| File name: | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.zip |
| Full analysis: | https://app.any.run/tasks/aa8f8bfd-01cf-4013-8683-9b86bc620879 |
| Verdict: | Malicious activity |
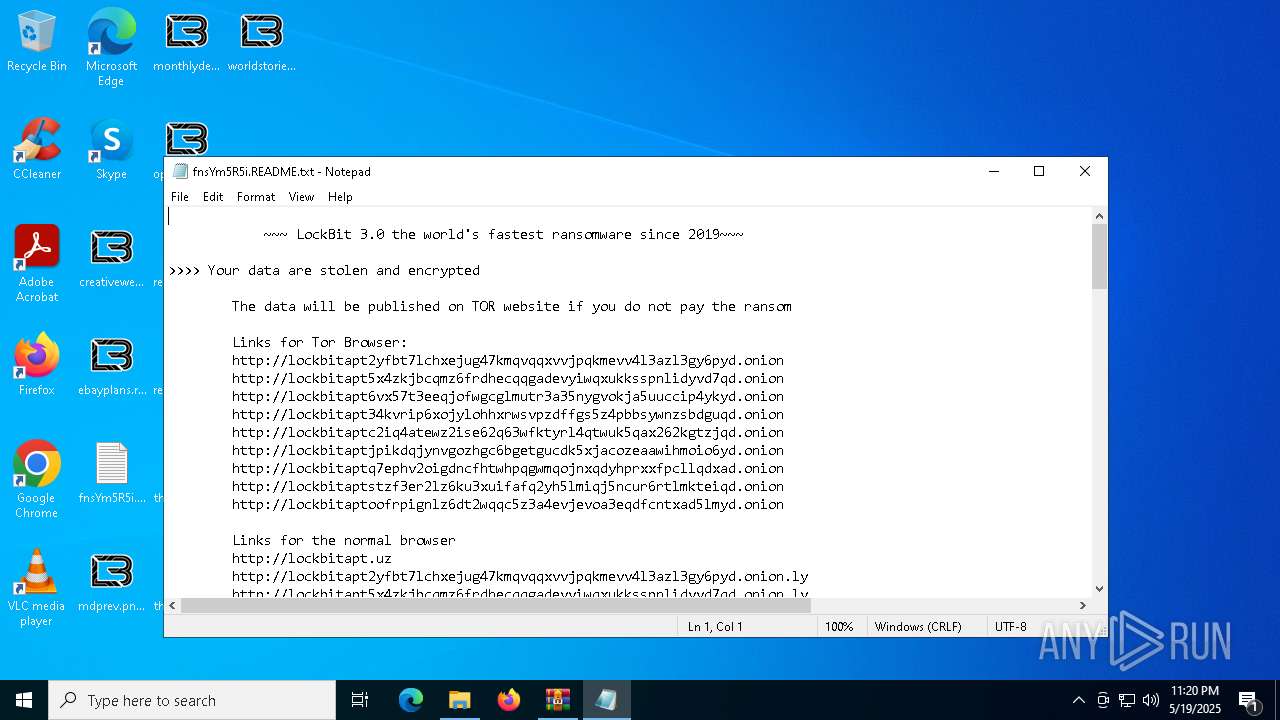
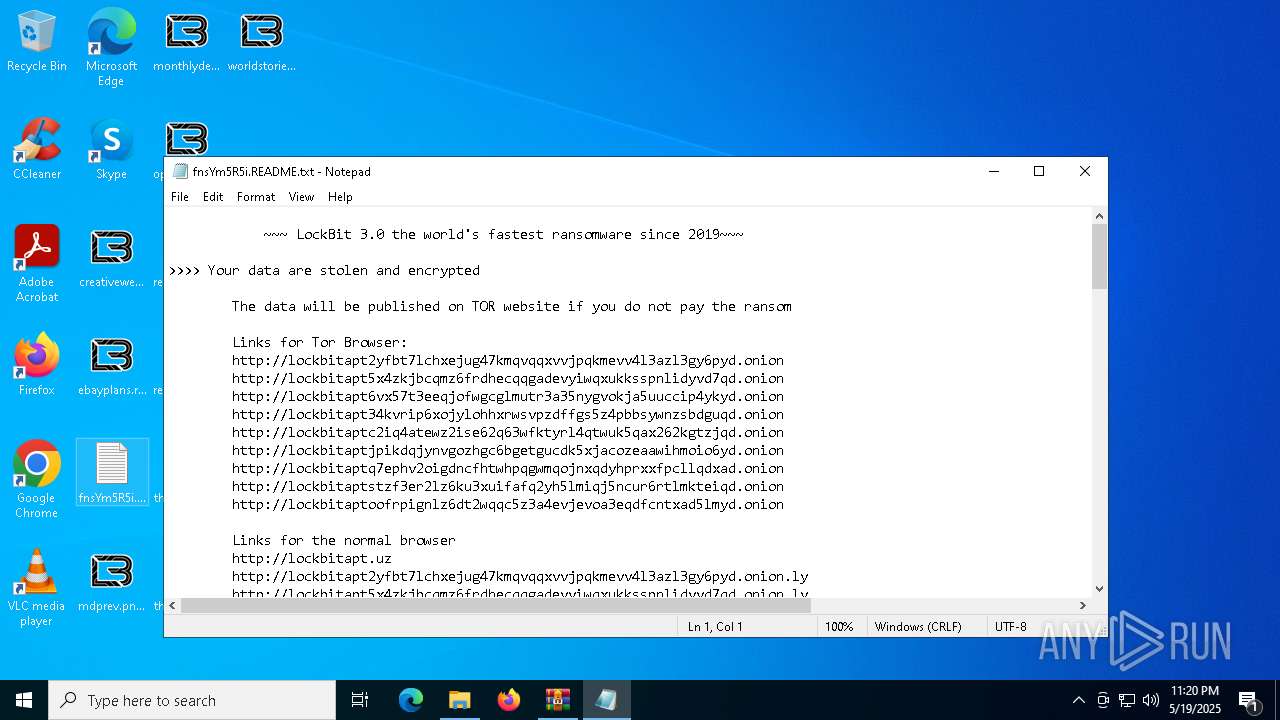
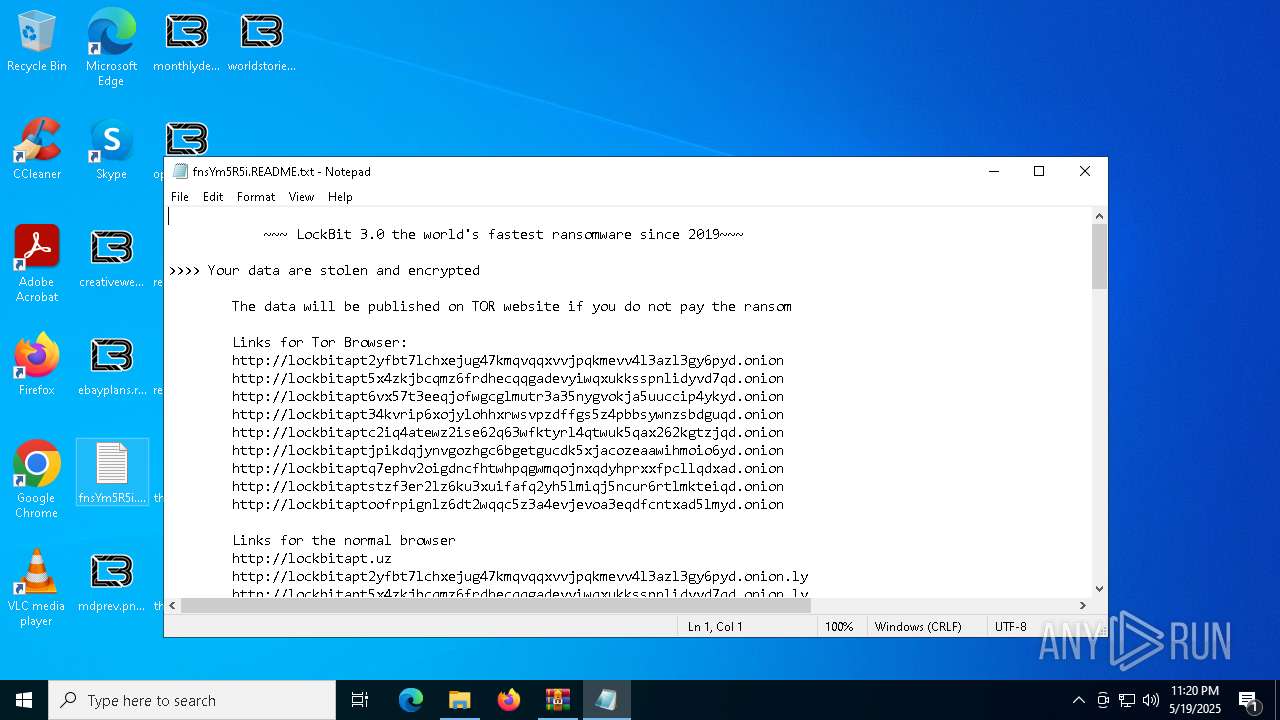
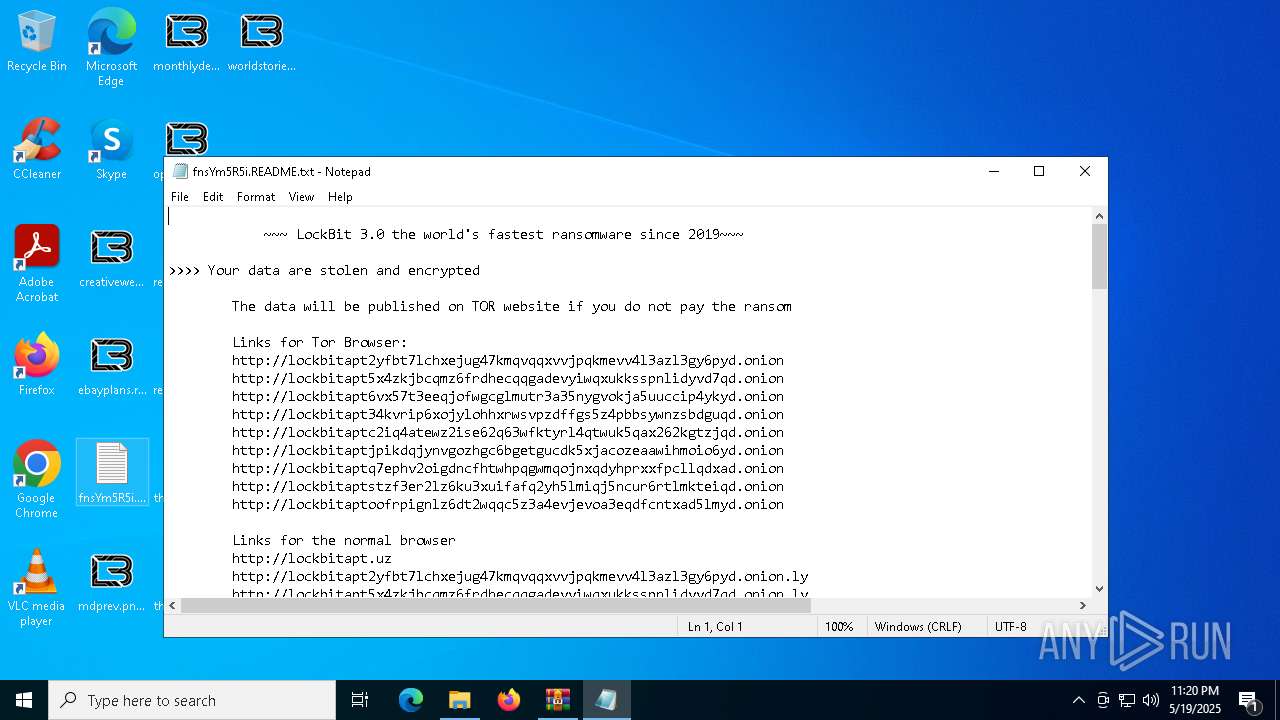
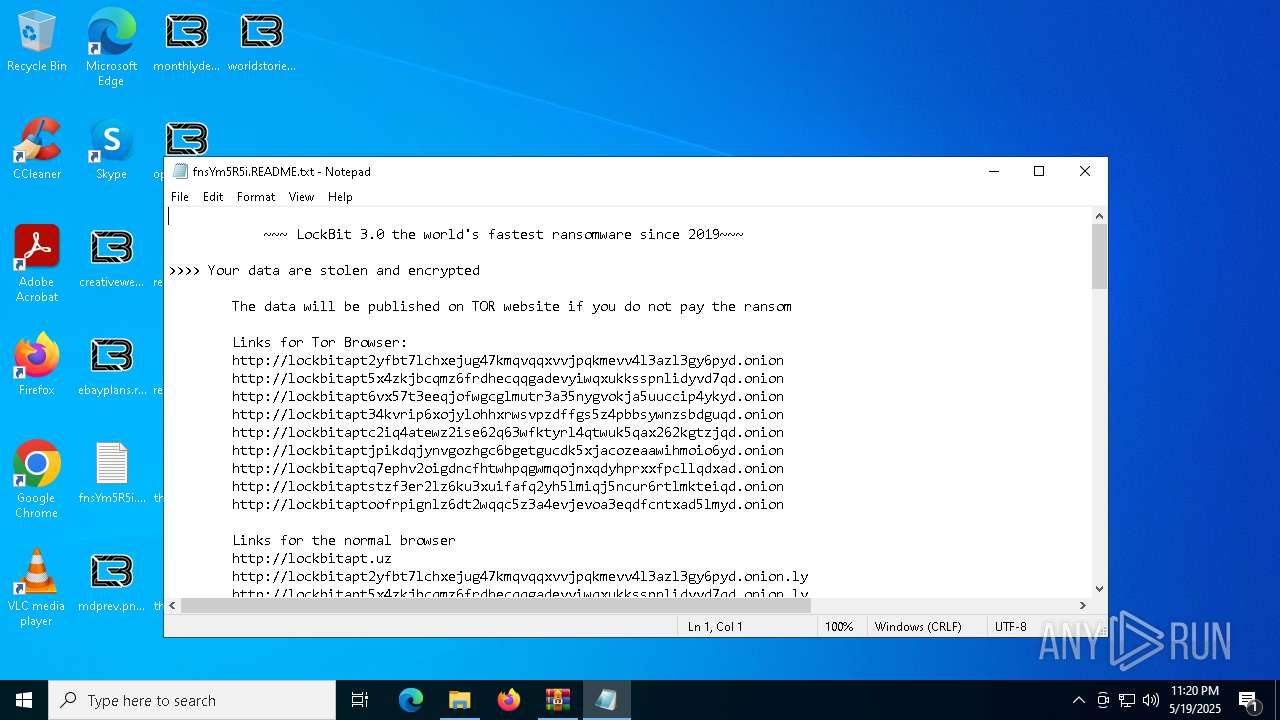
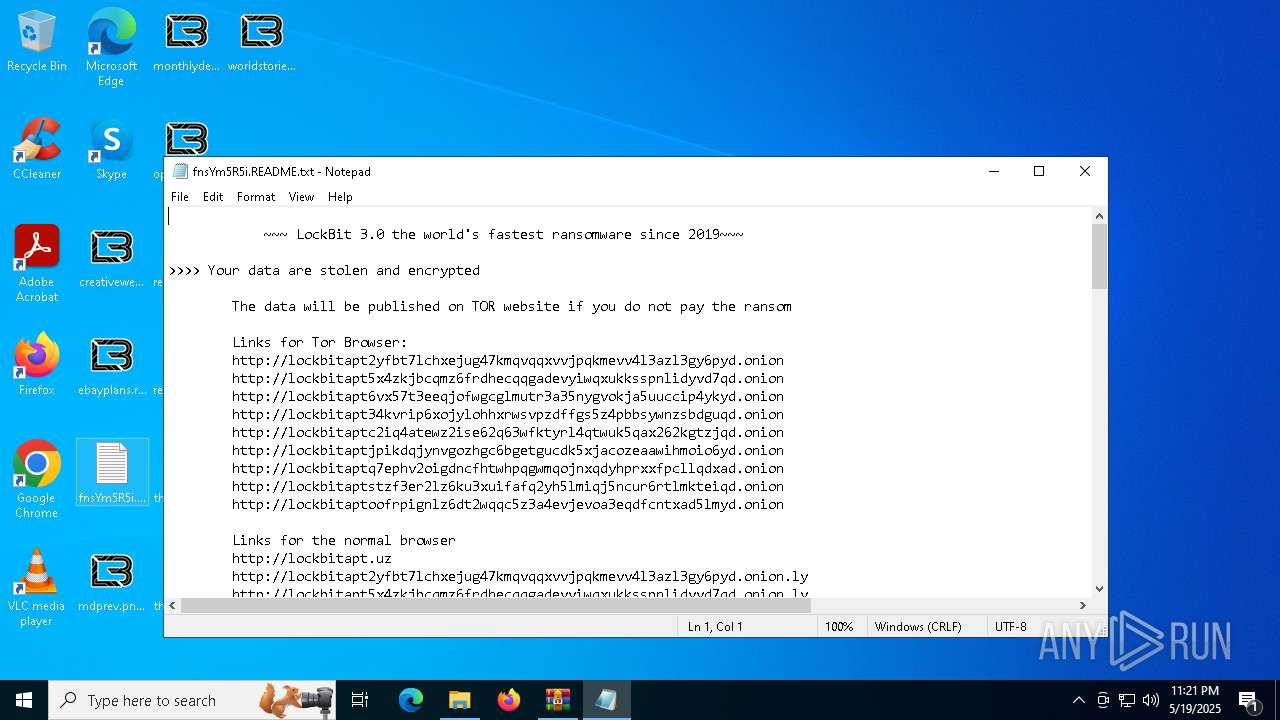
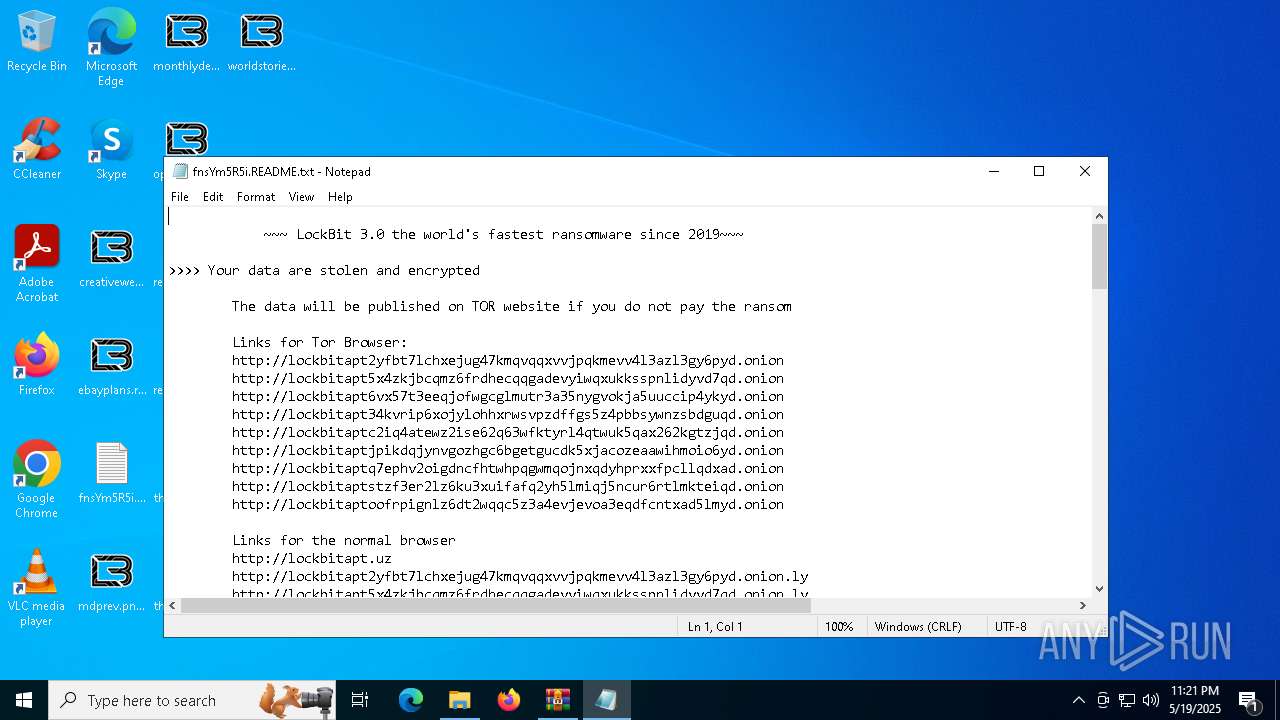
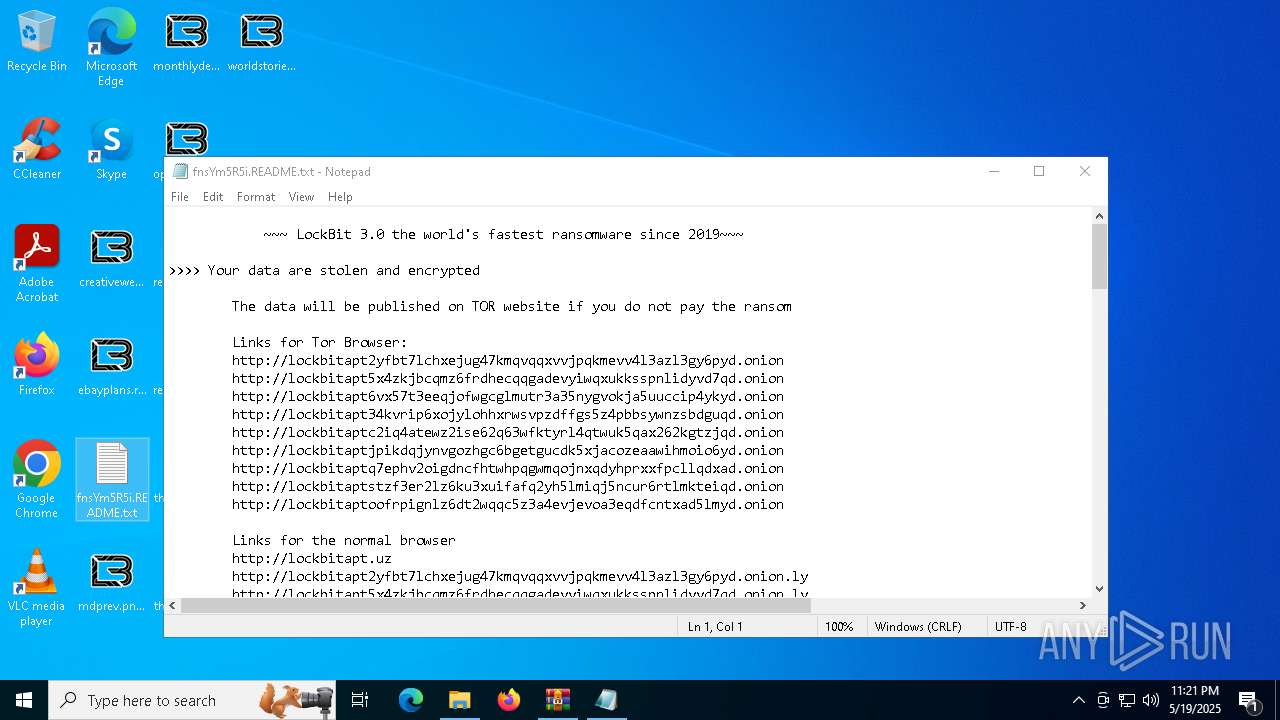
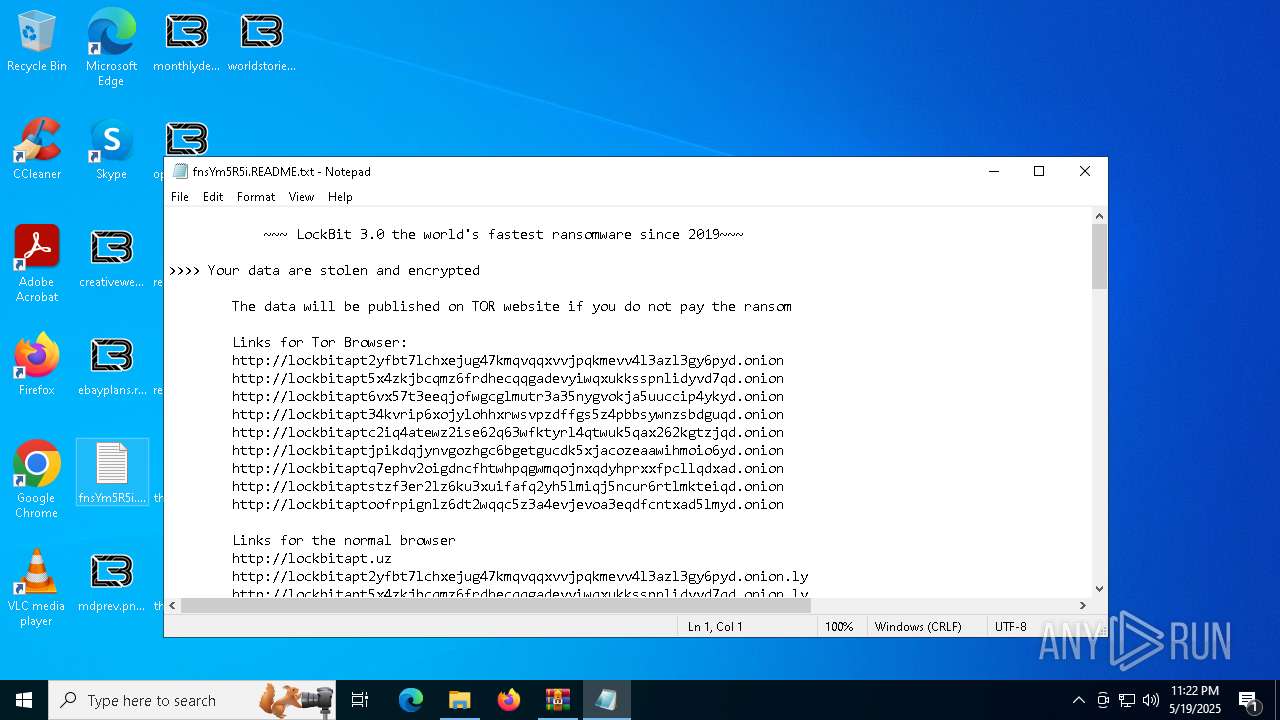
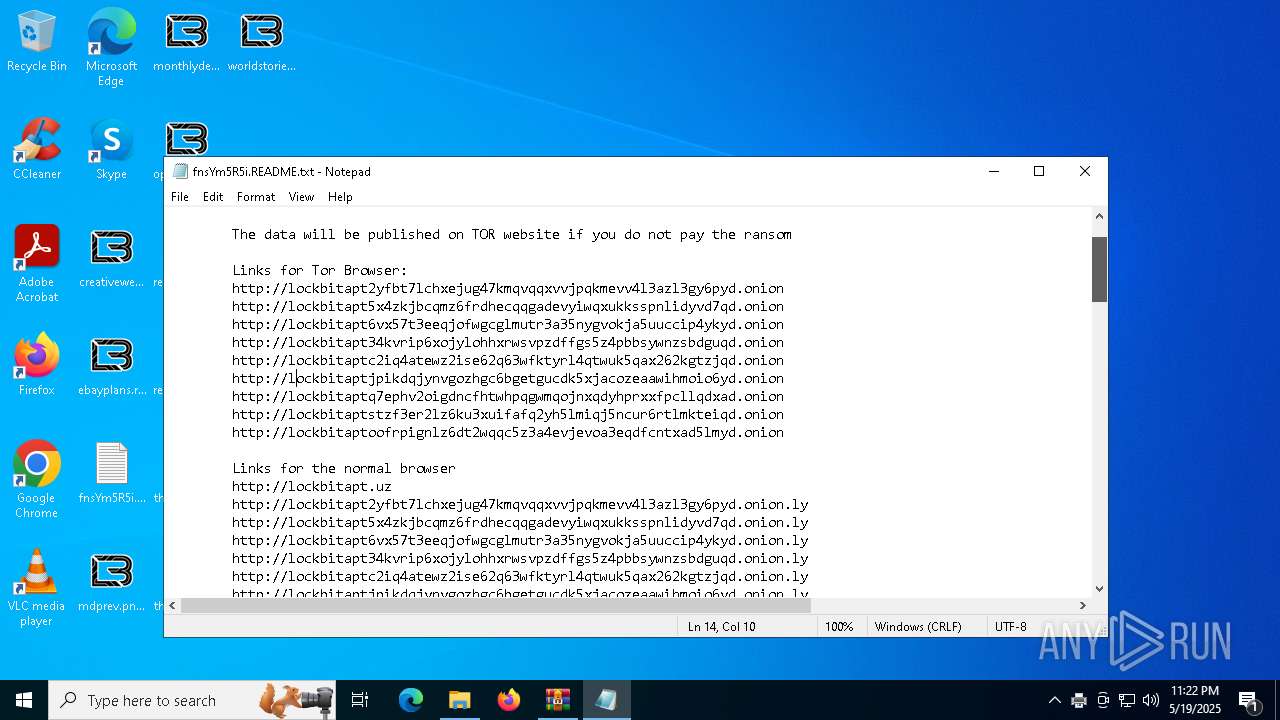
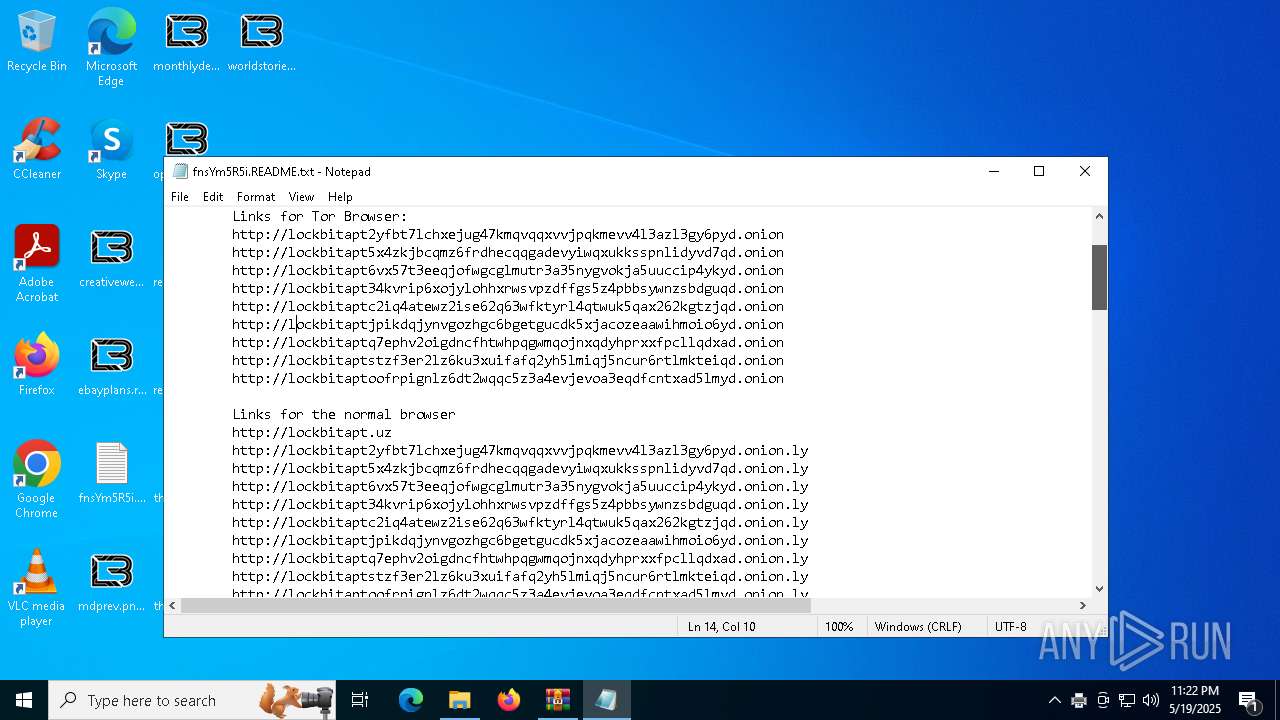
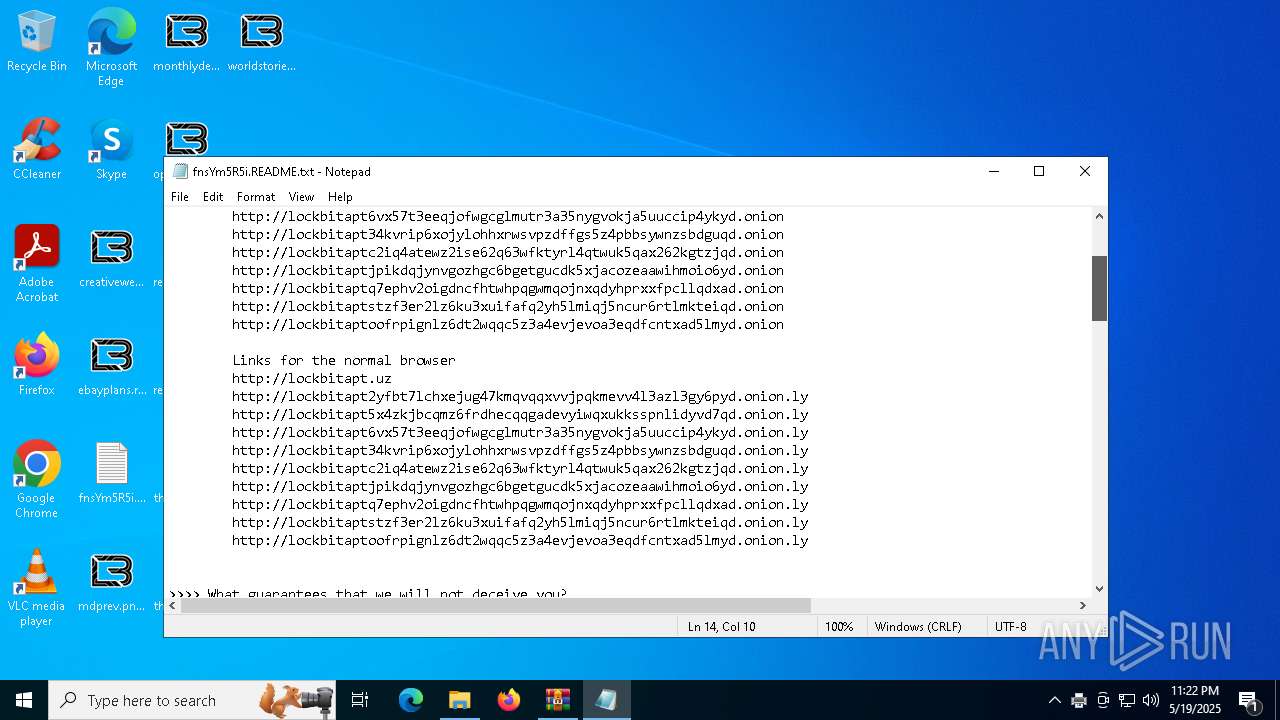
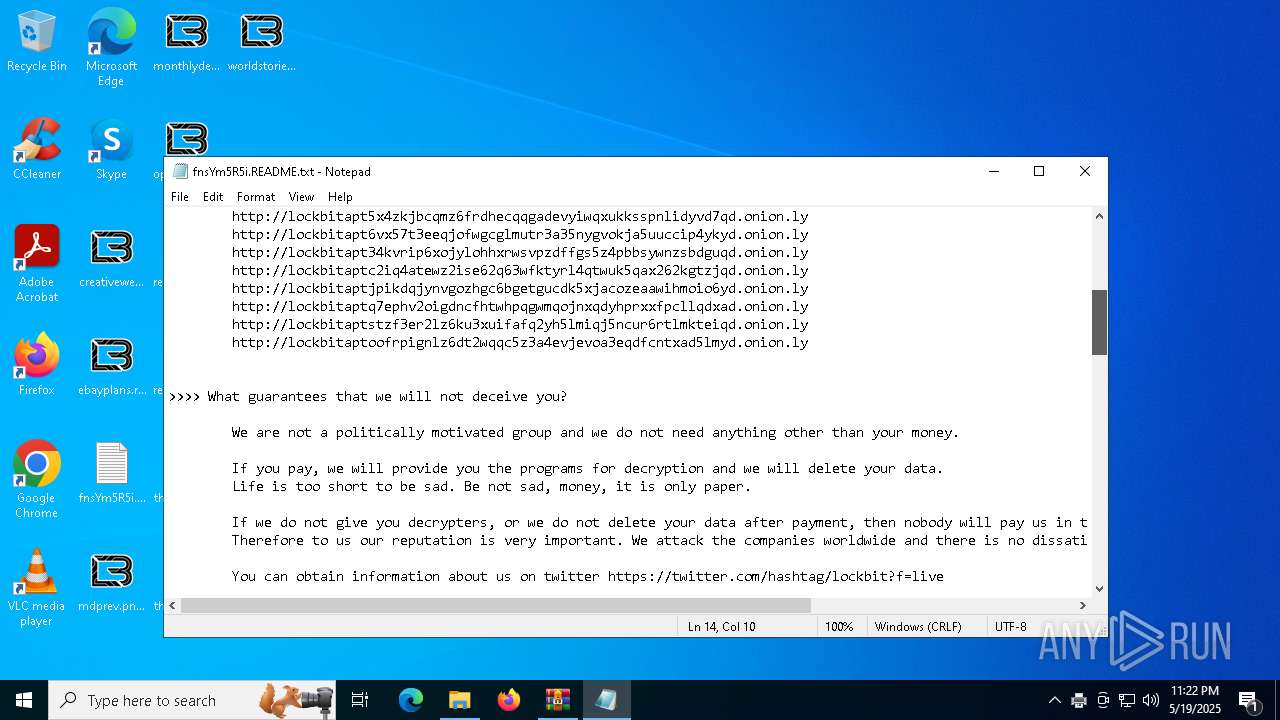
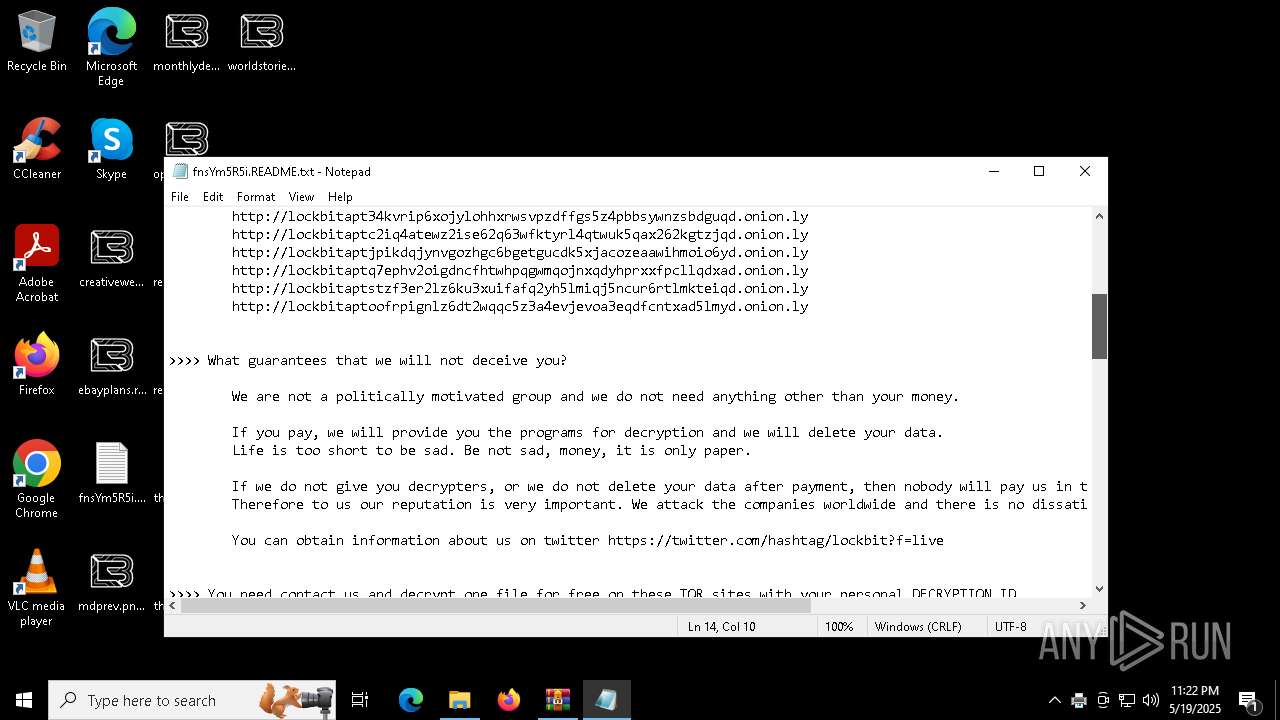
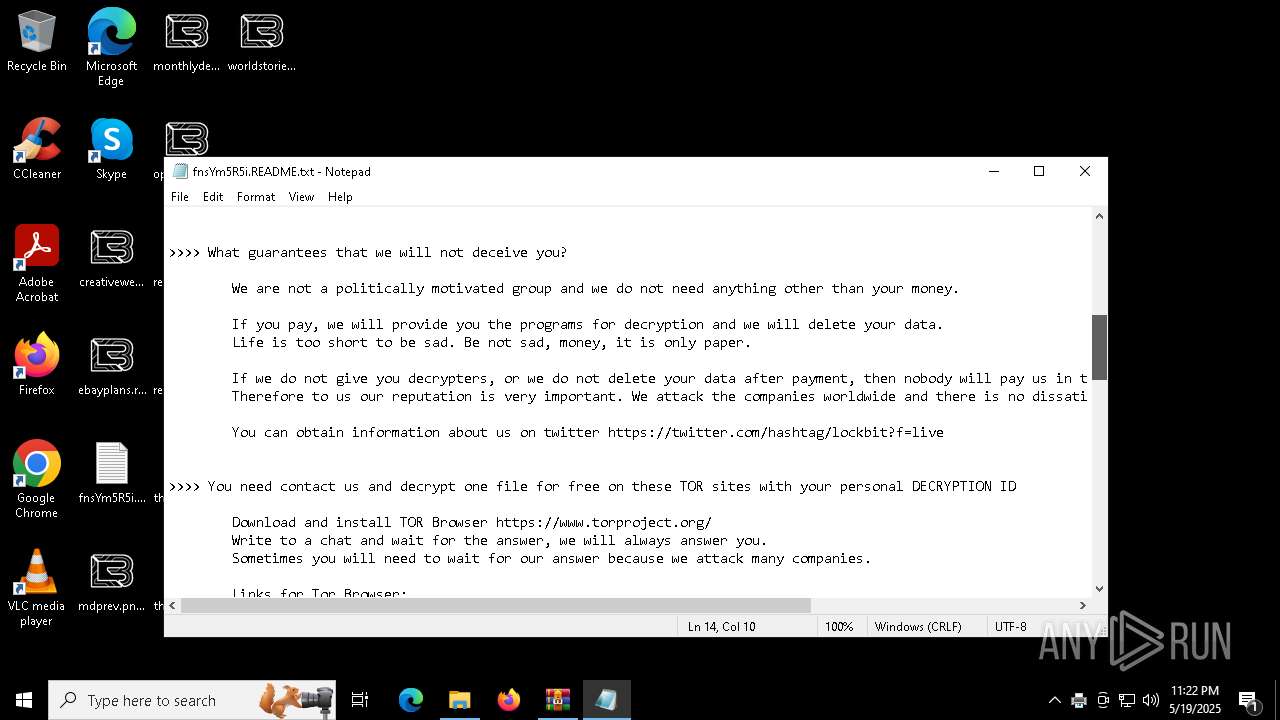
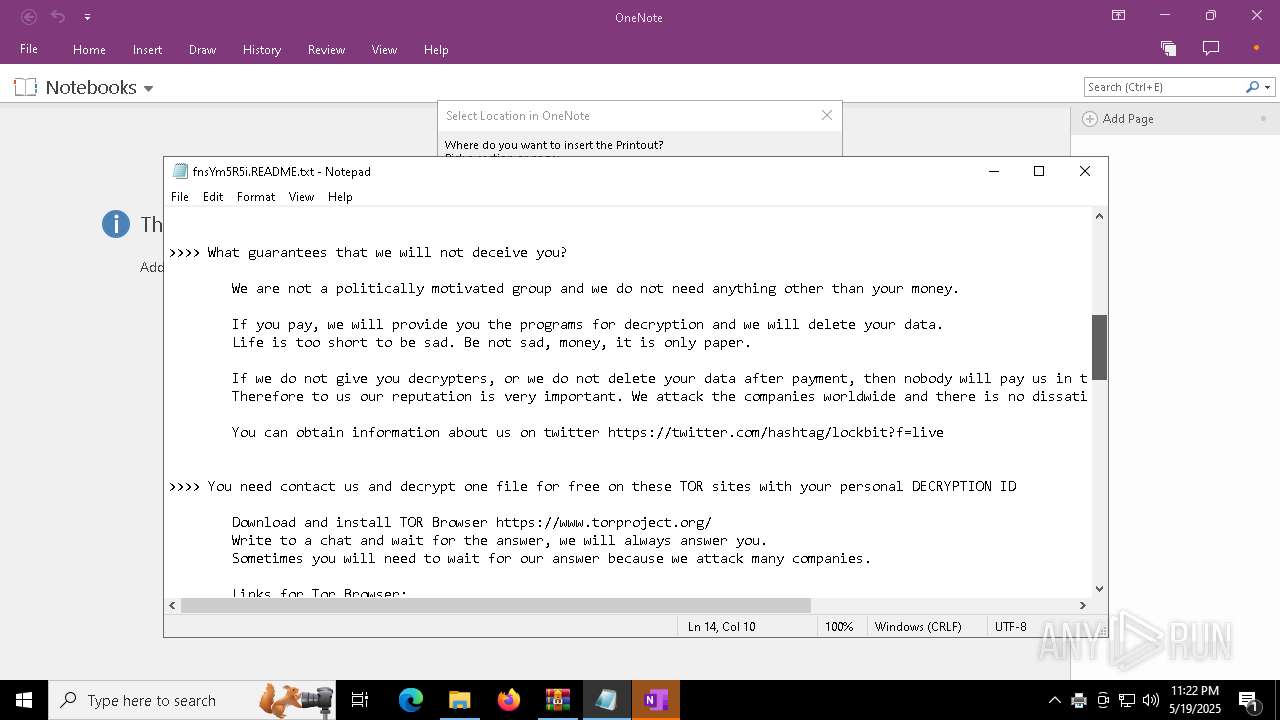
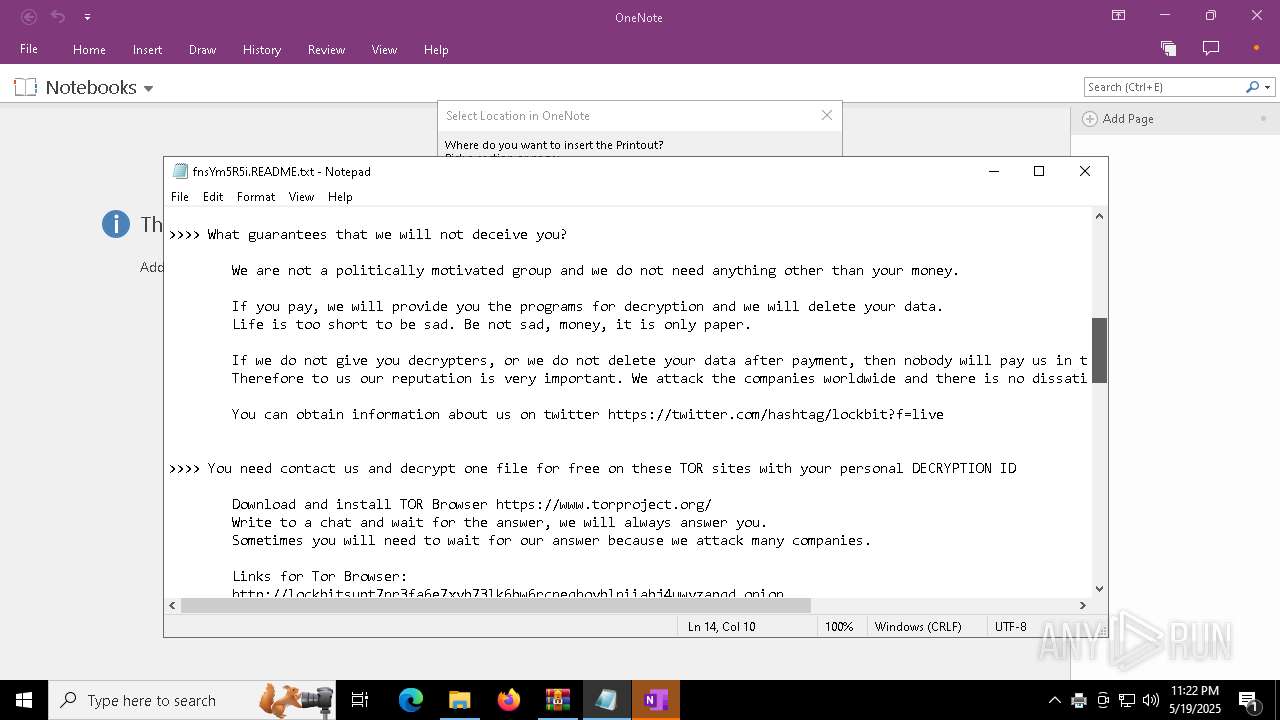
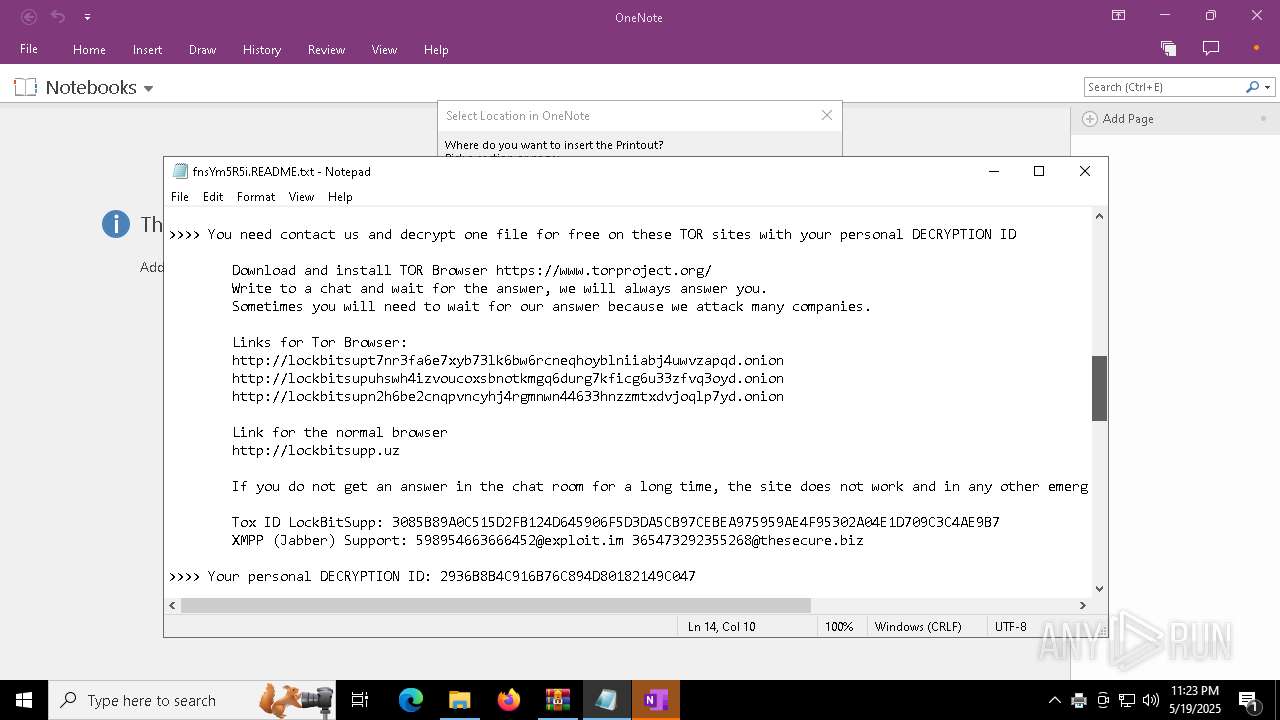
