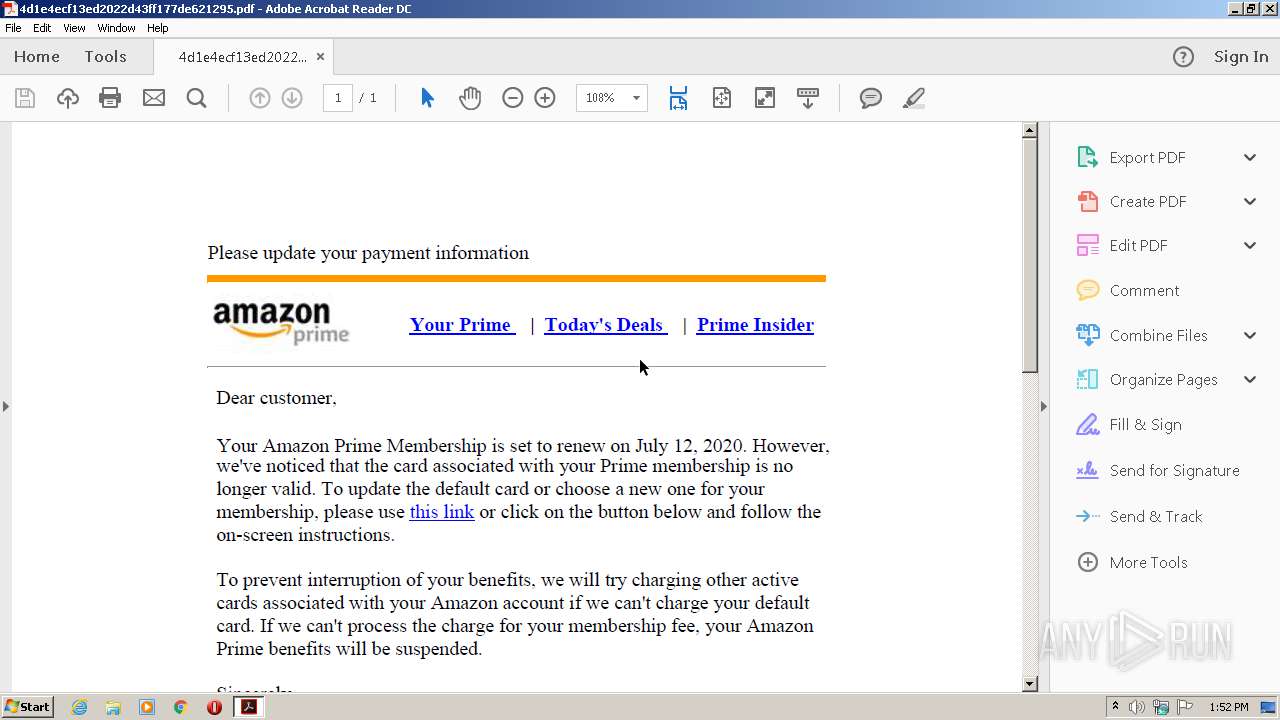
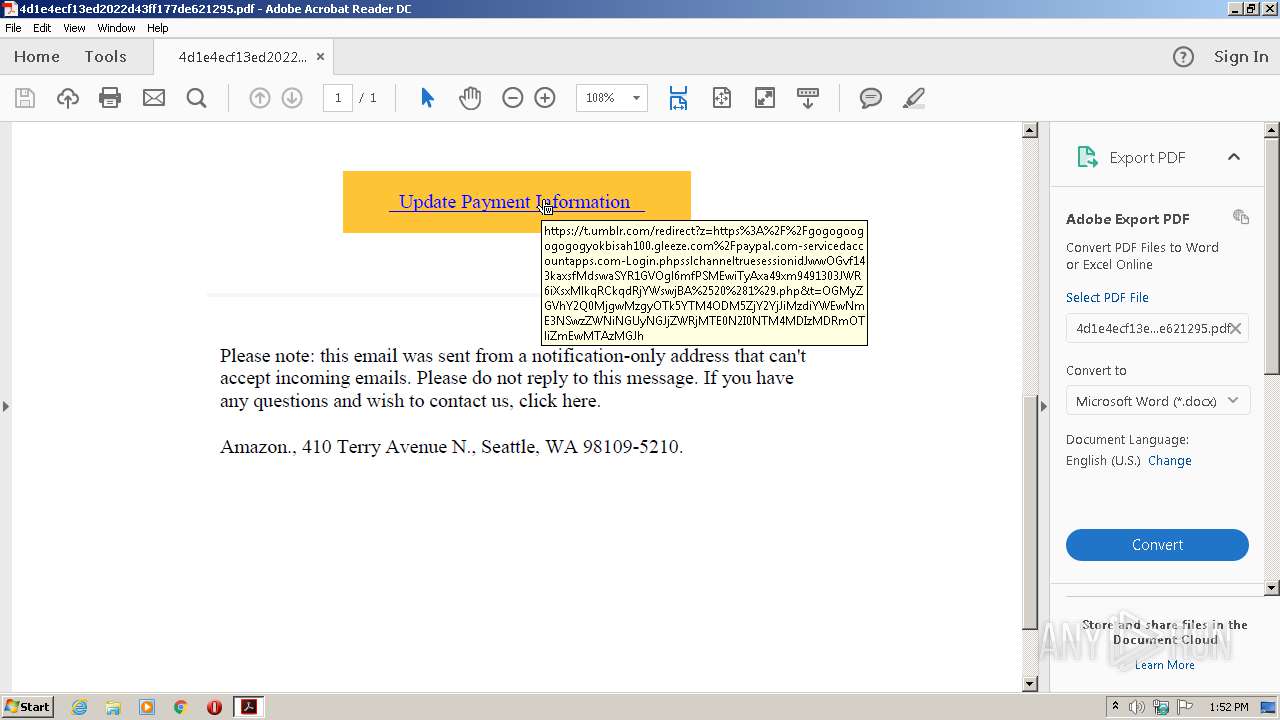
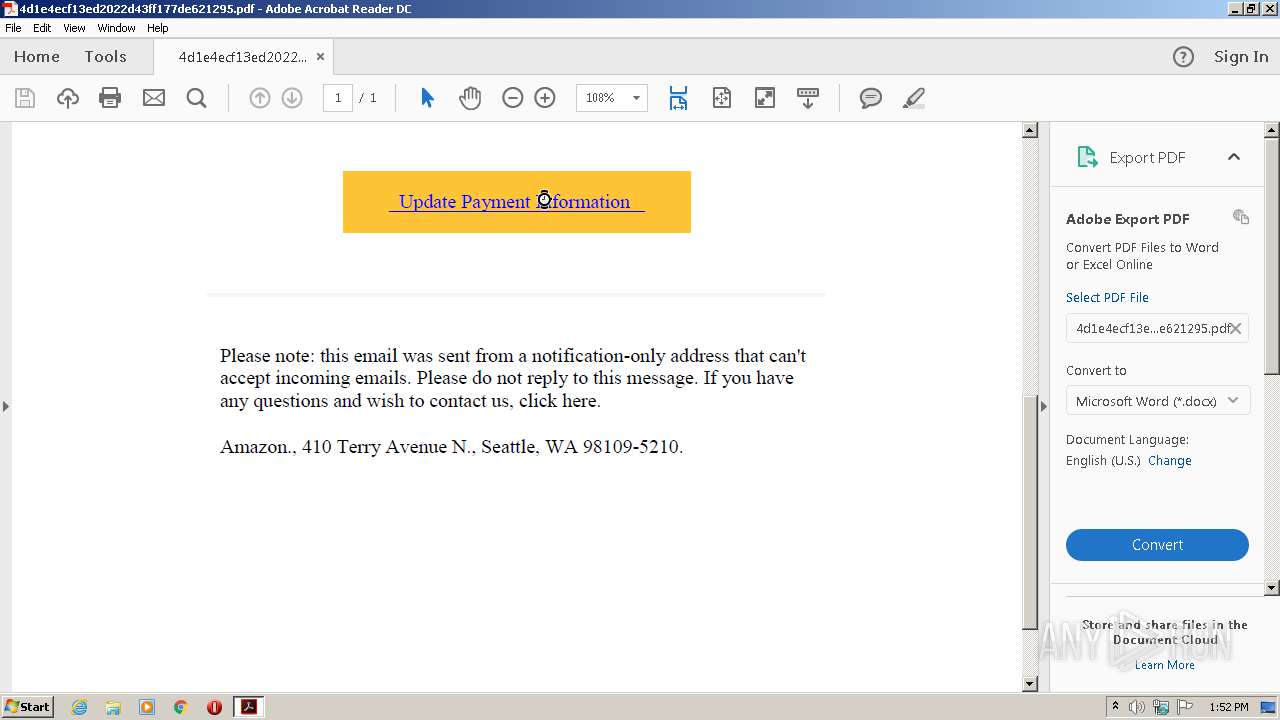
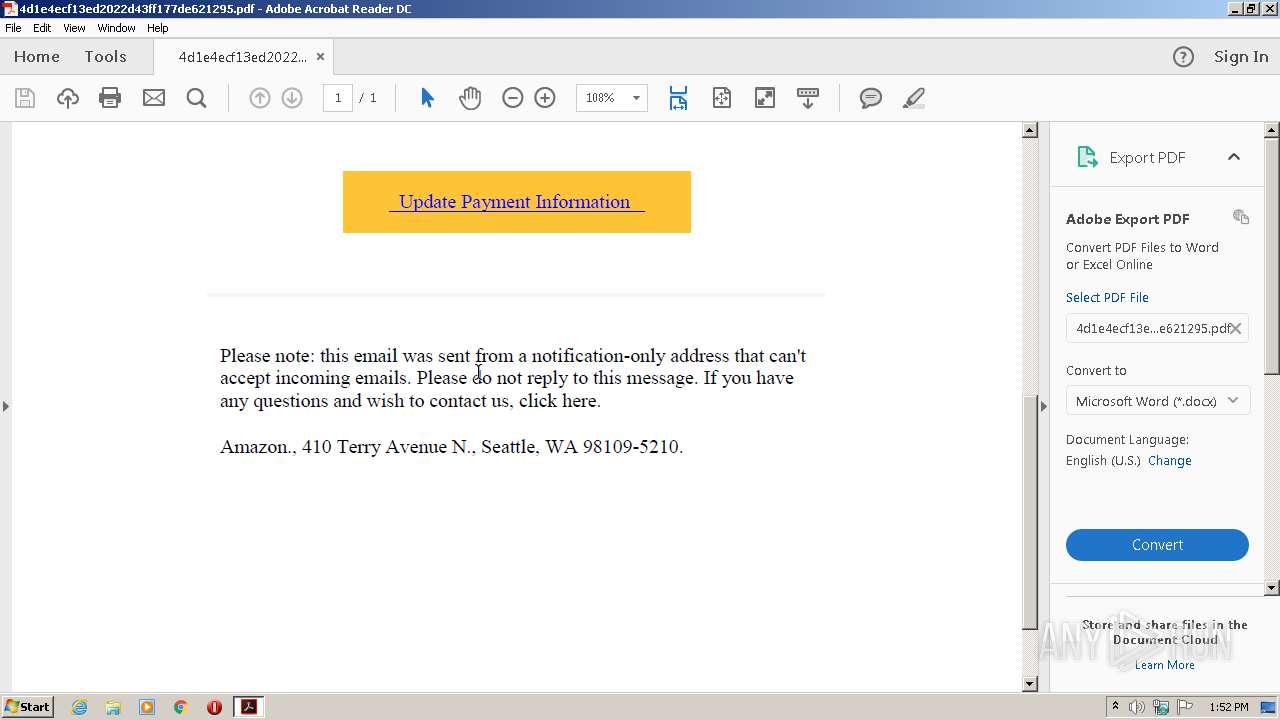
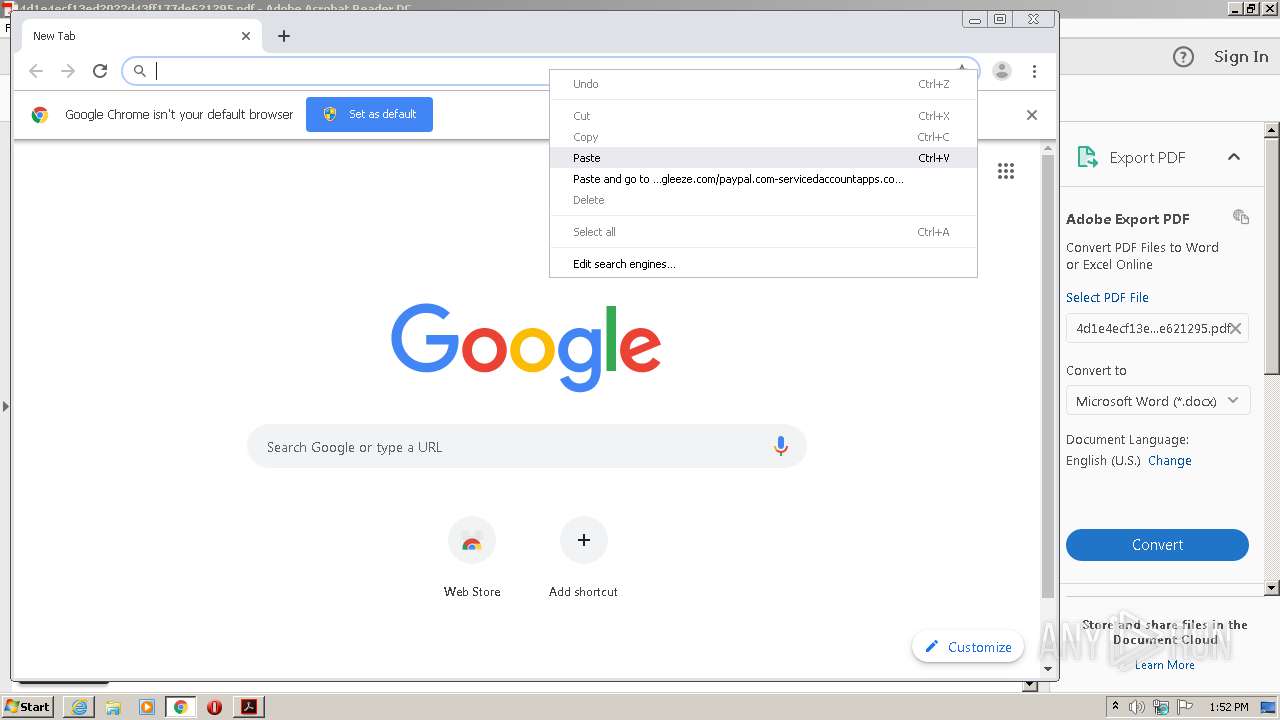
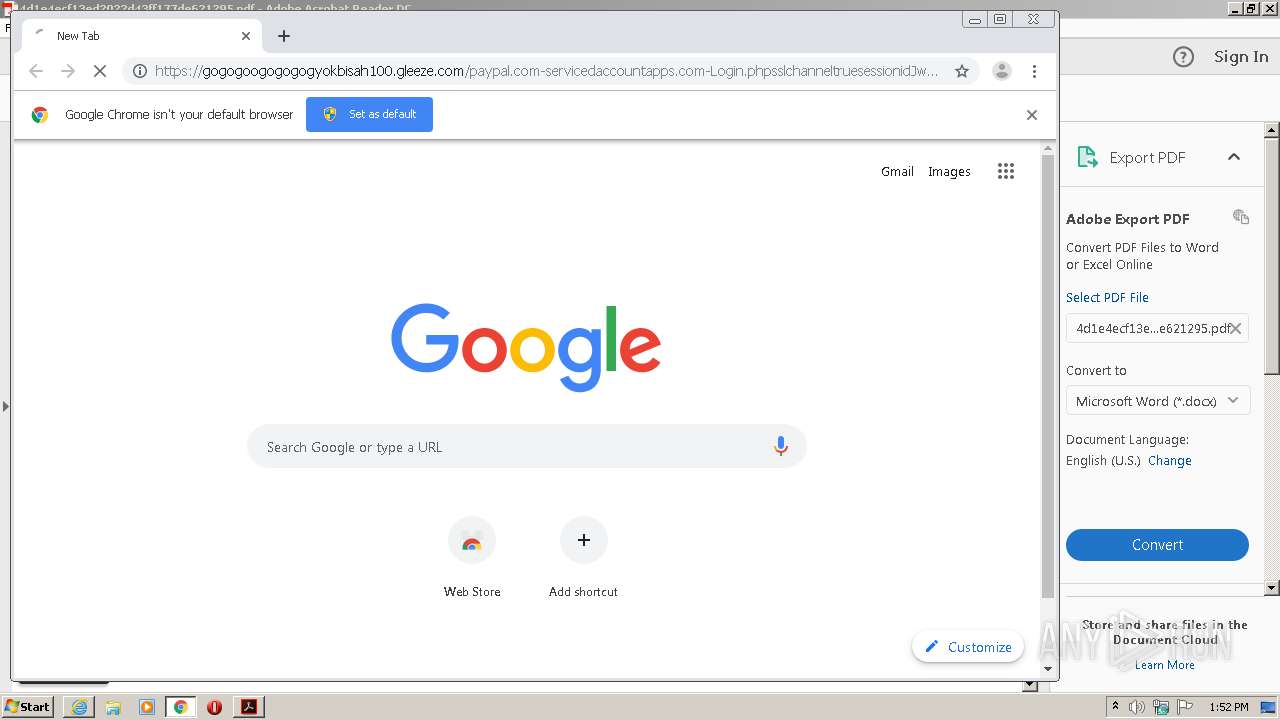
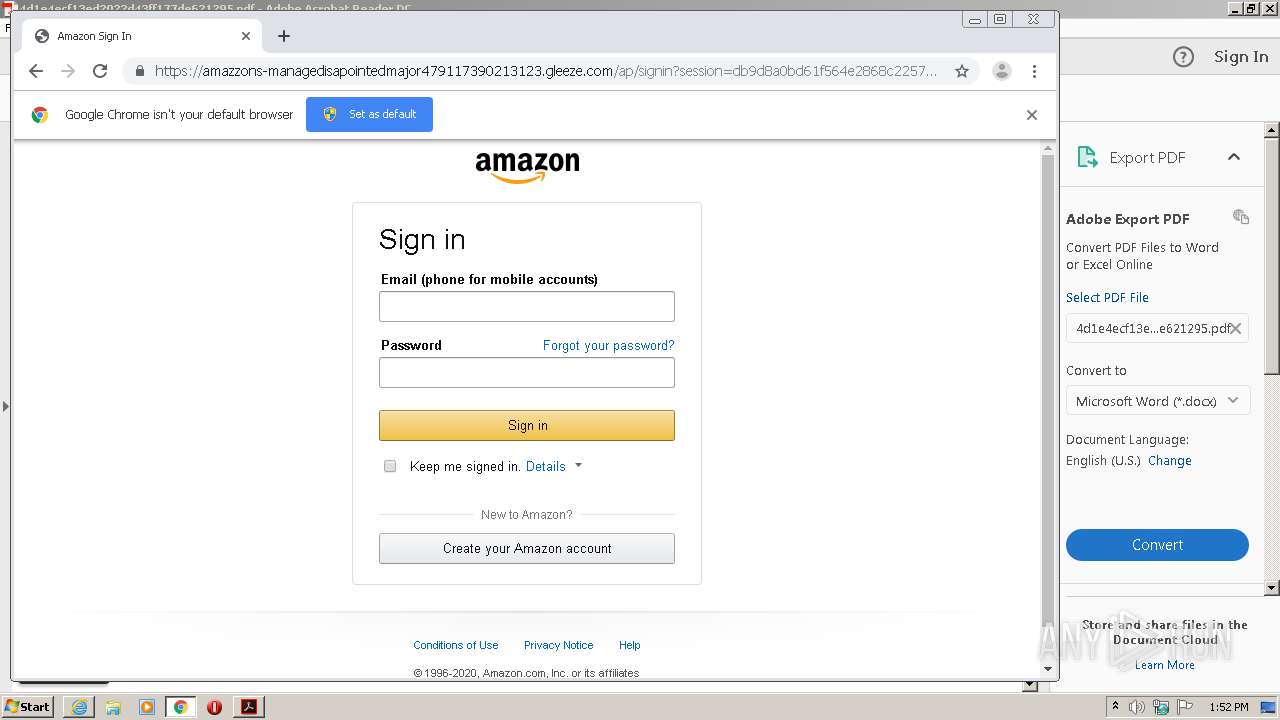
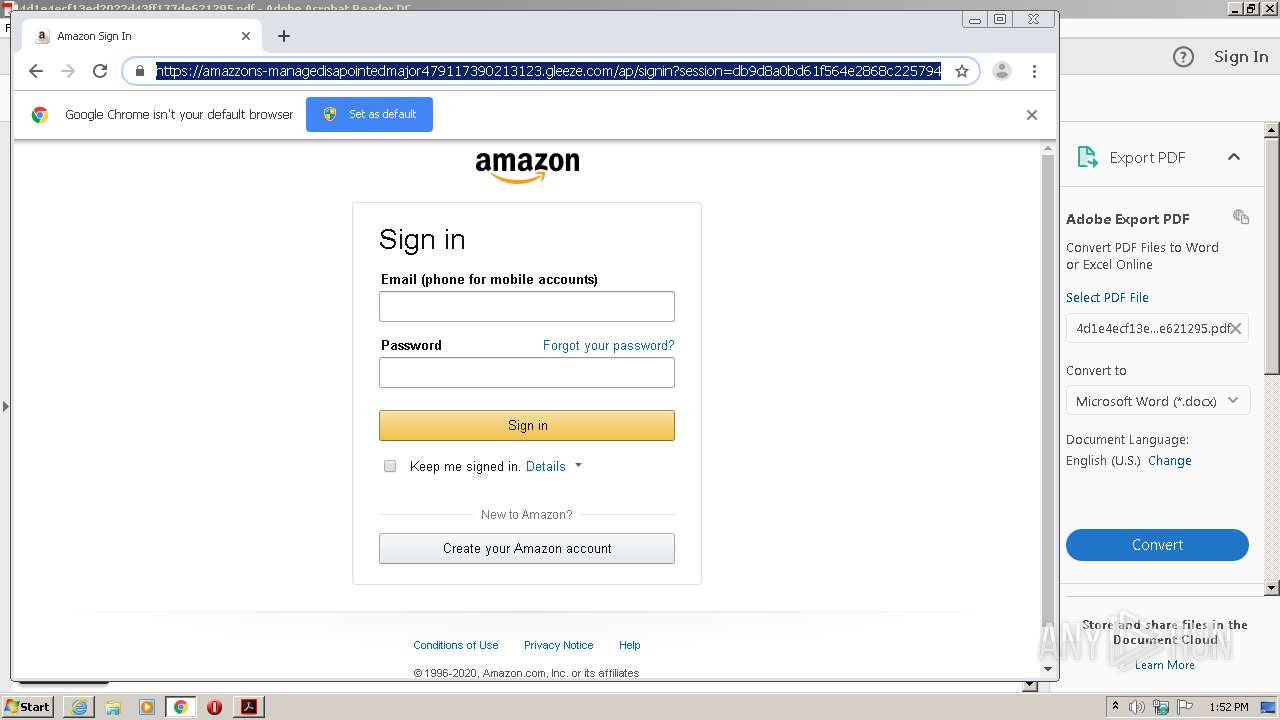
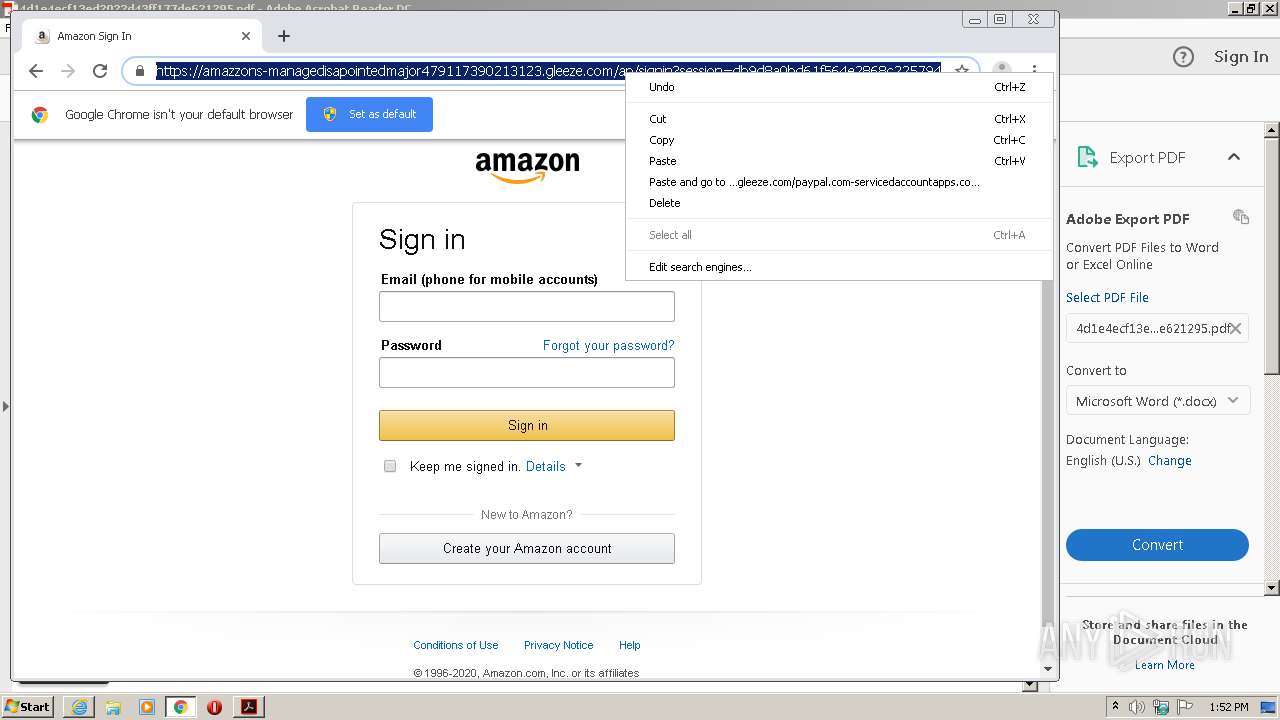
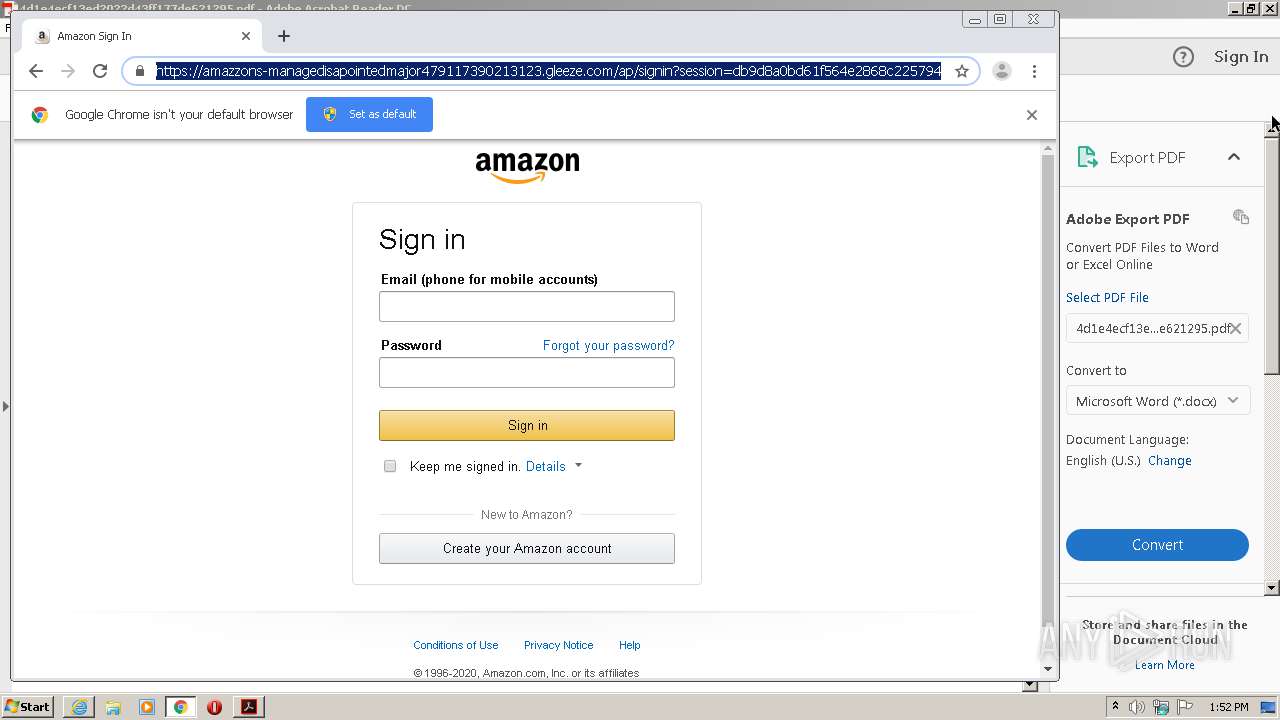
| File name: | 4d1e4ecf13ed2022d43ff177de621295.pdf |
| Full analysis: | https://app.any.run/tasks/15698a9e-5223-4813-84d6-190184242ef9 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 12:51:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | 4D1E4ECF13ED2022D43FF177DE621295 |
| SHA1: | 33C4AEFE937B07EE4A09375236F612492EC66FA3 |
| SHA256: | BC96C385D77BE91BD7AFD0A237AB0159EEE81A2C8F39704DB41B6DADFEAE10F7 |
| SSDEEP: | 3072:HEPt/KcCzjYpV5ICPFIi1sUNfHJwcWQeuUtI+v52dVE5LXQtBqSmqWY96Pi3d:khuj05ICtIDUV+QZUd52mXQDRd6g |
