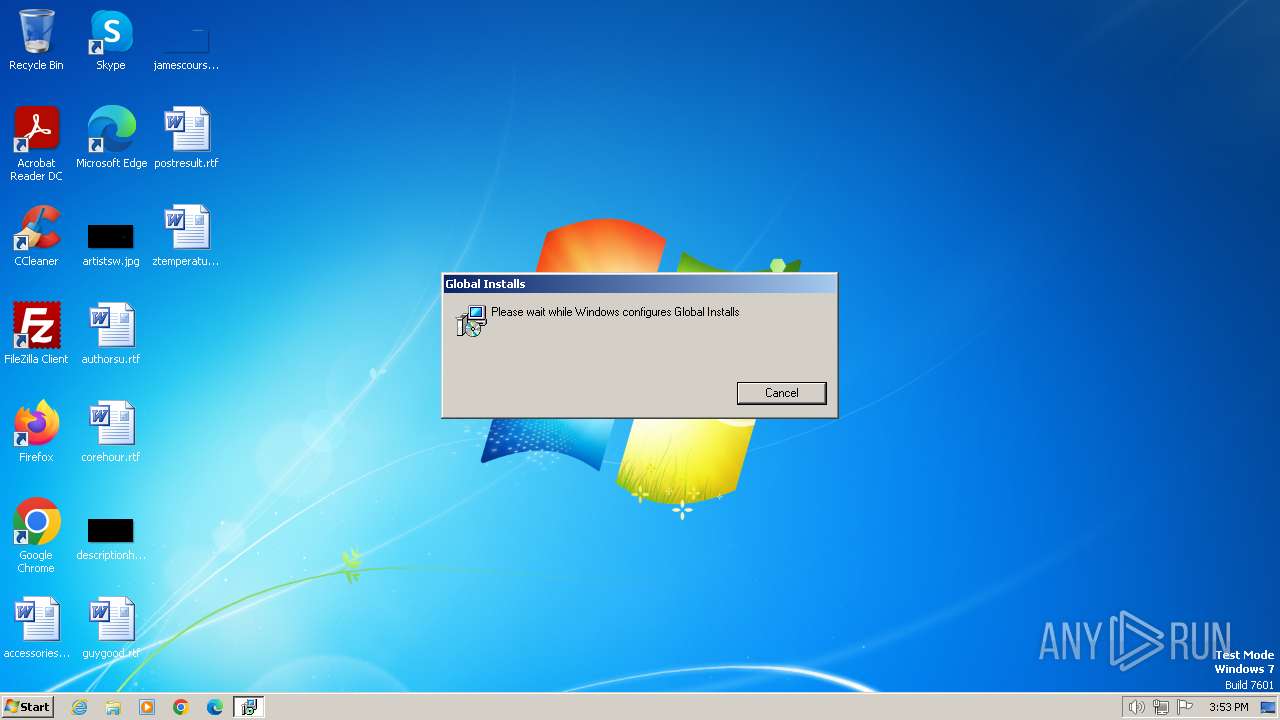
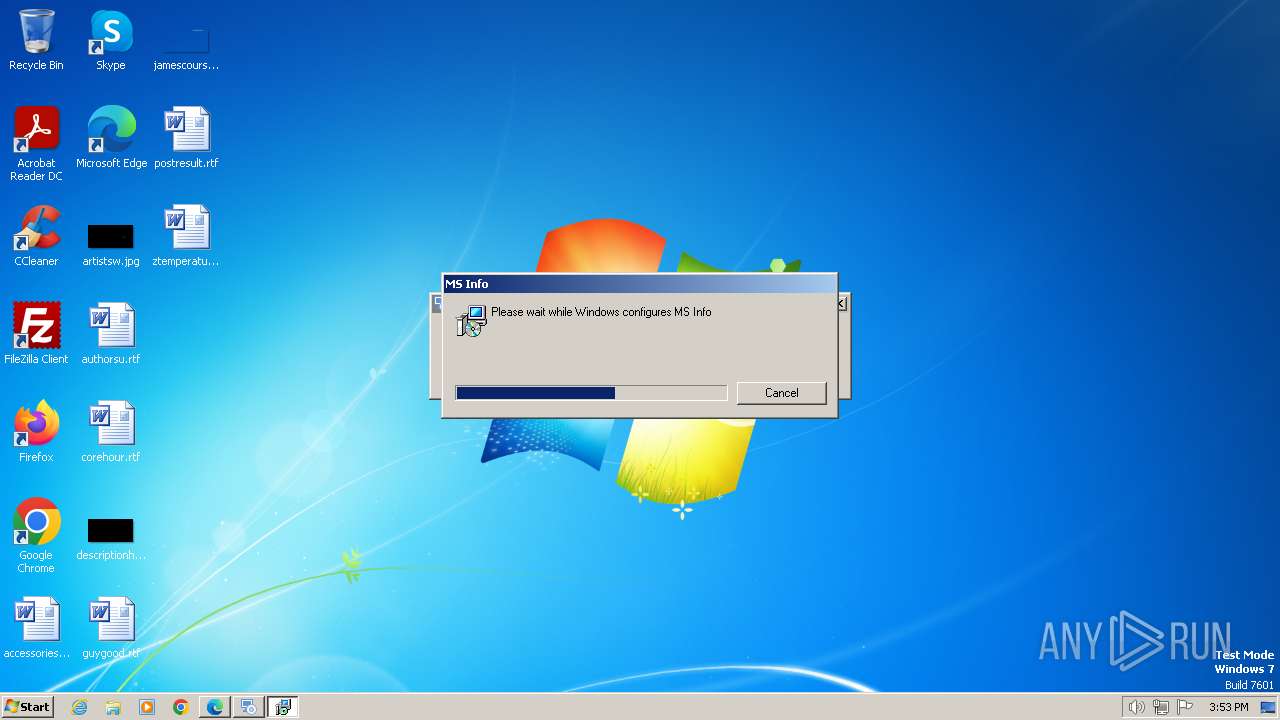
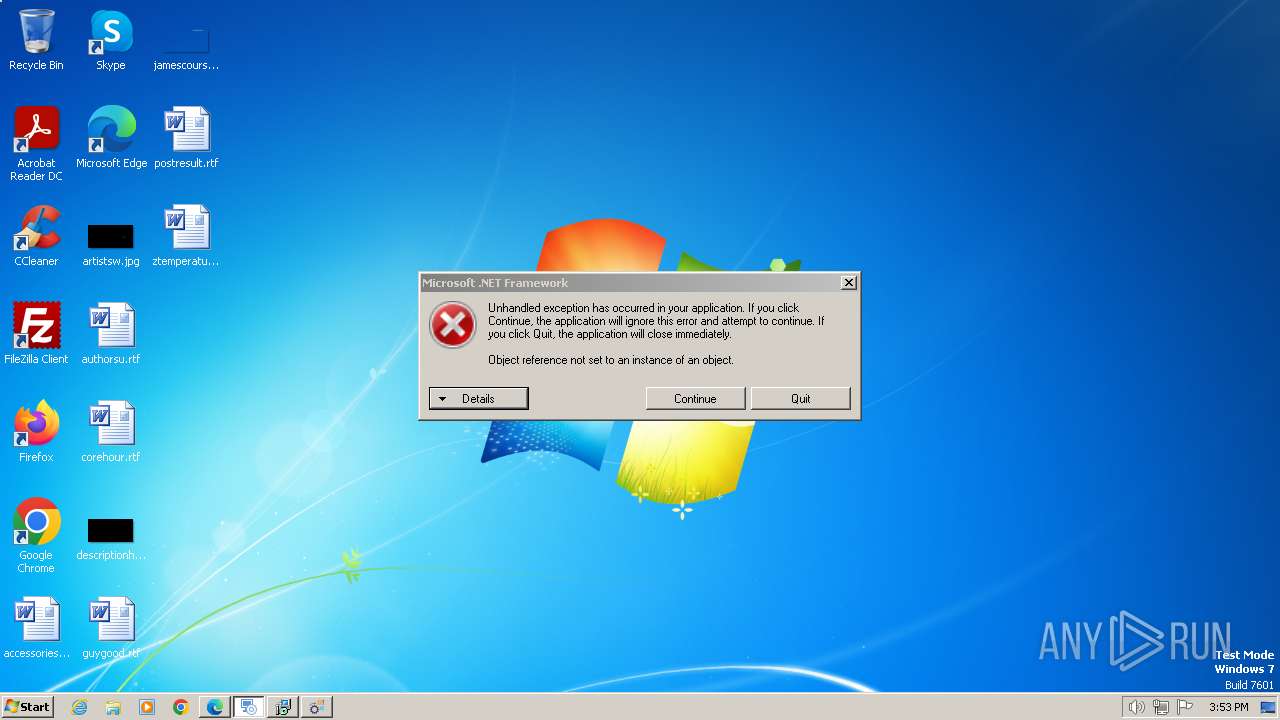
| File name: | Get Script.msi |
| Full analysis: | https://app.any.run/tasks/b181a5f5-19d9-4239-9134-ac2195806f05 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2024, 15:52:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {0E253F34-F71A-488F-8E96-892E01DBC8AC}, Number of Words: 2, Subject: Global Installs, Author: GlobalCo, Name of Creating Application: Global Installs, Template: ;1033, Comments: This installer database contains the logic and data required to install Global Installs., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Sun Dec 31 04:33:53 2023, Last Saved Time/Date: Sun Dec 31 04:33:53 2023, Last Printed: Sun Dec 31 04:33:53 2023, Number of Pages: 450 |
| MD5: | B63BD820A14D8ACFBDA0EEDD7A884268 |
| SHA1: | 207CBDA7E194C02E076984B3EE8EDDE9475AE426 |
| SHA256: | BC7CACF8352F528B20702CD768F57927F7B4C5B697F61942A8574EEE9A7DE050 |
| SSDEEP: | 98304:/9Iy5tVgKRFnETxBhBYfIgm/2D7BXdXAXWGULRJ0+3mwHsqmsoj:Y |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3700)
Creates a writable file in the system directory
- powershell.exe (PID: 2360)
SUSPICIOUS
Reads the Internet Settings
- RobustOperator.exe (PID: 2844)
- msiexec.exe (PID: 3700)
Executes as Windows Service
- RobustService.exe (PID: 2980)
- VSSVC.exe (PID: 3892)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2360)
Adds/modifies Windows certificates
- powershell.exe (PID: 2360)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 2360)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2360)
Reads security settings of Internet Explorer
- RobustOperator.exe (PID: 2844)
Application launched itself
- powershell.exe (PID: 2360)
Unusual connection from system programs
- powershell.exe (PID: 2360)
The Powershell connects to the Internet
- powershell.exe (PID: 2360)
Connects to unusual port
- RobustOperator.exe (PID: 2844)
Connects to FTP
- RobustService.exe (PID: 2980)
INFO
Create files in a temporary directory
- msiexec.exe (PID: 3700)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3700)
Checks supported languages
- RobustService.exe (PID: 2980)
- RobustOperator.exe (PID: 2844)
Reads the computer name
- RobustOperator.exe (PID: 2844)
- RobustService.exe (PID: 2980)
Creates files in the program directory
- RobustOperator.exe (PID: 2844)
Reads the software policy settings
- msiexec.exe (PID: 3700)
Reads the machine GUID from the registry
- RobustOperator.exe (PID: 2844)
- RobustService.exe (PID: 2980)
Reads Environment values
- RobustService.exe (PID: 2980)
Manual execution by a user
- chrome.exe (PID: 2360)
- explorer.exe (PID: 2828)
Application launched itself
- chrome.exe (PID: 2360)
Drops the executable file immediately after the start
- chrome.exe (PID: 2360)
Executable content was dropped or overwritten
- chrome.exe (PID: 2360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {0E253F34-F71A-488F-8E96-892E01DBC8AC} |
| Words: | 2 |
| Subject: | Global Installs |
| Author: | GlobalCo |
| LastModifiedBy: | - |
| Software: | Global Installs |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Global Installs. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:01:31 04:33:53 |
| ModifyDate: | 2024:01:31 04:33:53 |
| LastPrinted: | 2024:01:31 04:33:53 |
| Pages: | 450 |
Total processes
106
Monitored processes
26
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1612 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1352 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3984 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2152 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1444 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1040 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3708 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3744 --field-trial-handle=1148,i,17053803510532996362,13016799243974746430,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2360 | "C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -NonInteractive -NoLogo -ExecutionPolicy RemoteSigned -Command "C:\Windows\SystemTemp\AI_66A4.ps1 -paths 'C:\Users\admin\AppData\Roaming\GlobalCo\Global Installs\prerequisites\file_deleter.ps1','C:\Users\admin\AppData\Roaming\GlobalCo\Global Installs\prerequisites\aipackagechainer.exe','C:\Users\admin\AppData\Roaming\GlobalCo\Global Installs','C:\Users\admin\AppData\Roaming\GlobalCo' -retry_count 10" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | aipackagechainer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
30 096
Read events
29 710
Write events
368
Delete events
18
Modification events
| (PID) Process: | (3700) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B4E4BF64B961DA01340F00006C0F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B4E4BF64B961DA01340F0000C80E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B4E4BF64B961DA01340F0000940E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B4E4BF64B961DA01340F0000C00A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000068A9C464B961DA01340F00006C0F0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000068A9C464B961DA01340F0000940E0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000068A9C464B961DA01340F0000C80E0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000C20BC764B961DA01340F0000C00A0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3892) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 400000000000000046101066B961DA01340F0000C00A000001040000010000000000000000000000CF738494669A8047B9B53B57ADEDCBD00000000000000000 | |||
Executable files
2
Suspicious files
53
Text files
38
Unknown types
85
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:D82169B151B2E0954FA30EF7C116D0F2 | SHA256:3584A27F284BD5D57DBFD913B3473AF3886014AC68830908009A23D75EF4787C | |||
| 2360 | powershell.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\86844F70250DD8EF225D6B4178798C21_44AD5D0C299F1D4EE038B125B5E5863A | binary | |
MD5:7E2F43BE18E89B86F934B2C33AF93CD6 | SHA256:A34C179A2E29A6EAB428B763D4BCE6D6CAA2D57A9482E961F58FD2D3D13CEF3B | |||
| 3488 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gvyjdjbu.if0.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2360 | powershell.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94D97B1EC1F43DD6ED4FE7AB95E144BC_8DDC04EFB297854B49541C723EC3D642 | der | |
MD5:4D42D8BB0665C1571FC60FCE2AEFF906 | SHA256:C6A6ED7532A83D4A4677D67BF67514B32AD37D7B02ED6DC1E673DC8A0F51193E | |||
| 3700 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\TarEF72.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 2360 | powershell.exe | C:\Users\admin\AppData\Local\Temp\mluislsn.grr.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3700 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CabEF71.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3700 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1921a7.TMP | — | |
MD5:— | SHA256:— | |||
| 2360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
85
TCP/UDP connections
96
DNS requests
110
Threats
148
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3700 | msiexec.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?43acbfd2d70810b3 | unknown | compressed | 65.2 Kb | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
2908 | msiexec.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?086ab90f93ed01cb | unknown | — | — | unknown |
2908 | msiexec.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
3436 | msiexec.exe | POST | 200 | 54.156.181.99:80 | http://collect.installeranalytics.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3700 | msiexec.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2908 | msiexec.exe | 172.67.223.21:443 | globalinstaller.io | CLOUDFLARENET | US | unknown |
2908 | msiexec.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2908 | msiexec.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | unknown |
1808 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2668 | msedge.exe | 104.21.72.96:443 | typagesee.io | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
globalinstaller.io |
| unknown |
ocsp.pki.goog |
| whitelisted |
typagesee.io |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
trackingints.io |
| unknown |
downloaddowname.cfd |
| unknown |
downalekaemazo.pics |
| unknown |
campaignkeepy.buzz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2668 | msedge.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
146 ETPRO signatures available at the full report
Process | Message |
|---|---|
RobustOperator.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
RobustOperator.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
RobustOperator.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
RobustOperator.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
RobustOperator.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|