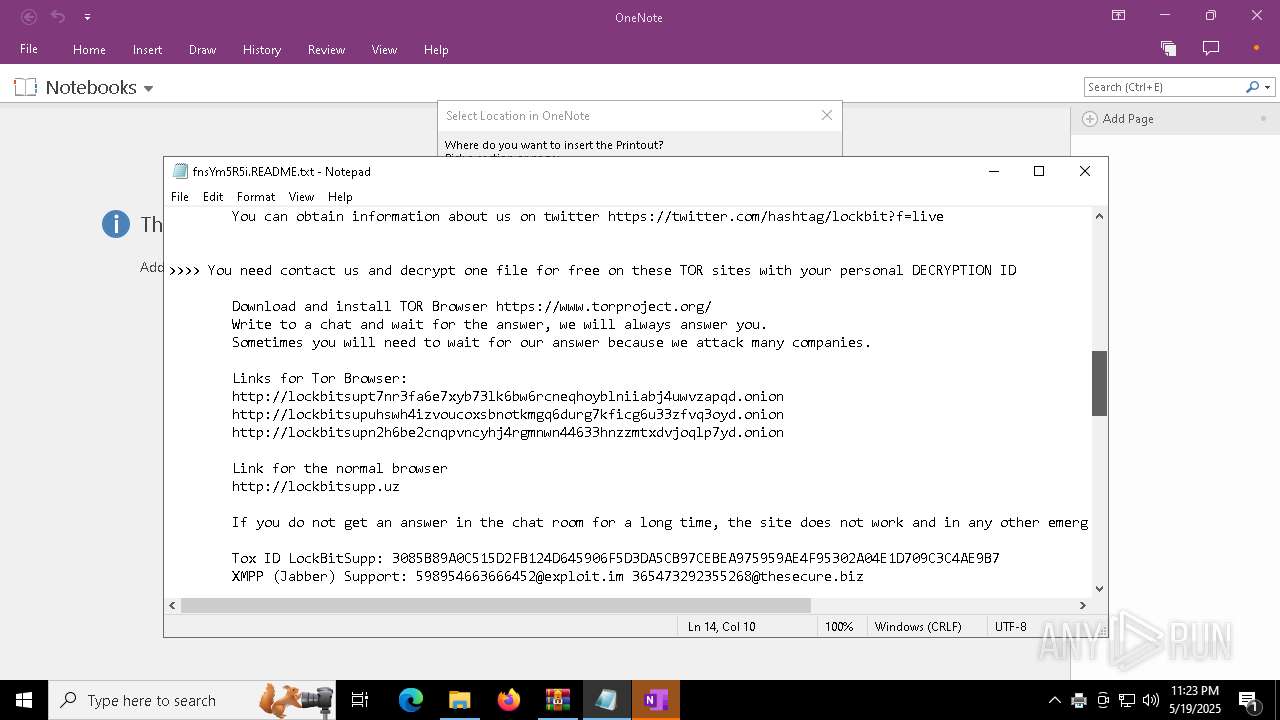
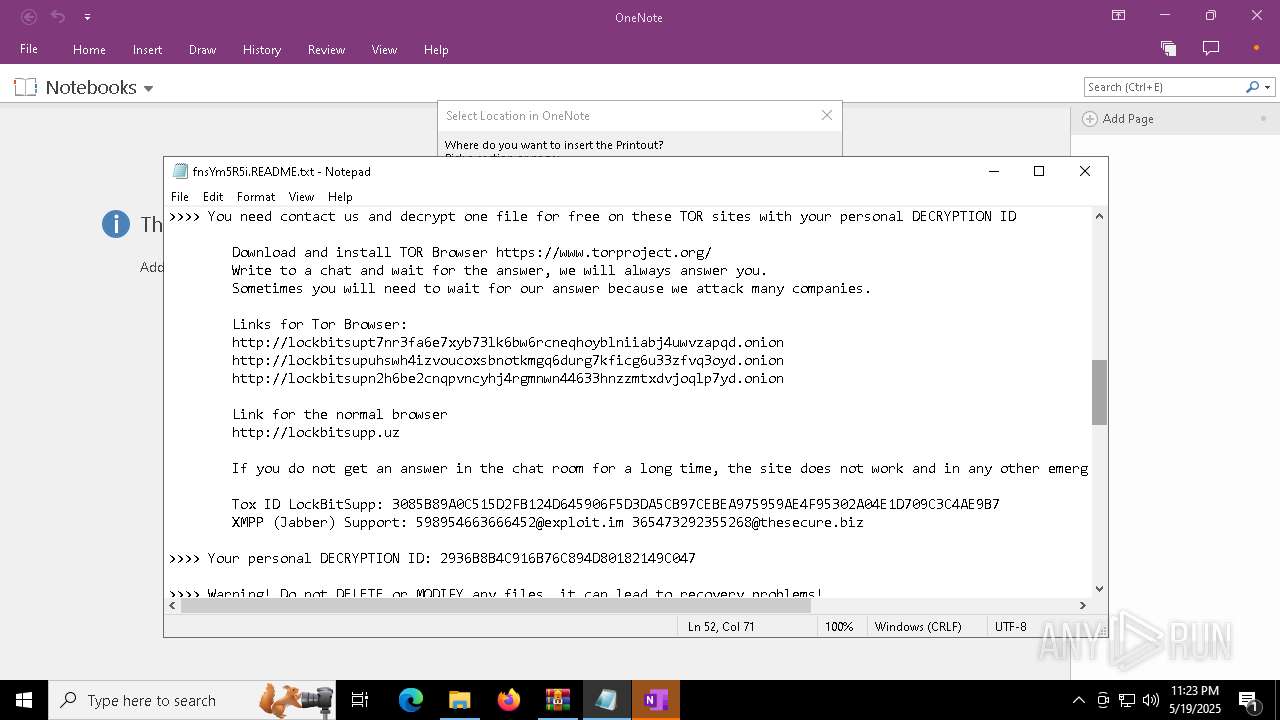
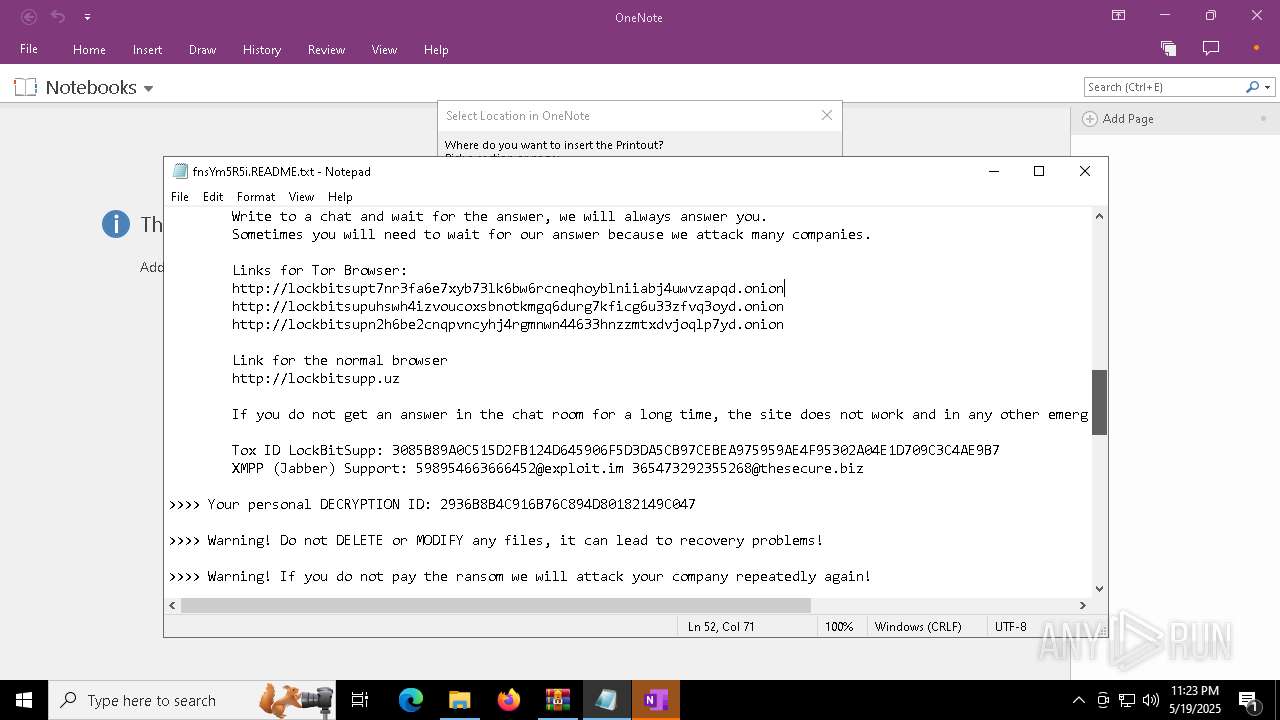
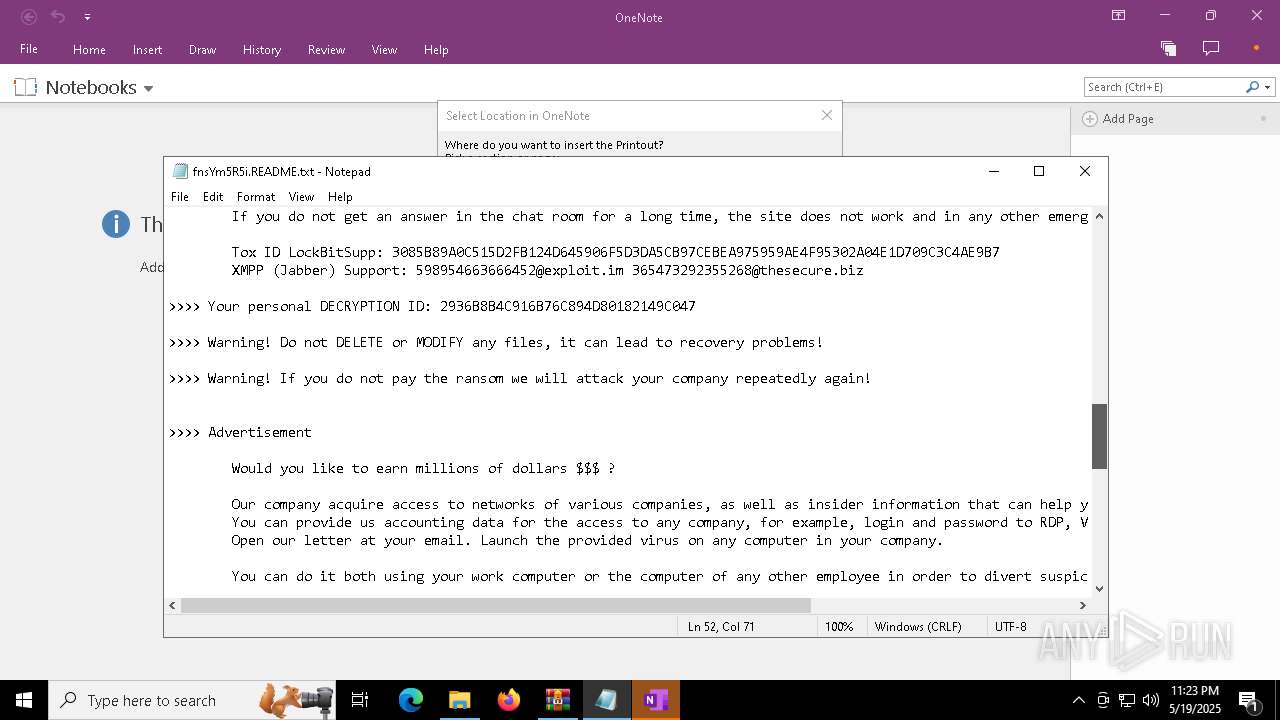
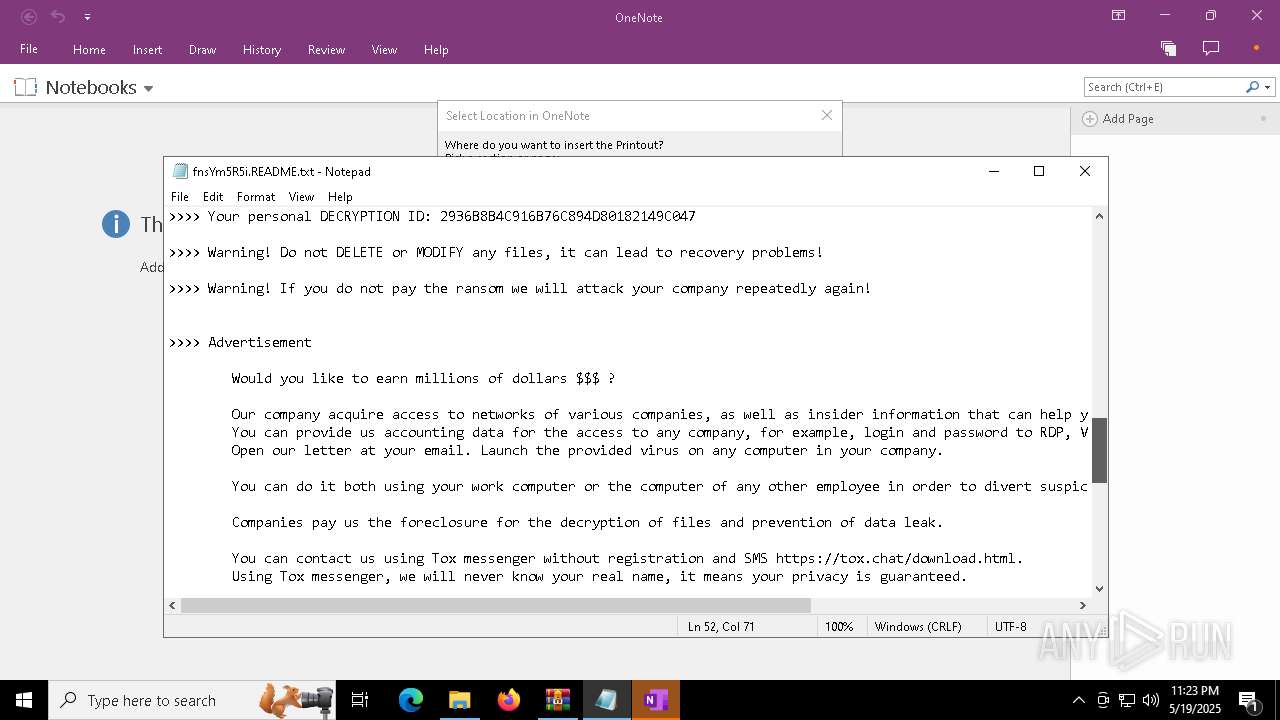
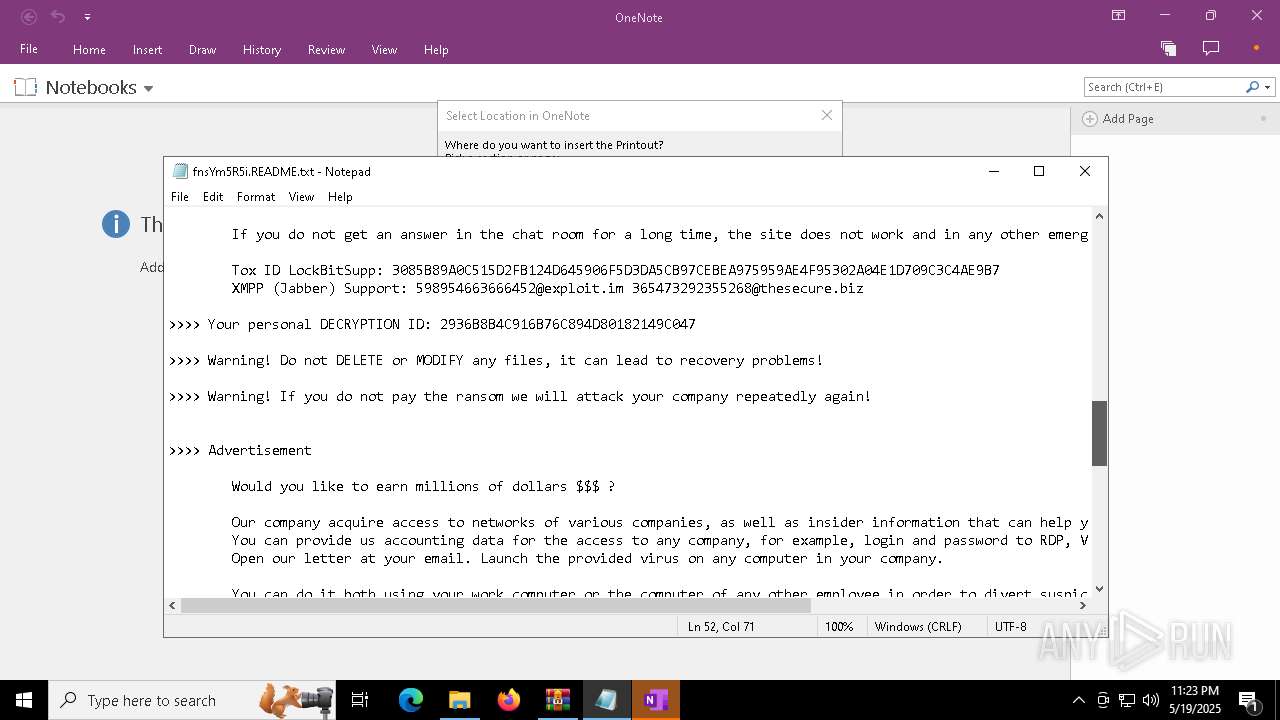
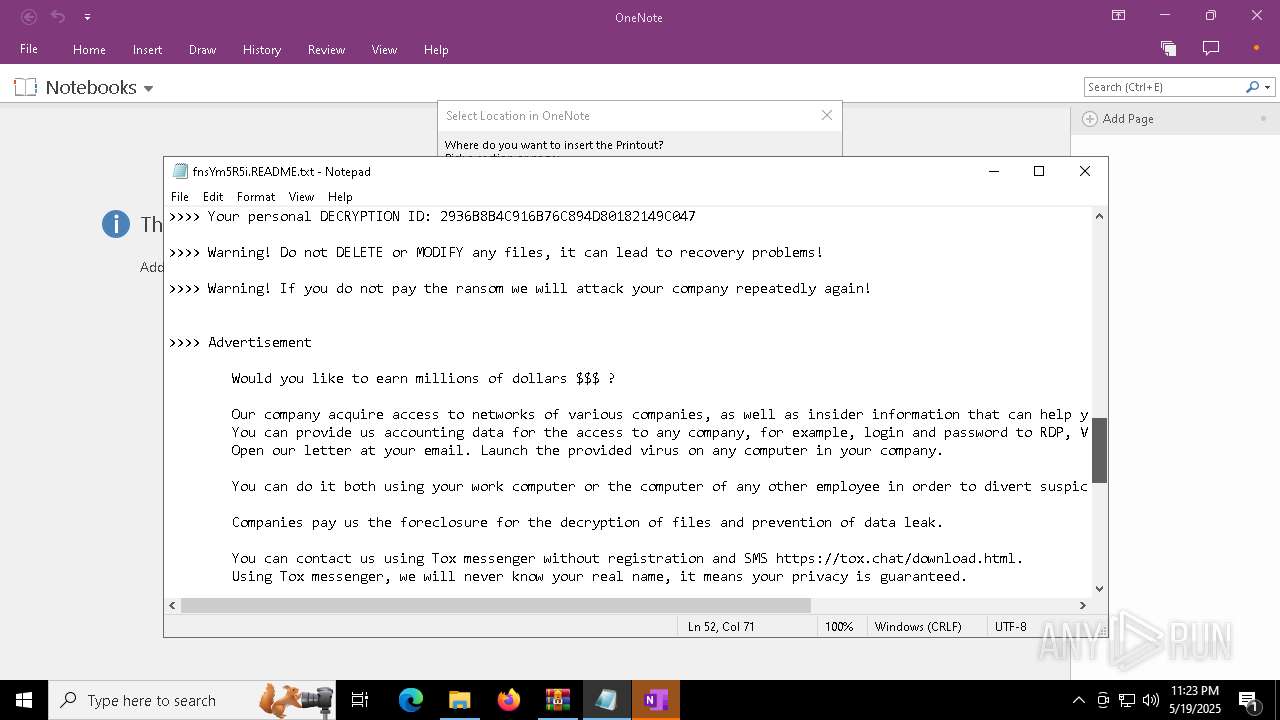
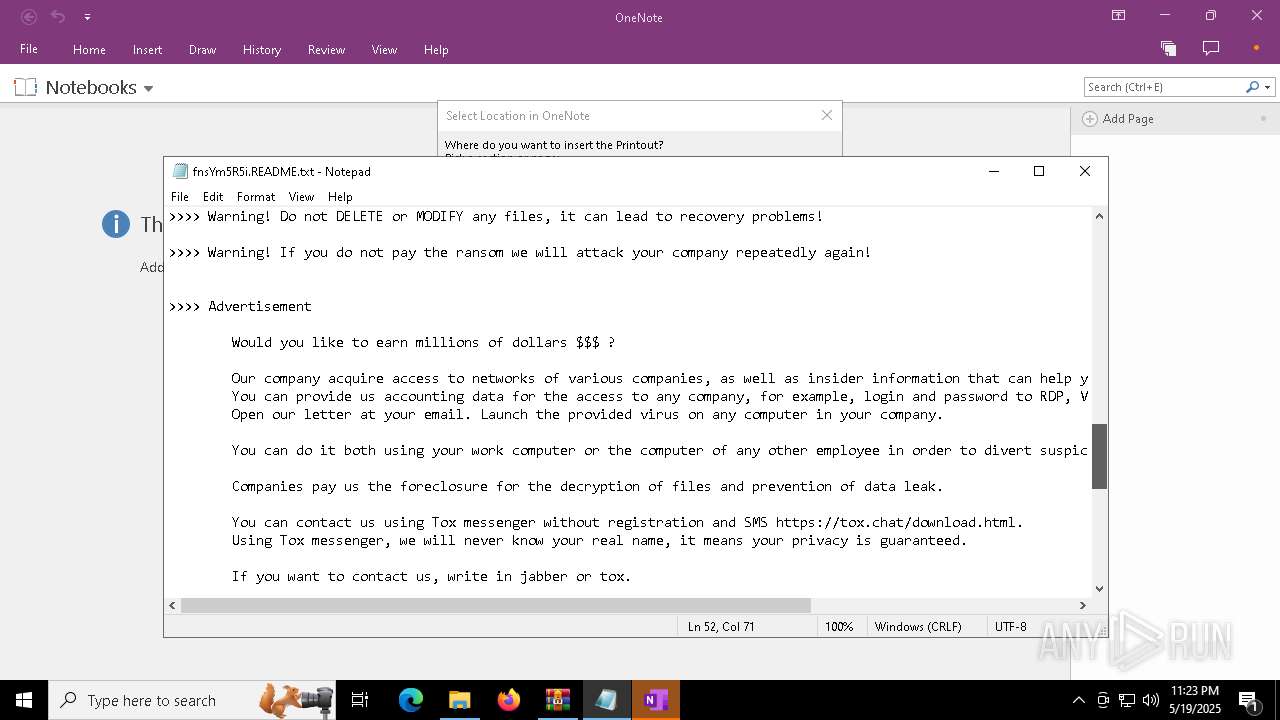
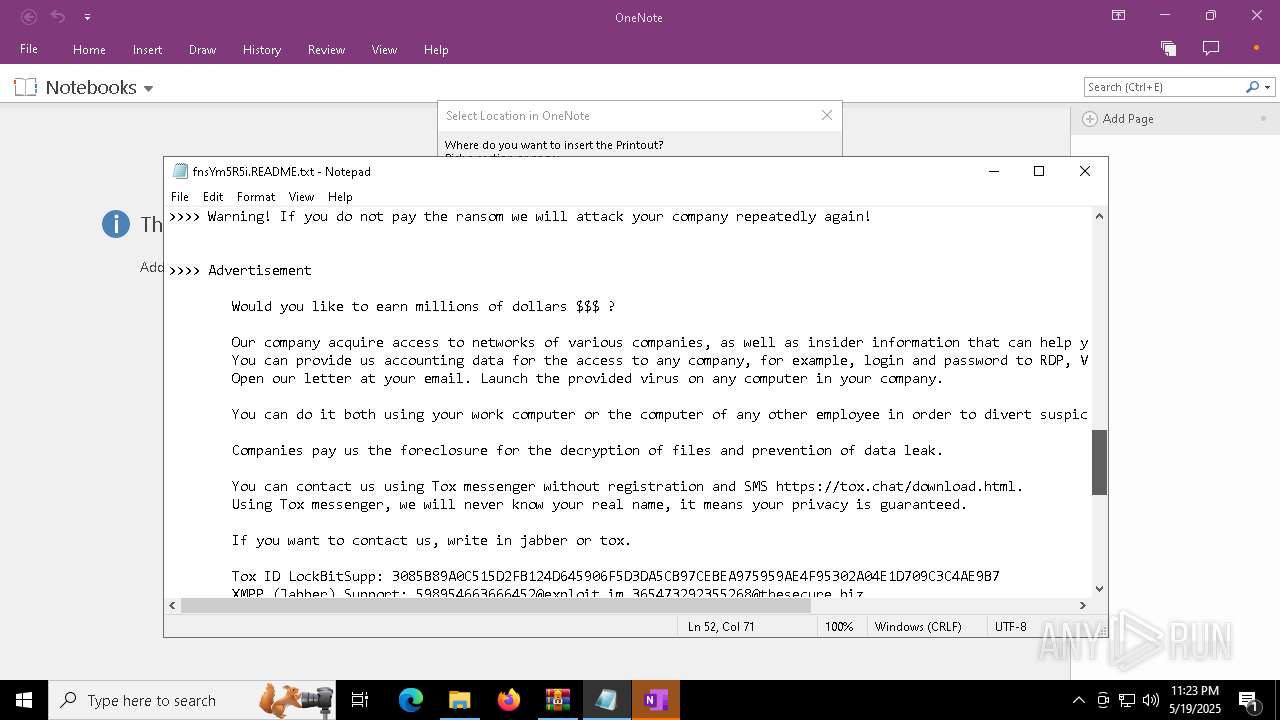
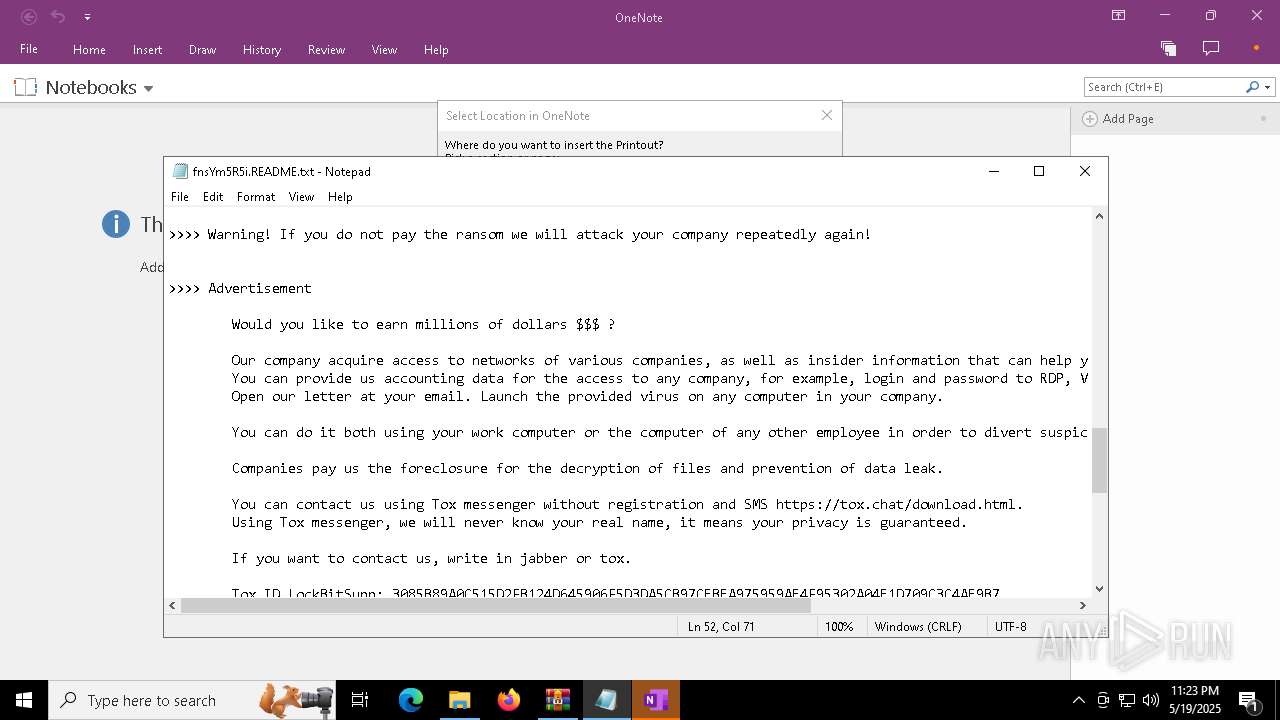
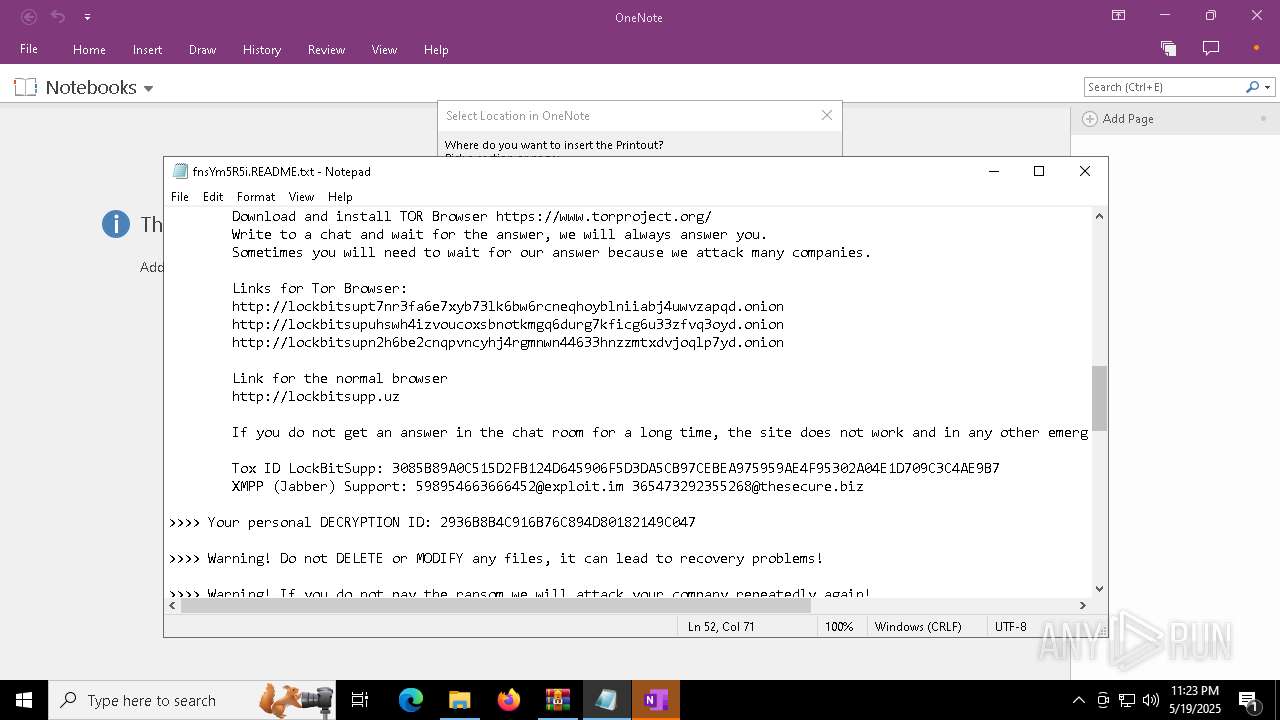
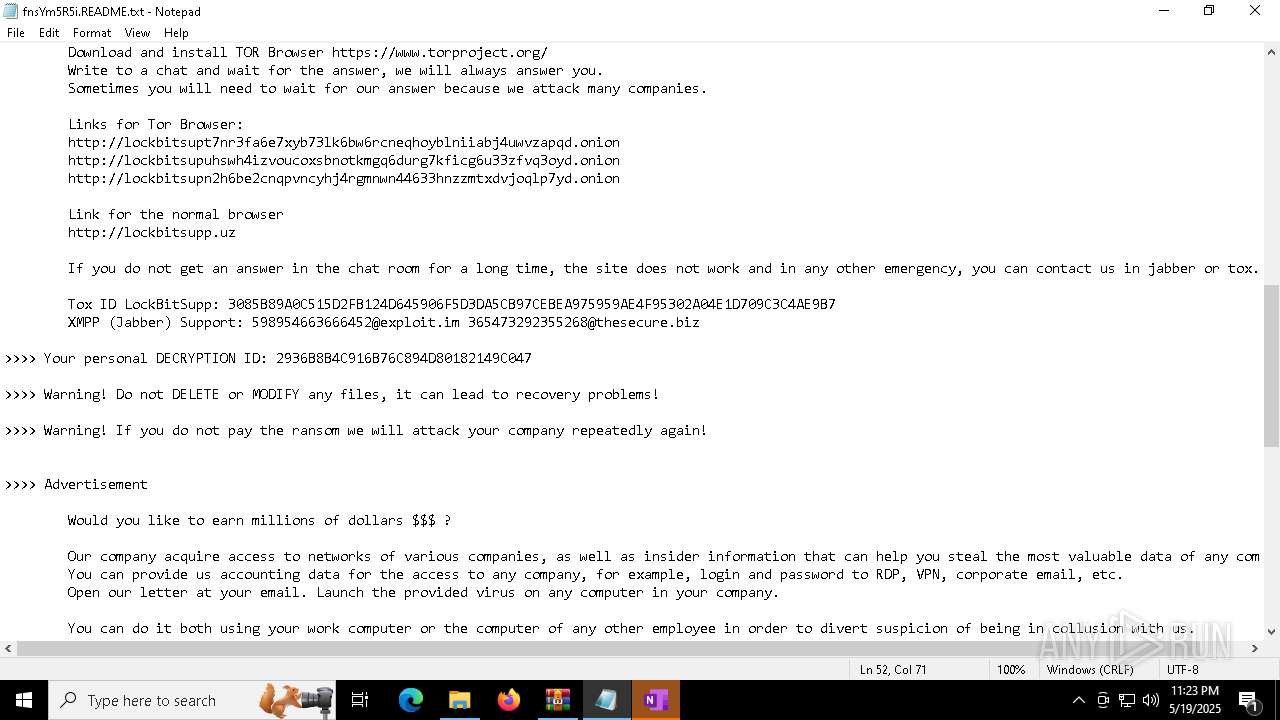
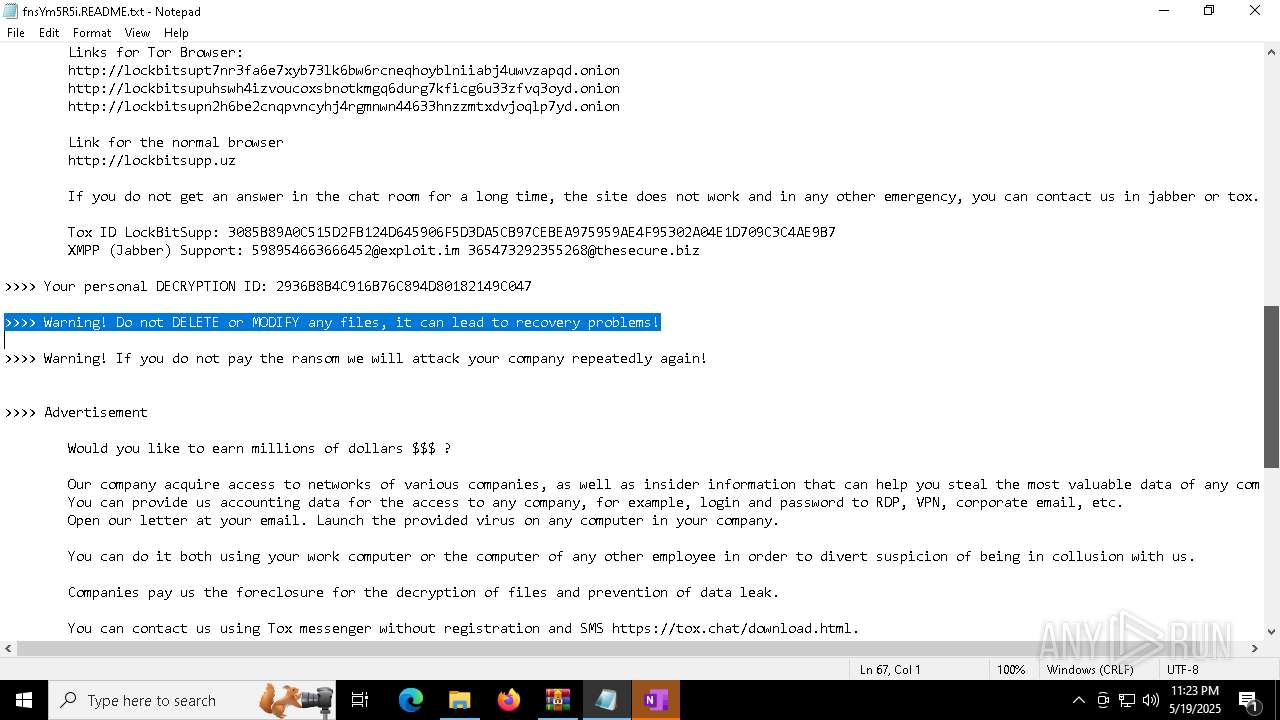
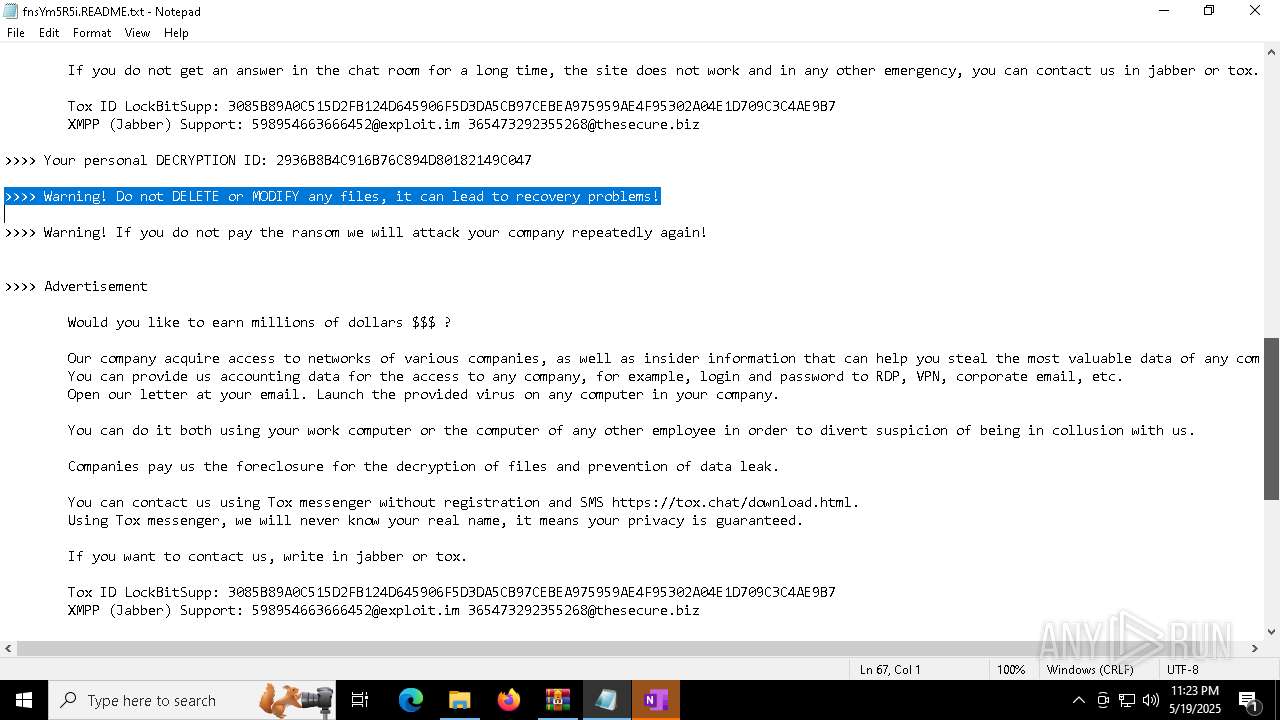
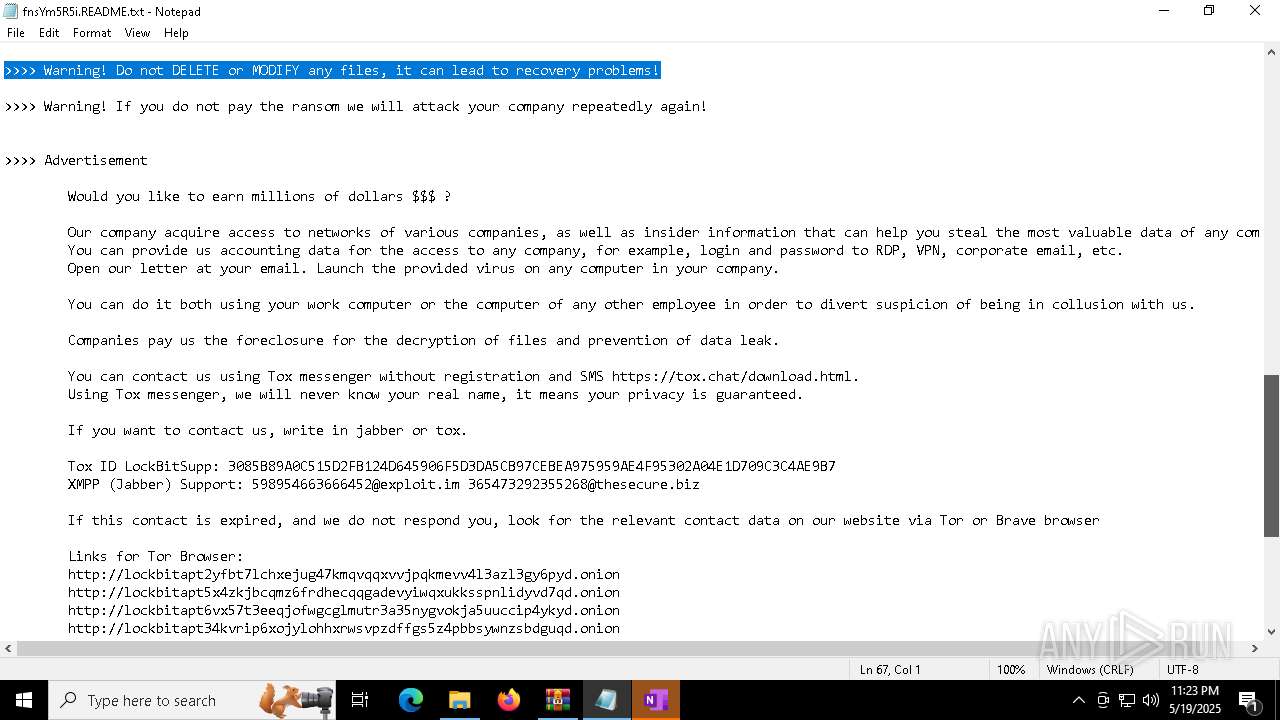
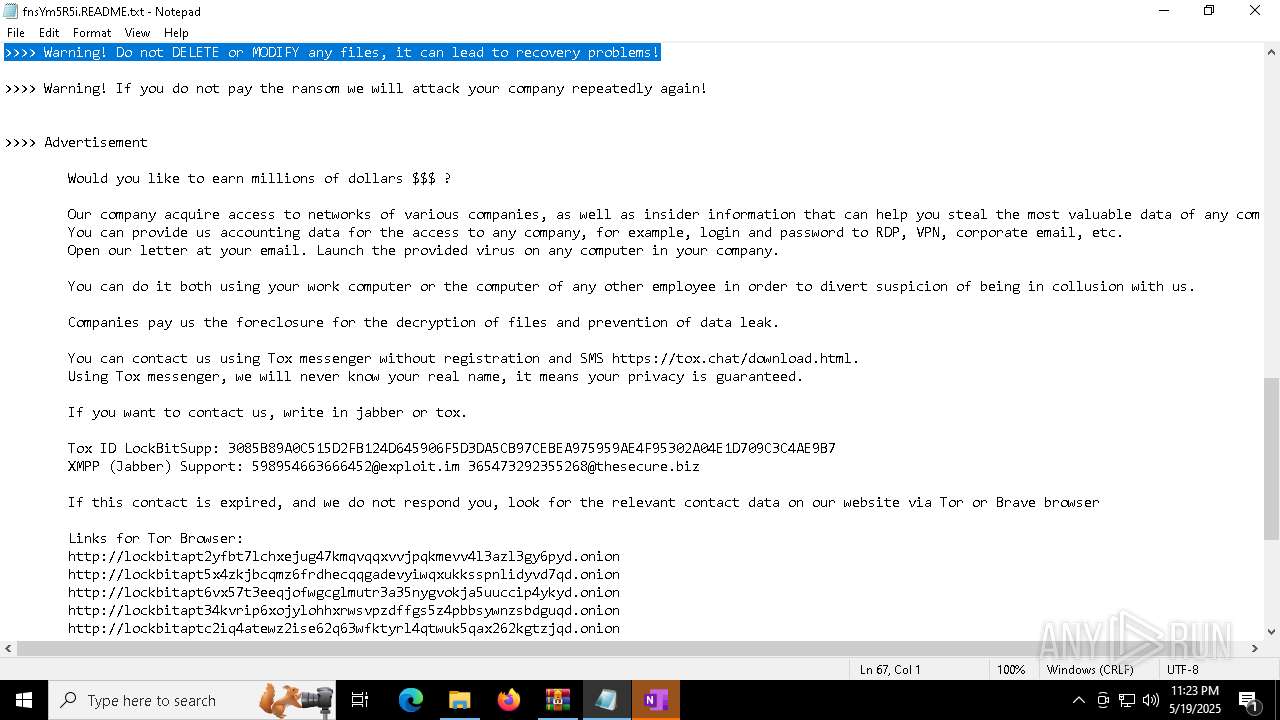
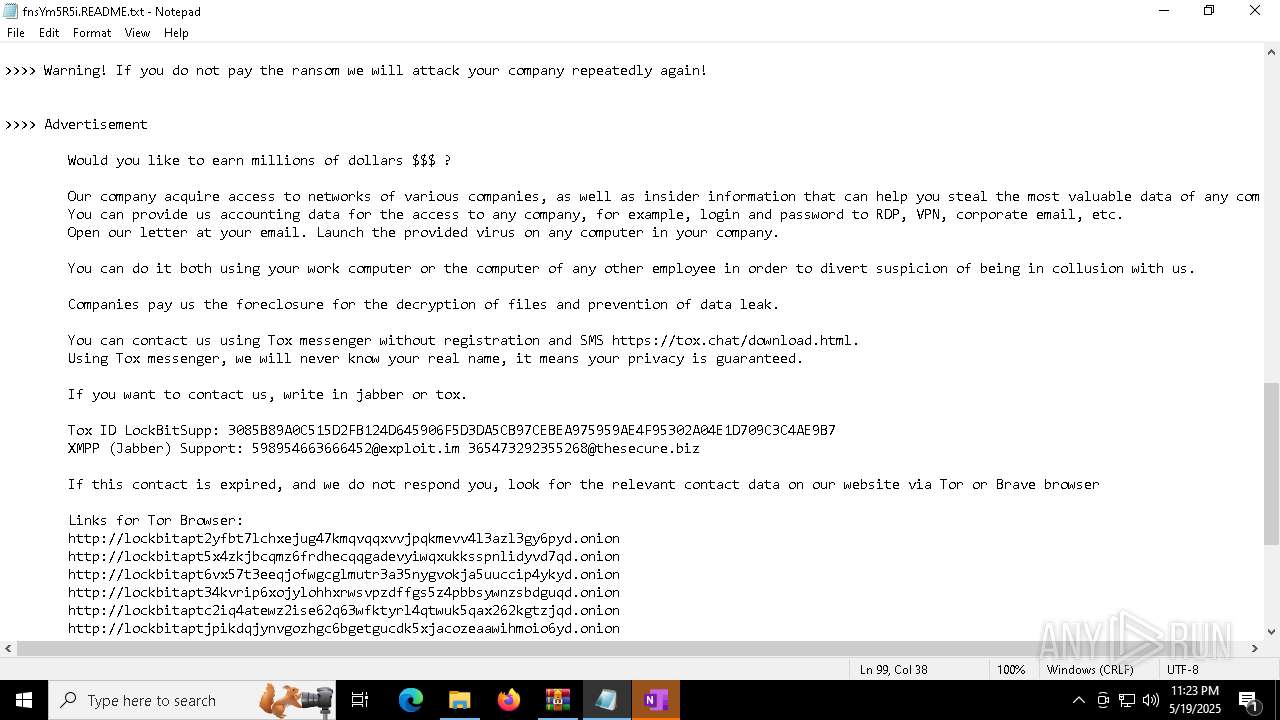
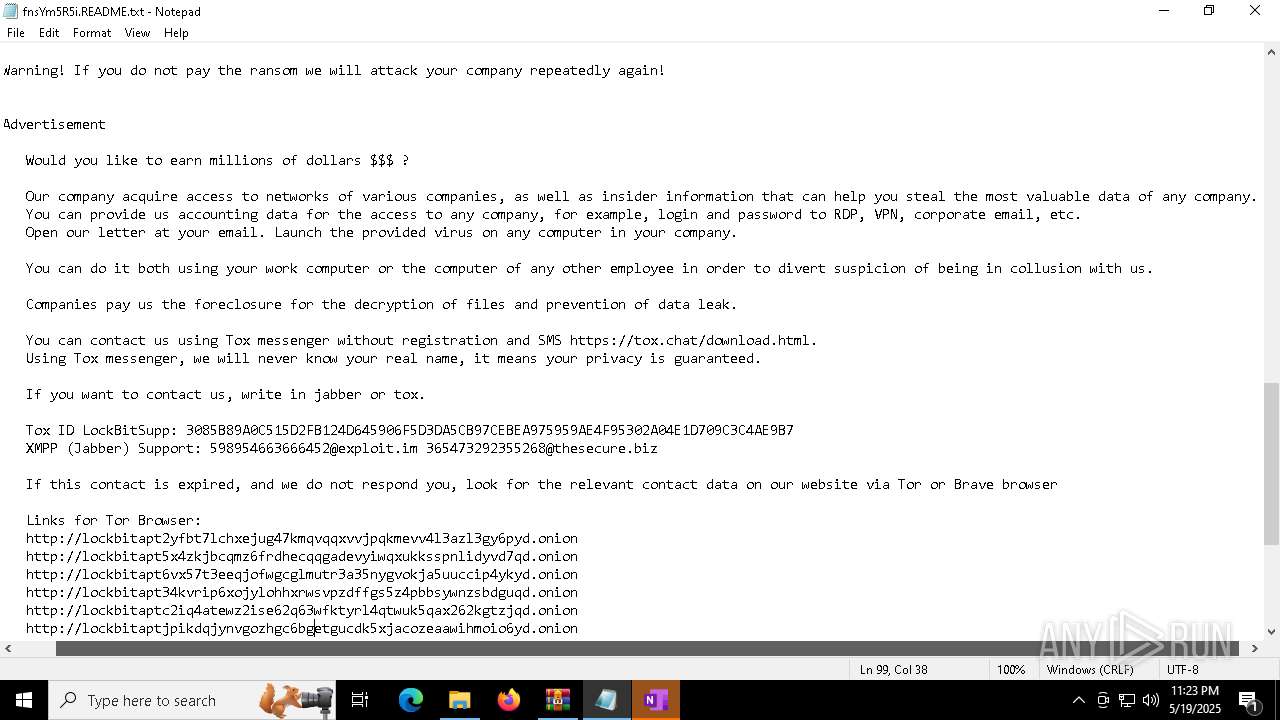
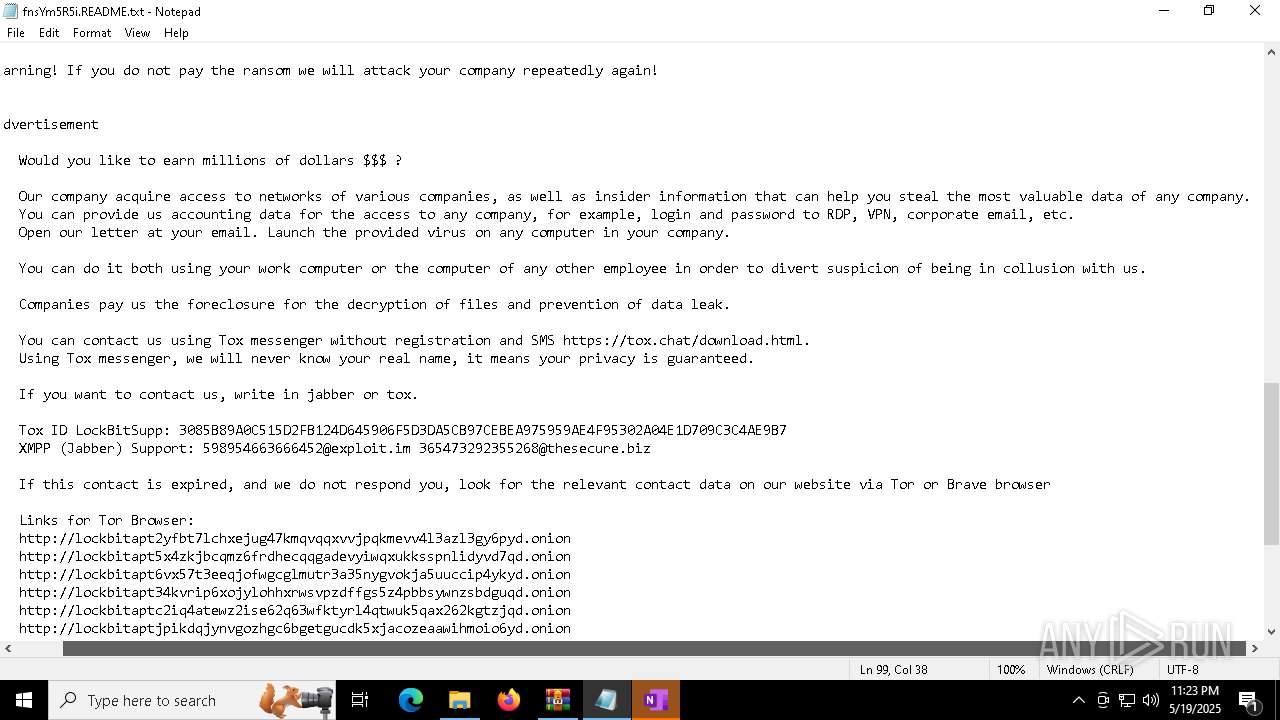
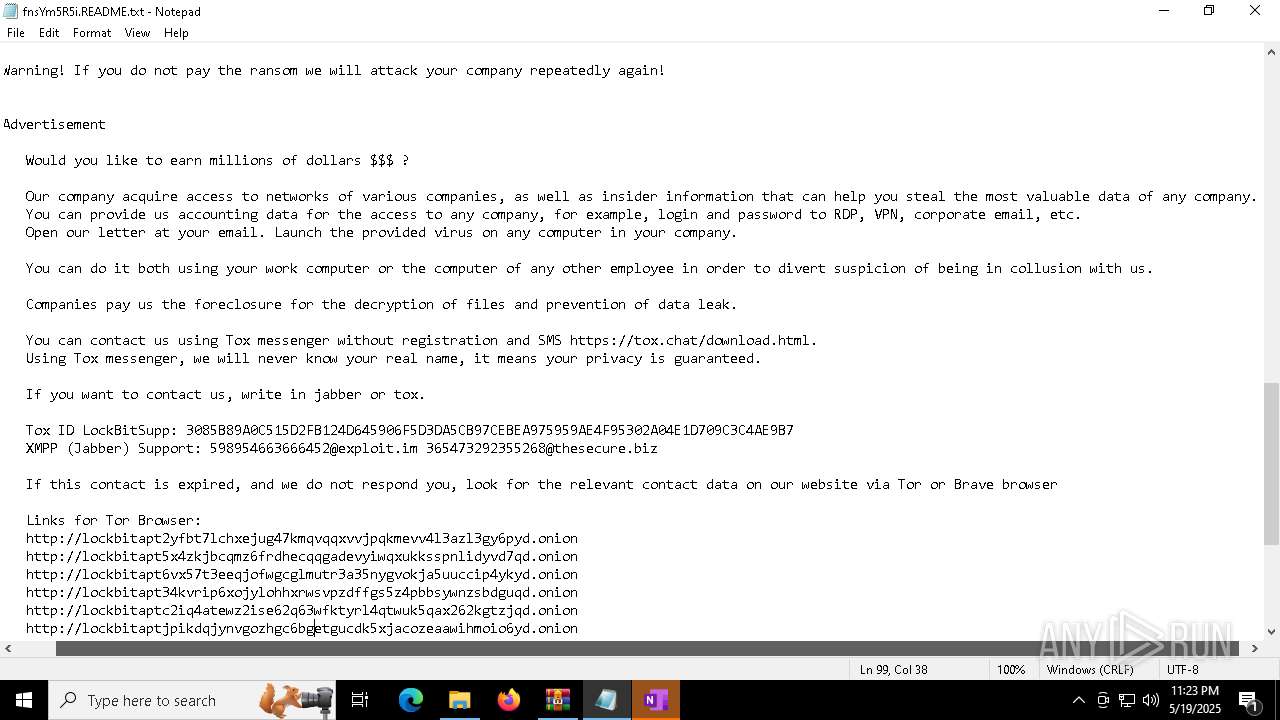
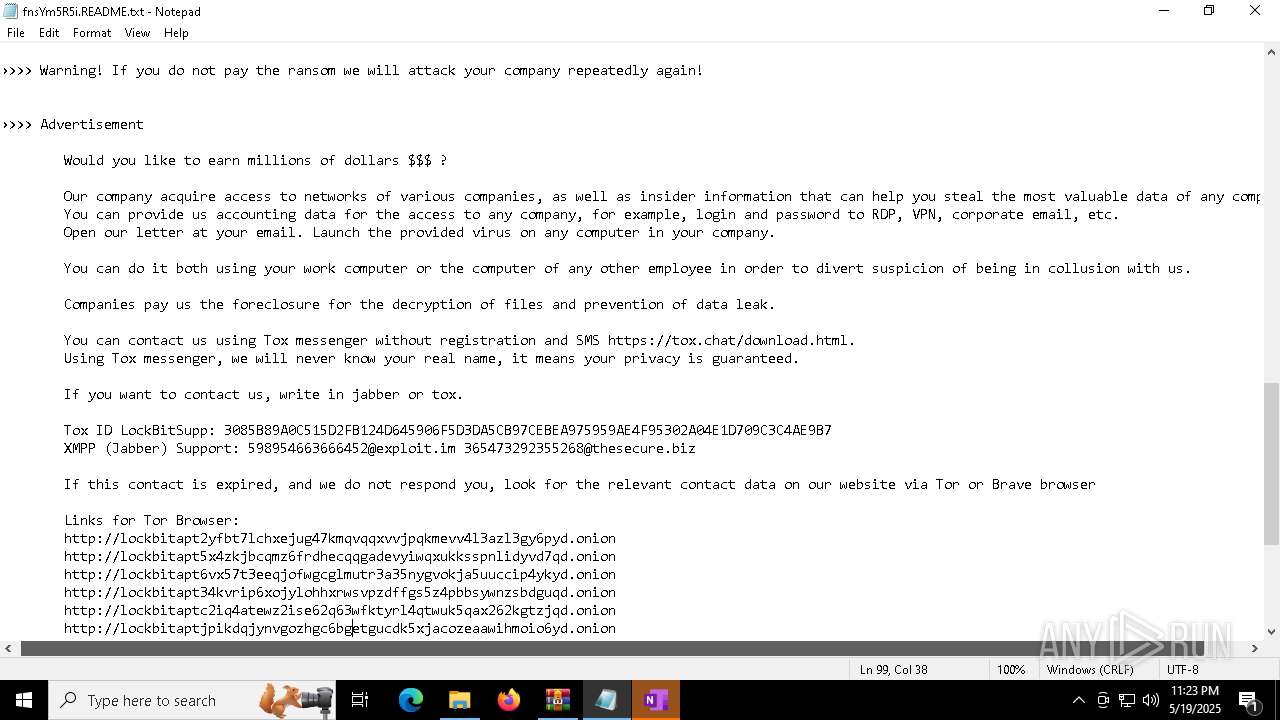
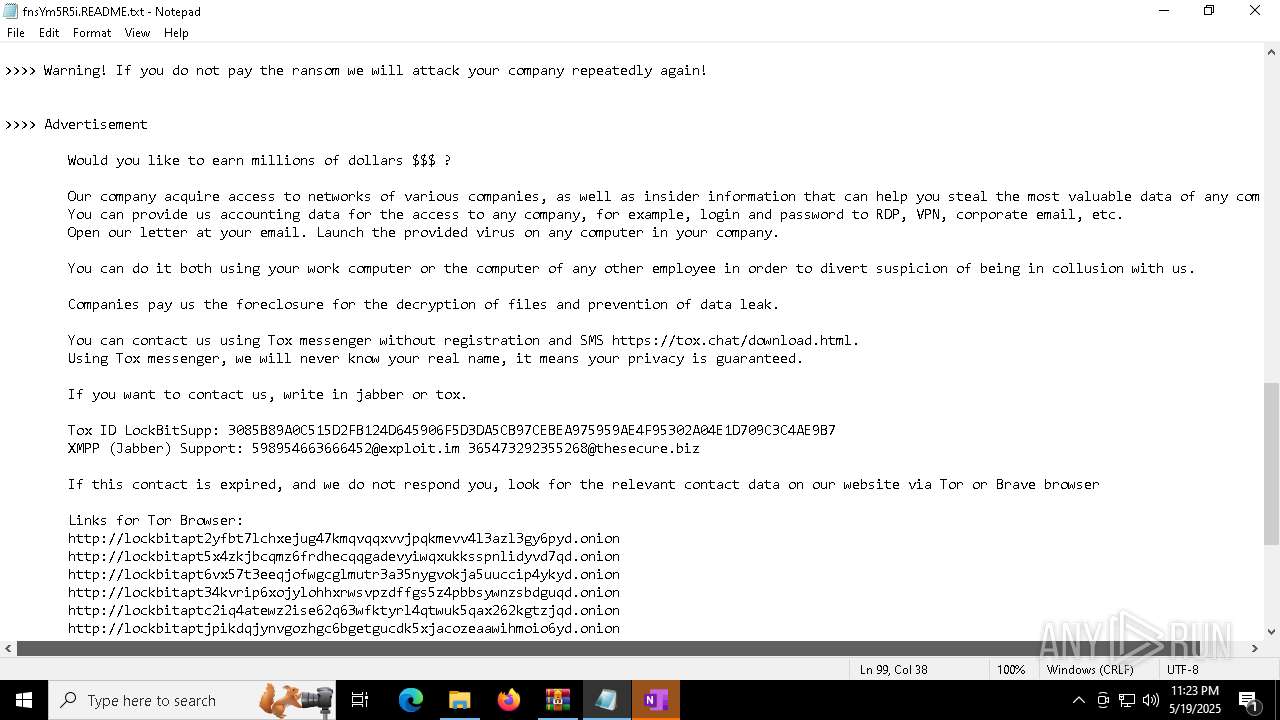
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | May 19, 2025, 23:19:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 07B3C45A82470D2FC0DD82485358A9CA |
| SHA1: | 3858B725AE8382CCEB46F1FBC2C40270099BB27E |
| SHA256: | BCB7E9DD4F098EAEE8B01F65E2EB7100C8C896EE1E0D3500F0AF14E58FCFC2A5 |
| SSDEEP: | 3072:J9MmlvjpPqDNVrAZJ7IGUiaV80h99ASAhUroIL5:3MgIpVrAZJ7AiaV80qSAdI5 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 496)
Renames files like ransomware
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
RANSOMWARE has been detected
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
[YARA] LockBit is detected
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
LOCKBIT3 has been detected
- DA57.tmp (PID: 7060)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 8084)
- wordpad.exe (PID: 632)
Executable content was dropped or overwritten
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Hides command output
- cmd.exe (PID: 1120)
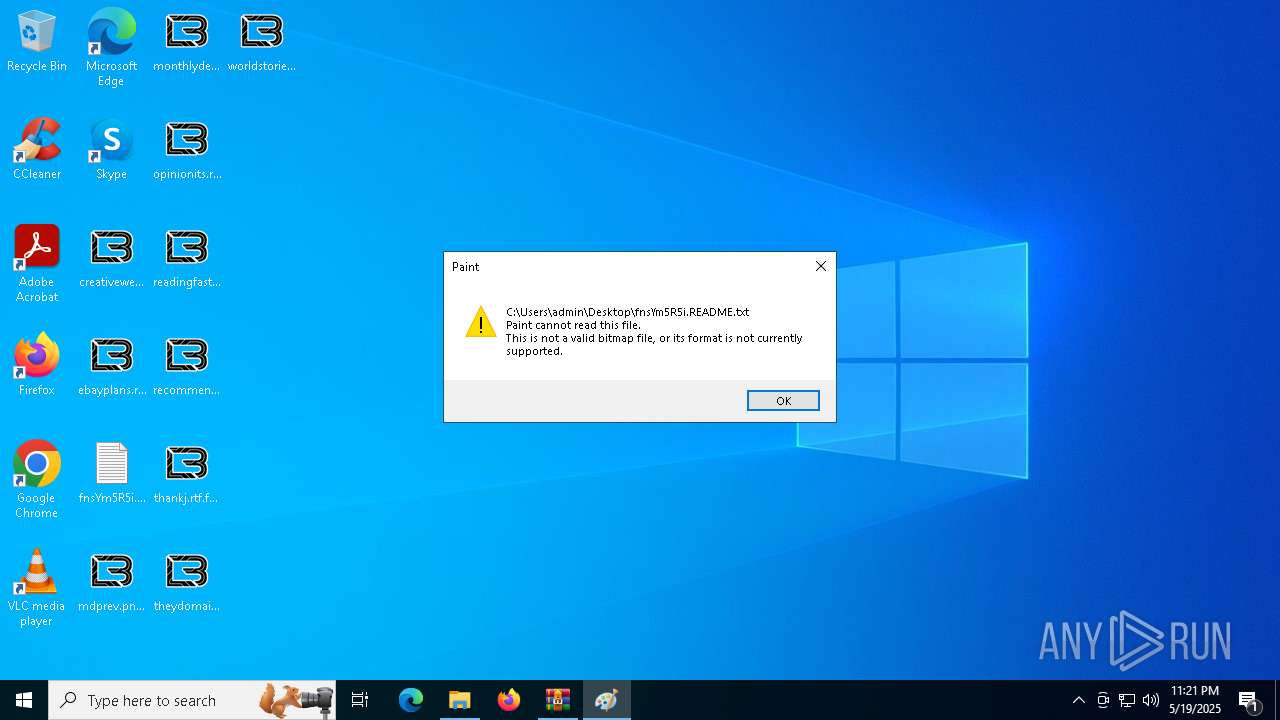
Starts application with an unusual extension
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Starts CMD.EXE for commands execution
- DA57.tmp (PID: 7060)
INFO
Reads the computer name
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
- ShellExperienceHost.exe (PID: 8084)
- wordpad.exe (PID: 632)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 496)
Creates files in the program directory
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Checks supported languages
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
- ShellExperienceHost.exe (PID: 8084)
- wordpad.exe (PID: 632)
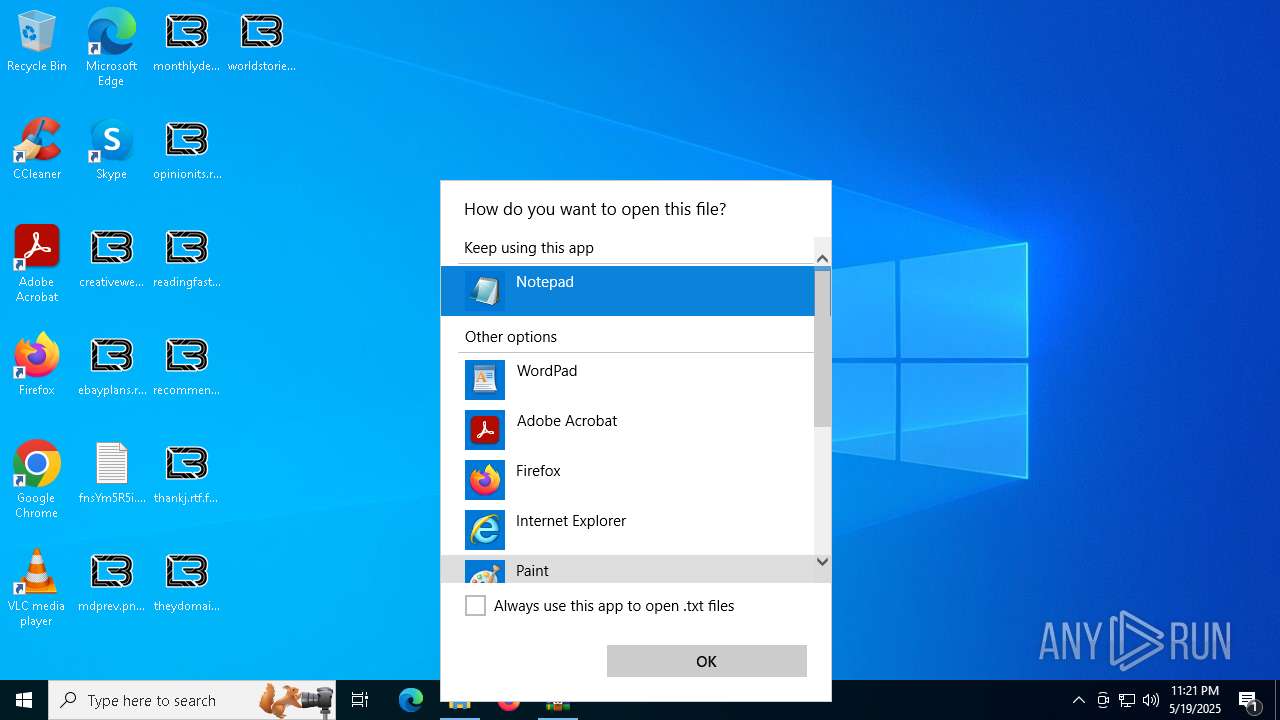
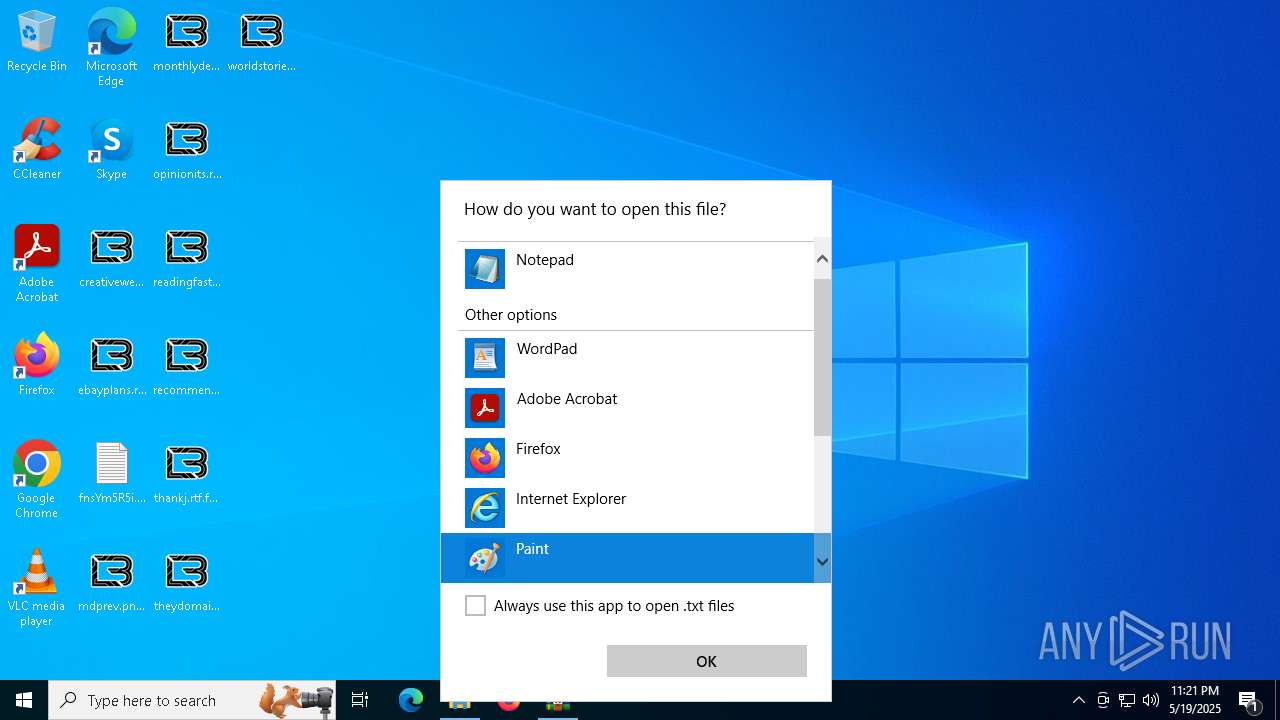
Manual execution by a user
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
- notepad.exe (PID: 7596)
- notepad.exe (PID: 2392)
- wordpad.exe (PID: 632)
- notepad.exe (PID: 7648)
- notepad.exe (PID: 5964)
- notepad.exe (PID: 6404)
- notepad.exe (PID: 7728)
- notepad.exe (PID: 7752)
- notepad.exe (PID: 3332)
- notepad.exe (PID: 744)
- notepad++.exe (PID: 7844)
- notepad.exe (PID: 232)
- notepad.exe (PID: 2908)
- notepad.exe (PID: 5360)
- notepad.exe (PID: 7768)
- notepad.exe (PID: 7824)
- notepad.exe (PID: 2596)
- firefox.exe (PID: 5044)
- notepad.exe (PID: 7688)
Creates files or folders in the user directory
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Create files in a temporary directory
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 7852)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7596)
- notepad.exe (PID: 2392)
- notepad.exe (PID: 5964)
- notepad.exe (PID: 7648)
- notepad.exe (PID: 7728)
- notepad.exe (PID: 6404)
Reads Environment values
- wordpad.exe (PID: 632)
Application launched itself
- firefox.exe (PID: 5344)
- firefox.exe (PID: 5044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:19 23:19:06 |
| ZipCRC: | 0x6601a46b |
| ZipCompressedSize: | 103143 |
| ZipUncompressedSize: | 157184 |
| ZipFileName: | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe |
Total processes
184
Monitored processes
38
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\fnsYm5R5i.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 552 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files\Windows NT\Accessories\WORDPAD.EXE" "C:\Users\admin\Desktop\fnsYm5R5i.README.txt" | C:\Program Files\Windows NT\Accessories\wordpad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\fnsYm5R5i.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | "C:\WINDOWS\System32\cmd.exe" /C DEL /F /Q C:\PROGRA~3\DA57.tmp >> NUL | C:\Windows\SysWOW64\cmd.exe | — | DA57.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url C:\Users\admin\Desktop\fnsYm5R5i.README.txt | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2392 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\fnsYm5R5i.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\fnsYm5R5i.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 839
Read events
24 027
Write events
2 770
Delete events
42
Modification events
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.zip | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
25
Suspicious files
2 152
Text files
2 432
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\JJJJJJJJJJJ | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\KKKKKKKKKKK | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\LLLLLLLLLLL | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\desktop.ini | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\AAAAAAAAAAA | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 496 | WinRAR.exe | C:\Users\admin\Downloads\77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | executable | |
MD5:278F2869944F6AE0311AEF80A379F3F2 | SHA256:77EBB550F38DA3F28A65940A4C665AE3A679249AD906AA39387568A1F7DDD3FA | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\HHHHHHHHHHH | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
| 7852 | 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe | C:\$Recycle.Bin\S-1-5-18\MMMMMMMMMMM | binary | |
MD5:073A890A1CCC9A64C0381CC25F2C9CD3 | SHA256:0CB82033269C33490F5CDA78FC97D1EF86F8FDBA70F45E7D1FEF2DFABD2768C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.170:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6480 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5572 | ONENOTE.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5572 | ONENOTE.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4996 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.170:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6268 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |