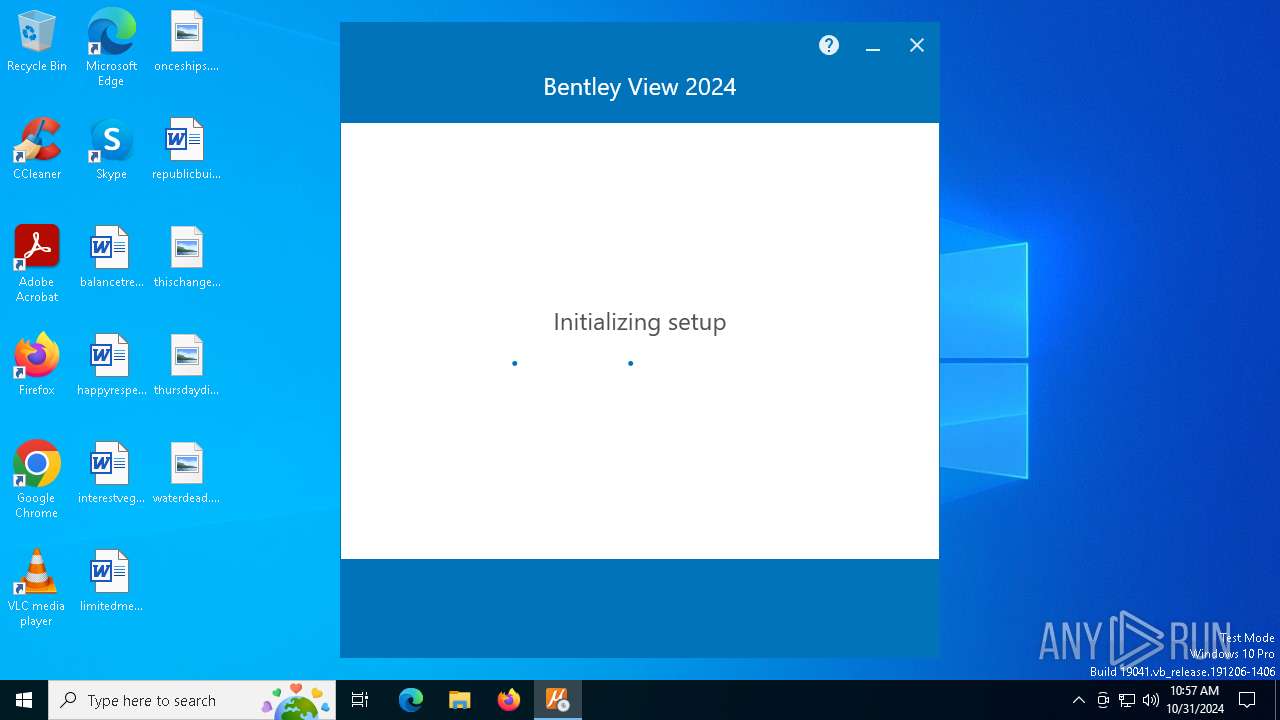
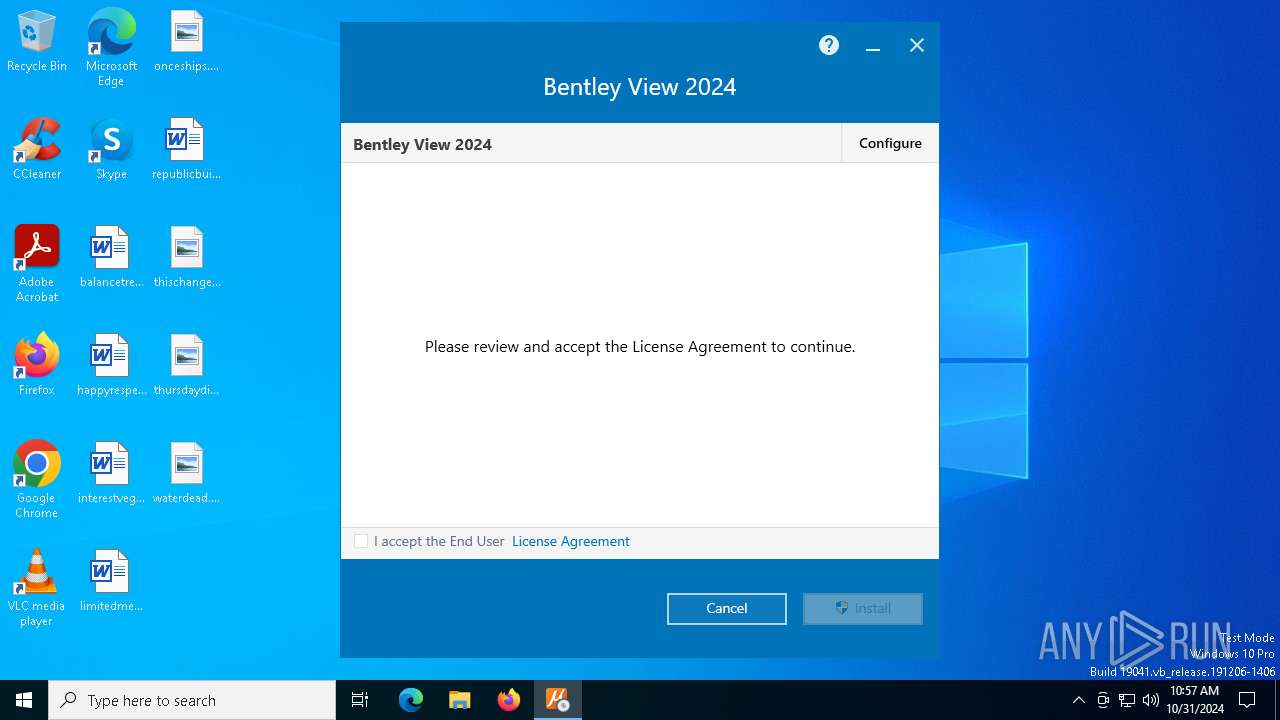
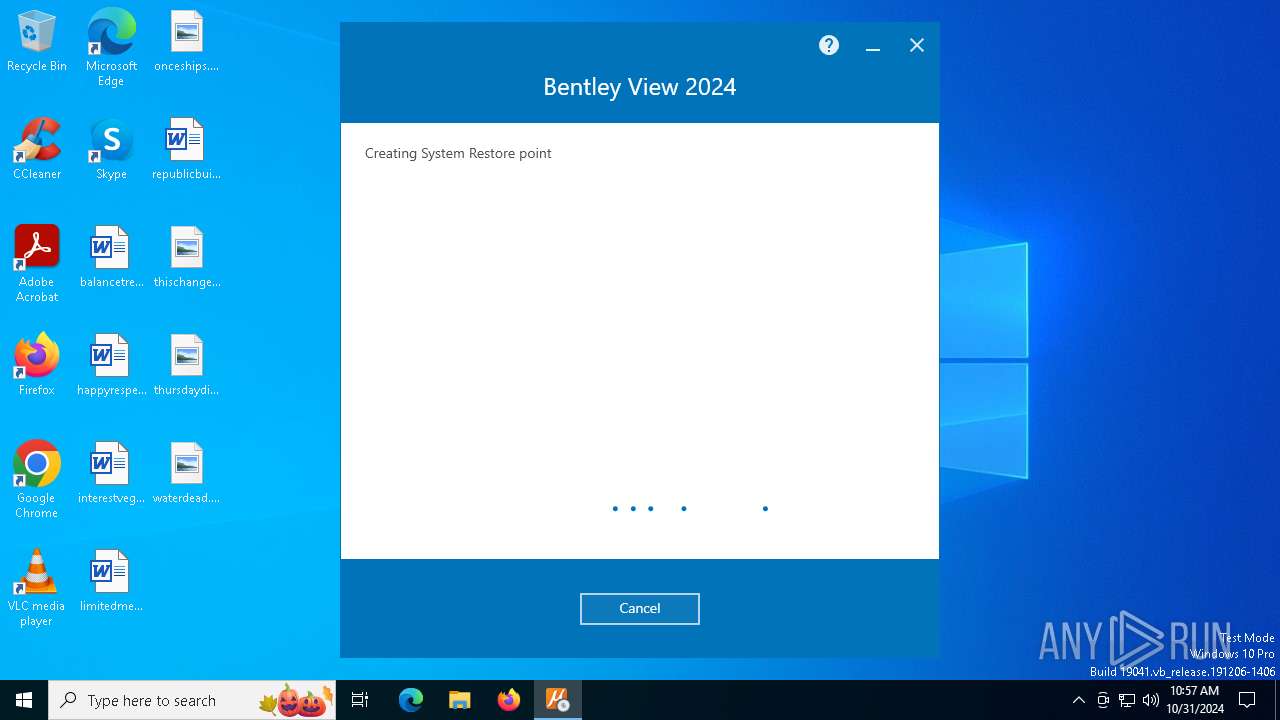
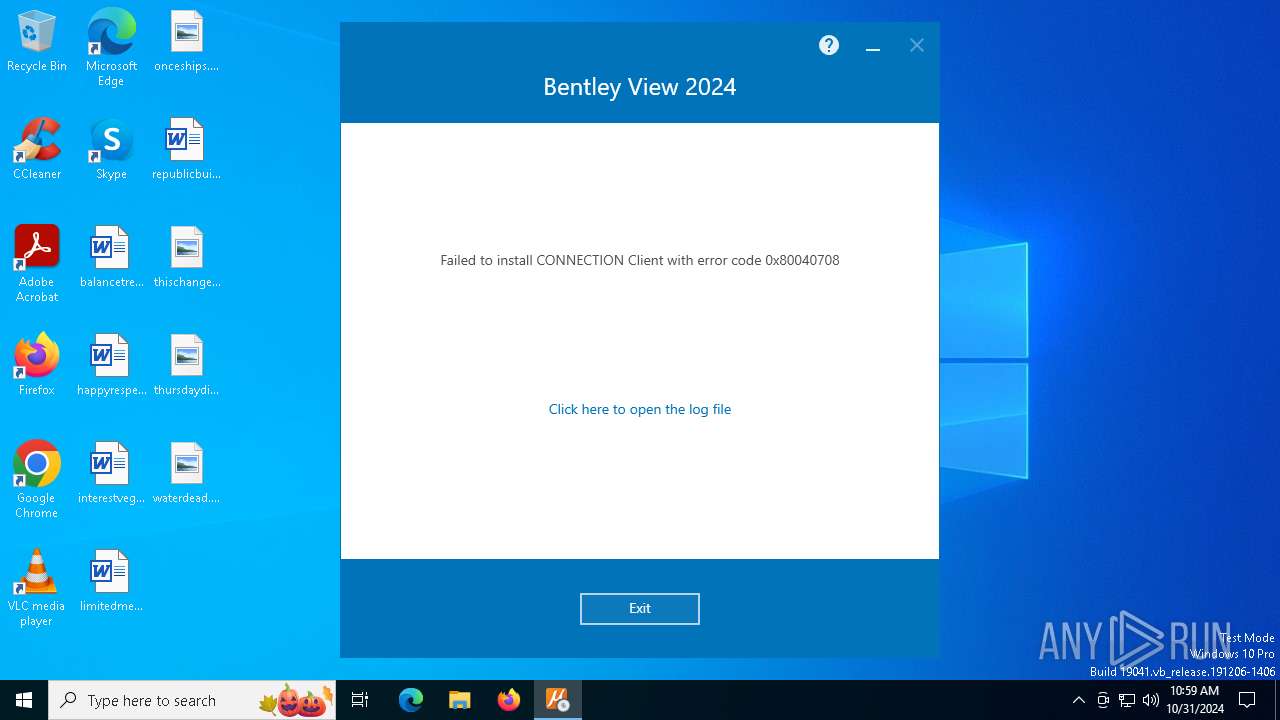
| File name: | Setup_Viewx64_24.00.00.122 (1).exe |
| Full analysis: | https://app.any.run/tasks/9d430215-1cc7-4608-bf11-695c13745e96 |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2024, 10:57:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | A4BC7B690F452D2DCCC78EBD9A602DC7 |
| SHA1: | 250903CB6D83C8A4344930668EDF2B15B46FFC3C |
| SHA256: | BC7F2CF175009C73E0A5BA339685429F0ACAB3B646B52AA795C0A2C4D75DEACA |
| SSDEEP: | 98304:F1svXJG6gIS6476e8cgYdeolDBDDDDDDgKWVCNgMCMuynEkmkYxD/Qi1PnQU+6bf:RHts1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 692)
Executable content was dropped or overwritten
- Setup_Viewx64_24.00.00.122 (1).exe (PID: 3128)
- Setup_Viewx64_24.00.00.122 (1).exe (PID: 6284)
- VC_redist.x64.exe (PID: 7760)
- Setup_Viewx64_24.00.00.122.exe (PID: 6564)
- VC_redist.x64.exe (PID: 7784)
- Setup_CONNECTIONClientx64_23.00.01.25.exe (PID: 8188)
- Setup_CONNECTIONClientx64_23.00.01.25.exe (PID: 6380)
- Setup_CONNECTIONClientx64_23.00.01.25.exe (PID: 7276)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 528)
Starts itself from another location
- Setup_Viewx64_24.00.00.122 (1).exe (PID: 3128)
- Setup_CONNECTIONClientx64_23.00.01.25.exe (PID: 6380)
Process drops legitimate windows executable
- Setup_Viewx64_24.00.00.122 (1).exe (PID: 3128)
- Setup_Viewx64_24.00.00.122.exe (PID: 6564)
- msiexec.exe (PID: 7588)
- VC_redist.x64.exe (PID: 7760)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 528)
- MicrosoftEdgeUpdate.exe (PID: 4316)
Starts a Microsoft application from unusual location
- VC_redist.x64.exe (PID: 7784)
- MicrosoftEdgeUpdate.exe (PID: 4316)
INFO
Manages system restore points
- SrTasks.exe (PID: 7316)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:22 22:14:43+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 314368 |
| InitializedDataSize: | 308736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x302e5 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 24.0.0.122 |
| ProductVersionNumber: | 24.0.0.122 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Bentley Systems, Incorporated |
| FileDescription: | Bentley View 2024 |
| FileVersion: | 24.0.0.122 |
| InternalName: | setup |
| LegalCopyright: | Copyright © 2024 Bentley Systems, Incorporated. All rights reserved. |
| OriginalFileName: | Setup_Viewx64_24.00.00.122.exe |
| ProductName: | Bentley View 2024 |
| ProductVersion: | 24.0.0.122 |
Total processes
160
Monitored processes
20
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\ProgramData\Package Cache\847B439D00D2629B3322F326E0558A7D9F96765A\MicrosoftEdgeWebView2RuntimeInstallerX64.exe" /silent /install | C:\ProgramData\Package Cache\847B439D00D2629B3322F326E0558A7D9F96765A\MicrosoftEdgeWebView2RuntimeInstallerX64.exe | Setup_CONNECTIONClientx64_23.00.01.25.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Setup Exit code: 2147747592 Version: 1.3.147.37 | |||||||||||||||
| 692 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "4316" "1896" "1528" "1892" "0" "0" "0" "0" "0" "0" "0" "0" | C:\Windows\SysWOW64\wermgr.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 3128 | "C:\Users\admin\AppData\Local\Temp\{268D61BF-26A5-4D5F-8393-D879CB326F79}\.cr\Setup_Viewx64_24.00.00.122 (1).exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\Setup_Viewx64_24.00.00.122 (1).exe" -burn.filehandle.attached=748 -burn.filehandle.self=576 | C:\Users\admin\AppData\Local\Temp\{268D61BF-26A5-4D5F-8393-D879CB326F79}\.cr\Setup_Viewx64_24.00.00.122 (1).exe | Setup_Viewx64_24.00.00.122 (1).exe | ||||||||||||
User: admin Company: Bentley Systems, Incorporated Integrity Level: MEDIUM Description: Bentley View 2024 Exit code: 2147747592 Version: 24.0.0.122 Modules
| |||||||||||||||
| 4316 | "C:\Program Files (x86)\Microsoft\Temp\EU348C.tmp\MicrosoftEdgeUpdate.exe" /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20WebView2%20Runtime&needsadmin=True" | C:\Program Files (x86)\Microsoft\Temp\EU348C.tmp\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeWebView2RuntimeInstallerX64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Exit code: 2147747592 Version: 1.3.147.37 | |||||||||||||||
| 6284 | "C:\Users\admin\AppData\Local\Temp\Setup_Viewx64_24.00.00.122 (1).exe" | C:\Users\admin\AppData\Local\Temp\Setup_Viewx64_24.00.00.122 (1).exe | explorer.exe | ||||||||||||
User: admin Company: Bentley Systems, Incorporated Integrity Level: MEDIUM Description: Bentley View 2024 Exit code: 2147747592 Version: 24.0.0.122 Modules
| |||||||||||||||
| 6380 | "C:\WINDOWS\Temp\{03190272-76B1-4CD8-B804-B26BF7F16A25}\.cr\Setup_CONNECTIONClientx64_23.00.01.25.exe" -burn.clean.room="C:\ProgramData\Package Cache\7988EE3B8B402410F5BE3E025AA1DB91F935EE90\Setup_CONNECTIONClientx64_23.00.01.25.exe" -burn.filehandle.attached=572 -burn.filehandle.self=536 /quiet SkipPendingSystemRebootCheck=1 /log C:\Users\admin\AppData\Local\Temp\Bentley_View_2024_20241031105714_003_BentleyConnectClient.log | C:\Windows\Temp\{03190272-76B1-4CD8-B804-B26BF7F16A25}\.cr\Setup_CONNECTIONClientx64_23.00.01.25.exe | Setup_CONNECTIONClientx64_23.00.01.25.exe | ||||||||||||
User: admin Company: Bentley Systems, Incorporated Integrity Level: HIGH Description: CONNECTION Client Exit code: 2147747592 Version: 23.0.1.25 | |||||||||||||||
| 6564 | "C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.be\Setup_Viewx64_24.00.00.122.exe" -q -burn.elevated BurnPipe.{0D1D2510-3615-4C05-8C45-E73E7336E0BE} {2B0DF709-F45B-4B28-AB9F-20D75C2D5803} 3128 | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.be\Setup_Viewx64_24.00.00.122.exe | Setup_Viewx64_24.00.00.122 (1).exe | ||||||||||||
User: admin Company: Bentley Systems, Incorporated Integrity Level: HIGH Description: Bentley View 2024 Exit code: 2147747592 Version: 24.0.0.122 Modules
| |||||||||||||||
| 7036 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7104 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 858
Read events
2 811
Write events
38
Delete events
9
Modification events
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3128) Setup_Viewx64_24.00.00.122 (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Setup_Viewx64_24_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
302
Suspicious files
57
Text files
126
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6284 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{268D61BF-26A5-4D5F-8393-D879CB326F79}\.cr\Setup_Viewx64_24.00.00.122 (1).exe | executable | |
MD5:BE0925C1612893A235138BBAE9703F7C | SHA256:B58F22C91657CCA4DF18B4CE09ADA30EE86B2A8A299FCC9627150E902C72E4A1 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\PPInstallerExtension.beext.dll | executable | |
MD5:9E3EFFF3338ED588F1524487D4048BE8 | SHA256:8A97B9F602757AE6A6D160E3A66B779817A23D1856ACB4CDE2BFB5E2449F1AFA | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\BootstrapperCore.dll | executable | |
MD5:E808F606E54D6F823B9D22F56E8982FC | SHA256:CF2AE76D1DA5AF70A72259E7E51DAE62C715BC32239DAF5DA6B1BDE122BCDAB6 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\Winterop.dll | executable | |
MD5:695BD38BB62302A0903E4CED008A73DD | SHA256:5EE45A965AA6BD6C00C795BDB394B9A8D911FBC8961EF62E55014F53EFE64F9F | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\mbapreq.wxl | xml | |
MD5:4D2C8D10C5DCCA6B938B71C8F02CA8A8 | SHA256:C63DE5F309502F9272402587A6BE22624D1BC2FEACD1BD33FB11E44CD6614B96 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\1028\mbapreq.wxl | xml | |
MD5:1D4B831F77EFEC96FFBC70BC4B59B8B5 | SHA256:1B93556F07C35AC0564D57E0743CCBA231950962C6506C8D4A74A31CD66FD04C | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\1031\mbapreq.wxl | xml | |
MD5:C8E7E0B4E63B3076047B7F49C76D56E1 | SHA256:631D46CB048FB6CF0B9A1362F8E5A1854C46E9525A0260C7841A04B2316C8295 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\1030\mbapreq.wxl | xml | |
MD5:7C6E4CE87870B3B5E71D3EF4555500F8 | SHA256:CAC263E0E90A4087446A290055257B1C39F17E11F065598CB2286DF4332C7696 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\1032\mbapreq.wxl | xml | |
MD5:074D5921AF07E6126049CB45814246ED | SHA256:B8E90E20EDF110AAAAEA54FBC8533872831777BE5589E380CFDD17E1F93147B5 | |||
| 3128 | Setup_Viewx64_24.00.00.122 (1).exe | C:\Users\admin\AppData\Local\Temp\{4894AA1C-137F-455F-84F4-46713E311F17}\.ba\mbahost.dll | executable | |
MD5:E3471734DF4345B4EC9F60333A96982B | SHA256:D728E7449243BC7099890BADB6FAE3F2B082A80D9C950E498051F89A65D48687 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
60
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3608 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3128 | Setup_Viewx64_24.00.00.122 (1).exe | 20.105.216.25:443 | aka.bentley.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3128 | Setup_Viewx64_24.00.00.122 (1).exe | 89.106.200.1:443 | communities.bentley.com | Enflow B.V. | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3128 | Setup_Viewx64_24.00.00.122 (1).exe | 149.96.243.108:443 | bentleysystems.service-now.com | SNC | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
aka.bentley.com |
| whitelisted |
communities.bentley.com |
| whitelisted |
www.bing.com |
| whitelisted |
bentleysystems.service-now.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |