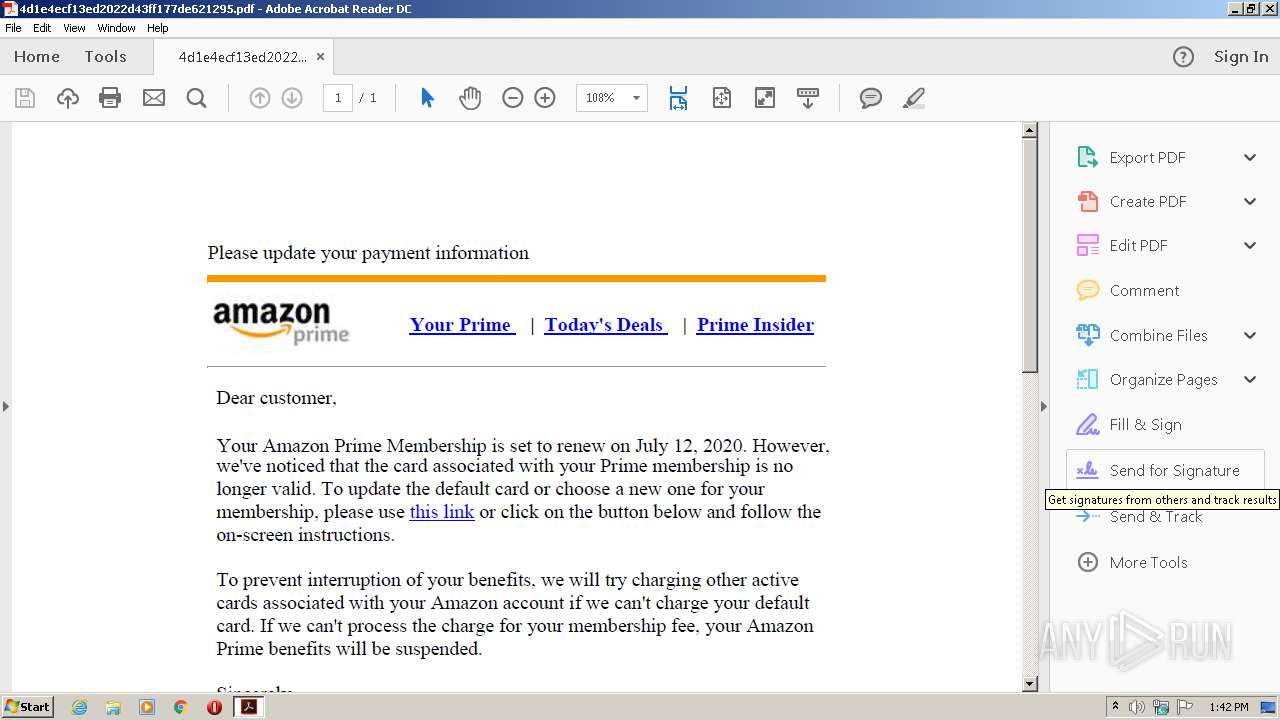
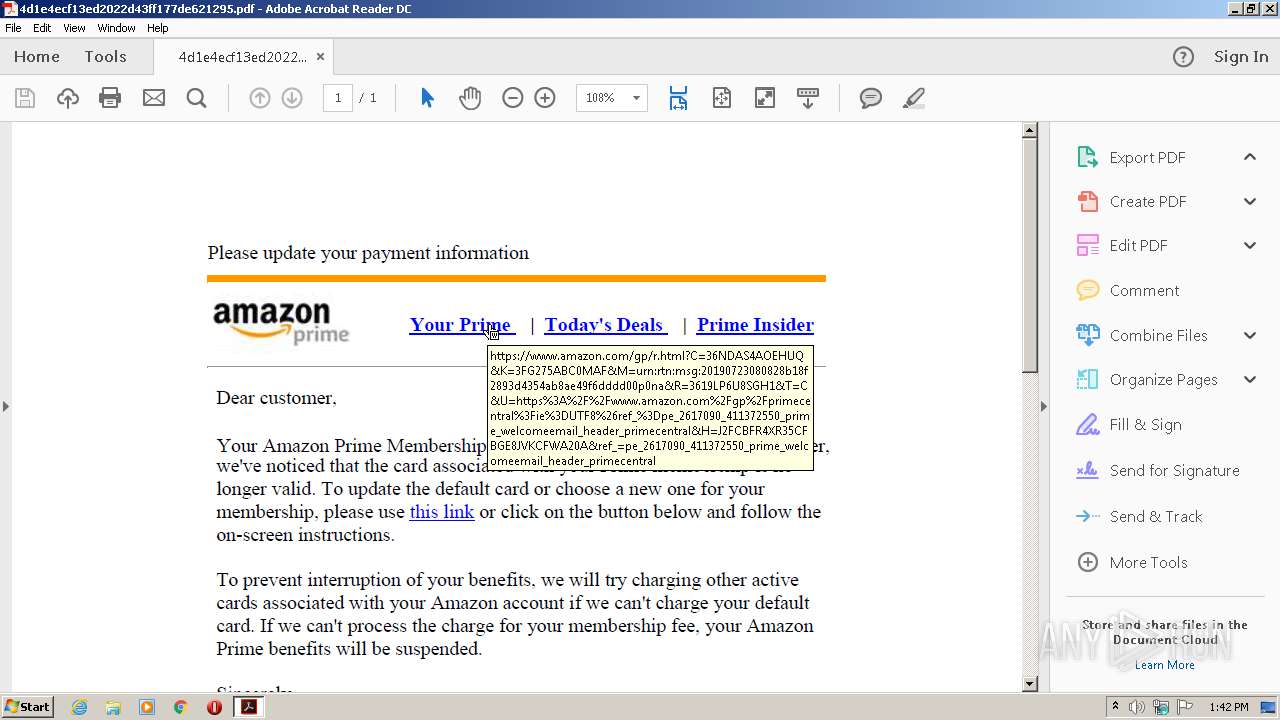
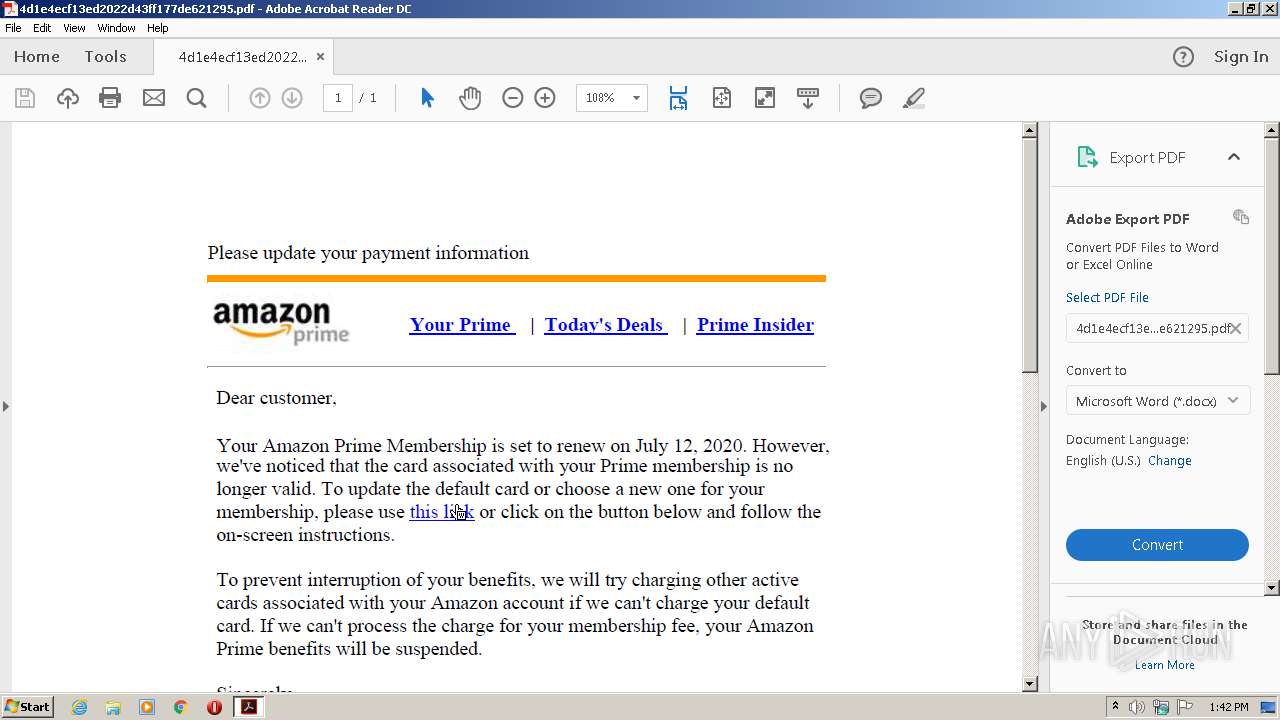
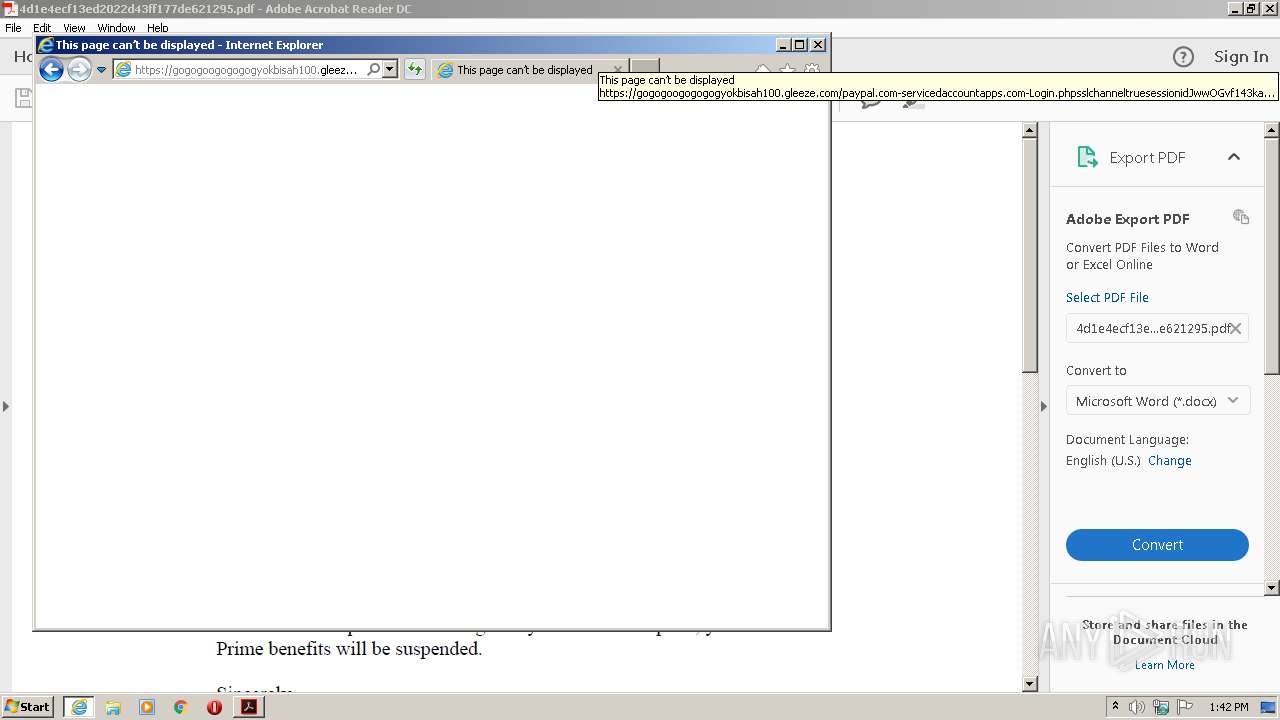
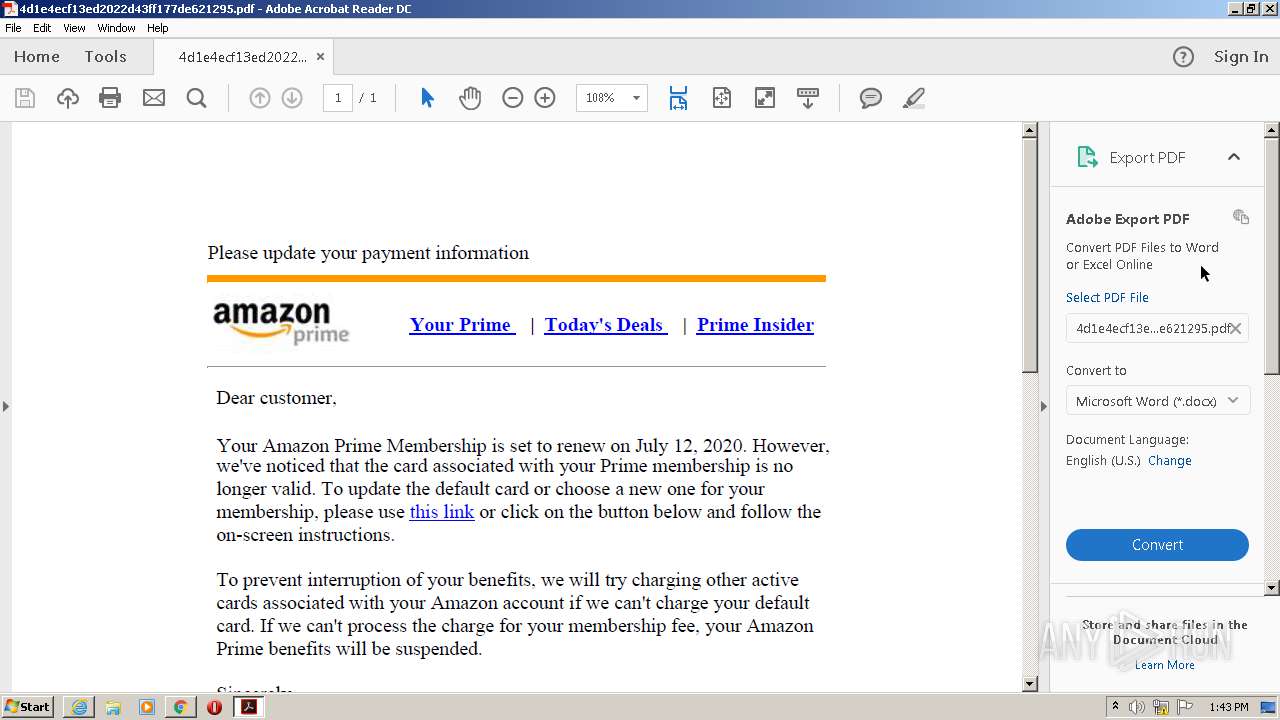
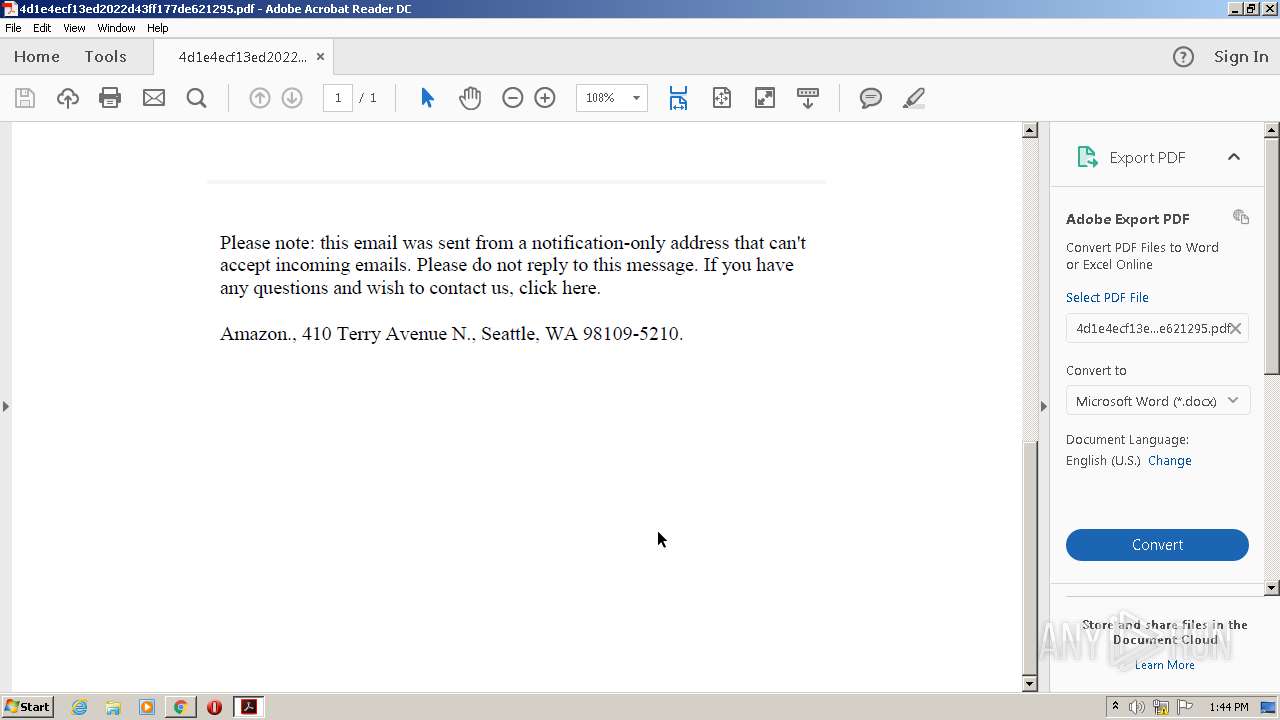
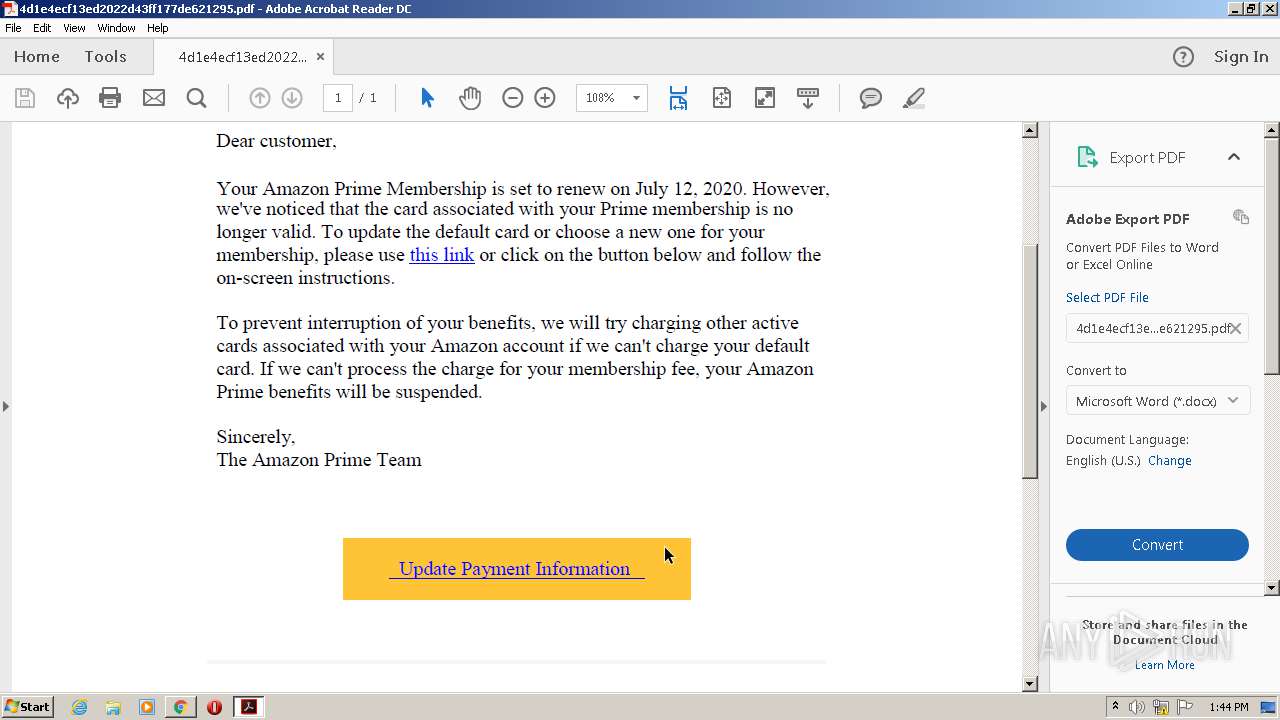
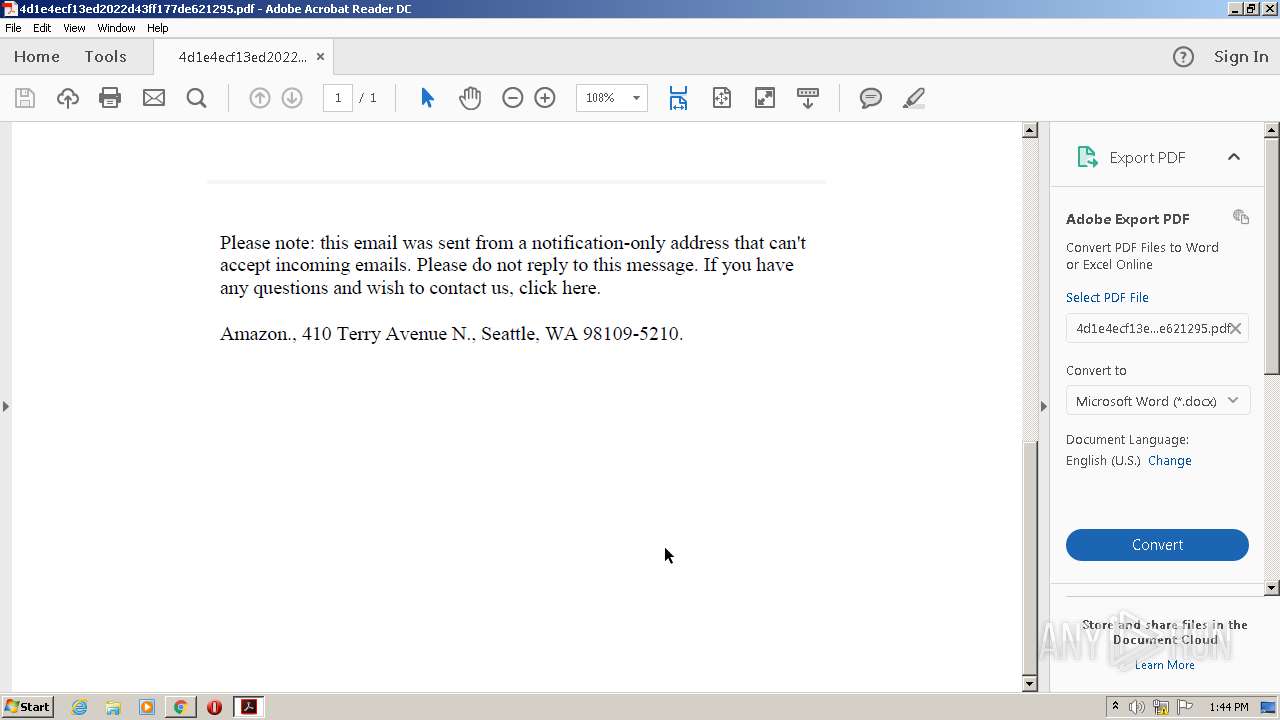
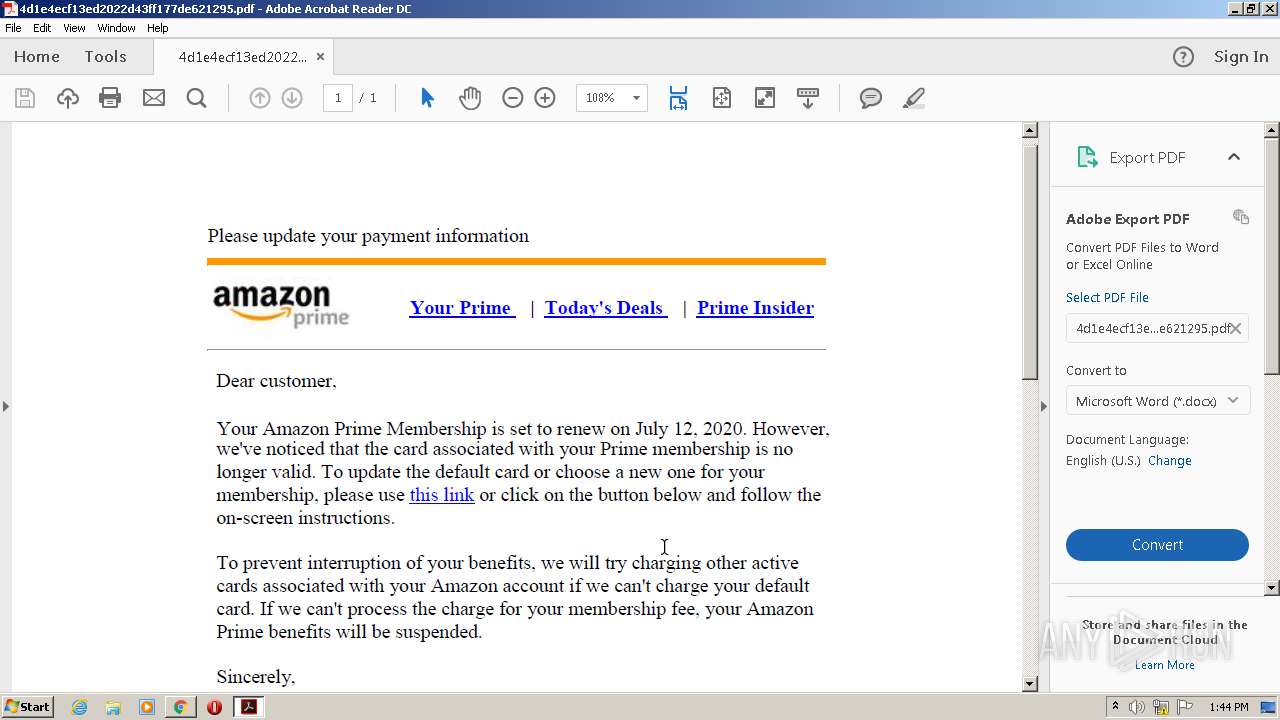
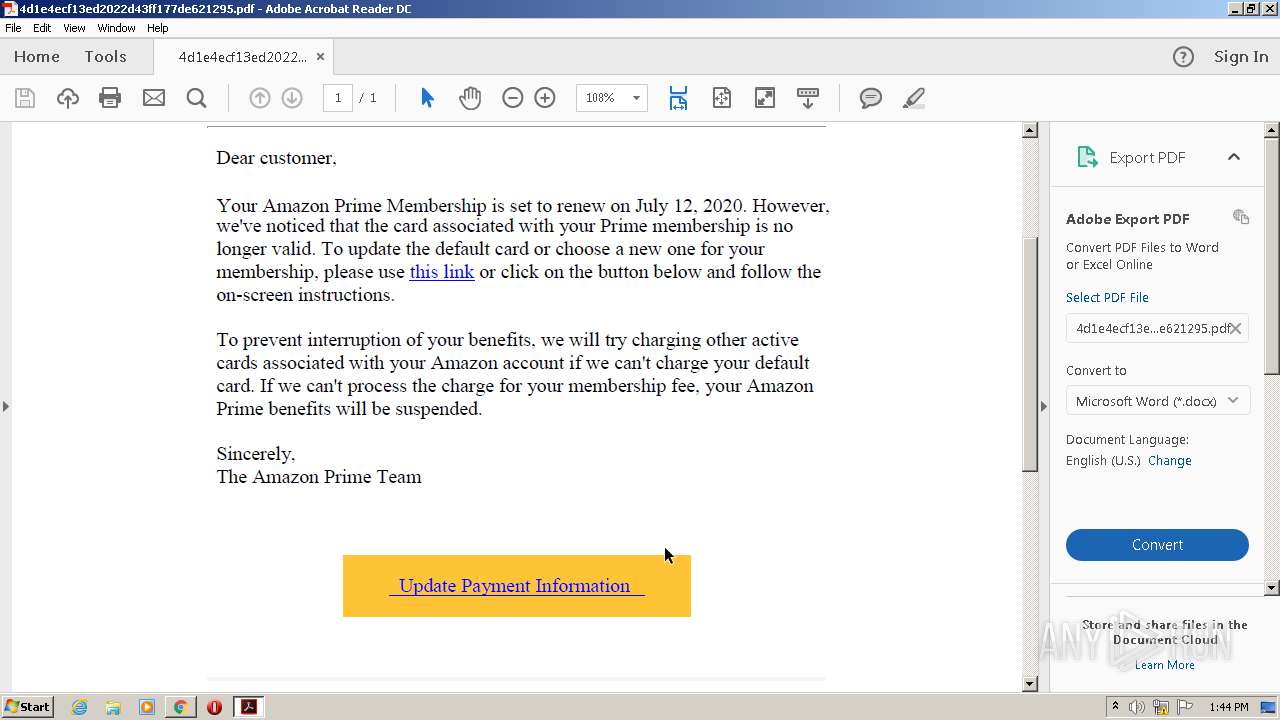
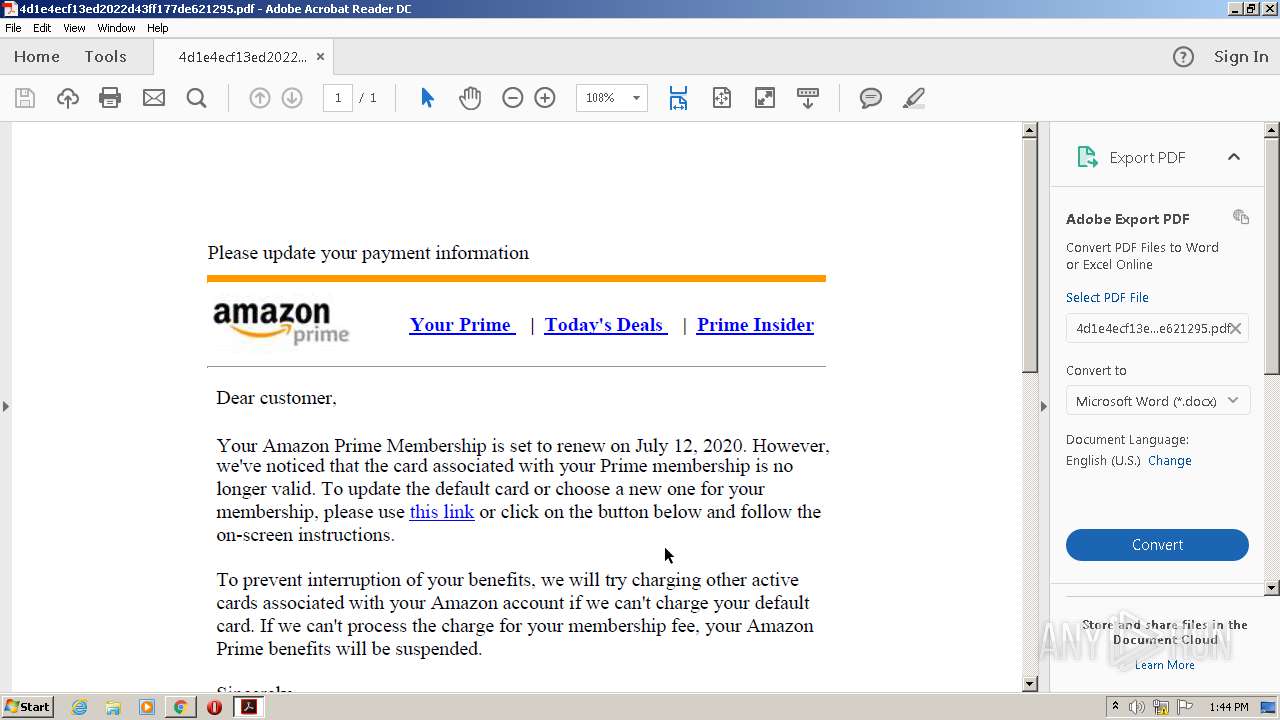
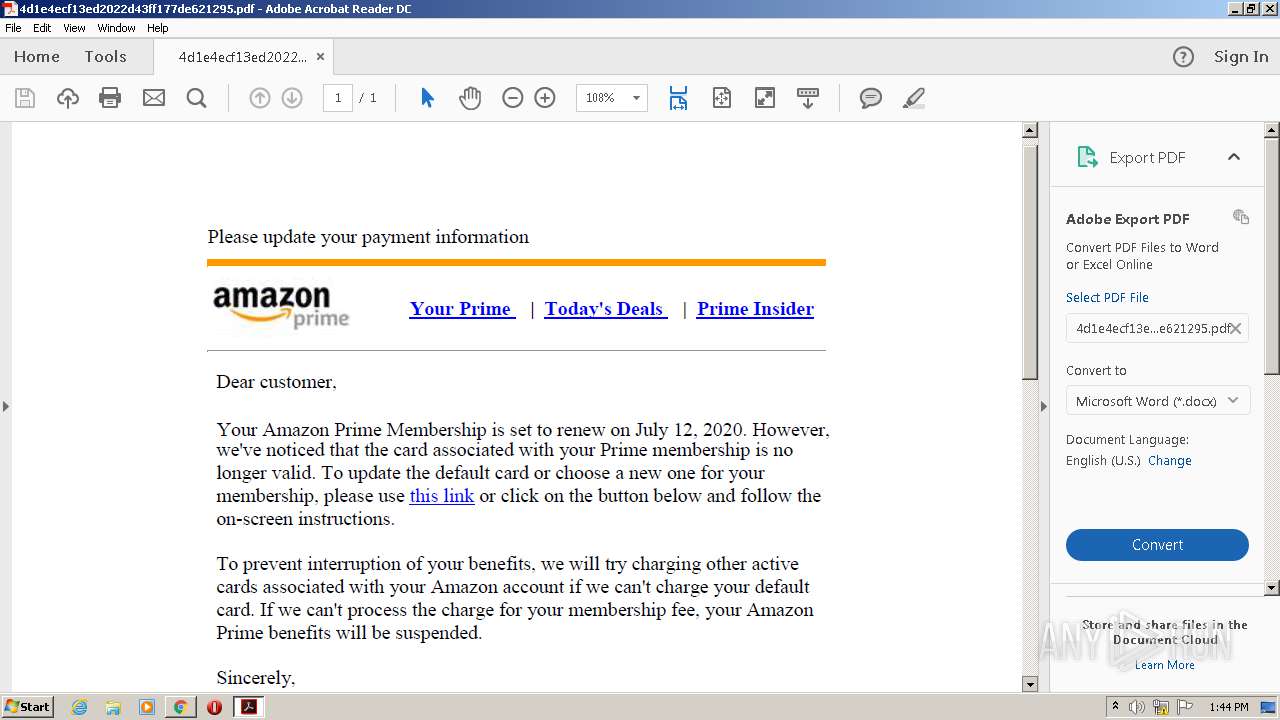
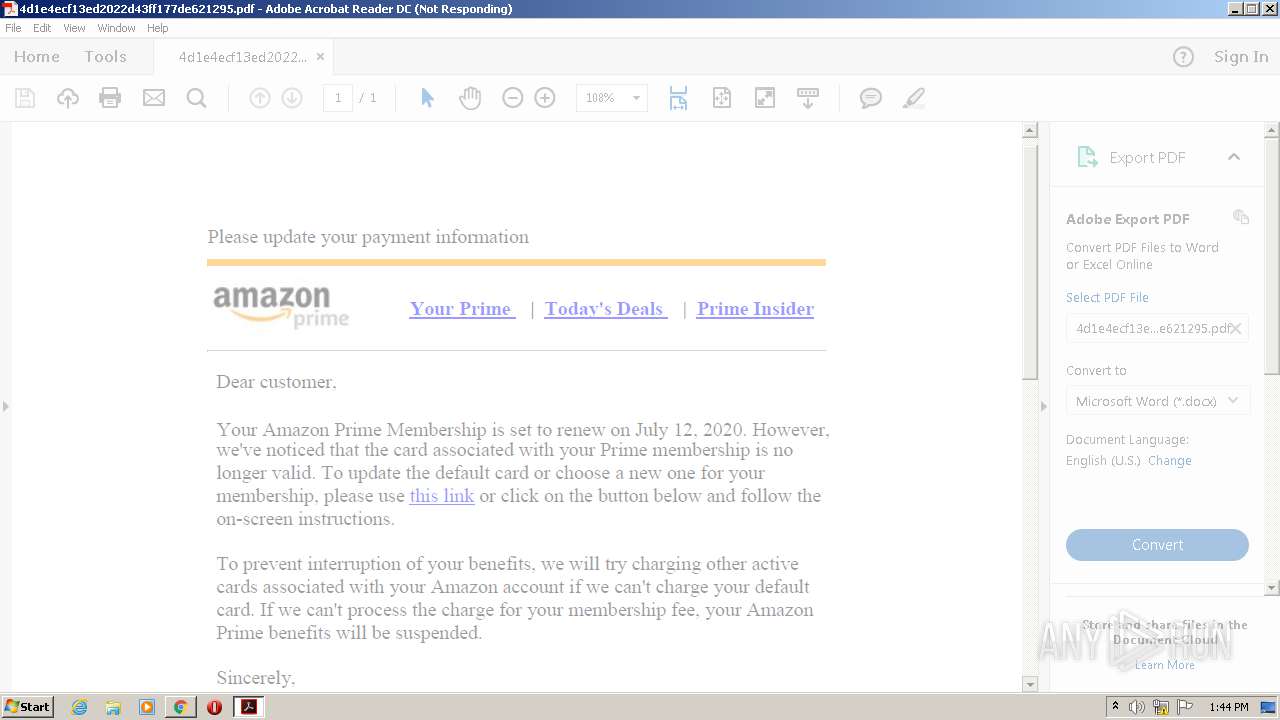
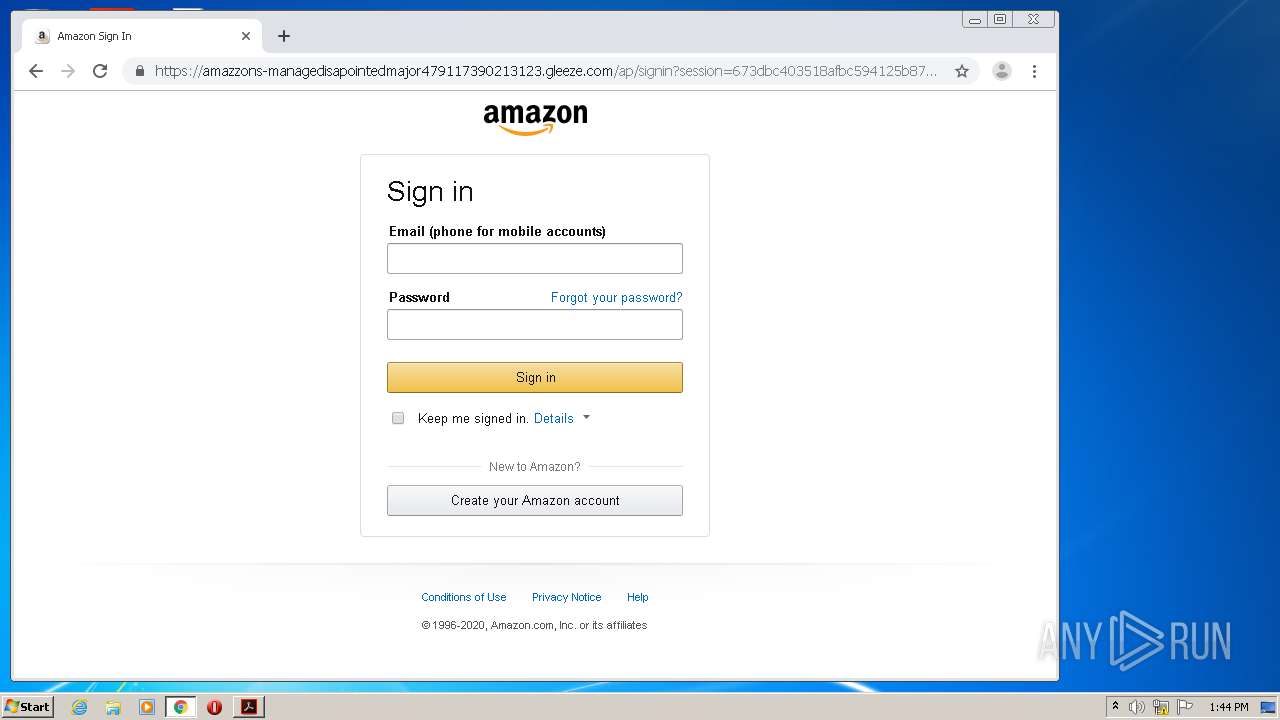
| File name: | 4d1e4ecf13ed2022d43ff177de621295.pdf |
| Full analysis: | https://app.any.run/tasks/e1c506c1-ec4a-44bd-8198-aab5611c833a |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 12:42:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | 4D1E4ECF13ED2022D43FF177DE621295 |
| SHA1: | 33C4AEFE937B07EE4A09375236F612492EC66FA3 |
| SHA256: | BC96C385D77BE91BD7AFD0A237AB0159EEE81A2C8F39704DB41B6DADFEAE10F7 |
| SSDEEP: | 3072:HEPt/KcCzjYpV5ICPFIi1sUNfHJwcWQeuUtI+v52dVE5LXQtBqSmqWY96Pi3d:khuj05ICtIDUV+QZUd52mXQDRd6g |
MALICIOUS
No malicious indicators.SUSPICIOUS
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 572)
Starts Internet Explorer
- AcroRd32.exe (PID: 572)
Creates files in the program directory
- AdobeARM.exe (PID: 3188)
Reads internet explorer settings
- AcroRd32.exe (PID: 572)
Modifies files in Chrome extension folder
- chrome.exe (PID: 4068)
INFO
Reads the hosts file
- RdrCEF.exe (PID: 1672)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 3116)
Application launched itself
- RdrCEF.exe (PID: 1672)
- iexplore.exe (PID: 1668)
- chrome.exe (PID: 4068)
Reads Internet Cache Settings
- iexplore.exe (PID: 1708)
- AcroRd32.exe (PID: 1556)
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 1668)
- AcroRd32.exe (PID: 572)
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 1736)
Reads internet explorer settings
- iexplore.exe (PID: 3896)
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 1736)
Changes internet zones settings
- iexplore.exe (PID: 1708)
- iexplore.exe (PID: 1668)
Manual execution by user
- chrome.exe (PID: 4068)
Reads settings of System Certificates
- AcroRd32.exe (PID: 572)
- iexplore.exe (PID: 1668)
- RdrCEF.exe (PID: 1672)
- iexplore.exe (PID: 3896)
- chrome.exe (PID: 3116)
- iexplore.exe (PID: 1708)
Creates files in the user directory
- iexplore.exe (PID: 1736)
- AcroRd32.exe (PID: 572)
- iexplore.exe (PID: 1668)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1736)
Changes settings of System certificates
- iexplore.exe (PID: 1668)
- iexplore.exe (PID: 1708)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1668)
- iexplore.exe (PID: 1708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.5 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en-US |
| HasXFA: | No |
| Author: | HANDSOME |
| Creator: | sejda.com (4.0.14) |
| CreateDate: | 2020:06:09 12:35:07-07:00 |
| ModifyDate: | 2020:07:12 09:10:03+02:00 |
| Producer: | SAMBox 2.1.24 |
Total processes
83
Monitored processes
46
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6126768324366325768 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2504 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5632874671562800198 --mojo-platform-channel-handle=2748 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\4d1e4ecf13ed2022d43ff177de621295.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7456652752329249720 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2492 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 688 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11588170896465054830 --mojo-platform-channel-handle=3064 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=10399169127393340251 --mojo-platform-channel-handle=4048 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,15084128681627358009,5665527325751659731,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10945880467265246475 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\4d1e4ecf13ed2022d43ff177de621295.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
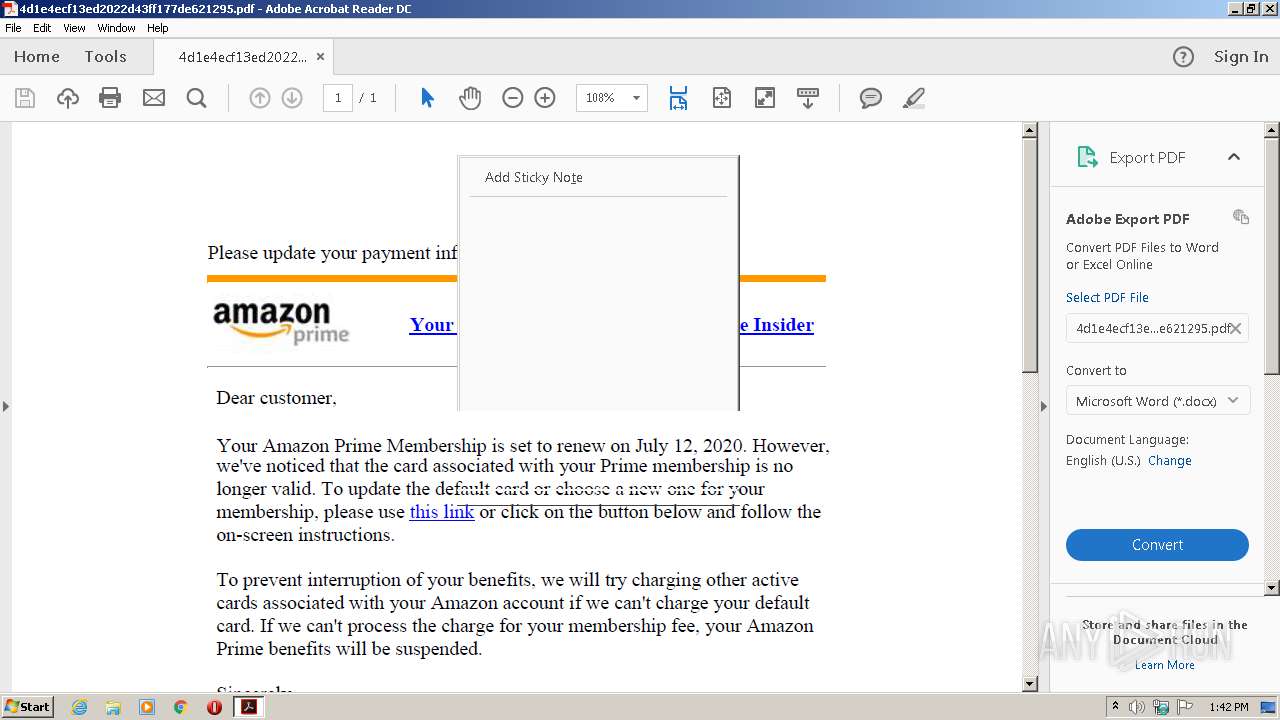
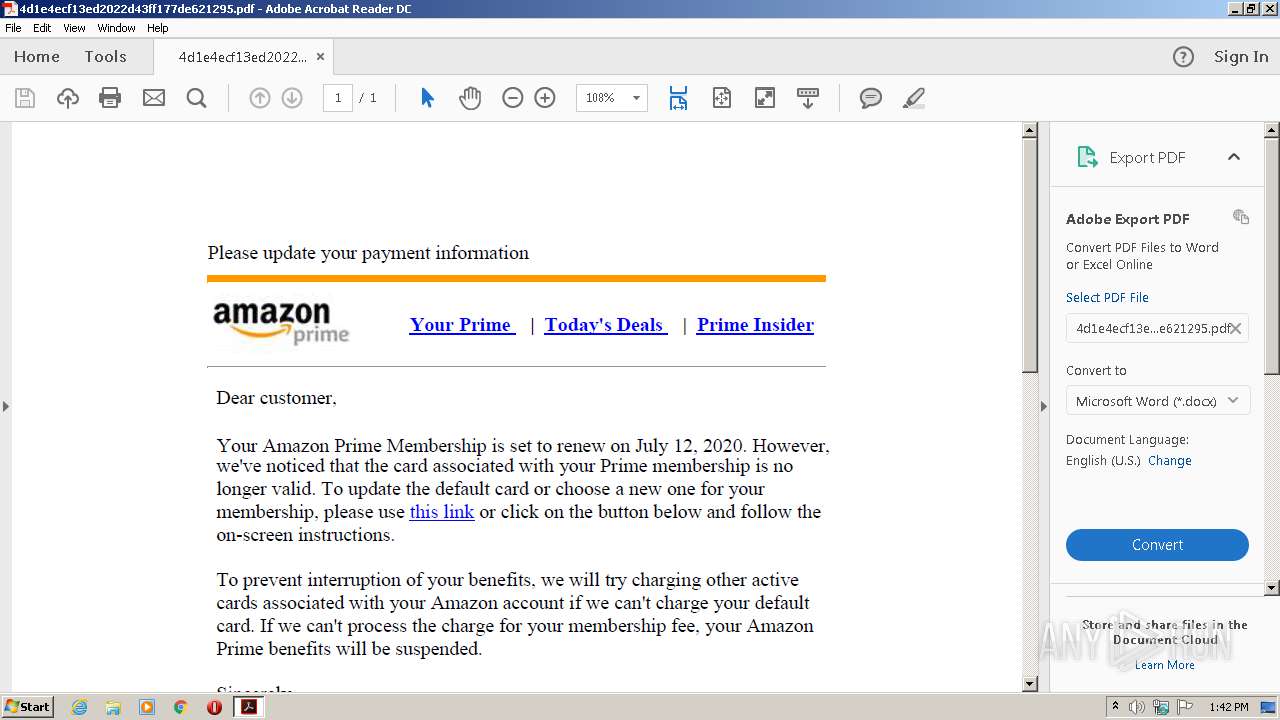
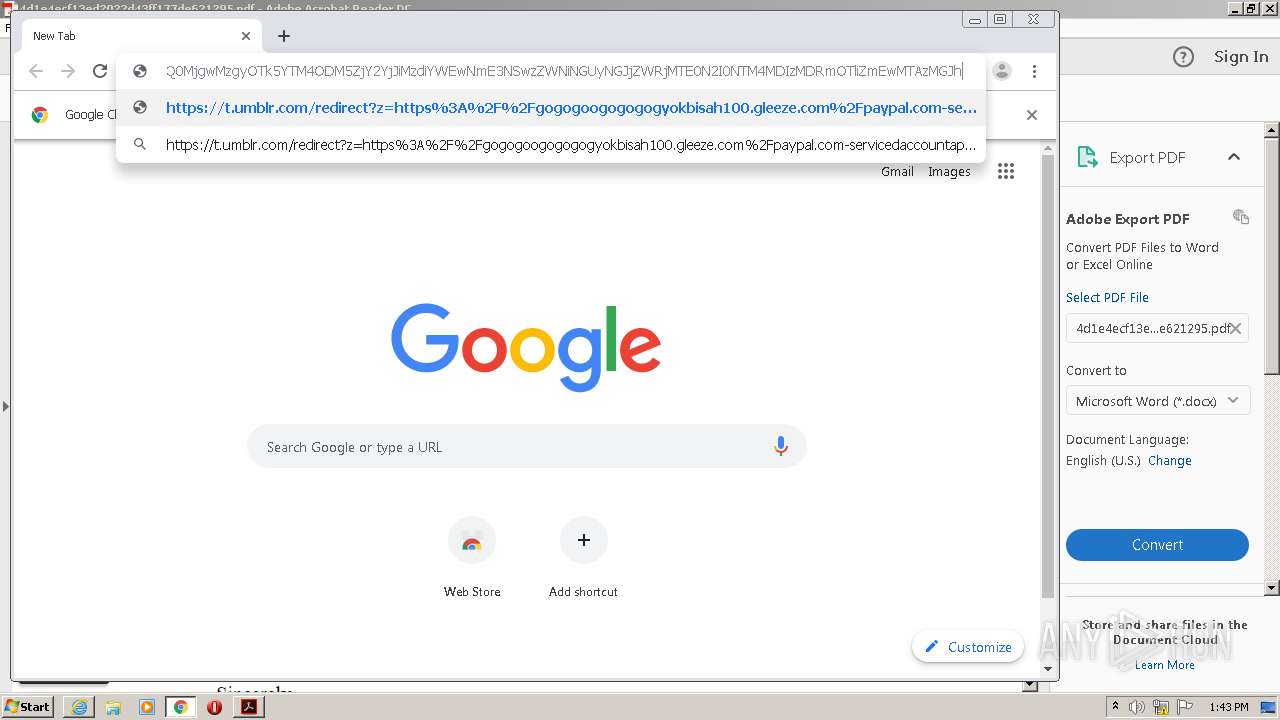
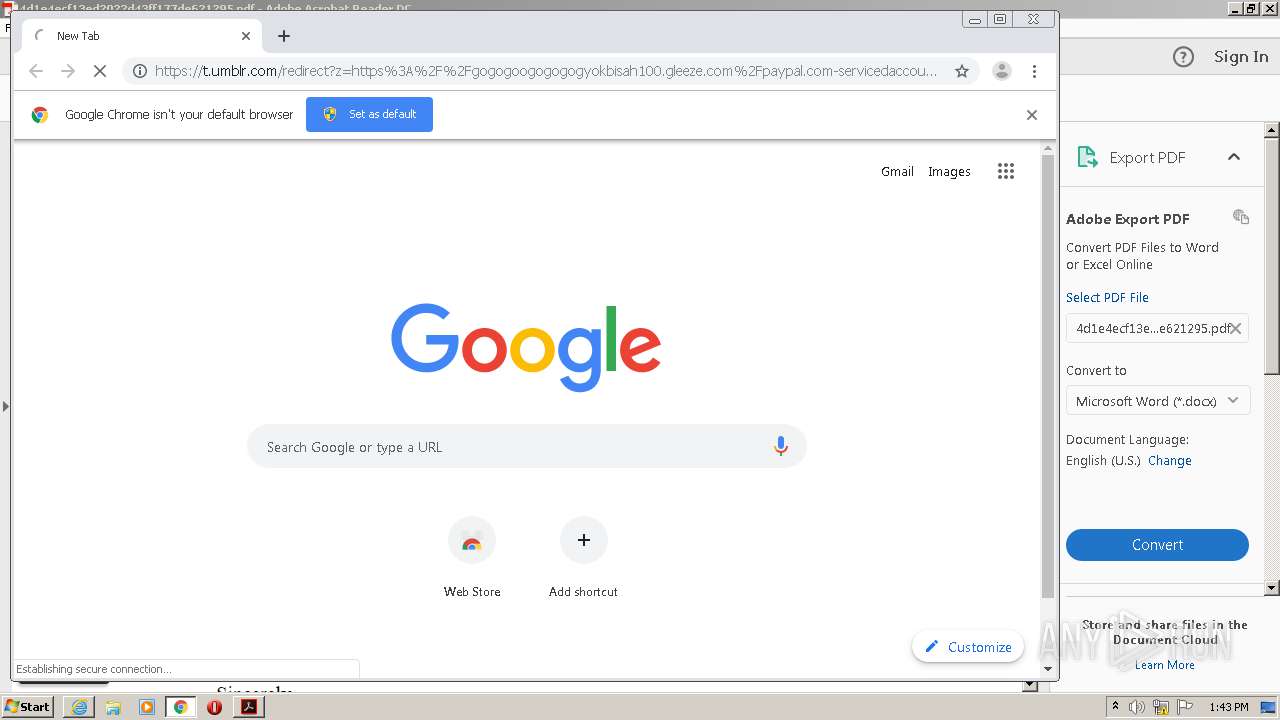
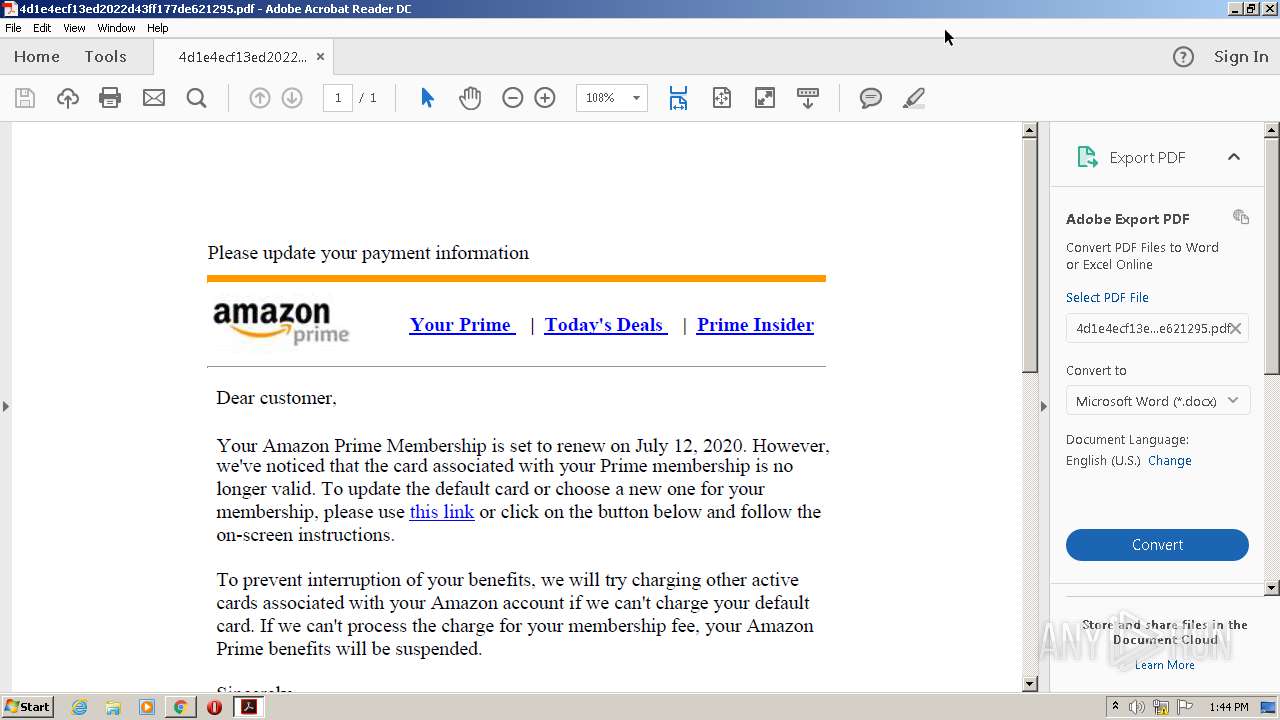
| 1668 | "C:\Program Files\Internet Explorer\iexplore.exe" https://t.umblr.com/redirect?z=https%3A%2F%2Fgogogoogogogogyokbisah100.gleeze.com%2Fpaypal.com-servicedaccountapps.com-Login.phpsslchanneltruesessionidJwwOGvf143kaxsfMdswaSYR1GVOgl6mfPSMEwiTyAxa49xm9491303JWR6iXsxMlkqRCkqdRjYWswjBA%2520%281%29.php&t=OGMyZGVhY2Q0MjgwMzgyOTk5YTM4ODM5ZjY2YjJiMzdiYWEwNmE3NSwzZWNiNGUyNGJjZWRjMTE0N2I0NTM4MDIzMDRmOTliZmEwMTAzMGJh | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
12 765
Read events
2 132
Write events
7 158
Delete events
3 475
Modification events
| (PID) Process: | (1556) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1556) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Adobe Acrobat\DC\DiskCabs |
| Operation: | write | Name: | bForms_AdhocWorkflowBackup |
Value: 0 | |||
| (PID) Process: | (1556) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (1556) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (572) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (1708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 4288449003 | |||
| (PID) Process: | (1708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30824521 | |||
| (PID) Process: | (1708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1708) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
73
Text files
341
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.1556 | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.1556 | — | |
MD5:— | SHA256:— | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF946.tmp | — | |
MD5:— | SHA256:— | |||
| 3896 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF947.tmp | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1q884x3_13xti2e_178.tmp | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R10b3fwa_13xti2d_178.tmp | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1awwhof_13xti2g_178.tmp | — | |
MD5:— | SHA256:— | |||
| 1556 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R162x29j_13xti2f_178.tmp | — | |
MD5:— | SHA256:— | |||
| 572 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\CabFEC5.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
120
DNS requests
67
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
572 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
572 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
572 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
572 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3116 | chrome.exe | GET | 200 | 173.194.163.105:80 | http://r3---sn-5go7yne6.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvY2Y1QUFXUjZlVjI5UldyLVpDTFJFcEx6QQ/7719.805.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Nf&mip=196.244.192.14&mm=28&mn=sn-5go7yne6&ms=nvh&mt=1594557740&mv=m&mvi=3&pl=24&shardbypass=yes | US | crx | 823 Kb | whitelisted |
3896 | iexplore.exe | GET | 200 | 2.16.107.114:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgN0skA4YBfRY3otxwY9hMnI4g%3D%3D | unknown | der | 527 b | whitelisted |
3116 | chrome.exe | GET | 302 | 172.217.23.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvY2Y1QUFXUjZlVjI5UldyLVpDTFJFcEx6QQ/7719.805.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
3896 | iexplore.exe | GET | 200 | 2.16.107.73:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3896 | iexplore.exe | GET | 200 | 2.16.107.114:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgN0skA4YBfRY3otxwY9hMnI4g%3D%3D | unknown | der | 527 b | whitelisted |
1708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3896 | iexplore.exe | 2.16.107.114:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | suspicious |
3896 | iexplore.exe | 2.16.107.80:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | suspicious |
