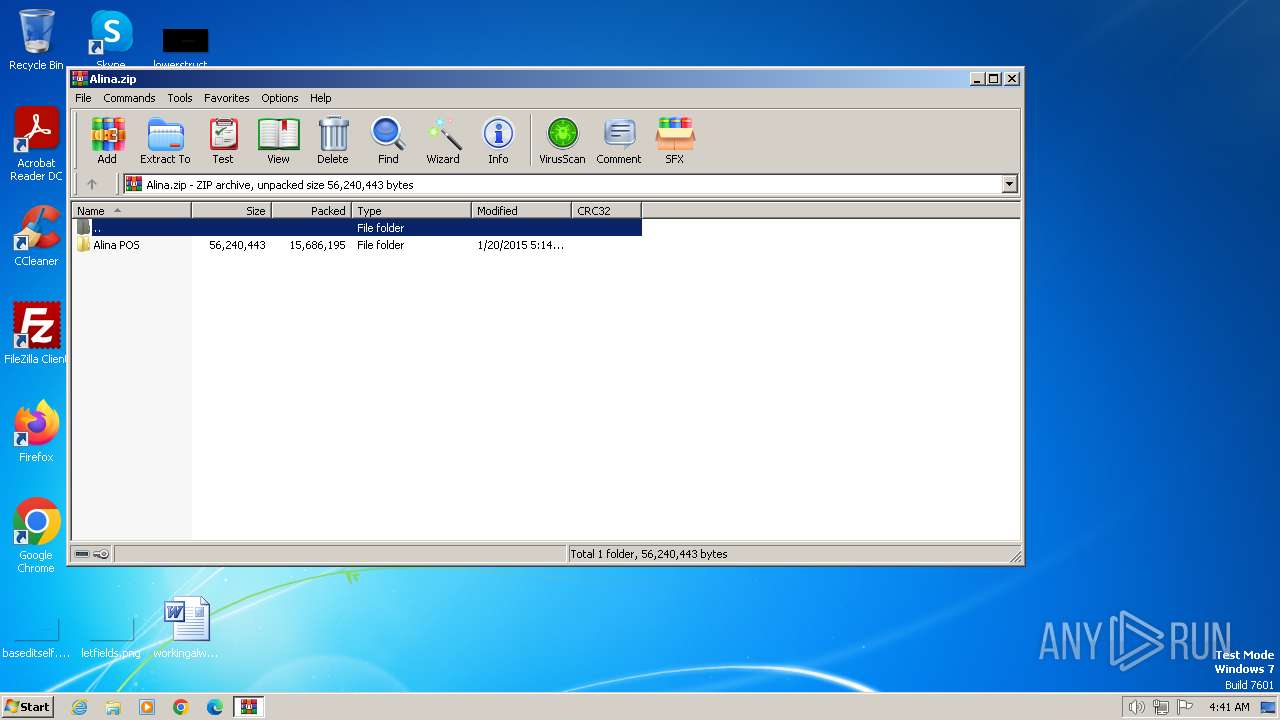
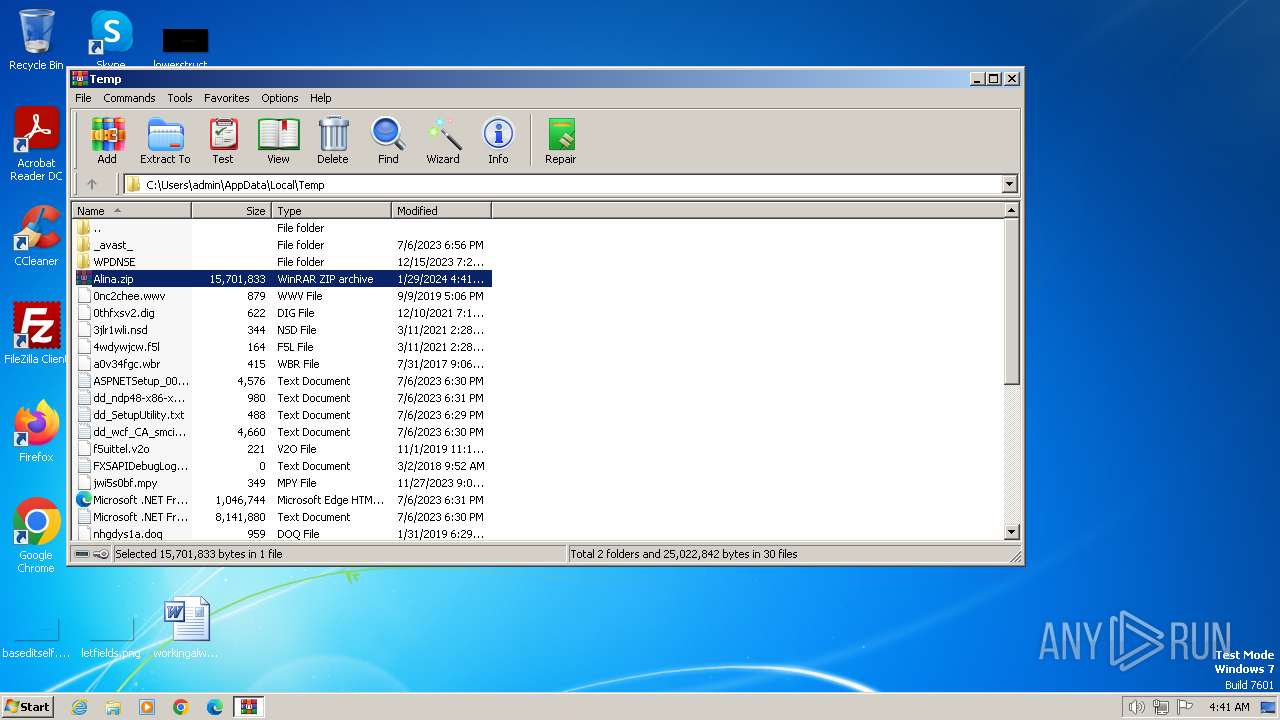
| File name: | Alina.zip |
| Full analysis: | https://app.any.run/tasks/66b8d5c5-0368-40aa-9118-0284855545b6 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2024, 04:40:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 9A70586AF61CAEF844A0A9969B2D5C36 |
| SHA1: | 215868350BDD2C4AF3B1A71209E518500D9A7BB6 |
| SHA256: | BC9C0D26872140B2ECB156AB065E02A85CF483E407BE9AEEB66F701A7F9B3EB3 |
| SSDEEP: | 98304:6+ScpO9zf0N18zVYJEIblXyrwLdArAgmpOXeodEpgjkbqWpWLajyPbF1606ICdx7:LR2fbqZvLwhdtIy81DIQ6IVQxejvb9 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1936)
- Spark.exe (PID: 452)
Runs injected code in another process
- windefender.exe (PID: 2712)
Application was injected by another process
- explorer.exe (PID: 1164)
SUSPICIOUS
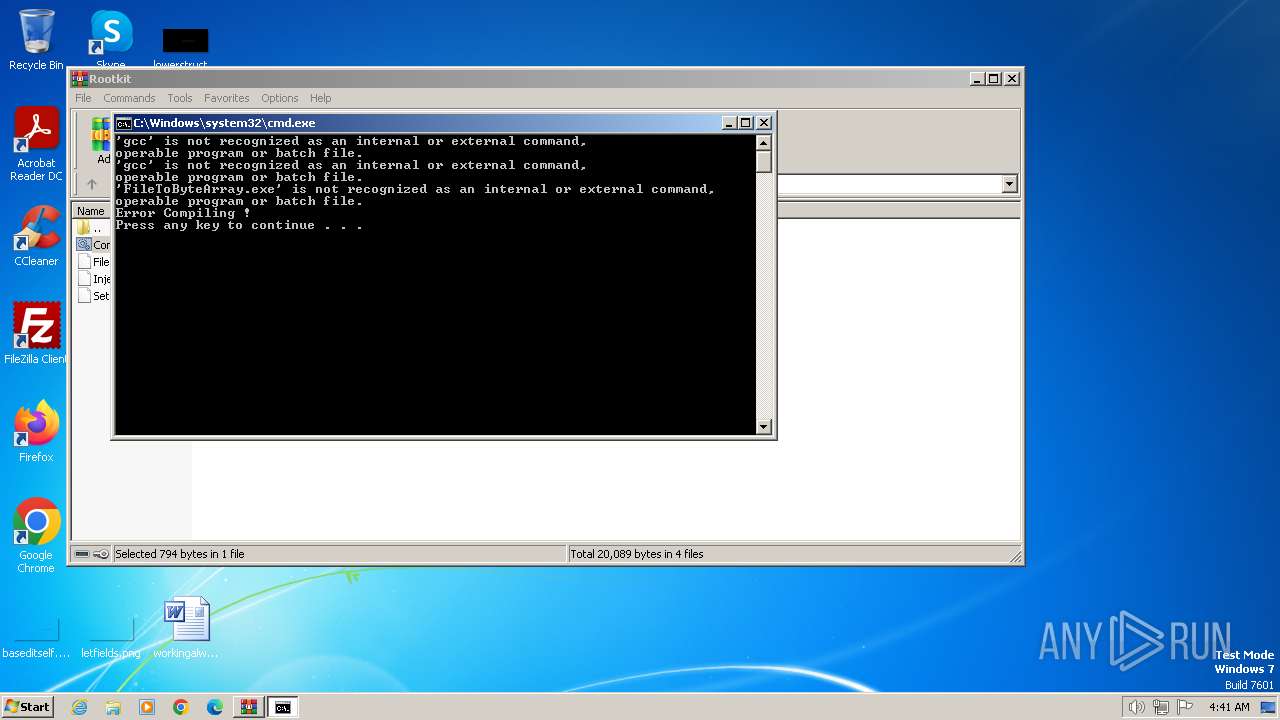
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1936)
Starts itself from another location
- Spark.exe (PID: 452)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 1936)
Executable content was dropped or overwritten
- Spark.exe (PID: 452)
Reads the Internet Settings
- Spark.exe (PID: 452)
INFO
Checks supported languages
- Spark.exe (PID: 452)
- windefender.exe (PID: 2712)
Reads the computer name
- Spark.exe (PID: 452)
- windefender.exe (PID: 2712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1936)