MALICIOUS
No malicious indicators.SUSPICIOUS
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 940)
Starts Internet Explorer
- AcroRd32.exe (PID: 940)
Creates files in the program directory
- AdobeARM.exe (PID: 2520)
INFO
Application launched itself
- AcroRd32.exe (PID: 940)
- RdrCEF.exe (PID: 1748)
- chrome.exe (PID: 3860)
Reads the hosts file
- RdrCEF.exe (PID: 1748)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3908)
Reads Internet Cache Settings
- AcroRd32.exe (PID: 3856)
- iexplore.exe (PID: 2632)
- AcroRd32.exe (PID: 940)
- iexplore.exe (PID: 2660)
- iexplore.exe (PID: 2312)
- iexplore.exe (PID: 1916)
Reads settings of System Certificates
- AcroRd32.exe (PID: 940)
- iexplore.exe (PID: 2632)
- iexplore.exe (PID: 2660)
- chrome.exe (PID: 3908)
Reads internet explorer settings
- iexplore.exe (PID: 2632)
- iexplore.exe (PID: 1916)
Changes internet zones settings
- iexplore.exe (PID: 2660)
- iexplore.exe (PID: 2312)
Creates files in the user directory
- iexplore.exe (PID: 2632)
Manual execution by user
- chrome.exe (PID: 3860)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2660)
Changes settings of System certificates
- iexplore.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.5 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en-US |
| HasXFA: | No |
| Author: | HANDSOME |
| Creator: | sejda.com (4.0.14) |
| CreateDate: | 2020:06:09 12:35:07-07:00 |
| ModifyDate: | 2020:07:12 09:10:03+02:00 |
| Producer: | SAMBox 2.1.24 |
Total processes
74
Monitored processes
38
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14309556344819730129 --mojo-platform-channel-handle=2700 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15197766034385179498 --mojo-platform-channel-handle=2772 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\4d1e4ecf13ed2022d43ff177de621295.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17673938349791910128 --mojo-platform-channel-handle=4596 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4426540977896597716 --mojo-platform-channel-handle=4332 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3509022278493289694 --mojo-platform-channel-handle=3112 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17440174105846911387 --mojo-platform-channel-handle=4188 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,2102496477798122713,3175106725288810941,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8336103395097674867 --mojo-platform-channel-handle=1044 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3888 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 310
Read events
1 651
Write events
1 169
Delete events
490
Modification events
| (PID) Process: | (3856) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3856) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Adobe Acrobat\DC\DiskCabs |
| Operation: | write | Name: | bForms_AdhocWorkflowBackup |
Value: 0 | |||
| (PID) Process: | (3856) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (3856) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (940) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
Executable files
0
Suspicious files
33
Text files
243
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.3856 | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.3856 | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1nebn6h_jlprli_2z4.tmp | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1y9a7y6_jlprlj_2z4.tmp | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Ri52jh0_jlprlk_2z4.tmp | — | |
MD5:— | SHA256:— | |||
| 3856 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rtz8v18_jlprll_2z4.tmp | — | |
MD5:— | SHA256:— | |||
| 940 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\CabBE24.tmp | — | |
MD5:— | SHA256:— | |||
| 940 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\TarBE25.tmp | — | |
MD5:— | SHA256:— | |||
| 2632 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCB44.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
51
DNS requests
37
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
940 | AcroRd32.exe | GET | 304 | 2.16.177.50:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
940 | AcroRd32.exe | GET | 304 | 2.16.177.50:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
940 | AcroRd32.exe | GET | 304 | 2.16.177.50:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
2632 | iexplore.exe | GET | 200 | 2.16.107.73:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2632 | iexplore.exe | GET | 200 | 2.16.107.80:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3908 | chrome.exe | GET | 302 | 172.217.21.