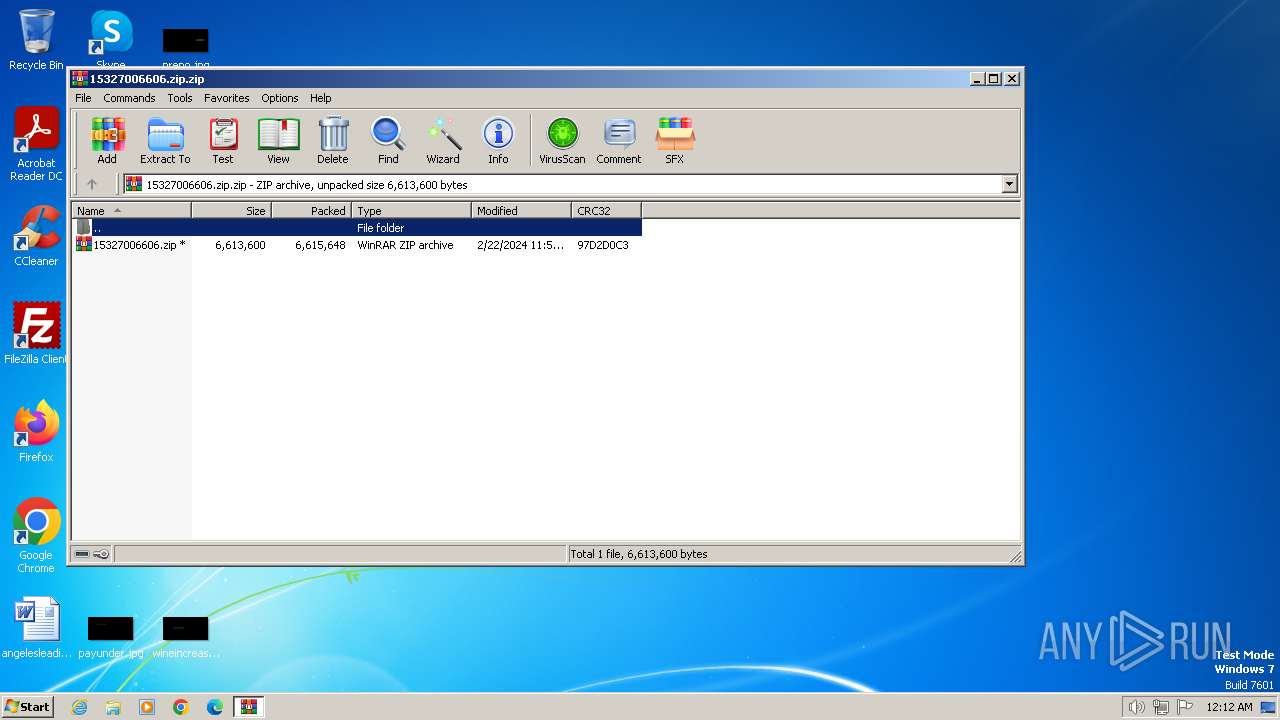
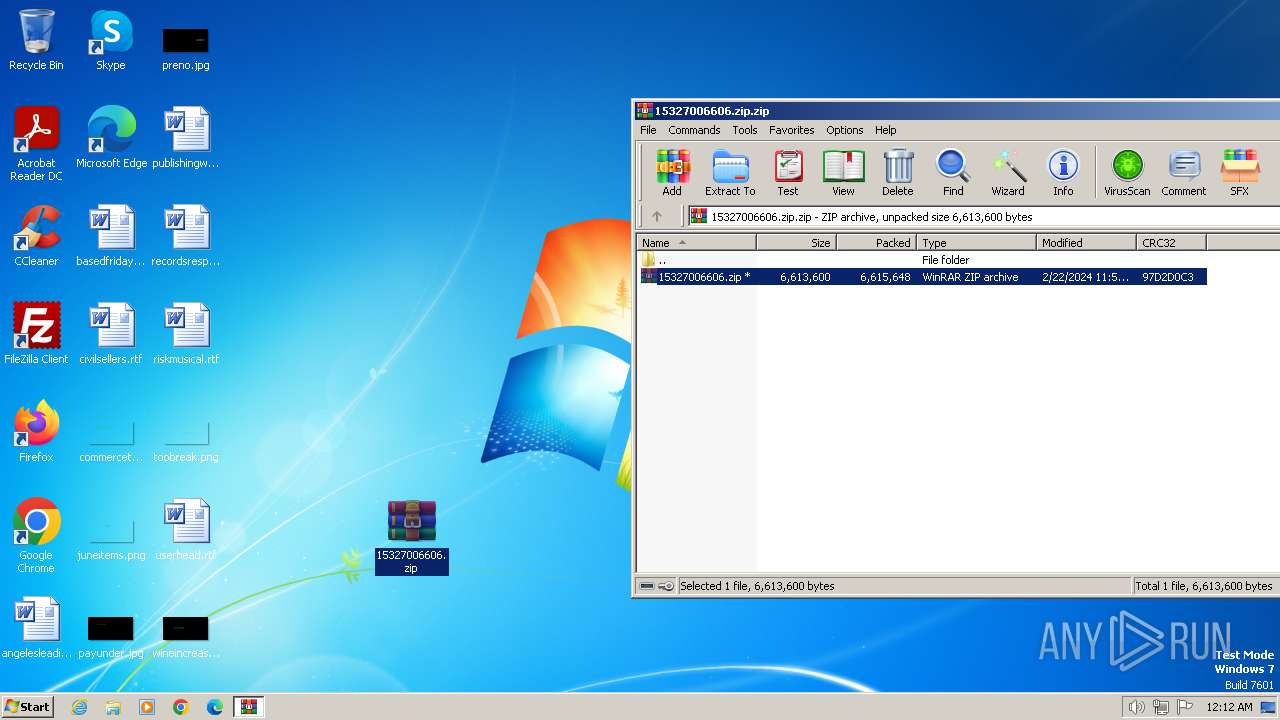
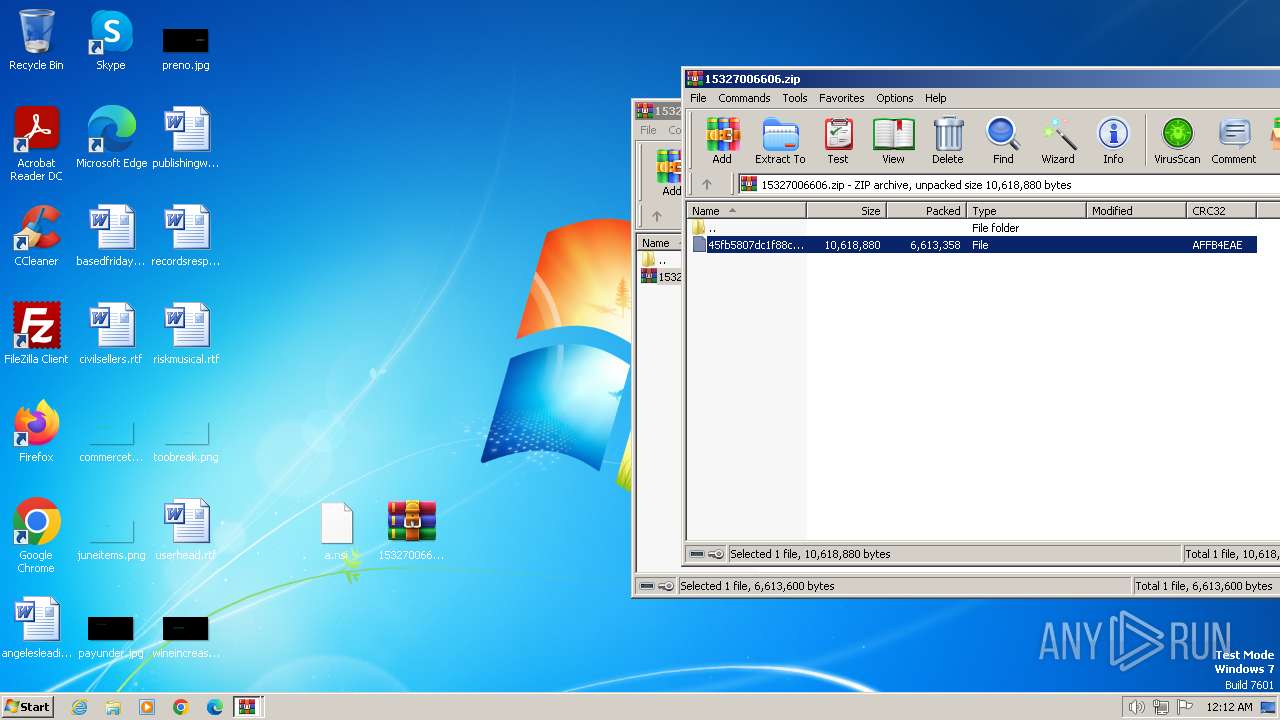
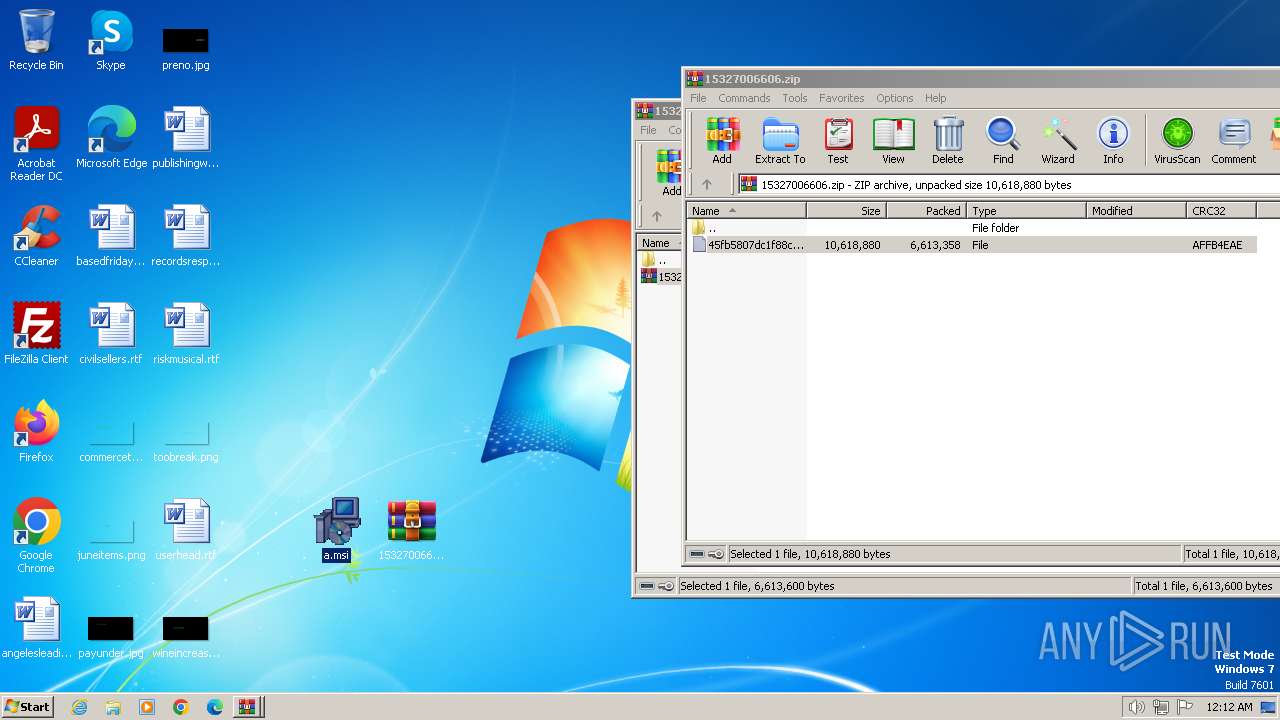
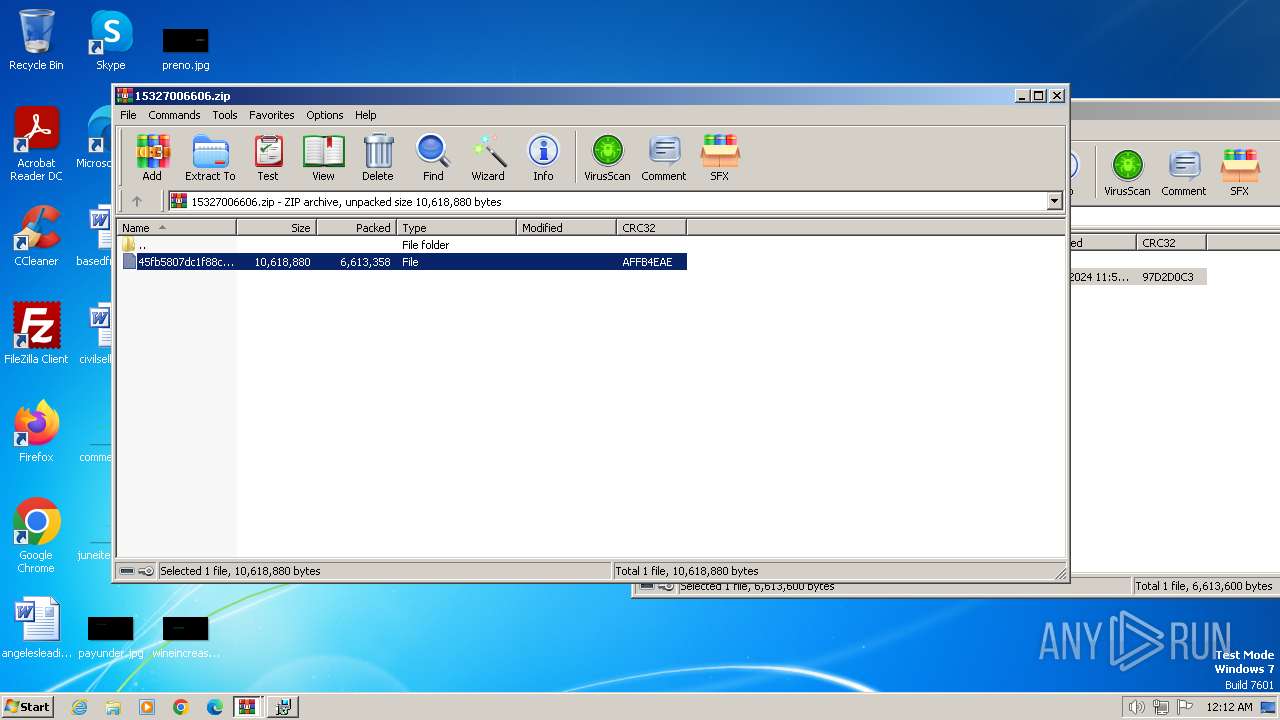
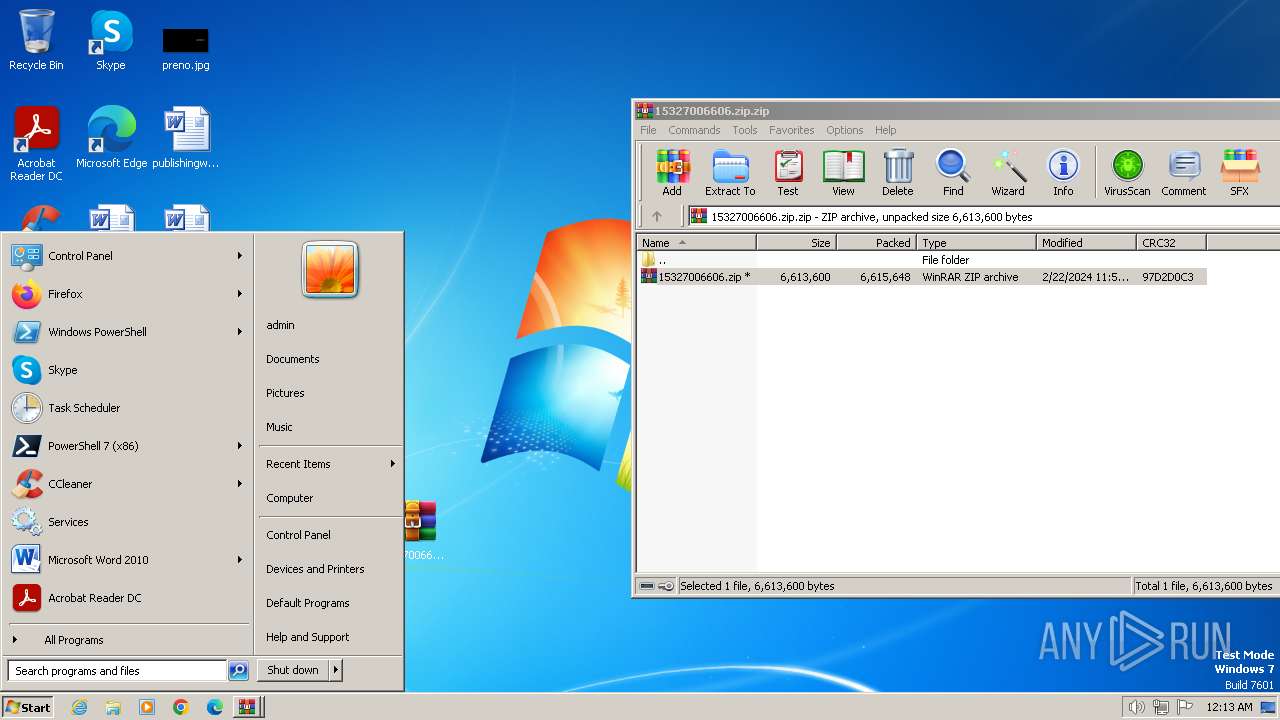
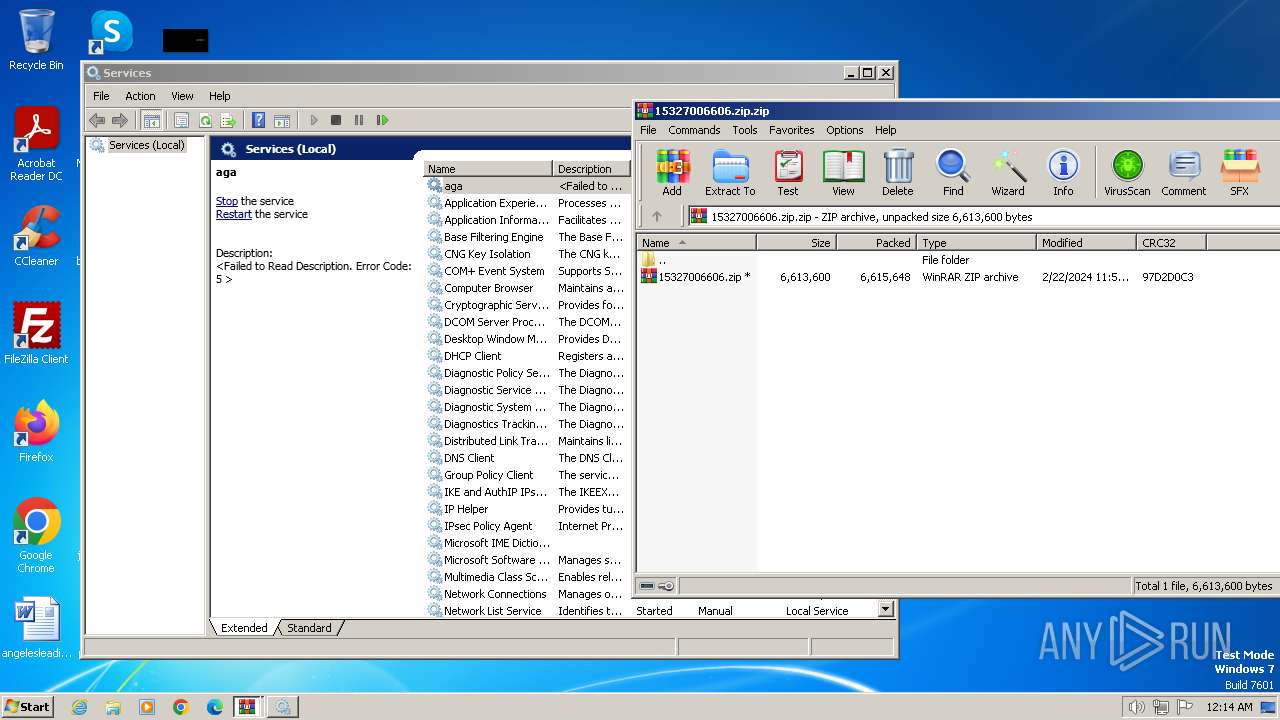
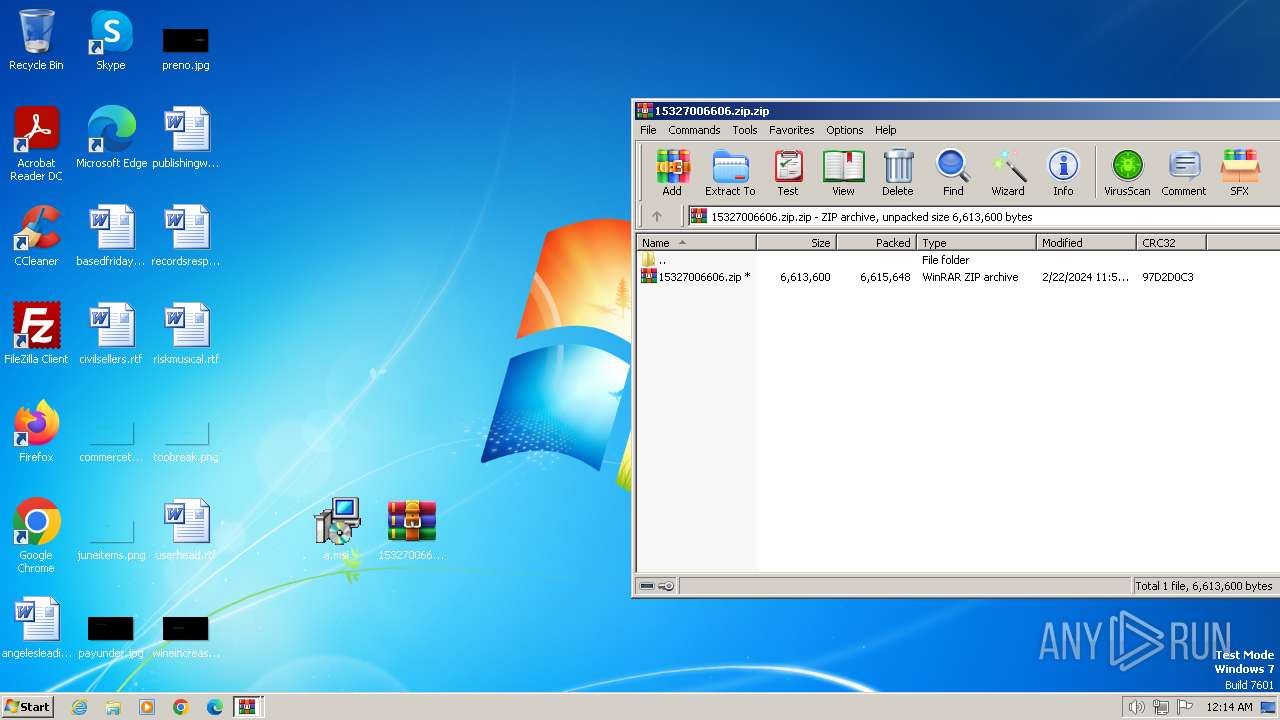
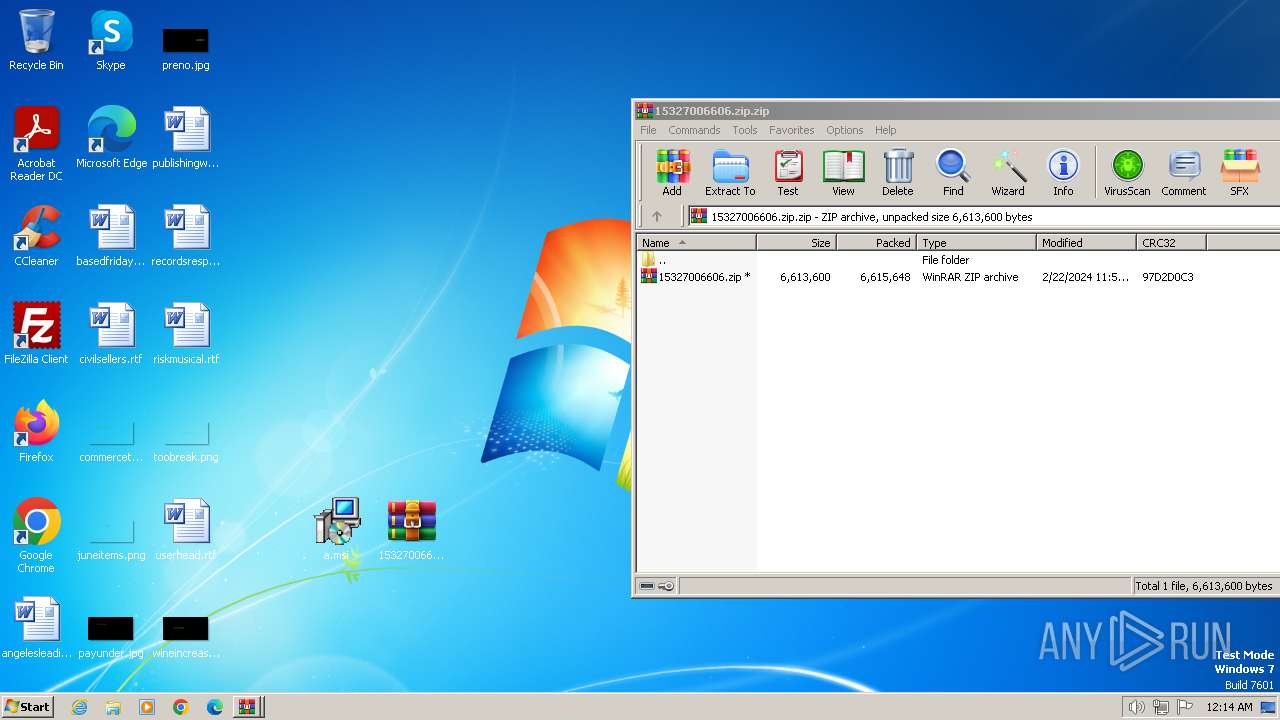
| File name: | 15327006606.zip.zip |
| Full analysis: | https://app.any.run/tasks/bdc01f73-b7ba-48dc-95a0-57b8392fa3a8 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 00:11:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
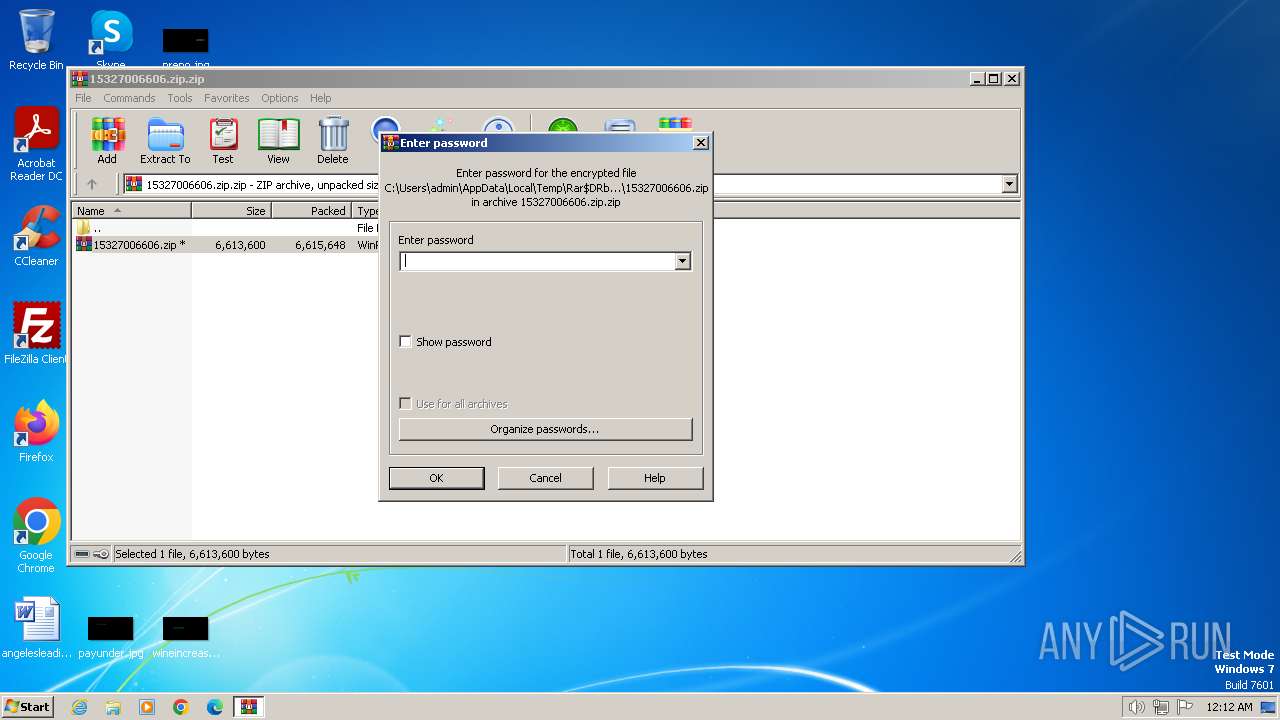
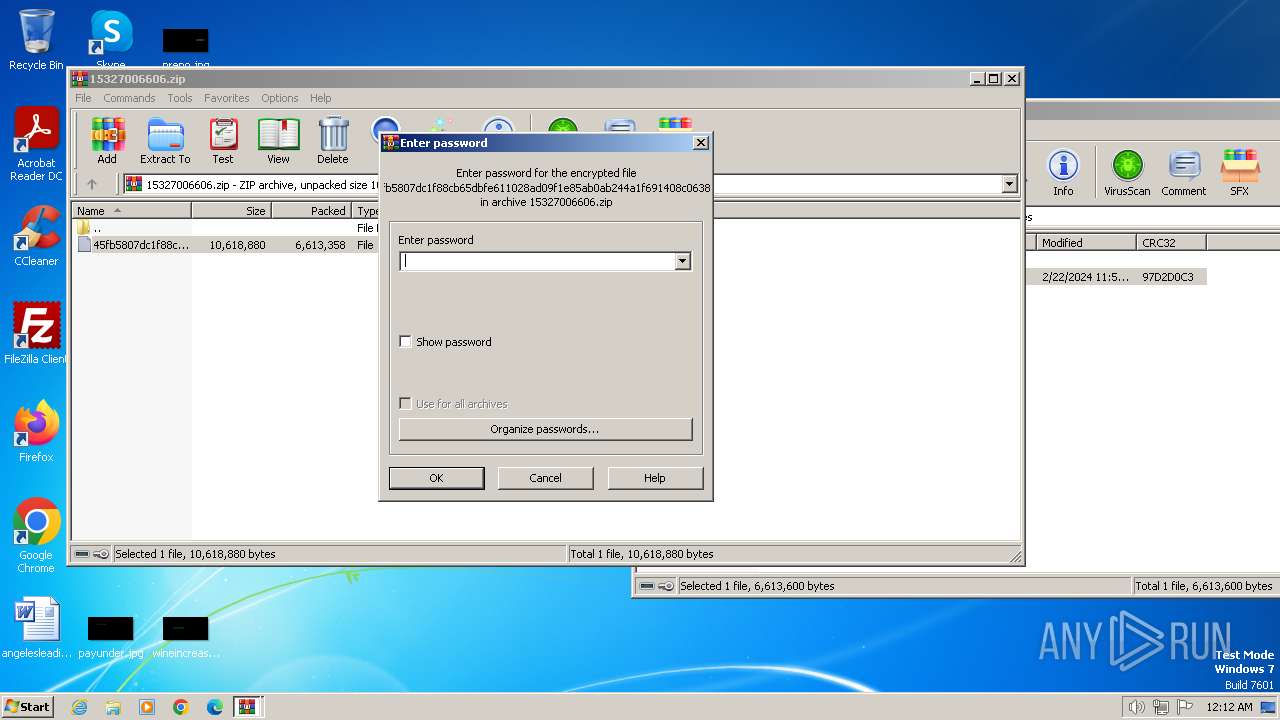
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 8DAB84DE721415A4E6D5CD33522D7378 |
| SHA1: | 77F631539556F085FCA4EEECB2DE79E8442C32E8 |
| SHA256: | BC7B3CE0C63C90E4AA386EF83F6C16CD8694BB525D630235F9E0656F5BDD3B6B |
| SSDEEP: | 98304:5TeGd2PTo6nr7XB5O8sCnZKDAHqM/3KrMm8JIVkpGPfgzO7f7FU1PBR6lFCmAxmF:BygSGiyqW88Spq |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3644)
- powershell.exe (PID: 3396)
SUSPICIOUS
Reads the Internet Settings
- msiexec.exe (PID: 2860)
- mmc.exe (PID: 3808)
The Powershell connects to the Internet
- powershell.exe (PID: 3644)
- powershell.exe (PID: 3396)
Unusual connection from system programs
- powershell.exe (PID: 3644)
- powershell.exe (PID: 3396)
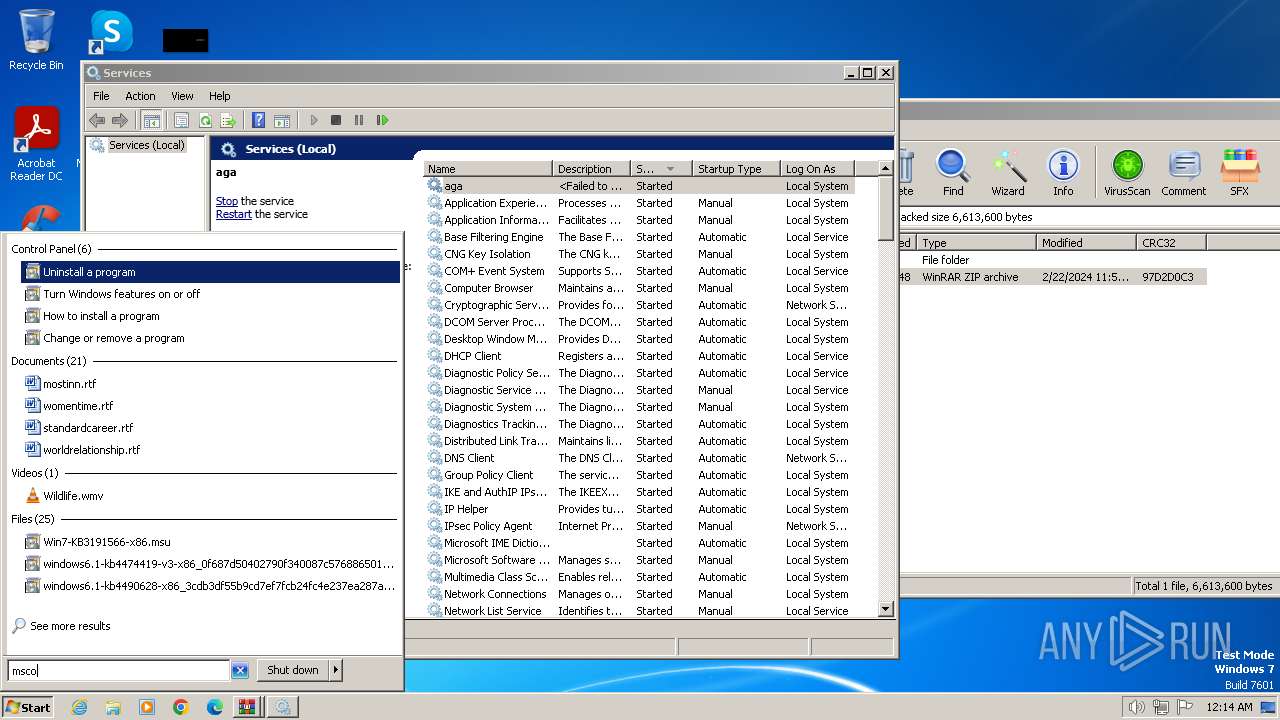
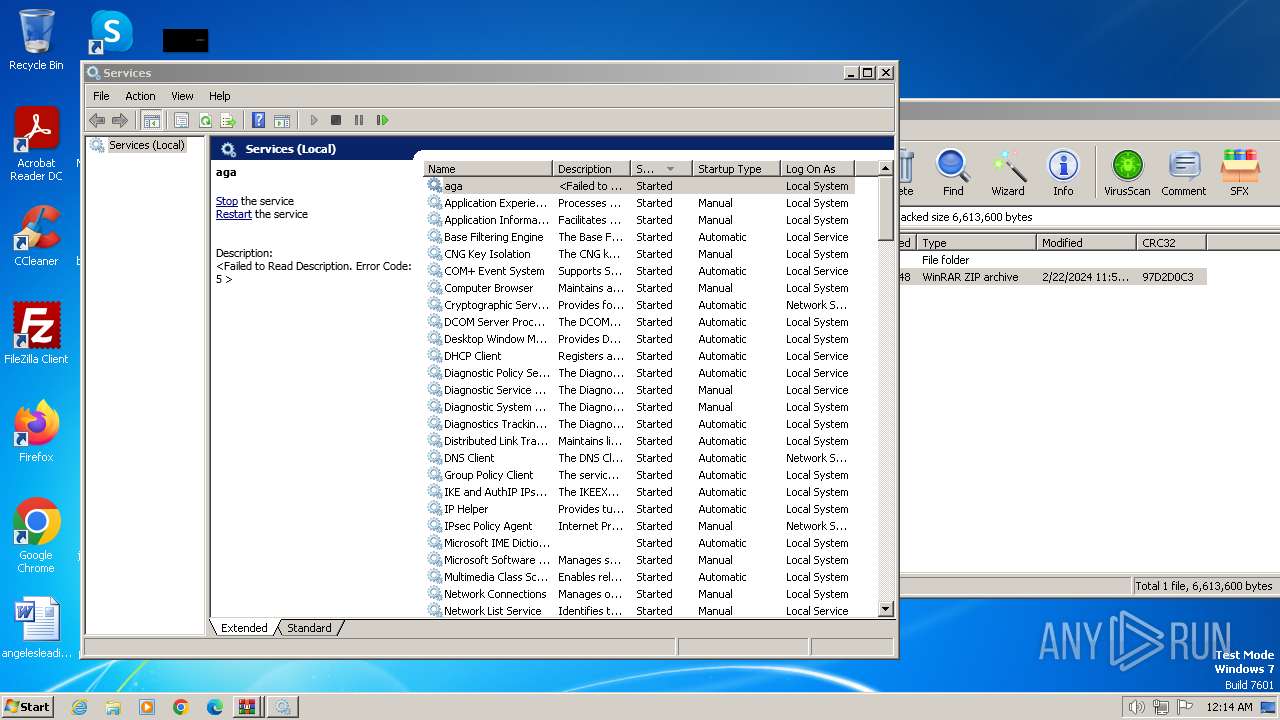
Executes as Windows Service
- VSSVC.exe (PID: 2240)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 3808)
Reads Internet Explorer settings
- mmc.exe (PID: 3808)
INFO
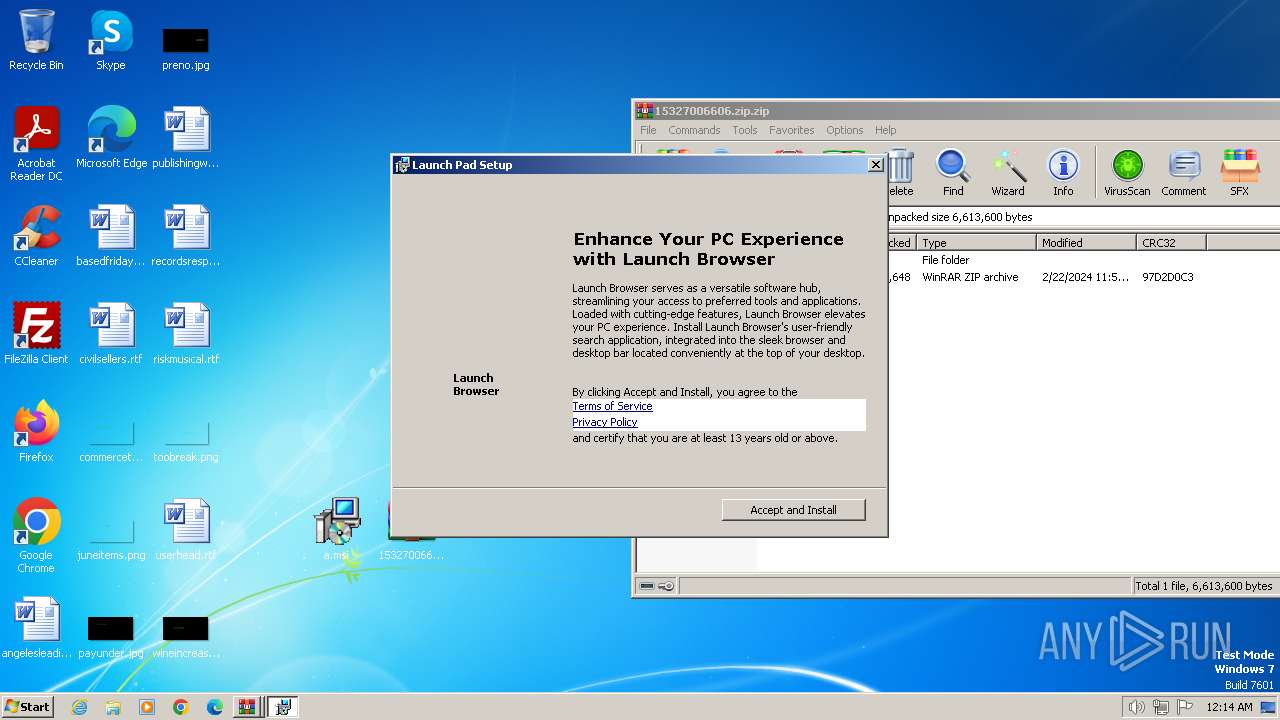
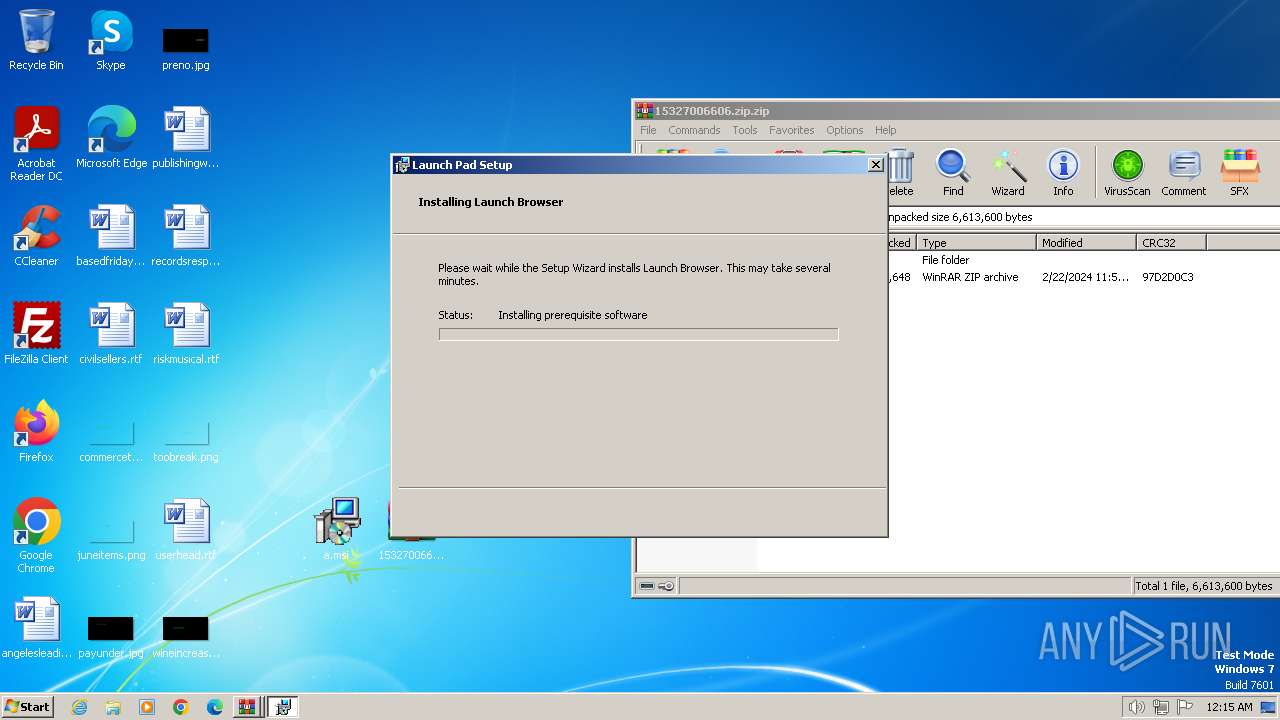
Manual execution by a user
- WinRAR.exe (PID: 3216)
- msiexec.exe (PID: 2860)
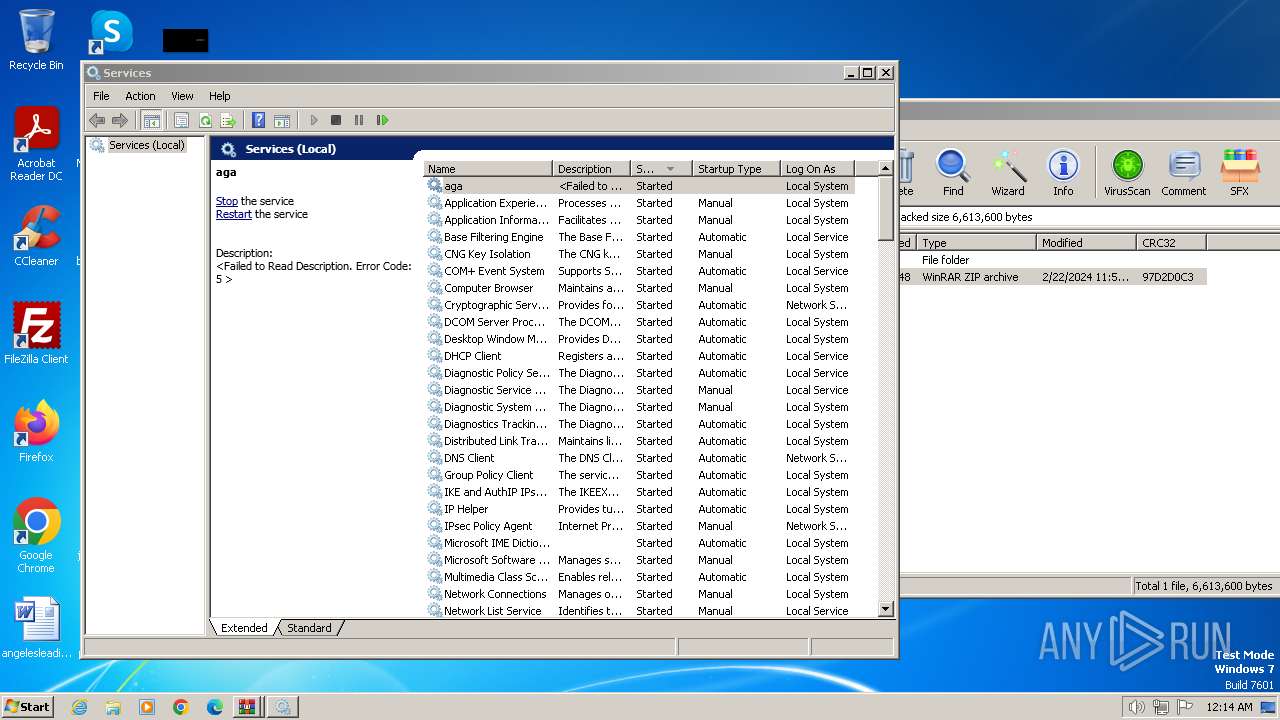
- mmc.exe (PID: 3808)
- mmc.exe (PID: 3140)
- msiexec.exe (PID: 3320)
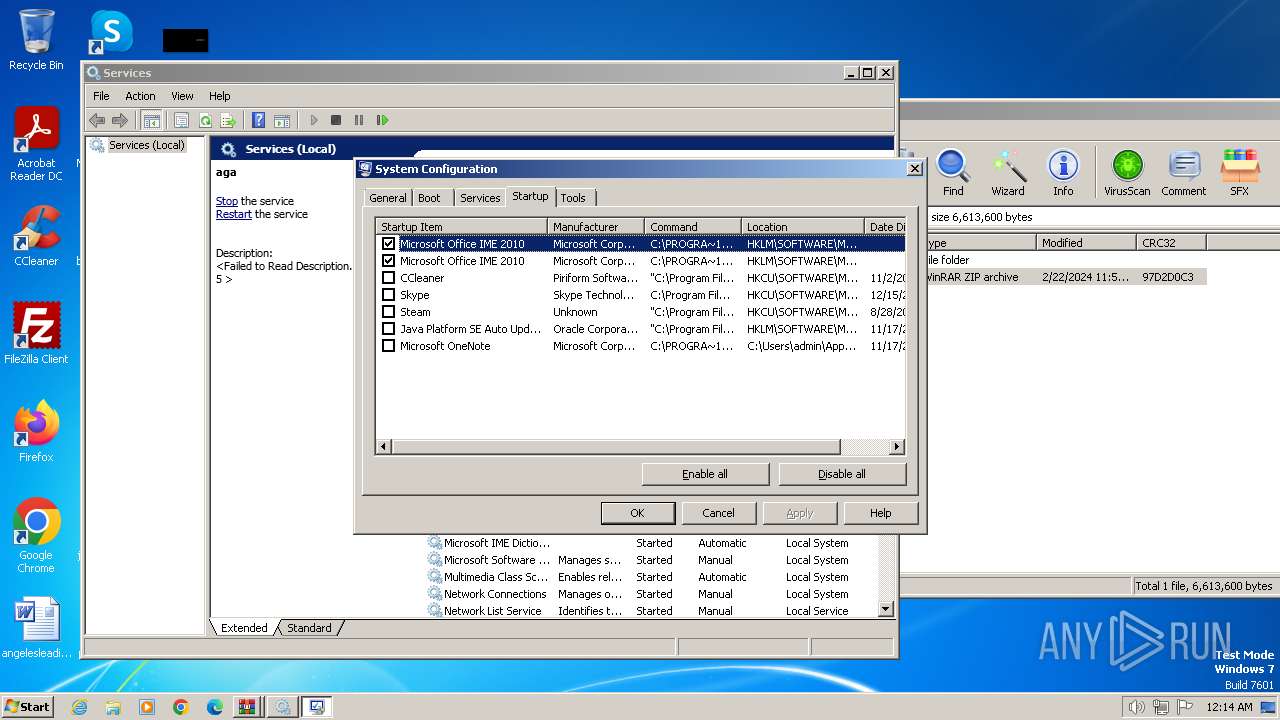
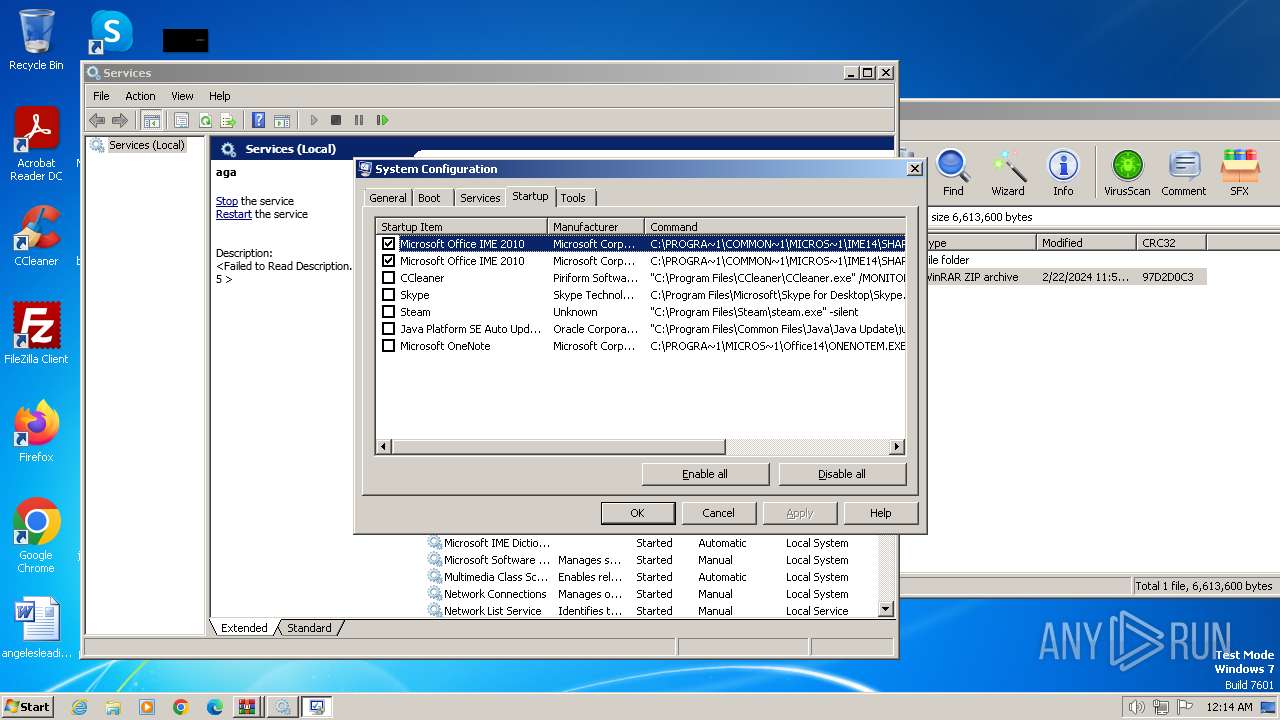
- msconfig.exe (PID: 3492)
- msconfig.exe (PID: 2476)
Create files in a temporary directory
- msiexec.exe (PID: 2860)
Creates files or folders in the user directory
- msiexec.exe (PID: 2860)
- mmc.exe (PID: 3808)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2860)
- mmc.exe (PID: 3808)
- msiexec.exe (PID: 3320)
Reads the software policy settings
- msiexec.exe (PID: 2860)
- msiexec.exe (PID: 3320)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2860)
- msiexec.exe (PID: 3320)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2860)
- msiexec.exe (PID: 3320)
Checks proxy server information
- mmc.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:02:22 23:58:48 |
| ZipCRC: | 0x97d2d0c3 |
| ZipCompressedSize: | 6615648 |
| ZipUncompressedSize: | 6613600 |
| ZipFileName: | 15327006606.zip |
Total processes
127
Monitored processes
11
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2240 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Windows\system32\msconfig.exe" | C:\Windows\System32\msconfig.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: System Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
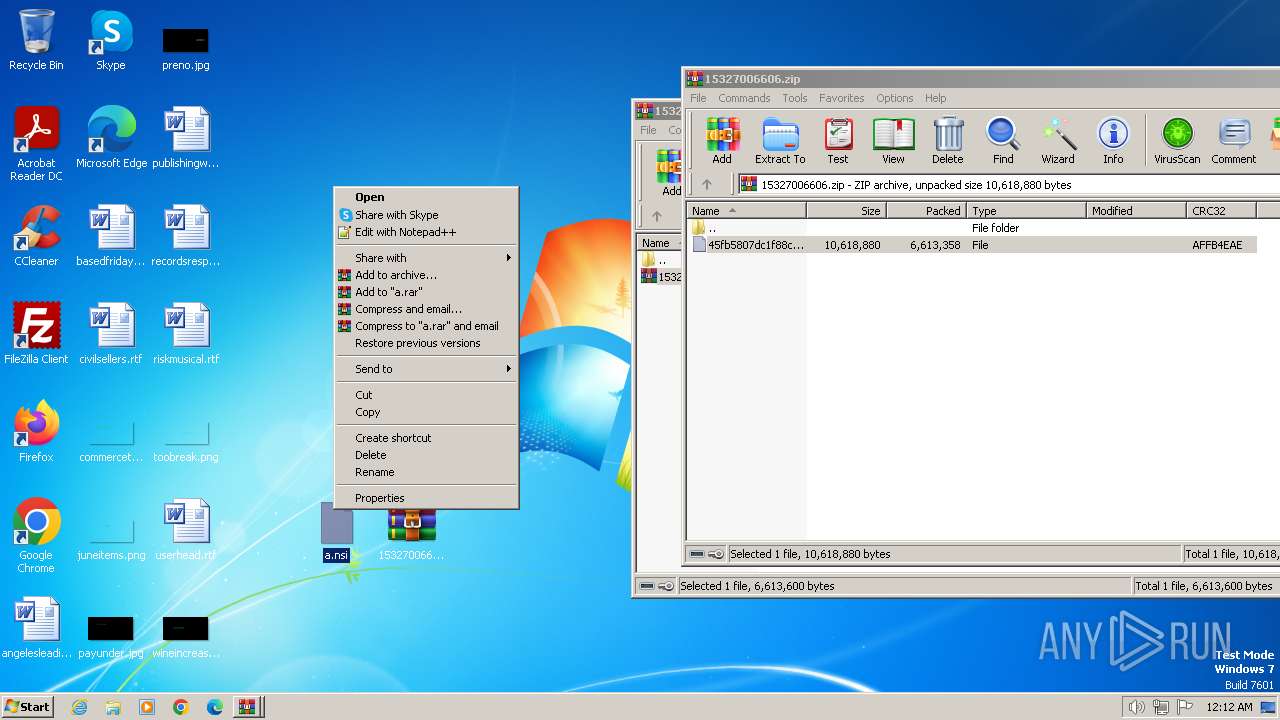
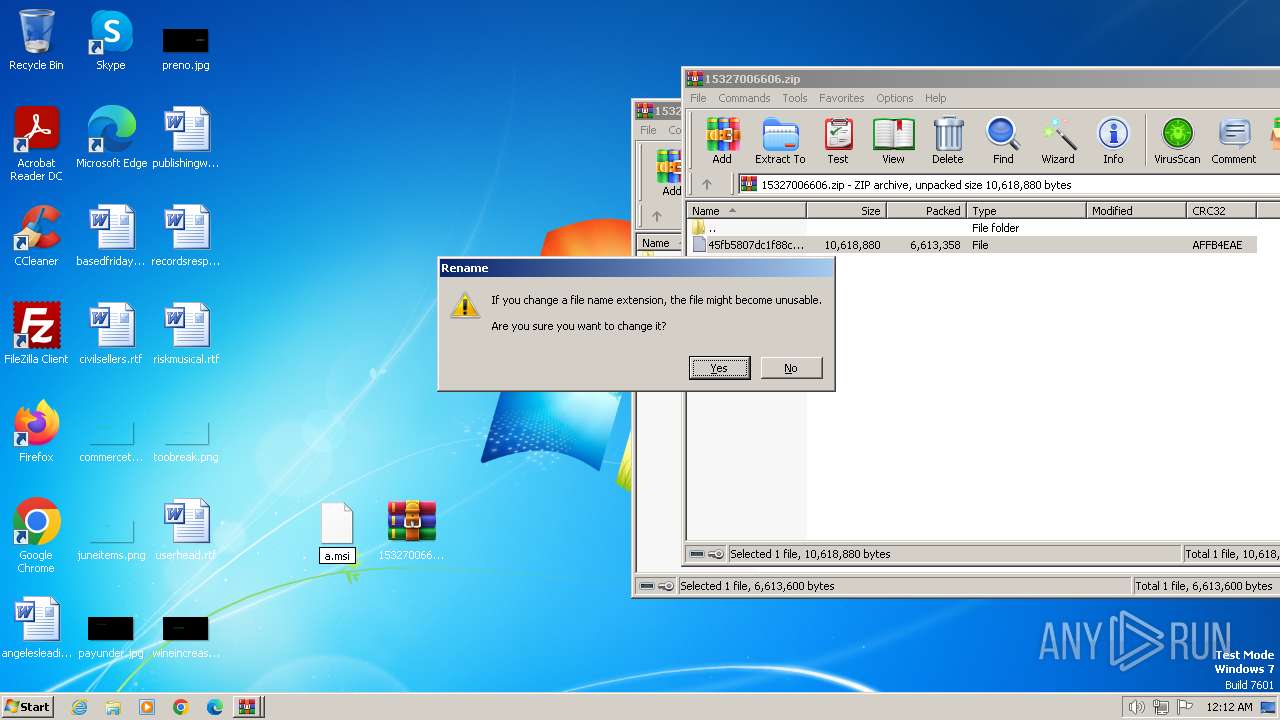
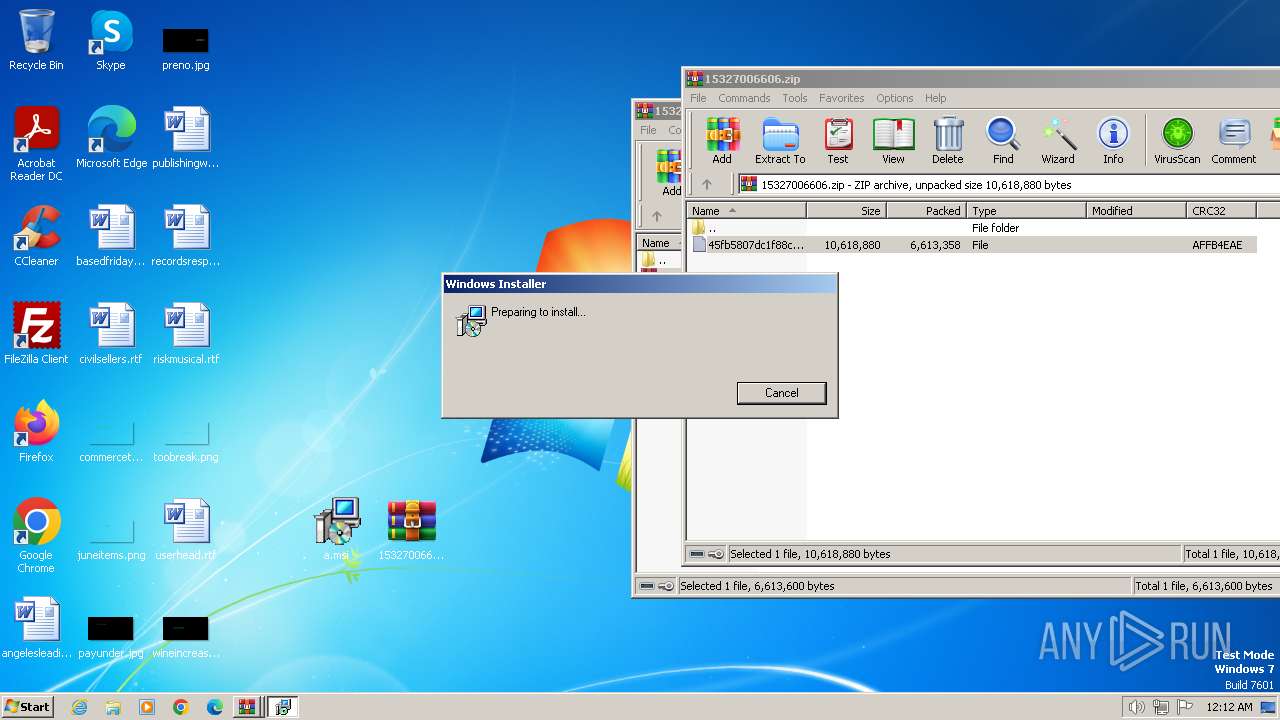
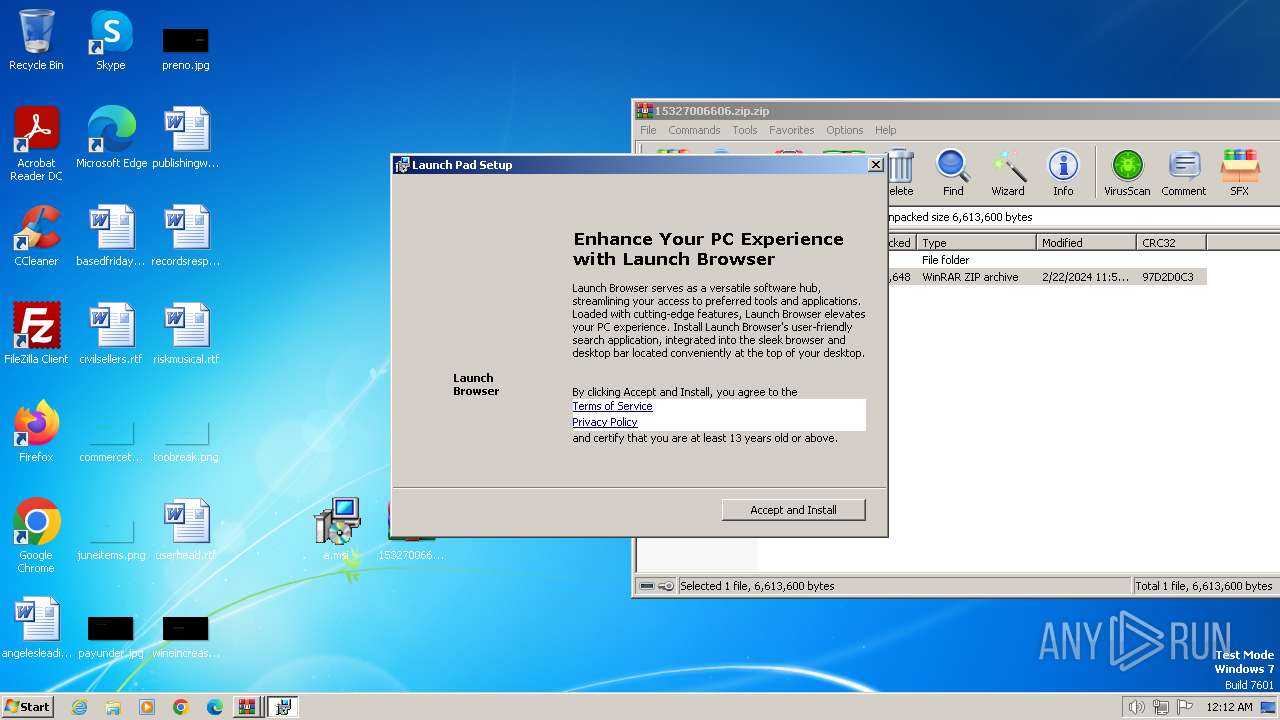
| 2860 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\a.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3140 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3216 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\15327006606.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3320 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\a.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3396 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noninteractive -ExecutionPolicy bypass -c "$w="$env:LOCALAPPDATA"+'/OPWC/';[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'OperaSharpDLL.dll'));[OperaSharpDLL.Helper]::Startup(1)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | MSIB621.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3492 | "C:\Windows\system32\msconfig.exe" | C:\Windows\System32\msconfig.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Configuration Utility Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noninteractive -ExecutionPolicy bypass -c "$w="$env:LOCALAPPDATA"+'/OPWC/';[Reflection.Assembly]::Load([System.IO.File]::ReadAllBytes($w+'OperaSharpDLL.dll'));[OperaSharpDLL.Helper]::Startup(1)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | MSIF2A4.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3808 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\services.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 512
Read events
22 323
Write events
186
Delete events
3
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\15327006606.zip.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
37
Suspicious files
10
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
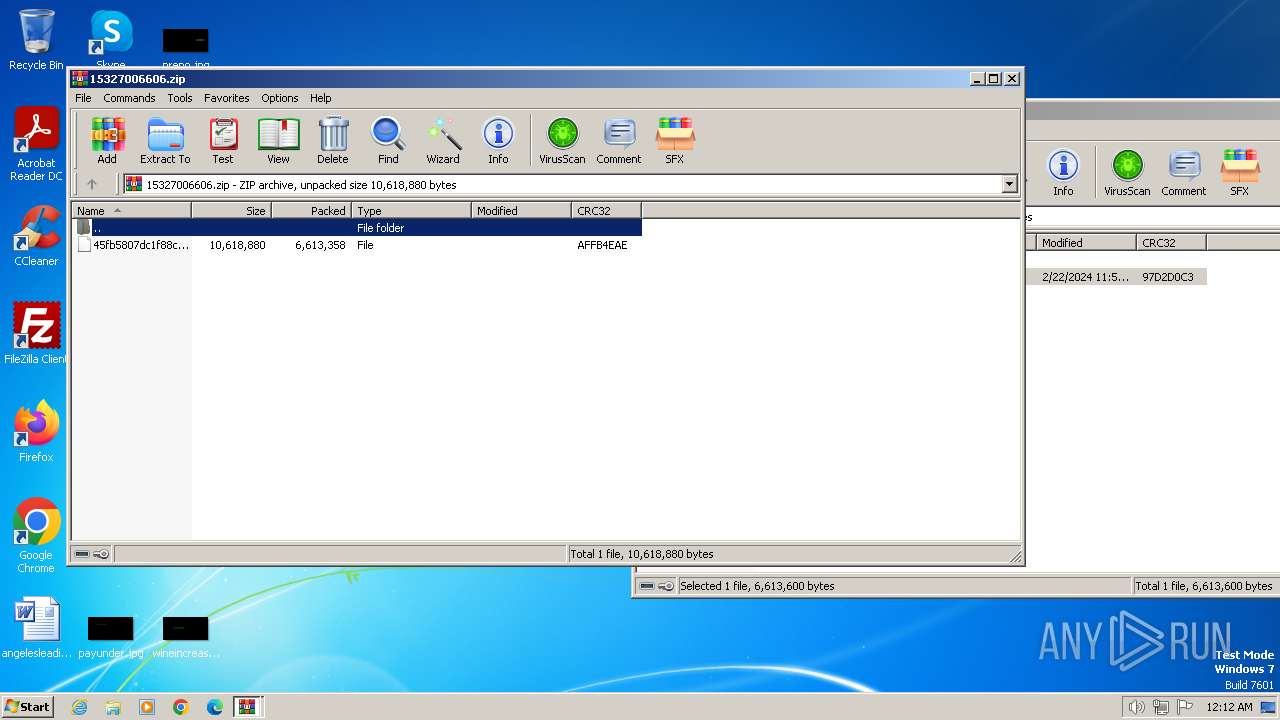
| 3216 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3216.12260\45fb5807dc1f88cb65dbfe611028ad09f1e85ab0ab244a1f691408c063851cc1 | — | |
MD5:— | SHA256:— | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C5C8CC0A7FE31816B4641D0465402560 | der | |
MD5:E94FB54871208C00DF70F708AC47085B | SHA256:7B9D553E1C92CB6E8803E137F4F287D4363757F5D44B37D52F9FCA22FB97DF86 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA941.tmp | executable | |
MD5:FB4665320C9DA54598321C59CC5ED623 | SHA256:9FB3156C665211A0081B189142C1D1AB18CDA601EE54D5F5D8883ECFA4177A59 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIACEC.tmp | executable | |
MD5:FB4665320C9DA54598321C59CC5ED623 | SHA256:9FB3156C665211A0081B189142C1D1AB18CDA601EE54D5F5D8883ECFA4177A59 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIBBE4.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA529.tmp | executable | |
MD5:FB4665320C9DA54598321C59CC5ED623 | SHA256:9FB3156C665211A0081B189142C1D1AB18CDA601EE54D5F5D8883ECFA4177A59 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIBB95.tmp | executable | |
MD5:6119E62D8047032A715BA0670FC476C5 | SHA256:BC31F85266DF2CDFDBE22149937105388FA3ADC17E3646FA4A167736E819AF77 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE170.tmp | executable | |
MD5:FB4665320C9DA54598321C59CC5ED623 | SHA256:9FB3156C665211A0081B189142C1D1AB18CDA601EE54D5F5D8883ECFA4177A59 | |||
| 2860 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIBC34.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
14
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2860 | msiexec.exe | GET | 200 | 104.18.20.226:80 | http://secure.globalsign.com/cacert/codesigningrootr45.crt | unknown | binary | 1.37 Kb | unknown |
2860 | msiexec.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?84ad992363c0e1c3 | unknown | compressed | 65.2 Kb | unknown |
268 | powershell.exe | POST | 200 | 99.86.105.6:80 | http://d2q8odwdblz94i.cloudfront.net/ | unknown | binary | 19 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2860 | msiexec.exe | 104.18.20.226:80 | secure.globalsign.com | CLOUDFLARENET | — | shared |
2860 | msiexec.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2788 | powershell.exe | 52.222.153.77:443 | d1bxm9wzv2im84.cloudfront.net | AMAZON-02 | US | unknown |
2128 | powershell.exe | 99.86.105.6:443 | d2q8odwdblz94i.cloudfront.net | AMAZON-02 | US | unknown |
268 | powershell.exe | 99.86.105.6:80 | d2q8odwdblz94i.cloudfront.net | AMAZON-02 | US | unknown |
3644 | powershell.exe | 99.86.105.6:443 | d2q8odwdblz94i.cloudfront.net | AMAZON-02 | US | unknown |
3084 | powershell.exe | 99.86.105.6:443 | d2q8odwdblz94i.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
secure.globalsign.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
d1bxm9wzv2im84.cloudfront.net |
| unknown |
d2q8odwdblz94i.cloudfront.net |
| unknown |