Creates files or folders in the user directory
- Spark.exe (PID: 452)
Checks proxy server information
- Spark.exe (PID: 452)
Reads the machine GUID from the registry
- Spark.exe (PID: 452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2015:01:20 19:14:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
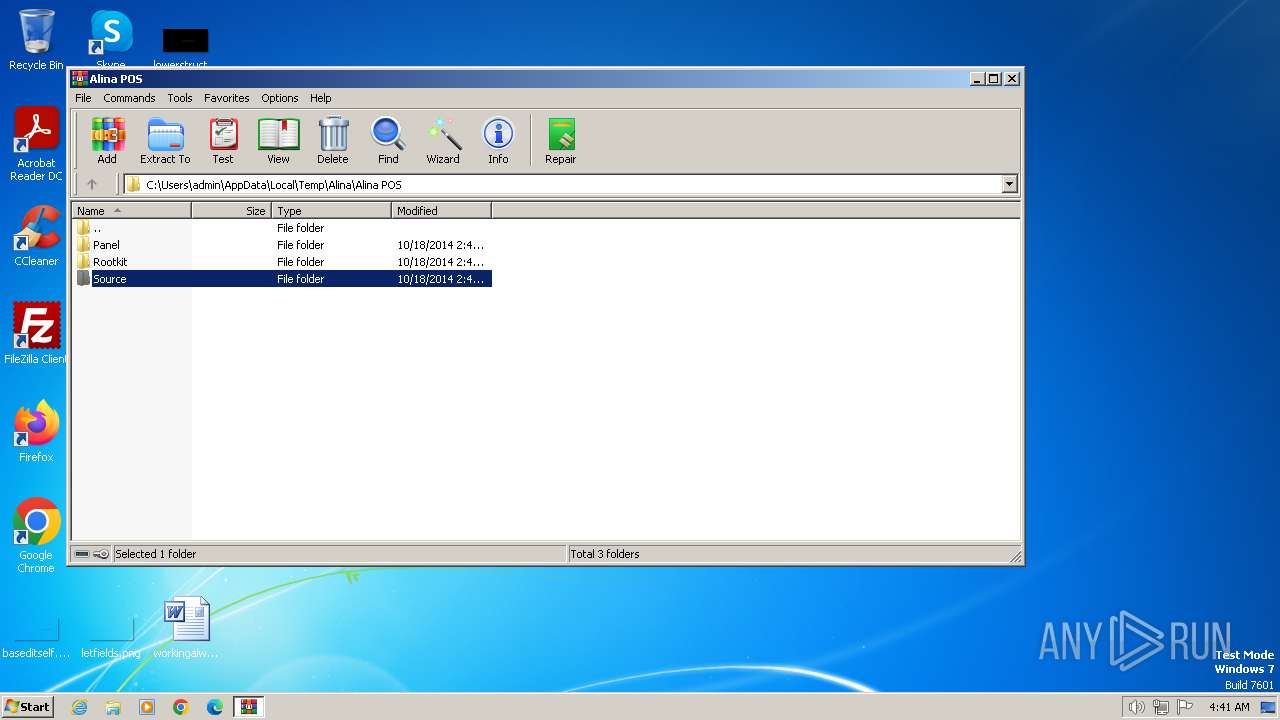
| ZipFileName: | Alina POS/ |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Source\Debug\Spark.exe" | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Source\Debug\Spark.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Alina.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
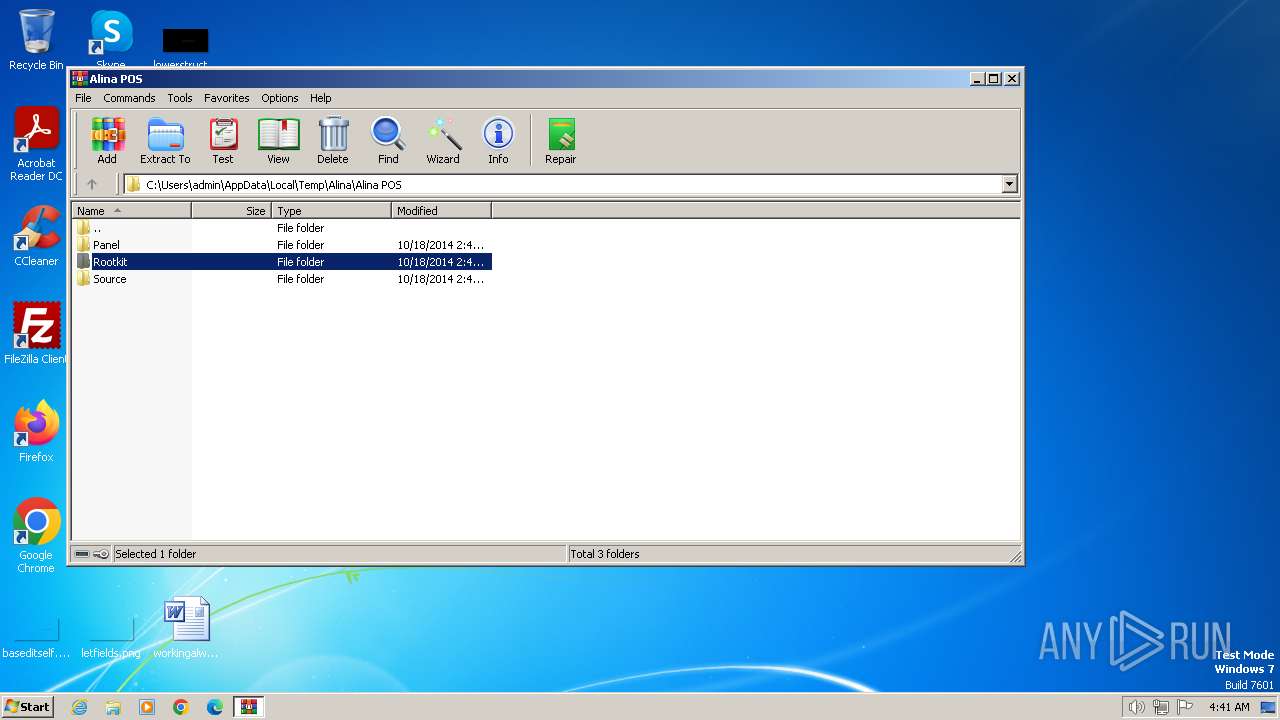
| 2560 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Rootkit\Compile.EXE.GCC.cmd" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2712 | "C:\Users\admin\AppData\Roaming\Installed\windefender.exe" | C:\Users\admin\AppData\Roaming\Installed\windefender.exe | — | Spark.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 803
Read events
1 752
Write events
51
Delete events
0
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C4700000000020000000000106600000001000020000000714C0B985B0540658F4A2080B484A48FEA0193B4945278E76DEADC9EF300F178000000000E80000000020000200000002B477AD6A48910EDA2BF44A8E4FAAFB7E2EDF3EE6F87B8965B303D8016BD90EA30000000CB02147CAA96DADF9F5A3BD08AC8A954F632048A3EC443FAA534C64E43A96953CAB4A202A2BC0443ADBC5B693897DBB44000000078BCD17E1DCD91E99A86D38616C049FA8C5E2A7C07BB269B76B0709DC8A01ABF25866BF6638D5C4422D1151CE173748901F5A2433E1BD07914E254B07BB130FD | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
17
Text files
53
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
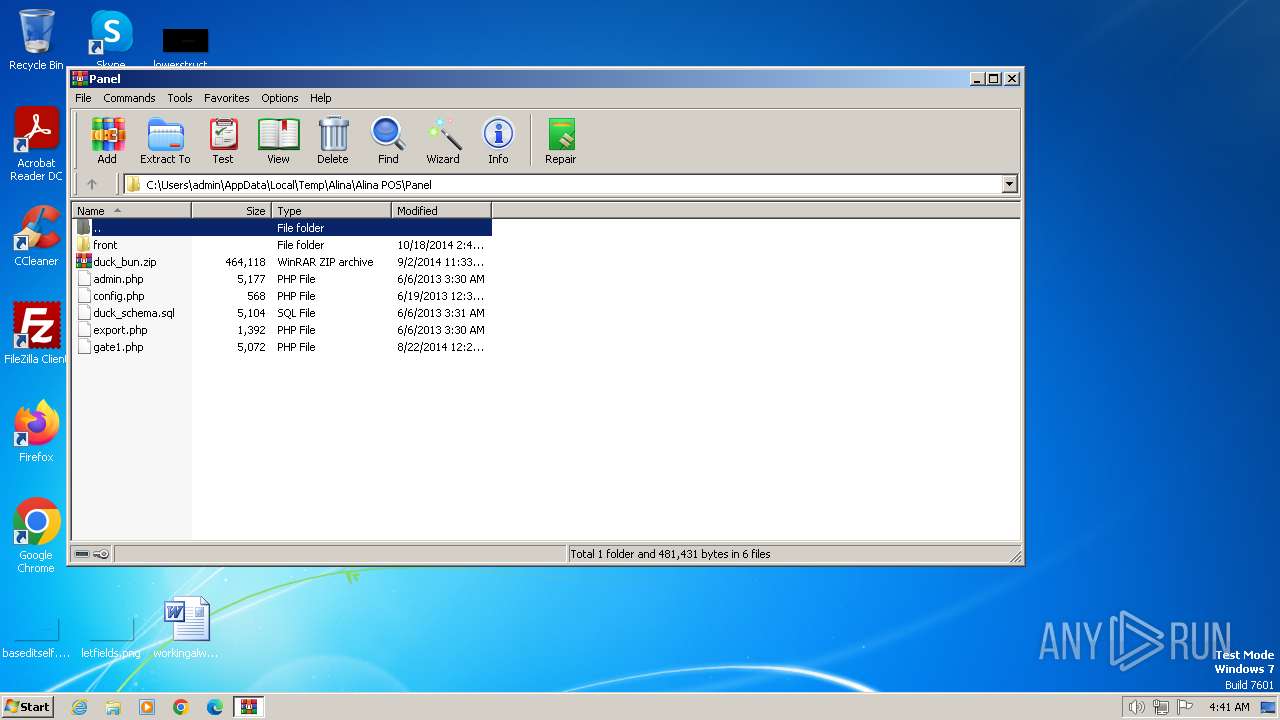
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\duck_bun.zip | compressed | |
MD5:93E4987B574B90617CE3F46C881E722C | SHA256:4C9946D4DD1E96F6AE84E5E1FC9593CE08EA1A0764E30F8EDE2C6AC0D76ED140 | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\config.php | text | |
MD5:4BE5EE8896A23174D0214277A26DA037 | SHA256:3E5C3121D8BDE1172FF581DE42818A7DA6243ED3DB302D0148EE7689CF1FD565 | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\export.php | text | |
MD5:510B9441E110B57B2F08E7E3BB3F5AE6 | SHA256:F92FC8009D090077F8B85759CC0973BC0C337B9F25DC806A70FDD2139440B1D2 | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\front\cards.php | text | |
MD5:6D3D961F1406EF324D13372085A1859E | SHA256:428F6A813974AC68D58824BD3D5510287173061AC3D927C80E2F76930CC28ABD | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\front\bins.php | text | |
MD5:CEECA517AB3D96E674BAADA18F8BB16A | SHA256:E8D6B897F8F94D20ABA38A8D61B826E89A3DA0A12FF1EE505B1AE1C2E1AC6A93 | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\duck_schema.sql | text | |
MD5:4197648EEB8BD58B97281F4CAF1BF555 | SHA256:FB34764F6A11BAB68FA507720922A3C0770CD169DD6D6A60BC3049859FE1AE96 | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Panel\admin.php | text | |
MD5:4A20AF8E9A5C4AEC6809545F30DE3879 | SHA256:55A5787E9AF116203675B71F10DB38E6B334B2228D30568BF54E30364E4B202F | |||
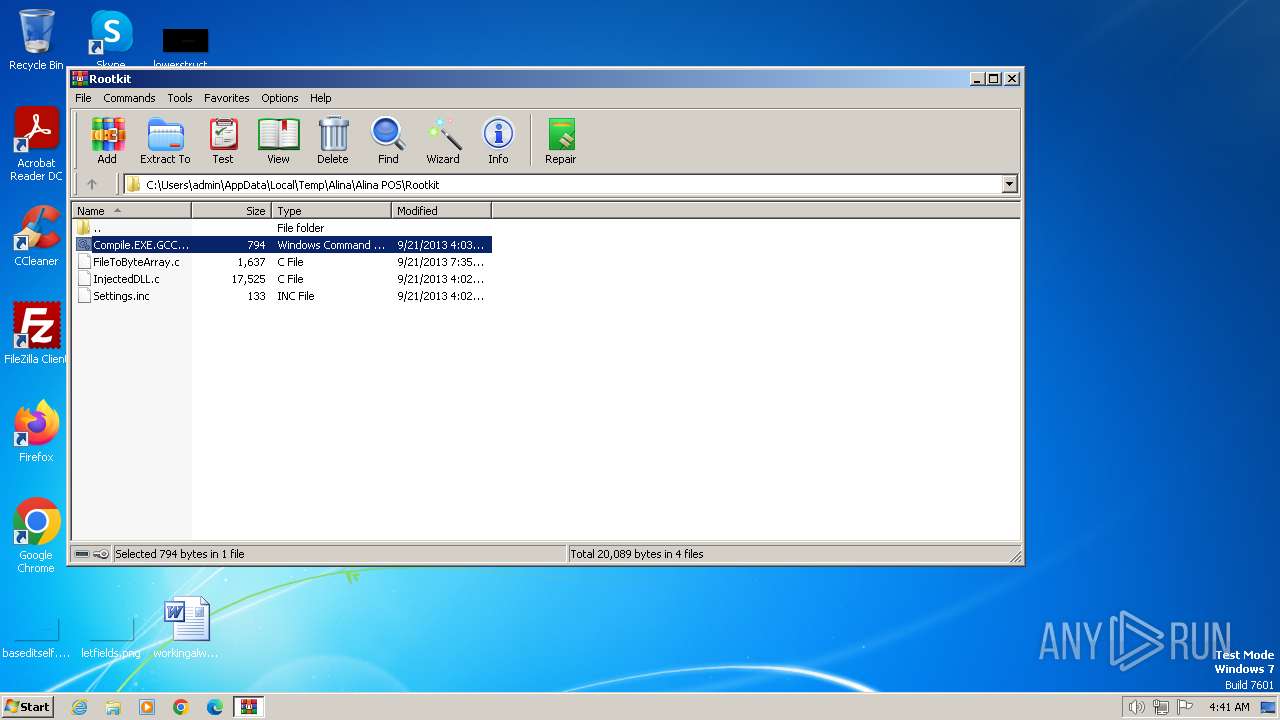
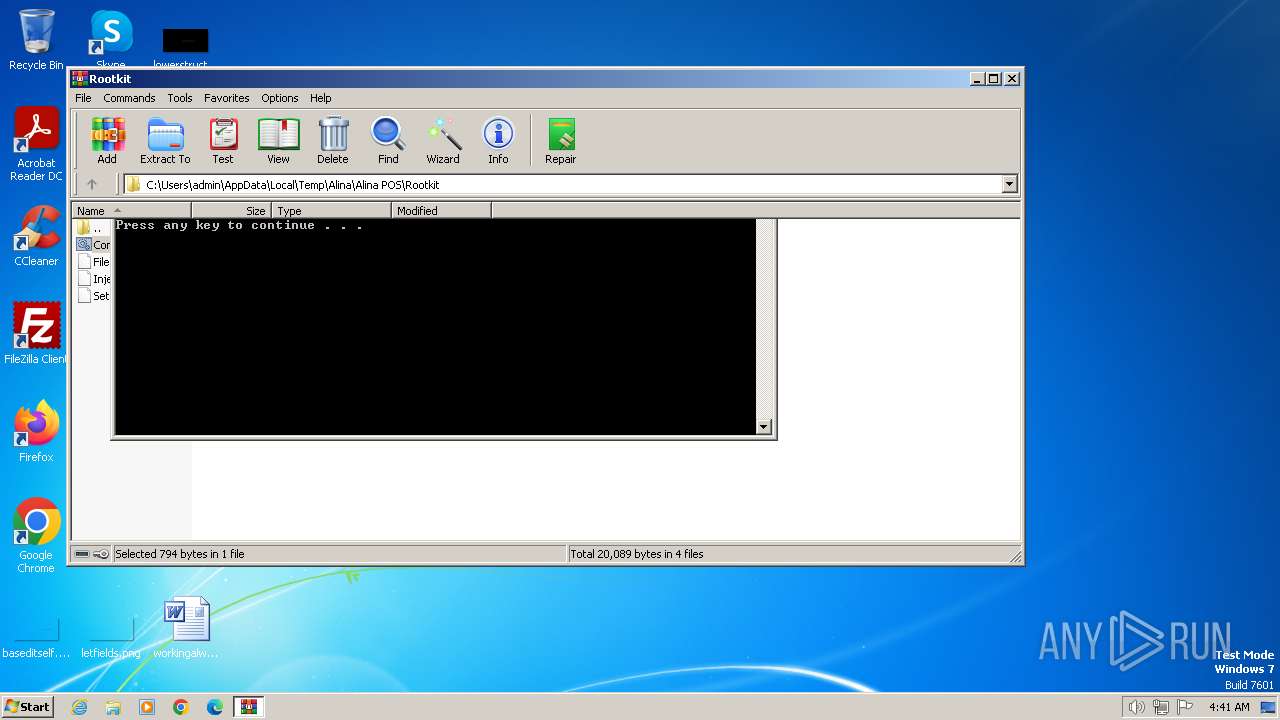
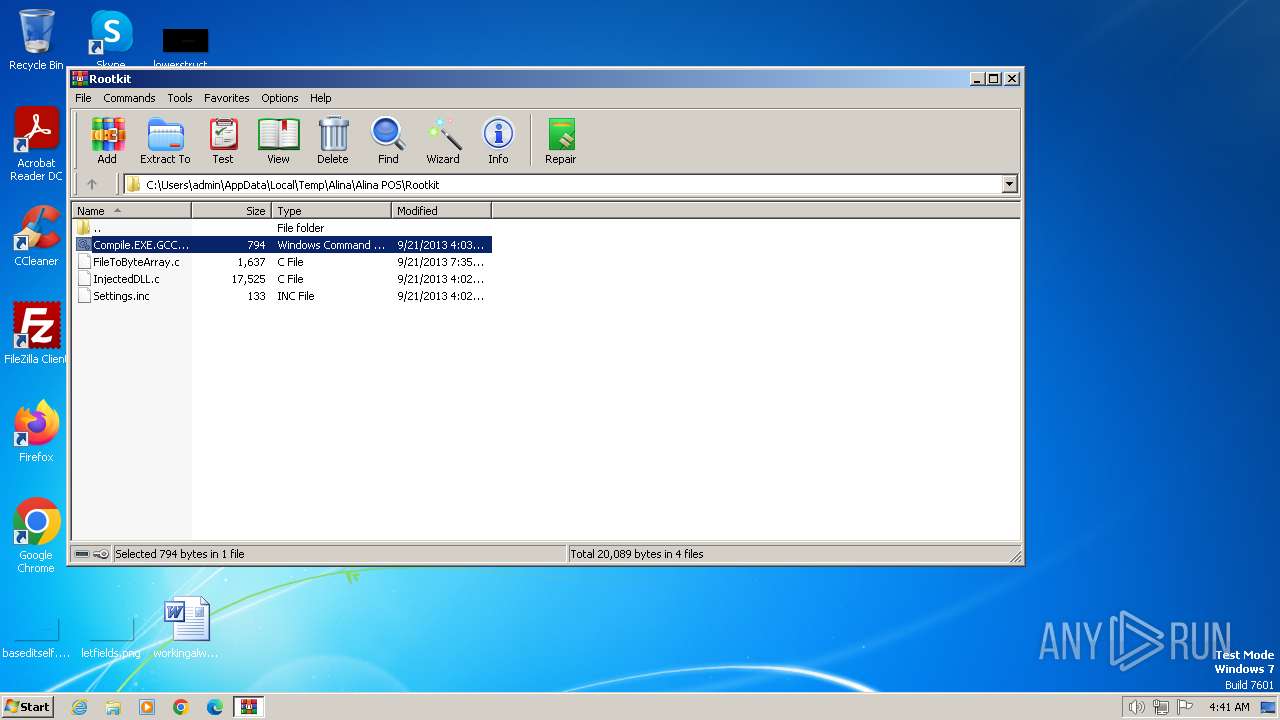
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Rootkit\Settings.inc | text | |
MD5:260929D29B20FAF82427F25FF0B01007 | SHA256:E4AC3BB8077585C431B4C96401B53CC06DE32D9A7AD0D08B661A4F7A6E4ED17D | |||
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Rootkit\Compile.EXE.GCC.cmd | text | |
MD5:DFFF42AE6040DCCD15A2FAA591D195F9 | SHA256:6B4F45F0CE1A29AF805ADC6AA1AA19DDFDEA639CD74C846F1B5B622A6A2B3F9B | |||
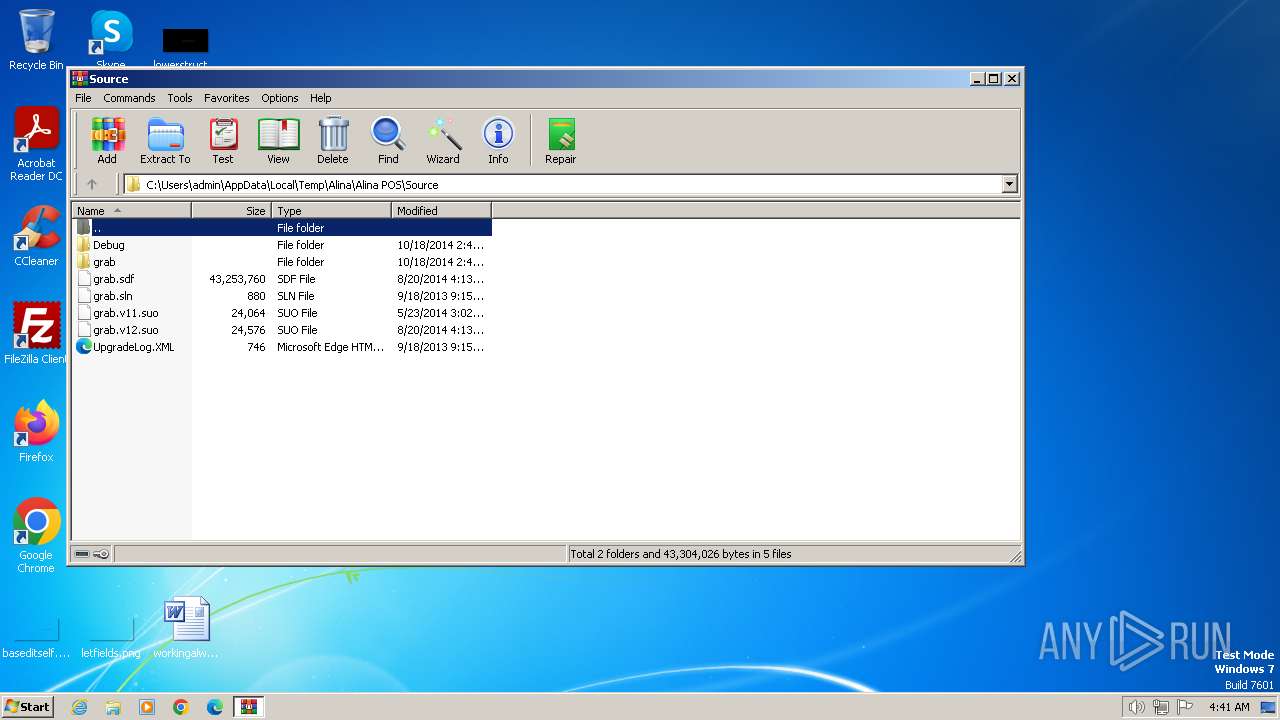
| 1936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Alina\Alina POS\Source\grab\Base.cpp | text | |
MD5:2EC86B7C18AAD18DADF40FD5EAA469A4 | SHA256:13738F8E8A02302D827FCC02E9E494998E30F7D3A7988D69D2D71C760C53801A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
adobeflasherup1.com |
| unknown |
javaoracle2.ru |
| unknown |