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 543 b | whitelisted |
940 | AcroRd32.exe | GET | 304 | 2.16.177.50:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2632 | iexplore.exe | GET | 200 | 2.16.107.114:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgN0skA4YBfRY3otxwY9hMnI4g%3D%3D | unknown | der | 527 b | whitelisted |
3908 | chrome.exe | GET | 302 | 172.217.21.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvY2Y1QUFXUjZlVjI5UldyLVpDTFJFcEx6QQ/7719.805.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 532 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2632 | iexplore.exe | 2.16.107.114:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | suspicious |
940 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
2632 | iexplore.exe | 2.16.107.80:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | suspicious |
2632 | iexplore.exe | 2.16.107.73:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | suspicious |
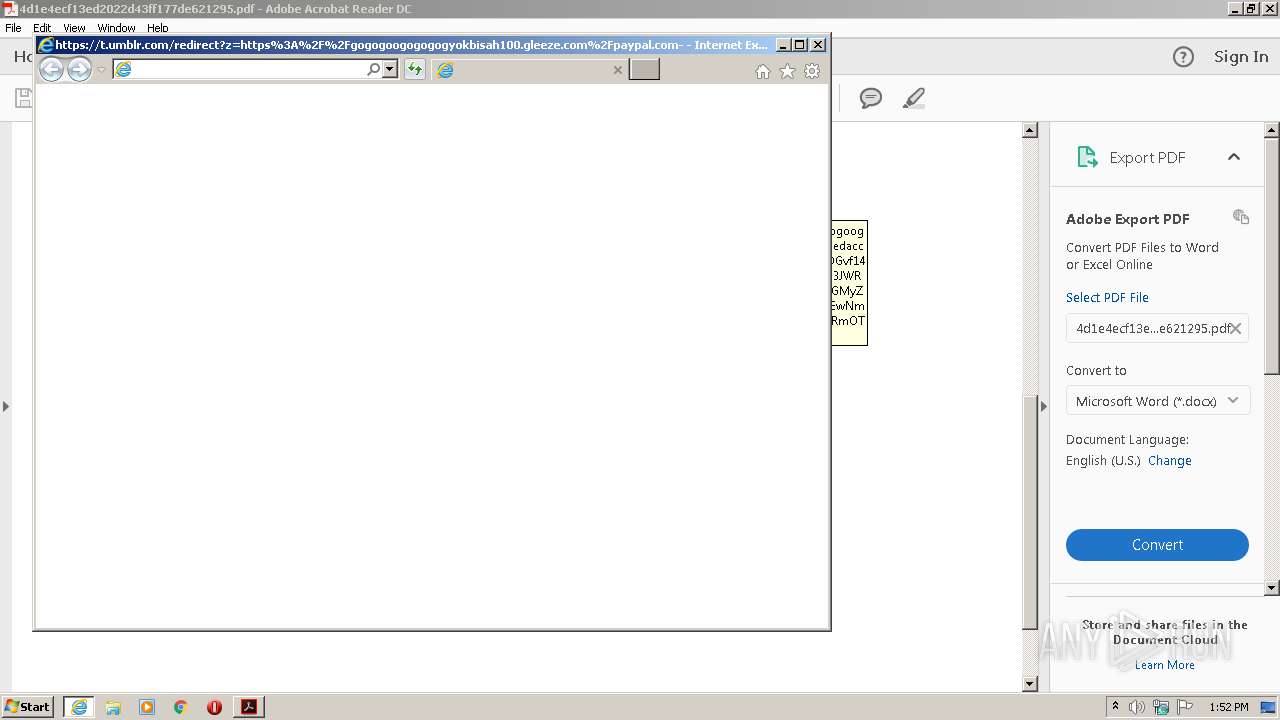
2632 | iexplore.exe | 51.140.141.249:443 | gogogoogogogogyokbisah100.gleeze.com | Microsoft Corporation | GB | suspicious |
2632 | iexplore.exe | 2.16.107.43:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | suspicious |
2632 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
3908 | chrome.exe | 172.217.23.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2660 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
t.umblr.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
gogogoogogogogyokbisah100.gleeze.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2632 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2632 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
1916 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |