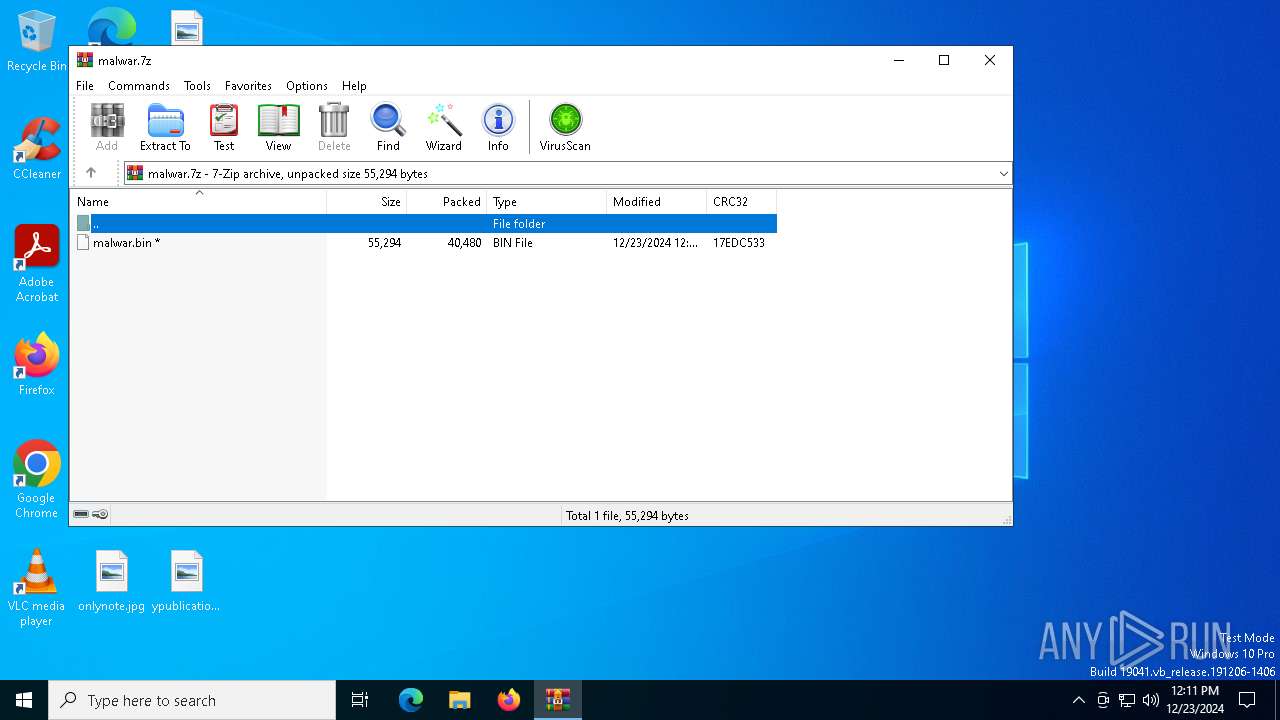
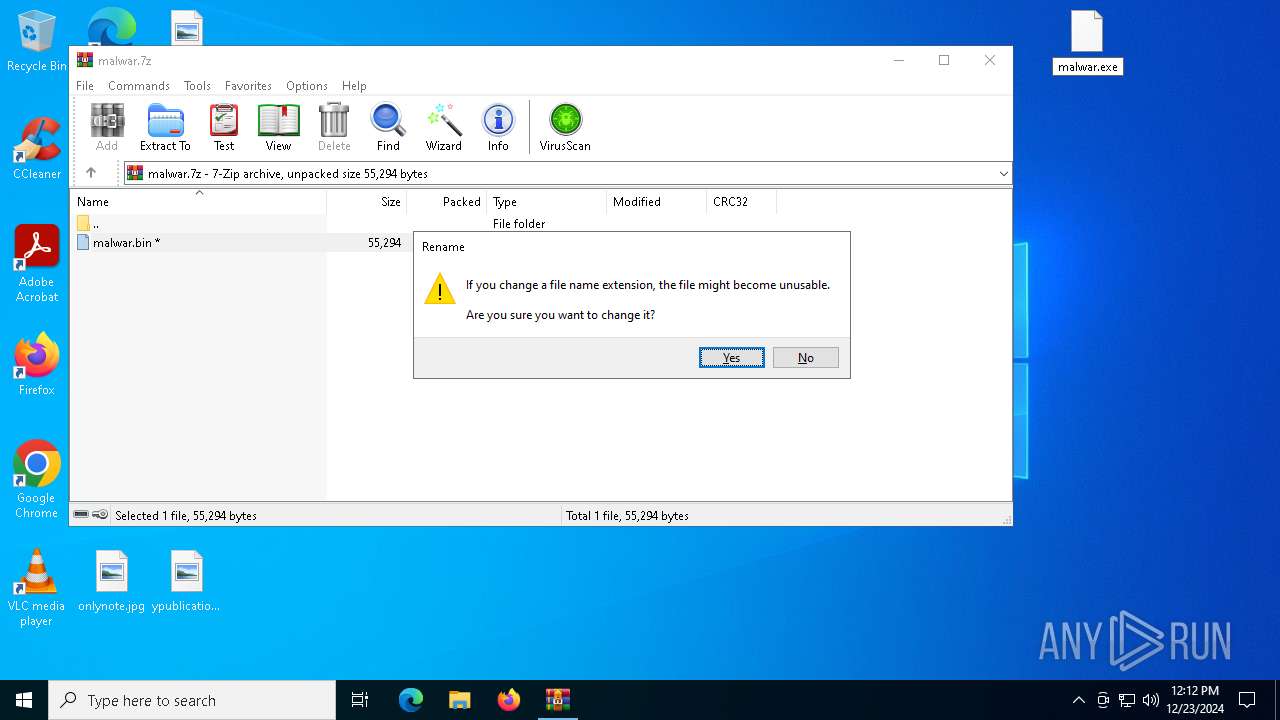
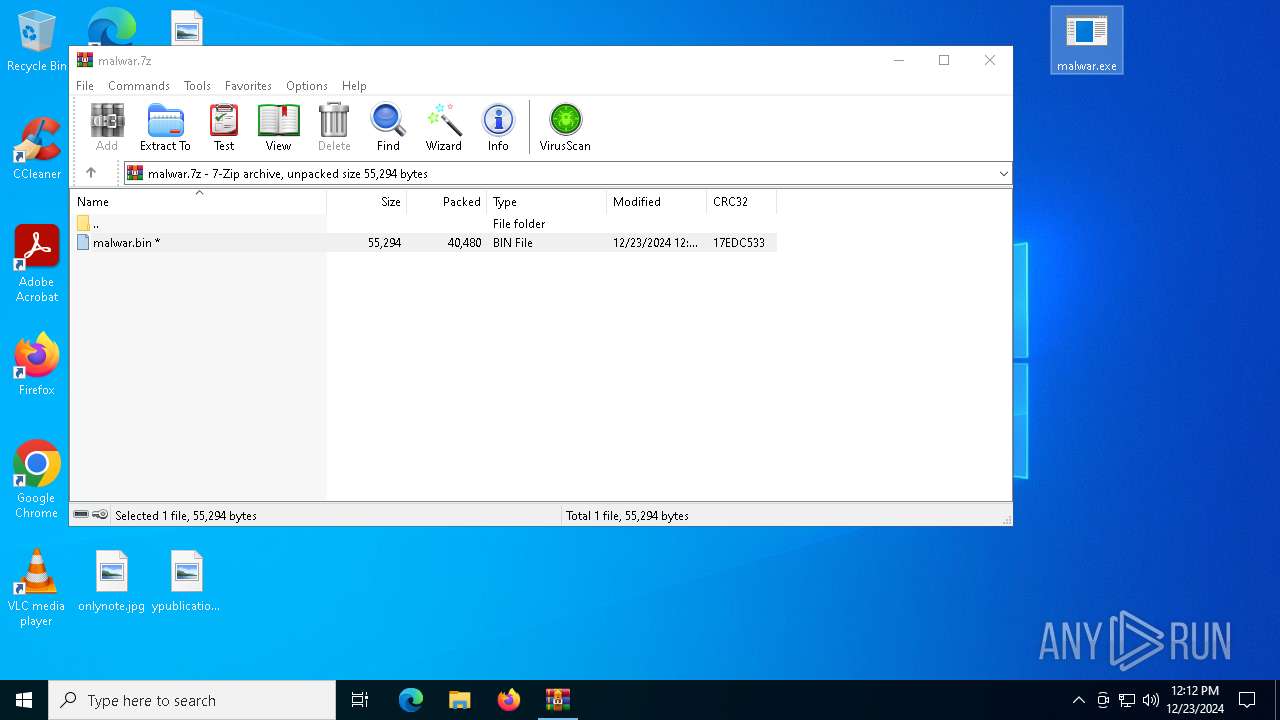
| File name: | malwar.7z |
| Full analysis: | https://app.any.run/tasks/086e4a32-8835-4aea-8bc3-bb3ae849f31a |
| Verdict: | Malicious activity |
| Analysis date: | December 23, 2024, 12:11:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3FFBF553AB5143E3608EC1F5F06586FA |
| SHA1: | 95373B7C7E845868D13F541BAD947EBCDC2DBDF7 |
| SHA256: | BCCC23AFE6C9EE225AEC02A2FE4E44C4D6CE537B44282C73BBBDADF5CE2A9184 |
| SSDEEP: | 1536:7YrZXWz+8dL3Mc0eF3APerQ5gdel/RBR8:clWzprMXcAyclpBR8 |
MALICIOUS
UAC/LUA settings modification
- malwar.exe (PID: 7052)
- malwar.exe (PID: 1616)
Changes Security Center notification settings
- malwar.exe (PID: 7052)
- malwar.exe (PID: 1616)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 4640)
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 6068)
Checks Windows Trust Settings
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Application launched itself
- CCleaner64.exe (PID: 6068)
Searches for installed software
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 6088)
Checks for external IP
- CCleaner64.exe (PID: 6068)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5464)
Reads the computer name
- malwar.exe (PID: 7052)
- ShellExperienceHost.exe (PID: 4640)
- CCleaner64.exe (PID: 6068)
The process uses the downloaded file
- WinRAR.exe (PID: 5464)
- CCleaner64.exe (PID: 6068)
Manual execution by a user
- malwar.exe (PID: 7052)
- malwar.exe (PID: 1616)
- CCleaner64.exe (PID: 6068)
Checks supported languages
- malwar.exe (PID: 7052)
- malwar.exe (PID: 1616)
- ShellExperienceHost.exe (PID: 4640)
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Reads Environment values
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
UPX packer has been detected
- malwar.exe (PID: 7052)
- malwar.exe (PID: 1616)
Reads CPU info
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
The sample compiled with english language support
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Reads the machine GUID from the registry
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Sends debugging messages
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Process checks computer location settings
- CCleaner64.exe (PID: 6068)
Creates files or folders in the user directory
- CCleaner64.exe (PID: 6068)
Reads the software policy settings
- CCleaner64.exe (PID: 6068)
Checks proxy server information
- CCleaner64.exe (PID: 6068)
Reads product name
- CCleaner64.exe (PID: 6068)
- CCleaner64.exe (PID: 6088)
Creates files in the program directory
- CCleaner64.exe (PID: 6088)
- CCleaner64.exe (PID: 6068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:23 12:09:15+00:00 |
| ArchivedFileName: | malwar.bin |
Total processes
138
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1616 | "C:\Users\admin\Desktop\malwar.exe" | C:\Users\admin\Desktop\malwar.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4640 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\malwar.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6068 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | explorer.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 6088 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
| 7052 | "C:\Users\admin\Desktop\malwar.exe" | C:\Users\admin\Desktop\malwar.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
21 835
Read events
21 647
Write events
135
Delete events
53
Modification events
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\malwar.7z | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5464) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
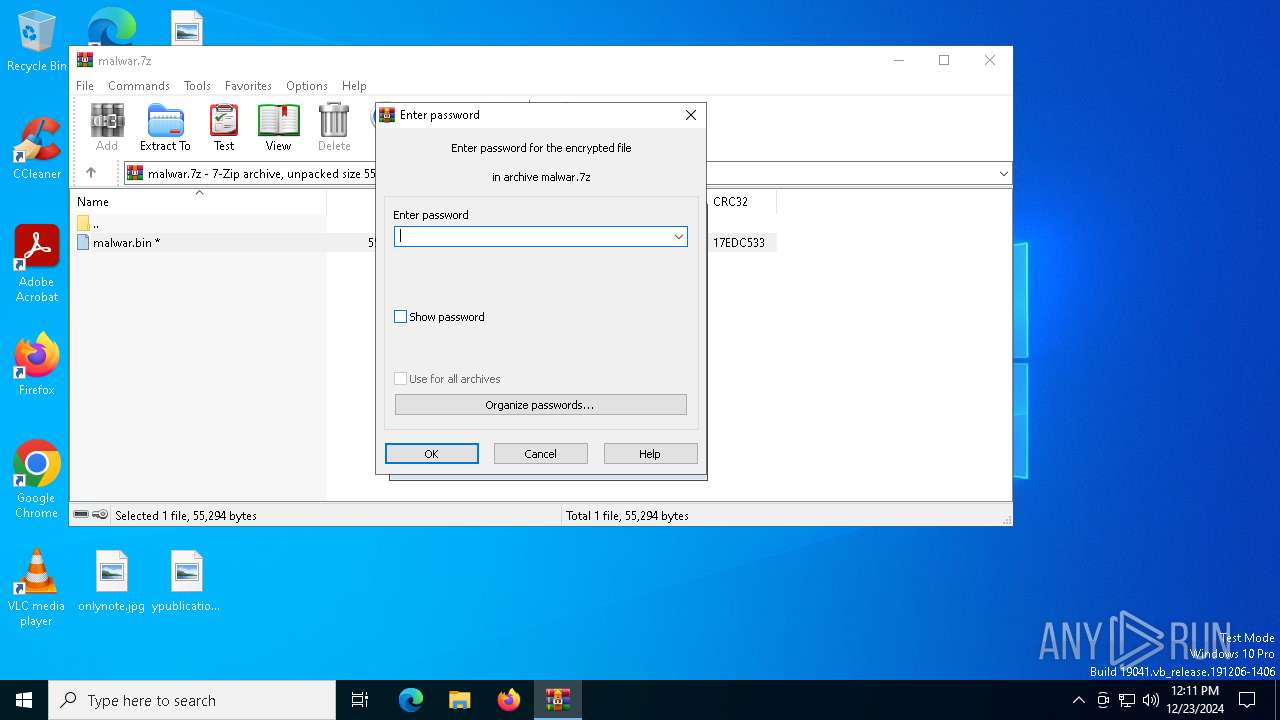
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7052) malwar.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Security Center |
| Operation: | write | Name: | AntiVirusOverride |
Value: 1 | |||
Executable files
6
Suspicious files
16
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6068 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:F8E8FDC0CF7A3E4E26ABE9834B76D49A | SHA256:C35318985777620C60E2665F6326B7664FBD92E48D8393C8B988534ACFCA7F17 | |||
| 6068 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ccc0fa1b9f86f7b3.customDestinations-ms | binary | |
MD5:F38E769E5ECBA7D79D828952B71E17B4 | SHA256:99A58807BB48B1B5996E5ADE5415BB18E33629CB769ABFBB447801FE99B74B8A | |||
| 6068 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 6068 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\ccupdate631_free[1].exe | — | |
MD5:— | SHA256:— | |||
| 6068 | CCleaner64.exe | C:\Program Files\CCleaner\temp_ccupdate\ccupdate631_free.exe | — | |
MD5:— | SHA256:— | |||
| 1616 | malwar.exe | C:\Windows\system.ini | binary | |
MD5:A6A3DA797D725D320BDD840893A9395A | SHA256:C6A78239549CC37583DA605B6A66B59853E0F01D5DDEF2C25E9501C84A4E86D5 | |||
| 7052 | malwar.exe | C:\Windows\system.ini | binary | |
MD5:B4CD9C8D9CC5590673F1C2A0D468E111 | SHA256:E808C205D92D5401F478F7AA5F288BF61C49EE468745DCE1BB6A0969C64C167A | |||
| 6068 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ccc0fa1b9f86f7b3.customDestinations-ms~RF1418b6.TMP | binary | |
MD5:715D03F2C851242AE02F082C92170337 | SHA256:52F9047E9A072554A68045FD0215B8484C2D6D758FEE82543FBAA7C7F7D163D9 | |||
| 6068 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:1F58A0742EBBB573586ACD3C31671FB9 | SHA256:7B4FCCDD0851558438E21A1060357E075B5979D6EDF25924C3EC3790F646973C | |||
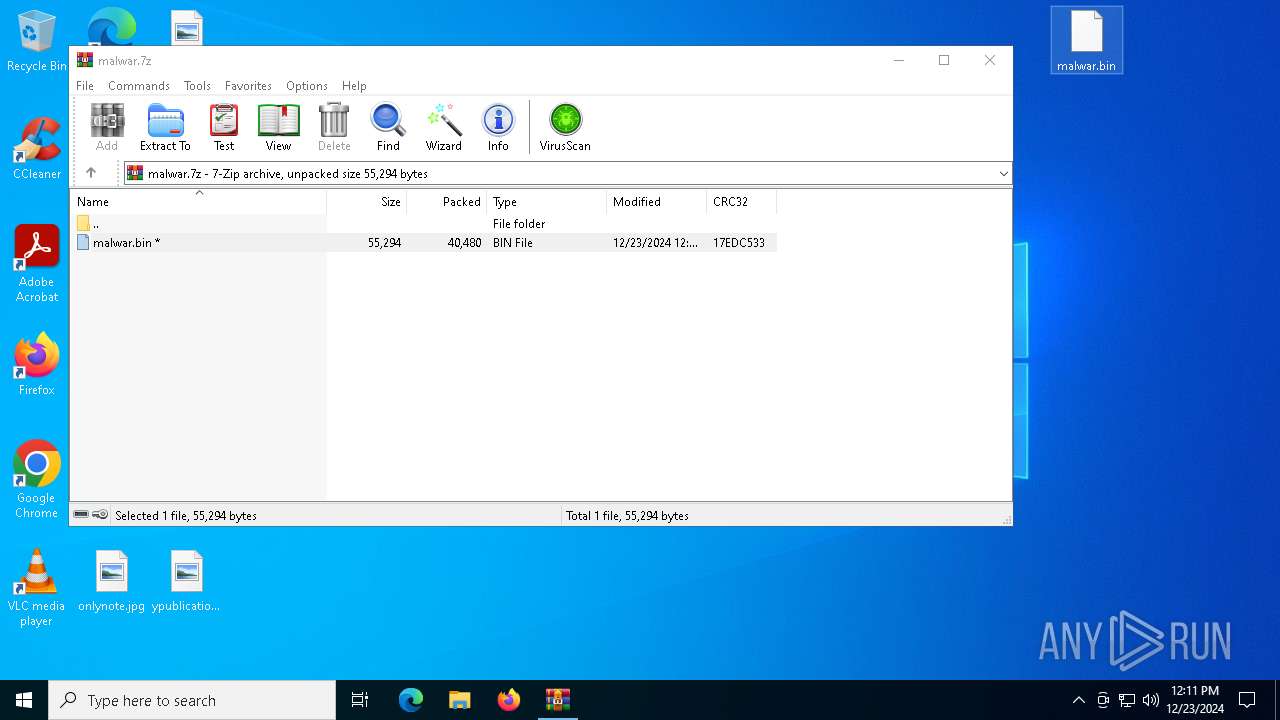
| 5464 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5464.22465\malwar.bin | executable | |
MD5:FDC5590AF1F907D895B5DC5421C94EF2 | SHA256:D9731E7748B49C037AF6B91AD4A90509FAC873A9857AFDB63737EEC8CEC2D718 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
44
DNS requests
27
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6088 | CCleaner64.exe | GET | 200 | 2.16.168.113:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
1596 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1596 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6320 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6068 | CCleaner64.exe | GET | 200 | 2.16.168.113:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7152 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6068 | CCleaner64.exe | GET | 200 | 142.250.185.99:80 | http://o.pki.goog/s/wr3/R_4/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEEf%2BFZGpnvWuEEGk5mBYdOg%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1596 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1596 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6068 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
Process | Message |
|---|---|
CCleaner64.exe | [2024-12-23 12:12:33.045] [error ] [settings ] [ 6068: 6780] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-12-23 12:12:33.046] [error ] [ini_access ] [ 6068: 6780] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2024-12-23 12:12:33.768] [error ] [settings ] [ 6068: 5556] [D2EC45: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2024-12-23 12:12:33.796] [error ] [Burger ] [ 6068: 5556] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | [2024-12-23 12:12:33.796] [error ] [Burger ] [ 6068: 5556] [904E07: 253] [23.2.1118.0] [BurgerReporter.cpp] [253] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner64.exe | file:///tis/optimizer.tis(1131) : warning :'await' should be used only inside 'async' or 'event'
|
CCleaner64.exe | file:///tis/optimizer.tis(1288) : warning :'async' does not contain any 'await'
|
CCleaner64.exe | startCheckingLicense()
|