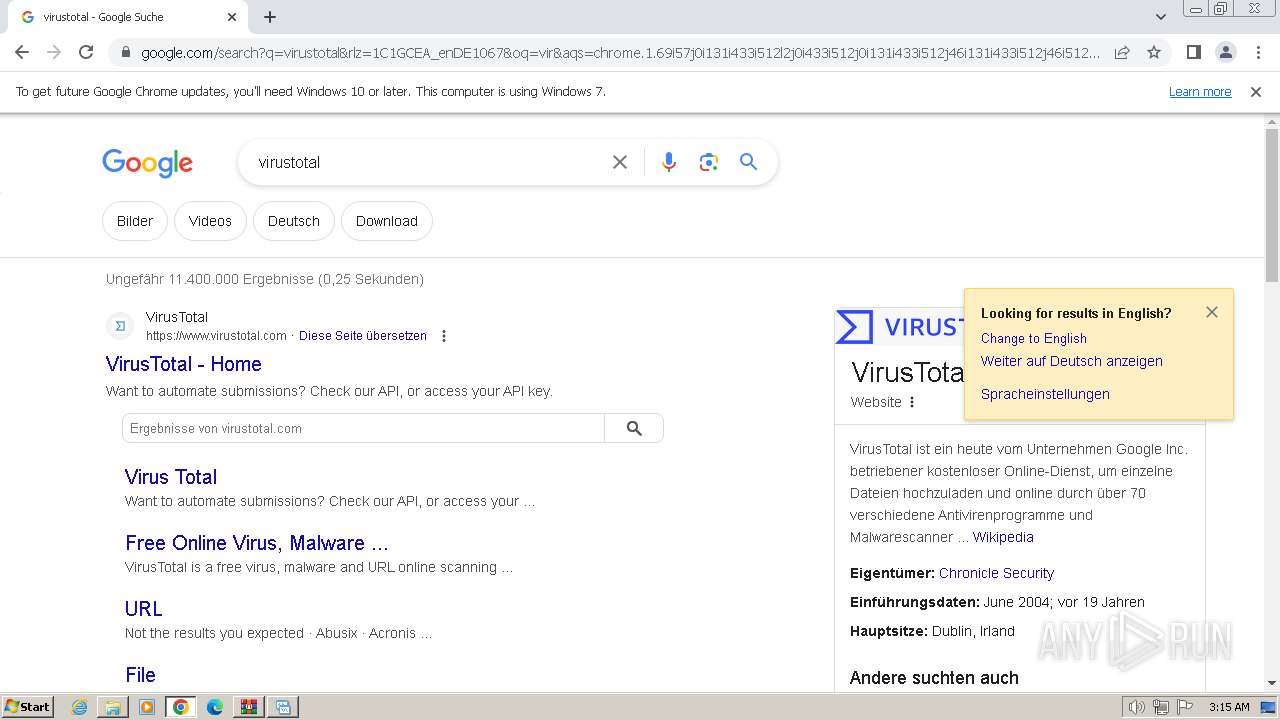
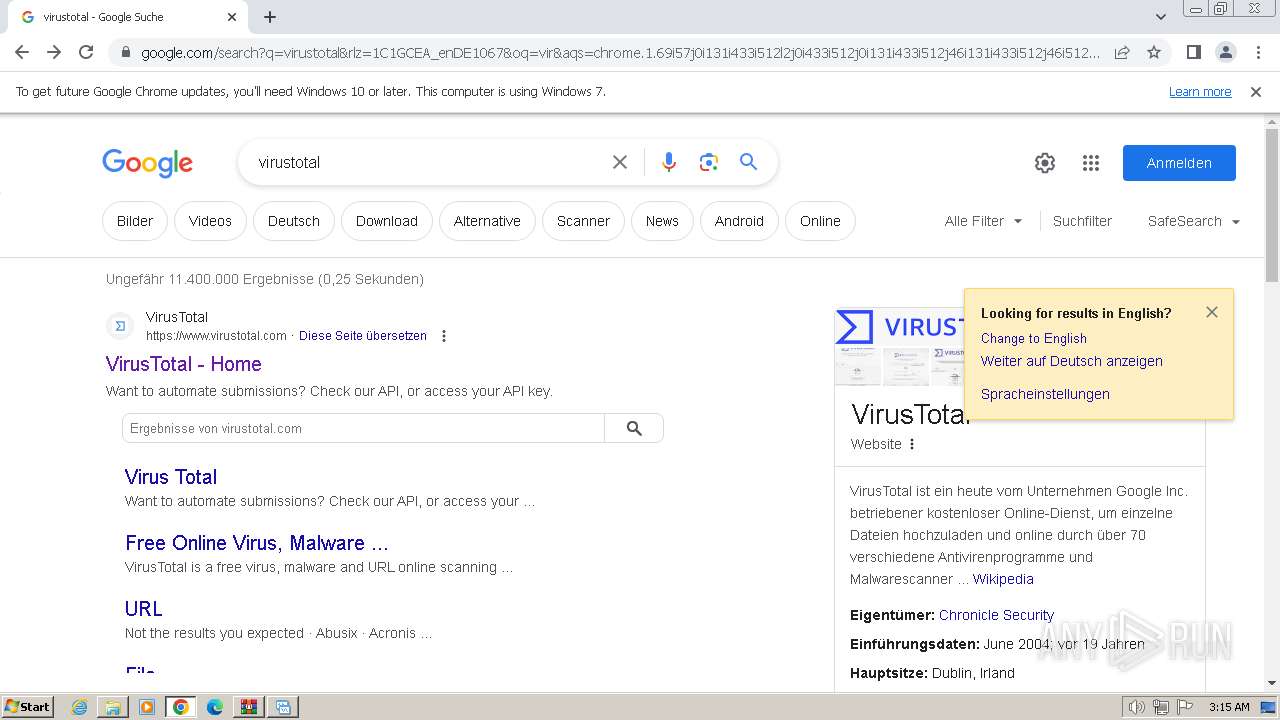
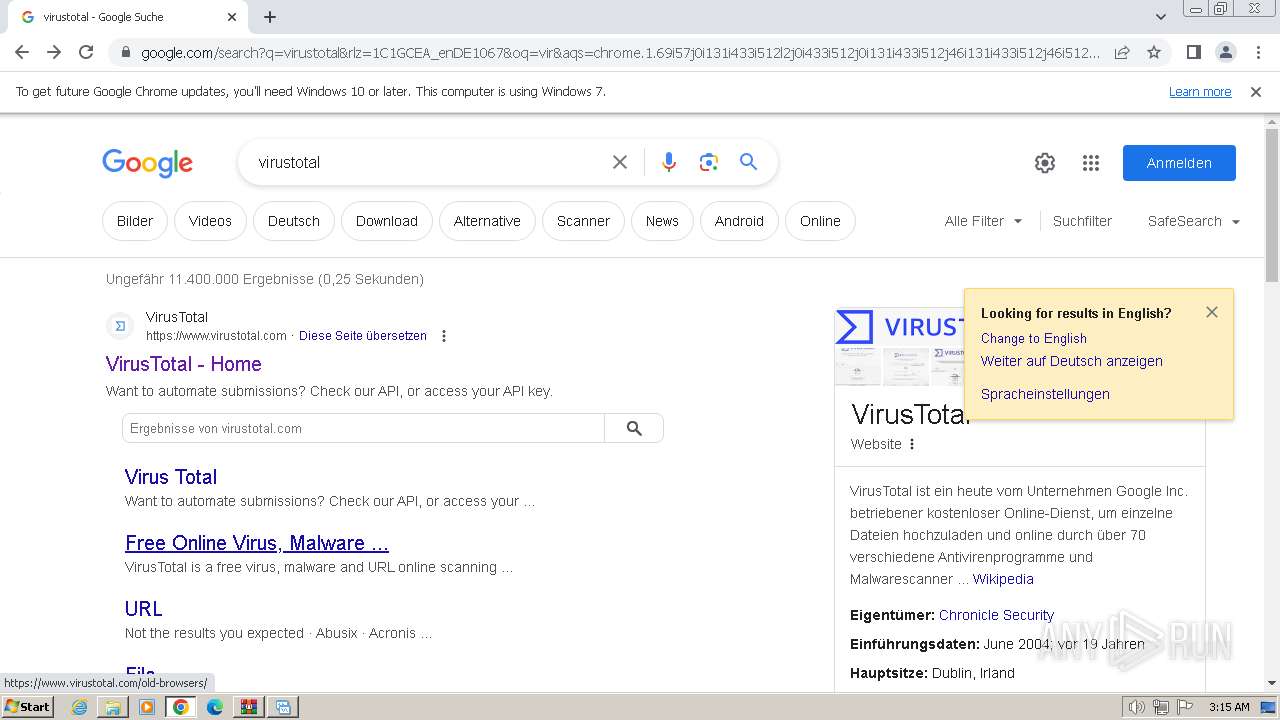
| File name: | terminal.zip |
| Full analysis: | https://app.any.run/tasks/50d2d656-07ad-4472-b415-57f2d347f8d1 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 03:12:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5B50185E53E0C706FBBCF98E2F734A75 |
| SHA1: | 81C271D3AE117DD81DC787F18F554BB99D754E04 |
| SHA256: | BCB91D20C5EDAF44666F637C7D1BFE7583E161F89C239DF52AC143DB32BDB272 |
| SSDEEP: | 196608:NUujBHPWw6OVq4uLbgMii+6cDoSJbbgAChuF4L:NUupBxuLpii+66oa/gtsG |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3700)
- terminal.exe (PID: 3772)
SUSPICIOUS
Executable content was dropped or overwritten
- terminal.exe (PID: 3772)
Reads the Internet Settings
- terminal.exe (PID: 3772)
Reads the BIOS version
- terminal.exe (PID: 3772)
Changes Internet Explorer settings (feature browser emulation)
- terminal.exe (PID: 3772)
Reads settings of System Certificates
- terminal.exe (PID: 3772)
Connects to unusual port
- terminal.exe (PID: 3772)
INFO
Checks supported languages
- terminal.exe (PID: 3772)
Reads Windows Product ID
- terminal.exe (PID: 3772)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3700)
Manual execution by a user
- terminal.exe (PID: 3772)
- explorer.exe (PID: 2292)
- chrome.exe (PID: 2900)
- explorer.exe (PID: 2364)
- rundll32.exe (PID: 2372)
Reads Environment values
- terminal.exe (PID: 3772)
Reads CPU info
- terminal.exe (PID: 3772)
Checks proxy server information
- terminal.exe (PID: 3772)
Reads product name
- terminal.exe (PID: 3772)
Process checks whether UAC notifications are on
- terminal.exe (PID: 3772)
Creates files in the program directory
- terminal.exe (PID: 3772)
Creates files or folders in the user directory
- terminal.exe (PID: 3772)
Reads the computer name
- terminal.exe (PID: 3772)
Reads the software policy settings
- terminal.exe (PID: 3772)
Drops the executable file immediately after the start
- chrome.exe (PID: 2900)
Reads the machine GUID from the registry
- terminal.exe (PID: 3772)
Application launched itself
- chrome.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:19 22:10:18 |
| ZipCRC: | 0x4098b13c |
| ZipCompressedSize: | 14673037 |
| ZipUncompressedSize: | 29016072 |
| ZipFileName: | terminal.exe |
Total processes
59
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4044 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=1912 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3916 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2124 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1384 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3412 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1448 --field-trial-handle=1096,i,12311406627277390696,11002565652947056953,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2292 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2364 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
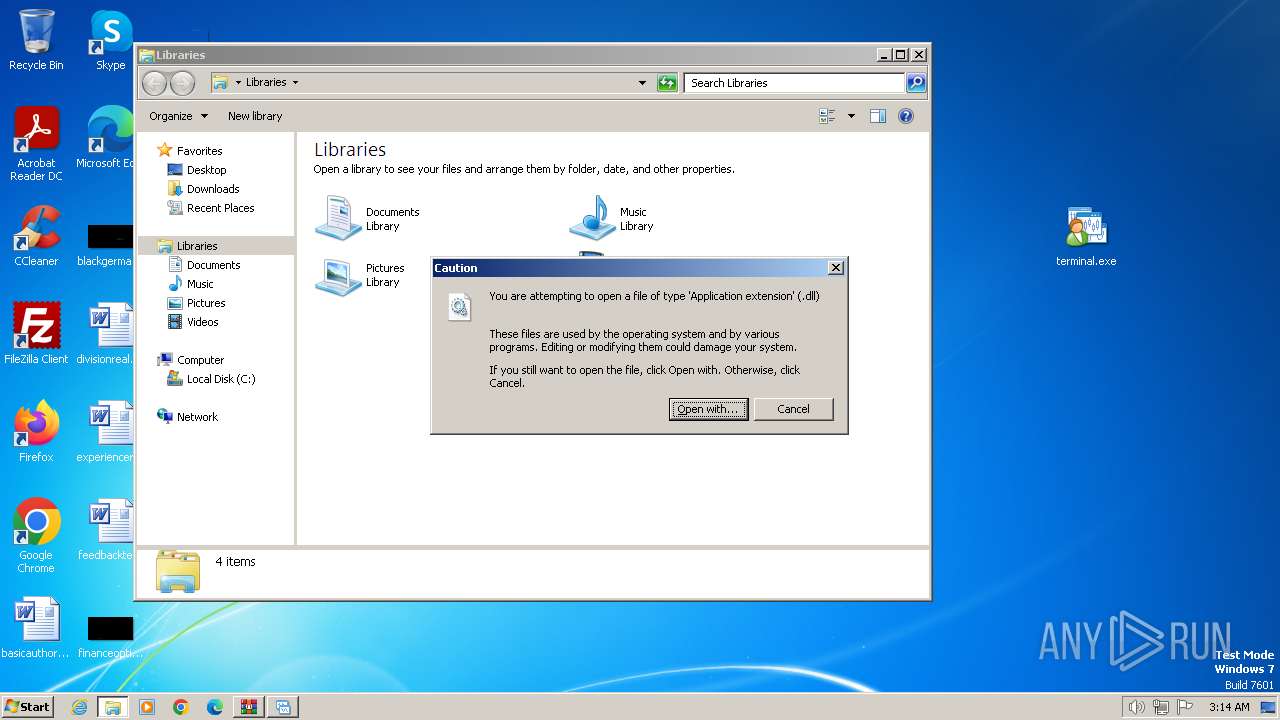
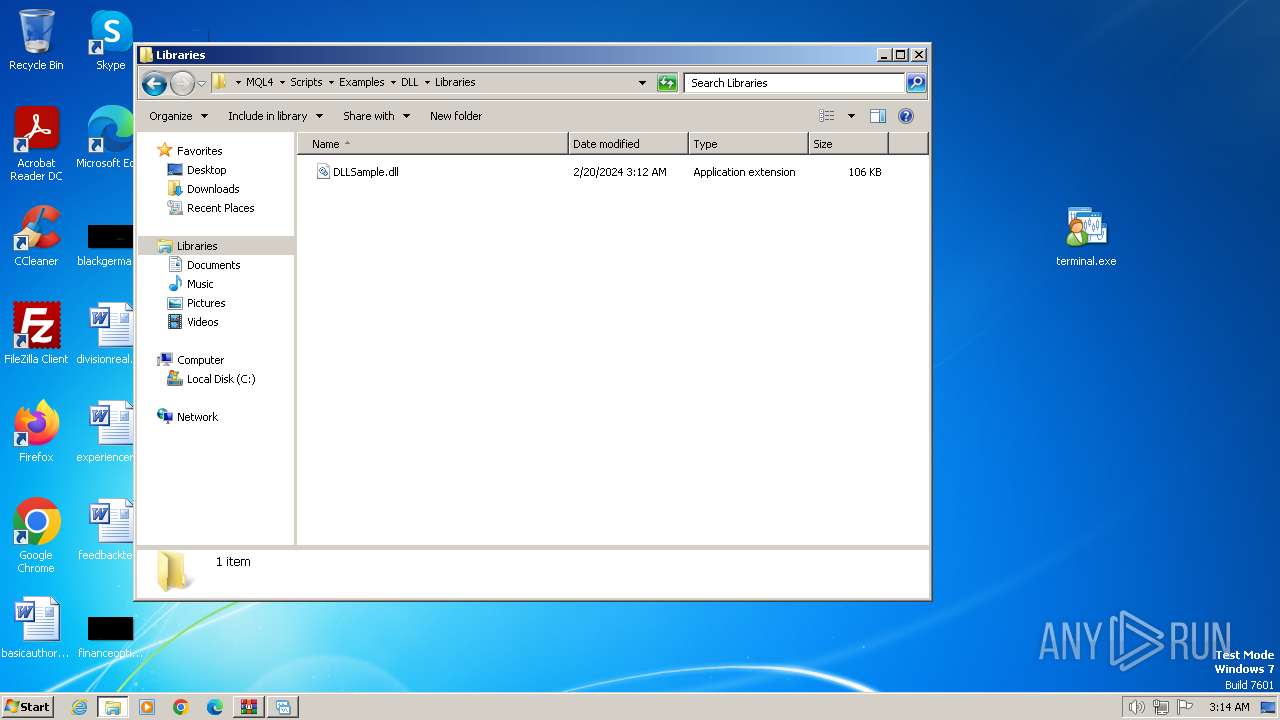
| 2372 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Scripts\Examples\DLL\Libraries\DLLSample.dll | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 274
Read events
26 188
Write events
85
Delete events
1
Modification events
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\terminal.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
78
Text files
208
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Experts\Moving Average.mq4 | text | |
MD5:FAF509A2D59302077B71F494AE8ED42E | SHA256:94B8A95BA1E8F5DE250938E09CABE433D8CB16037796F7B9A24AD261A6A6DACB | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayString.mqh | text | |
MD5:50B760340DB5ED51CB72B3BFB29AF6ED | SHA256:1917D788AB1208C17F1FB49AE3A4B1989BBAE3035893648C950C0570E3B7C04B | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\List.mqh | text | |
MD5:6800539E6D92B736127FE5D94996924F | SHA256:F7334C9E21FF241B1D1154B06D431CCE49C0E296B6C7FB46B59F7657D2991F8B | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayChar.mqh | text | |
MD5:A6D32CEDC7FD7E24D82F36039A1220AC | SHA256:595C4CB02C29CE99495ABB37E1BC93CB9384B05CE1A089A3ADE7E90090C27AF5 | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayLong.mqh | text | |
MD5:7FD0D8764BFD83E848593977B3F3ACC6 | SHA256:AD4F1F2315B49E1196209E1AB7EE6E47A952AB3CDE60E21C574ACF1D0FD75ED6 | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\templates\StrategyTester.htm | html | |
MD5:14EABFE565F4093C112ACA11E4AF3B9C | SHA256:BC11A2EA23005E246D554B458C35B8BBD9C1853B5CE92AFA29D20D843CB0AEAC | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Experts\MACD Sample.mq4 | text | |
MD5:76336FF9B38FBEBBFBAEFF0B2DE320FC | SHA256:4B9B0837BE9A580444A15513E02DBBFC4E3FBA7321133AEFE5CFB1CC7C34FD5F | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\templates\OptimizationReport.htm | html | |
MD5:6EC497DC13E18BE3E4FE4F68B5293AEB | SHA256:2ED4AF3129FB1479732BE1AC2DB94ADC89C0CAAE1FC366884FB63240C8D8268A | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\config\terminal.ini | text | |
MD5:9F8A94E170DAAC4481BCED95A016FFDF | SHA256:0085F8B127E6D8E9D07DAB1B61602F3F64540AFCE1E2B20E9F041F2D6154BC95 | |||
| 3772 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\Tree.mqh | text | |
MD5:76CB57572F055249A78AF710D0B2ABEE | SHA256:4D4DD2007FA4D4577C9E40C28CF8544F8B154C15861B096BD1A840924D495500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
124
DNS requests
50
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 10.2 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 5.98 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 10.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 89.0 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 19.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 176 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 44.1 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 351 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | binary | 140 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3772 | terminal.exe | 195.201.80.82:443 | download.mql5.com | Hetzner Online GmbH | DE | unknown |
3772 | terminal.exe | 78.140.180.54:443 | updates.metaquotes.net | Webzilla B.V. | NL | unknown |
3772 | terminal.exe | 52.78.60.193:443 | — | AMAZON-02 | KR | unknown |
3772 | terminal.exe | 38.76.16.43:443 | — | Beeks Financial Cloud Ltd | US | unknown |
3772 | terminal.exe | 192.229.22.192:443 | — | LCPRODASN | US | unknown |
3772 | terminal.exe | 119.23.154.38:443 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3772 | terminal.exe | 170.75.202.205:1950 | — | Beeks Financial Cloud Ltd | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.mql5.com |
| whitelisted |
updates.metaquotes.net |
| unknown |
api1.mql5.net |
| unknown |
content.finteza.com |
| unknown |
api2.mql5.net |
| unknown |
api3.mql5.net |
| unknown |
api4.mql5.net |
| unknown |
api5.mql5.net |
| unknown |
download.metatrader.com |
| unknown |
api6.mql5.net |
| unknown |