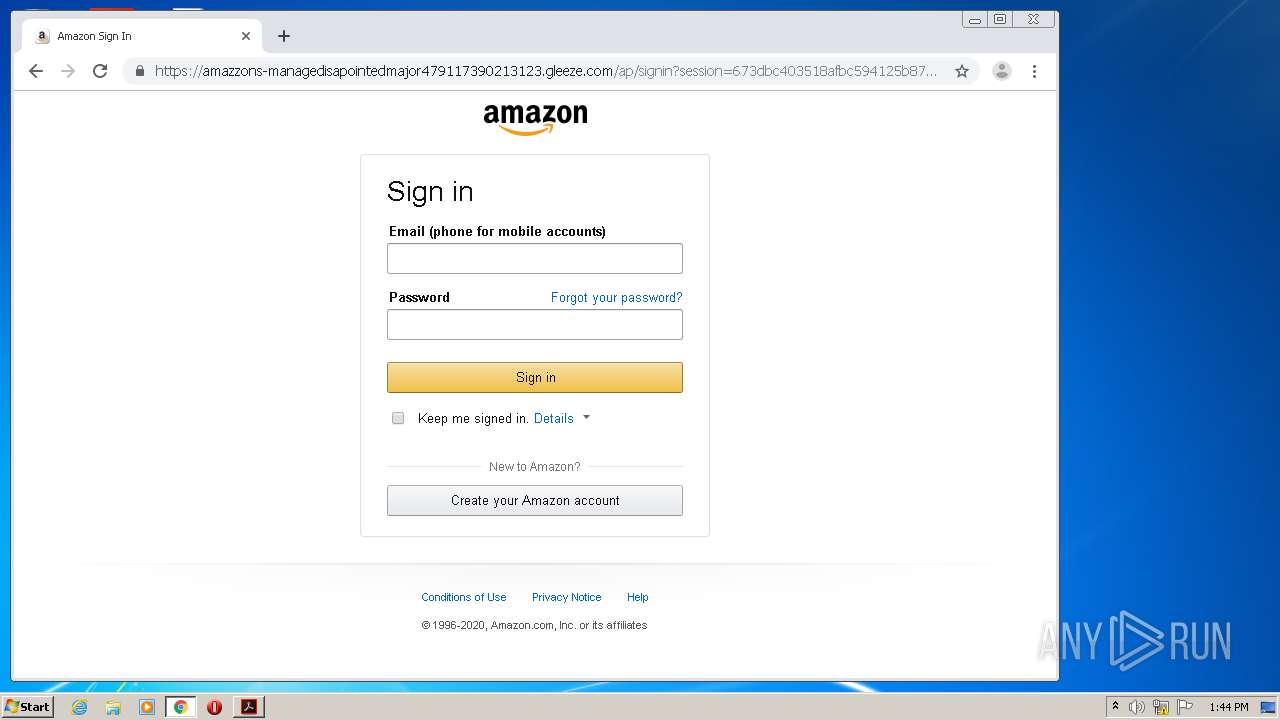
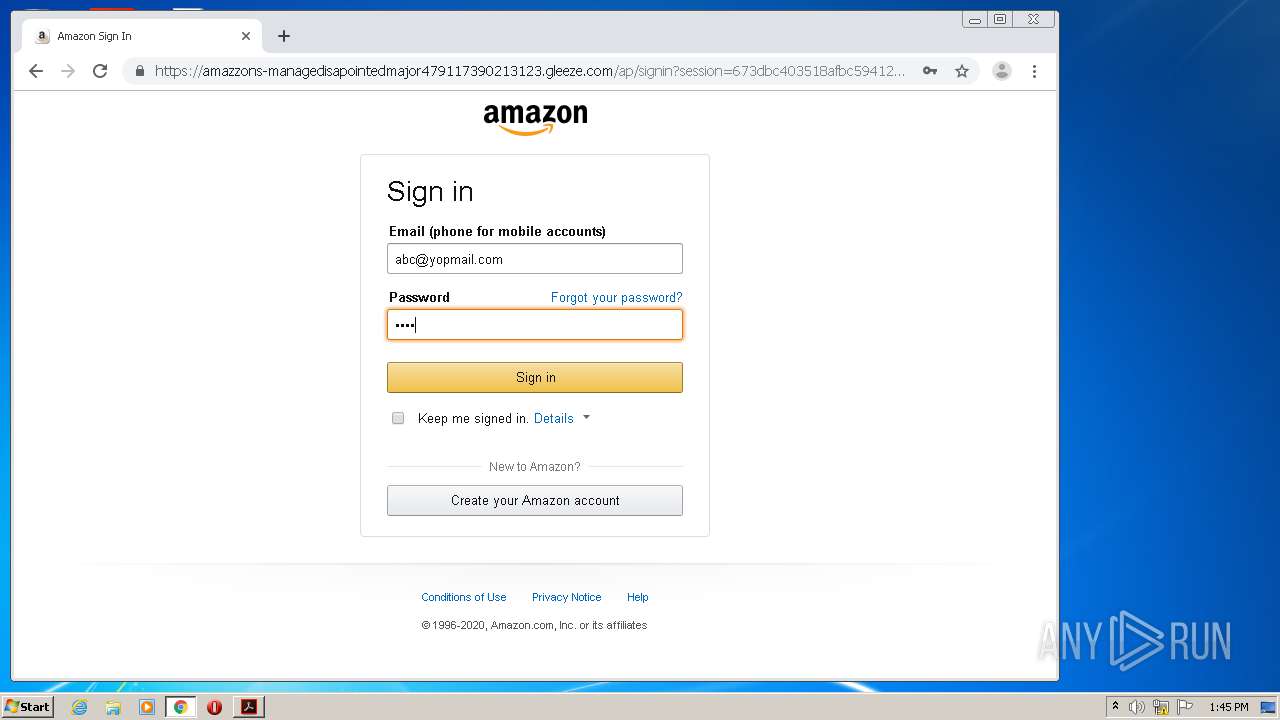
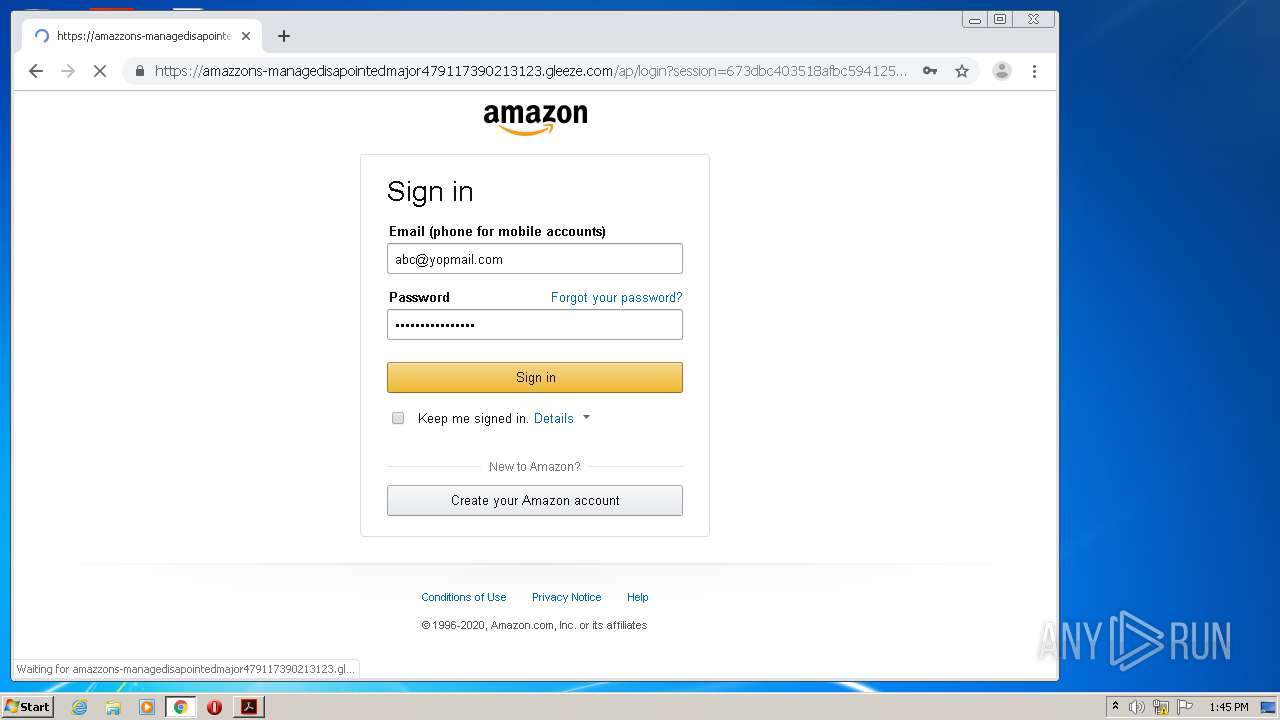
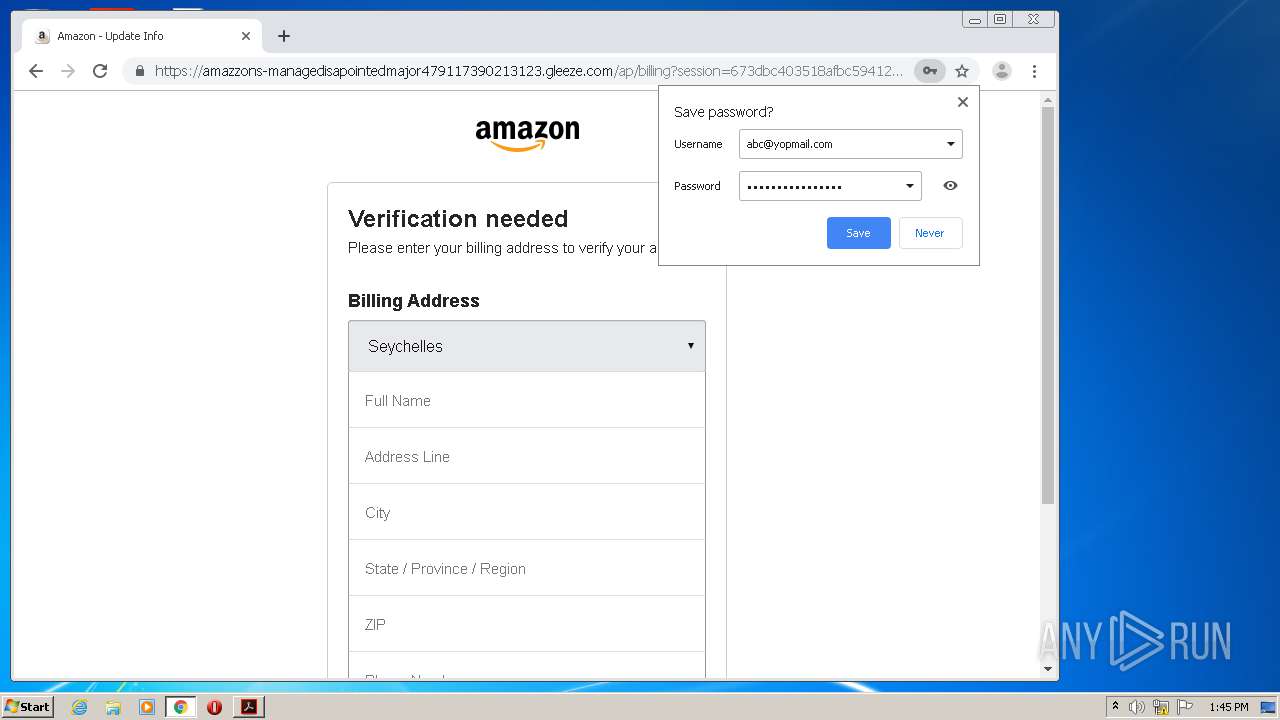
3896 | iexplore.exe | 51.140.141.249:443 | gogogoogogogogyokbisah100.gleeze.com | Microsoft Corporation | GB | suspicious |
3896 | iexplore.exe | 74.114.154.17:443 | t.umblr.com | Automattic, Inc | CA | unknown |
572 | AcroRd32.exe | 2.16.177.91:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 51.140.141.249:443 | gogogoogogogogyokbisah100.gleeze.com | Microsoft Corporation | GB | suspicious |
572 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
1708 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4032 | iexplore.exe | 51.140.141.249:443 | gogogoogogogogyokbisah100.gleeze.com | Microsoft Corporation | GB | suspicious |
3116 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t.umblr.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
gogogoogogogogyokbisah100.gleeze.com |
| suspicious |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3896 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4032 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |