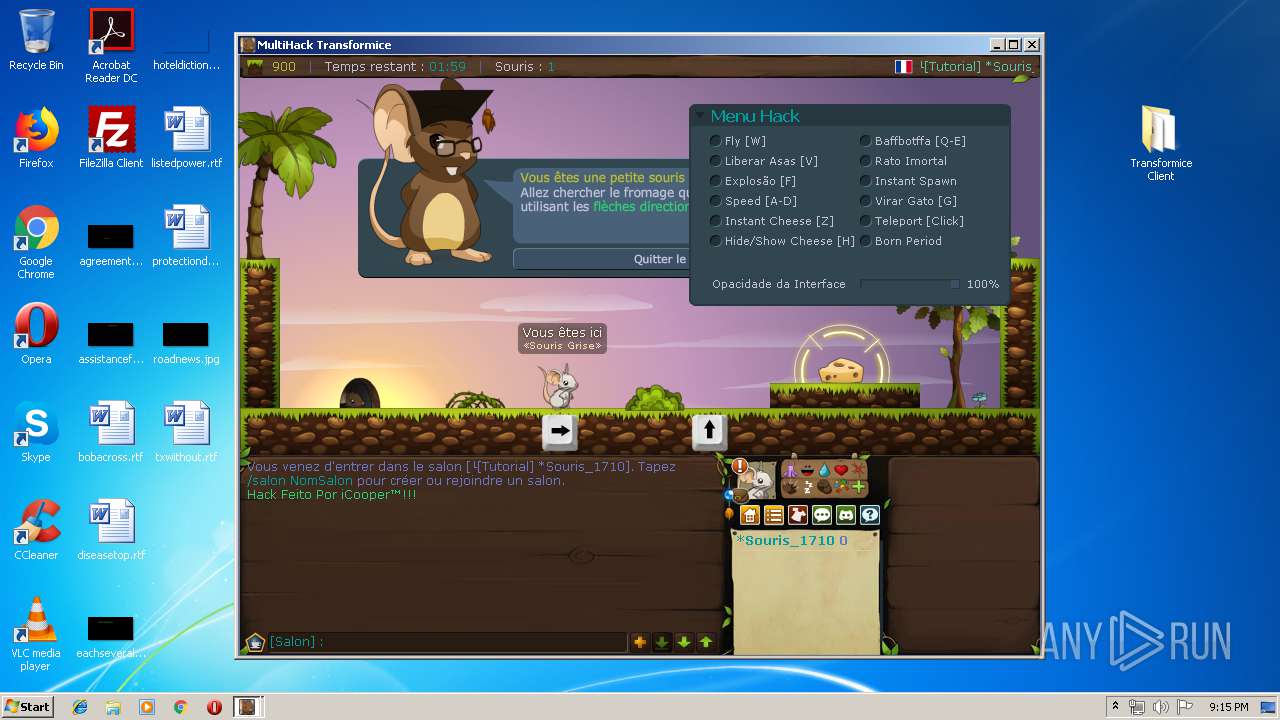
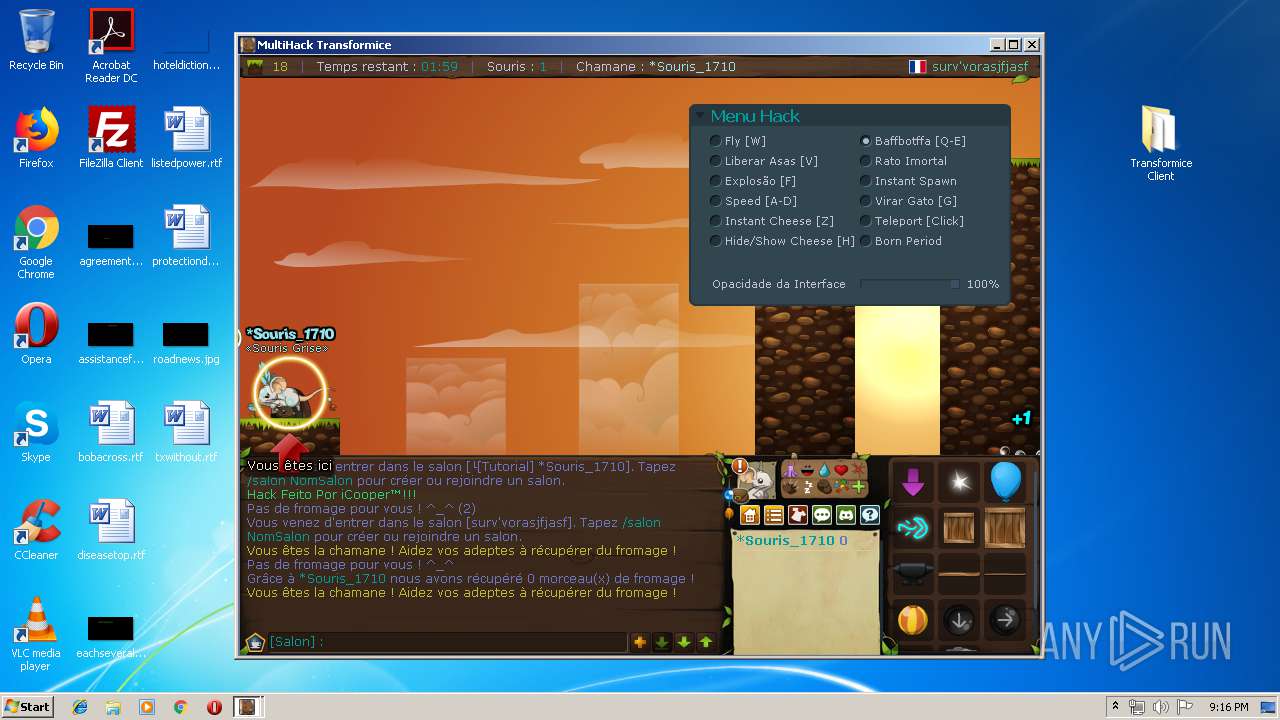
MALICIOUS
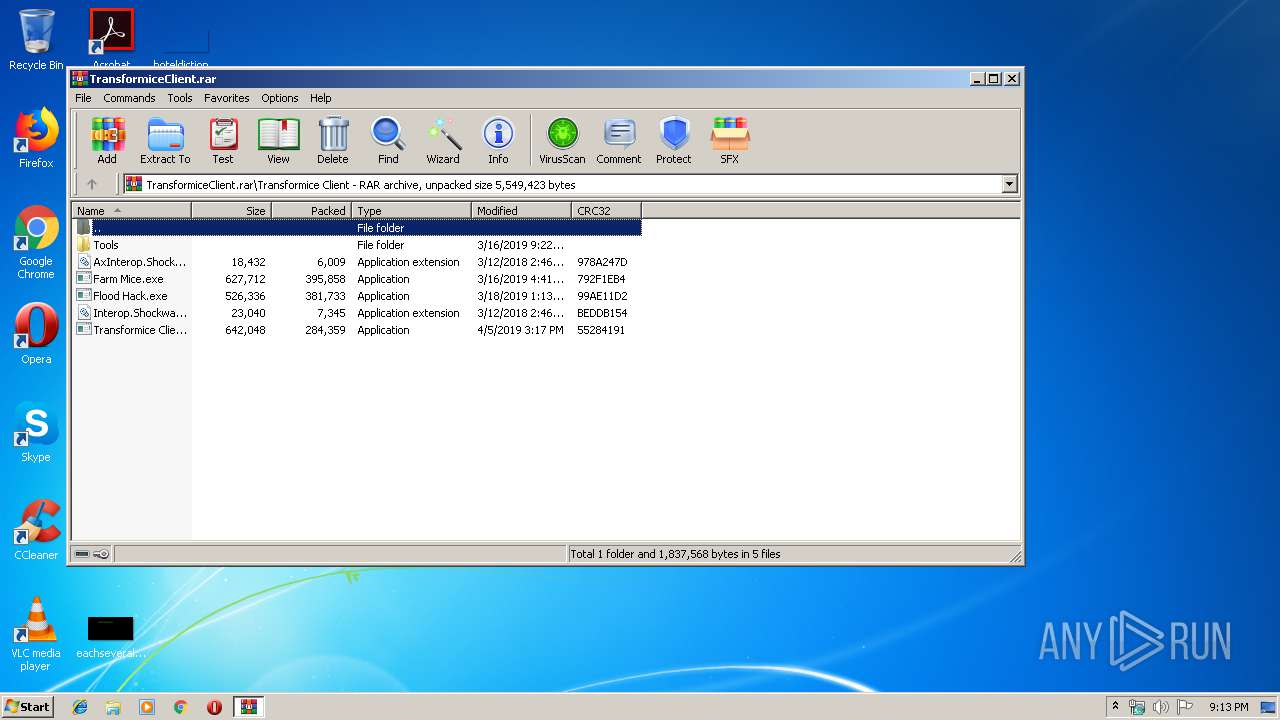
Application was dropped or rewritten from another process
- Transformice Client.exe (PID: 4076)
- abcexport.exe (PID: 2444)
- rabcdasm.exe (PID: 3872)
- swfdecript.exe (PID: 2672)
- swfdump.exe (PID: 3616)
- rabcdasm.exe (PID: 3512)
- abcexport.exe (PID: 3040)
- rabcasm.exe (PID: 840)
- abcreplace.exe (PID: 3068)
Loads dropped or rewritten executable
- abcexport.exe (PID: 2444)
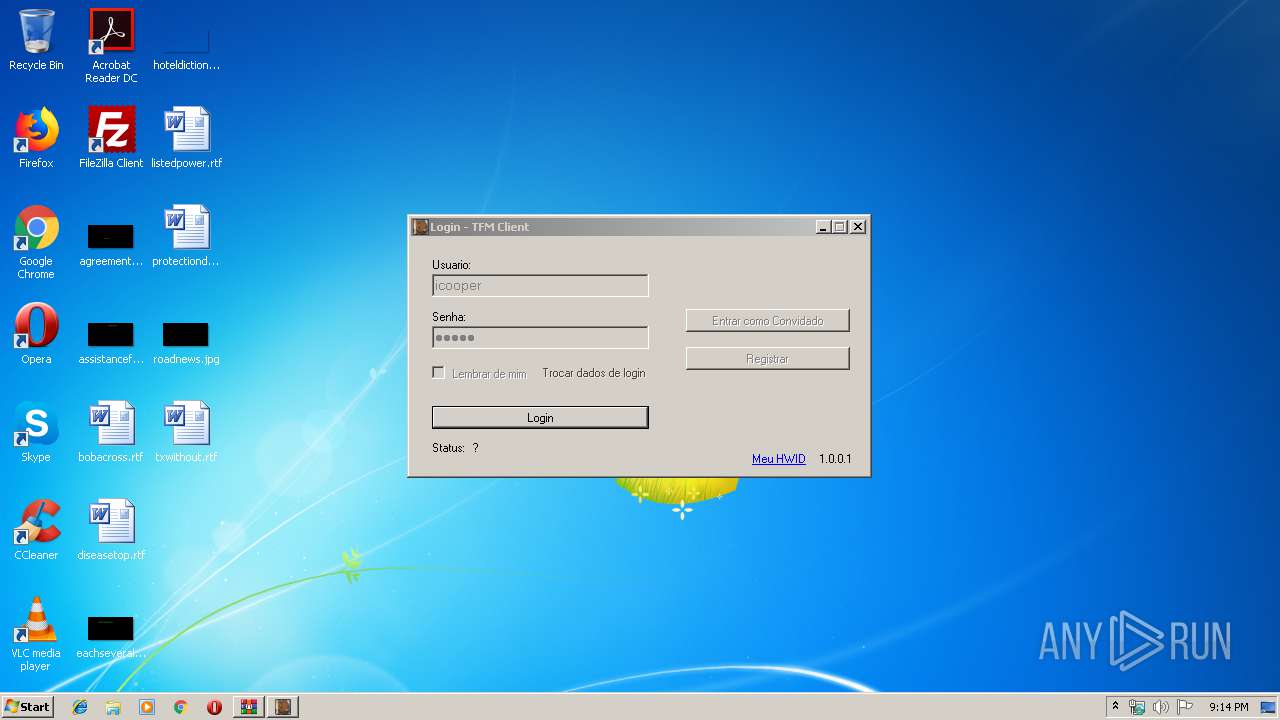
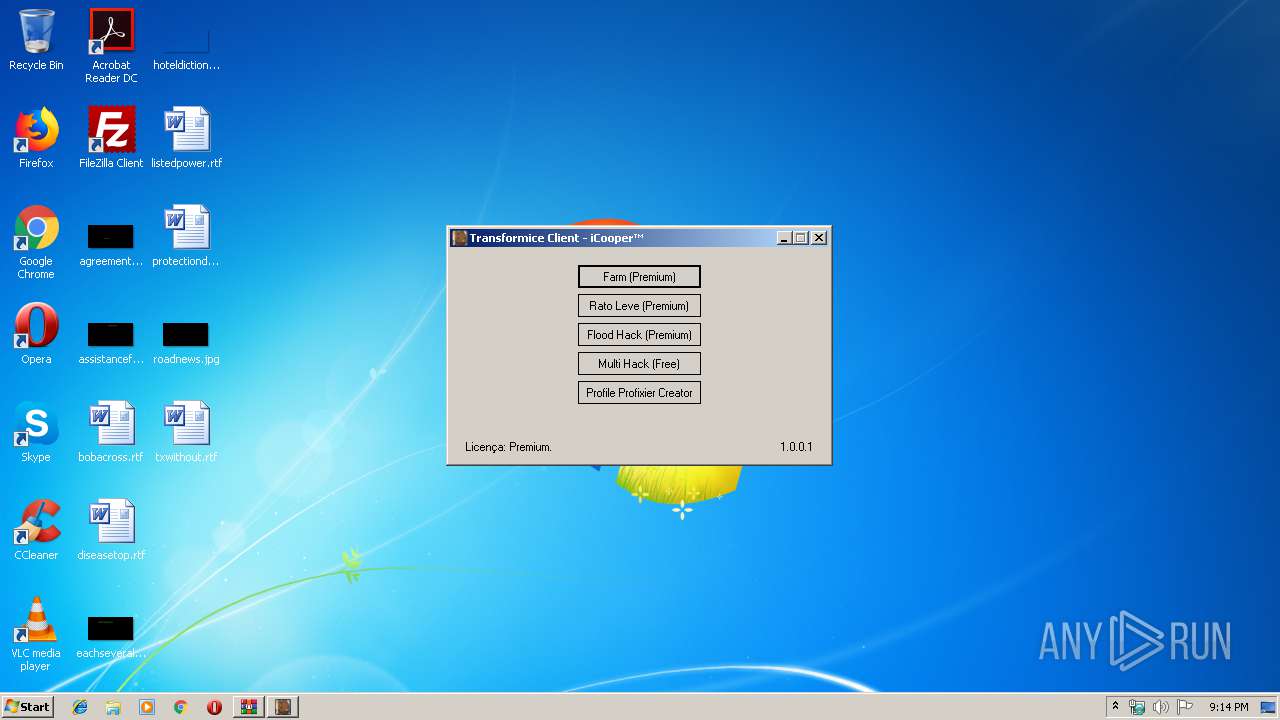
- Transformice Client.exe (PID: 4076)
- abcexport.exe (PID: 3040)
- abcreplace.exe (PID: 3068)
- SearchProtocolHost.exe (PID: 856)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3144)
Creates files in the user directory
- abcexport.exe (PID: 3040)
- Transformice Client.exe (PID: 4076)
- abcexport.exe (PID: 2444)
- rabcasm.exe (PID: 840)
- rabcdasm.exe (PID: 3872)
- rabcdasm.exe (PID: 3512)
Reads internet explorer settings
- Transformice Client.exe (PID: 4076)
Reads Internet Cache Settings
- Transformice Client.exe (PID: 4076)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3144)
Reads settings of System Certificates
- Transformice Client.exe (PID: 4076)
Manual execution by user
- taskmgr.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
55
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
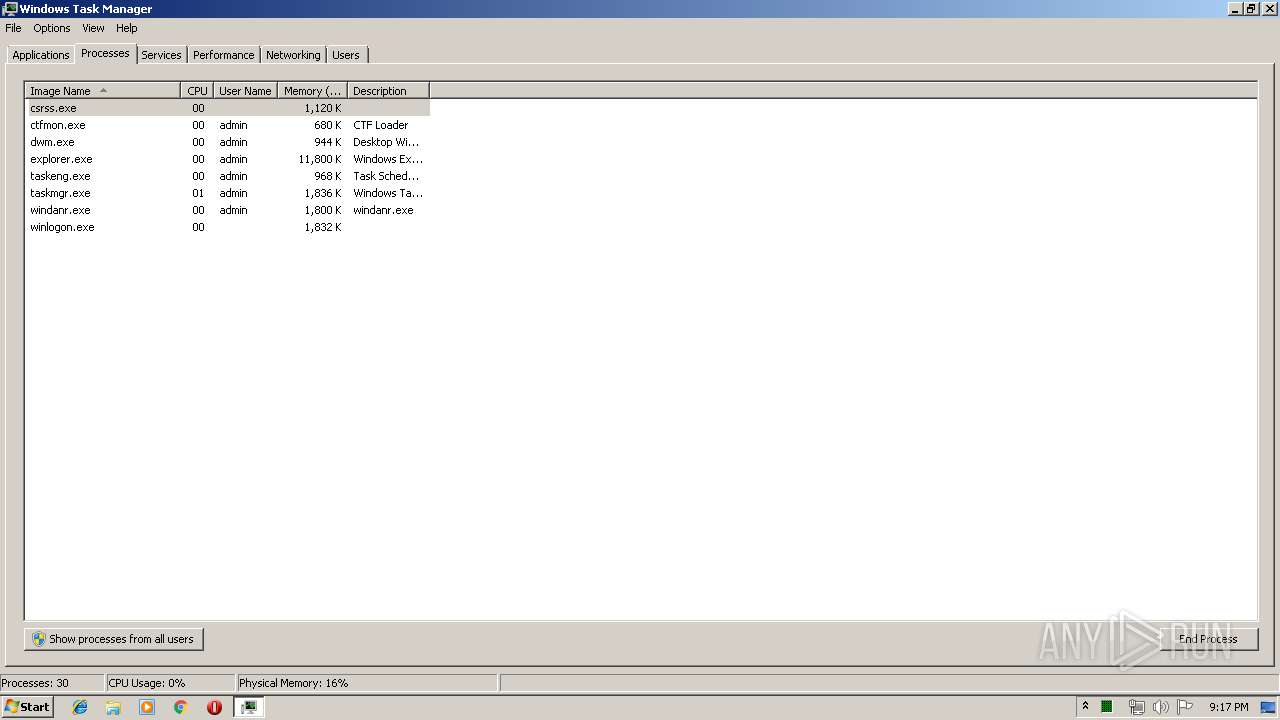
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 840 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\rabcasm.exe" Chargeur-0/Chargeur-0.main.asasm | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\rabcasm.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 856 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe7_ Global\UsGthrCtrlFltPipeMssGthrPipe7 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcexport.exe" Transformice.swf | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcexport.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\swfdecript.exe" Transformice.swf Transformice.swf | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\swfdecript.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcexport.exe" Chargeur.swf | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcexport.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3068 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcreplace.exe" Chargeur.swf 0 Chargeur-0/Chargeur-0.main.abc | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcreplace.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TransformiceClient.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3392 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3512 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\rabcdasm.exe" Transformice-0.abc | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\rabcdasm.exe | — | Transformice Client.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3616 | "swfdump.exe" -a "C:\Users\admin\AppData\Roaming\iCooper\Multi\Transformice.swf" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\swfdump.exe | — | swfdecript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 269
Read events
1 218
Write events
51
Delete events
0
Modification events
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TransformiceClient.rar | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
12
Suspicious files
3
Text files
2 682
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Flood Hack.exe | executable | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Transformice Client.exe | executable | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\AxInterop.ShockwaveFlashObjects.dll | executable | |
MD5:— | SHA256:— | |||
| 3040 | abcexport.exe | C:\Users\admin\AppData\Roaming\iCooper\Multi\Chargeur-0.abc | binary | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Interop.ShockwaveFlashObjects.dll | executable | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Farm Mice.exe | executable | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\abcexport.exe | executable | |
MD5:5FB748BE478DB6282BBDEBF7D5887849 | SHA256:CD2957356F5AA384EC66F4A02BF0987A2665C406AD68B2D7E48DA1732806FBF7 | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\swfdecript.exe | executable | |
MD5:B2838DF135FE035279E47343492B0DB5 | SHA256:FAEF2860350CCF11B3F4BA1A39C194B461F022044814B5CDF68BF2EC47C94F4D | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\rabcasm.exe | executable | |
MD5:A71C93BB550C24DB1EDB27212783EE6F | SHA256:C02A62FA65831F0D165AAD63F9CF589BCB3800A9C1391050A076049014FCBDAC | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3144.4637\Transformice Client\Tools\liblzma.dll | executable | |
MD5:0E5D3BC6FF20B7F7C82824E1D5E3512C | SHA256:4F920F7AC2904171CB0F265239EE2225ACB19769D3D438566C0D43E857DEE8A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
11
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_bibliotheques/x_fourrures.swf?d=528.94?d=528 | FR | swf | 153 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_bibliotheques/x_pictos_editeur.swf?d=528.94?d=528 | FR | swf | 218 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 51.75.128.119:80 | http://transformice.com/Transformice.swf | GB | swf | 1.99 Mb | whitelisted |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_bibliotheques/x_meli_costumes.swf?d=528.94?d=528 | FR | swf | 398 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/langues/tfz_fr?d=94 | FR | pz | 35.4 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_transformice/x_interface/3.png?d=94 | FR | image | 793 b | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_illu_tribu.jpg?d=94 | FR | image | 15.4 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_illu_amis.jpg?d=94 | FR | image | 11.9 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_bibliotheques/x_fourrures2.swf?d=528.94?d=528 | FR | swf | 179 Kb | suspicious |
4076 | Transformice Client.exe | GET | 200 | 145.239.9.124:80 | http://www.transformice.com/images/x_transformice/x_aventure/x_banniere/x_21.jpg?d=94 | FR | image | 6.96 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4076 | Transformice Client.exe | 172.217.23.174:443 | docs.google.com | Google Inc. | US | whitelisted |
4076 | Transformice Client.exe | 172.217.18.97:443 | doc-04-08-docs.googleusercontent.com | Google Inc. | US | whitelisted |
4076 | Transformice Client.exe | 51.75.128.119:80 | transformice.com | — | GB | suspicious |
4076 | Transformice Client.exe | 94.23.193.229:12801 | — | OVH SAS | FR | unknown |
4076 | Transformice Client.exe | 46.105.100.198:12801 | — | OVH SAS | FR | unknown |
4076 | Transformice Client.exe | 145.239.9.124:80 | transformice.com | OVH SAS | FR | suspicious |
4076 | Transformice Client.exe | 195.154.124.74:80 | — | Online S.a.s. | FR | unknown |
4076 | Transformice Client.exe | 188.165.220.57:13801 | — | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docs.google.com |
| shared |
doc-04-08-docs.googleusercontent.com |
| shared |
transformice.com |
| whitelisted |
www.transformice.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4076 | Transformice Client.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |
4076 | Transformice Client.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |